Abstract
In this paper, we investigate the outage performance of simultaneous wireless information and power transfer (SWIPT) based Decode-and-Forward (DF) relay networks, where the relay needs to simultaneously forward information for two relaying links, primary relaying link and parasitic relaying link. The primary relaying link is the traditional source-relay-destination relay system. While in the parasitic relaying link, the parasitic source, i.e., Internet-of-Things (IoT) tag, is not connected to the stable power source and thus has to backscatter the signals from the primary source to convey its information. The relay not only harvests energy from Radio Frequency (RF) signals from both sources but also forwards messages to their corresponding destinations. The primary source and destination are unaware of the parasitic backscatter transmission, but the relay and parasitic destination can employ successive interference cancellation (SIC) detector to eliminate the interference from the primary link and detect the message from the parasitic source. In order to investigate the interplay between the primary and parasitic relaying links, the outage probabilities of both relaying links are derived. Besides, the effects of system parameters, i.e., power splitting coefficient, forwarding power allocation coefficient and backscatter reflection coefficient, on the system performance are discussed. Simulation results verify our theoretical analysis. In the meanwhile, it is revealed that the advised relaying system has far larger sum throughput than the one with only primary relaying link and the parasitic relaying link can gain considerable throughput at the cost of negligible degradation of primary throughput.
1. Introduction
Backscatter communication enables information transmission by reflecting incident radio frequency (RF) signal and as such enjoys trivial power consumption and low implementation cost. It has been recognized as a promising solution to the massive communication requirements of internet of things (IoT) [1,2,3,4]. Generally speaking, at present there are three main ways to implement backscatter communications, i.e., monostatic, bistatic, and ambient modes [4,5]. In monostatic and bistatic modes, a dedicated carrier transmitter is required to emit excitation RF signal to the backscatter tag. The difference between both modes is that in the monostatic mode the carrier transmitter and information receiver are equipped at the same node and can share the same antenna, and in the bistatic mode carrier transmitter and receiver belong to separate nodes. On the other hand, in ambient backscatter communication (AmBC) mode, the backscatter tag alternatively employs the ambient RF signal as the excitation signal. As IoT is envisioned to provide pervasive and ubiquitous interconnections among various kinds of entities, one of the most significant features of IoT is heterogeneous and compatible with existing networks [6]. For this reason, AmBC can make full use of a mess of various RF signals from heterogeneous wireless networks and has been widely investigated by the research community. To this end, we also focus on AmBC in this paper.
The backscatter tag modulates information onto the incidence RF signal and reflects it to its receiver/reader. The basic principle of backscatter communication is utilizing impedance mismatch to reflect RF signal. Thus, the characteristics of the incidence RF signal can be modified by the tag to convey its information to be transmitted. For examples, On-Off Keying (OOK) [7], Binary Phase Shift Keying (BPSK) [8], Multi-Phase Shift Keying (MPSK) [9], Differential Phase Shift Keying (DPSK) [10], Quadrature Amplitude Modulation (QAM) [11], Multi-frequency-shift Keying (MFSK) [12,13] etc., have been proposed for backscatter communication. Additionally, the Orthogonal Frequency Division Multiplexing (OFDM) signal is exploited to perform AmBC [14,15]. Various detection methods are addressed in [16,17,18,19]. For all these backscatter schemes, the backscattered signal is excited by the incident RF signal. Therefore, except in FSK backscatter scheme, the backscattered signal and ambient RF signal may interfere with each other in certain instances, for example, the tag is close to the legacy receiver. As the FSK backscatter scheme needs extra frequency resources and may not be suitable for massive IoT networks [3], the ambient RF and backscattered signals have the same frequency in our paper.
Along with the rapid development of backscattering technology, AmBC has been applied widely in many wireless systems and incorporated with other advanced wireless technologies. Multi-antenna backscatter tags were considered in order to gain spatial diversity [18,19,20,21,22,23]. The scenarios of multiple backscatter tags were investigated by [5,24,25,26]. In order to prevent the reflected signal from degrading the transmissions of ambient RF signals, the cognitive backscatter tag was proposed in [27,28,29,30]. To improve the energy efficiency of backscatter communication, full-duplex communication was also introduced into backscatter tags [31,32]. In order to achieve high energy efficiency, multiple backscatter tags performing non-orthogonal multiple access (NOMA) was proposed in [33]. Instinctively, the cooperative relaying communications were also incorporated with AmBC. Since the backscatter tag can transmit its information through reflecting incident ambient RF signal, it also can reflect the ambient RF signal to the legacy receiver to improve the reliability of legacy transmission. Then AmBC based relay systems were proposed by [34,35,36]. In [34,35], the ambient RF signal carried no information and the interference from the ambient RF signal was not considered in the AmBC. While the performance of the legacy receiver was not investigated and the non-coherent receiver was employed in [36]. The optimal resource allocation with instantaneous channel state information was addressed for relay-assisted AmBC system in [37]. Based on the two-hop RF signals, the AmBC between relay and the cognitive tag was proposed in [38]. Although the interference from AmBC tag was considered in the primary destination, the secondary AmBC receiver was not interfered by the primary transmission.
Specifically, AmBC naturally causes interference to ambient RF sources. It is of importance to explore interaction and coexistence issues between AmBC and ambient wireless transmissions [39]. Liang et al. in [17,40,41,42] proposed the concept of symbiotic radio to capture the key feature of AmBC and investigated the overall performance of the symbiotic system which incorporates AmBC and other wireless systems. In [17], three practical symbiotic radio schemes, commensal, parasitic, and competitive schemes, were proposed to represent the symbiotic relationship between AmBC and primary transmission. In [40], joint optimal primary transmit power and the reflection coefficient of AmBC tag was studied in different symbiotic setups. A full-duplex AmBC tag in the parasitic scheme was proposed in [41], where the optimization resource allocation was addressed. Furthermore, the symbiotic system consisting of AmBC and NOMA system was proposed in [42,43]. From a practical viewpoint, it is costly to let the IoT backscatter tag fully cooperate with the ambient RF transmitter due to signaling overhead. Considering the transmission quality of the authorized RF signal, the full competition from massive IoT tags is not allowed. Thus, the parasitic AmBC, which means we could only improve the performance of IoT AmBC transmission under the condition that the performance of primary transmission is guaranteed or the performance degradation generated by AmBC is acceptable.
In this paper, we investigate the symbiotic relaying system of AmBC and DF relay networks using SWIPT. To the best of our knowledge, it is the first work concerning the symbiotic relaying system. In our considered symbiotic radio system, there are two source-destination pairs, primary source-destination pair and parasitic source-destination pair. Both pairs have no direct transmission channel, so the DF relay is designed to help both sources to forward messages for their corresponding destinations. Considering the IoT scenario, we assume the relay is not connected to a stable power supply and has to harvest energy from the ambient RF signal. Thus, the DF relay adopts the SWIPT during the source transmission phase. The power splitting structure is adopted at the relay. Thus, the relay can detect the received information signal while harvesting energy (refer to [44] and references therein). If the harvested energy can cover the circuit dissipation, the relay performs DF relaying scheme with the left harvested energy. Furthermore, the relay needs to forward two different messages to both destinations simultaneously, therefore, the power domain NOMA is employed to broadcast regenerated signals. The parasitic relaying transmission is fully compatible with the traditional DF relay scheme. In order to investigate the interplay between primary and parasitic relaying links, we derive the analytical expressions of outage probabilities and throughput of both relaying links. Besides, the effects of system parameters on the system performance are discussed via our theoretical results. Finally, the simulation results verify our theoretical results. We also show that the advised relaying system has far larger sum throughput than the one with only primary relaying link and the parasitic relaying link can gain considerable throughput at the cost of negligible degradation of primary throughput. The main contributions of this paper are summarized as follows:
- To the best of our knowledge, the scenario, where the DF relay using SWIPT helps the primary source and parasitic AmBC source to forward information for their corresponding destinations, is investigated for the first time.
- We achieve the analytical expressions of outage probabilities and throughput of both primary and parasitic relaying links. Via the derived theoretical results, we also discuss the effects of the system parameters on the whole system performance.
- From simulation results, we can see that the considered relaying system has a far larger sum throughput than the one with the only primary relaying link. Besides, it is found that the parasitic relaying link can attain considerable throughput gains at the expense of negligible performance degradation of the primary relaying link. It means that utilizing the provided theoretical results, one can carefully choose the system parameters to drastically improve the system performance of the advised relaying system.
The rest of this paper is structured as follows. Section 2 introduces the transmission scheme, system models and assumptions. In Section 3, the outage probabilities and throughput are derived. Besides, the effects of system parameters are also discussed in Section 3. Numerical and theoretical results are shown in Section 4 to verify our analysis. Finally, we conclude this paper in Section 5.
Notations: denotes the probability of random event A. is the expectation of random variable x. stands for the complex Gaussian distribution with mean and variance . denotes the exponential distribution with mean . is the magnitude of complex number x.
2. System Model
The considered DF relay network consists of five types of nodes, primary source (PS), tag source (TS), primary destination (PD), tag destination (TD), and relay (R), as illustrated in Figure 1. Due to the possible blockage and severe path loss, PS and TS intend to transmit their information to PD and TD respectively, with the help of DF relay. It is assumed that there is no direct transmission between both source-destination pairs. PS is an active information transmitter while TS, which employs AmBC to convey information, is a passive transmitter. If PS keeps silent, there is no RF signal for TS performing signal reflection. Therefore, the PS-R-PD is the primary relaying link while TS-R-TD is the parasitic relaying link. In practice, PS with stable power supply is usually designed to transmit data with high quality of service (QoS) requirement, e.g., high information rate and reliability. The TS using AmBC always deliveries low rate application, such as measurement data, environment state information or indicator signal [1,2,3,4].
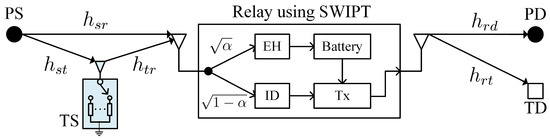
Figure 1.
System model.
Besides that, the DF relay is not linked to the stable power supply, so that it needs to harvest energy from ambient RF signals. For the PS-R-PD link, and denote the channel coefficients from PT to R and from R to PD, respectively. While, for the parasitic relaying link, , and stand for the channel coefficients of PS-PT, PT-R, and R-TD, respectively. For clarity, we use to denote the transmission distance which corresponds to channel ; e.g., is the distance from PS to R. The path loss exponent is . For convenience, we assume that all channel coefficients follow the independently and identically distributed (i.i.d) complex Gaussian distribution with zero mean and unit variance, e.g., . That is to say, all channel power gains are i.i.d. exponential distribution with unit mean, e.g., . Additionally, all channels experience quasi-static fading and change from block to block.
Since the relay-assisted AmBC is parasitic on the traditional DF relaying transmission, the whole transmission block is still divided into two phases, source transmitting and relay forwarding phases. The relaying block is shown in Figure 2. In order to let the time-block structure compatible with the traditional DF relaying scheme, we herein adopt the power splitting scheme in the DF relaying network. Suppose the whole transmission duration is T, we allocate to the source transmitting phase and the left duration belongs to the relay forwarding phase.
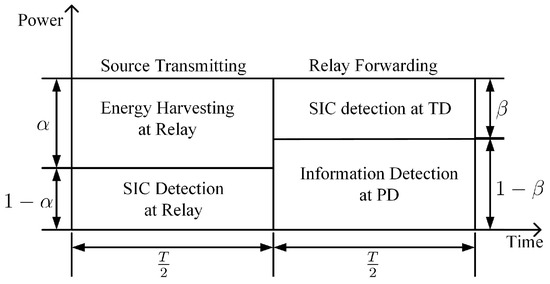
Figure 2.
Illustration of transmission time-block.
2.1. Models in Source Transmitting Phase
In the source transmitting phase, both PS and TS transmit information to the DF relay using SWIPT. In the considered scenario, PS has bits to be delivered to PD while TS tries to convey bits to TD. In other words, the target information rates of PS and TS are and . Let s and c be the transmitted baseband symbol from PS and TS respectively. In this paper, both s and c are generated from Gaussian codebook and . Considering the practical applications, the primary relaying link usually has larger information rate than the parasitic relaying link, i.e., . The received signal at the relay can be expressed as
where is the transmit power of PS and is the power reflection coefficient of AmBC. We define and . As and , the probability density function (PDF) of is
where is the zero-order modified Bessel function of the second kind. Note that we omit the reflected antenna noise from the TS for the reason that the reflected noise is degraded by the path loss and becomes negligible [34,45]. is the received noise which follows complex Gaussian distribution with zero mean and variance . The received signal is fed into a power splitter with a splitting coefficient . As Figure 2 is used to harvest energy (EH) and is employed to perform information detection (ID).
At the energy harvester, the harvested direct current (DC) power is
in which is the RF-DC power conversion efficiency. Although we can deduce the PDF of with the PDFs of and , the exact expression of PDF of makes performance analyzing intractable. Hence, in this paper, considering the severe path loss and power reflection loss, we alternatively evaluate the performance lower-bound with approximation . In practice, depends on the input RF power and appears non-linear behavior with respect to input RF power. While the non-linear power conversion model introduces a considerable complexity when we analyze the statistical performance of wireless-powered communications. As stated in [46], the distribution function of the non-linear energy harvesting (EH) model can be approximately represented by the piecewise linear EH models. Therefore, many works adopt the linear EH model for tractability [44,47,48,49,50]. The DF relay uses all harvested energy to forward its decoded information to PD and TD. Denote the transmit circuit dissipation power with , then the total energy consumption is . The available transmit power of the DF relay is given as
Obviously, means the relay has no enough harvested energy to forward information.
For information transmission, the first step in the DF relay is to extract information from . As the strength of backscattered signal from TS to R is always far less than the primary signal from PS to R due to more severe path loss and signal reflection loss, successive interference cancellation (SIC) is applied to detecting s and c in sequence. It means that s is firstly detected and subtracted from . Then c is detected from the left information signal. Thus, the received signal-to-interference-plus-noise ratio (SINR) with respect to s at relay can be written as
We assume that the ideal channel coding is utilized to protect the information bits. That is to say if where , the relay can recover s successfully. Otherwise, relay cannot obtain s without error. Note that if the detected s is in error, we omit the probability of detecting c successfully in this case, because the detection error of s is propagated to the detector of c and the success probability of detecting c becomes trivial [8]. Consequently, if , the relay does not forward information and the transmission block ends. When s is detected successfully, the received signal-to-plus-noise ratio (SNR) of c at relay is
Similarly, the detection SNR threshold of c is . If , we can recover c with no error.
2.2. Models in Relay Forwarding Phase
By the DF relaying scheme, the relay discards the received message with error and only forwards the information decoded successfully. Therefore, the DF relay acts in one of two cases, only forwarding s and forwarding s and c simultaneously. If the relay does not forward information, the harvested energy is stored in the battery to maintain the system operation and routine. Next, we describe both relaying cases separately.
In the case of only forwarding s, case I, the relay uses to transmit s to PD. Then, the received signal at PD is
in which is the receiver noise following complex Gaussian distribution with zero mean and variance . In this case, only PD needs to detect s from . The SNR on s at PD is
While if both s and c are detected correctly, case II, the relay has the ability of forwarding s and c to PD and TD. In order to be compatible with the traditional DF relaying scheme, the relay simultaneously transmits s and c with transmit power in the second phase. Let , then is forwarded by the relay. Hence the received signal at PD is
Similarly, the received signal at TD is
where is the receiver noise and . Considering , we set to guarantee the QoS priority of the primary relaying link. As a result, PD just employs traditional detector to extract s from . So, the SINR at PD is
Differently, the TD has to adopt SIC detection to decode c from . The SINR of s at TD is
If , then s can be successfully decoded by TD and subtracted from . Consequently, the SNR of c at TD is expressed as
While if , we also deem that both s and c cannot be decoded without error.
3. Outage Performance Analysis
In this section, we investigate the outage performance of the primary PS-R-PD and parasitic TS-R-TD links. As the harvested energy in the source transmitting phase is used to transmit information in the relay forwarding phase, the two hops in DF relaying scheme are not independent any more. Besides, the parasitic AmBC link affects the primary link. Therefore, we take two hops as a whole to analyze the outage probabilities.
3.1. Outage Probability of Primary Relay Transmission
For the primary relay transmission, successfully transmitting s via PS-R-PD link needs to simultaneously meet three conditions: (1) Relay decodes s without error; (2) Relay harvests enough energy, i.e., ; (3) PD decodes s correctly. Furthermore, as stated in the system model section there are two cases in the relay forwarding phase, case I (only forwarding s) and case II (forwarding s and c simultaneously), according to the results of SIC detection at the DF relay. Let and denote the successful transmission probabilities in cases I and II, respectively. The overall outage probability with respect to s can be expressed as
Next, we derive the expressions of and separately.
Theorem 1.
The probability of successful transmission of s via PS-R-PD in case I, where the relay only forwards s to PD, can be expressed as
where
where , and . The definitions of , , , , , ϕ, and can be found in (A3), (A4), (A9), and (A13) in Appendix A.
Proof.
See Appendix A. □
Theorem 2.
The probability of successful transmission of s via PS-R-PD in case II, where the relay simultaneously forwards s and c to PD and TD, can be expressed as
where and are as defined in (A22) in Appendix B.
Proof.
See Appendix B. □
Due to Theorem 1 and 2, the overall outage probability with respect to s can be deduced. In addition, the throughput of the primary PS-R-PD link is given by
3.2. Outage Probability of Parasitic AmBC Transmission
In contrast to the primary relay transmission, correctly transmitting c through the parasitic AmBC transmission has four conditions: (1) Relay decodes c correctly; (2) Relay harvests enough energy, i.e., ; (3) TD decodes s with no error; (4) TD decodes s successfully. Accordingly, the overall outage probability of c can be written as
where
Theorem 3.
The probability of successful transmission of c via TS-R-TD can be expressed as
where the definition of φ can be found in (A27) in Appendix C.
Proof.
See Appendix C. □
Therefore, the throughput of the parasitic TS-R-TD link can be presented as
3.3. Effects of Parameters
After deriving the outage probability and throughput of two relaying links, we can now investigate the effects of the system parameters on transmission performance. By the derived outage probabilities, all parameters affect the performance of and greatly. Note that stands for the efficiency of RF-DC power converting. Therefore, it is usually preferable to let approach 1 as closely as possible. In practical scenarios, is determined by the rectifier. Next, therefore, we discuss the effects of these three parameters (, , ) on both relaying links.
3.3.1. Effects of
As is involved in , and , there exists great difficulty in investigating the effects of in a theoretical way. Unavoidably, we have to apply numerical methods to determine the optimal in this paper. In spite of this, we can explore the asymptotic performance in the extreme cases of . If , we have and . Accordingly, there are and . The reason is that the relay cannot harvest any energy on the condition of . On the contrary, if , both and converge to infinity. Due to (A2) and (A17), in this case it is easy to know , , and . The phenomenon can be interpreted as the fact that no information is passed to relay in this case. As a result, we need to choose an optimal to minimize the outage probability via numerical methods.
3.3.2. Effects of
Obviously, just affects the system performance during the relay forwarding phase and is only involved in [cf. (A3)]. For PD, it is expected that the relay allocates as much power as possible to s. So is a monotonically decreasing function with respect to and the optimal choice is .
However, TD should detect s first and detect c after subtracting s. Thus, we should balance the power allocated to s and c in order to maximize . Based on (A26), we can rewrite as
where We can see that if , is a monotonically decreasing function of . Differently, if , increases as increasing. That is to say the optimal to maximize , i.e., to minimize , is
Interestingly, we can see that is independent of . It means even if affects the performance of , it does not influence . Oppositely, it is apparent that influences not only the source transmitting phase but also the relay forwarding phase. So, seeking the optimal to minimize , we should concern as affects the performance of the relay forwarding phase. While, for , the optimal equals to zero (note that we let in practice). It means the optimal has no relation to the optimal to maximize .
3.3.3. Effects of
Similarly, the expressions of the outage probabilities are so complicated with respect to , thus we have to apply numerical method to investigate the effects of on the system performance. There is an evident fact that given all other parameters, makes achieve the minimum. This is because all harvested power is used to forward s to PD and there is no interference. For c, increasing from zero, the strength of the signal reflected by TS becomes greater and it may improve the probability of decoding c without error at the relay. Nonetheless, increasing also causes a degradation of the probability of decoding s successfully at the relay. As a result, enlarging is not always the best choice to minimize . We need to find the optimal via numerical solutions.
4. Simulation
In this section, we show the simulation results to verify our theoretical analysis. The system parameters in simulations follow the default values listed in Table 1, unless otherwise specified. The simulation results are generated by Monte Carlo experiments over channel realizations. The theoretical results are obtained by the expressions of the derived outage probabilities. In the figure legends, ‘Sim.’ and ‘The.’ are the abbreviations of simulational and theoretical, respectively.

Table 1.
Parameters in simulations.
In Figure 3, the outage probabilities are demonstrated with various information rate configurations. First of all, we can see that all theoretical results fit the simulational results closely. It means our derived expressions of outage probabilities can represent the performance of both primary and parasitic relaying links. As raises up, both and constantly decrease. Moreover, under the same rate configuration is always less than given a . We consider three information rate configurations in this simulation. For bps/Hz, decreasing from 1 bps/Hz to bps/Hz diminishes not only but also . Nevertheless, for bps/Hz, decreasing from bps/Hz to bps/Hz just reduces . This phenomenon shows plays a more significant role in transmission performance than . The reason is that the precondition of decoding c successfully is that s has been decoded without error. Furthermore, the scenario bps/Hz has the maximum performance gap between and among all three scenarios. While the scenario with bps/Hz and bps/Hz achieves the minimum performance gap. In other words, the larger the rate difference between primary and parasitic relaying links is, the less the outage probability gap is. Therefore, the derived theoretical results provide useful tools for the system designers to determine system parameters according to the required transmission QoS.
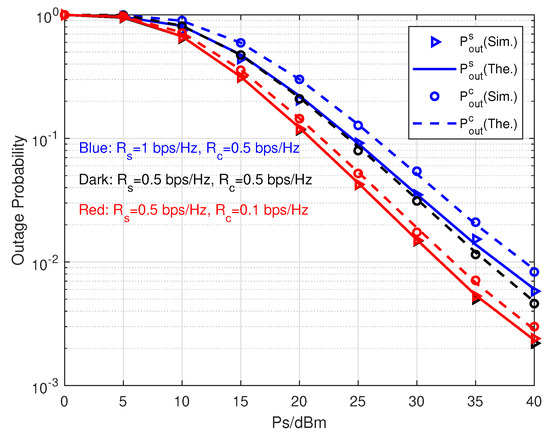
Figure 3.
Outage probabilities versus with different information rates.
The effects of power splitting coefficient on outage probabilities are illustrated in Figure 4. Obviously, the simulation results verify our theoretical results well. Given an , the larger transmit power brings in lower outage probability. When , the relay can not harvest any RF energy and has to stop forwarding information. So the outage probabilities equal to 1. As increasing, the relay harvests more and more energy to forward information during the relay forwarding phase. Thus, and start to decrease. When , and achieve almost the same performance. While, when , the performance gap between and gradually appears. The reason is R can simultaneously successfully decode s and c in most cases when . So, and have nearly the same values. However, when , increasing lowers the growth of probability of decoding s successfully at R and produces more harm to decoding c successfully due to the SIC detector. As s result, the outage gap appears. We also can see that given , apparently has the minimum value over . As for , the optimal generating minimum approaches 1 extremely closely, e.g., the optimal is about 0.98 when dBm. This is because the extremely high produces large harvested energy and nearly no c can be received successfully at R. In this case, although the probability of decoding s correctly becomes lower, R could own large transmit power to forward s to PD with almost no interference. Given that in the source transmitting phase s and c always interference each other, it is obviously to deduce that the optimal tends to allocate more energy to the R-PD transmission without interference.
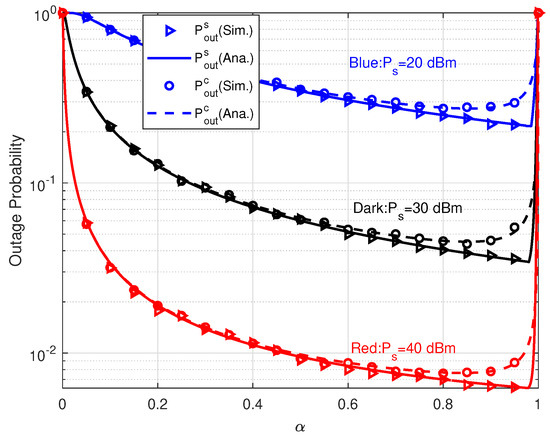
Figure 4.
Outage probabilities versus with different .
That is to say that and own different optimal power splitting coefficients. When , both and converge to 1 again because of information link interruption. Then our analysis on the effect of is also verified. Comparing these three scenarios with different , it is observed that the optimal occurs at the same and it is independent on . From Figure 4, it is concluded that we have to carefully choose to balance the performance of primary and parasitic relaying links. In Table 1, we let to make both and achieve favorable performance.
In Figure 5, we show the performance of and versus power allocation coefficient . In this simulation, we set bps/Hz and bps/Hz. Therefore, by (23) the optimal power allocation coefficient is for Then, the feasible region of is . The curves of in Figure 5 also show that makes minimum . On the contrary, increases as rises. These results verify our analysis on the effects of . When , reaches the minimum value because all relay transmit power is allocated to s. Differently, if , although total is used to forward c, still converges to 1. The reason is that SIC detector at TD cannot decode c successfully under the condition of . By this figure, it is shown that also affects and greatly and we need to adjust to coordinate the performance of both relaying links. In practice, the QoS requirement of primary relaying link should be satisfied as far as possible. With the primary QoS constraint, the outage probability of parasitic relaying link could be minimized through optimizing . For example, in the scenario dBm, if the constraint is , the optimal is 0.22 to minimize . While, if we let , should be larger than 0.36. Therefore, the optimal for is 0.36, since is out of the feasible range.
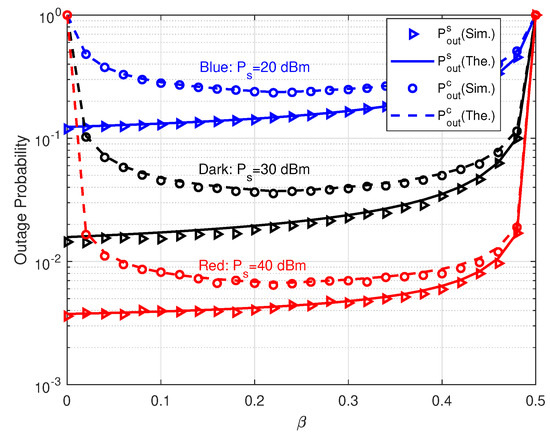
Figure 5.
Outage probabilities versus with different .
The effects of reflection coefficient on outage probabilities are investigated in Figure 6. It is notable that decreases and nearly keep constant as increases in the cases of dBm and dBm. This is because the reflected signal by TS interferes with the primary link slightly. Therefore, in both cases, we can reduce via enhancing while bringing in trivial impact on . In other words, the performance of parasitic relaying link can be improved at the expense of negligible performance degradation of primary relaying link. However, the aforementioned conclusion does not hold if dBm. We can see that as increases becomes larger and larger. The reason is the power of reflection signal conveying c is proportional to . When and are large enough, e.g., dB and , the signal reflected by TS incurs considerable interference to the primary link. Therefore, increasing increases in the case of 40 dB. Furthermore, the increasing finally enlarges a little. It is also shown we can choose a suitable to meet the QoS requirements of primary and parasitic relaying links.
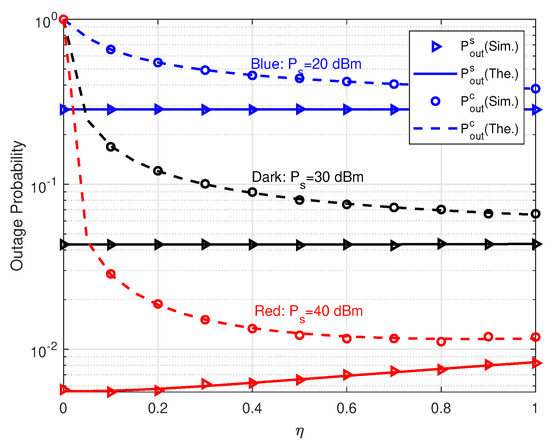
Figure 6.
Outage probabilities versus with different .
In Figure 7, average throughput versus are depicted. Note that stands for the average throughput of the system with only a primary relaying link, i.e., and . Here, is the sum throughput, i.e., . Herein we draw and to demonstrate the throughput gain and advantage of the parasitic relaying link. As increases, all four types of throughput increase and approach corresponding performance limits. Observing the throughput performance over , the considered parasitic relaying link can gain certain throughput at the expense of sacrificing a little throughput of the primary relaying link. It is worth pointing out that the sum throughput outperforms when dBm. That is to say, the parasitic relaying link can attain throughput gains than the traditional SWIPT relaying system which just forwards s. Not only that, when dBm, approaches closely. It means the throughput degradation caused by parasitic relaying link can be eliminated in the high transmit power scenario and the parasitic relaying link can gain considerable throughput at no additional expense.
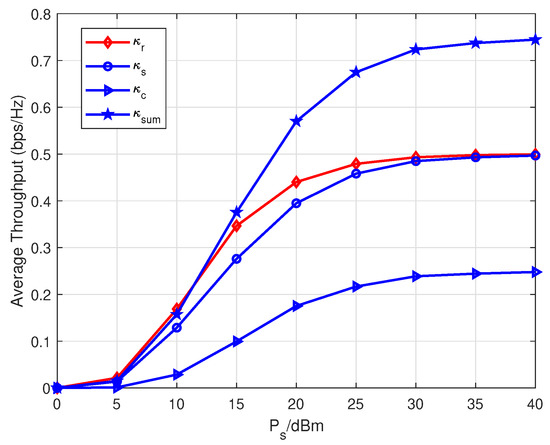
Figure 7.
Average throughput versus .
5. Conclusions
In conclusion, we have studied AmBC, which is parasitic on a relay system that employs simultaneous wireless information and power transfer and decode-and-forward. The relay is responsible for forwarding information both for the primary source and for the AmBC tag source. Both the relay and the tag destination perform successive interference cancellation to eliminate the interference from the primary source and detect the message from tag source. We presented a careful analysis of the outage probabilities of both the primary and parasitic relaying transmissions. The analytical expressions obtained to enable a system designer to perform optimization on the system parameters. Specifically, we have studied the effects of three system parameters, namely power splitting coefficient, forwarding power allocation coefficient and the AmBC reflection coefficient, on the system performance. Simulation results show that the considered relay system achieves more sum throughput than the original relay system. It is also found that the parasitic relaying link is able to achieve sizable throughput at the cost of negligible degradation of the relay system without AmBC tag.
Author Contributions
Conceptualization, Y.T. and C.Z.; methodology and formal analysis, Y.T.; validation, Y.T., C.Z.; writing—original draft preparation and editing, C.Z.; supervision, C.Z.; project administration, C.Z.; funding acquisition, C.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by the Key Research and Development Program of Shaanxi Province.
Acknowledgments
The authors would like to express their thanks and appreciation to Zhengdao Wang for his valuable suggestion and comments.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
Appendix A. Proof of Theorem 1
In the case I, in the light of the system model, we have
Based on (A2), we can see that if , it is obvious that , which means s cannot be transmitted successfully under this condition. Therefore, we just need to investigate the performance under the condition
Moreover, comparing to , we can rewrite (A2) as
Nest, we separately give the expressions of and .
For , if , then . If , can be rewritten by
Due to , it is obvious that
Utilizing the PDF of in (2), we have
where the first-order modified Bessel function of the second kind. Substituting (A7) and (A8) into (A6), we can express as
Although (A9) is a definite integral, it is intractable mathematically. Alternatively, we can resort to the n-point Chebyshev-Gauss Quadrature [52] to approximately express (A9) as
where , , and n controls the exactness of the computed integral.
For , define , there is
Like (A8), it can be expressed as
Furthermore, we have
In step , we let and step refers to ([53], eq. (3.324)). Following also the n-point Chebyshev-Gauss Quadrature, we have
Appendix B. Proof of Theorem 2
In the case II, like (A1), there is
Obviously, if , . It represents the event that when the relay simultaneously transmits s and c to PD, s cannot be received correctly. This situation leads to energy inefficiency. To avoid such situation, we should choose to make ; i.e., . Meanwhile, recall that in the analysis in the case I, there is no extra constraint on . As the system performance depends on the statistical channel state information (CSI), to make PD receive s successfully with a non-vanishing probability in both cases, we force to hold.
Considering , can be further written as
Since , we can obtain
By the PDF of , we have
Therefore, under the constraint , the successful transmission probability of s in case II can be expressed as in (A22).
Unfortunately, we cannot find an analytical expression of . We can resort to Gauss–Laguerre Quadrature [52] to evaluate , i.e.,
where nodes and weights can be found in [52].
In summary, if , then
and if , . Therefore, Theorem 2 is proven.
Appendix C. Proof of Theorem 3
Therefore, Theorem 3 is proven.
References
- Huynh, N.V.; Hoang, D.T.; Lu, X.; Niyato, D.; Wang, P.; Kim, D.I. Ambient backscatter communications: A contemporary survey. IEEE Commun. Surv. Tutorials 2018, 20, 2889–2922. [Google Scholar] [CrossRef]
- Clerckx, B.; Zhang, R.; Schober, R.; Ng, D.W.K.; Kim, D.I.; Poor, H.V. Fundamentals of wireless information and power transfer: From RF energy harvester models to signal and system designs. IEEE J. Sel. Areas Commun. 2019, 37, 4–33. [Google Scholar] [CrossRef]
- Bletsas, A.; Alevizos, P.N.; Vougioukas, G. The Art of Signal Processing in Backscatter Radio for μW (or Less) Internet of Things: Intelligent Signal Processing and Backscatter Radio Enabling Batteryless Connectivity. IEEE Signal Process. Mag. 2018, 35, 28–40. [Google Scholar] [CrossRef]
- Xu, C.; Yang, L.; Zhang, P. Practical Backscatter Communication Systems for Battery-Free Internet of Things: A Tutorial and Survey of Recent Research. IEEE Signal Process. Mag. 2018, 35, 16–27. [Google Scholar] [CrossRef]
- Mishra, D.; Larsson, E.G. Sum Throughput Maximization in Multi-Tag Backscattering to Multiantenna Reader. IEEE Trans. Commun. 2019, 67, 5689–5705. [Google Scholar] [CrossRef]
- Xu, K.; Qu, Y.; Yang, K. A tutorial on the internet of things: from a heterogeneous network integration perspective. IEEE Netw. 2016, 30, 102–108. [Google Scholar] [CrossRef]
- Zhao, W.; Wang, G.; Fan, R.; Fan, L.S.; Atapattu, S. Ambient Backscatter Communication Systems: Capacity and Outage Performance Analysis. IEEE Access 2018, 6, 22695–22704. [Google Scholar] [CrossRef]
- Yang, G.; Zhang, Q.; Liang, Y.C. Cooperative Ambient Backscatter Communications for Green Internet-of-Things. IEEE Internet Things J. 2018, 5, 1116–1130. [Google Scholar] [CrossRef]
- Qian, J.; Parks, A.N.; Smith, J.R.; Gao, F.; Jin, S. IoT Communications with M -PSK Modulated Ambient Backscatter: Algorithm, Analysis, and Implementation. IEEE Internet Things J. 2019, 6, 844–855. [Google Scholar] [CrossRef]
- Qian, J.; Gao, F.; Wang, G. Signal detection of ambient backscatter system with differential modulation. In Proceedings of the 2016 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Shanghai, China, 20–25 March 2016; pp. 3831–3835. [Google Scholar]
- Correia, R.; Carvalho, N.B. Dual-band high order modulation ambient backscatter. In Proceedings of the 2018 IEEE/MTT-S International Microwave Symposium - IMS, Philadelphia, PA, USA, 10–15 June 2018; pp. 270–273. [Google Scholar]
- Tao, Q.; Zhong, C.; Huang, K.; Chen, X.; Zhang, Z. Ambient Backscatter Communication Systems with MFSK Modulation. IEEE Trans. Wirel. Commun. 2019, 18, 2553–2564. [Google Scholar] [CrossRef]
- Vougioukas, G.; Bletsas, A. Switching frequency techniques for universal ambient backscatter networking. IEEE J. Sel. Areas Commun. 2019, 37, 464–477. [Google Scholar] [CrossRef]
- Yang, G.; Liang, Y.C.; Zhang, R.; Pei, Y. Modulation in the air: Backscatter communication over ambient OFDM carrier. IEEE Trans. Commun. 2018, 66, 1219–1233. [Google Scholar] [CrossRef]
- ElMossallamy, M.A.; Pan, M.; Jantti, R.; Seddik, K.G.; Li, G.Y.; Han, Z. Noncoherent backscatter communications over ambient OFDM signals. IEEE Trans. Commun. 2019, 67, 3597–3611. [Google Scholar] [CrossRef]
- Tao, Q.; Zhong, C.; Lin, H.; Zhang, Z. Symbol Detection of Ambient Backscatter Systems with Manchester Coding. IEEE Trans. Wirel. Commun. 2018, 17, 4028–4038. [Google Scholar] [CrossRef]
- Guo, H.; Liang, Y.-C.; Long, R.; Zhang, Q. Cooperative Ambient Backscatter System: A Symbiotic Radio Paradigm for Passive IoT. IEEE Wirel. Commun. Lett. 2019, 8, 1191–1194. [Google Scholar] [CrossRef]
- Chen, C.; Wang, G.; He, R.; Gao, F.; Li, Z. Semi-blind detection of ambient backscatter signals from multiple-antenna tags. In Proceedings of the 2018 24th Asia-Pacific Conference on Communications (APCC), Ningbo, China, 12–14 November 2018; pp. 570–575. [Google Scholar]
- Zhang, Y.; Gao, F.; Fan, L.; Lei, X.; Karagiannidis, G.K. Backscatter communications over correlated nakagami-m fading channels. IEEE Trans. Commun. 2019, 67, 1693–1704. [Google Scholar] [CrossRef]
- Guo, H.; Zhang, Q.; Xiao, S.; Liang, Y.C. Exploiting Multiple Antennas for Cognitive Ambient Backscatter Communication. IEEE Internet Things J. 2019, 6, 765–775. [Google Scholar] [CrossRef]
- Duan, R.; Jantti, R.; ElMossallamy, M.; Han, Z.; Pan, M. Multi-antenna receiver for ambient backscatter communication systems. In Proceedings of the 2018 IEEE 19th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Kalamata, Greece, 25–28 June 2018; pp. 1–5. [Google Scholar]
- Chen, C.; Wang, G.; Fan, L.; Verde, F.; Guan, H. Detection of ambient backscatter signals from multiple-antenna tags. In Proceedings of the 2018 IEEE 19th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Kalamata, Greece, 25–28 June 2018; pp. 1–5. [Google Scholar]
- Tao, Q.; Zhong, C.; Chen, X.; Wu, Q.; Zhang, Z. Ambient backscatter communication systems with multi-antenna reader. In Proceedings of the 2018 24th Asia-Pacific Conference on Communications (APCC), Ningbo, China, 12–14 November 2018; pp. 245–250. [Google Scholar]
- Zhu, G.; Ko, S.W.; Huang, K. Inference from Randomized Transmissions by Many Backscatter Sensors. IEEE Trans. Wirel. Commun. 2018, 17, 3111–3127. [Google Scholar] [CrossRef]
- Zawawi, Z.B.; Huang, Y.; Clerckx, B. Multiuser Wirelessly Powered Backscatter Communications: Nonlinearity, Waveform Design, and SINR-Energy Tradeoff. IEEE Trans. Wirel. Commun. 2019, 18, 241–253. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, F.; Fan, L.; Lei, X.; Karagiannidis, G.K. Secure Communications for Multi-tag Backscatter Systems. IEEE Wirel. Commun. Lett. 2019, 8, 1146–1149. [Google Scholar] [CrossRef]
- Kang, X.; Liang, Y.C.; Yang, J. Riding on the Primary: A New Spectrum Sharing Paradigm for Wireless-Powered IoT Devices. IEEE Trans. Wirel. Commun. 2018, 17, 6335–6347. [Google Scholar] [CrossRef]
- Lyu, B.; Guo, H.; Yang, Z.; Gui, G. Throughput Maximization for Hybrid Backscatter Assisted Cognitive Wireless Powered Radio Networks. IEEE Internet Things J. 2018, 5, 2015–2024. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Verde, F. Cloud-Aided Cognitive Ambient Backscatter Wireless Sensor Networks. IEEE Access 2019, 7, 57399–57414. [Google Scholar] [CrossRef]
- Kishore, R.; Gurugopinath, S.; Sofotasios, P.C.; Muhaidat, S.; Al-Dhahir, N. Opportunistic Ambient Backscatter Communication in RF-Powered Cognitive Radio Networks. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 413–426. [Google Scholar] [CrossRef]
- Yang, G.; Yuan, D.; Liang, Y.; Zhang, R.; Leung, V.C. Optimal resource allocation in full-duplex ambient backscatter communication networks for wireless-powered iot. IEEE Internet of Things J. 2019, 6, 2612–2625. [Google Scholar] [CrossRef]
- Xiao, S.; Guo, H.; Liang, Y. Resource allocation for full-duplex-enabled cognitive backscatter networks. IEEE Trans. Wirel. Commun. 2019, 18, 3222–3235. [Google Scholar] [CrossRef]
- Guo, J.; Zhou, X.; Durrani, S.; Yanikomeroglu, H. Design of non-orthogonal multiple access enhanced backscatter communication. IEEE Trans. Wirel. Commun. 2018, 17, 6837–6852. [Google Scholar] [CrossRef]
- Gong, S.; Huang, X.; Xu, J.; Liu, W.; Wang, P.; Niyato, D. Backscatter Relay Communications Powered by Wireless Energy Beamforming. IEEE Trans. Commun. 2018, 66, 3187–3200. [Google Scholar] [CrossRef]
- Jia, X.; Zhou, X. Performance Characterisation of Relaying Using Backscatter Devices. CoRR 2019. Available online: http://arxiv.org/abs/1904.01323 (accessed on 25 February 2020).
- Yan, W.; Li, L.; He, G.; Li, X.; Gao, A.; Zhang, H.; Han, Z. Performance analysis of two-way relay system based on ambient backscatter. In Proceedings of the 2018 13th IEEE Conference on Industrial Electronics and Applications (ICIEA), Wuhan, China, 31 May–2 June 2018; pp. 1853–1858. [Google Scholar]
- Lyu, B.; Yang, Z.; Guo, H.; Tian, F.; Gui, G. Relay cooperation enhanced backscatter communication for internet-of-things. IEEE Internet Things J. 2019, 6, 2860–2871. [Google Scholar] [CrossRef]
- Shah, S.T.; Choi, K.W.; Lee, T.; Chung, M.Y. Outage probability and throughput analysis of swipt enabled cognitive relay network with ambient backscatter. IEEE Internet Things J. 2018, 5, 3198–3208. [Google Scholar] [CrossRef]
- Ruttik, K.; Duan, R.; Jäntti, R.; Han, Z. Does ambient backscatter communication need additional regulations? In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Korea, 22–25 October 2018; pp. 1–6. [Google Scholar]
- Guo, H.; Liang, Y.C.; Long, R.; Xiao, S.; Zhang, Q. Resource Allocation for Symbiotic Radio System with Fading Channels. IEEE Access 2019, 7, 34333–34347. [Google Scholar] [CrossRef]
- Long, R.; Guo, H.; Zhang, L.; Liang, Y.C. Full-Duplex Backscatter Communications in Symbiotic Radio Systems. IEEE Access 2019, 7, 21597–21608. [Google Scholar] [CrossRef]
- Zhang, Q.; Zhang, L.; Liang, Y.C.; Kam, P.Y. Backscatter-NOMA: A Symbiotic System of Cellular and Internet-of-Things Networks. IEEE Access 2019, 7, 20000–20013. [Google Scholar] [CrossRef]
- Li, Y.; Jiang, M.; Zhang, Q.; Qin, J. Secure Beamforming in MISO NOMA Backscatter Device Aided Symbiotic Radio Networks. CoRR 2019, 1–4. Available online: http://arxiv.org/abs/1906.03410 (accessed on 25 February 2020).
- Ye, Y.; Li, Y.; Wang, D.; Zhou, F.; Hu, R.Q.; Zhang, H. Optimal Transmission Schemes for DF Relaying Networks Using SWIPT. IEEE Trans. Veh. Technol. 2018, 67, 7062–7072. [Google Scholar] [CrossRef]
- Lyu, B.; Hoang, D.T.; Yang, Z. User Cooperation in Wireless-Powered Backscatter Communication Networks. IEEE Wirel. Commun. Lett. 2019, 8, 632–635. [Google Scholar] [CrossRef]
- Alevizos, P.N.; Bletsas, A. Sensitive and Nonlinear Far-Field RF Energy Harvesting in Wireless Communications. IEEE Trans. Wirel. Commun. 2018, 17, 3670–3685. [Google Scholar] [CrossRef]
- Hoang, D.T.; Niyato, D.; Wang, P.; Kim, D.I.; Han, Z. Ambient Backscatter: A New Approach to Improve Network Performance for RF-Powered Cognitive Radio Networks. IEEE Trans. Commun. 2017, 65, 3659–3674. [Google Scholar] [CrossRef]
- Li, D.; Peng, W.; Liang, Y.C. Hybrid Ambient Backscatter Communication Systems With Harvest-Then-Transmit Protocols. IEEE Access 2018, 6, 45288–45298. [Google Scholar] [CrossRef]
- Kim, S.H.; Kim, D.I. Hybrid Backscatter Communication for Wireless-Powered Heterogeneous Networks. IEEE Trans. Wirel. Commun. 2017, 16, 6557–6570. [Google Scholar] [CrossRef]
- Ma, Z.H.E.; He, C.; Rao, Y.; Jiang, J.; Ma, S.; Gao, F.; Xing, L. Time- and Power-Splitting Strategies for Ambient Backscatter System. IEEE Access 2019, 7, 40068–40077. [Google Scholar] [CrossRef]
- Kong, H.; Flint, I.; Wang, P.; Niyato, D.; Privault, N. Exact performance analysis of ambient RF energy harvesting wireless sensor networks with Ginibre point process. IEEE J. Sel. Areas Commun. 2016, 34, 3769–3784. [Google Scholar] [CrossRef]
- Olver, F.W.J.; Olde Daalhuis, A.B.; Lozier, D.W.; Schneider, B.I.; Boisvert, R.F.; Clark, C.W.; Miller, B.R.; Saunders, B.V. NIST Digital Library of Mathematical Functions. Release 1.0.23 of 2019-06-15. Ann. Math. Artif. Intell. 2003, 38. Available online: http://dlmf.nist.gov/ (accessed on 25 February 2020).
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Elsevier/Academic Press: Amsterdam, The Netherlands, 2007. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).