Abstract
To provide secure communication, the authentication-and-key-agreement scheme plays a vital role in multi-server environments, Internet of Things (IoT), wireless sensor networks (WSNs), etc. This scheme enables users and servers to negotiate for a common session initiation key. Our proposal first analyzes Amin et al.’s authentication scheme based on RSA and proves that it cannot provide perfect forward secrecy and user un-traceability, and is susceptible to offline password guessing attack and key-compromise user impersonation attack. Secondly, we provide that Srinivas et al.’s multi-server authentication scheme is not secured against offline password guessing attack and key-compromise user impersonation attack, and is unable to ensure user un-traceability. To remedy such limitations and improve computational efficiency, we present a multi-server two-factor authentication scheme using elliptic curve cryptography (ECC). Subsequently, employing heuristic analysis and Burrows–Abadi–Needham logic (BAN-Logic) proof, it is proven that the presented scheme provides security against all known attacks, and in particular provides user un-traceability and perfect forward security. Finally, appropriate comparisons with prevalent works demonstrate the robustness and feasibility of the presented solution in multi-server environments.
1. Introduction
With the recent advancements in Internet and communication technology and the growing demand for sharing multiple data resources, secure and efficient communication between the involved stakeholders has become more essential in areas such as e-commerce, telecare medical information, distributed cloud storage systems, etc. Obviously, privacy protection has emerged as a vital issue for secure and trusted communication. For secure and effective communication over an insecure network, the involved parties are required to negotiate on a common session key beforehand. For such negotiations, authentication-and-key-agreement protocols serve as the only solution. The first password authentication with insecure communication was established by Lamport in 1981 [1]. Later, Frank et al. [2] presented an authentication protocol based on hypertext transport protocol in 1991. However, Yang et al. [3] identified that Frank’s proposal was insecure and provided an improved solution in 2005. In order to present a secure and efficient authentication and key agreement protocol, in the following decade, many single-, two-, and three-factor authentication protocols were constructed while employing RSA, discrete logarithm over general groups, elliptic curve cryptography (ECC), chaotic maps [4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22], etc. However, some security limitations are prevailing in these protocols. By analyzing a large number of authentication protocols, we found that such shortcomings are resulted due to either improper usage of the cryptographic primitives or design defects of the protocols.
In 2011, Awasthi et al. [23] showed that the protocol of Shen et al. [24] is prone to user impersonation attack. To remedy impersonation attack, Awasthi et al. put forward a refined time stamp-based authentication-and-key-agreement protocol. However, in that protocol, the adversary can easily obtain smart card and identity parameters through an open channel. In 2014, Huang et al. [25] pointed out that the scheme presented by Awasthi et al. is unable to resist against user impersonation attack, and overlooks the password updation stage. Moreover, we remark that Awasthi et al.’s scheme also fails to ensure user anonymity. Huang et al. proposed an enhanced time stamp-based two-factor remote user authentication protocol while incorporating RSA, and claimed that the scheme can resist various attacks. However, Amin et al. [26] proved that the proposal of Huang et al., is susceptible to impersonation, offline password guessing, and insider attacks, while also having an inefficient password updation stage. Keeping in view the limitations of Huang et al.’s proposal, Amin et al. presented an authentication-and-key-agreement mechanism based on RSA.
In a multi-server environment, users interact with multiple servers. To login with different identities and passwords in such an environment is troublesome for the users. To eliminate this problem, first, users and multiple servers are registered at the registration center (RC). Subsequently, users can make an authentication-and-key-agreement with multiple servers by utilizing the unique identity and password pair. A proposed architecture of the multi-server authentication system is depicted in Figure 1. In 2013, Pippel et al. [27] employed smart cards to present a robust multi-server authentication protocol and proved it to be resistant against various known attacks. In a subsequent work, Li et al. [28] identified that the protocol presented by Pippel et al. is unable to provide correct authentication. Moreover, it cannot withstand impersonation attack and insider attack. Afterwards, Li et al. designed an improved smart card authentication protocol and proved that it can withstand perfect forward secrecy, stolen smart-card attack, offline password guessing attack, and so on. Even so, Srinivas et al. [29] provided that Li et al.’s scheme is unable to resist insider attack, denial-of-service attack, and stolen smart-card attack, and cannot provide perfect forward secrecy. However, we remark that Li et al.’s scheme addresses perfect forward secrecy. As a solution, Srinivas et al. presented an improved two-factor authentication scheme for the same multi-server architecture with reduced computation and communication cost while claiming that their protocol is susceptible to various known attacks. To the best of our knowledge, most of the schemes cannot provide perfect forward secrecy and user un-traceability, and are susceptible to key-compromise user impersonation attack and offline password guessing attack. More precisely, once an authentication-and-key-agreement mechanism fails to ensure user un-traceability, the user’s entire whereabouts are exposed to the attacker. This provides a great deal of convenience for attackers to carry out more attacks. This proposal takes the schemes of Amin et al. and Srinivas et al. as examples to depict how an adversary traces the legal user, effectively guesses the correct password, or succeeds in obtaining the session key. These security flaws usually exist in wireless sensor networks (WSNs) as well [30,31,32,33,34,35,36,37,38,39,40]. Moreover, The methods of attacking and designing we use are very useful and effective in analyzing similar vulnerabilities and designing new protocols in WSNs, respectively.
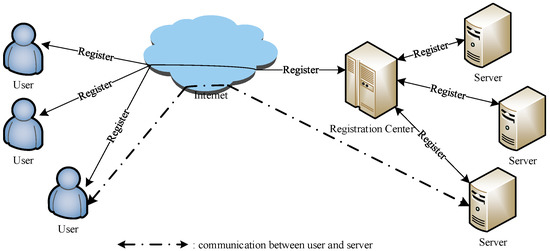
Figure 1.
The architecture of the multi-server authentication system.
1.1. Contributions
The key contributions of our proposal are listed as follows: (1) We prove that Amin et al.’s protocol fails to ensure perfect forward secrecy and user un-traceability, and is susceptible to key-compromise user impersonation attack and offline password guessing attack. (2) It is proven that Srinivas et al.’s scheme fails to ensure user un-traceability, and is prone to key-compromise user impersonation attack and offline password guessing attack. (3) To overcome these limitations, we design a two-factor authentication-and-key-agreement scheme for multi-server architecture while incorporating ECC. (4) The presented scheme ensures perfect forward secrecy, user anonymity, and un-traceability. Moreover, it provides security against major attacks, including impersonation attack, offline password guessing attack, key-compromise user impersonation attack, etc. (5) The security analysis using Burrows–Abadi–Needham logic (BAN-Logic) provides that the proposed protocol ensures secured mutual authentication between a remote user and server.
1.2. Outline of This Paper
The remaining contents of the proposal are organized as follows: cryptographic primitive and attacker model are detailed in Section 2. The scheme of Amin et al., and its cryptanalysis are presented in Section 3 and Section 4, respectively. Section 5 and Section 6 provide the scheme of Srinivas et al., and its cryptanalysis, respectively. The improved version of the proposed scheme is provided in Section 7. The heuristic security analysis and BAN-Logic are presented in Section 8 and Section 9, respectively. Section 10 details the security and performance comparisons. Finally, Section 11 contains the concluding remarks.
2. Preliminary
We take advantage of ECC to present a two-factor authentication scheme. The following section briefly introduces the collision-resistant cryptographic one-way hash function as well as some computationally infeasible problems, including the elliptic curve computational Diffie–Hellman Problem (ECCDHP) and the elliptic curve discrete-logarithm problem (ECDLP). Table 1 depicts some notations and descriptions that are used in the proposed scheme.

Table 1.
Notations and their descriptions.
2.1. Collision-Resistant One-Way Hash Function
Basically, the one-way hash function requires an input in the form of an arbitrary length binary string , and yields a string in binary form . In brief terms, a cryptographic collision-resistant one-way hash function ensures the following:
- Given , it is difficult to determine the input within polynomial time.
- It is difficult to determine such that , where .
- It is difficult to uncover a pair , such that and could hold.
2.2. Intractable Problems in ECC
The elliptic curve equation over a finite field in ECC takes the form , where and [41].
- ECDLP: The elliptic curve discrete-logarithm problem over elliptic curve refers to computing from for given .
- ECCDHP: The elliptic curve computational Diffie–Hellman problem over elliptic curve refers to computing , given points .
2.3. Adversary Model
According to [18,42,43,44,45,46,47], the capacities of in authentication and key agreement schemes, which are used in cryptanalysis of Amin et al.’s scheme, Srinivas et al.’s scheme, and our proposed scheme, are listed as follows:
- is able to intercept, block, delete, modify, and resend the message contents through an open channel.
- Because identity and password have low entropy, can enlist all pairs of simultaneously from within polynomial time, where and refer to the space of passwords and identities in and , respectively.
- can either acquire of the via malicious device or reveal the information from , but is not permitted to use both methods together.
- can acquire a server’s private key while evaluating forward secrecy or key-compromise user impersonation attack.
- has the ability to reveal all parameters of the smart card when assessing stolen smart-card attack, offline password guessing attack, impersonation attack, forward secrecy, etc.
3. Brief Review of Amin et al.’s Proposal
This section provides a brief review of Amin et al.’s [26] authentication scheme for Session Initiation Protocol (SIP). The scheme presented by the authors comprises four stages: initialization, registration, login and authentication, and password updation. We omit the description of the password updation stage.
3.1. Initialization
S takes two large primes p and q as secret parameters to calculate as a public parameter. Afterwards, S chooses a prime e to obtain d by computing , such that .
3.2. Registration
- enters an identity and password . Subsequently, randomly picks up a number r and calculates . Afterwards, transmits the registration request message to S via secure medium.
- Upon receiving the request message from the new user , S calculates , , and . Afterwards, S stores the contents in a new card and sends to .
- Once obtaining , stores u into .
3.3. Login and Authentication
- To start the session with the S, inserts into a card reader and inputs their login details, including and . Subsequently, calculates , and . Afterwards, it verifies the value of . In case of invalid values, the session is ended. Otherwise, randomly chooses a number , the current time stamp , and calculates and . Next, transmits the login request message to S.
- Upon receiving the login request from , S verifies the time stamp corresponding to the current time stamp . In the case of valid time stamp , it continues to execute the following steps. Otherwise, it aborts the session. Afterwards, S decrypts to obtain and then checks whether and . Afterwards, S checks . After finishing this verification, S randomly selects a number and computes . Finally, S transmits the respond message to via public channel.
- Once receiving the response message from S, checks the validity of . After finishing the verification, checks whether and verifies . If it holds, accepts the response message. Finally, S and calculate the session key:
4. Limitations of Amin et al.’s Scheme
According to the adversary model presented in Section 2.3, in the following, we prove that Amin et al.’s scheme is unable to provide user un-traceability and perfect forward secrecy, and is prone to key-compromise user impersonation attack and offline password guessing attack.
4.1. User Un-Traceability
Observing the protocol of Amin et al., it can be found that is transmitted during the login request message stage. However, is a fixed value in , unless changes their password during the password updation stage. Usually, the user does not change their password after every session. Therefore, can be traced by the adversary using . Hence, Amin et al.’s protocol does not ensure user un-traceability.
4.2. Offline Password Guessing Attack
Offline password guessing attack is the main limitation for most of the presented proposals addressing authentication. If somehow steals the of and embeds the data in it, then the adversary can perform the following steps to obtain and of .
- From the password dictionary space , the adversary randomly chooses the password , and picks up the identity from the identity dictionary space .
- calculates .
- calculates .
- calculates .
- To check the correctness of and , examines whether , where belongs to of .
- If the aforementioned equality holds, ’s guess results as successful. Otherwise, repeats Steps 1–5 until it obtains the correct password and identity of .
From the aforementioned procedure, we find that the computational time complexity of offline password guessing attack is where , and refer to the number of , the number of , and the performing time of hash function , respectively. According to [48,49,50], usually, . Therefore, the aforementioned attack is very efficient. Hence, Amin et al.’s protocol is unable to resist offline password guessing attack. Actually, the verified data are stored in ’s smart card, which is the main reason for the success of the above attack. By computing , the smart card is able to check the correct login of the legal user. Moreover, it also gives the chance to guess password and identity. Since the identity and password have low entropy in such scenarios, can guess them successfully within polynomial time.
4.3. Lacks of Perfect Forward Secrecy
Assume that the obtains the long term private key d of S and eavesdrops the transmitted message . Having that information, can easily calculate two key random numbers . undergoes the following procedure to compute between and S.
- The adversary computes to obtain .
- computes .
- computes .
- computes .
The computational time overhead of the aforementioned attack is , where and are the running time of modular exponentiation and exclusive-or operation, respectively. Therefore, the protocol of Amin et al. does not ensure perfect forward secrecy. This problem can be solved by adding an operation of public key cryptography, which slightly increases the computation load. However, it is a feasible approach in terms of the trade-off between security and practicality.
4.4. Key-Compromise User Impersonation Attack
If the long-term private key d of S is revealed to the adversary in Amin et al.’s protocol, can impersonate the legitimate user to S as follows:
- computes , and subsequently calculates and .
- obtains the login request message of , randomly selects a number , and computes Afterwards, transmits the forged request message to S.
- Upon receiving the forged message, obviously S can verify it successfully. Thus, S randomly provokes a number , and computes and . Finally, S sends to .
- Upon receiving the response from S, calculates . Finally, the server S believes that is the common session key between a legitimate user and itself. However, in actual terms, acts as .
Therefore, Amin et al.’s protocol is unable to resist key-compromise user impersonation attack.
5. Review of Srinivas et al.’s Scheme
The following section reviews Srinivas et al.’s protocol [29] comprising four steps: initialization, registration, login and authentication, and password updation stage.
5.1. Initialization
The trusted registration center during this stage selects a 1024-bit large prime p, generates , chooses a one-way hash function , and randomly picks a number as the master secret key.
5.2. Registration Process
5.2.1. Server Registration
chooses a unique identity and sends to through a secure-medium. Upon receiving , calculates , and sends to through a secure medium.
5.2.2. User Registration
First, a new user selects , , and randomly chooses a number . Subsequently, the user calculates and sends to . Upon receiving the registration request, calculates Afterwards, sends a new smart card containing through a secure medium. Finally, upon receiving from , inputs to .
5.3. Login and Authentication
- inserts into a card reader and inputs and . checks , and . Afterwards, randomly generates a number a, chooses the current time stamp , and calculates and . Subsequently, transmits the login request message to .
- receives the request message from , figures out , and checks . terminates the login request if the expression does not hold. Apart from that, a random number b and calculates . Afterwards, picks the current time stamp and computes and . Finally, sends the response message to .
- On receiving the response message, figures out , and Subsequently, checks and terminates this login request if the expression does not hold. Otherwise, calculates and transmits it to through a public channel.
- Upon acquiring , computes and checks . After successful accomplishment of all steps, and believe that they have the common session key .
5.4. Password Updation Stage
After the authentication session between and targeted server , inputs , and a new password . Subsequently, calculates and , where . Afterwards, replaces with
6. Limitations of Srinivas et al.’s Protocol
According to the adversary model presented in Section 2.3, we present some possible attacks for Srinivas et al.’s protocol, including key-compromise user impersonation attack, offline password guessing attack, and lack of user un-traceability. The details are described in the following sections.
6.1. Offline Password Guessing Attack
Assume that extracts the information of by side-channel attack. Now, can execute the following steps to get the correct identity and password of user in polynomial time.
- From the password dictionary space , the adversary chooses the password , and picks up the identity from the identity dictionary space .
- computes .
- computes .
- computes .
- computes .
- verifies whether , where is acquired from smart card of .
- If it holds, then and is the correct identity and password pair. Otherwise, repeats Steps 1–6 until it obtains the correct identity and password of .
We determine the computational time complexity of the aforementioned attack algorithm. That is,
where , and are the number of , the number of , and the time to compute hash function , respectively. According to [48,49,50], usually, . Therefore, the offline password guessing attack is very efficient. Thus, Srinivas et al.’s protocol is not resistant against offline password guessing attack.
6.2. Lack of User Un-Traceability
It can be observed from Srinivas et al.’s protocol that the attacker can get transmitted within the login request message. Since is a fixed value, where and are invariable, unless the user changes their password during the password updation stage, any adversary can trace the user by using . Therefore, Srinivas et al.’s protocol cannot provide user un-traceability.
6.3. Key-Compromise User Impersonation Attack
If the long-term private key of is revealed to in Srinivas et al.’s protocol, then can adopt the following actions to impersonate the legitimate to .
- intercepts the login request message of , and calculates .
- randomly selects a number to compute . Afterwards, sends the forged login request message to .
- Obviously, the forged message can pass the verification of . Thus, randomly chooses a number to compute . Subsequently, chooses the current time stamp to compute and . Finally, sends the response message to .
- On receiving the response message, figures out Subsequently, calculates and transmits it to through a public channel.
- receives , computes , and checks whether . After finishing all steps successfully, believes that it holds the common session key with . Actually, however, plays as . Thus, successfully impersonated to under the condition that the long-term private key of the server was leaked.
Therefore, Srinivas et al.’s protocol is prone to key-compromise user impersonation attack.
7. The Improved Scheme
The following section presents an improved mutual authentication protocol that gets motivation from Srinivas et al.’s [29] scheme to incorporate ECC. The presented solution not only remedies the limitations of Amin et al.’s [26] and Srinivas et al.’s [29] schemes, but also ensures mutual authentication and is resistant to many known attacks. The presented scheme comprises five stages: initialization, server registration, user registration, authentication-and-key-agreement, and password updating. The notations of the presented scheme are listed in Table 1. Figure 2, Figure 3 and Figure 4 depict the registration and authentication process of the proposed protocol.
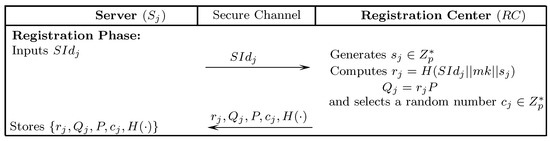
Figure 2.
Server registration.
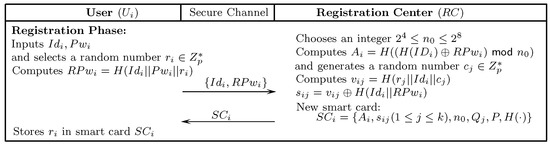
Figure 3.
User registration.

Figure 4.
Login and authentication.
7.1. Initialization
chooses an elliptic curve from , where p is a 160-bit-long prime number. Afterwards, selects a fixed point , and one-way hash function , and randomly picks a number as .
7.2. Server Registration
- chooses an identity and transmits it to via a secure-medium.
- receives the registration message, randomly generates a number , and computes Subsequently, randomly generates a number for . Finally, sends to through secure-medium.
- stores in its database.
7.3. User Registration
After the successful registration of with , can communicate with any server .
- selects , , and randomly generates a number to compute . Afterwards, transmits the registration request message to through a secure medium.
- Upon receiving the registration message, randomly generates numbers , and computes the following: , where . Afterwards, inserts , into a new . and sends it to through secure-medium.
- stores in .
7.4. Login and Mutual Authentication
initiates the login and authentication request for sending to by performing the following steps.
- inserts into a card reader and inputs , . computes , and subsequently calculates . Afterwards, inspects the correctness of while comparing it with the value of sorted in . If , and are validated. Otherwise, the session is expired. continues to compute and randomly selects a number to calculate the following: Finally, transmits the request to via an open channel.
- After receiving , calculates , and Afterwards, computes Then, verifies . In the case of invalidation, terminates the session and sets the counter . keeps suspending the card until registers again if N surpasses some threshold mark (e.g., 8). Otherwise, randomly selects a number to compute , and Finally, sends the response message to via open channel.
- Upon receiving the respond message , computes , and Subsequently, checks whether . The session is aborted if these are not equal, . Otherwise, is authenticated by and accepts . Afterwards, computes Finally, transmits the challenge message to through an open channel.
- Upon receiving the challenge message from , computes and verifies whether . If these are equal, then is authenticated successfully.
Finally, both and share the common session key .
7.5. Password Updation
is able to change their password whenever they want, for which and have to undergo the following procedure:
- inserts the into a card reader and inputs , current password , and password to be updated .
- computes and Afterwards, checks whether . In case of inequality, refuses to update the password.
- Apart from that, randomly selects a number to compute Subsequently, computes Finally, replaces with , respectively.
Remark: As Amin et al.’s scheme and Srinivas et al.’s scheme are vulnerable to offline password guessing attack and key-compromise user impersonation attack and cannot provide user un-traceability, and because Amin et al.’s scheme cannot provide perfect forward secrecy, in the proposed scheme: (1) we employ “honey words” + “fuzzy-verifiers” to resist against offline password guessing attack [42]; (2) according to [47], to provide perfect forward secrecy, we use public key cryptosystems (e.g., ECC); (3) we store a secret parameter in the server database which cannot be compromised by the adversary in order to resist key-compromise user impersonation attack; and (4) to provide user un-traceability, we deploy a dynamic identity technique via a public key algorithm, that is, .
8. Security Inspection
This section provides the details of how the presented protocol ensures the security against all known attacks, including key-compromise user impersonation attack and offline password guessing attack. Further, it also offers more comprehensive security features, in particular, user un-traceability and perfect forward secrecy under the capabilities of the adversary that were introduced in Section 2.3.
8.1. User Un-Traceability and Anonymity
During the login authentication stage, is not sent through the public channel. Even if intercepts the login request messages from the public channel, still cannot extract from , because is protected by and is a dynamic identity. Thus, the proposed scheme provides the user un-traceability and anonymity.
8.2. Stolen Smart-Card Attack
In the proposed scheme, even if steals of , then can extract the parameters stored in utilizing power analysis technology, and captures the transmitted message over a public channel. However, as per the following details, cannot execute any attack. Thus, the presented protocol is secured against stolen smart-card attack.
8.3. Offline Password Guessing Attack
Assuming that steals and extracts stored in it. intercepts all messages over a public channel. If guesses an ID and a password , can calculate , and then figures out . Afterwards, examines whether . According to [42], can obtain the reduced password guessing space of size , where is the space of passwords. Further, can guess the correct password only by online password guessing. However, prevents this guessing by using a login request threshold value (e.g., 8). Once the number of online guesses exceeds the threshold value, will terminate communication and suspend until registers again. Therefore, the presented scheme offers resistance against offline password guessing attack.
8.4. Privileged Insider Attack
If an internal attacker eavesdrops the registration information during user registration, is unable to get , because it is secured by one-way hash function as well as with random number . Thus, the presented scheme is immune to the privileged insider attack.
8.5. Key-Compromise User Impersonation Attack
If the adversary steals the long-term private key of the server, it is still unable to impersonate the user to the server. This kind of attack is referred to as a key-compromise user impersonation attack. In the presented protocol, even if of is revealed to , still cannot determine , because is unable to obtain the random number . Therefore, cannot forge the login request message , and therefore cannot be authenticated by . That is, cannot impersonate . Thus, the presented protocol is insusceptible to key-compromise user impersonation attack. Further, it implies that the presented scheme ensures resistance against user impersonation attack.
8.6. Server Impersonation Attack
intercepts the response message if tries to make a server impersonation attack. randomly generates a number to compute . Afterwards, tries to compute and . Since does not know and computed by the secret key of , is unable to calculate and cannot forge . Thus, cannot carry out the server impersonation attack.
8.7. Replay Attack
If intercepts the login message from , and wants to replay this message to . This replay attack is easily captured by inspecting the freshness of in the presented scheme, where , and is a random number. Similarly, replaying the challenging message and response message is detected by either or . Thereupon, it is inferred that the presented protocol is immune to replay attack.
8.8. Known Key Security
Suppose that compromises the previous session key between and . However, the next session key will be computed by new random numbers and . That is, . To calculate the new session key, has to compute from . However, this is computationally infeasible for because of and . Therefore, the presented scheme offers known key security.
8.9. Mutual Authentication
In the proposed scheme, only the legitimate and can be verified by , and only the legitimate can be verified as the user . That is, the proposed scheme allows and to authenticate each other. Thus, the presented protocol ensures mutual authentication between a legitimate and .
8.10. Man-in-the-Middle Attack
It is impossible for in the proposed scheme to compute the correct login request and challenge message. Therefore, cannot be authenticated by the server. Moreover, is unable to calculate the correct response message, and thus cannot pass the user verification. It is therefore inferred that the proposed scheme is immune to man-in-the-middle attack.
8.11. Denial-of-Service Attack
If wants the login authentication in the proposed scheme, it must input the correct and to pass the verification of . If inputs wrong and into , is unable to compute the correct login request message. Moreover, if wants to update the password, it has to pass the verification of . An incorrect or previous password cannot pass the verification. Therefore, the proposed scheme ensures resistance against denial-of-service attack.
8.12. Perfect Forward Secrecy
Suppose that of is compromised and acquires , , and . To calculate the correct , is required to calculate . However, it is impossible for to compute because of and . Thus, is not capable of figuring out . Therefore, the presented protocol ensures perfect forward secrecy.
9. BAN-Logic Proof
BAN is a logic of belief. The intended use of BAN is to analyze authentication protocols by deriving the beliefs that honest principals correctly executing a protocol can come to as a result of the protocol execution. For example, a user might come to believe that a session key they have negotiated with a server is a good key for a future session [51]. This section incorporates the BAN-Logic [52] to prove the session key agreement between user and server after the execution of the improved scheme. BAN-Logic notations and Basic BAN-Logic postulates are described in Table 2 and Table 3.

Table 2.
Burrows–Abadi–Needham logic (BAN-Logic) notations.

Table 3.
Basic BAN-Logic postulates
9.1. Idealized Scheme
The ideal form of the presented protocol is derived as follows:
- Message 1.
- : ,
- Message 2.
- : , .
9.2. Security Objectives
We prove that the improved scheme can satisfy the following objective:
- Objective 1.
- Objective 2.
- Objective 3.
- Objective 4.
9.3. Initiative Premises
For the initial status of the proposed scheme, the following assumptions are made.
- IP 1.
- .
- IP 2.
- .
- IP 3.
- .
- IP 4.
- .
- IP 5.
- .
- IP 6.
- .
- IP 7.
- .
- IP 8.
- .
9.4. Proof Procedure
The main proof steps of the proposed scheme are presented below.
- Step 1.
- From Message 2, it shows the following:
- Step 2.
- From Step 1, IP 5, and the message-meaning rule, it illustrates the following:
- Step 3.
- From IP 1 and the freshness conjuncatenation rule, the following can be inferred:
- Step 4.
- From Steps 2 and 3, the freshness rule, and the nonce verification rule, we obtain the following:
- Step 5.
- From Step 4 and the believe rule, we deduce the first objective as follows:
- Step 6.
- From Objective 1, IP 7, and the jurisdiction rule, we accomplish the second objective as follows:
- Step 7.
- From Message 1, it indicates the following:
- Step 8.
- From Step 7, IP 6, and the message meaning rule, the following can be inferred:
- Step 9.
- From IP 2 and the freshness conjuncatenation rule, the following can be obtained:
- Step 10.
- From Steps 8 and 9, the freshness rule, and the nonce-verification rule, we determine the following:
- Step 11.
- From Step 10 and the believe rule, the third objective can be achieved as follows:
- Step 12.
- From Objective 3, IP 8, and the jurisdiction rule, the fourth objective is accomplished as follows:
By accomplishing Objectives 1–4, both and believe that the is settled between them. Therefore, the proposed scheme ensures mutual authentication along with key agreement.
10. Performance Comparison
This section analyzes the computational and security performance of the presented scheme while comparing it with multiple schemes, including those of Awasthi et al. [23], Huang et al. [25], Amin et al. [26], Pippal et al. [27], Li et al. [28], and Srinivas et al. [29]. The exclusive-OR operation and string concatenation are usually neglected when comparing the computational cost. However, the following operations are considered: , the execution time of point multiplication operation; , the time for execution of modular exponentiation operation; , the running time of a hash operation; and , the running time for modular multiplication operation. More precisely, we compare the experimental results of the aforementioned operations as performed by [53,54], where , , , and take ms, ms, ms, and ms, respectively (Table 4). Following [53,54], the aforementioned operations were executed on a computing platform having Intel Pentium Dual Core E2200 2.20 GHz processor, the Ubuntu 12.04.1 LTS 32-bits operating system, and 2048 MB of RAM.

Table 4.
The performing time of cryptographic operations (adapted from [53,54]).
In Table 5, we compare the schemes of [23,25,26,27,28,29] with the presented protocol in terms of security. In Table 5, we observe that [23,25,26,27,28,29] cannot provide features. The scheme in [26] is still unable to provide perfect forward secrecy , although the authors used RSA-based public cryptography. The proposed scheme fulfills all known security features . Thus, the presented scheme surpasses [23,25,26,27,28,29] in terms of security.

Table 5.
Comparison of security features.
Table 6 presents the computational cost of the schemes [23,25,26,27,28,29] and the proposed scheme for login and authentication. The computational cost of the proposed protocol is comparatively lower than the schemes in [23,25,27,28,29], but slightly higher than the scheme in [26]. However, according to Table 5, the scheme in [26] cannot address security features. Thus, combining Table 5 and Table 6, we remark that the presented solution is more feasible for practical multi-server environments in terms of the trade-off between usability and security.

Table 6.
Comparison of computational complexity.
11. Conclusions
This paper first analyzes Amin et al.’s [26] scheme and proves that the considered scheme cannot provide perfect forward secrecy and user un-traceability, and is susceptible to offline password guessing attack and key-compromise user impersonation attack. Second, we review Srinivas et al.’s [29] multi-server authentication scheme while proving that it cannot resist offline password guessing attack and key-compromise user impersonation attack, and is unable to ensure user un-traceability. Afterwards, to address the limitations of prevalent works, we put forward an enhanced multi-server two-factor authentication scheme. Heuristic analysis and BAN-Logic proof ensure that the presented scheme includes various known security features. The security and efficiency analyses display the robustness and efficiency of the presented scheme. Overall, the presented scheme is proven to be more feasible for multi-server authentication-and-key-agreement scenarios in various low-power networks. Moreover, the design and analysis methods in this paper can also be used for authentication protocols in IoT, WSNs, etc.
Author Contributions
Writing—original draft, G.X. (Guosheng Xu), S.Q., H.A., G.X. (Guoai Xu), Y.G., M.Z. and H.X.; and Writing—review and editing, G.X. (Guosheng Xu), S.Q., H.A. and G.X. (Guoai Xu).
Funding
This work was funded by the National Key Research and Development Program of China (No. 2018YFB0803600 and No. 2017YFB0801901) to Guoai Xu, and BUPT Excellent Ph.D. Students Foundation (No. CX2018312) to Shuming Qiu.
Acknowledgments
The authors are thankful to the Editor and anonymous reviewers for the generous feedback and constructive comments.
Conflicts of Interest
There are no conflicts of interest regarding the publication of this paper.
References
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Franks, J.; Hallam-Baker, P.; Hostetler, J.; Lawrence, S.; Leach, P.; Luotonen, A. HTTP Authentication: Basic and Digest Access Authentication. IETF RFC 1999, 2617, 1–34. [Google Scholar]
- Yang, C.; Wang, R.; Liu, W. Secure authentication scheme for session initiation protocol. Comput. Secur. 2005, 24, 381–386. [Google Scholar] [CrossRef]
- Khan, M.K. Fingerprint Biometric-based Self-Authentication and Deniable Authentication Schemes for the Electronic World. IETE Tech. Rev. 2009, 26, 191–195. [Google Scholar] [CrossRef]
- Farash, M.S.; Chaudhry, S.A.; Heydari, M.; Sadough, S.M.S.; Kumari, S.; Khan, M.K. A lightweight anonymous authentication scheme for consumer roaming in ubiquitous networks with provable security. Int. J. Commun. Syst. 2017, 30, e3019. [Google Scholar] [CrossRef]
- Arkko, J.; Torvinen, V.; Camarillo, G.; Niemi, A.; Haukka, T. Security Mechanism Agreement for SIP Sessions; IETF Internet Draft: Fremont, CA, USA, 2002. [Google Scholar]
- Arshad, R.; Ikram, N. Elliptic curve cryptography based mutual authentication scheme for session initiation protocol. Multimed. Tools Appl. 2013, 66, 165–178. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Khan, I.; Irshad, A.; Ashraf, M.U.; Khan, M.K.; Ahmad, H.F. A provably secure anonymous authentication scheme for session initiation protocol. Secur. Commun. Netw. 2016. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Naqvi, H.; Shon, T.; Sher, M.; Farash, M.S. Cryptanalysis and Improvement of an Improved Two Factor Authentication Protocol for Telecare Medical Information Systems. J. Med. Syst. 2015, 39, 66. [Google Scholar] [CrossRef] [PubMed]
- Farash, M.S.; Attari, M.A. An Enhanced authenticated key agreement for session initiation protocol. Inf. Technol. Control 2013, 42, 333–342. [Google Scholar] [CrossRef]
- He, D. An efficient remote user authentication and key agreement protocol for mobile client-server environment from pairings. Ad Hoc Netw. 2012, 10, 1009–1016. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Chen, Y. A secure mutual authentication scheme for session initiation protocol using elliptic curve cryptography. Secur. Commun. Netw. 2012, 5, 1423–1429. [Google Scholar] [CrossRef]
- Islam, S.; Khan, M. Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J. Med. Syst. 2014, 38. [Google Scholar] [CrossRef] [PubMed]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Gupta, V. Design of a secure anonymity-preserving authentication scheme for session initiation protocol using elliptic curve cryptography. J. Ambient Intell. Hum. Comput. 2017. [Google Scholar] [CrossRef]
- Qiu, S.; Xu, G.; Ahmad, H.; Wang, L. A Robust Mutual Authentication Scheme Based on Elliptic Curve Cryptography for Telecare Medical Information Systems. IEEE Access 2018, 6, 7452–7463. [Google Scholar] [CrossRef]
- Shen, C.; Nahum, E.; Schulzrinne, H.; Wright, C.P. The impact of TLS on SIP server performance: Measurement and modeling. IEEE/ACM Trans. Netw. 2012, 20, 1217–1230. [Google Scholar] [CrossRef]
- Thomas, M. SIP Security Requirements; Work In Progress; IETF Internet Draft: Fremont, CA, USA, 2001. [Google Scholar]
- Wang, D.; He, D.; Wang, P.; Chu, C. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Depend. Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Xie, Q. A new authenticated key agreement for session initiation protocol. Int. J. Commun. Syst. 2012, 25, 47–54. [Google Scholar] [CrossRef]
- Zhang, Z.; Qi, Q.; Kumar, N.; Chilamkurti, N.; Jeong, H.J. A secure authentication scheme with anonymity for session initiation protocol using elliptic curve cryptography. Multimed. Tools Appl. 2015, 74, 3477–3488. [Google Scholar] [CrossRef]
- Qiu, S.; Xu, G.; Ahmad, H.; Guo, Y. An enhanced password authentication scheme for session initiation protocol with perfect-forward-secrecy. PLoS ONE 2018, 13, e0194072. [Google Scholar] [CrossRef] [PubMed]
- Qiu, S.; Xu, G.; Guo, Y.; Zhang, M. Cryptanalysis and improvement of 2 mutual authentication schemes for Session Initiation Protocol. Int. J. Commun. Syst. 2018, 31, e3568. [Google Scholar] [CrossRef]
- Awasthi, A.K.; Srivastava, K.; Mittal, R.C. An improved timestamp-based remote user authentication scheme. Comput. Electr. Eng. 2011, 37, 869–874. [Google Scholar] [CrossRef]
- Jau-Ji, S.; Lin, C.-W.; Hwang, M.-S. Security enhancement for the timestamp-based password authentication scheme using smart cards. Comput. Secur. 2003, 22, 591–595. [Google Scholar]
- Huang, H.-F.; Chang, H.-W.; Yu, P.-K. Enhancement of Timestamp-based User Authentication Scheme with Smart Card. Int. J. Netw. Secur. 2014, 16, 463–467. [Google Scholar]
- Amin, R.; Maitra, T.; Giri, D.; Srivastava, P.D. Cryptanalysis and Improvement of an RSA Based Remote User Authentication Scheme Using Smart Card. Wirel. Pers. Commun. 2017, 96, 4629–4659. [Google Scholar] [CrossRef]
- Pippal, R.S.; Jaidhar, C.D.; Tapaswi, S. Robust Smart Card Authentication Scheme for Multi-server Architecture. Wirel. Pers. Commun. 2013, 72, 729–745. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Liao, J.; Liang, W. An Enhancement of a Smart Card Authentication Scheme for Multi-server Architecture. Wirel. Pers. Commun. 2015, 80, 175–192. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. A Self-Verifiable Password Based Authentication Scheme for Multi-Server Architecture Using Smart Card. Wirel. Pers. Commun. 2017, 96, 6273–6297. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. Int. J. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Chang, I.; Lee, T.; Lin, T.; Liu, C. Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Hsiu-Lien, Y.; Chen, T.H.; Liu, P.C.; Tai-Hoo, K.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar]
- Choi, Y.; Lee, D.; Kim, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Shi, W.; Gong, P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 2013, 2013, 51–59. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Jung, J.; Moon, J.; Lee, D.; Won, D. Efficient and security enhanced anonymous authentication with key agreement scheme in wireless sensor networks. Sensors 2017, 17, 644. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the Anonymity of Two-Factor Authentication Schemes for Wireless Sensor Networks: Attacks, Principle and Solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014, 20, 1–15. [Google Scholar] [CrossRef]
- Menezes, A.J. Elliptic Curve Public Key Cryptosystems; Kluwer Academic Publishers: Boston, MA, USA, 1993. [Google Scholar]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Depend. Secur. Comput. 2016. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. Adv. Cryptol. 1999, 1666, 388–397. [Google Scholar]
- Eisenbarth, T.; Kasper, T.; Moradi, A.; Paar, C.; Salmasizadeh, M.; Shalmani, M.T. On the power of power analysis in the. real world: A complete break of the KeeLoq code hopping scheme. In Advances in Cryptology-CRYPTO; Lecture Notes in Computer Science; Springer: Berlin, Germany, 2008; Volume 5157, pp. 203–220. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Castiglione, A.; De Santis, A.; Castiglione, A.; Palmieri, F. An Efficient and Transparent One-Time Authentication Protocol with Non-interactive Key Scheduling and Update. AINA 2014, 351–358. [Google Scholar] [CrossRef]
- Wang, D.; Wang, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Wang, D.; Zhang, Z.; Wang, P. Targeted online password guessing: An underestimated threat. Proc. ACM CCS 2016, 16, 1242–1254. [Google Scholar]
- Wang, D.; Wang, P. On the implications of Zipf’s law in passwords. In Proceedings of the 21st European Symposium on Research in Computer Security, Heraklion, Greece, 26–30 September 2016; pp. 11–131. [Google Scholar]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s Law in Passwords. IEEE Trans. Inform. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Syverson, P.F.; Cervesato, I. The Logic of Authentication Protocols; FOSAD: Bertinoro, Italy, 2000; pp. 63–136. [Google Scholar]
- Burrow, M.; Abadi, M.; Needham, R.M. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Arshad, H.; Nikooghadam, M. An efficient and secure authentication and key agreement scheme for session initiation protocol using ECC. Multimed. Tools Appl. 2014, 75, 1–17. [Google Scholar] [CrossRef]
- Kilinc, H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2013. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).