Abstract
With the rapid growth in wireless communication and IoT technologies, Radio Frequency Identification (RFID) is applied to the Internet of Vehicles (IoV) to ensure the security of private data and the accuracy of identification and tracking. However, in traffic congestion scenarios, frequent mutual authentication increases the overall computing and communication overhead of the network. For this reason, in this work, we propose a lightweight RFID security fast authentication protocol for traffic congestion scenarios, designing an ownership transfer protocol to transfer access rights to vehicle tags in non-congestion scenarios. The edge server is used for authentication, and the elliptic curve cryptography (ECC) algorithm and the hash function are combined to ensure the security of vehicles’ private data. The Scyther tool is used for the formal analysis of the proposed scheme, and this analysis shows that the proposed scheme can resist typical attacks in mobile communication of the IoV. Experimental results show that, compared to other RFID authentication protocols, the calculation and communication overheads of the tags proposed in this work are reduced by 66.35% in congested scenarios and 66.67% in non-congested scenarios, while the lowest are reduced by 32.71% and 50%, respectively. The results of this study demonstrate a significant reduction in the computational and communication overhead of tags while ensuring security.
1. Introduction
RFID [1] is one of the fundamental technologies in the Internet of Things (IoT) [2]. It can identify specific targets and read relevant data through radio signals without the need for direct contact with the targets. The Internet of Vehicles is an important component of the Internet of Things, in which vehicles can exchange data with roadside infrastructure. Such a network can help drivers better grasp traffic information and ensure road safety [3,4]. The rapid development of IoT [5,6] has driven the application of RFID in IoV. RFID has been used in various IoV scenarios, such as vehicle location tracking and traffic prediction [7,8,9,10]. Any roadside unit (RSU) must meet contactless and rapid identification requirements and read information from passing vehicles. RFID tags can be embedded in vehicles and associated with other vehicle information, such as vehicle identity and location information, to identify and track vehicle location and movement.
During vehicle identification, location and driving information can be leaked or falsified [11,12,13], and RFID is vulnerable to attacks during wireless transmission. To ensure the accuracy of IoV traffic information, RFID authentication is required before using the reader for identification reading. This is crucial to ensure that the privacy data from the vehicle network remain secure and that information identification remains accurate. RFID authentication for IoV has become an important issue for many scholars. Based on different identification methods, RFID tags can be divided into active and passive tags, as well as semiactive tags. Active and passive tags have very limited storage capacity and computing power [14,15], which poses a greater security threat to RFID tags. Therefore, RFID authentication protocols must be lightweight and secure to provide effective protection.
When traffic is congested, vehicles tend to stay in one place for long periods of time. As a result, the RSU and the vehicle will perform frequent mutual authentication, which can lead to a significant amount of computation and communication overhead. However, longer authentication intervals can reduce security, so it is important to balance security and overhead by reducing the authentication time. In non-congested scenarios, vehicles move faster, and RFID authentication needs to be performed quickly to ensure that the reader on the RSU can read all vehicle tags within the range [16]. Figure 1 illustrates the RFID authentication framework for IoV. The contributions of this paper are as follows.
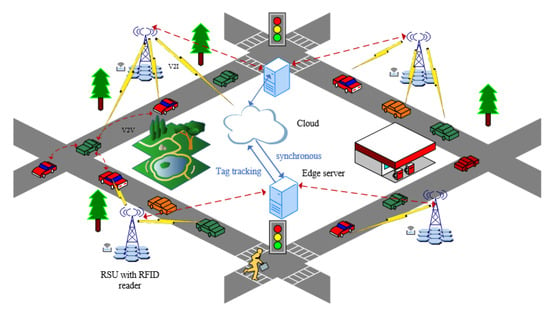
Figure 1.
RFID authentication for IoV framework.
- This paper presents an edge server-based RFID authentication protocol for IoV, which reduces the computing and communication costs of the cloud due to the high overhead of cloud computing, communication, and storage;
- The protocol proposed in this research is the first to achieve fast authentication in the IoV traffic congestion scenario, significantly lower computing and communication overhead, and to satisfy security and lightweight authentication requirements.
2. Related Work
RFID can be utilized in the IoV to enable vehicle identification and authentication functions, providing technical support for smart transportation and smart city construction. While RFID allows for automatic identification and management without contact, its non-contact feature also poses certain security risks. Therefore, the RFID authentication protocol plays a critical role in ensuring the secure transmission of vehicle network data and accurate identification information. Many scholars have contributed to research on RFID authentication, which mainly includes lightweight authentication protocols based on bit operations, RFID authentication protocols based on quadratic residue, ECC, and grouping-proof, and other RFID authentication protocols.
- (1)
- Lightweight RFID authentication protocols based on bit operationsTo reduce computational and communication overhead in the RFID authentication process, several scholars have proposed lightweight RFID protocols based on bit operations. Chen et al. [17] introduced a lightweight authentication protocol based on an asymmetric encryption algorithm, where the reader performs most of the complex work, and the tag only needs to execute simple operations such as bitwise XOR, one-bit circular shift, and bit flip. This method reduces computational and communication overhead. Fan et al. [18] proposed a lightweight RFID authentication privacy protection scheme that encrypts authentication data through the operation of a cross and the operation of rotation. Although the computational overhead of this algorithm is relatively small, it is vulnerable to attacks. Aghili et al. [19] introduced a lightweight authentication protocol and designed a more secure function to encrypt private data in the authentication process by improving the function. Fan et al. [20] proposed an efficient protocol that uses rotation and enhanced permutation encryption to reduce RFID overhead. However, the ambiguous timestamp in this protocol is vulnerable to brute-force attacks, leading to secret information leakage. Although these protocols are lightweight, they use simple bit operations such as XOR, bit flip, and rotation to encrypt private data, which can be vulnerable to attacks and may result in key leakage.
- (2)
- RFID authentication protocols based on quadratic residueScholars have implemented RFID mutual authentication using the quadratic residue algorithm to improve security. Fan et al. [21] proposed a lightweight authentication protocol based on the quadratic residue and the operation of rotation. However, the computational speed of the quadratic residue is slow, leading to high computational overhead, which does not meet the lightweight requirements. Doss et al. [22] proposed a grouping-proof authentication protocol based on the quadratic residue zero-knowledge property. However, in this protocol, the reader is not authenticated, which can make it vulnerable to counterfeit readers that illegally read the tag data. Lee et al. [23] proposed a protocol based on homomorphic encryption and quadratic residue to address the issue of ownership transfer in the RFID of the IoV, which can achieve batch ownership transfer of tags. However, Tu et al. [24] conducted a security assessment of the protocol and identified security loopholes that could result in attacks such as replay, tracking, and simulated tag attack. To address these issues, Song et al. [25] proposed a quadratic residue-based zero-knowledge authentication protocol with active tags that have zero-knowledge properties.
- (3)
- RFID authentication protocols based on grouping-proofTo achieve fast authentication in large-scale RFID systems, Rahman et al. [26] proposed a group-based anonymous privacy authentication protocol to achieve batch authentication. This method is better than the original tree-based authentication protocol, and the group-based protocol security level is higher. To address the security challenge of simultaneous authentication of multiple readers and tags in a distributed RFID system, Liu et al. [27] proposed a Grouping-Proofs-Based Authentication Protocol (GUPA) that can withstand classic attacks such as replay, forgery, and tracking. However, Sun et al. [28] pointed out that the GUPA scheme [27] is vulnerable to man-in-the-middle attacks and can result in key leakage, leading to replay, forgery, tracking, and rejection of proofs. Therefore, Sun et al. [28] utilized a hash function to encrypt private data for better authentication security. To solve the problem of high communication overhead when authenticating tags in batches, Yang et al. [29] proposed an efficient authentication grouping-proof protocol based on symmetric keys and bit collisions, which can solve the conflict issue of one-time authentication of multiple tags.
- (4)
- RFID authentication protocol based on ECCWu et al. [30] introduced a UAV-assisted IoV authentication protocol that utilizes ECC and hash functions for encryption. Analysis shows that the protocol can withstand various attacks, but its computational and communication overheads are relatively high. Shabani et al. [31] proposed an ECC-based RFID authentication protocol for IoV, but this protocol may result in tag tracking. Kumar et al. [32] proposed an ECC-based RFID authentication protocol for vehicle cloud computing, RSEAP, which is resistant to man-in-the-middle attacks and replay attacks and has high-performance communication. However, Safkhani et al. [33] pointed out that the protocol proposed by Kumar et al. could not provide the claimed security or improved vulnerability based on RSEAP. They therefore proposed a more secure RSEAP2 protocol with less computing and communication overhead, but with more overhead in authentication. During the process, neither the tag nor the cloud will verify the identity of the reader, which may lead to man-in-the-middle attacks and impersonation of the reader attacks. Meher et al. [34] proposed an ECC-based RFID authentication protocol without public/private key pairs to address the issue of limited resources of RFID tags, greatly reducing the computation and storage costs of the tags.
- (5)
- Other RFID authentication protocolsChander et al. [35] proposed an RFID protocol based on hash functions and bit logic functions, which are easy to implement but vulnerable to attacks. Jangirala et al. [36] proposed a blockchain RFID protocol based on a single hash function, bit-by-bit dissimilarity, and bit-by-bit rotation operations, enhancing security and increasing communication overhead. Salem et al. [37] proposed a privacy-preserving RFID authentication protocol based on ElGamal encryption. The protocol allows for direct authentication between the tag and server without the need for the reader’s involvement. Unlike traditional authentication methods in which both the tag and the server authenticate each other, in this protocol, only the tag authenticates the server. However, it also makes the protocol sensitive to beacon attacks simulated by potential attackers. Shariq et al. [38] proposed a Schnorr-based RFID authentication protocol. However, the protocol provides only one-way verification of the server and does not verify the legitimacy of the tag. Akram et al. [39] proposed an RFID authentication protocol based on cloud computing for IoV. The protocol utilizes a chaotic map to achieve mutual authentication and offers significant advantages in terms of computing, communication, and storage compared to other protocols. However, the mutual authentication process within the protocol is cloud-based, which may overload computing, communication, and cloud storage.
Current RFID authentication schemes typically rely on cloud-based authentication, resulting in high computing and communication overheads. This can lead to reduced real-time performance, decreased network reliability, and an increased risk of data leakage. To address these challenges, this paper proposes an RFID authentication for IoV that utilizes edge servers, thereby reducing the cloud burden. Although many high-security encryption algorithms cannot be applied directly to RFID due to the limited computing and storage capabilities of RFID tags, some encryption algorithms can still be used, such as hash functions and ECC algorithms. Hash functions have the advantages of fast calculation speed and high security, making them a suitable option for RFID; however, using only a hash function can leave RFID vulnerable to attacks such as man-in-the-middle attacks. On the other hand, the ECC algorithm offers fast calculation speed and high security, making it a suitable choice for resource-constrained RFID systems [40,41]. ECC can protect private data in the authentication process and also offers a faster calculation speed.
To address the challenges of a heavy cloud computing communication burden, limited RFID resources, and the balance between RFID security and performance, this work proposes a lightweight and adaptive RFID security authentication protocol for IoV. The Elliptic Curve Discrete Logarithm Problem (ECDLP) of the ECC algorithm and the anti-collision characteristics of the hash function are utilized to guarantee the security of the protocol. This scheme balances security and performance by ensuring low overhead calculation, communication, and storage in the authentication process.
The remainder of this paper is organized as follows. The preparation work for this study is introduced in Section 3, covering the ECC algorithm and the adversary model. In Section 4, an IoV-based, lightweight, adaptive, and efficient RFID security authentication scheme is proposed, while the security of this proposed scheme is analyzed in Section 5. Performance comparison and evaluation are demonstrated in Section 6. Finally, this work is summarized, and the directions for future work are discussed in Section 7.
3. Preliminaries
3.1. ECC Algorithm over Finite Fields
The ECC algorithm over finite fields [42] is an asymmetric encryption algorithm. Let be a finite field on a large prime number p. The most commonly used curve equation for elliptic curves over finite fields is defined below.
Let be an elliptic curve over a finite field of large prime numbers p. Define , which is an additive group, and O is an element in called the point at infinity, which is also the identity element of . Let , have the following definition:
- ;
- Let , then , where represents the additive inverse of P;
- Let , then ;
- Let , , then , is determined by:where
3.2. Difficult Problems
Definition 1
(ECDLP). Given two points P and Q on an elliptic curve , computing a positive integer k such that is difficult in polynomial time.
Definition 2
(Elliptic Curve Diffie–Hellman Problem (ECDLP)). Given two points A and B on an elliptic curve , and knowing and (), solving in polynomial time is difficult.
Definition 3
(One-way Property of the Hash Function). Given , it is difficult to solve m.
Definition 4
(Collision Resistance of Hash Functions). Given different plaintexts , the probability of is negligible; given , finding such that is difficult.
3.3. Adversary Model
To analyze the security of the authentication scheme proposed in this paper, certain assumptions must be made regarding the adversary’s attack capabilities. This section introduces attack models commonly used in many related studies [27,28,29], which will be used for security analysis. The assumptions of the adversary model are as follows:
- (1)
- An adversary can interrupt communication between readers, tags, and edge servers through common channels;
- (2)
- The adversary in this paper can launch active and passive attacks against the protocol;
- (3)
- Adversaries can launch attacks using fake readers or tags.
4. The VASERP Protocol
The paper presents a scheme involving four entities: the cloud server, the edge server, the vehicle, and the RSU. The tag, which contains information such as vehicle identity, location, and status, is embedded in the vehicle, while the RFID reader is installed in the RSU to identify and read information from passing vehicles. Both tags and readers register through the cloud, and the cloud records their identifiers. The cloud does not directly synchronize the tag identifiers with the edge server to ensure data privacy. Instead, it encrypts the hash and then synchronizes it with the edge server. The edge server performs the verification between RFIDs. In a special situation that requires verification of the vehicle’s real identity, the edge server can send a request to the cloud server.
During RFID authentication, the reader will process the information on the tag to give road condition information and forecast traffic conditions to prevent illegal tags from forcing vehicles to provide false road condition information. During authentication, the tag needs to be authenticated, and in order to ensure that the information about the vehicle is not read by an illegal reader, the reader also needs to be authenticated. At the same time, in order to ensure that the read information is non-repetitive, this paper stipulates that, at a certain moment, one reader can read multiple tags at the same time, but one tag can be read by only one reader. Three stages are included: (1) the registration phase, (2) the fast mutual authentication phase, and (3) the ownership transfer phase. Algorithm 1 is the pseudocode for an adaptive selection protocol scheme that can choose appropriate authentication protocols based on the actual traffic scenarios
| Algorithm 1: An adaptive, lightweight, secure, and efficient RFID-based authentication scheme for IoV. |
Register with the cloud; the cloud synchronizes the RID to the edge server after hashing and encryption broadcast to the surrounding area, where ,. receive if compute if Perform rapid mutual authentication phase else Perform the transfer of ownership phase else return 0 (Request Timeout) |
4.1. Initialization Phase
An appropriate elliptic curve should be chosen to implement the authentication protocol, and a large prime number d should be generated randomly as the private key of the edge server. The public key can then be calculated through the base point G of the curve. Table 1 provides symbols and definitions used in the authentication protocol.

Table 1.
Symbols in this scheme.
4.2. Registration Phase
This phase aims to establish the legitimate identities of the readers and tags in the system, with registration carried out through a secure channel. Upon registration, a unique identifier will be obtained for the reader or tag, which will be stored in the cloud to facilitate subsequent real identity tracking. To protect the privacy of vehicle information, the edge server will only store encrypted tag identifier information. As shown in Table 2, to verify the legal identity of the tag and record the authentication status of the tag, the edge server will maintain a tag index table.

Table 2.
Tag index table.
4.2.1. Tag Registration
Step1: generates its own identifier and sets a variable to store the reader identifier of the tag currently accessible, initially , then sends a registration request {registration request,,} to the cloud through a secret channel.
Step2: The cloud receives registration request, , , and checks whether the same value as exists already in Table 2. If it exists, it means that has already been registered, and the registration fails. Otherwise, it creates a record in Table 2. The cloud sends {k, p, G, Q} to . The cloud encrypts the identifier of the tag through the hash and synchronizes it to each edge server.
4.2.2. Reader Registration
Step1: sends a registration request to the cloud {registration request }
Step2: The cloud receives registration request and then sends {, k, G, Q} to the reader.
4.3. Fast Mutual Authentication Phase
This phase is a mutual rapid verification process designed for the traffic congestion scene of the IoV. It achieves quick mutual authentication of tags and readers without the need for an edge server, thus reducing the computational and communication overhead associated with authentication in the congestion scenario of the IoV. Specific steps for rapid mutual authentication are outlined below.
Step1: generates a random number ; calculate:
which broadcasts around .
Step2: Nearby tags receive and verify ; if valid, then compute:
Formula (7) indicates that only a legitimate tag with a shared key k can solve based on . Then, it checks . If it is true, it means that and have been authenticated by the edge server, and the fast authentication between the reader and the tag can be performed directly. The tag computes:
Send to the reader. If false, then perform the ownership transfer phase.
Step3: Reader receives and verifies ; if valid, then compute:
Verify , while represents the operation . Since , k, and are all secret information, they are not available to illegitimate tags and attackers. Only legitimate tags can obtain them using formula (7). Therefore, if it is true, the tag is a legal tag; otherwise, it is an illegal tag. Then calculate:
and send to the validated tag.
Step4: receives and verifies ; if it is valid, then verify , and if it is valid, then compute and verify the authenticity of the value of through the value of . If the verification passes, it is a legal reader, and fast mutual authentication ends.
The process of fast mutual authentication is shown in Figure 2.
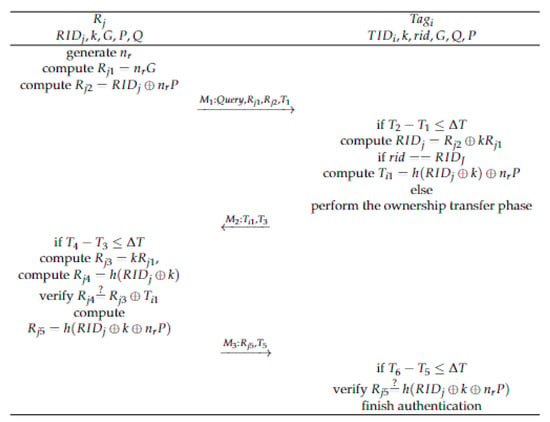
Figure 2.
The fast mutual authentication phase.
4.4. The Ownership Transfer Phase
This phase is applied to non-congested scenarios in IoV. In this scenario, the vehicle tags are mutually authenticated with the readers in the RSU. When a vehicle moves from one reader’s reading range to another, an ownership transfer is required. This process relies on edge servers to transfer the ownership of the tag. That is, authentication between the reader and the tag is done through the edge server. The following are the detailed steps for ownership transfer:
Step1: generates a random number ; calculate:
and send to . Formula (13) is used by the reader to verify the identity information of the , while formula (14) is used by the edge server to verify the identity information of .
Step2: receives , and verifies . If it is legal, it verifies the validity of by verifying . If it is legal, it calculates:
and sends to .
Step3: receives and verifies . If it is legal, it computes:
has the private key d of the edge server, so it can obtain through Formulas (19) and (21) and can verify by checking if . In addition, calculates using Formulas (18) and (20). To verify , searches in Table 2. If the search fails, it means that the tag is illegal; otherwise, update Table 2 and update the content corresponding to the index value to . Then, generate a random number and calculate:
and send to , where is used for to verify and is used for to verify .
Step4: receives and verifies . Since and are secret messages and can only calculate using its private key d through formula (19), attackers and illegal devices cannot calculate . Therefore, the legitimacy of can be verified by checking . If it is legitimate, then compute:
sends to , where is used for to verify .
Step5: receives and verifies . If it is true, then verify to verify the validity of and verify to check the the validity of . As is a secret message, attackers cannot obtain it through . Moreover, due to the difficulty of ECDHP, attackers cannot solve from and . Only with the private key d can solve . Set . The mutual authentication of and is complete.
The proposal of the ownership transfer phase is shown in Figure 3.
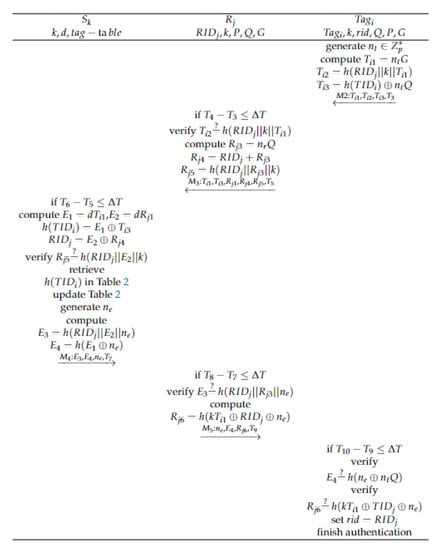
Figure 3.
The ownership transfer phase.
5. Security Analysis
5.1. Formal Analysis
This section presents a formal analysis of the protocol proposed in this paper to verify its security. Existing formal analysis methods include proof methods based on logical reasoning such as BAN logic and GNY logic, hypothesis-based formal proof methods such as random oracles, and automated formal proof methods such as Scyther and AVISPA. In this paper, we conduct a formal analysis of the proposed protocol using Scyther, an automated security protocol verification tool that can simulate attackers with varying levels of sophistication and detect potential vulnerabilities and flaws in security protocols. Scyther can also analyze security attributes such as confidentiality, integrity, authentication, and availability of the protocol and provide detailed analysis reports. The protocol must be written in a formal description language called SPDL for Scyther.
The protocol defines participants using the roles of Tag, Reader, and Server. Each role can perform operations such as sending and receiving messages and computing key values. The claim section is used to verify the security properties of the protocol. Running the protocol code produces an analysis results window. When Scyther executes the proposed protocol, it begins by simulating adversaries with the Dolev–Yao model. If the protocol meets the verification requirements for security and no security vulnerabilities or attack types are found, Scyther outputs “OK”. If an attack is detected, Scyther outputs the type of attack, the role played by the attacker, and a flow chart of the attack. As shown in Figure 4, the protocol of this work satisfies security requirements and does not have vulnerabilities.
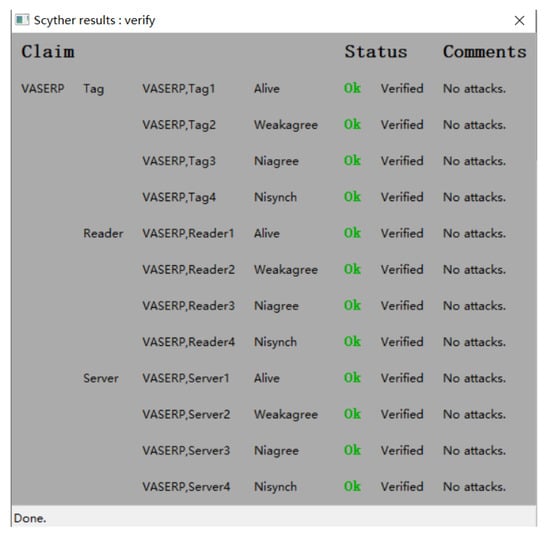
Figure 4.
Scyther’s claim results for the VASERP.
5.2. Informal Analysis
The following will provide an informal analysis of the scheme, mainly analyzing whether VASERP can withstand common attacks and whether it can meet the required security.
Support for tag anonymity: The tag is registered with the cloud through a secure channel, and the cloud will synchronize the of with each edge server after hash encryption. When performing authentication, the edge server only knows and cannot know the real identity of . During the authentication process, the tag identifier will not appear directly in the message. Therefore, our scheme can support tag anonymity.
Achieve mutual authentication: Taking the ownership transfer stage as an example, sends to , and verifies through . sends to . obtains though , then verifies whether is in Table 2. obtains by , and verifies by checking . sends to , then verifies . sends to , then verifies by checking and verifies by checking . Therefore, the proposed scheme in this work can realize mutual authentication.
Provide key agreement: Take the ownership transfer stage as an example. and through and perform mutual authentication. and conduct mutual authentication through . and conduct mutual authentication through . The dynamism of the session key depends on the random numbers and . Due to the difficulty of ECDLP, it is difficult for an attacker to break the session key.
Even if P, Q, and G are leaked, the VASERP can prevent the imitation attack of tags: In the fast authentication phase, if an attacker wants to simulate a tag, they need to forge the information , where . The attacker needs to obtain the secret messages , k, and . Since solving ECDLP is difficult, the attacker cannot solve based on in message (the fast authentication phase) and therefore cannot obtain . The key k is a shared secret between the reader and the tag that the attacker cannot obtain. Therefore, the attacker cannot simulate the tag. Similarly, the attacker cannot simulate the tag in the ownership transfer phase either.
VASERP is resistant to man-in-the-middle attacks: The authentication process of this scheme will verify the sender at each step, and the messages are encrypted by the hash function and ECC. If the attacker wants to steal the communication message in the authentication and manipulate it, then the attacker needs to obtain the secret information and, at the same time, obtain the random numbers generated by the three authentication participants; however, these messages are not available to the attackers. Therefore, VASERP is resistant to man-in-the-middle attacks.
VASERP is resistant to replay attacks: In the fast authentication phase and the ownership transfer phase, the time stamp is set , and the random number for each authentication round will be updated. Even if an attacker obtains a message in the communication, the attacker cannot find the session key, so the attacker cannot perform a replay attack using a previously eavesdropped message.
VASERP is resistant to desynchronization attacks: In the authentication process, in order to resist desynchronization attacks, this scheme sets a timestamp for each piece of information during authentication. After receiving the information, each entity will verify the timestamp to ensure the legitimacy of the message. If the timestamp expires, then the entity discards the message. An attacker cannot perform a desynchronization attack.
VASERP is resistant to tag tracking: In the authentication process, an attacker can eavesdrop on communication between the tag and the reader, and even if they do not know the real identity of the tag, they may be able to track it through repeated messages. In the fast authentication phase, the tag does not have identity information involved in the encrypted messages sent by the tag, and changes with the value of , which is a random number generated by the reader and which is different for each round of authentication. Therefore, is also different for each round, and the attacker cannot track the tag according to . In the ownership transfer phase, the tag sends to the reader, where , , and . Only contains the identity information of the tag , but since is updated in each round of authentication, is also updated, and the attacker cannot track the tag based on unless the attacker can obtain through and . However, as defined in Definition 1, ECDLP is difficult. Therefore, the attacker cannot track the tag.
6. Performance Comparison and Discussion
In order to evaluate the performance of the proposed scheme, this paper compares the vehicular RFID protocol with the schemes proposed by Shabani et al. [31], Kumar et al. [32], Safkhani et al. [33], and Salem et al. [34] in terms of computation, communication, security, and storage in two scenarios: traffic congestion and non-congestion in vehicular networks.
6.1. Security Comparison
In order to better evaluate the security of the protocol, the protocol proposed in this work and other RFID protocols for IoV are evaluated from multiple security aspects, such as tag anonymity and resistance to replay attacks. It can be seen in Table 3 that, among the four protocols compared, only the proposed protocol and the scheme [33] can meet the security requirements stated in this investigation. Neither the protocols of reference [31] nor reference [32] can satisfy replay attacks, man-in-the-middle attacks, or impersonation attacks.

Table 3.
Security comparison of different protocols.
6.2. Computational Overhead Comparison
The computing capability of RFID tags is very limited, and computation and communication overhead is an important performance evaluation standard for RFID authentication protocols. This section compares different RFID protocols. Let be the time for SHA hash operations, be the time for elliptic curve point multiplication, be the time for elliptic curve addition, and be the time for symmetric encryption/decryption. Amin et al. [40,43] used MIRACL, a C/C++ library, to estimate the computation time of different encryption methods. The authors in [40,43] used Visual C++ 2008 S/W and a 32-bit Windows 7 operating system to calculate the encryption time of 1024 cyclic groups, 160-bit prime fields, 160-bit elliptic curve addition, and the SHA-1 hash function. The time for elliptic curve point multiplication is 0.0171 s; the time for elliptic curve addition is 0.0061 s; the time for SHA-1 encryption is 0.0005 s; the time for symmetric encryption/decryption is 0.0056 s; and the time for modular exponentiation is 0.057 s. Compared to the calculation time for elliptic curve point multiplication, the calculation time for addition, XOR, and cascade operations is negligible. Table 4 shows the computational time comparison of different protocols in a congested vehicle network. The calculation time comparison of different protocols in non-congested scenarios is shown in Table 5. Figure 5a provides a comparison of the computing overheads of different protocols in congested scenarios, while Figure 5b compares the computing overheads of different protocols in non-congested scenarios.

Table 4.
Comparison of computational costs in congested scenarios.

Table 5.
Comparison of computational costs in non-congested scenarios.
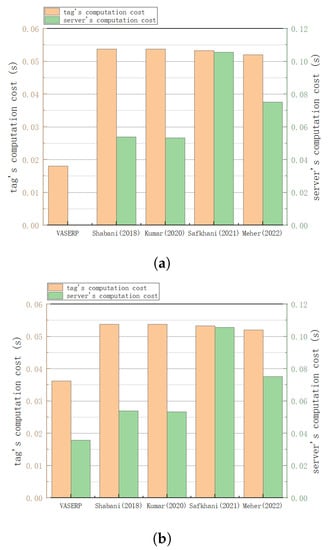
Figure 5.
Computational overhead comparison. (a) Comparison of computational costs in congested scenarios; (b) comparison of computational costs in non-congested scenarios [31,32,33,34].
As shown in Figure 5a, in the congestion scenario, the scheme in this paper has an absolute advantage in the overhead of the tag calculation, which is 66.35% lower than in references [31,32], 66.04% lower than in reference [33], and 65.19% lower than in reference [34]. As shown in Figure 5b, the computational overhead of the scheme in this paper is also relatively small in non-congested scenarios. The overhead of tag calculation is reduced by 32.71% compared to references [31,32], reduced by 32.08% compared to reference [33], and reduced by 30.38% compared to reference [34]. The server computing overhead is reduced by 33.64% compared to reference [31], 33.02% compared to reference [32], 66.19% compared to reference [33], and 52.52% compared to reference [34]. The schemes of reference [31] and reference [32] have very little tag computation overhead and overall computation overhead. Both schemes use only the reader as the intermediary of message exchange without mutual authentication, so although the computational overhead is relatively small, it will lead to other attacks such as man-in-the-middle and simulation attacks. However, the cost of the tag in the scheme in [33] is the same as that of the proposed scheme in terms of general scenarios; however, the total cost of the calculation is relatively large.
6.3. Communication Overhead Comparison
This section compares the communication overhead of different protocols. Figure 6a shows the specific communication overhead comparison in the congested scenario, and Figure 6b shows the specific communication overhead comparison in the non-congested scenario. In the congested scenario, the communication overhead of our scheme is reduced by 33.3% compared to reference [31], 66.6% compared to reference [32], and 71.42% compared to reference [33]. In the non-congested scenario, the communication overhead of the tag in this scheme is reduced by 50% compared with reference [32] and 57.14% compared with reference [33]. The protocols in both scenarios have significant advantages over other protocols.
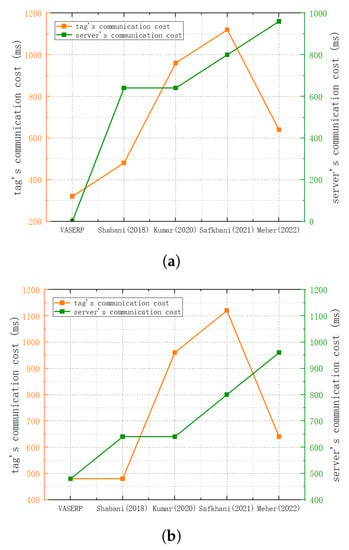
Figure 6.
Communication overhead comparison. (a) Communication overhead comparison in congestion scenarios; (b) comparison of communication overhead in non-congestion scenarios [31,32,33,34].
6.4. Storage Overhead Comparison
This section compares the storage overhead of tags and servers. Storage overhead refers to the space required to store parameters on tags, readers, and servers. As the number of tags increases, the storage overhead of the server for the scheme proposed in this work is the same as that of [32,33], while the order of [31] is 1.3 times that of our scheme. Tags need to store . Figure 7 is a comparison of the storage overhead of tags of different protocols. The scheme in this paper has a good advantage in storage.
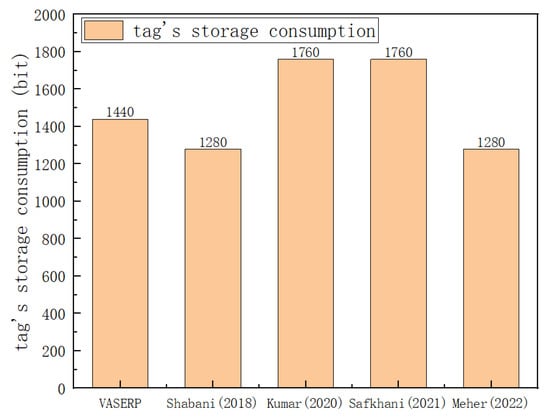
Figure 7.
Tag’s storage cost comparison [31,32,33,34].
7. Conclusions and Future Work
Aiming at the problems of RFID transmission security, IoV data privacy protection, and fast authentication in traffic congestion scenarios, this article proposes an adaptive, lightweight, and efficient IoV-based authentication scheme. Authentication is performed through the edge server, reducing the cloud’s computing and communication overhead. ECC and hash functions are used to encrypt private data during communication, and this scheme can meet speed and security requirements. Security analysis shows that the scheme in this paper can resist man-in-the-middle attacks, tracking attacks, tag and reader simulation attacks, desynchronization attacks, and other means of attack. Through comparative experiments with other RFID car networking protocols that use the ECC algorithm, the tag calculation overhead in traffic congestion scenarios is reduced by 66.35% compared to other schemes, while the tag calculation overhead in non-congested scenarios is reduced by 32.71%. In terms of communication, the communication overhead of tags and edge servers is also greatly reduced, which improves the authentication efficiency in the IoV. It shows that the scheme proposed in this paper has significant advantages in computing, storage, and communication in congested scenarios. It also achieves a good balance between performance and security in non-congested scenarios.
However, in the IoV, when the RFID reader authenticates passing vehicles, the speed of authenticating a single tag is relatively slow and cannot adapt to the environment of fast-moving vehicles in the IoV. Therefore, subsequent research will be carried out on the reduction of tag computing overhead in the RFID authentication of the IoV and the realization of group authentication of vehicles in the IoV, as well as research on the RFID group authentication protocol for the IoV that uses homomorphic encryption to achieve lower computational overhead.
Author Contributions
Conceptualization, Y.G. and W.L.; Methodology, Y.G.g, L.X. and M.K.K.; Software, L.X. and J.X.; Formal analysis, J.C.; Investigation, Y.G., J.C. and J.X.; Resources, Y.G.; Data curation, Y.G., J.C. and J.X.; Writing—original draft, J.C. and J.X.; Writing—review & editing, K.L. and M.K.K.; Supervision, K.L. and W.L.; Project administration, K.L. and W.L.; Funding acquisition, W.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was partially supported by the National Natural Science Foundation of China under Grants 62072170, the Science and Technology Project of the Department of Communications of Hunan Provincial under Grant 202101, the Key Research and Development Program of Hunan Province under Grant 2022GK2015, and the Hunan Provincial Natural Science Foundation of China under Grant 2021JJ30141. We extend our appreciation to the Deputyship for Research and Innovation, Ministry of Education in Saudi Arabia for funding this research work through project no. (IFKSUOR3–061-1).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Lai, J.; Luo, C.; Wu, J.; Li, J.; Wang, J.; Chen, J.; Feng, G.; Song, H. TagSort: Accurate relative localization exploring RFID phase spectrum matching for Internet of Things. IEEE Internet Things J. 2019, 7, 389–399. [Google Scholar] [CrossRef]
- Cao, B.; Gu, Y.; Lv, Z.; Yang, S.; Zhao, J.; Li, Y. RFID reader anticollision based on distributed parallel particle swarm optimization. IEEE Internet Things J. 2020, 8, 3099–3107. [Google Scholar] [CrossRef]
- Gupta, B.B.; Gaurav, A.; Marín, E.C.; Alhalabi, W. Novel graph-based machine learning technique to secure smart vehicles in intelligent transportation systems. IEEE Trans. Intell. Transp. Syst. 2022. [Google Scholar] [CrossRef]
- Hammoud, A.; Otrok, H.; Mourad, A.; Dziong, Z. On demand fog federations for horizontal federated learning in IoV. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3062–3075. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Cai, J.; Wang, C.; Hong, Y.; Kui, X. Novel private data access control scheme suitable for mobile edge computing. China Commun. 2021, 18, 92–103. [Google Scholar] [CrossRef]
- Diao, C.; Zhang, D.; Liang, W.; Li, K.C.; Hong, Y.; Gaudiot, J.L. A novel spatial-temporal multi-scale alignment graph neural network security model for vehicles prediction. IEEE Trans. Intell. Transp. Syst. 2022, 24, 904–914. [Google Scholar] [CrossRef]
- Song, X.; Li, X.; Tang, W.; Zhang, W. A fusion strategy for reliable vehicle positioning utilizing RFID and in-vehicle sensors. Inf. Fusion 2016, 31, 76–86. [Google Scholar] [CrossRef]
- Qin, H.; Peng, Y.; Zhang, W. Vehicles on RFID: Error-cognitive vehicle localization in GPS-less environments. IEEE Trans. Veh. Technol. 2017, 66, 9943–9957. [Google Scholar] [CrossRef]
- Chen, R.; Huang, X.; Zhou, Y.; Hui, Y.; Cheng, N. UHF-RFID-based real-time vehicle localization in GPS-less environments. IEEE Trans. Intell. Transp. Syst. 2021, 23, 9286–9293. [Google Scholar] [CrossRef]
- Pedraza, C.; Vega, F.; Manana, G. PCIV, an RFID-based platform for intelligent vehicle monitoring. IEEE Intell. Transp. Syst. Mag. 2018, 10, 28–35. [Google Scholar] [CrossRef]
- Long, J.; Liang, W.; Li, K.C.; Wei, Y.; Marino, M.D. A Regularized Cross-Layer Ladder Network for Intrusion Detection in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 19, 1747–1755. [Google Scholar] [CrossRef]
- Zhang, S.; Hu, B.; Liang, W.; Li, K.C.; Gupta, B.B. A Caching-based Dual K-Anonymous Location Privacy-Preserving Scheme for Edge Computing. IEEE Internet Things J. 2023, 10, 9768–9781. [Google Scholar] [CrossRef]
- Liang, W.; Yang, Y.; Yang, C.; Hu, Y.; Xie, S.; Li, K.C.; Cao, J. PDPChain: A consortium blockchain-based privacy protection scheme for personal data. IEEE Trans. Reliab. 2022. [Google Scholar] [CrossRef]
- Fang, W.; Li, Y.; Zhang, H.; Xiong, N.; Lai, J.; Vasilakos, A.V. On the throughput-energy tradeoff for data transmission between cloud and mobile devices. Inf. Sci. 2014, 283, 79–93. [Google Scholar] [CrossRef]
- Sandor, V.K.A.; Lin, Y.; Li, X.; Lin, F.; Zhang, S. Efficient decentralized multi-authority attribute based encryption for mobile cloud data storage. J. Netw. Comput. Appl. 2019, 129, 25–36. [Google Scholar] [CrossRef]
- Yang, A.; Weng, J.; Yang, K.; Huang, C.; Shen, X. Delegating authentication to edge: A decentralized authentication architecture for vehicular networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1284–1298. [Google Scholar] [CrossRef]
- Chen, M.; Chen, S.; Fang, Y. Lightweight anonymous authentication protocols for RFID systems. IEEE/ACM Trans. Netw. 2017, 25, 1475–1488. [Google Scholar] [CrossRef]
- Fan, J.; Elmagarmid, A.K.; Zhu, X.; Aref, W.G.; Wu, L. ClassView: Hierarchical video shot classification, indexing, and accessing. IEEE Trans. Multimed. 2004, 6, 70–86. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Fan, K.; Luo, Q.; Zhang, K.; Yang, Y. Cloud-based lightweight secure RFID mutual authentication protocol in IoT. Inf. Sci. 2020, 527, 329–340. [Google Scholar] [CrossRef]
- Fan, K.; Zhu, S.; Zhang, K.; Li, H.; Yang, Y. A lightweight authentication scheme for cloud-based RFID healthcare systems. IEEE Netw. 2019, 33, 44–49. [Google Scholar] [CrossRef]
- Doss, R.; Trujillo-Rasua, R.; Piramuthu, S. Secure attribute-based search in RFID-based inventory control systems. Decis. Support Syst. 2020, 132, 113270. [Google Scholar] [CrossRef]
- Lee, C.C.; Li, C.T.; Cheng, C.L.; Lai, Y.M.; Vasilakos, A.V. A novel group ownership delegate protocol for RFID systems. Inf. Syst. Front. 2019, 21, 1153–1166. [Google Scholar] [CrossRef]
- Tu, Y.J.; Kapoor, G.; Piramuthu, S. On Group Ownership Delegate Protocol for RFID Systems. Inf. Syst. Front. 2022, 24, 1577–1584. [Google Scholar] [CrossRef]
- Song, J.; Harn, P.W.; Sakai, K.; Sun, M.T.; Ku, W.S. An RFID zero-knowledge authentication protocol based on quadratic residues. IEEE Internet Things J. 2021, 9, 12813–12824. [Google Scholar] [CrossRef]
- Rahman, F.; Hoque, M.E.; Ahamed, S.I. Anonpri: A secure anonymous private authentication protocol for RFID systems. Inf. Sci. 2017, 379, 195–210. [Google Scholar] [CrossRef]
- Liu, H.; Ning, H.; Zhang, Y.; He, D.; Xiong, Q.; Yang, L.T. Grouping-proofs-based authentication protocol for distributed RFID systems. IEEE Trans. Parallel Distrib. Syst. 2012, 24, 1321–1330. [Google Scholar] [CrossRef]
- Sun, D.Z.; Mu, Y. Security of grouping-proof authentication protocol for distributed RFID systems. IEEE Wirel. Commun. Lett. 2017, 7, 254–257. [Google Scholar] [CrossRef]
- Yang, A.; Boshoff, D.; Hu, Q.; Hancke, G.P.; Luo, X.; Weng, J.; Mayes, K.; Markantonakis, K. Privacy-preserving group authentication for rfid tags using bit-collision patterns. IEEE Internet Things J. 2021, 8, 11607–11620. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Luo, X.; Gu, K. A novel authentication scheme for edge computing-enabled Internet of Vehicles providing anonymity and identity tracing with drone-assistance. J. Syst. Archit. 2022, 132, 102737. [Google Scholar] [CrossRef]
- Shabani, F.; Gharaee, H.; Ghaffari, F. An intelligent RFID-enabled authentication protocol in VANET. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018; pp. 587–591. [Google Scholar]
- Kumar, V.; Ahmad, M.; Mishra, D.; Kumari, S.; Khan, M.K. RSEAP: RFID based secure and efficient authentication protocol for vehicular cloud computing. Veh. Commun. 2020, 22, 100213. [Google Scholar] [CrossRef]
- Safkhani, M.; Camara, C.; Peris-Lopez, P.; Bagheri, N. RSEAP2: An enhanced version of RSEAP, an RFID based authentication protocol for vehicular cloud computing. Veh. Commun. 2021, 28, 100311. [Google Scholar] [CrossRef]
- Meher, B.K.; Amin, R.; Das, A.K.; Khan, M.K. KL-RAP: An Efficient Key-Less RFID Authentication Protocol Based on ECDLP for Consumer Warehouse Management System. IEEE Trans. Netw. Sci. Eng. 2022, 9, 3411–3420. [Google Scholar] [CrossRef]
- Chander, B.; Gopalakrishnan, K. A secured and lightweight RFID-tag based authentication protocol with privacy-preserving in Telecare medicine information system. Comput. Commun. 2022, 191, 425–437. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5G mobile edge computing environment. IEEE Trans. Ind. Inform. 2019, 16, 7081–7093. [Google Scholar] [CrossRef]
- Salem, F.M.; Amin, R. A privacy-preserving RFID authentication protocol based on El-Gamal cryptosystem for secure TMIS. Inf. Sci. 2020, 527, 382–393. [Google Scholar] [CrossRef]
- Shariq, M.; Singh, K.; Bajuri, M.Y.; Pantelous, A.A.; Ahmadian, A.; Salimi, M. A secure and reliable RFID authentication protocol using digital schnorr cryptosystem for IoT-enabled healthcare in COVID-19 scenario. Sustain. Cities Soc. 2021, 75, 103354. [Google Scholar] [CrossRef]
- Akram, W.; Mahmood, K.; Li, X.; Sadiq, M.; Lv, Z.; Chaudhry, S.A. An energy-efficient and secure identity based RFID authentication scheme for vehicular cloud computing. Comput. Netw. 2022, 217, 109335. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Lee, Y.K.; Sakiyama, K.; Batina, L.; Verbauwhede, I. Elliptic-curve-based security processor for RFID. IEEE Trans. Comput. 2008, 57, 1514–1527. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).