Abstract
Quantum Cloud Computing is the technology which has the capability to shape the future of computing. In “Platform as a Service (PaaS)” type of cloud computing, the development environment is delivered as a service. In this paper, a multi-user broadcast protocol in network is developed with the mode of one master and N slaves together with a sequence of single photons. It can be applied to a multi-node network, in which a single photon sequence can be sent to all the slave nodes simultaneously. In broadcast communication networks, these single photons encode classical information directly through noisy quantum communication channels. The results show that this protocol can realize the secret key generation and sharing of multiple nodes. The protocol we propose is also proved to be unconditionally secure in theory, which indicates its feasibility in theoretical application.
1. Introduction
The interest in quantum cloud computing (see [1]) has really taken off in the past few years, but, in the future, quantum computers will be quite expensive in nature and will not be available to every one. To solve this problem, a basic idea of cloud computing, which migrates the processing power from customer’s computer to remote Internet servers, is put forward. One of the service models on quantum cloud computing, “Platform as a Service” [2] is proposed for supporting online development environment. Multi-user broadcast, similar to multicast, can be used on cloud platform to communicate between router and users.
Multicast has many applications such as access to business information dissemination, distributed databases, distance teleconferencing, and network learning. Multi-user broadcast protocol can increase quantum network efficiency and conserve its resources. A sender, Alice, wants to send some confidential information to receivers, Bob brothers. They must multicast communicating messages, on the basis of high enough confidentiality and legitimacy of information. As an applied system, its safety is very important.
A simple communication mode is one to one, such as the BB84 protocol [3]. Multiparty communication [4,5,6] has drawn much attention. Matsumoto [7] proposed a quantum-key-distribution protocol that could enable three parties to agree at once on a shared common random bit string in the presence of an eavesdropper without the use of entanglement, which might not be directly applied to the one-to-many multicast communication. Yan [8] proposed a quantum secret sharing protocol between multiparty m members in Group 1 and multiparty n members in Group 2 using a sequence of single photons. Another extension of the theory of various Quantum Cloning Machines () protocols [9,10,11,12,13,14] has been designed and their applications and implementations have been studied, both theoretically and experimentally. The research of quantum cloning and deep application are continuously developing. In our research, we use optimal one to M phase-covariant to implement multi-user broadcast protocol. Theoretically, these , which provide the most dangerous and efficient attack for the BB84 protocol, can be used to multicast message in an optimal fidelity.
The rest of this paper is organized as follows. We show a summary of relevant results concerning multicast addresses and quantum cloning in Section 2. In Section 3, we present multi-user broadcast protocol based on quantum cloning. In Section 4, we analyze optimal fidelity, throughput efficiency and security. Finally, we present our conclusions.
2. Overview
2.1. Multicast Addresses
There are one source and a group of destinations in multicast communication protocol. Figure 1 shows the simple multicast communication network, which depicts a set of quantum network nodes. The node of quantum network is a source sub of quantum data that must be delivered to a group of quantum network nodes, , , …, , …, , respectively. There is more than one quantum network node, but the group does not contain all possible quantum network nodes. This relationship is one to many.
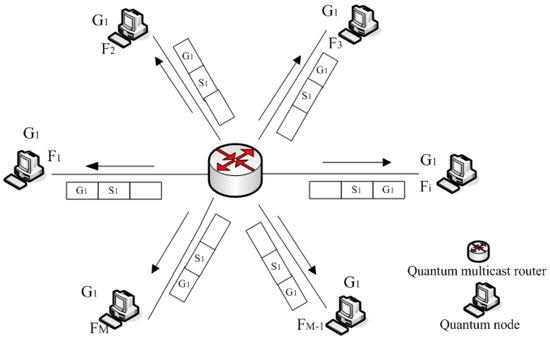
Figure 1.
The simple multicast communication network.
The multicast address is a destination address for a group of quantum network nodes that have joined a multicast group, which is a great help to classical communication of quantum network communication protocol. A packet that uses a multicast address as a destination can reach all members of the group unless there are some filtering restrictions by the quantum network node. It only discusses the multicast addresses in the network layer, in particular the multicast addresses used in the protocol. Multicast addresses for can hardly even be touched. In TCP/IP protocol suites, Class D IP addresses are used as multicast addresses. The range of Class D addresses is 224.0.0.0–239.255.255.255, include 28 variable bits, (more than 268 million) multicast groups. Quantum network nodes may be permanent or transient. The former refers to the fact that the group has a permanently assigned address, rather than that members are permanently assigned to the group. The latter refers to the groups which do not have a permanent assignment to unreserved address.
2.2. Phase-Covariant Quantum Cloning
The no-cloning theorem [15] states that it is impossible to build a quantum copying machine that would perfectly copy arbitrary quantum states. However, we can try to clone a quantum state approximately with the optimal fidelity, or instead, we can try to clone it perfectly with the largest probability. Thus, various quantum cloning machines have been designed for different quantum information protocols. Some well-known quantum cloning machines include universal quantum cloning machine, phase-covariant cloning machine, the asymmetric quantum cloning machine, and the probabilistic quantum cloning machine. For instance, a cloning machine that achieves equal fidelity for every state is called a universal quantum cloning machine (). This problem is equivalent to distributing information to different receivers, and it is natural to require the performance is the same for every input state, since we do not have any specific information about the input state ahead. According to no-cloning theorem, it is expected that the original input state will be destroyed and become as one of the output copies. Because of the different types of copies, there are symmetric and asymmetric . In the past years, much progress has been made in studying quantum cloning machines and their applications and implementations, both theoretically and experimentally. More details about quantum cloning are proposed in [16,17,18].
Here, we mainly discuss the phase-covariant quantum cloning, which has developed on the basis of universal quantum cloning and can produce equally good copies for all input states that lie on the equator of the Bloch sphere. The quantum state
where is an arbitrary phase parameter, is often used as the input qubit of the phase-covariant . For instance, the optimal phase-covariant cloning transformation takes the form [19]
where , A is the initial state of the cloning machine, B is an ancilla state of the system, and C is the blank state. The optimal fidelity of phase-covariant is , which is higher than the fidelity () of .
Then, considering the optimal phase-covariant , one of the cloning transformations is
where is the state of Hilbert space H, is a blank state, and is the state of auxiliary system (ancilla). The is described by the following unitary operator [20]:
in which , is the initial state of the copy machine and the blank copies, and are orthogonal normalized internal states of the . With the help of an ancilla qubit, the optimal fidelity of phase-covariant for equatorial qubits takes the form [18]
which is the decreasing function for M and is better than the fidelity of via numerical computation.
3. Multi-User Broadcast Protocol Based on
3.1. Neighbor Quantum Node Discovery Process
The quantum multicast router starts to discover its neighbors with probe packet messages, which contain the important informations: a list of addresses for neighbors from which the originating router has received probe packet messages, a generation ID used to detect changes in status of neighbors, and so on. After receiving the probe packet messages, the quantum multicast router records the address of the original router and the interface of received messages.
3.2. Neighbor Quantum Node Pruning Process
Probe packet messages are also used as keepalives when a neighbor has been discovered, and then the neighbor node send messages to the quantum multicast router within strict time intervals. If the quantum multicast router does not receive messages from this node after several probes within a specified period of time, the neighbor node will be declared dead. We call this step a neighbor quantum node pruning process, and this node is considered undependable at this time. For example, the pruning process of neighbor node is shown in Figure 2. The quantum multicast router must store the states of all nodes after each pruning process. If necessary, nodes and the router need to repeatedly send and receive messages in this process as many times as possible to complete the pruning process of quantum nodes.
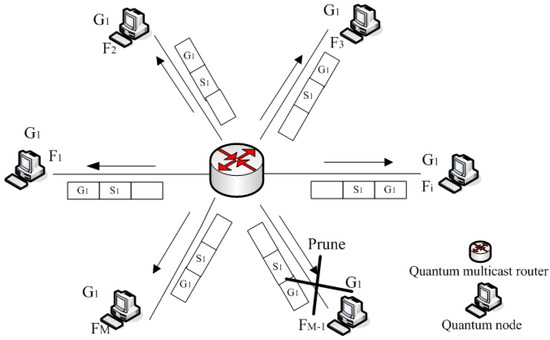
Figure 2.
Pruning process of an undependable neighbor quantum node.
3.3. Group Routing Tables Building Process
The quantum multicast router needs to collect members’ information and share it with other multicast routers, and then construct group routing table containing group members’ information. The graph of quantum nodes and links is called tree, so the quantum multicast router can be regarded as the root node. All other nodes can only be reached from the root node through a single path. Multicast communication means that a sender sends messages to a group of recipients who are members of the same group. Since a copy of the message is sent by the sender and then copied and forwarded by the router, each multicast router needs to know the list of groups.
The group routing tables carry four core data: the quantum nodes identity, the list of links, a sequence number, and the age. The quantum nodes identity and the list of links are needed to make the quantum topology. The sequence number distinguishes new routing tables from old ones. The age prevents old routing tables from remaining in the domain for a long time. When the topology of a domain changes, any quantum nodes in the domain are quickly notified by the router to update their topology.
3.4. Multicast Date Packet Communication on Quantum Cloning Process
We apply the phase-covariant cloning machine to multicast communication (in Figure 3). For each input single photons, we use a unitary transformation matrix A to prepare the input state on the equator of the Bloch sphere:
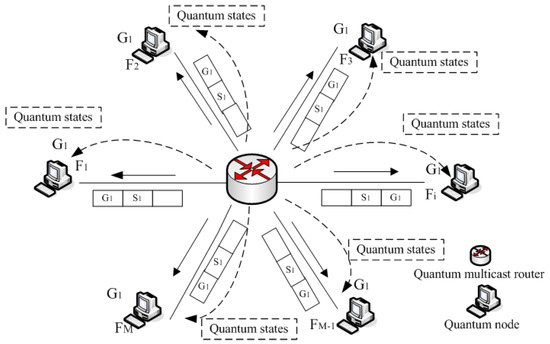
Figure 3.
Multicast quantum cloning process.
The quantum multicast router encodes these strings as a block of , and sends to by quantum cloning via the quantum communication channel. For simplicity, we assume that the quantum channel is noiseless. The quantum multicast router transmits through quantum channel to construct .
The quantum multicast router acts on an input state as follows:
where represents the internal state of with for all , and the equatorial qubits take the forms
Quantum correlation is the key concept for the quantum computation, quantum processing, and quantum information. Entanglement is a special case of quantum correlation. It is a property of correlations between two or more quantum systems. This nonlocal nature of entanglement has also been identified as an essential resource for many novel tasks. The preparation of entangled states in different physical systems has been widely studied and constitutes an essential step in many quantum information processing and transmission tasks [21,22,23]. For Alice and M Bob brothers, we assume that they all share a multi-particle entangled state , and a choice of with these properties in the following M-qubit state:
where and are the optimal cloning states given by Equation (4), and turns into
The tenser product of with the equator qubits held by the -qubit state of Alice. Alice performs a joint measurement of the system by using Bell measurement [24], where the four Bell states are defined as usual as the following
Once one of the Bell states is obtained, we can recover the correct state by exploiting the symmetries of states and under the unitary transformation. Consider three Pauli matrices; the unitary transformation can be expressed as
The quantum multicast router measures Bell state of A, and the router and each nodes can transmit qubit in the following four forms as or . When is obtained, the unitary transformation is corresponding to the symbol “+”(“–”) in the equations. When is obtained, the unitary transformation is corresponding to the symbol “+”(“–”). After these operations, the secret key is transmitted to the server, and the quantum multicast router and each node releases part of the quantum information. If the test is correct, the communication station () is a legitimate user. Otherwise, there must be illegal eavesdroppers, which we discuss in the next section. In this process, quantum multicast router transmits classical information through Ethernet addresses. The main problem below is to change the three right-most bytes of the multicast IP address to hexadecimal. If the left-most number is greater than or equal to 8, subtract 8 from the left-most number. After the system gets the result, add the result to the starting Ethernet multicast address. Thus, the multicast date packet communication on quantum cloning process has completed successfully.
3.5. Selective Repeating Process
In this protocol model, the multicast router node acts as a key management system and authenticates the communication users in communication. The multicast router manages the security key for the communication users and authenticates the identity of users by arbitrating the quantum signature using the shared quantum state [25]. In the process of communication, the multicast router node conducts authentication occasionally to prevent the user from being attacked.
Ideally, we assume that each photon emission is perfect. If the information transmission fails due to channel loss or eavesdropping, the multicast router will return a negative acknowledgment () to the nodes. After receiving the , the node will start the selective repeating process, thus ensuring the security and reliability of the communication. The strings are transmitted continuously as a block of , the quantum multicast router resends (or repeats) only those codewords that are negatively acknowledged. Since the strings must be delivered to the user in correct order, a buffer must be provided at the receiver to store the error-free qubits of received qubits after error detection. When the first negatively acknowledged strings are successfully received, the receiver releases the error-free qubits in consecutive order until the next erroneously received qubits are encountered. Sufficient qubits receiver buffers must be provided, otherwise the qubits buffers may overflow and quantum data may be lost.
4. Analysis
4.1. Analysis of Quantum Bit Error Rate and Secure Key Rate
The Quantum Bit Error Rate () is defined as the number of wrong bits to the total number of received bits and is normally in the order of a few percent. In the following, we use it expressed as a function of rates:
where the sifted key corresponds to the cases in which Alice and Bob made compatible choices of bases, hence its rate is half that of the raw key. In a practical quantum key distribution system, e.g. the protocol, after attenuation and sifting, the sifted key generation rate is given by [26]
where the factor q (, typically 1 or ) must be introduced for some phase-coding setups in order to correct for noninterfering path combinations, is the pulse rate, is the mean number of photon per pulse, is the probability of a photon to arrive at the analyzer, and is the probability of the photon being detected.
The secure key rate in our protocol is the quantum communication rate of the whole system. This depends on the rate of key distribution when each root node communicates with its children, that is the rate of the sifted key generation.
4.2. Analysis of Optimal Fidelity
The fidelity is widely used within the quantum computation and quantum information community, and we discuss the quantum multi-user broadcast protocol for the “Platform as a Service” model. In our study, the algorithm discussed above is sufficient to complete each step of the computation with higher fidelity than phase-covariant by Equation (5).
The quantum multicast router obtains measurement outcome for , and publicly announces the results. , , …, , …, carry out the unitary transformation separately on their qubits. The final states of qubits for equal to the original state . We now wish that the optimal phase-covariant cloning machine can be achieved. Let us see fidelity, which is found to take the form
where
4.3. Analysis of Throughput Efficiency
Next, we discuss the throughput efficiency which is defined as the ratio of the average number of information digits successfully accepted by the receiver per unit of time to the total number of digits that could be transmitted per unit of time. Suppose the simple case of the communication protocol, and the sender continuously sends codewords to the receiver and only resends those negatively acknowledged codewords. First, three probabilities are defined: , and , where . is the probability of receiving no error message, is the probability of receiving detectable error pattern, and is the probability of receiving undetectable error pattern. Then, the probability of receiving vector being accepted by the receiver is .
The average number of retransmissions (including original transmissions) for a codeword to be successfully received by the receiver is
Finally, the throughput of sending n codewords successfully is . Thus, the throughput efficiency depends on the channel error rate only.
4.4. Analysis of Security under Typical Attack
The Security of this broadcast protocol depends on every process of communication between one source and a group of destinations. The protocol is divided into five parts as neighbor quantum node discovery process, neighbor quantum node pruning process, group routing tables building process, multicast date packet communication on quantum cloning process, and selective repeating process. Conventional data communication is used in processing classical information, and cleartext can be transferred through quantum channel. There is no information revealed. As for the vector attack, according to quantum no-cloning theorem, the attacker cannot accurately copy quantum nodes for DOS attack. If the attacker generates illegal users to prevent information transmission, it will be found in the authentication process by the key management system and the illegal communication will be terminated.
4.4.1. Attack via Direct Measurement
One can analyze the security of multicast data packet communication via direct measurement. receives the random qubits, who measures each qubits in the basis or at random. receives , where describes the quantum operation due to the combined effect of the channel and eavesdropper’s (Eve) actions. then publicly announces this fact. For now, each of the nodes has its own states described by separate density matrices. Note that, at this point, since did not reveal b, Eve has no knowledge of what basis she should have measured to eavesdrop in the communication. At best, she can only guess. If her guess were wrong, then she would have disturbed the state received by . Moreover, whereas in reality the noise may be partially due to the environment in addition to Eve’s eavesdropping, it does not help Eve to have complete control over the channel. Thus, Eve is entirely responsible for .
When the quantum multicast router first receives a multicast packet from , the packet check is performed, using the routing table to verify that the packet arrived on the right interface for the packet’s source. If the packet arrived on any other interface, drop it.
4.4.2. Attack via Ancilla Particle
We suppose Eve intercepts the particle sent by Alice, which will be entangled with an ancilla prepared by Eve. The unitary transformation that is implemented on Alice’s particle E does not change the state of single photons [27].
where the unitary transformation E can be written as
where , , and . Thus, the probability of Eve being detected is
the eavesdropping brings a certain amount of error rate, and it must be detected.
According to the information theory, the amount of maximum accessible information in quantum system is limited by limit:
where is the von Neumann entropy of state , , and is a state prepared in probability . If communicating parties prepare states , , and , then the information entropy . Thus the von Neumann entropy of Eve [27] is . It seems that Eve cannot obtain the complete information of photons in our protocol.
5. Conclusions
We describe a multi-user broadcast protocol in network for the one-to-many multicast communication network including the master and N slave mode using a sequence of single photons. This protocol might be useful in practice because it guarantees multicast information robustness. In the one-to-many multicast communication mode, creates () random bits and multicasts information to . and publicly announce the selection of the random measurement basis. There are at least 2n bits left, and if not, the protocol will be aborted. Meanwhile, the Calderbank–Shor–Steane () coding theory can be employed for correcting the errors introduced by the noisy communication channel. Therefore, the nodes compute the related information, and finally obtains the correct key. The commercial success of quantum key distribution for the generation of a private shared secret key motivates this investigation. The protocol is also proved to be unconditionally secure in theory, which indicates its feasibility in theoretical application. For future study, it may be significant to investigate the performance of our protocol for encoding secret classical messages.
In our proposed protocol, the photon is the carrier of information. Quantum information is encoded in the flying photon bit, and the transmit power is related to the performance of the transmitter module. In practical quantum communication, the transmission distance is limited due to the imperfection of the transmitter module and the detection module, which is a general problem in all practical quantum communication systems.
This protocol mainly establishes the quantum multi-user communication model without considering channel noise. In the practical noisy channel, we can use the quantum error-correction code to correct the error generated in the transmission process. Commonly used quantum error-correction codes are Quantum Stabilizer Code (QSC) and Quantum Low-Density Party-Check Code (QLDPC) [28].
One thing to point out is that we concentrate only on closed systems where the decoherence and dissipations are neglected. It is well-known that in open quantum systems the Hamilton operator is non-Hermitian [29,30]. The dynamical behavior of open quantum systems plays a key role in many applications of quantum mechanics, such as the environment-induced decay of quantum coherence, relaxation in many-body systems, and applications in condensed matter theory, quantum transport, quantum chemistry, and quantum information. If the decoherence and dissipation of the open systems are considered, the protocol based on quantum error correction coding needs to be studied in the future in more detail.
Author Contributions
Conceptualization, H.M.; methodology, H.M. and P.S.; validation, N.L. and S.W.; investigation, S.W. and Z.L.; writing—original draft preparation, P.S. and H.M.; writing—review and editing, P.S. and N.L.; and visualization, M.R.
Funding
This work was supported by the Project of Shandong Province Higher Educational Science and Technology Program (No. J18KZ012), the National Natural Science Foundation of China (Nos. 61772295 and 11975132), and the Natural Science Foundation of Shandong Province (No. ZR2016FB09).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Singh, H.; Sachdev, A. The Quantum way of Cloud Computing. In Proceedings of the 2014 International Conference on Reliability Optimization and Information Technology (ICROIT), Faridabad, India, 6–8 February 2014; pp. 397–400. [Google Scholar]
- Keller, E.; Rexford, J. The ”Platform as a Service” Model for Networking. In Proceedings of the 2010 Internet Network Management Workshop/Workshop on Research on Enterprise Networking (INM/WREN), San Jose, CA, USA, 27 April 2010; pp. 95–108. [Google Scholar]
- Bennett, C.H.; Brassard, G. WITHDRAWN: Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Bangalore, India, 9–12 December 1984; p. 175. [Google Scholar]
- Loukopoulos, K.; Browne, D.E. Secure multiparty computation with a dishonest majority via quantum means. Phys. Rev. A 2010, 81, 062336. [Google Scholar] [CrossRef]
- Ma, H.; Chen, B.; Guo, Z.; Li, H. Development of quantum network based on multiparty quantum secret sharing. Can. J. Phys. 2008, 86, 1097–1101. [Google Scholar] [CrossRef]
- Zhou, N.R.; Cheng, H.L.; Gong, L.H.; Li, C.S. Three-Party Quantum Network Communication Protocols Based on Quantum Teleportation. Int. J. Theor. Phys. 2014, 53, 1387–1403. [Google Scholar] [CrossRef]
- Matsumoto, R. Multiparty quantum-key-distribution protocol without use of entanglement. Phys. Rev. A 2007, 76, 062316. [Google Scholar] [CrossRef]
- Yan, F.L.; Gao, T. Quantum secret sharing between multiparty and multiparty without entanglement. Phys. Rev. A 2005, 72, 012304. [Google Scholar] [CrossRef]
- Woodhead, E. Quantum cloning bound and application to quantum key distribution. Phys. Rev. A 2013, 88, 012331. [Google Scholar] [CrossRef]
- Iblisdir, S.; Acín, A.; Cerf, N.J.; Filip, R.; Fiurášek, J.; Gisin, N. Multipartite asymmetric quantum cloning. Phys. Rev. A 2005, 72, 042328. [Google Scholar] [CrossRef]
- Bužek, V.; Braunstein, S.L.; Hillery, M.; Bruß, D. Quantum copying: A network. Phys. Rev. A 1997, 56, 3446–3452. [Google Scholar] [CrossRef]
- Andersen, U.L.; Josse, V.; Leuchs, G. Unconditional Quantum Cloning of Coherent States with Linear Optics. Phys. Rev. Lett. 2005, 94, 240503. [Google Scholar] [CrossRef]
- Scarani, V.; Iblisdir, S.; Gisin, N.; Acín, A. Quantum cloning. Rev. Mod. Phys. 2005, 77, 1225–1256. [Google Scholar] [CrossRef]
- Fang, B.L.; Song, Q.M.; Ye, L. Realization of a universal and phase-covariant quantum cloning machine in separate cavities. Phys. Rev. A 2011, 83, 042309. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Fan, H.; Matsumoto, K.; Wang, X.B.; Wadati, M. Quantum cloning machines for equatorial qubits. Phys. Rev. A 2001, 65, 012304. [Google Scholar] [CrossRef]
- Bruß, D.; Cinchetti, M.; Mauro D’Ariano, G.; Macchiavello, C. Phase-covariant quantum cloning. Phys. Rev. A 2000, 62, 012302. [Google Scholar] [CrossRef]
- Fan, H.; Wang, Y.N.; Jing, L.; Yue, J.D.; Shi, H.D.; Zhang, Y.L.; Mu, L.Z. Quantum cloning machines and the applications. Phys. Rep. 2014, 544, 241–322. [Google Scholar] [CrossRef]
- Fan, H.; Imai, H.; Matsumoto, K.; Wang, X.B. Phase-covariant quantum cloning of qudits. Phys. Rev. A 2003, 67, 022317. [Google Scholar] [CrossRef]
- Gisin, N.; Massar, S. Optimal Quantum Cloning Machines. Phys. Rev. Lett. 1997, 79, 2153–2156. [Google Scholar] [CrossRef]
- Eleuch, H. Quantum Trajectories and Autocorrelation Function in Semiconductor Microcavity. Appl. Math. Inf. Sci. 2009, 3, 185–196. [Google Scholar]
- Mohamed, A.B.; Eleuch, H. Non-classical effects in cavity QED containing a nonlinear optical medium and a quantum well: Entanglement and non-Gaussanity. Eur. Phys. J. D 2015, 69, 191. [Google Scholar] [CrossRef]
- Berrada, K.; Abdel-Khalek, S.; Eleuch, H.; Hassouni, Y. Beam splitting and entanglement generation: Excited coherent states. Quantum Inf. Process. 2013, 12, 69–82. [Google Scholar] [CrossRef]
- Lütkenhaus, N.; Calsamiglia, J.; Suominen, K.A. Bell measurements for teleportation. Phys. Rev. A 1999, 59, 3295–3300. [Google Scholar] [CrossRef]
- Zeng, G.; Keitel, C.H. Arbitrated quantum-signature scheme. Phys. Rev. A 2002, 65, 042312. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145–195. [Google Scholar] [CrossRef]
- Cao, Z.W.; Zhao, G.; Zhang, S.H.; Feng, X.Y.; Peng, J.Y. Quantum secure direct communication protocol based on the mixture of Bell state particles and single photons. Acta Phys. Sin. 2016, 65, 230301. [Google Scholar]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information, 1st ed.; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Eleuch, H.; Rotter, I. Resonances in open quantum systems. Phys. Rev. A 2017, 95, 022117. [Google Scholar] [CrossRef]
- Eleuch, H.; Rotter, I. Open quantum systems and Dicke superradiance. Eur. Phys. J. D 2014, 68, 74. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).