Abstract
In this paper, we address the problem of authenticating transmitters in millimeter-wave (mmWave) multiple-input multiple-output (MIMO) communication systems, and propose a location verification scheme based on multi-dimensional mmWave MIMO channel features. In particular, we first examine the mmWave MIMO channel features in terms of azimuth angle of arrival (AAoA), elevation angle of arrival (EAoA), and path gain, and then extract these fine-grained channel features through the maximum-likelihood (ML) estimation method. Based on the extracted feature parameters, authentication validation is cast in the framework of hypothesis testing theory. We also derive the analytical expressions for the typical false alarm and detection rates by using the likelihood ratio test and thus the statistical performance is analytically established. Finally, extensive numerical results are provided to demonstrate the performance of the proposed authentication scheme.
1. Introduction
Millimeter-wave (mmWave) multiple-input multiple-output (MIMO) systems serve as a critical technique for 5G (fifth-generation communication) and beyond wireless communication networks. The mmWave MIMO technique can lead to a significant increase in data rates, wide bandwidth, and higher spectrum efficiency. By integrating huge antenna arrays, 5G and beyond communication systems operating from 30 to 300 GHz can support huge connections among a bulk of smart devices, contributing to various applications such as the Industrial Internet of Things (IIoT) and the Internet of Vehicles (IoV).
However, mmWave MIMO communication systems may become subject to malicious attacks because of the above important applications they can support. Moreover, the mmWave wireless communication medium is open in space and thus attackers can easily access the communication network and obtain the transferred information between legitimate users and base stations. One of the main threats in mmWave MIMO systems is identity-based spoofing attack, where an attacker eavesdrops the legitimate communication links and further impersonates a legitimate transmitter to inject harmful signals into the communication network. To tackle the spoofing attacks in mmWave systems, identity authentication presents a promising solution to secure mmWave MIMO communication systems.
We note that the existing authentication schemes can be roughly divided into higher layer and physical layer authentication schemes. The higher layer authentication schemes are mainly dependent on secret keys and encryption/decryption algorithms to validate transmitter identities [1,2,3]. Meanwhile, the physical layer authentication schemes verify transmitter identities through physical layer features [4]. It is noted that the higher layer authentication may not completely adapt to the emerging mmWave MIMO systems which include distributed, dynamic and highly heterogeneous devices. Such mmWave MIMO systems may not support the cryptographic key distribution and management, high consumption of communication and computation resources in higher layer authentication schemes. As a complement and an enhancement of the higher layer authentication, physical layer authentication possesses several characteristics such as high security, low complexity and high compatibility [5]. Thus, in this paper we focus on physical layer authentication in mmWave MIMO systems.
Existing physical layer authentication schemes mainly include channel-based authentication and hardware-impairment-based authentication. The hardware-impairment-based method authenticates the legitimacy of a transmitter identity by extracting specific non-ideal hardware parameters from received signals. In contrast, channel-based authentication utilizes the fact that wireless channels decorrelate rapidly as the source (e.g., a transmitter or user using transmitter is transmitting signals to an intended destination/receiver) changes location in an environment with rich scatterers and reflectors. In fact, channel-based authentication verifies the location of the current transmitter rather than transmitter physics identity, and hence is referred to as location verification. There exists some research works on physical layer authentication for mmWave systems [6,7,8,9,10,11,12,13,14,15]. In [6], the authors propose a physical layer authentication scheme by using sparse mmWave channel. A power allocation technique for the precoder and the authentication tag is first developed for fingerprint-based authentication in a multi-user mmWave UAV network [7]. Multipath time delay caused by planar specular reflectors is acquired to illustrate the authenticity of user position 5G mmWave communication with planar reflectors [8]. The intrinsic physical attributes for 5G communications are analyzed for physical layer authentication in detail and the future possible directions for the exploitation of physical attributes is demonstrated in [9]. The authors in [10] further study the physical characteristics of 5G IoT in various application scenarios and describe the possible security threats resulting from the 5G IoT physical layer. Based on virtual angles of arrival in mmWave systems and machine learning methods, the authors in [11] propose a physical layer authentication scheme to detection spoofing attacks. Two effective pilot contamination attack detection approaches are proposed for power non-orthogonal multiple access in massive MIMO 5G communications, based on the sparseness and statistics of mmWave virtual channels [12]. Following this line, the authors in [13] present a new physical layer countermeasure using channel virtual representation to defend against pilot contamination attack. In [14], unique beam pattern features are utilized to achieve physical layer spoofing attack detection and the detection problem is cast as a machine learning classification through the sector level sweep (SLS) process. The authors in [15] develop a physical layer authentication scheme by using signal-to-noise ratio (SNR) trace features to detect spoofing attacks in mmWave systems.
Frequency-selective Rayleigh channel time variations are used to detect spoofing attacks in wireless networks, considering the channel estimation errors [16]. To improve the spoofing detection accuracy, a logistic regression-based authentication approach is developed without the requirements of the known channel model [17]. The authors jointly use multipath delay and channel gain characteristics of the channel impulse response to achieve performance improvement of physical layer authentication [18]. The above existing approaches demonstrate the uniqueness and usability of physical layer features for spoofing attack detection and authentication. It is noted that the above existing approaches are developed for spoofing detection by conventional channel state information. These approaches cannot be extended directly to mmWave MIMO communication systems because it is difficult for them to sufficiently excavate fine-grained physical layer characteristics from mmWave MIMO channels. Hardware-impairment-based authentication generally needs to employ high-precision hardware equipment for hardware feature extraction and bears high computational complexity [14,15]. Moreover, machine-learning-based authentication framework requires an expensive training stage with a large amount of training data, which might be unrealistic in practice. In addition, the analytic establishment of statistical performances still remains an open problem in machine-learning-based authentication frameworks. To this end, we explore the exploitation of multi-dimensional mmWave MIMO channel features to design a new location verification scheme for mmWave MIMO communication systems. These channel features include azimuth angle of arrival (AAoA), elevation angle of arrival (EAoA) and path gain, which are jointly used to validate the legitimacy of transmitters and to improve the authentication performance. The main difference between the schemes proposed in this paper and those in previous works [16,17,18] is that the previous approaches mainly focus on channel statistics in the time domain while this paper extracts channel features in the time domain as well as the angle domain. In addition, the scheme proposed in this paper attempts to explore the exploitation of multi-dimensional mmWave MIMO channel features to achieve location verification.
The main contributions of this paper are summarized as follows:
- By exploiting multi-dimensional mmWave MIMO channel features in both the time domain and angle domain, we develop a new location verification scheme to achieve validation of a transmitter location for mmWave MIMO communication systems.
- To determine estimation error variances of channel features in terms of AAoA, EAoA, and path gain, we estimate the mmWave MIMO channels based on maximum-likelihood estimation theory. To analytically evaluate the performance of our proposed location verification scheme, we derive the typical two performance metrics and the statistical performance is analytically established.
- Extensive numerical results are provided to demonstrate that the proposed scheme achieves desired performance. Numerical results are used to further show how the system parameters can affect the statistical performance.
The remainder of this paper is organized as follows. Section 2 introduces the concerned system model and problem formulation. Section 3 and Section 4 present the proposed location verification scheme and performance analysis, respectively. Section 5 shows the numerical results and performance evaluation. Finally, Section 6 concludes this paper.
Notation: , , , , denote the conjugate-transpose, transpose, conjugate, inverse and pseudo-inverse of a matrix, respectively. The -th element of a matrix is . is a diagonal matrix with on the main diagonal. is the vectorization of matrix . and ≜ represent the matrix trace function and definitions, respectively. represents the expectation operator. is the Euclidean norm operator. A Gaussian random variable x with mean and variance c can be represented by . If let be the subspace spanned by the columns of matrix , then denotes the orthogonal projection matrix onto , that is,
2. Problem Formulation and System Model
2.1. Problem Formulation
Similar to previous works [16,17,18], we also use a three-entity model including a legitimate transmitter (Alice), a malicious attacker (Eve) and a legitimate base station (Bob), where Alice and Eve are both equipped with a single antenna and Bob is equipped with antennas, as shown in Figure 1. Eve intends to spoof Bob by using the identity of Alice and thus may launch some more advanced attacks, such as a man-in-the-middle attack and session hijacking attack while Alice communicates with Bob.
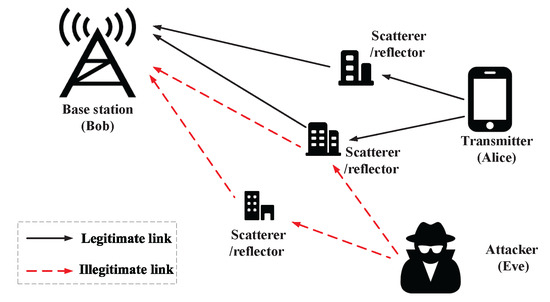
Figure 1.
System model.
Suppose Alice transmits one data frame to Bob at time and this data frame was validated by cryptography-based higher layer authentication approaches. In this process, Bob measures and stores physical layer features information, e.g., mmWave MIMO channel features, with the help of signal estimation techniques. Subsequently, at time t, an unknown transmitter (either Alice or Eve) sends another data frame to Bob and Bob needs to validate the data frame origin (i.e., the current transmitter identity) to avoid impersonation attack.
Eve has data frame structure information by probing the transmitted signals between Alice and Bob and some publicly known information (e.g., training sequences and pilot signals). The estimation techniques and authentication schemes that Bob utilizes cannot be known by the attacker, Eve. Further, we exploit the carrier sense multiple access/collision detection protocol.
2.2. Channel Model
Bob has a -antenna uniform planar array (UPA) where the numbers of antennas in the horizon and vertical directions are M and N, respectively, where . The number of radio frequency chains of Bob is [19]. Let d be the distance between any arbitrary two adjacent antennas, and be the analog beamformer equipped at Bob. Considering the limited scattering characteristics of the mmWave communication environments, we here adopt the extended Saleh-Valenzuela (SV) model to characterize the mmWave MIMO channels [20,21]. Denote as the azimuth angle of arrival (AAoA) of the l-th propagation multipath of the transmitter and as the elevation angle of arrival (EAoA) of that, for , respectively. We assume and . The steering matrix is expressed by
where is the wavelength of the carrier signal [22]. For simplicity, let and . The steering matrix can be further written as
where and .
Similar to [23], the mmWave channel with L being the number of propagation paths is modeled as
where , , and is the path gain of the l-th propagation path [22,24,25].
The -th element ( and ) for matrix is
Path gain is assumed to keep unchanged during one frame [26]. Based on [27], we use first-oder Gauss–Markov process to model the time-varying path gain as
where is the path gain correlation coefficient [28] and is zero-mean Gaussian noise, i.e., .
Similarly, we use first-order Gauss–Markov process to model the time-varying azimuth angle of arrival as
where is the AAoA correlation coefficient [28] and is zero-mean Gaussian noise, i.e., . We also use first-order Gauss–Markov process to model the time-varying elevation angle of arrival as
where is the EAoA correlation coefficient [28] and is zero-mean Gaussian noise, i.e., .
Channel-based verification utilizes the fact that wireless channels decorrelate rapidly as the source (e.g., a transmitter or user using transmitter is transmitting signals to an intended destination/receiver) changes location in an environment with rich scatterers and reflectors. This indicates that wireless channel features are spatially decorrelated between different geographic locations. When the distance between a legitimate source and an adversary is greater than half of the wavelength, it is extremely difficult for the adversary to obtain the accurate wireless channel features. Although the channel-based method essentially authenticates the practical geographic location related to the inherent properties of channel features, it is an effective authentication to achieve legitimacy validation of the source identity. Therefore, this paper aims to design a new location verification scheme for validating data frame origin to resist against the impersonation attack.
2.3. Communication Model
The baseband signal received by Bob at time t is written as
where
- is the transmitted signal at time t. The signal power is .
- denotes the channel matrix between transmitter X (either Alice or Eve) and receiver Bob.
- is a zero-mean complex additive white Gaussian noise (AWGN), i.e., .
3. Proposed Location Verification Scheme
3.1. Estimation of MmWave Channels
To exploit the fine-grained mmWave channel features, we estimate the channel parameters separately. We first estimate AAoA and EAoA, and then estimate the mmWave path gain. We can write the estimations of , and , respectively, as
where , and are the corresponding estimation errors, respectively. Next, we calculate the variances of the estimation errors, i.e., , and .
For notational simplicity, here we ignore the time index t and the path index l. The signal received by Bob at time t is given by
where is the steering matrix with its -th element given by
The conditional PDF of is expressed by
The maximum-likelihood (ML) method in [29] is used to estimate mmWave channel features , , and . The estimation of these features can be expressed as
When giving and , the estimation of is calculated as
Substituting (17) into (16), the estimations of and is written as
where is the cost function related to and , is the signal power and .
Next, we give Lemma 1 regarding the variance of the estimations for and .
Lemma 1.
The variance of the estimations for and in (18) are given by
where . and are the diagonal matrices given by
Proof.
The received signal without noise can be written as
When considering the receiver noise, the received signal can be further written as . By using Taylor series expansion, the first derivative of the cost function is given by
where denotes perturbation on .
Setting (23) equal to zero, is given by
where and are the first- and second-order derivatives of the cost function conditioned on , respectively.
is expressed as
Due to the independence between and , we have
The second-order conditional derivative with respect to is written as
Similarly, is calculated as
Based on (28) and (29), is further written as
where and represent the linear and quadrature functions of in , respectively. can be written as
where and are the linear and quadrature functions of in , respectively.
is expressed by
where
Based on (17), is rewritten as
where is calculated by the estimation of . By using Taylor’s expansion, we approximate as
Based on (19), the statistical characteristics of the estimation error of the mmWave path gain is calculated as
3.2. Location Validation
The location validation is implemented by comparing the similarity between the current channel parameters and the previous ones with preset thresholds, based on a binary hypothesis test. If we denote the difference between the current channel parameters (i.e., ) at successive time as for , then we have
Let , and be preset thresholds for AAoA, EAoA and path gain, respectively. Next, we design a simple binary hypothesis testing for location validation as
Under , the current transmitter is Alice. In contrast, means that the current transmitter is Eve.
The fundamental principle for the proposed scheme in this paper is that location validation decision is implemented by comparing the similarities between current estimated channel features at time t and previous ones at time with the corresponding preset thresholds, based on the framework of hypothesis testing theory. Channel statistics and the temporal values for AAoA, EAoA and path gain at time , and correlation coefficients can be modeled as side information that is known at both the transmitter (Alice) and the legitimate receiver (Bob), but not the adversary (Eve). The legitimate transmitter (Alice) and intended legitimate receiver (Bob) cooperate to secure communication transmission by means of the knowledge of this side information; this is beneficial for both partners. It should be stressed that the validation and efficiency of this idea were already studied from an information-theoretical point-of-view in [30], and the work [30] also provided the right guidance to the appropriate code design in practice.
4. Performance Analysis
In this section, we focus on the modeling of false alarm rate (denoted by ) and detection rate (denoted by ). To facilitate the calculation of the two probabilities, we denote the probability of under for and , and we consider , and . Based on authentication decision in (45), we establish the following lemmas regarding the probability .
Proof.
To calculate the probability distribution of in (44), we define as
One can see that is a zero-mean Gaussian distribution with variance . Therefore, under is a central chi-square distribution random variable and the PDF of under is then written as
where is a Gamma function. The CDF of under is written as
Accordingly, is written as
Similarly, based on (47), we derive under hypothesis as
Because , , and are independent zero-mean Gaussian random variables with variances , , and , respectively, and then the PDF of under is written as
where . Then, the CDF of under is written as
According to (54), is written as
□
Lemma 3.
Lemma 4.
Based on the above lemmas, we can establish the following theorem regarding the closed expressions of and .
Theorem 1.
For the mmWave MIMO communication model shown in Figure 1, and of the proposed authentication scheme are determined, respectively, as
Suppose that Bob has no knowledge of the channel parameters from data frame at time t such as and for , . In this case becomes
Following similar steps for the derivation of , we can obtain with u being without the knowledge of channel parameters at time , and then we have
where , , , , , and . In this case, and of the proposed authentication scheme are determined, respectively, as
Suppose that legitimate Alice and adversary Eve transmit signals to Bob with equal probability. We use to denote the secrecy rate improvement afforded by the knowledge of data frame at time for both legitimate transmitter and receiver, relative to the case in which the knowledge is not used. Then, can be calculated as
5. Numerical Results
5.1. System Parameters and Simulation Settings
Let signal-to-noise ratio (SNR) denote as and be the ratio of Eve’s and Alice’s AAoA variances. We use to denote the ratio of Eve’s and Alice’s EAoA variances, and to denote the ratio of Eve’s and Alice’s path gain variances. We set the number of the receiver antennas as . In the simulations, the first frame is validated based on a higher layer verification scheme and the second frame is validated by using the proposed location verification scheme.
5.2. Impact of SNR on the Verification Performance
We plot in Figure 2 ROC (receiver operating characteristic, ROC) variations under the settings of ( = 128, L = 20, = 2 dB, = 2 dB, = 2 dB) at different SNRs. From Figure 2, we can see that the authentication performance ( and ) under SNR = 5 dB outperforms that of the others and the performance for SNR = −5 dB is poorest. This indicates that the SNRs have severe impacts on the authentication performance. One can improve the authentication performance by setting a higher SNR. However, the SNR level usually has a limit due to the practical conditions. In many practical environments, and are usually a required constraint pair to satisfy the requirements of a practical authentication system. As shown in Figure 2, the authentication performance ( and ) for SNR = 0 dB and SNR = 5 dB can satisfy the practical requirements and the performance at SNR = 5 dB is best. From Figure 2, we also can see that when is fixed, increases when SNR increases. This means that a higher SNR can lead to a better authentication performance.
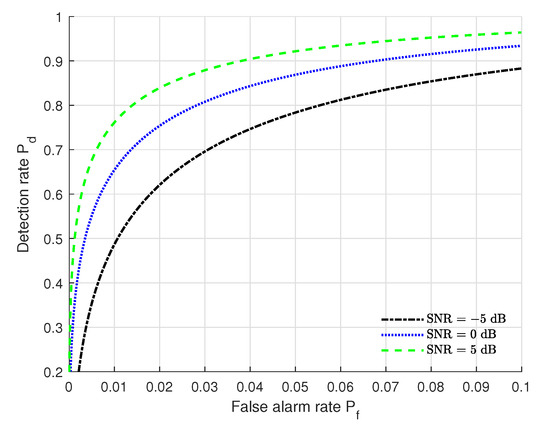
Figure 2.
ROC curves under different SNRs with the settings of ( = 128, L = 20, = 2 dB, = 2 dB, = 2 dB).
5.3. Impact of the Number of Antennas on the Authentication Performance
We show in Figure 3 the ROC results under different receiver antenna numbers with the settings of (SNR = 10 dB, L = 20, = 2 dB, = 2 dB, = 2 dB). From Figure 3, we can see that the authentication performance (, ) under 64 receiver antennas outperforms that of the others, and the performance under 16 receiver antennas is poorest. This is because multiple antennas can improve feature dimensions and further improve the authentication performance. When is fixed, increases when the number of receiver antennas increases. Moreover, the authentication performance (, ) under 64 receiver antennas can satisfy the practical authentication requirements.
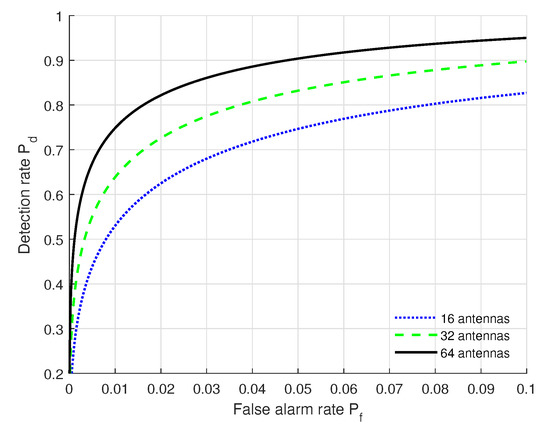
Figure 3.
ROC curves under different numbers of receiver antennas with the settings of (SNR = 10 dB, L = 20, = 2 dB, = 2 dB, = 2 dB).
5.4. Impact of the Number of Multipaths on the Authentication Performance
We show in Figure 4 the ROC curves under different numbers of multipaths with the settings of (SNR = 10 dB, = 64, = 2 dB, = 2 dB, = 2 dB). From Figure 4, we can see that the authentication performance (, ) under L = 15 multipaths outperforms that of the others, and the performance under L = 5 multipaths is poorest. This means that more multipaths can contribute to the authentication performance. We can also see that when is fixed, increases when the number of multipaths increases.
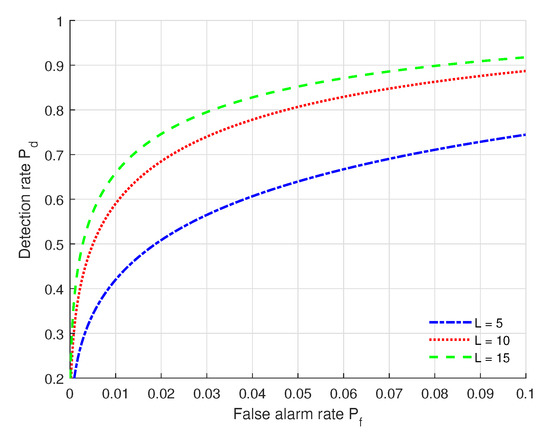
Figure 4.
ROC curves under different numbers of multipaths with the settings of (SNR = 10 dB, = 64, = 2 dB, = 2 dB, = 2 dB).
5.5. Impact of on the Authentication Performance
To investigate the impact of the distance between Eve–Bob and Alive–Bob on performance, we need to characterize being the variance of the path gain of the l-th propagation path from the transmitter X to Bob. According to [31], baseband path gain is written as , where is the attenuation coefficient of l-th propagation path and is carrier frequency. According to the Central Limit Theorem, the path gain can be modeled as a zero-mean complex circular symmetric Gaussian process and for large-scale fading channels, can be modeled by applying ([32], Chapter 2), as
where K is a reference path gain value; is a reference distance for antenna far-field; is a path loss exponent ranging between 2 and 5 in free space propagation wireless environments; and is a shadowing factor modeled as a log-normal random variable. Because the distance between the transmitter and receiver is much larger than antenna separation, we can use the approximation for . From (67), we have . Both Alice and Eve are assumed to be randomly deployed at arbitrary locations in a circular area centered on Bob, and there is no shadow fading in that area. By using (67), by dB value without shadow fading is given by . We make an assumption (without loss of generality) that Alice is in a fixed location, i.e., is a constant and we adjust the distance between Eve and Bob to obtain different .
We show in Figure 5 how varies with under different s and with the settings of (SNR = 10 dB, = 128, L = 25, = 2 dB, = 2 dB). From Figure 5, increases when increases for a given . This clearly indicates that if Eve is closer to Bob, she might be successfully detected by Bob, and Eve might select an appropriate location in which she has a high probability of succesfully impersonating Alice. In addition, the authentication performance under = 0.08 outperforms that of the others, and the performance under = 0.02 is poorest. This is because a lower value means a stricter performance requirement and there would be a trade-off between and . We can also see from Figure 5 that when is fixed, increases when increases.
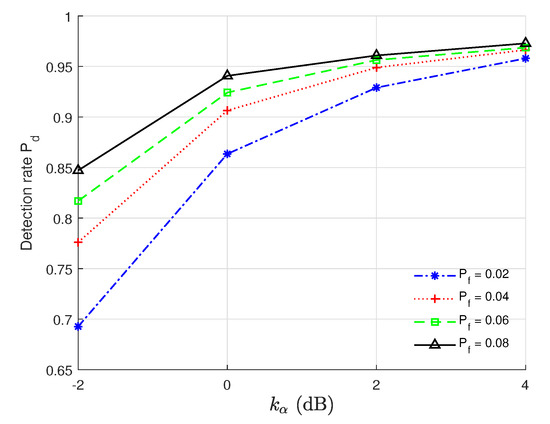
Figure 5.
vs. with the settings of (SNR = 10 dB, = 128, L = 25, = 2 dB, = 2 dB).
5.6. Performance Comparison
Figure 6 displays a performance comparison between the authentication scheme proposed in [16] and our scheme. From Figure 6, we can see that the performance (, ) of our scheme jointly using AAoA, EAoA and path gain outperforms that of the scheme only using path gain [16]. This is because the scheme in [16] uses coarse-grained channel information while our scheme uses multi-dimensional mmWave MIMO channel features (i.e., AAoA, EAoA and path gain) to effectively utilize the fine-grained channel information. It is also noted that when increases, the detection rates of both schemes increase. Moreover, the authentication performance (, ) of our scheme can better satisfy the practical authentication requirements. This is beneficial for exploiting both the AAoA and EAoA features, and allows us to gain important insights on the impacts of angle domain features on authentication performance.
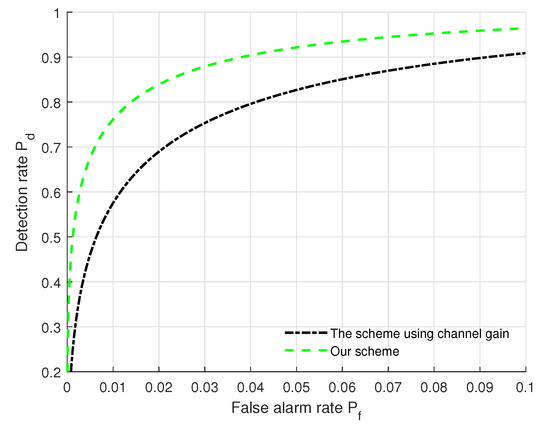
Figure 6.
Performance comparison between the scheme in [16] and our scheme with the settings of (SNR = 5 dB, = 128, L = 20, = 2 dB, = 2 dB, = 2 dB).
5.7. Impact of on the Authentication Performance
We show in Figure 7 ROC variations under the settings of (SNR = 10 dB, = 128, L = 20, = 2 dB, = 2 dB, = 2 dB) at different correlation coefficients of path gain. From Figure 7, we can see that the authentication performance (, ) under = 0.9 outperforms that of the others, and the performance under = 0.7 is the poorest. This is because a larger means that the communication entities move slower. When is fixed, increases when increases. Moreover, the authentication performance (, ) under = 0.9 can satisfy the practical authentication requirements.
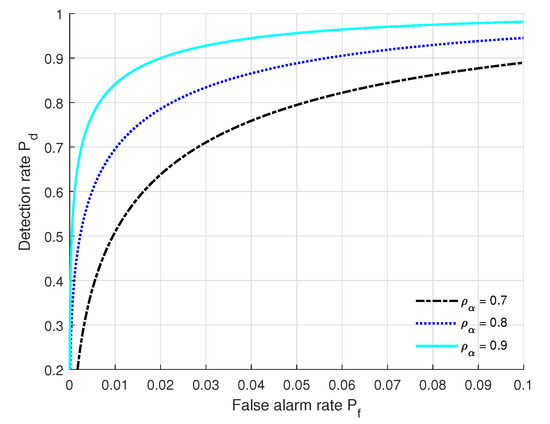
Figure 7.
ROC curves under different correlation coefficients of path gain with the settings of (SNR = 10 dB, = 128, L = 20, = 2 dB, = 2 dB, = 2 dB).
6. Conclusions
By utilizing multi-dimensional mmWave MIMO channel features, this paper developed a location verification scheme for mmWave MIMO communication systems. Furthermore, we modeled the three-dimensional mmWave channel features (i.e., AAoA, EAoA and path gain) and extracted these feature parameters through maximum-likelihood estimator. We also derived the analytical expressions for the typical performance metrics. Numerical results indicate that the proposed authentication scheme can benefit from using multi-dimensional mmWave channel features. The results in this paper reveal that the proposed scheme is general in nature and can be applied to more communication systems, and we expect the methodology developed in this paper to be valuable for devising new physical layer authentication schemes in other network scenarios.
Author Contributions
Conceptualization, Y.L. and P.Z.; methodology, Y.L.; validation, J.H., Y.L. and P.Z.; investigation, P.Z.; writing—original draft preparation, P.Z.; writing—review and editing, J.H.; funding acquisition, J.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Natural Science Foundation of China (NSFC) Grant (62272241), Japan Society for the Promotion of Science (JSPS) Grant (18H03235), and Nanjing University of Posts and Telecommunications Scientific Research Foundation Grant (NY221122).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Esfahani, A.; Mantas, G.; Matischek, R.; Saghezchi, F.B.; Rodriguez, J.; Bicaku, A.; Maksuti, S.; Tauber, M.G.; Schmittner, C.; Bastos, J. A lightweight authentication mmechanism for M2M communications in industrial IoT environment. IEEE Internet Things J. 2019, 6, 288–296. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.; Gupta, B.B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Wang, X.; Hao, P.; Hanzo, L. Physical-layer authentication for wireless security enhancement: Current challenges and future developments. IEEE Commun. Mag. 2016, 54, 152–158. [Google Scholar] [CrossRef]
- Xie, N.; Chen, J.; Huang, L. Physical-layer authentication using multiple channel-based features. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2356–2366. [Google Scholar] [CrossRef]
- Tang, J.; Xu, A.; Jiang, Y.; Zhang, Y.; Wen, H.; Zhang, T. MmWave MIMO physical layer authentication by using channel sparsity. In Proceedings of the 2020 IEEE International Conference on Artificial Intelligence and Information Systems (ICAIIS), Dalian, China, 20–22 March 2020; pp. 221–224. [Google Scholar]
- Maeng, S.J.; Yapici, Y.; Güvenç, I.; Dai, H.; Bhuyan, A. Power allocation for fingerprint-based PHY-Layer authentication with mmWave UAV networks. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
- Lord, S.F. 5G Millimeter-Wave Physical-Layer Authentication with Planar Reflectors. Ph.D. Thesis, Naval Postgraduate School, Monterey, CA, USA, 2019. [Google Scholar]
- Wang, N.; Li, W.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical layer authentication for 5G communications: Opportunities and road ahead. IEEE Netw. 2020, 34, 198–204. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-layer security of 5G wireless networks for IoT: Challenges and opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Wang, N.; Jiao, L.; Wang, P.; Dabaghchian, M.; Zeng, K. Efficient identity spoofing attack detection for IoT in mm-Wave and Massive MIMO 5G communication. In Proceedings of the IEEE Global Communications Conference, GLOBECOM 2018, Abu Dhabi, United Arab Emirates, 9–13 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Wang, N.; Jiao, L.; Alipour-Fanid, A.; Dabaghchian, M.; Zeng, K. Pilot contamination attack detection for NOMA in 5G mm-Wave massive MIMO networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1363–1378. [Google Scholar] [CrossRef]
- Wang, N.; Li, W.; Alipour-Fanid, A.; Jiao, L.; Dabaghchian, M.; Zeng, K. Pilot contamination attack detection for 5G mmWave grant-Free IoT networks. IEEE Trans. Inf. Forensics Secur. 2021, 16, 658–670. [Google Scholar] [CrossRef]
- Wang, N.; Jiao, L.; Wang, P.; Li, W.; Zeng, K. Exploiting beam features for sspoofing attack detection in mmWave 60-GHz IEEE 802.11ad networks. IEEE Trans. Wirel. Commun. 2021, 20, 3321–3335. [Google Scholar] [CrossRef]
- Wang, N.; Jiao, L.; Wang, P.; Li, W.; Zeng, K. Machine learning-based spoofing attack detection in MmWave 60GHz IEEE 802.11ad Networks. In Proceedings of the 39th IEEE Conference on Computer Communications, INFOCOM 2020, Toronto, ON, Canada, 6–9 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 2579–2588. [Google Scholar]
- Xiao, L.; Greenstein, L.J.; Mandayam, N.B.; Trappe, W. Channel-based spoofing detection in frequency-selective Rayleigh channels. IEEE Trans. Wirel. Commun. 2009, 8, 5948–5956. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Han, Z. PHY-Layer authentication with multiple landmarks with reduced overhead. IEEE Trans. Wirel. Commun. 2018, 17, 1676–1687. [Google Scholar] [CrossRef]
- Liu, F.J.; Wang, X. Physical layer authentication enhancement using two-dimensional channel quantization. IEEE Trans. Wirel. Commun. 2016, 15, 4171–4182. [Google Scholar] [CrossRef]
- Alkhateeb, A.; Ayach, O.E.; Leus, G., Jr.; Heath, R.W. Channel estimation and hybrid precoding for millimeter Wave cellular systems. IEEE J. Sel. Top. Signal Process. 2014, 8, 831–846. [Google Scholar] [CrossRef]
- Méndez-Rial, R.; Rusu, C.; Alkhateeb, A.; González Prelcic, N.; Heath, R.W., Jr. Channel estimation and hybrid combining for mmWave: Phase shifters or switches? In Proceedings of the 2015 Information Theory and Applications Workshop, ITA 2015, San Diego, CA, USA, 1–6 February 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 90–97. [Google Scholar]
- Singh, J.; Ramakrishna, S. On the feasibility of codebook-based beamforming in millimeter wave systems with multiple antenna arrays. IEEE Trans. Wirel. Commun. 2015, 14, 2670–2683. [Google Scholar] [CrossRef]
- Hemadeh, I.A.; Satyanarayana, K.; El-Hajjar, M.; Hanzo, L. Millimeter-wave communications: Physical channel models, design considerations, antenna constructions, and link-budget. IEEE Commun. Surv. Tutor. 2018, 20, 870–913. [Google Scholar] [CrossRef]
- Fan, D.; Gao, F.; Liu, Y.; Deng, Y.; Wang, G.; Zhong, Z.; Nallanathan, A. Angle domain channel estimation in hybrid millimeter wave massive MIMO systems. IEEE Trans. Wirel. Commun. 2018, 17, 8165–8179. [Google Scholar] [CrossRef]
- Buzzi, S.; D’Andrea, C. On clustered statistical MIMO millimeter wave channel simulation. arXiv 2016, arXiv:1604.00648. [Google Scholar]
- Ayach, O.E.; Rajagopal, S.; Abu-Surra, S.; Pi, Z.; Heath, R.W., Jr. Spatially sparse precoding in millimeter wave MIMO systems. IEEE Trans. Wirel. Commun. 2014, 13, 1499–1513. [Google Scholar] [CrossRef]
- Shen, W.; Dai, L.; Shim, B.; Wang, Z.; Heath, R.W., Jr. Channel feedback based on AoD-adaptive subspace codebook in FDD massive MIMO systems. IEEE Trans. Commun. 2018, 66, 5235–5248. [Google Scholar] [CrossRef]
- Xie, N.; Zhang, S. Blind authentication at the physical layer under time-varying fading channels. IEEE J. Sel. Areas Commun. 2018, 36, 1465–1479. [Google Scholar] [CrossRef]
- Médard, M. The effect upon channel capacity in wireless communications of perfect and imperfect knowledge of the channel. IEEE Trans. Inf. Theory 2000, 46, 933–946. [Google Scholar] [CrossRef]
- Kay, S.; Hall, P. Fundamentals of statistical signal processing, Volume II: Detection theory. Technometrics 1993, 37, 465–466. [Google Scholar]
- Zaidi, A.; Vandendorpe, L. Coding schemes for relay-assisted information embedding. IEEE Trans. Inf. Forensics Secur. 2009, 4, 70–85. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Goldsmith, A. Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).