Abstract
Wireless sensor networks (WSN) are widely used to provide users with convenient services such as health-care, and smart home. To provide convenient services, sensor nodes in WSN environments collect and send the sensing data to the gateway. However, it can suffer from serious security issues because susceptible messages are exchanged through an insecure channel. Therefore, secure authentication protocols are necessary to prevent security flaws in WSN. In 2020, Moghadam et al. suggested an efficient authentication and key agreement scheme in WSN. Unfortunately, we discover that Moghadam et al.’s scheme cannot prevent insider and session-specific random number leakage attacks. We also prove that Moghadam et al.’s scheme does not ensure perfect forward secrecy. To prevent security vulnerabilities of Moghadam et al.’s scheme, we propose a secure and lightweight mutual authentication protocol for WSNs (WSN-SLAP). WSN-SLAP has the resistance from various security drawbacks, and provides perfect forward secrecy and mutual authentication. We prove the security of WSN-SLAP by using Burrows-Abadi-Needham (BAN) logic, Real-or-Random (ROR) model, and Automated Verification of Internet Security Protocols and Applications (AVISPA) simulation. In addition, we evaluate the performance of WSN-SLAP compared with existing related protocols. We demonstrate that WSN-SLAP is more secure and suitable than previous protocols for WSN environments.
1. Introduction
As a rapid development of wireless communication technology, wireless sensor networks (WSN) can be applied to various environments such as smart grids, smart homes, agriculture, industrial internet of things (IoT), and health-care [1,2,3,4,5]. People can achieve a more bountiful life by utilizing WSN environments. Generally, WSN environments consist of sensor nodes, a gateway, and users, as shown in Figure 1. Sensor nodes detect and monitor their surrounding environment. Then, sensor nodes transmit the monitored data to the gateway. The gateway relays and analyzes the message between sensor nodes and users. The gateway also manages the private information of sensor nodes and users to provide secure services. Users can access the data collected by sensor nodes through the gateway.
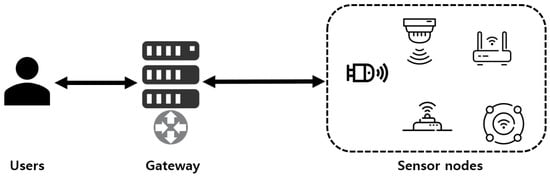
Figure 1.
System model in Wireless sensor networks (WSNs).
An example of the application environment in WSN is health-care services. Wearable sensors attached to a patient analyze the health condition of the patient. Then, these sensors send the collected data to the physician. However, these services can be exposed to various security attacks because each entity exchanges information through a public channel. If an adversary intercepts messages in WSN, the adversary can disguise as a legal user and send an incorrect message to the sensor node. Moreover, if an adversary registers to the gateway as a legal entity, the adversary can try to obtain other legal user’s sensitive information. Therefore, we need an authentication protocol that can provide secure services and prevent various attacks in WSN environments.
In 2020, Moghadam et al. [6] suggested an authentication and key agreement scheme for WSN environments utilizing Elliptic-Curve Diffie-Hellman (ECDH) [7]. They demonstrated that their scheme is efficient and secure against various security attacks such as replay, password guessing, stolen verifier, and man-in-the-middle (MITM) attacks. However, we discover that Moghadam et al.’s scheme does not provide security against insiders, and session-specific random number leakage attacks. We also prove that Moghadam et al.’s scheme does not support perfect forward secrecy. Moreover, each entity performs Elliptic Curve Cryptography (ECC) multiplication operations to compute a session key in Moghadam et al.’s scheme. However, ECC requires heavy computational costs. Since sensor nodes have low computation capabilities and storage resources in a WSN environment, we cannot ensure real-time communications using ECC in WSN environments. Therefore, using Moghadam et al.’s scheme makes it difficult to provide efficient services. To improve security vulnerabilities and reduce the computational cost of Moghadam et al.’s scheme, we propose a secure and lightweight mutual authentication protocol (WSN-SLAP) considering security and efficiency features using hash functions and XOR operations.
1.1. Contributions
Our paper’s contributions are as below.
- We analyze and prove the security vulnerabilities of Moghadam et al.’s scheme. Then, we propose WSN-SLAP to resolve security vulnerabilities of Moghadam et al.’s scheme.
- We demonstrate the mutual authentication of WSN-SLAP using Burrows–Abadi–Needham (BAN) logic [8].
- We proof the session key security of WSN-SLAP by using the Real-or-Random (ROR) model [9]
- We use Automated Verification of Internet Security Protocols and Applications (AVISPA) [10,11] to prove security features of WSN-SLAP against replay and MITM attacks.
- We analyze the communication cost, the computational cost, and security properties of WSN-SLAP compared with related schemes.
1.2. Adversary Model
WSN-SLAP uses a well-known adversary model called the Dolev–Yao (DY) model [12]. Through the DY model, the adversary can eavesdrop, delete, intercept, and insert exchanged messages through a public channel. Moreover, the adversary can get exposed session-specific ephemeral parameters, which is based on the Canetti–Krawczyk (CK) adversary model [13]. The adversary can perform various security attacks with the DY model and the CK model. The detailed assumptions of the adversary model are defined in the following manner.
- If an adversary registers as a legal user to the gateway, the adversary can authenticate with other entities.
- An adversary can obtain a user’s lost/stolen smart card. The adversary can perform the power analysis attack [14] to get stored parameters of the smart card.
- An adversary can attempt various attacks such as replay, sensor node capture, stolen verifier, and off-line password guessing attacks.
1.3. Organization
In Section 2, we describe related works for WSN environments. Then, we revisit Moghadam et al.’s scheme in Section 3 and prove the security flaws of Moghadam et al.’s scheme in Section 4. Section 5 illustrates WSN-SLAP. In Section 6, we perform informal and formal security analyses of WSN-SLAP by using BAN logic, the ROR model, and AVISPA simulation tool. In Section 7, we analyze WSN-SLAP’s performance compared with the existing related protocols. In Section 8, we conclude and summarize our paper.
2. Related Works
In the past few decades, numerous password-based authentication schemes have been proposed to provide security and efficiency in WSN environments [15,16,17,18,19]. In 1981, Lamport [20] suggested an authentication mechanism based on a password. Lamport used one-way hash functions to encode the password and stored the hashed password inside the system. In 2006, Wong et al. [21] suggested a password-based authentication scheme in WSN environments. Unfortunately, Tseng et al. [22] proved that Wong et al.’s scheme is insecure against forgery and replay attacks. Tseng et al. demonstrated a dynamic user authentication scheme to improve security vulnerabilities of Wong et al. [21]’s scheme. However, these schemes [20,21,22] can suffer from on/off-line password guessing attacks because they only used the password as a factor to login and authenticate with other entities.
In the last few decades, two-factor-based authentication schemes [23,24,25] have been presented using hash functions and XOR operations to improve single factor’s security weaknesses. In 2009, Das et al. [23] proposed a two-factor authentication scheme based on a smart card in WSNs. They demonstrated that their scheme can prevent various attacks such as replay, stolen verifier, and off-line password guessing attacks. However, Khan et al. [24] analyzed that Das et al. [23]’s scheme is vulnerable to privileged insider attack. He et al. [25] found that Das et al. [23]’s scheme is vulnerable to insider and impersonation attacks. To improve the security vulnerabilities of Das et al.’s scheme, He et al. [25] suggested an enhanced two-factor user authentication scheme for WSNs. However, these schemes [23,24,25] can suffer from various attacks such as thoe using stolen smart cards and mobile devices.
To resolve the security flaws associated with two-factor-based authentication schemes and improve the security level in WSN environments, researchers have proposed many ECC-based authentication schemes [26,27,28,29,30,31]. In 2011, Yeh et al. [26] proposed an authentication protocol for WSN environments using ECC. Yeh et al.’s scheme used a smart card and ECC to prevent various security issues such as insider, and masquerade attacks. Choi et al. [27] suggested an ECC-based user authentication scheme for WSN. However, Wu et al. [28] pointed out that Choi et al.’s protocol does not provide security against forgery attack. Nam et al. [29] suggested a secure authentication protocol for WSN based on ECC. Nam et al.’s scheme provides a secure protocol based on an Elliptic Curve Computation Diffie-Hellman (ECCDH) problem. In 2016, Jiang et al. [30] proposed an ECC-based authentication scheme. Jiang et al.’s scheme provides secure communications and untraceability in WSN environments. In 2017, Wu et al. [31] suggested a user authentication scheme using ECC. Wu et al.’s scheme can preserve user privacy in WSN environments. However, sensor nodes in WSN have low computing power and resources. Therefore, it is difficult to provide efficiency in WSN environments using these schemes [26,27,28,29,30,31] because ECC requires large computational resources.
In 2020, Moghadm et al. [6] suggested an authentication and key agreement scheme using ECDH. They asserted that their scheme provides resistance against various attacks such as replay, MITM, off-line password guessing, and stolen verifier attacks. However, we discover that Moghadam et al.’s scheme is vulnerable to insider, session-specific random number leakage attacks and perfect forward secrecy. Moreover, Moghadam et al.’s scheme suffers from heavy computational cost because it involves an ECC-based computation. Therefore, we propose WSN-SLAP, which has resistance to various security problems.
3. Review of Moghadam et al.’s Scheme
Moghadam et al. proposed an authentication scheme based on ECDH in WSN [6]. Moghadam et al.’s scheme is composed of sensor node registration, user registration, and login and authentication phases. Table 1 indicates the notations of Moghadam et al.’s scheme and WSN-SLAP.

Table 1.
Notations.
3.1. Sensor Node Registration Phase
In this phase, a sensor node sends its identity to the gateway . Then, computes a shared secret parameter between and . In Figure 2, we show the sensor node registration phase and the details are as follows.
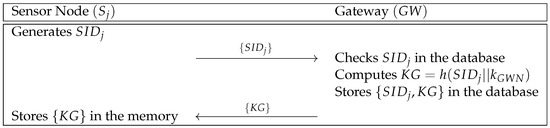
Figure 2.
Sensor node registration phase of Moghadam et al.’s scheme.
- Step 1:
- generates its identity , and sends it to over a secure channel.
- Step 2:
- receives and checks the validity of . After that, computes , and stores in its secure database, where is the master key of . Finally, sends to .
- Step 3:
- receives and stores in its database.
3.2. User Registration Phase
A user registers to the gateway by sending an identity and a masked password value. Then, issues a smart card to . In Figure 3, we describe the user registration phase and the details are shown as below.
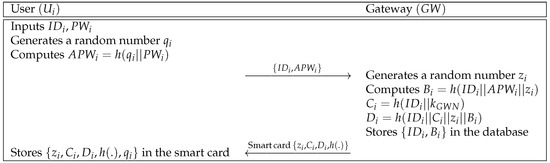
Figure 3.
User registration phase of Moghadam et al.’s scheme.
- Step 1:
- inputs the identity and the password , and then generates a random number . After that, computes and sends the registration request message to the gateway over a secure channel.
- Step 2:
- receives from , and then generates a random number . After that, computes , and . Finally, stores in a smart card and issues it to over a secure channel.
- Step 3:
- receives the smart card, and stores in the smart card. Finally, parameters are stored in the smart card.
3.3. Login and Authentication Phase
After the registration phase, the user authenticates the gateway . In Figure 4, we describe the login and authentication phase and the detailed steps of the phase are shown as below.

Figure 4.
Login and authentication phase of Moghadam et al.’s scheme.
- Step 1:
- After inserting the smart card, inputs the identity and the password . The smart card computes and verifies . If the verification process is successful, the smart card generates a random nonce and timestamp . With the public key of the gateway X, the smart card computes , and . At last, the smart card sends to through a public channel.
- Step 2:
- receives from , and selects a timestamp and checks the validity of . If the timestamp is vaild, computes and verifies . If the equality holds, generates a random nonce and computes . At last, sends to the sensor node over a public channel.
- Step 3:
- After reception of the message from , selects a timestamp and checks the validity of . Then, computes and verifies . If the verification is legitimate, generates a random nonce , and computes . At last, sends to .
- Step 4:
- After receiving from , selects a timestamp and checks the validity of . Then, computes and verifies . If it is equal, computes and sends to .
- Step 5:
- receives the message , and selects a timestamp and checks the validity of . At last, computes and verifies . If it is equal, the key agreement is successful.
4. Cryptanalysis of Moghadam et al.’s Scheme
In this section, we demonstrate the security vulnerabilities of Moghadam et al.’s scheme [6] such as insider, and session-specific random number leakage attacks. Moghadam et al.’s scheme also does not achieve perfect forward secrecy.
4.1. Insider Attack
If an adversary ordinary registers as a legal user , can authenticate with the gateway and the sensor node by exchanging messages. With this information, can compute another legal user ’s session key. The details are shown as below.
- Step 1:
- inserts the smart card, and inputs the identity and the password of . Then, the smart card checks the validity of , and sends a login request message to . After authenticating , sends to . Upon reception of the message , computes a session key . Then, sends the authentication response message to . computes the session key and sends to . computes the session key and obtains communication messages during the login and authentication phase.
- Step 2:
- After obtaining the message , computes , where is the secret key of using ECC and is a shared secret key between and .
- Step 3:
- intercepts a message from the message of another legal user . Since knows , it can compute , where is the secret key of .
- Step 4:
- obtains the message and decrypts using the secret key of . Then, can obtain the random secret nonce of sensor node. can compute by utilizing the message . Finally, compute the session key .
Therefore, Moghadam et al.’s scheme cannot prevent insider attacks.
4.2. Perfect Forward Secrecy
Moghadam et al. demonstrated that their scheme can ensure the security feature of perfect forward secrecy. However, if the adversary gets the master key of the gateway , the adversary can compute the legal user ’s session key . The details are shown in following steps.
- Step 1:
- If obtains the master key , can compute the secret key of by utilizing the login request message .
- Step 2:
- When intercepts the message , can decrypt because is the symmetric key between the and the gateway .
- Step 3:
- After obtains the message , can get and . At last, computes ’s session key .
Consequently, Moghadam et al.’s scheme does not ensure perfect forward secrecy.
4.3. Session-Specific Random Number Leakage Attack
Suppose that a random nonce is disclosed to an adversary . Using the public key X of the gateway , can calculate . Then, can compute the session key . The details are described as below.
- Step 1:
- After getting the parameter , captures the message . Then, decrypts by using the symmetric key and obtains .
- Step 2:
- eavesdrops the message of the sensor node . Finally, computes the session key using in the message of .
Therefore, Moghadam et al.’s scheme cannot prevent session-specific random number leakage attacks.
5. Proposed Scheme
We propose a secure and lightweight mutual authentication protocol for WSN environments to resolve security weaknesses of Moghadam et al.’s scheme [6]. To consider the resource-limited sensor nodes, WSN-SLAP uses hash functions and XOR operations that generate low computational overheads. WSN-SLAP is composed of sensor node registration, user registration, login and authentication, password update, and sensor node addition phases.
5.1. Sensor Node Registration Phase
If a sensor node sends a registration request message, the gateway computes a secret parameter for the sensor node. Then, stores the parameter. We show the sensor node registration phase in Figure 5 and the details are presented as below.
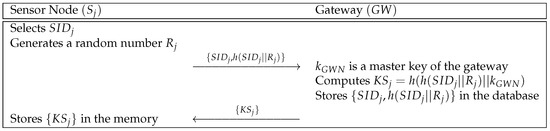
Figure 5.
Sensor node registration phase of a secure and lightweight mutual authentication protocol (WSN-SLAP).
- Step 1:
- selects its identity and generates a random number . Then, computes and sends to over a secure channel.
- Step 2:
- receives and computes , where is the master key of . stores in the secure database and sends to .
- Step 3:
- At last, stores in its memory.
5.2. User Registration Phase
A user sends a registration request message to the gateway . Then, computes secret parameters and issues a smart card to the user. In Figure 6, we describe the user registration phase and the detailed steps are shown as below.
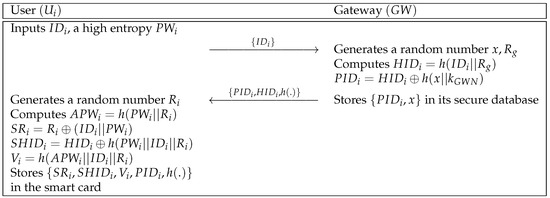
Figure 6.
User registration phase of WSN-SLAP.
- Step 1:
- inputs an identity and a high entropy password . After that, transmits to via a secure channel.
- Step 2:
- generates random numbers x and , and computes . stores in its secure database and sends the message to .
- Step 3:
- generates a random number . With , computes , and . Finally, stores in the smart card.
5.3. Login and Authentication Phase
To access information of the sensor , the user sends a login request message to the gateway . In Figure 7, we describe the login and authentication phase and the details are presented below.

Figure 7.
Login and authentication phase of WSN-SLAP.
- Step 1:
- After inserting the smart card, inputs the identity and the password . The smart card computes and . Then, the smart card checks the validity of compared with stored in the smart card. If the validity is confirmed, the smart card generates a random nonce , and computes and . At last, sends to over a public channel.
- Step 2:
- When receives from , retrieves and the shared secret value x from ’s database. Then, computes and , and checks the validity of compared with . If the validity is confirmed, retrieves and from ’s database. computes and . At last, sends to over a public channel.
- Step 3:
- If receives , computes and checks the validity of compared with the parameter . If the validity is confirmed, computes , where is a session key. Finally, sends to .
- Step 4:
- After receiving the message from , computes and verifies the equality of and . If the verification is successful, generates a random nonce and computes and . At last, sends to and updates to if the key agreement is successful.
- Step 5:
- When receives the message from , computes and checks the validity of compared with . If the validity is confirmed, replaces to in the smart card.
5.4. Password Update Phase
In WSN-SLAP, users can easily change their own password. The details are shown as below.
- Step 1:
- After inserting the smart card, The user inputs the identity and the password . The smart card computes and verifies the equality of and . If the verification is successful, the smart card requests a new password to .
- Step 2:
- inputs a new password . The smart card selects a random number and computes . Finally, the smart card stores .
5.5. Sensor Node Addition Phase
To add a new sensor node to WSN-SLAP, registers to the gateway . The detailed steps are described as follows.
- Step 1:
- selects its identity . Then, generates a random number . With and , computes and sends to through a secure channel.
- Step 2:
- After receiving from , computes and stores in the database of . Finally, sends to .
- Step 3:
- receives the message from and stores in the memory of .
6. Security Analysis
WSN-SLAP not only considers lightweight features using hash functions and XOR operations, but also ensures a higher security level compared with related schemes. To evaluate the security of WSN-SLAP, we perform informal security analysis and formal security analysis such as BAN logic, ROR model, and AVISPA simulation tool. We show that WSN-SLAP prevents a variety of attacks using informal analysis. We demonstrate the mutual authentication of WSN-SLAP using BAN logic and also prove the session key security of WSN-SLAP by using the ROR model. We use the AVISPA simulation tool to prove security features of WSN-SLAP against replay and MITM attacks.
6.1. Informal Security Analysis
WSN-SLAP provides security against various attacks such as insider, stolen smart card, replay, sensor node capture, off-line password guessing, privileged insider, stolen verifier, and MITM attacks. Furthermore, WSN-SLAP ensures perfect forward secrecy and mutual authentication.
6.1.1. Insider Attack
If an adversary registers to the gateway as a legal user, can authenticate to and the sensor node . captures messages and . Then, computes and . To compromise other legal user’s sessions, must need to compute the session key. Since hash functions mask the random nonce and the user’s secret parameter such as , cannot compute the shared secret parameter between and . Therefore, WSN-SLAP is secure against the insider attacks.
6.1.2. Stolen Smart Card Attack
Suppose that an adversary captures the legal user ’s smart card. Then, uses the power analysis attack to extract stored parameters in the smart card. With ’s smart card parameters, tries to authenticate with the gateway and the sensor node . However, cannot compute the login request message because is masked by . To calculate , needs to guess and at the same time. Since these tasks are computationally infeasible task, it is hard to obtain both and . For these reasons, WSN-SLAP is secure against stolen smart card attacks.
6.1.3. Replay Attack
If an adversary intercepts messages and from a legal user , tries to authenticate with the gateway by sending intercepted messages at other sessions. In WSN-SLAP, and the sensor node check the freshness of random nonces and . Thus, WSN-SLAP can provide security against replay attacks.
6.1.4. Sensor Node Capture Attack
We assume that an adversary captures a specific sensor node and obtains parameters from the ’s memory by using the power analysis attack. Then, can authenticate with gateway and user . However, cannot threat other sensor nodes. Since the shared secret parameter , can only authenticate with the specific sensor node . cannot calculate any information about other sensor nodes. Therefore, WSN-SLAP is secure against sensor node capture attacks.
6.1.5. Off-Line Password Guessing Attack
According to Section 1.2, an adversary can guess a legal user ’s password . can also extract stored parameters from ’s legitimate smart card. Then, tries to impersonate as . However, cannot compute to obtain without knowing the identity . Therefore, cannot compute the legal message . Accordingly, WSN-SLAP has resistance to off-line password-guessing attacks.
6.1.6. Privileged Insider Attack
If a privileged insider adversary intercepts a legal user ’s registration message , tries to compute ’s session key by using messages in Section 5.3. However, cannot compute the session key of . To compute , has to calculate which is the shared secret parameter between and the gateway . However, cannot compute from the login request message without ’s password and the random number . Consequently, WSN-SLAP ensures security against privileged insider attacks.
6.1.7. Stolen Verifier Attack
Assuming that an adversary steals the gateway ’s verification table including and . However, cannot compute the session key of the legal user with these parameters. To compute the session key , must compute by using . Since the parameter is ’s master key, cannot compute . Therefore, WSN-SLAP has resistance to stolen verifier attacks.
6.1.8. MITM Attack
During the login and authentication phase, an adversary intercepts and tries to modify the login request message . However, the gateway can easily detect the modified message by using the verification table. In addition, it is impossible to modify all messages because they include random parameters. Therefore, WSN-SLAP can prevent MITM attacks.
6.1.9. Session-Specific Random Number Leakage Attack
Assume that an adversary obtains all random parameters , and . Then, tries to compute the session key . However, it is impossible to calculate the session key without knowing . is masked with the secret key x and the master key during the session. Accordingly, WSN-SLAP is secure against session-specific random number leakage attacks.
6.1.10. Perfect Forward Secrecy
We suppose that an adversary obtains ’s master key . Then, tries to compute the session key of the user . However, the master key is utilized, i.e., and . Therefore, needs the shared secret parameter x or to analyze the secret parameter. For this reason, WSN-SLAP provides perfect forward secrecy.
6.1.11. Mutual Authentication
To authenticate with each other, each participant of WSN-SLAP performs verification processes. The gateway checks the validity of and , the sensor node verifies , and the checks . If the whole verification process is successful, we can conclude that each participant is authenticated with each other. Therefore, WSN-SLAP guarantees mutual authentication.
6.2. BAN Logic
In this section, we prove mutual authentication of WSN-SLAP using BAN logic analysis [8]. BAN logic has been widely used to analyze the mutual authentication of various authentication schemes [32,33]. In WSN-SLAP, the participants authenticate with each other to establish a session key among U, , and . Table 2 presents the basic notations of the BAN logic used in this proof.

Table 2.
The basic notations.
6.2.1. Rules
The logical rules of the BAN logic are described as below.
- 1.
- Message meaning rule (MMR):
- 2.
- Nonce verification rule (NVR):
- 3.
- Jurisdiction rule (JR):
- 4.
- Belief rule (BR):
- 5.
- Freshness rule (FR):
6.2.2. Goals
In WSN-SLAP, the basic goals of the BAN logic are that each principal establishes a session key and achieves mutual authentication. The goals for proving mutual authentication of WSN-SLAP are defined as follows:
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Goal 5:
- Goal 6:
- Goal 7:
- Goal 8:
6.2.3. Idealized Forms
In WSN-SLAP, the authentication request and response messages , , , and are transmitted through a public channel. We will transmit these messages into the idealized form and omit other messages because they cannot efficiently provide the logical properties of BAN logic. WSN-SLAP’s idealized form messages are shown as below:
- :
- :
- :
- :
6.2.4. Assumptions
After the registration phase, each principal believes that it has secret keys which are shared among each other. The principal also trusts that random numbers and pseudo identity are fresh. Moreover, the principal believes that a legal principal can control the entitled components and values. The assumptions of the BAN logic in WSN-SLAP are as below:
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
6.2.5. BAN Logic Proof
We conduct the BAN logic analysis of WSN-SLAP as follows:
- Step 1:
- can be obtained from .:
- Step 2:
- can be induced by applying the MMR using and .:
- Step 3:
- can be induced by applying the FR using and .:
- Step 4:
- can be induced by applying the NVR using and .:
- Step 5:
- is can be induced by and the BR.:
- Step 6:
- is obtained from .:
- Step 7:
- is can be induced by applying the MMR using and .
- Step 8:
- is can be induced by applying the FR using and .
- Step 9:
- is can be induced by applying the NVR using and .
- Step 10:
- is obtained from .
- Step 11:
- can be induced by applying the MMR using and .:
- Step 12:
- can be induced by applying the NVR using and .
- Step 13:
- and can be induced by , and . and can compute the session key .(Goal 8)(Goal 6)
- Step 14:
- and can be induced by applying the JR using and , and and , respectively.(Goal 7)(Goal 5)
- Step 15:
- is obtained from .:
- Step 16:
- can be induced by , and the MMR.:
- Step 17:
- can be induced by applying the FR using and .:
- Step 18:
- can be induced by , and the NVR.:
- Step 19:
- and can be induced by , . U and can compute the session key(Goal 2)(Goal 4)
- Step 20:
- and can be induced by applying the JR using and , , and , respectively.(Goal 1)(Goal 3)
6.3. ROR Model
This section proves the security of the session key of WSN-SLAP by using the well-known Real-Or-Random (ROR) model [9]. In WSN-SLAP, there are three participants. is a user, is a gateway, and is a sensor node. In the ROR model, the network is under an adversary who can eavesdrop, capture, insert, and delete messages. With these abilities, performs various attacks using , and queries.
- : This query is a passive attack that can eavesdrop the legal entity’s message.
- : This query means obtains stored parameters from the user’s smart card.
- : This query means reveals the session key .
- : This query is an active attack that sends a message to receive a response message.
- : An adversary obtains a flipped unbiased coin before the game starts. If obtains , it means the session key is fresh. If obtains , it means the session key is not fresh. Otherwise, obtains a value. To ensure the security of the session key, it is necessary that cannot distinguish the result value between a random number and the session key.
Security Proof
Theorem 1.
Let attempt to obtain the session key of WSN-SLAP in polynomial time as follows. is the probability of the session key being broken by . , , and mean the number of hash queries, the range space of the hash function, and the number of send queries, respectively. and are the Zipf’s parameters [34].
We follow the proof according to the method of [35,36]. We perform four games , where . is the event that can guess a correct bit c in the , and is the probability of . We can perform as follows with these parameters.
- -
- : This game describes a real attack of in WSN-SLAP under the ROR model. The random bit c needs to be selected before starting the game. Therefore, we can derive as follows.
- -
- : In the , obtains each entity’s messages , , , and using query. Then, performs and queries to obtain the session key . Since , has to get random nonces , , and . In addition, needs the user’s masked identity . For these reasons, cannot calculate . This means and are indistinguishable. Therefore, we can get the following equivalent.
- -
- : In this game, performs query, which is an active attack. utilizes , , , and to get the session key . Parameters , , , and are masked by query. In addition, parameters , , , , , , , and contain random nonces , , and . By using random nonces, we can prevent collision from other sessions. According to the birthday paradox [37], we can get the following inequation.
- -
- : In the , executes query and obtains smart card’s stored parameters by using the power analysis attack, where , and . To obtain and , needs the identity and the password . Therefore, cannot distinguish with and if guessing is computationally infeasible task. Then, we can obtain the result by using Zipf’s law [34].Finally, gets the guessed bit c because games are done.We get the following result utilizing the triangular inequality.By multiplying (8) by 2, we get the following result.Therefore, we prove
6.4. AVISPA Simulation
In this section, we analyze security features of WSN-SLAP by using AVISPA [10,11]. AVISPA is a formal security verification tool that detects MITM and replay attacks against the authentication protocol.
AVISPA uses the High-Level Protocols Specification Language (HLPSL). After receiving a protocol written in HLPSL, the translator converts the HLPSL-based protocol to an intermediate format (IF). Then, the translator inputs the IF to four back-ends, which are Constraint Logic-based Attack Searcher (CL-AtSe), Tree Automata based on Automatic Approximations for Analysis of Security Protocol (TA4SP), SAT-based Model-Checker (SATMC), and On the fly Model-Checker (OFMC), respectively. Consequently, the IF is converted to an output format (OF). If the summary of OF is SAFE, it means the protocol has resistance to replay and MITM attacks.
Specifically, OFMC back-end can utilize XOR operations. Therefore, we use this back-end in our paper.
6.4.1. HLPSL Specifications
In HLPSL, WSN-SLAP consists of users , gateway , and sensor nodes . These entities are written as . There are also two named and , which contain security goals. Figure 8 indicates goals and the of and of WSN-SLAP.
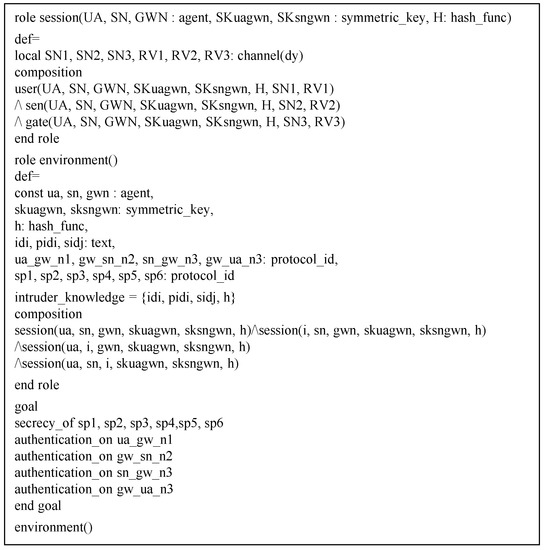
Figure 8.
Role of session, environment and goal.
Figure 9 shows the whole process of the user . In state 1, the user registers to . To start the session, receives the start message. Then, sends a registration request message to the gateway through a secure channel. In state 2, receives a smart card from and stores in the smart card. In the login and authentication phase, sends to via a public channel. The function indicates the freshness of generated by . In State 3, receives from . Then, authenticates with using in .

Figure 9.
Role of user.
6.4.2. Simulation Result
If the protocol’s result summary is SAFE in OFMC simulation, the protocol has resistance to replay and MITM attacks. The result of WSN-SLAP’s AVISPA simulation tool using OFMC back-end is shown in Figure 10. Thus, WSN-SLAP can prevent replay and MITM attacks.
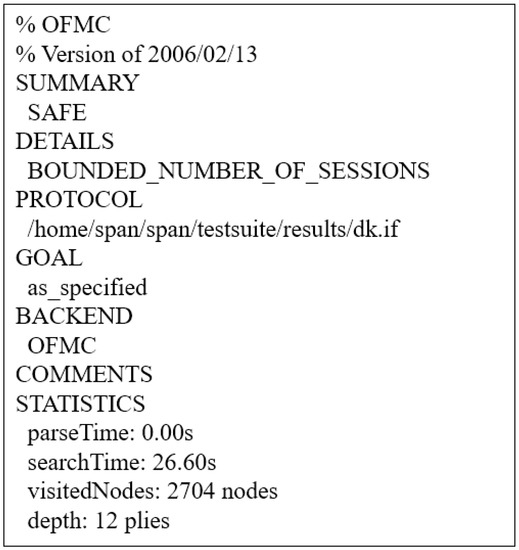
Figure 10.
Result of the Automated Verification of Internet Security Protocols and Applications (AVISPA) simulation.
7. Performance Analysis
In this section, we estimate computational costs, communication costs, and security properties of WSN-SLAP compared with existing related schemes [6,27,28,31].
7.1. Computational Costs
We analyze WSN-SLAP’s computational cost compared with the performance of the related schemes [6,27,28,31]. According to [6,38], the execution time of each operation is acquired on a computer with a four-core 3.2 GHz CPU, and 8 GB memory. We estimate that , , and are the execution time of the hash function (≈0.00032 s), ECC point multiplication (≈0.0171 s), and symmetric encryption/decryption (≈0.0056 s), respectively. We do not consider the execution time of the XOR operation because it is negligible. Table 3 indicates the result for computational costs. Accordingly, WSN-SLAP has a more efficient computational cost than related schemes [6,27,28,31].

Table 3.
Computational costs comparison.
7.2. Communication Costs
We evaluate the communication cost of WSN-SLAP compared with related schemes [6,27,28,31] in this section. According to [6], we define that the user identity, sensor node identity, random number, timestamp, SHA-1 hash digest, and ECC point are 128, 16, 128, 32, 160 and 320 bits, respectively. In WSN-SLAP, the login request message requires bits), and the transmitted authentication messages , , and require bits), bits), and bits), respectively. Consequently, total communication costs of WSL-SLAP and related schemes [6,27,28,31] are as shown in Table 4. Therefore, WSN-SLAP provides a more efficient communication cost than related schemes do [6,27,28,31].

Table 4.
Communication costs comparison.
7.3. Security Properties
In Table 5, we present the security properties of WSN-SLAP with related schemes [6,27,28,31]. We show that existing protocols [6,27,28,31] suffer from various attacks, including insider, stolen smart card, and session-specific random number leakage attacks. Therefore, WSN-SLAP provides better functionality and security features compared with those of related schemes [6,27,28,31].

Table 5.
Security properties.
8. Conclusions
In this paper, we discovered that Moghadam et al.’s scheme has vulnerabilities against insider, and session-specific random number leakage attacks. We also proved that Moghadam et al.’s scheme does not guarantee perfect forward secrecy. To resolve the security weaknesses of Moghadam et al.’s scheme, we proposed a secure and lightweight mutual authentication protocol for WSN environments. WSN-SLAP has resistance to various attacks, including insider, stolen smart card, off-line password guessing, stolen verifier, and session-specific random number leakage attacks. We demonstrated that WSN-SLAP provides perfect forward secrecy and mutual authentication. We proved the security of WSN-SLAP using formal security analyses, which are AVISPA, BAN logic, and ROR model. Moreover, WSN-SLAP has lightweight computational and communication costs because it involves XOR operations and hash functions. Therefore, the proposed WSN-SLAP provides more secure and efficient communication services compared with existing related protocols and is suitable for WSN environments. In future work, we will implement a whole network and secure protocol to design a new scheme that is practical for use in WSN.
Author Contributions
Conceptualization, D.K.K.; Formal analysis, S.J.Y., J.Y.L. and S.H.S.; Investigation, S.J.Y. and Y.H.P.; Methodology, D.K.K.; Software, J.Y.L.; Supervision, Y.H.P.; Validation, J.Y.L. and S.H.S.; Writing—original draft, D.K.K.; Writing—review & editing, S.J.Y., S.H.S. and Y.H.P. All the authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by the Basic Science Research Program through the National Research Foundation of Korea(NRF) funded by the Ministry of Education under Grant 2020R1I1A3058605, and in part by the BK21 FOUR project funded by the Ministry of Education, Korea under Grant 4199990113966.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mandal, S.; Bera, B.; Sutrala, A.K.; Das, A.K.; Choo, K.K.R.; Park, Y. Certificateless-signcryption-based three-factor user access control scheme for IoT environment. IEEE Internet Things J. 2020, 7, 3184–3197. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. SLUA-WSN: Secure and lightweight three-factor-based user authentication protocol for wireless sensor networks. Sensors 2020, 20, 4143. [Google Scholar] [CrossRef] [PubMed]
- Ghahramani, M.; Javidan, R.; Shojafar, M.; Taheri, R.; Alazab, M.; Tafazolli, R. RSS: An energy-efficient approach for securing IoT service protocols against the DoS attack. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably secure and lightweight authentication and key agreement scheme without verification table in medical internet of things. IEEE Access 2020, 8, 119387–119404. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [PubMed]
- Moghadam, M.F.; Nikooghadam, M.; Al Jabban, M.A.B.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An efficient authentication and key agreement scheme based on ECDH for wireless sensor network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Coron, J.S. Resistance against differential power analysis for elliptic curve cryptosystems. In Proceedings of the 1st International Workshop on Cryptographic Hardware and Embedded Systems, Worcester, MA, USA, 12–13 August 1999; pp. 292–302. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Lecture Notes in Computer Science (LNCS), Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84. [Google Scholar]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 4 December 2020).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 4 December 2020).
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques—Advances in Cryptology (EUROCRYPT’02), Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Fu, X.; Fortino, G.; Li, W.; Pace, P.; Yang, Y. WSNs-assisted opportunistic network for low-latency message forwarding in sparse settings. Future Gener. Comput. Syst. 2019, 91, 223–237. [Google Scholar] [CrossRef]
- Fu, X.; Fortino, G.; Pace, P.; Aloi, G.; Li, W. Environment-fusion multipath routing protocol for wireless sensor networks. Inf. Fusion 2020, 53, 4–19. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Kim, M.; Park, Y.; Das, A.K. On the design of secure and efficient three-factor authentication protocol using honey list for wireless sensor networks. IEEE Access 2020, 8, 107046–107062. [Google Scholar] [CrossRef]
- Fu, X.; Pace, P.; Aloi, G.; Yang, L.; Fortino, G. Topology optimization against cascading failures on wireless sensor networks using a memetic algorithm. Comput. Netw. 2020, 177, 107327. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC), Taichung, Taiwan, 5–7 June 2006; pp. 1–8. [Google Scholar]
- Tseng, H.R.; Jan, R.H.; Yang, W. An improved dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE Globecom, Washington, DC, USA, 26–30 November 2007; pp. 986–990. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of ‘two-factor user authentication in wireless sensor networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Netw. Appl. 2017, 10, 16–30. [Google Scholar] [CrossRef]
- Nam, J.; Kim, M.; Paik, J.; Lee, Y.; Won, D. A provably-secure ECC-based authentication scheme for wireless sensor networks. Sensors 2014, 14, 21023–21044. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on Internet of Things security. J. Ambient. Intell. Humaniz. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Ghahramani, M.; Javidan, R.; Shojafar, M. A secure biometric-based authentication protocol for global mobility networks in smart cities. J. Supercomput. 2020, 76, 8729–8755. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, K.; Das, A.K.; Park, Y. IoV-SMAP: Secure and efficient message authentication protocol for IoV in smart city environment. IEEE Access 2020, 8, 167875–167886. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Lee, C.C.; Chen, C.T.; Wu, P.H.; Chen, T.Y. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–55. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).