Abstract
Industrial control systems (ICS) are applied in many fields. Due to the development of cloud computing, artificial intelligence, and big data analysis inducing more cyberattacks, ICS always suffers from the risks. If the risks occur during system operations, corporate capital is endangered. It is crucial to assess the security of ICS dynamically. This paper proposes a dynamic assessment framework for industrial control system security (DAF-ICSS) based on machine learning and takes an industrial robot system as an example. The framework conducts security assessment from qualitative and quantitative perspectives, combining three assessment phases: static identification, dynamic monitoring, and security assessment. During the evaluation, we propose a weighted Hidden Markov Model (W-HMM) to dynamically establish the system’s security model with the algorithm of Baum–Welch. To verify the effectiveness of DAF-ICSS, we have compared it with two assessment methods to assess industrial robot security. The comparison result shows that the proposed DAF-ICSS can provide a more accurate assessment. The assessment reflects the system’s security state in a timely and intuitive manner. In addition, it can be used to analyze the security impact caused by the unknown types of ICS attacks since it infers the security state based on the explicit state of the system.
1. Introduction
The industrial control system can be remotely interacted with and communicated with cloud services [1], cyber-physical systems [2], or edge devices in a highly networked environment [3]. Cyber-attacks are increasingly becoming a threat to ICS; thus, their security is critical [4,5]. Once an essential piece of equipment experiences a safety incident, it causes a shutdown of the system and even causes casualties [6].
The security assessment of industrial control systems is an integral part of security [7,8]. The system’s security integrates internal attributes and external environments. The elements involved in assessment have the following characteristics: large number, strong correlation, and poor accessibility. Thus, evaluating the security of the system accurately is difficult.
In recent years, security assessment research has mainly focused on artificial intelligence [9], medical subjects [10,11], infrastructure [12], power systems [13], coal mining [14], chemicals [15], etc. The industrial field focuses on assessing the system’s functional safety or the static information security assessment for the design, and its security status is easily observerd [16,17]. However, the critical equipment executing complex control tasks in ICS is challenging for capturing security statuses directly. System security information is also related to running variables, such as system operating status and environmental status. Security assessment must have the ability to obtain security information of complex systems dynamically.
New cyberattacks for which its forms and types tend to be unknown are hard to be detected [18]. Due to the limited resources of devices and networks in ICS [19,20], it is hard to obtain security information of assessments directly by detecting attacks [21]. Cyberattacks make ICS more undependable and unsafe when using the Internet [22]. Scholars generally evaluate system security through the consequences of information attacks [23]. Consequence refers to the property losses caused by an information attack. For example, Muhammad Adil et al. identified a jamming attack channel by detecting different transmission frequencies and Round Trip Time (RTT) of transmitting a signal from multi-channel in WSNs transmission media [24].
There are three methods of assessment based on consequences of attacks [20,25]: qualitative assessment, quantitative assessment [26], and the combination of them. There are many qualitative evaluation methods, such as attack trees and fuzzy calculations. These methods are coarse-grained assessments of system parameters. For example, Xu Hui et al. used attack trees to identify various attacks for security management of SDN [27]. However, they could not provide a quantitative value to evaluate the consequences of the attack. The quantitative evaluation methods can assess the impacts of information attacks. Wenli Shang et al. provided a security assessment method based on an attack tree model with fuzzy set theory and probability risk assessment technology [28]. Jingjing Hu et al. proposed a multi-dimensional network security risk assessment framework [29], including two stages: risk identification and risk calculation. They used HMM to assess the network security risk in the risk calculation stage. The HMM assessment method can effectively reflect and quantify the security risks of the physical network system. However, they did not assign the weight to the result in the risk value calculation, as the network servers and nodes have different importance. We should weigh different parts of ICS in ICS due to its heterogeneity. Nary Subramanian et al. proposed a quantitative method of NFR (non-functional requirements) safety assessment for the infrastructure system of oil pipeline systems [30]. This method can solve the integrated assessment of functional safety and security. However, it cannot calculate the assessed value of the security. Aziz A. et al. used ontology knowledge to analyze the causal relationship between events [31], established corresponding probability models, and identified the consequences of abnormalities. This method can quantitatively assess the consequences of the system’s attacks. However, the probability established by this method was stationary, while the system risk is changing. It is challenging to apply dynamic evaluations.
Currently, the most commonly used security assessment method is a combination of qualitative and quantitative information [32,33]. One is the analytic hierarchy process, which is a multi-level weight decision analysis method. Jun Chen applied the analytical hierarchy process for industrial control system evaluation [34]. Moreover, it can effectively evaluate industrial control risks. However, it cannot dynamically assess the system of ICS due to unknown attacks and threats that follow ICS. Some pieces of research had brought focus onto the necessity of a framework for the evaluation of IoT device security [35,36]. The above research methods are not dynamic and cannot meet this assessment requirement.
We propose a practical security assessment framework, a three-stage dynamic assessment framework for ICS based on a method of W-HMM. The main contributions of this work are as follows:
- i.
- The proposed method combines a qualitative and quantitative assessment of ICS security dynamically by using a W-HMM model. The method can infer the system’s risk value, which can be used as a system risk reference in a timely and intuitive manner through the explicit consequences of the attack on the device.
- ii.
- The assessment of the industrial robot control system (IRCS) is used as an example to illustrate the use of the method and compared with two typical security assessment methods.
The article is structured as follows. In the next section, we introduce the static recognition of DAF-ICSS. Dynamic monitoring is described in Section 3. Section 4 shows the assessment. Section 5 explains the framework of DAF-ICSS. Section 6 uses an IRCS as an example to verify DAF-ICSS. We discuss the results in Section 7. Finally, Section 8 summarizes the work of this paper.
2. Static Recognition
2.1. Basic Value
The ICS is a part of the company’s fixed assets, and its security will affect the value of the company’s fixed assets. We use the analytic hierarchy process to evaluate the basic value of ICS. The basic value, , is used to assess the economic value of ICS. The basic value is divided into three layers: target layer, factor layer, and index layer, shown in Figure 1.
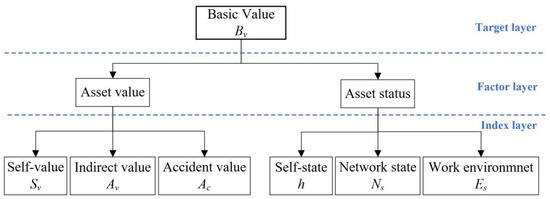
Figure 1.
The basic value decomposition diagram.
The target layer obtains . The factor layer decomposes the basic value of the ICS into two critical factors: asset value and asset status. Asset value represents the economic value of the ICS, and asset status reflects the state and the environment. The index layer decomposes the factors into the fine-grained index. The asset value includes three values: self-value , indirect value , and accident value . Self-value refers to the asset value of the ICS. Indirect value is the indirect economic loss of the enterprise caused by ICS failure without injury. accident value represents the estimated financial loss of an injury accident caused by ICS attacks. It is obtained from accident probability and accident loss g.
Asset status is divided into three states: self-state h, network state , and work environment , as shown in Table 1. The self-state reflects the performance and stability of the system, thereby affecting asset value. The latter two reflect the harshness of the system’s external environment and affect the system’s vulnerability value. Network state refers to the value determined by the network bandwidth, traffic, and peak value. The working environment is the value determined by temperature, humidity, and electromagnetic interference. The smaller the valuation, the lower the risk. The basic value is calculated as follows.

Table 1.
Quantitative table of asset status.
2.2. Vulnerability
The vulnerability of ICS refers to the system’s weakness that attackers can abstract [37]. When the vulnerability of an ICS is attacked, a basic attack path model should be shown in Figure 2. The attack is achieved through three steps: network path connection, data manipulation, and breaking through protection. The first step ensures that the attacker can connect to ICS through the network. The second step is that the attacker sends malicious attack instructions when the attacker could imitate external communication data of ICS. The third step hides or floods attack instructions so that the instructions can pass through the protection. The attack instructions could steal, change, or delete the system’s data. Moreover, the attack may cause the system’s faults.
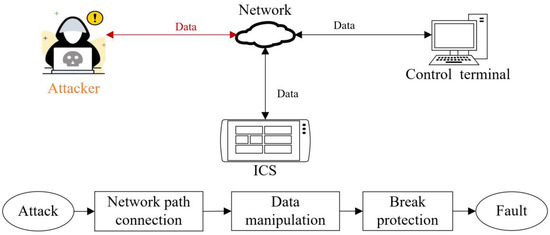
Figure 2.
The processes of the attack path model.
The vulnerability of ICS can be illustrated from three factors depending on the three steps of the attack path model. The three factors are availability , data weakness , and safety protection . Availability means the degree that ICS can achieve specific operations through the network when random attacks are launched. Data weakness evaluates the possibility of communication data being attacked. Security protection is the system’s ability to prevent information attacks. These three factors respectively assess the vulnerability of the three steps of the attack model. Figure 3 shows the hierarchy diagram of vulnerabilities of ICS.
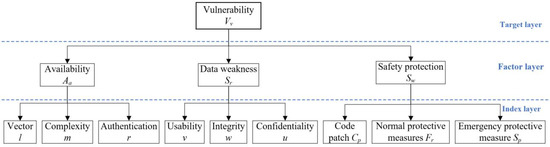
Figure 3.
Hierarchy diagram of the vulnerability of ICS.
The availability is divided into three indexes to measure the difficulty of attackers connecting to the system: Vector l, complexity m, and authentication r. l is used to measure the network distance between the attacker and ICS. Before an attacker can connect to the system, he must transfer instructions through network nodes such as routing equipment. The more nodes are, the more inefficiently the instructions connect. m describes the level of attack method that an attacker can achieve. When the attacker is connected to the system, r will be an index to stop the connection. The description and corresponding valuation, which are given by experts of cybersecurity, are shown in Table 2.

Table 2.
The valuation of availability.
The data weakness is divided into three indexes: confidentiality u, integrity w, and usability v, as shown in Table 3.

Table 3.
Data weakness valuation value.
Safety protection includes three indexes: code patch , normal protective measure , and emergency protective measure , shown in Table 4. Code patch reflects the extent of the patches covering system vulnerabilities. Normal protective measure refers to the ability to protect the system against information attacks under normal operating conditions. The emergency protective measure is the capability to handle emergencies when in danger. The vulnerability value is shown as follows.

Table 4.
Safety protection value.
3. Dynamic Monitoring
3.1. W-HMM Establishment
The HMM model can be used to build a dynamic evaluation model. Describing the stochastic process of generating explicit state sequences from hidden state sequences, HMM is a probability model related to time series. Each hidden state generates an explicit state. The security status of ICS is mostly unobservable. All the operations and the faults caused by the attack are recorded in the system’s log. The security is related to the fault with a certain observation probability. The probability of mutual transition between security states is the occurrence probability. By using the occurrence probability of the security state, the current system risk probability can be calculated to monitor the system’s risk dynamically.
However, HMM cannot distinguish the magnitude of the danger caused by different states. This paper proposes a W-HMM (weight HMM) method. W-HMM is the optimization method of HMM and weighs the results calculated by HMM. The value of weight is estimated based on the magnitude of the danger. The aim is to improve the accuracy of the evaluation when calculating the risk value. In W-HMM, we optimize the calculation of HMM results by weighing the security state. The W-HMM model is proposed, shown in Figure 4.
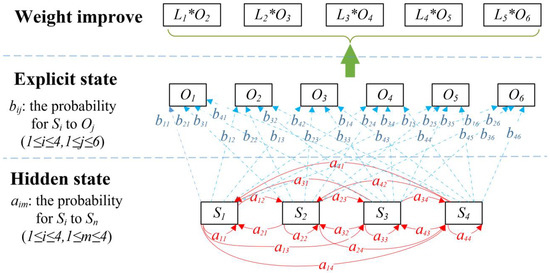
Figure 4.
The W-HMM model.
We construct a mapping relation of the Markov process with parameters. The security state can be categorized into secure , monitored , attacked , and captured states. indicates that the system is scanned or spied by an attacker. In this state, the bandwidth resources are occupied, and parameters will be stolen. In the attacked state, the attacker sends malicious data, but the system has not been captured. In the captured state, the system is captured by the attacker to execute the attacker’s instructions. In this state, the system may crash or perform dangerous operations. According to the severity of the fault, system faults are classified into normal , error , mild alarm , and warning ; moderate alarm ; and serious alarm , as shown in Figure 5 and Table 5.
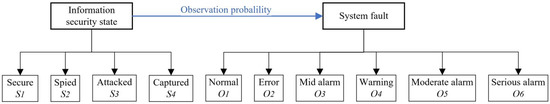
Figure 5.
The analysis diagram of security and system fault.

Table 5.
Example of system faults.
3.2. Calculating Occurrence Probability of Security by W-HMM
The specific steps are as follows.
- Constructing State and Model
The explicit state set O and the hidden state set S are, respectively, shown as follows.
The development relationships between hidden states is related by . is the probability of transition from state at time t to state at time .
The hidden state is represented by the explicit state. is called the explicit state probability matrix, and shows the relationship between hidden and explicit state. is the probability of transition from the state at time t to state at the time .
The state transition probability matrix A and the explicit state probability matrix B can be written as follows.
The W-HMM of the ICS can be described as , among which represents the probability of the initial state, which is shown as follows.
- 2.
- Algorithm of Baum–Welch
Markov model correction algorithms based on state sequences are classified into supervised and unsupervised learning algorithms [38]. A supervised learning algorithm records a large amount of state data to estimate the parameters. However, it is time consuming, costly, and causes difficulty in evaluating parameters dynamically. Unsupervised learning algorithms identify model parameters based on training samples and are suitable for calculating the parameters of W-HMM of ICS. To accurately describe the system and adapt to system changes, the W-HMM model is trained and updated iteratively with the Baum–Welch algorithm [39]. It is possible to obtain (see Appendix A) Equation (12), which represents the W-HMM model after iterations. When adding new sample data, the current Markov parameters are taken as the initial parameters, and Baum–Welch iterative calculations are carried out to obtain the latest parameters. The occurrence probability of security risks is extracted from the state transition probability matrix of parameters.
4. Assessment
Field experts of ICS obtained the state weight values that affect the risk value of ICS, shown in Table 6. The risk value describes the loss caused by an attack on the company. It is equal to the product of the failure probability and consequence of the attack. The security risk value can be determined as follows.

Table 6.
State weight value.
From Equation (13), , and are the weight values of the five states in the observation states , and . Since some model parameters change with time, they are classified according to the measurement of their period, demonstrated in Table 7.

Table 7.
Type of parameters.
5. Framework of DFA-ICSS
Illustrated in Figure 6, the DAF-ICSS framework is composed of static identification, dynamic monitoring, and evaluation. The framework can evaluate the security of ICS qualitatively and quantitatively. In this section, we will briefly summarize the procedure of the assessment.
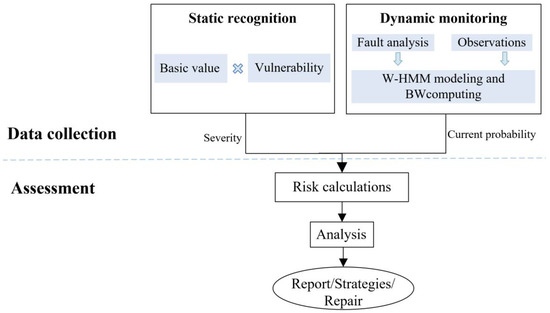
Figure 6.
Security evaluation framework of DAF-ICSS.
During data collection, there are two stages. One is static identification, which identifies the value and vulnerability of each part of the evaluation system. The analytic hierarchy process enumerates the factors that affect the value and the vulnerability of the system. The result of static identification is represented by a severity value, which is obtained by multiplying the value and vulnerability of the system.
The other is dynamic monitoring, which calculates the system’s security risk probability. Moreover, the calculation is based on W-HMM. Its result predicts the possibility of system security risks.
The system security state is unobservable. W-HMM is introduced for dynamic monitoring to establish the connection between the observable states and the unobservable security state. This method calculates the risk probability according to the observation state and updates the risk probability in the next new observation state. W-HMM can quantify and weigh the risk probability based on different application scenarios and models.
In the assessment stage, we obtain the system risk value by multiplying the severity value and the risk probability. We develop a risk map. The map determines the risk level by the risk value’s boundary. The boundary is set by the risk tolerance of the system, shown in Figure 7. The system is safe when the risk value is in the green area. If it is in the yellow area, the system is at risk. The evaluation system will immediately issue an alarm if it reaches the red zone. Its purpose is to locate risk levels according to the calculated risk value quickly. The corresponding protection strategy can be chosen rapidly according to the level and risk value.

Figure 7.
Risk map.
6. Experiments and Results
6.1. Experimental Setup
An attack test platform is built to verify the feasibility and effectiveness of the evaluation method proposed in this paper, shown in Figure 8.
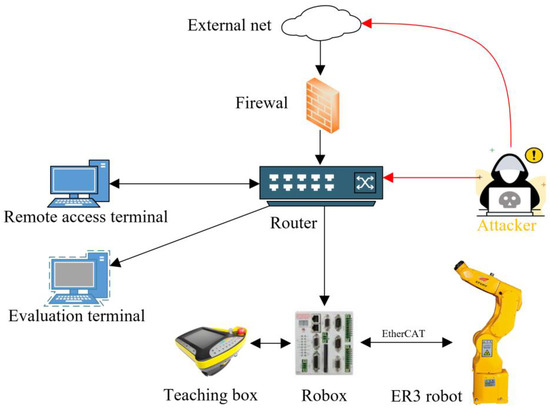
Figure 8.
The topography of the system.
The platform comprises three computers and a robot that are connected through a gigabit router. The robot, which is ER3, is produced by Effort. The controller of the robot is Robox produced by Robox SPA.
The computers play as the remote terminal, the evaluation terminal, and the attack terminal. The remote terminal sends instructions and programs. The attack terminal attacks the control system. Meanwhile, the evaluation terminal records the robot’s status data and evaluates the system.
6.2. Experimental Data Collection and Calculation
- Step 1: Static identification
The company’s asset data and data evaluated by asset management are shown in Table 8. Table 9 displays the vector and complexity in availability. When the robot connects to the PC, the robot does not perform authentications or check the content of the communication. As a result, the authentication score is 0.704. Most system security measures are warnings. The valuation of data weakness can be found in Table 9. Most system faults are alarming. When a serious failure occurs, the system will stop running. The score of the emergency protective measure is 0.5.

Table 8.
Basic value datasheet of the robot unit.

Table 9.
Control system information sheet.
- Step 2: Dynamic monitoring
The initial parameters of the model are obtained by collecting and sorting empirical data. The initial parameters , , and are obtained by empirical estimation. We used two types of DOS attacks during the experiment in the two periods. In the first period, the hacker uses ping flooding random attacks. In the second period, the hacker uses UDP attacks to attack the vulnerable spots of the system. In the experiment, the attacked ports are random, and the attack frequency is once every 10 min.
- Step 3: Assessment
The failure of the industrial control system caused by the attack is probabilistic. We divide the experiment into two stages. Each attack stage lasts a week, and the robot control system status is collected once an hour during the working time every day. We record the status of the control system with three different methods: DAF-ICSS, expert [40] and HMM [41]. The data obtained by these methods are shown in Table 10. We obtain the average value of each stage evaluation from the on-site enterprise expert group.

Table 10.
The data of the observation sequence.
Figure 9 shows that the risk value evaluated by experts is close to the other algorithms at the beginning of stage 1. It means that every assessment method is accurate at the beginning. After the beginning stage, the expert’s assessment remains the same at each stage and cannot dynamically evaluate the system’s security. HMM and DAF-ICSS assessment methods can dynamically assess the security of the system.
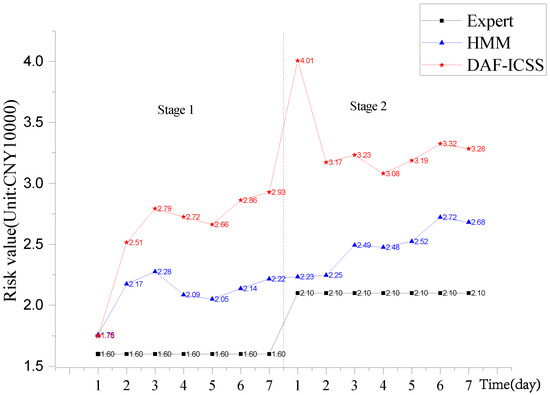
Figure 9.
The result of the experiment.
At the beginning of stage 2 in the assessment, we open the UDP port of the system, which leads to a new vulnerability. We increase the weight of Vv, and it results in a severe alarm state. However, the HMM assessment method draws an insensitive rise in Figure 9. Because the HMM method assigns no risk weight to a variety of system security states, DAF-ICSS can sensitively reflect the changes of system risk by weighing the evaluation elements and establishing a dynamic evaluation model. When the system is attacked by a UDP flood, the risk value assessed by DAF-ICSS exceeds CNY 40,000. The values given by other evaluation methods do not exceed CNY 40,000. DAF-ICSS assessment is more accurate than HMM.
Then, the evaluation system issues an alarm and closes the UDP port to lower the risk’s value. The experiment confirms the effectiveness and timeliness of DAF-ICSS.
ICS may expose different vulnerabilities during running. For example, the operator opens the remote service port by mistake, which could lead to system vulnerability. We should focus on the dynamic changes in risk value. When the risk value suddenly increases, the system is probably experiencing a security risk.
The proposed framework of DAF-ICSS is more sensitive than other methods [42,43], which could provide a dynamical risk value. Table 11 lists the comparision of some security assessment methods in performance.

Table 11.
The comparison of some security assessment methods in performance.
7. Disscusion
In addition to industrial robots, the proposed method can also be used for other industrial control systems. Some parameters in the method need to be evaluated based on a specific application scenario. For example, the work environment will be changed according to different scenarios. If we obtain a more accurate risk value, the sequence and state can be increased to enhance the quality of DAF-ICSS. It will also increase the computational burden of the system.
The security assessment combines the qualitative method, which uses a risk map to determine the system’s security, and the quantitative method, which uses a risk value to measure security value. Because the assessment relies on observations of ICS anomaly alarms, the risk value may be inaccurate when the alarms do not accurately match the system’s state. In the future, it can be overcome to some extent.
8. Conclusions
Security assessment is the critical part of the system’s security. We propose a security assessment method for ICS. We divide the security assessment of ICS into three steps: static recognition, dynamic monitoring, and assessment. A hierarchical system is provided for evaluating security risks. To obtain the system’s risk level, the assessment method based on W-HMM calculates the industrial security risk value. It can be updated online for optimized estimation results and determine the degree of influence with different parameters in the factory. DAF-ICSS enables operators to find out a change of risk with high precision and efficiency. It also can be used to conduct cause analysis and security impact analysis.
However, this assessment method still has room for improvement, such as exploring methods for selecting more reasonable weights, etc. In addition, there is a well-known problem in industrial systems: The already designed secure architecture that does not sacrifice functionality has difficulty in providing a coordination of security and safety. In the future, we could focus on assessing multiple industrial control systems and fundamental understanding between safety and security based on dynamic security assessments so that dedicated modeling constructs and metrics can be proposed.
Author Contributions
Conceptualization, X.J.; Formal analysis, Y.C. and H.W.; Methodology, X.J. and G.W.; Data curation, H.W.; Software, H.W. and G.W.; Resources, H.W.; Funding acquisition & Project administration, Y.C.; Supervision, X.J.; Validation, Y.C.; Visualization, X.-F.J. and G.W.; Writing—original draft, X.J.; Writing—review & editing & Investigation, X.-F.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research received the support of the National Key R&D Program of China (2019YFB1312202).
Data Availability Statement
Not applicable.
Acknowledgments
Projects supported by the National Key R&D Program of China (2019YFB1312202) are greatly acknowledged.
Conflicts of Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Appendix A
The probability of the hidden state, , at time, t, is expressed in Equation (A1). The probabilities of the hidden states that is at time t and at time are defined in Equation (A2). The Baum–Welch algorithm is used to calculate the model parameters for n times, as shown in Equations (A3)–(A5). The condition for terminating iteration is that the absolute values of , or are within a tolerance criterion.
References
- Dieber, B.; Breiling, B.; Taurer, S.; Rass, S.; Schartner, P. Security for the robot operating system. Robot. Auton. Syst. 2017, 98, 192–203. [Google Scholar] [CrossRef]
- Tan, Q.; Tong, Y.; Wu, S.; Li, D. Towards a next-generation production system for industrial robots: A CPS-based hybrid architecture for smart assembly shop floors with closed-loop dynamic cyber physical interactions. Front. Mech. Eng. 2020, 15, 1–11. [Google Scholar] [CrossRef]
- Cevallos, H.; Gualacio, J.; Silva, A.; Montalvo, P. Implementation of a Remote Control and Monitoring System in Assembly Processes with Industrial Robot Kawasaki Rs003 Through the GSM Network in the Industrial Automation Laboratory of the Faculty of Mechanics. KnE Eng. 2018, 3, 101–110. [Google Scholar] [CrossRef]
- Li, L.; Xie, L.; Hao, B.; Yang, L.; Hu, T.; Wang, Z. Data Logic Attack on Heavy-Duty Industrial Manipulators. IEEE Access 2020, 8, 17419–17433. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Avasthi, V.; Goundar, S. Cyber security attacks on robotic platforms. Netw. Secur. 2019, 2019, 13–19. [Google Scholar] [CrossRef]
- Robla-Gómez, S.; Becerra, V.M.; Llata, J.R.; Gonzalez-Sarabia, E.; Torre-Ferrero, C.; Perez-Oria, J. Working together: A review on safe human-robot collaboration in industrial environments. IEEE Access 2017, 5, 26754–26773. [Google Scholar] [CrossRef]
- Wangen, G.; Hallstensen, C.; Snekkenes, E. A framework for estimating information security risk assessment method completeness. Int. J. Inf. Secur. 2018, 17, 681–699. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Bi, F.; Chen, W.; Miao, X.; Liu, J.; Tang, C. An improved information security risk assessments method for cyber-physical-social computing and networking. IEEE Access 2018, 6, 10311–10319. [Google Scholar] [CrossRef]
- Kumar, D.; Meeden, L. A robot laboratory for teaching artificial intelligence. ACM SIGCSE Bull. 1998, 30, 341–344. [Google Scholar] [CrossRef]
- Das, S.; Mukhopadhyay, A.; Saha, D.; Sadhukhan, S. A markov-based model for information security risk assessment in healthcare MANETs. Inf. Syst. Front. 2019, 21, 959–977. [Google Scholar] [CrossRef]
- Kessler, S.R.; Pindek, S.; Kleinman, G.; Andel, S.A.; Spector, P.E. Information security climate and the assessment of information security risk among healthcare employees. Health Inform. J. 2020, 26, 461–473. [Google Scholar] [CrossRef] [PubMed]
- Turskis, Z.; Goranin, N.; Nurusheva, A.; Boranbayev, S. Information security risk assessment in critical infrastructure: A hybrid MCDM approach. Informatica 2019, 30, 187–211. [Google Scholar] [CrossRef]
- Manickavasagam, K.; Prasad, B.K.S.; Ramasangu, H. Assessment of power system security using Security Information Index. IET Gener. Transm. Distrib. 2019, 13, 3040–3047. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Sun, Z. Coal resource security assessment in China: A study using entropy-weight-based TOPSIS and BP neural network. Sustainability 2020, 12, 2294. [Google Scholar] [CrossRef] [Green Version]
- Zhou, J.; Reniers, G.; Zhang, L. A weighted fuzzy Petri-net based approach for security risk assessment in the chemical industry. Chem. Eng. Sci. 2017, 174, 136–145. [Google Scholar] [CrossRef]
- Smith, D.; Veitch, B.; Khan, F.; Taylor, R. Understanding industrial safety: Comparing Fault tree, Bayesian network, and FRAM approaches. J. Loss Prev. Process Ind. 2017, 45, 88–101. [Google Scholar] [CrossRef]
- Hu, L.; Li, H.; Wei, Z.; Dong, S.; Zhang, Z. Summary of research on IT network and industrial control network security assessment. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 1203–1210. [Google Scholar]
- Alladi, T.; Chamola, V.; Zeadally, S. Industrial control systems: Cyberattack trends and countermeasures. Comput. Commun. 2020, 155, 1–8. [Google Scholar] [CrossRef]
- Adil, M.; Khan, R.; Ali, J.; Roh, B.H.; Ta, Q.T.H.; Almaiah, M.A. An energy proficient load balancing routing scheme for wireless sensor networks to maximize their lifespan in an operational environment. IEEE Access 2020, 8, 163209–163224. [Google Scholar] [CrossRef]
- AlMedires, M.; AlMaiah, M. Cybersecurity in Industrial Control System (ICS). In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 640–647. [Google Scholar]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Adil, M.; Khan, R.; Almaiah, M.A.; Binsawad, M.; Ali, J.; Al Saaidah, A.; Ta, Q.T.H. An efficient load balancing scheme of energy gauge nodes to maximize the lifespan of constraint oriented networks. IEEE Access 2020, 8, 148510–148527. [Google Scholar] [CrossRef]
- Ratnayake, R.C. Consequence classification based spare parts evaluation and control in the petroleum industry. In Proceedings of the 2019 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Macao, China, 15–19 December 2019; pp. 1204–1210. [Google Scholar]
- Adil, M.; Almaiah, M.A.; Omar Alsayed, A.; Almomani, O. An anonymous channel categorization scheme of edge nodes to detect jamming attacks in wireless sensor networks. Sensors 2020, 20, 2311. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef] [Green Version]
- Park, J.W.; Lee, S.J. A quantitative assessment framework for cyber-attack scenarios on nuclear power plants using relative difficulty and consequence. Ann. Nucl. Energy 2020, 142, 107432. [Google Scholar] [CrossRef]
- Xu, H.; Su, J.; Zong, X.; Yan, L. Attack identification for software-defined networking based on attack trees and extension innovation methods. In Proceedings of the 2017 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017; pp. 485–489. [Google Scholar]
- Shang, W.; Gong, T.; Chen, C.; Hou, J.; Zeng, P. Information security risk assessment method for ship control system based on fuzzy sets and attack trees. Secur. Commun. Netw. 2019, 2019, 3574675. [Google Scholar] [CrossRef]
- Hu, J.; Guo, S.; Kuang, X.; Meng, F.; Hu, D.; Shi, Z. I-HMM-Based Multidimensional Network Security Risk Assessment. J. Abbr. 2019, 8, 1431–1442. [Google Scholar] [CrossRef]
- Subramanian, N.; Zalewski, J. Quantitative assessment of safety and security of system architectures for cyberphysical systems using the NFR approach. IEEE Syst. J. 2014, 10, 397–409. [Google Scholar] [CrossRef]
- Aziz, A.; Ahmed, S.; Khan, F.I. An ontology-based methodology for hazard identification and causation analysis. Process. Saf. Environ. Prot. 2019, 123, 87–98. [Google Scholar] [CrossRef]
- Ye, Y.; Yan, L.; Sun, W.; Zhang, Q.; Wang, N. Discussion on Risk Assessment of Network Security Management. In Proceedings of the 2018 10th International Conference on Measuring Technology and Mechatronics Automation (ICMTMA), Changsha, China, 10–11 February 2018; pp. 409–411. [Google Scholar]
- Zou, Z.; Hou, Y.; Yang, H.; Li, M.; Wang, B.; Guo, Q. Research and implementation of intelligent substation information security risk assessment tool. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 24–26 May 2019; pp. 1306–1310. [Google Scholar]
- Chen, J.; Zhu, H.; Chen, Z.; Cai, X.; Yang, L. A Security Evaluation Model Based on Fuzzy Hierarchy Analysis for Industrial Cyber-Physical Control Systems. In Proceedings of the 2019 IEEE International Conference on Industrial Internet (ICII), Orlando, FL, USA, 11–12 November 2019; pp. 62–65. [Google Scholar]
- Datta, S.K. DRAFT-A Cybersecurity Framework for IoT Platforms. In Proceedings of the 2020 Zooming Innovation in Consumer Technologies Conference (ZINC), Novi Sad, Serbia, 26–27 May 2020; pp. 77–81. [Google Scholar]
- Park, K.C.; Shin, D.H. Security assessment framework for IoT service. Telecommun. Syst. 2017, 64, 193–209. [Google Scholar] [CrossRef]
- He, D.; Deng, Z.; Zhang, Y.; Chan, S.; Cheng, Y.; Guizani, N. Smart contract vulnerability analysis and security audit. IEEE Netw. 2020, 34, 276–282. [Google Scholar] [CrossRef]
- Holgado, P.; Villagrá, V.A.; Vazquez, L. Real-time multistep attack prediction based on hidden markov models. IEEE Trans. Dependable Secur. Comput. 2017, 17, 134–147. [Google Scholar] [CrossRef]
- Tu, S. Derivation of Baum-Welch Algorithm for Hidden Markov Models. 2015. Available online: Https://people.eecs.berkeley.edu/~stephentu/writeups/hmm-baum-welch-derivation.pdf (accessed on 1 March 2022).
- Tian, D.; Yang, B.; Chen, J.; Zhao, Y. A multi-experts and multi-criteria risk assessment model for safety risks in oil and gas industry integrating risk attitudes. Knowl.-Based Syst. 2018, 156, 62–73. [Google Scholar] [CrossRef]
- Wang, C.; Li, K.; He, X. Network risk assessment based on baum welch algorithm and HMM. Mob. Netw. Appl. 2021, 26, 1630–1637. [Google Scholar] [CrossRef] [Green Version]
- Aly, S.; Tyrychtr, J.; Kvasnicka, R.; Vrana, I. Novel methodology for developing a safety standard based on clustering of experts’ assessments of safety requirements. Saf. Sci. 2021, 140, 105292. [Google Scholar] [CrossRef]
- Budiyanto, M.A.; Fernanda, H. Risk assessment of work accident in container terminals using the fault tree analysis method. J. Mar. Sci. Eng. 2020, 8, 466. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).