An Improved Proxy Re-Encryption Scheme for IoT-Based Data Outsourcing Services in Clouds
Abstract
1. Introduction
- (i)
- Device-to-Device Communication: Two or more devices could communicate with each other without relying on middleware servers. These devices can work in various networks such as Bluetooth, Z-Wave, and ZigBee, etc.
- (ii)
- Device-to-Cloud Communication: IoT devices could directly connect to cloud service providers for exchanging information and controlling flow messages. Such a communication mode usually utilizes existing communication mechanisms like Ethernet or WiFi.
- (iii)
- Device-to-Gateway Communication: IoT devices connect to the gateway to obtain cloud services. Specifically, application software of the gateway will provide the security and functionality for data and protocol conversion.
- (iv)
- Back-End Data-Sharing Model: It allows users to combine the data output of other sources and analyze the intelligent object data of cloud services. It thus could be regarded as an extension of device-to-cloud communications.
Contributions
- (i)
- The proposed PRE scheme is bidirectional and supports the functionality of multi-hop.
- (ii)
- Our scheme is provably secure in the random oracle model using the Bilinear Inverse Diffie–Hellman assumption.
- (iii)
- The ciphertext size of our scheme is constant, i.e., it is independent of the number of IoT nodes.
- (iv)
- The re-encryption process only takes one exponentiation computation.
- (v)
- The proposed PRE scheme earns more computational savings compared with a related work presented by Kim and Lee.
2. Research Backgrounds
2.1. Related Works
2.2. Preliminaries
- (i)
- Bilinearity:Given two group elements in G1, say g1 and g2, and two integers in Zq, say a and b, the value e(g1a, g2b) is equivalent to the value e(g1, g2)ab.
- (ii)
- Non-degeneracy:There are two group elements in G1, say g1 and g2 such that e(g1, g2) ≠ 1.
- (iii)
- Computability:Given two group elements in G1, say g1 and g2, there exists an efficient algorithm which could derive the value e(g1, g2).
- (i)
- Bilinear Diffie–Hellman Problem (BDHP)Given elements g, ga, gb, gc ∈ G1 for three positive integers a, b, c ∈ Zq*, the Bilinear Diffie–Hellman problem is to derive the G2 element e(g, g)abc.
- (ii)
- Assumption of Bilinear Diffie–Hellman (BDH)The assumption of BDH states that the probability for any probabilistic polynomial time algorithm to successfully break the BDHP is negligible.
- (iii)
- Bilinear Inverse Diffie–Hellman Problem (BIDHP)Given elements g, ga, gb ∈ G1 for some positive integers a, b ∈ Zq*, the BIDHP is to compute the value e(g, g)a−1b∈ G2.
- (iv)
- Assumption of Bilinear Inverse Diffie–Hellman (BIDH)The assumption of BIDH states that the probability for any probabilistic polynomial time algorithm to successfully break the BIDHP is negligible.
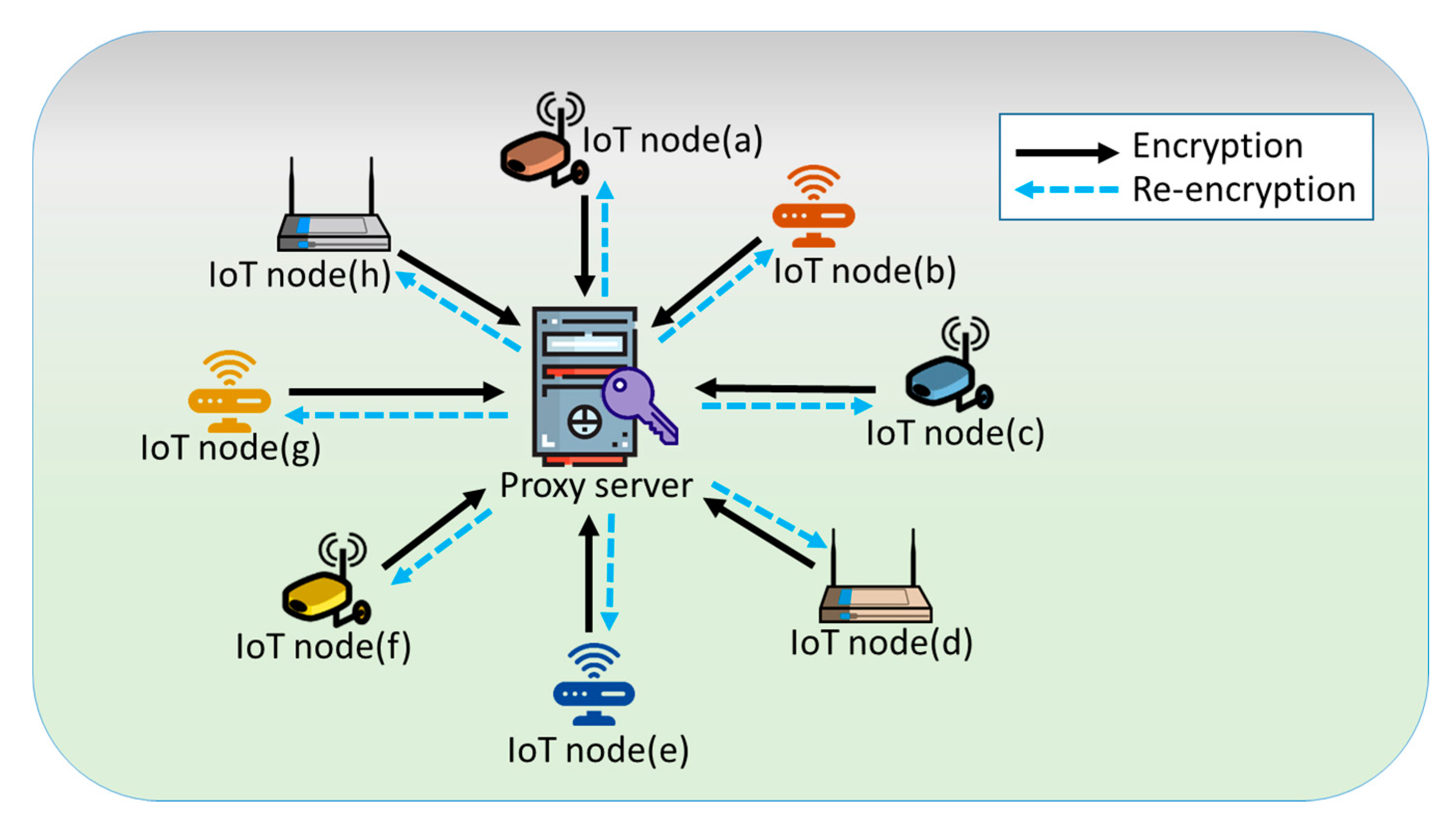
3. Proposed PRE Scheme
3.1. Algorithms
3.2. Construction
4. Security Analysis and Performance
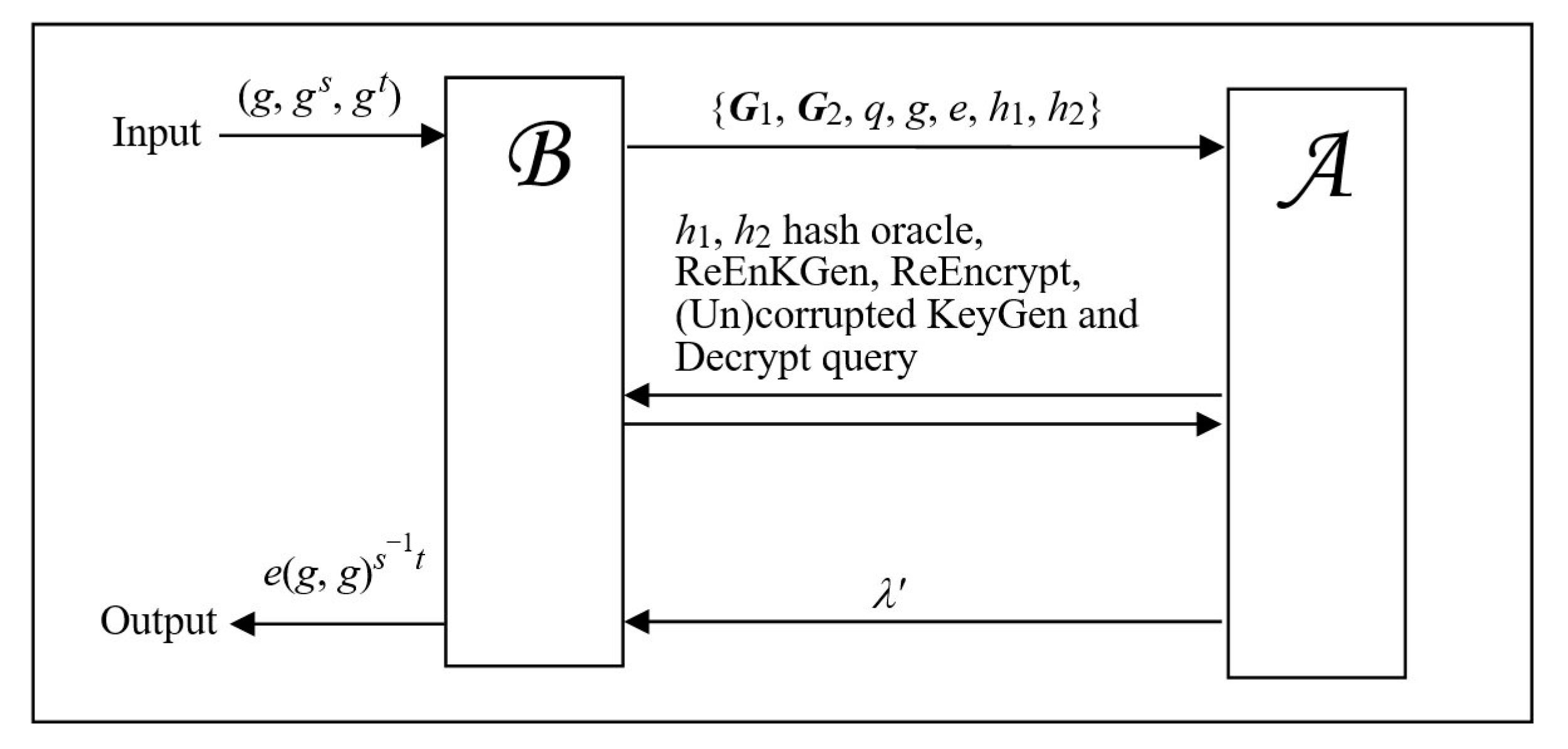
4.1. Security Model
4.2. Security Analysis
- Search the maintained Ukey-table for a record (x*, Y*);
- Randomly select z* and b* from {0, 1}k1 and Zq*, respectively;
- Compute a* = e(gx* z*, c*) and let c* be gt, i.e., this parameter t is implicitly set to be the output of h1(mλ || z*) and the value b*(mλ || z*)−1 is implicitly defined as the output of ;
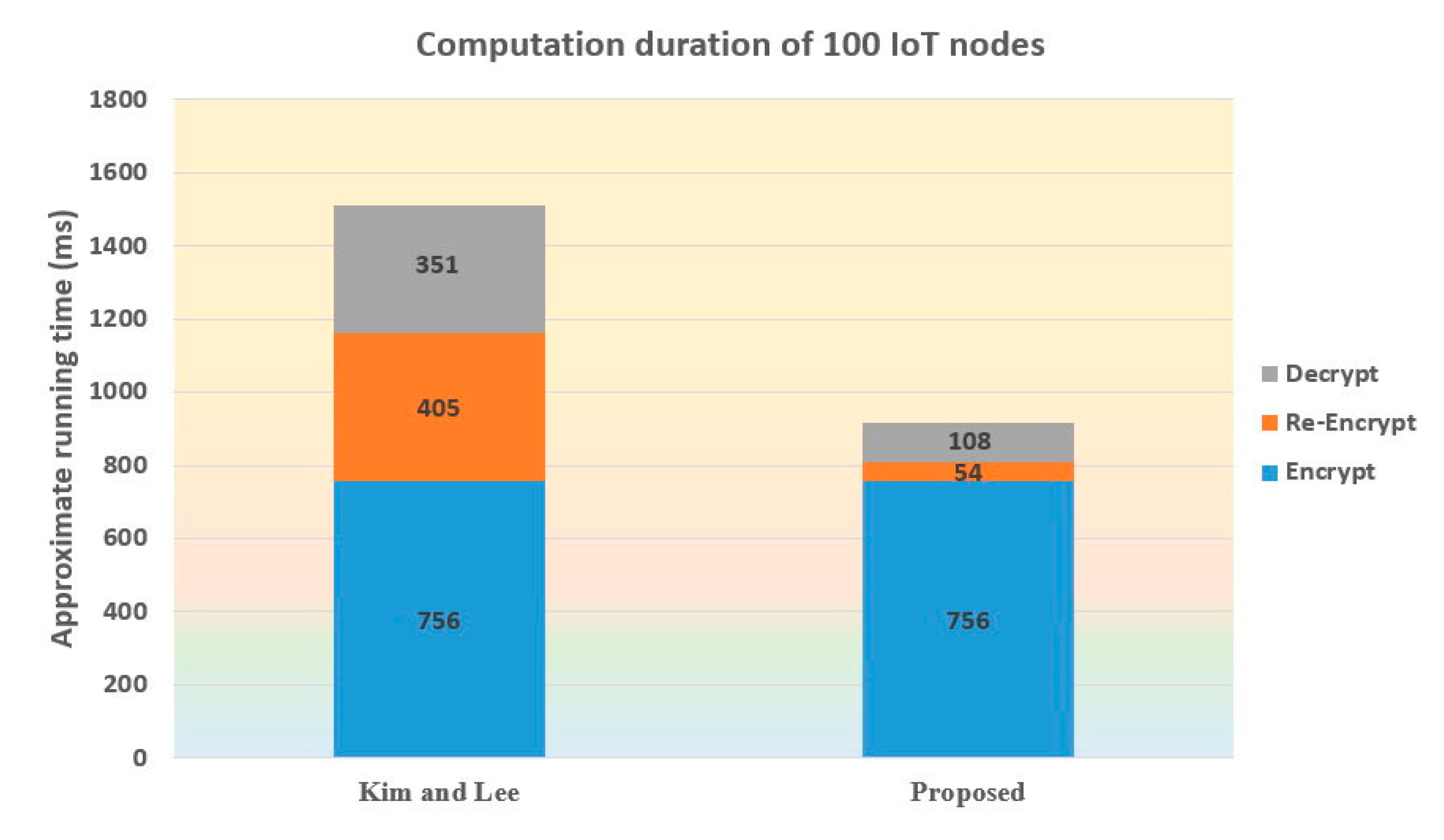
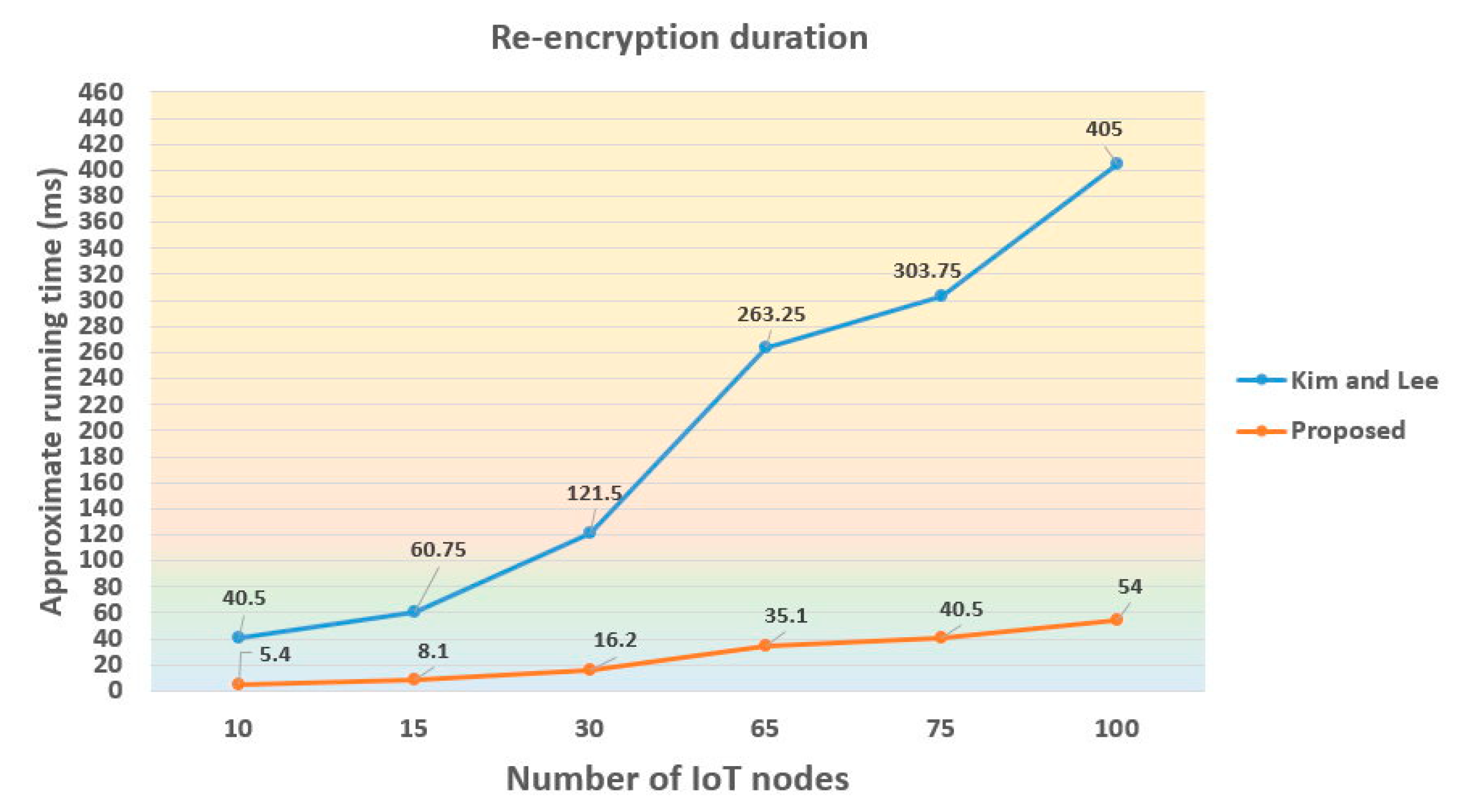
4.3. Performance Evaluation
4.4. Discussion of Results
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Ethical Approval
References
- Wang, C.; Dong, S.; Zhao, X.; Papanastasiou, G.; Zhang, H.; Yang, G. SaliencyGAN: Deep learning semisupervised salient object detection in the fog of IoT. IEEE Trans. Ind. Inf. 2020, 16, 2667–2676. [Google Scholar] [CrossRef]
- Sidhu, M.S.; Saif, S.; Ghazali, N.E.; Shah, S.M.; Chun, T.W.; Hussain, T.J. Automating switchgear asset supply chain management with IoT and RFID technology. In Proceedings of the 2020 8th International Conference on Information Technology and Multimedia (ICIMU), Selangor, Malaysia, 24–26 August 2020; pp. 404–408. [Google Scholar]
- Minerva, R.; Biru, A.; Rotondi, D. Towards a Definition of the Internet of Things (IoT). 2015. Available online: https://iot.ieee.org/images/files/pdf/IEEE_IoT_Towards_Definition_Internet_of_Things_Revision1_27MAY15.pdf (accessed on 15 December 2020).
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef]
- Divarcı, S.; Urhan, O. Secure gateway for network layer safety in IoT systems. In Proceedings of the 2018 26th Signal Processing and Communications Applications Conference (SIU), Izmir, Turkey, 2–5 May 2018; pp. 1–4. [Google Scholar]
- Yassein, M.B.; Shatnawi, M.Q.; Al-zoubi, D. Application layer protocols for the Internet of things: A survey. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–4. [Google Scholar]
- Tschofenig, H.; Arkko, J.; Thaler, D.; McPherson, D. Architectural Considerations in Smart Object Networking; Technical No. RFC 7452; Internet Architecture Board, March 2020. [Google Scholar]
- Chunpeng, G.; Liu, Z.; Xia, J.; Liming, F. Revocable identity-based broadcast proxy re-encryption for data sharing in clouds. IEEE Trans. Dependable Secure Comput. 2020. [Google Scholar] [CrossRef]
- Rawal, B.S. A proxy re-encryption-based webmail and file sharing system for collaboration in cloud computing environment. In Proceedings of the 2018 International Conference on Computational Techniques, Electronics and Mechanical Systems (CTEMS), Belgaum, India, 4–6 October 2018; pp. 213–218. [Google Scholar]
- Xu, P.; Jiao, T.; Wu, Q.; Wang, W.; Jin, H. Conditional identity-based broadcast proxy re-encryption and its application to cloud email. IEEE Trans. Comput. 2016, 65, 66–79. [Google Scholar] [CrossRef]
- Kanchan, S.; Chaudhari, N.S. Integrating group signature scheme with non-transitive proxy re-encryption in VANET. In Proceedings of the 2016 International Conference on Computing, Analytics and Security Trends (CAST), Pune, India, 19–21 December 2016; pp. 227–231. [Google Scholar]
- Wang, X.A.; Xhafa, F.; Zheng, Z.; Nie, J. Identity based proxy re-encryption scheme (IBPRE+) for secure cloud data sharing. In Proceedings of the 2016 International Conference on Intelligent Networking and Collaborative Systems (INCoS), Ostrawva, Czech Republic, 7–9 September 2016; pp. 44–48. [Google Scholar]
- Wang, X.A.; Xhafa, F.; Hao, W.; He, W. Non-transferable unidirectional proxy re-encryption scheme for secure social cloud storage sharing. In Proceedings of the 2016 International Conference on Intelligent Networking and Collaborative Systems (INCoS), Ostrawva, Czech Republic, 7–9 September 2016; pp. 328–331. [Google Scholar]
- Henriques, M.S.; Vernekar, N.K. Using symmetric and asymmetric cryptography to secure communication between devices in IoT. In Proceedings of the 2017 International Conference on IoT and Application (ICIOT), Nagapattinam, India, 19–20 May 2017; pp. 1–4. [Google Scholar]
- Li, Z.; Ma, C.; Wang, D. Towards multi-hop homomorphic identity-based proxy re-encryption via branching program. IEEE Access 2017, 5, 16214–16228. [Google Scholar] [CrossRef]
- Ge, C.; Susilo, W.; Wang, J.; Huang, Z.; Fang, L.; Ren, Y. A key-policy attribute-based proxy re-encryption without random oracles. Comput. J. 2016, 59, 970–982. [Google Scholar] [CrossRef]
- Fugkeaw, S.; Sato, H. Improved lightweight proxy re-encryption for flexible and scalable mobile revocation management in cloud computing. In Proceedings of the 2016 IEEE 9th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 27 June–2 July 2016; pp. 894–899. [Google Scholar]
- Chandu, Y.; Kumar, K.S.R.; Prabhukhanolkar, N.V.; Anish, A.N.; Rawal, S. Design and implementation of hybrid encryption for security of IoT data. In Proceedings of the 2017 International Conference on Smart Technologies for Smart Nation (SmartTechCon), Bengaluru, India, 17–19 August 2017; pp. 1228–1231. [Google Scholar]
- Fang, L.; Susilo, W.; Ge, C.; Wang, J. Chosen-ciphertext secure anonymous conditional proxy re-encryption with keyword search. Theor. Comput. Sci. 2012, 462, 39–58. [Google Scholar] [CrossRef]
- Wang, X.A.; Huang, X.; Yang, X.; Liu, L.; Wu, X. Further observation on proxy re-encryption with keyword search. J. Syst. Softw. 2012, 85, 643–654. [Google Scholar] [CrossRef]
- Liang, K.; Fang, L.; Susilo, W.; Wong, D.S. A ciphertext-policy attribute-based proxy re-encryption with chosen-ciphertext security. In Proceedings of the IEEE 2013 5th International Conference on Intelligent Networking and Collaborative Systems (INCoS), Xi’an, China, 9–11 September 2013; pp. 552–559. [Google Scholar]
- Akhil, N.V.; Vijay, A.; Kumar, D.S. QR code security using proxy re-encryption. In Proceedings of the 2016 International Conference on Circuit, Power and Computing Technologies (ICCPCT), Nagercoil, India, 18–19 March 2016; pp. 1–5. [Google Scholar]
- Zeng, P.; Choo, K.R. A new kind of conditional proxy re-encryption for secure cloud storage. IEEE Access 2018, 6, 70017–70024. [Google Scholar] [CrossRef]
- Hussain, I.; Negi, M.C.; Pandey, N. Proposing an encryption/decryption scheme for IoT communications using binary-bit sequence and multistage encryption. In Proceedings of the 2018 7th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 29–31 August 2018; pp. 709–713. [Google Scholar]
- Krishnamoorthy, S.; Muthukumaran, V.; Yu, J.; Balamurugan, B. A secure privacy preserving proxy re-encryption scheme for IoT security using near-ring. In Proceedings of the 2019 International Conference on Pattern Recognition and Artificial Intelligence, Wenzhou, China, August 2019; pp. 27–32. [Google Scholar]
- Fan, C.I.; Tseng, Y.F.; Huang, Y.L. Key-aggregate proxy re-encryption with dynamic condition generation using multilinear map. In Proceedings of the 2020 15th Asia Joint Conference on Information Security (AsiaJCIS), Taipei, Taiwan, 20–21 August 2020; pp. 9–15. [Google Scholar]
- Chandrakala, B.M.; Reddy, S.C.L. Proxy re-encryption using MLBC (modified lattice based cryptography). In Proceedings of the 2019 International Conference on Recent Advances in Energy-efficient Computing and Communication (ICRAECC), Nagercoil, India, 7–8 March 2019; pp. 1–5. [Google Scholar]
- Fimiani, G. Supporting privacy in a cloud-based health information system by means of fuzzy conditional identity-based proxy re-encryption (FCI-PRE). In Proceedings of the 2018 32nd International Conference on Advanced Information Networking and Applications Workshops (WAINA), Krakow, Poland, 16–18 May 2018; pp. 569–572. [Google Scholar]
- Lian, Z.; Su, M.; Fu, A.; Wang, H.; Zhou, C. Proxy re-encryption scheme for complicated access control factors description in hybrid cloud. In Proceedings of the 2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Maiti, S.; Misra, S. P2B: Privacy preserving identity-based broadcast proxy re-encryption. IEEE Trans. Veh. Technol. 2020, 69, 5610–5617. [Google Scholar] [CrossRef]
- Meiliasari, R.P.; Syalim, A.; Yazid, S. Performance analysis of the symmetric proxy re-encryption scheme. In Proceedings of the 2019 International Workshop on Big Data and Information Security (IWBIS), Bali, Indonesia, 11 October 2019; pp. 91–96. [Google Scholar]
- Rabieh, K.; Mercan, S.; Akkaya, K.; Baboolal, V.; Aygun, R.S. Privacy-preserving and efficient sharing of drone videos in public safety scenarios using proxy re-encryption. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 11–13 August 2020; pp. 45–52. [Google Scholar]
- Seo, J.W.; Yum, D.H.; Lee, P.J. Proxy-invisible CCA-secure type-based proxy re-encryption without random oracles. Theor. Comput. Sci. 2013, 491, 83–93. [Google Scholar] [CrossRef]
- Wu, L.; Yang, X.; Zhang, M.; Liu, L. New identity based proxy re-encryption scheme from lattices. China Commun. 2019, 16, 174–190. [Google Scholar] [CrossRef]
- Shen, Y.; Zhang, H.; Fan, Y.; Lee, A.P.W.; Xu, L. Smart health of ultrasound telemedicine based on deeply-represented semantic segmentation. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Kim, S.; Lee, I. IoT device security based on proxy re-encryption. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1267–1273. [Google Scholar] [CrossRef]
- Scott, M.; Costigan, N.; Abdulwahab, W. Implementing cryptographic pairings on smartcards. In Proceedings of the Workshop on Cryptographic Hardware and Embedded Systems 2006 (CHES 2006), Yokohama, Japan, 10–13 October 2006; pp. 134–147. [Google Scholar]

| Parameter | Description |
|---|---|
| k | security parameter |
| q | large prime |
| G1, G2 | multiplicative group |
| g | generator |
| e | bilinear map |
| h1, h2 | one-way hash function |
| xi | private key |
| Yi | public key |
| rki→j | re-encryption key |
| m | message |
| δ | ciphertext |
| Scheme | Kim and Lee | Proposed | |
|---|---|---|---|
| Item | |||
| Provable Security | X | √ | |
| Cryptographic Assumption | Unknown | BIDHP | |
| Public Information | {G, GT, e, g, q, H} | {G1, G2, e, g, q, h1, h2} | |
| Computation Complexity | 4TB + 6TE | 2TB + 6TE | |
| Amount of Sharing * | O(n) | O(n) | |
| NodeCount | Traditional Way | Kim and Lee | Proposed | |||
|---|---|---|---|---|---|---|
| Comm. Count | Duration (ms) | Comm. Count | Duration (ms) | Comm. Count | Duration (ms) | |
| 2 | 2 | 8.10 | 2 | 8.10 | 2 | 1.08 |
| 3 | 6 | 24.3 | 3 | 12.15 | 3 | 1.62 |
| 4 | 12 | 48.6 | 4 | 16.2 | 4 | 2.16 |
| 5 | 20 | 81 | 5 | 20.25 | 5 | 2.7 |
| - | - | - | - | - | - | - |
| 50 | 2450 | 9922.5 | 50 | 202.5 | 50 | 27 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.-Y.; Hung, Y.-M. An Improved Proxy Re-Encryption Scheme for IoT-Based Data Outsourcing Services in Clouds. Sensors 2021, 21, 67. https://doi.org/10.3390/s21010067
Lin H-Y, Hung Y-M. An Improved Proxy Re-Encryption Scheme for IoT-Based Data Outsourcing Services in Clouds. Sensors. 2021; 21(1):67. https://doi.org/10.3390/s21010067
Chicago/Turabian StyleLin, Han-Yu, and Yao-Min Hung. 2021. "An Improved Proxy Re-Encryption Scheme for IoT-Based Data Outsourcing Services in Clouds" Sensors 21, no. 1: 67. https://doi.org/10.3390/s21010067
APA StyleLin, H.-Y., & Hung, Y.-M. (2021). An Improved Proxy Re-Encryption Scheme for IoT-Based Data Outsourcing Services in Clouds. Sensors, 21(1), 67. https://doi.org/10.3390/s21010067





