Abstract
Heterogeneous wireless sensor networks (HWSNs) are employed in many real-time applications, such as Internet of sensors (IoS), Internet of vehicles (IoV), healthcare monitoring, and so on. As wireless sensor nodes have constrained computing, storage and communication capabilities, designing energy-efficient authentication protocols is a very important issue in wireless sensor network security. Recently, Amin et al. presented an untraceable and anonymous three-factor authentication (3FA) scheme for HWSNs and argued that their protocol is efficient and can withstand the common security threats in this sort of networks. In this article, we show how their protocol is not immune to user impersonation, de-synchronization and traceability attacks. In addition, an adversary can disclose session key under the typical assumption that sensors are not tamper-resistant. To overcome these drawbacks, we improve the Amin et al.’s protocol. First, we informally show that our improved scheme is secure against the most common attacks in HWSNs in which the attacks against Amin et al.’s protocol are part of them. Moreover, we verify formally our proposed protocol using the BAN logic. Compared with the Amin et al.’s scheme, the proposed protocol is both more efficient and more secure to be employed which renders the proposal suitable for HWSN networks.
1. Introduction
In wireless sensor networks (WSNs) there are many sensor nodes scattered in a defined area [1]. These networks can be categorized into two important classes: homogeneous and heterogeneous sensor networks. On the one hand, in homogeneous sensor networks, all the sensor nodes are equal in terms of energy and hardware complexity. On the other hand, heterogeneous sensor networks (HWSNs) include various types of wireless sensor nodes with different capabilities and functions. In HWSNs, the sensors share their functions and increase the reliability of the network without increasing the cost of implementation [2,3,4,5]. Some of these sensors are low-cost, low-power and consequently have constrained computational power, transmission range, storage capacity and battery life [6]. It is clear that there are great needs to design energy-efficient protocols for such networks. In HWSN, users communicate to the sensor nodes to acquire data of their own interest. Therefore, the user and sensor node authentication is an important line of research in HWSN security which has recently awakened interest from the network security research community. In HWSN, the gateway node (GWN) plays an essential part in the authorization procedure since this element is the connection (input/output) with the all the elements outside the network. As shown in Figure 1, there are five models in authenticating users and sensor nodes in HWSN [7]. In these five schemes, a user, a gateway node and a sensor node implement the authentication protocol by exchanging four messages (e.g., Figure 1(a.1–a.4)). In each scheme, there are four steps: (1) the gateway node authenticates the user (e.g., Figure 1(a.1)); (2) the sensor node authenticates the legitimate user and the gateway node (e.g., Figure 1(a.2)); (3) the sensor node verifies the legitimacy of the gateway node (e.g., Figure 1(a.3)); and finally, (4) in the last step, the user authenticates the legitimate sensor node (e.g., Figure 1(a.4)). Since HWSN nodes face with to many limitations in power consumption and communication range, models, in which a user and a sensor are a long way apart, are not practical, Figure 1e,b,d [8,9].
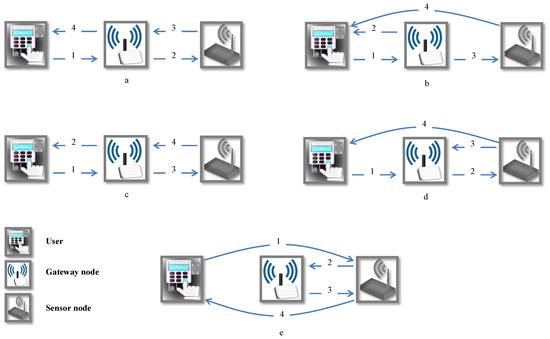
Figure 1.
Five user authentication models in HWSN [7].
To tackle with security challenges of HWSN networks, we need lightweight enough and secure schemes. In the literature, authentication protocols are the most common adopted solution [7,10,11,12,13,14]. Unfortunately, most of them do not provide the required security and present important security pitfalls or are not energy-efficient. In this vein, recently, Amin et al. presented an untraceable and anonymous 3FA scheme for HWSNs. They used the model depicted in Figure 1a to design their protocol and asserted that their protocol can resist all common attacks known in the context of HWSN [15]. Nevertheless, in this article, we cryptanalyzed this protocol to show that this scheme is vulnerable against user impersonation, de-synchronization and session key disclosure attacks and also the adversary can trace the user. In order to hinder these attacks, we improve the Amin et al.’s protocol.
1.1. Our Contribution
The contributions of this article are summarized as below:
- At first, we present several serious security attacks against the Amin et al.’s scheme [15]. Our proposed attacks include de-synchronization, user impersonation, user traceability and session disclosure attacks.
- In order to increase the security level offered by Amin et al.’s protocol, we remedy the security faults found in their scheme.
- The security of the proposed scheme has be scrutinized from a formal and informal point of view. The attacks mentioned in Amin et al.’s protocol and other common security attacks have been considered in the design of the new protocol.
- The efficiency of our proposal is higher than the offered by Amin et al.’s scheme. Therefore, our scheme can be used for resource constrained sensors as the ones employed in HWSNs.
1.2. Paper Organization
The organization of the article is as follows. In Section 2, some related work are presented. Section 3 introduces the required preliminaries and notations. We review Amin et al.’s protocol in Section 4. Section 5 shows the security pitfalls of this scheme. We propose the improved scheme in Section 6. Then, we discuss the security of the proposed protocol in an informally way in Section 7, while, in Section 8, a formal analysis is presented. Finally, we extract some conclusions in Section 9.
2. Related Work
In a wireless sensor network, to allow a legitimate user to obtain information from a target sensor, the system needs to verify the validity of user by running an authentication protocol. In this section, we briefly discuss some existing schemes that aim to increase the security level of these networks.
Two-factor Authentication Schemes: Several two-factor authentication (2FA) schemes have been proposed for WSN, where the login phase of these protocols is based on passwords and smartcards.
In 2006, Wong et al. [16] presented a 2FA protocol based on the use of a hash function for wireless sensor networks, but the authors in [11] found that the protocol suffers from serious security pitfalls (i.e., replay, stolen-verifier and forgery attacks). To overcome these important weaknesses, authors in [11] proposed a new 2FA protocol based on passwords and smartcards. However, this protocol also is not immune against denial of service attacks and the nodes can be compromised [17].
In 2010, to improve the [11] protocol, Chen et al. [10] presented a bilateral authentication protocol in which three entities are involved (i.e., users, sensor nodes and the gateway node). In the same year, Khan et al. [12] showed that [11] fails in the authentication and in the key updating mechanism and presented a new protocol that they claimed it hinders the mentioned attacks. Later, Vaidya et al. [18] introduced several security vulnerabilities in [10,11,12] based on the stolen smartcard assumption. Xue et al. in 2013 presented a mutual authentication protocol based on temporal credentials, which is mainly based on the use of hash functions [7]. Nevertheless, He et al. [19] showed how the above protocol [7] is not resistant against user node and sensor node impersonation attacks and proposed a new temporal-credential-based protocol to overcome these weaknesses. In addition, Mir et al. [20] compromised the security of the healthcare system designed by He et al. [21], uncovering impersonation and password disclosure attacks. In addition, Turkanovic et al. [22] presented another bilateral authentication scheme in the context of HWSNs. However, Amin and Biswas [23] examined the Turkanovic et al. scheme and identified certain security problems (e.g., offline identity and password guessing attacks) and finally claimed to remove these security pitfalls in an efficient protocol. In the same year, Farash et al. [6] showed also some security shortcomings in [22] and proposed a new lightweight protocol. In the context of lightweight cryptography, Gope et al. [24] presented a 2FA protocol with especial security features including user anonymity and forward/backward secrecy. Soon, in [25], the authors analyzed the Gope’s protocol by presenting a session key disclosure attack.
Three-Factor Authentication Schemes: In 2016, Amin et al. [26] pointed out how the Farash et al. protocol is susceptible to a number of attacks and proposed a new mechanism which was claimed to be resistant against these attacks. To enhance the security flaws of 2FA protocols, Amin et al. proposed a three-factor authentication (3FA) scheme based on password, smartcard and biometric trait linked to the legitimate user. However, Arasteh et al. [27] proposed replay and Denial-of-Service (DoS) attacks against Amin et al.’s scheme. In 2017, the authors in [28] presented an smartcard loss attack against Amin et al.’s 3FA protocol [26]. They also showed that the attacker can reveal the session keys in other sessions of the protocol. To overcome the security flaws of this protocol, they proposed the enhanced scheme based on the Rabin’s cryptosystem. In the same year, Jiang et al. [29] presented a solution to enhance the security of another 3FA protocol [30] that suffers from important security faults including traceability, identity guessing, offline password guessing, user impersonation and server impersonation attacks.
Chang et al. in [31] found several vulnerabilities in the Turkanovic et al. 2FA protocol [22] and presented an enhancement solution, but the scheme was shown to be vulnerable to a wide set of attacks such as traceability, information disclosure or session key attacks [15]. Eventually, Amin et al. [15] presented a new untraceable and anonymous 3FA scheme for HWSNs which was argued to be the improved version of Chang et al. scheme. Nevertheless, in this article, we scrutinize the security of this 3FA protocol and show how it is vulnerable to user impersonation, de-synchronization and session key disclosure attacks and also the adversary can trace the user. To prevent these attacks, we upgrade the Amin et al.’s protocol and analyze its security from a formal and informal perspective.
Privacy Schemes: In some of the protocols mentioned, the authors have stated that their schemes can preserve the user’s privacy. To do this, the user’s identifier is encoded using a dynamic identity. This anonymous identifier is used when the user communicates with the gateway node, and this information is useless for the attacker to reveal the user’s identity [24]. In detail, in schemes [7,32,33], the authors claim that their proposals preserve users’ privacy. Unfortunately, all of them fail in this purpose [24].
Threat Model: Our threat model mainly follows the Dolev–Yao model [34]. Therefore, the adversary can intercept, modify, delete and change any of messages transmitted over the insecure communication channel. The adversary can also execute side channel attacks and then obtain the secrets stored on the smartcard. In addition, the adversary can capture the sensors and reveal their private information stored in their memory as these devices do not have tamper protection mechanisms [24].
3. Preliminaries and Notations
This section first shows the notations used in this paper and then revises the proposed fuzzy extractor function for extracting the biometric parameters required for the third factor of the authentication procedure.
3.1. Notations
The notation used through this article is summarized in the Table 1.

Table 1.
Notations.
3.2. Fuzzy Extractor
The facts that biometric tokens cannot be easily guessed, are difficult to be copied, shared and forged, and are not lost or forgotten makes biometric based authentication more preferable than traditional password based ones [35,36].
A fuzzy extractor can generate cryptography keys over noisy data. In other words, they are error tolerant. In detail, this is composed of two processes, a probabilistic algorithm and a deterministic algorithm as described below:
- The generation procedure (): given a biometric input , this probabilistic algorithm generates a secret key and a non-secret string , i.e., .
- The reproduction procedure (): given the noisy input and the corresponding auxiliary string , this algorithm is able to recover the same key as in the generation process, i.e., .
4. Review of Amin et al.’s Scheme
In this section, we scrutinize the security of the authentication protocol proposed by Amin et al., which is composed of nine phases: (1) pre-deployment; (2) user registration; (3) login; (4) authentication and key agreement; (5) updating; (6) post-deployment; (7) password recovery; (8) password change; and (9) smartcard revocation.
4.1. Pre-Deployment Phase
Firstly, the gateway node chooses as a long-term secret key and assigns identities to the sensor nodes ( for a population of m sensor nodes in the network). Then, the calculates and stores into the memory of .
4.2. User Registration Phase
Using a secure channel, the user executes the following steps in conjunction with the .
- Step 1.
- chooses an identity , attaches to it a personal credentials (e.g., social security number), and submits both values to the .
- Step 2.
- If the does not find in the database, it generates and calculates and . Both values () are stored in a new smartcard and the device is handed over to .
- Step 3.
- Once receiving the smartcard, chooses a password and then uses a sensor device to obtain his biometric information and finally writes to the .
- Step 4.
- uses the fuzzy extractor technique to calculate , it then computes , , , , and deletes .
Finally, the smartcard contains the tuple .
4.3. Login Phase
The user follows these steps to access the data collected by sensor .
- Step 1.
- inserts into the terminal and then enters and and also uses the sensor device to imprint his biometric information .
- Step 2.
- retrieves and computes , and . verifies the correctness of . If so, concludes , and ; otherwise, denies .
- Step 3.
- generates and computes , , and — represents the current timestamp.
Finally, sends the tuple to through an insecure channel.
4.4. Authentication and Session Key Agreement Phase
Two goals are achieved in this phase (see Figure 2): (1) and are authenticated through ; and (2) and set a session key. In particular, the following five steps are executed.

Figure 2.
Authentication and key agreement phases in Amin et al.’s protocol [15].
- Step 1.
- After receiving the message in login phase, the checks whether the timestamp condition holds, being the current time of . If the condition is fulfilled, the aborts the connection. Otherwise, it calculates and then decodes , and . It then computes and checks the validity of the received . If so, the identifies to as an authorized user. If not, it aborts the connection.
- Step 2.
- Then, calculates , , and . then sends the tuple to .
- Step 3.
- Upon receiving the message , checks the validity of timestamp . If , it terminates the connection. Otherwise, computes , and the and verifies the validity of received . If it is invalid, then aborts the session. Otherwise, it generates and computes as a session key and then computes and . Then, sends the tuple to .
- Step 4.
- Once the message is received, the verifies the freshness of . If , aborts the connection. Otherwise, it decodes and calculates the session key . It then computes to verify the correctness of the received . If the above verification fails, then discontinues the session. Otherwise, it calculates and forwards the message to .
- Step 5.
- Once the message is received, checks whether the condition is satisfied. If it is not fulfilled, aborts the session. Otherwise, it calculates , and to verify the correctness of the received . Now the entities are mutually authenticated and a session key has been negotiated.
4.5. Update Phase
In this phase, in order to achieve user untraceability, updates as follows:
- Step 1.
- computes and sends it to as a confirmation message. After receiving the message, decodes and updates and , where . It then computes , and and sends the tuple to .
- Step 2.
- After receiving the message , calculates to check the validity of the received . If so, it extracts and and computes . Then, rewrites to instead of previous .
4.6. Post-Deployment Phase
A new sensor node is used in this phase to replace a damaged sensor node . The generates a new identity and then calculates and stores in ’s memory.
4.7. Password Recovery Phase
executes this phase when he forgets his password. needs to insert in the card reader and enter his identity along with . Now, the computes and . Then, checks whether . If so, then it computes and sends the recovered password to the user.
4.8. Password Change Phase
The password of the user can be updated by executing the updating procedure with and without the intervention of . In detail, the following steps show how the user can update the old password for a new one .
- Step 1.
- inserts in to the terminal and enters along with biometric information .
- Step 2.
- uses the fuzzy extractor technique to calculate , it then computes and . If , then requests to enter a new password at ; otherwise, aborts this procedure.
- Step 3.
- Now, calculates , , , and replaces with .
4.9. Smartcard Revocation Phase
Generally, smartcards can be lost, stolen or damaged. Thus, the smartcard revocation phase is very important. This phase is executed as described below:
- Step 1.
- submits and a personal credential (e.g., social security number) to the smartcard issuer.
- Step 2.
- If the smartcard issuer can find in the database, it generates and calculates and . It then writes into a new smartcard and delivers it to the user .
- Step 3.
- Once is received, chooses a password , receives new biometric information from the sensor and writes to the .
- Step 4.
- uses the fuzzy extractor technique to calculate . It then computes , , , and , and implants into and deletes .
5. Security Analysis of Amin et al.’s Protocol
In [15], the authors claimed that the adversary/attacker A cannot trace or identify the user using the transmitted messages. Moreover, they claimed that the attacker cannot impersonate the user by accessing to the old login eavesdropped messages.
Unfortunately, for Amin et al.’s protocol, we show how the proposed protocol is not immune against user impersonation and de-synchronization attacks. The user can be also tracked by an attacker who eavesdrops on only one protocol session. In addition, we provide evidence of how an adversary can easily obtain the session key under the assumption that sensors are not tamper-resistant.
5.1. User Impersonation Attack
In this attack, we point out how an adversary A is authenticated by both the gateway node and the sensor node . The attack is described below:
- A eavesdrops on the message sent by to the , then he changes the value to .
- After receiving the message in the login phase, the checks two issues: (1) timestamp condition and (2) validity of the received , which does not depend on . Thus, the accepts these two conditions and computes and . It then calculates . Now, the believes that A is an authorized user.
- Then, calculates and then computes , and and sends the tuple to .
- check the correctness of timestamp and computes , and and checks validity of the received . It generates and computes as a session key and then computes and . Now, the also believes that A is an authorized user and sends the tuple to .
- The checks the validity of . It decodes and computes the session key . It then computes and checks validity of the received and computes and sends the message to which is the adversary. At this point, the adversary sends the random number to as a confirmation message. After receiving the message, uses the message to obtain which is the random number. Due to the absence of any checking process, it employs this value to compute , and and then sends the tuple to the adversary.
Following this attack, the adversary cheats and to pass the protocol with the success probability of “1”. Moreover, and establish the wrong session key along with .
5.2. De-Synchronization Attack
In Amin et al.’s authentication phase, an adversary A by eavesdropping only one session can reveal the of the user and uses it to render the user to a de-synchronization state as follows. Note that, in the proposed attack, the superscript j indicates the parameters of the j-th run of protocol, . In addition, in the Amin et al. scheme, the values of of the user is a constant value. In detail, the attack can be executed following the steps described below:
- A eavesdrops on the message from session 1;
- A eavesdrops on the message from session 2;
- A obtains from equation ;
- In Step 6 of the authentication phase, A intercepts and modifies them to , and ;
- A sends the tuple to ;
- calculates and then checks validity of the received . Then, it extracts and and computes . Then, rewrites to instead of previous .
Following this attack, the adversary compels the to insert the wrong into ’s memory. Now, cannot use to do the login.
5.3. User Traceability Attack
Following the privacy model proposed by Ouafi and Phan [37], the attacker can perform following phases to mount a traceability attack.
- Step 1.
- In round n, A sends an and eavesdrops on messages , , , and ;
- Step 2.
- The adversary A selects two users and and sends a and depending on the random bit the adversary A receives a corresponding to users ;
- Step 3.
- A sends an and eavesdrops on messages , , , and ;
- Step 4.
- A guesses the random bit if with a probability higher than a random coin flip following the procedure described below.
- Step 5.
- We have,,,
- As is constant and the user does not update it,
- If , then .
- Step 6.
- As a result, we can express ;
Following the described attack, the attacker can trace any target user . In other words, Amin et al.’s scheme is not resistant against user traceability attack.
5.4. Session Key Disclosure Attack
As described in Section 5.2, A can extract belonged to . Thus, if we assume that the sensor is not equipped with tamper-resistant, A obtains from sensor’s memory—note that the adversary does not require to execute the proposed attack. Then, it executes the session key disclosure attack as follows:
- A eavesdrops on messages and ;
- A obtains from equation ;
- A obtains from equation ;
- A computes the session key using the .
Therefore, an adversary can disclose the session key in Amin et al.’s protocol.
Finally, we would like to highlight that all our proposed attacks exploit the fact that the bitwise XOR operation is a source of vulnerability against passive and active attacks [38,39,40].
6. Our Proposed Protocol
We present an enhanced version of Amin et al.’s protocol to remedy its security pitfalls. The scheme, as the original proposal, is split into night phases: (1) pre-deployment; (2) user registration; (3) login; (4) authentication and key agreement; (5) update; (6) post-deployment; (7) password recovery; (8) password change; and (9) smart revocation. As we only enhanced the (3), (4), and (5) phases, these are the ones that we describe.
In summary, the enhanced authentication and key agreement phase, and update phase of the proposed scheme, as shown in the blue boxes in Figure 3, have five important changes. To prevent the user impersonation attack, the user makes uses of in the message . Subsequently, the gateway node verifies this value to authenticate the legitimate user (boxes number 1 and 2). To overcome the de-synchronization attack, we change the format of message as well as the equation the user employs to update . Therefore, the attacker cannot obtain by XORing these two values (boxes number 4 and 5). To avoid the replay attack, the gateway node checks the validity of by verifying the value of (box number 3).

Figure 3.
Modified Amin et al.’s authentication and key agreement phase. Changes are highlighted by boxes in the proposed scheme.
6.1. Login Phase
In this phase, we employ the in to guarantee the integrity of . performs the following steps to login when it wishes to access data collected by :
- Step 1.
- inserts into the terminal and then enters and and also uses the sensor device to imprint his biometric information .
- Step 2.
- retrieves and computes , and . checks validity of . If so, implies , and ; otherwise, denies .
- Step 3.
- generates and calculates , , and , being the current timestamp.
After this, forwards the tuple to using a public communication channel.
6.2. Authentication and Session Key Agreement Phase
At this point, and are authenticated through and a session key is set between both entities. In addition, we modify the message to tackle the attacker when she tries to obtain in the next session. In Figure 3, we summarize the details of this phase:
- Step 1.
- Once the message is received in the Login phase, the checks whether the timestamp condition holds. If the condition is fulfilled, the terminates the connection. Otherwise, it calculates and then decodes and . It then calculates and checks validity of the received . If so, the identifies to as an authorized user. If not, it terminates the connection.
- Step 2.
- Then, obtains and calculates and then computes , and , being the current timestamp. then forwards the tuple to .
- Step 3.
- Once the message is received, checks validity of the timestamp . If , it terminates the connection. Otherwise, calculates , and and checks validity of the received . If the verification fails, then aborts the session. Otherwise, it generates and computes as the session key and then computes and . Finally, sends the tuple to .
- Step 4.
- Once the message is received, the verifies the correctness of . If , aborts the connection. Otherwise, it decodes and computes the session key . It then computes and checks the validity of the received . If the above verification fails, then discontinues the session. Otherwise, it calculates and forwards the message to .
- Step 5.
- Once the message is received, checks whether the condition is satisfied. If it does not fulfilled, ends the session. Otherwise, it calculates , and and checks the validity of . At this point, the entities are mutually authenticated and a session key has been negotiated.
6.3. Update Phase
In this phase, updates in order to achieve user untraceability, as described in the next steps and depicted in Figure 3:
- Step 1.
- computes and sends it to as a confirmation message. After receiving the message, decodes and checks if the condition holds. If the verification fails, then aborts the session. Otherwise, it updates and , where . It then computes , and and sends the tuple to .
- Step 2.
- After receiving the message , calculates and then checks validity of . If so, it extracts and and computes . Then, rewrites to instead of previous .
7. Security Analysis of the Proposed Protocol
The proposed protocol is analyzed from an informal and formal point of view. This analysis shows how the proposed scheme withstands relevant and common security attacks.
The informal security analysis of a security scheme discusses its robustness against the common attacks known in its context. However, the formal security analysis methods employ mathematics or logic tools such as BAN-logic [41], AVISPA [42] or Proverif [43] to formally scrutinize the security of a cryptographic protocol. In this article, we employ the BAN-logic tool to formally verify our proposed protocol.
7.1. Informal Security Analysis
In this section, we point out how our proposed protocol withstands against relevant and well-known attacks.
7.1.1. Stolen Smartcard Attack
In our proposal, if the smartcard is stolen or lost, the adversary can access its memory and obtain all the information , , , , and stored in the smartcard. Note that, in our protocol, the smartcard is not tamper-resistant. Since some values (, and ) are unknown for the adversary, s/he cannot compute , and without having any information about these parameters. Furthermore, it is also computationally unfeasible for the attacker to disclose the , and the secret biometric information of the user thanks to the collision-resistance property of the one-way hash function. Thus, the proposed protocol is secure against the stolen smartcard attack.
7.1.2. Offline Password Guessing Attack
In our scheme, the password of the user is involved in , , and values, which are stored in the smartcard. As discussed above, the adversary A cannot use any of these stored items to obtain the password. In addition, using the messages transferred from the user , the attacker cannot relate these messages to the items stored on the smartcard to find useful information to verify her/his guess about . Therefore, our proposed scheme is robust against offline password guessing attack.
7.1.3. Privileged Insider Attack
In this kind of attack, the insider attacker tries to impersonate the legitimate user by using this user’s password. However, in the user registration phase of our scheme, only submits as a registration request. In addition, all the messages transmitted via a public channel are independent of . Thus, by no means can the insider of get ’s password. That is, our proposed protocol is resistant against the privileged insider attack.
7.1.4. Offline Identity Guessing Attack
On this occasion, the adversary tries to obtain knowledge about the real identity of a user —the user and are the unique entities who know this information. In our proposal, the adversary cannot derive from information obtained from the smartcard. In addition, is never passed over the public communication channel. As a consequence of using the one-way hash function , the adversary cannot find any useful information related to to verify her/his guess. Therefore, our proposed scheme is robust against identity guessing attack.
7.1.5. User Impersonation Attack
In this attack, the adversary aims to cheat by attempting to take the place of a legitimate user in the logging phase. S/he may use the eavesdropped login message of the previous sessions to conduct her/his attack. We show how our scheme is resistant against this attack. Once the eavesdropped message is received, the checks the legitimacy of the user by validating . A has to possess and to forge . However, without having any knowledge about the password , the biometric key and the of the smartcard, the adversary A cannot calculate a valid . Therefore, our proposed scheme is secure against user impersonation attack.
7.1.6. Gateway Node Impersonation Attack
To impersonate the gateway node, the adversary has to forge the message . Thus, the adversary A needs to know , and to compute which is impossible. Thus, A cannot forge the aforementioned message. In addition, A cannot compute and , which are created by . Therefore, our proposed scheme resists impersonation attack.
7.1.7. Sensor Node Impersonation Attack
In the authentication phase, the typical sensor node computes and and sends these values along with to the gateway node . To forge the messages and , the adversary A must compute and must know and . Moreover, A cannot compute without the knowing and . Therefore, A cannot compute ’s messages to execute a sensor node impersonation attack.
7.1.8. Session Key Security
In the authentication and session key agreement, the attacker can eavesdrop the messages and . Nevertheless, the session key is protected by the usage of the one-way hash function . For this, it is computationally impossible for the adversary to derive the used key. Thus, our proposed scheme provides session key security.
7.1.9. User Anonymity
In our proposed protocol, the identity of user is never passed in plain-text over an insecure communication channel. In this sense, is the value transmitted in the public messages. Due to the collision-resistant property of the one-way hash function , deriving from is computationally impossible for the attacker. Therefore, our proposed scheme preserves user anonymity.
7.1.10. Preserving User Untraceability
In this attack, an adversary A aims to determine whether two messages are generated by the same (unknown) user. Luckily, in our proposal, the attacker cannot be able to find any relationship between , and user’s identity . Furthermore, it must be noted that, in our proposed protocol, all the parameters used in the messages are random. Moreover, when the update phase of the protocol is executed, updates for the next session. Therefore, A cannot determine whether two protocol sessions are linked to the same user. Therefore, in our proposed protocol, users cannot be tracked.
7.1.11. Replay Attack
In the replay attack, the adversary forwards eavesdropped messages of the protocol (previous sessions) to try to deceive legitimate entities. The timestamp values and random numbers used in all messages of the protocol prevents any replay efforts from attacker. Therefore, replay attacks can be identified by verifying the freshness of the timestamp values and random numbers. Therefore, the replay attack does not work in our scheme.
7.2. Formal Security Analysis
We use BAN-logic [41] to conduct the security analysis of the authentication and key agreement phase of our proposal. Table 2 summarizes the used notation. Thereupon, we introduce the two main rules used in our analysis.

Table 2.
BAN-logic notations.
R1 (Shared key rule)., if P believes that s/he shared the key K with Q, and P receives the message ; then, P believes that Q sent X.
R2 (Belief rule)., if P believes Q sends the message set ; then, P believes Q sends the message X.
Our formal security analysis is split into the following steps:
Step 1. Protocol messages.
PM1:
PM2:
PM3:
PM4:
Step 2. Idealizing the protocol messages. At this point, the protocol messages are converted into the idealized format based on the BAN-logic notations. The results are denoted by IM1, ..., IM9 as below:
IM1 ():
IM2 ():
IM3 ():
IM4 ():
IM5 ():
IM6 ():
IM7 ():
IM8 ():
IM9 ():
Step 3. Explicit assumptions. The seven assumptions on the proposed scheme are described by A1, ..., A7 as below:
A1:
A2:
A3:
A4:
A5:
A6:
A7:
Step 4. Security goals. The nine security goals which are expected to be verified after analyzing the protocol by BAN-logic are listed by G1, ..., G9 as below. For instance, the goal G1 states that the gateway node must believe that the user has sent the key :
G1:
G2:
G3:
G4:
G5:
G6:
G7:
G8:
G9:
Step 5. Deriving the security goals. Finally, to show the achievement of the above-mentioned goals, we apply logical rules of the BAN-logic to the idealized messages and initial premises as described below.
In accordance with IM1, A5 and R1:
Result1: (satisfy G1);
Given the IM2, A5 and R1:
Result2: (satisfy G2);
In accordance with IM4, Result1 and R1:
Result3: (satisfy G3);
Given the IM5, A7 and R1:
Result4:
Taking into account Result4 and R2:
Result5: (satisfy G4);
Result6: (satisfy G5);
In accordance with IM6, A6 and R1:
Result7: (satisfy G6);
In accordance with IM7, A2 and R1:
Result8: (satisfy G7);
In accordance with IM8, A1 and R1:
Result9: (satisfy G8);
In accordance with IM9, Result9 and R1:
Result10: (satisfy G9).
Given the above steps, it can easily be concluded that the protocol can meet all preset goals. Therefore, we can state that our proposed scheme is secure.
8. Performance Comparison
In this work, we propose a new 3FA protocol to overcome the security weaknesses of the Amin et al. [15] scheme. We show how our enhanced protocol is not only secure but also efficient enough to be used in HWSNs. The discussion about the security features, computational overhead and computational cost offered by our proposed scheme and other related schemes, such as Amin et al. [15], Yeh et al. [32], Xue et al. [7], Das et al. [44], Jiang et al. [33], Das et al. [45] and Gope et al. [24] is presented in this section.
8.1. Security Features’ Comparison
In Table 3, we sum up the security features offered by our proposed protocol and other similar ones. The symbol “Yes” indicates that the scheme is secure against the related attack and the symbol “No” indicates the contrary. From this, we can conclude that our proposal satisfies all the security features required and offers a higher security level than its predecessors. In addition, protocols [7,24,32,33] do not provide three-factor authentication while our scheme does.

Table 3.
Security features’ comparison.
8.2. Overall Computational Overhead Comparison
In HWSNs, sensors have limited energy so any authentication protocol designed for these networks should be lightweight and energy efficient. Moreover, we use the model represented in Figure 1a to design our scheme. In our scheme, we use the hash, and the fuzzy extractor functions, which are both efficient. In fact, using the low-power cryptographic functions, rather than a very demanding one, can reduce energy consumption [46]. According to the results of the experiments presented in [24], each modular exponential operation in ECC-160 algorithm consumes 1.2 Ws energy and takes = 11.69 ms execution time. Moreover, for symmetric key encryption/decryption (128-bit AES-CBC), the running time and energy consumption are approximately = 4.62 ms and 0.72 Ws and for hash function (SHA-256) these two values are approximately = 1.06 ms and 0.27 Ws, respectively. These results were obtained using the MSB-430 sensor boards with the TI MSP430 micro controller [24]. Moreover, the time that the fuzzy extractor takes is about 17.1 ms [47]. In Table 4, previous works [7,15,24,32,33,44,45] and our proposed scheme are compared in terms of computational cost. As shown in this table, in our proposal, the total computational cost is only . Although our proposed scheme consumes slightly more time than some proposals [7,24,33], these extra time is because of the additional operations needed for securing the scheme (improving security pitfalls of its predecessors) and the three-factor capability, which is critical for secure HWSN networks. Finally, it is worth noticing that our results are similar to [15,45], but we offer a higher security level.

Table 4.
Overall computational overhead of the authentication phase.
8.3. Computational Cost and Execution Time
To achieve better efficiency and taking into account the energy restrictions of sensor nodes, the computation costs of sensors should be kept as low as possible. In Table 5, we summarize both the computational cost and execution time of our proposal and its predecessors [7,15,32,33,44,45]. From this, it is clear that our proposal is one of the most efficient in terms of energy and execution time. That is, our proposal can be fitted in resource-limited sensor nodes.

Table 5.
Computational cost and execution time comparison.
9. Conclusions
In heterogeneous wireless sensor networks (HWSNs), we find sensors with different capabilities and functionalities and dispersed within a defined area. Generally, their capabilities, such as computation and energy, are very limited. The security of these devices is pivotal and challenging due to its constrained resources. In this vein, we propose a secure and efficient three-factor authentication (3FA) scheme that is suitable for HWSNs and enhances the security of a recent proposed protocol [15]. Meanwhile, we showed how [15] is not resistant to user impersonation and de-synchronization attacks and also the attacker can track the user by eavesdropping only one session. In addition, an adversary can disclose the session key under the common assumption that the hardware of sensors is not tamper-resistant. To scrutinize the security of our proposal, we informally and formally analyze its security and show how our protocol guarantees all the security features and provides the highest security level in comparison with their predecessors. Moreover, in relation to performance, our scheme consumes only few milliseconds and is very efficient in terms of energy consumption. All of this renders our scheme adequate for HWSNs in which sensors generally have very limited resources. Therefore, as a future work, we aim to propose a new scheme to support user access control that guarantees authorized users to access the information allowed in HWSNs.
Author Contributions
All authors contributed equally to this work in all tasks.
Funding
This work was partially supported by the MINECO grant TIN2016-79095-C2-2-R (SMOG-DEV—Security mechanisms for fog computing: advanced security for devices); and by the CAM grant S2013/ICE-3095 (CIBERDINE: Cybersecurity, Data, and Risks).
Acknowledgments
The authors would like to thank the anonymous reviewers for their valuable comments and suggestions to improve the quality of the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jiang, Q.; Ma, J.; Yang, C.; Ma, X.; Shen, J.; Chaudhry, S.A. Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput. Electr. Eng. 2017, 63, 182–195. [Google Scholar] [CrossRef]
- Karl, H.; Willig, A. Protocols and Architectures for Wireless Sensor Networks; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Yarvis, M.; Kushalnagar, N.; Singh, H.; Rangarajan, A.; Liu, Y.; Singh, S. Exploiting heterogeneity in sensor networks. In Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies, INFOCOM 2005, Miami, FL, USA, 13–17 March 2005; Volume 2, pp. 878–890. [Google Scholar]
- Castiglione, A.; D’Arco, P.; De Santis, A.; Russo, R. Secure group communication schemes for dynamic heterogeneous distributed computing. Future Gener. Comput. Syst. 2017, 74, 313–324. [Google Scholar] [CrossRef]
- Zhong, H.; Shao, L.; Cui, J.; Xu, Y. An efficient and secure recoverable data aggregation scheme for heterogeneous wireless sensor networks. J. Parallel Distrib. Comput. 2018, 111, 1–12. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Pal, V.; Singh, G.; Yadav, R. Effect of Heterogeneous nodes location on the performance of clustering algorithms for wireless sensor networks. Procedia Comput. Sci. 2015, 57, 1042–1048. [Google Scholar] [CrossRef]
- Castiglione, A.; Palmieri, F.; Fiore, U.; Castiglione, A.; De Santis, A. Modeling energy-efficient secure communications in multi-mode wireless mobile devices. J. Comput. Syst. Sci. 2015, 81, 1464–1478. [Google Scholar] [CrossRef]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of ‘two-factor user authentication in wireless sensor networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Nyang, D.; Lee, M.K. Improvement of Das’s Two-Factor Authentication Protocol in Wireless Sensor Networks. IACR Cryptol. ePrint Arch. 2009, 2009, 631. [Google Scholar]
- Sun, D.Z.; Li, J.X.; Feng, Z.Y.; Cao, Z.F.; Xu, G.Q. On the security and improvement of a two-factor user authentication scheme in wireless sensor networks. Pers. Ubiquitous Comput. 2013, 17, 895–905. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Kumar, N.; Choo, K.K.R. An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 2017, 104, 133–144. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; Volume 1. [Google Scholar]
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2016, 9, 171–183. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Mir, O.; Munilla, J.; Kumari, S. Efficient anonymous authentication with key agreement protocol for wireless medical sensor networks. Peer-to-peer Netw. Appl. 2017, 10, 79–91. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Adavoudi-Jolfaei, A.; Ashouri-Talouki, M.; Aghili, S.F. Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer-to-peer Netw. Appl. 2017, 1–17. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Arasteh, S.; Aghili, S.F.; Mala, H. A new lightweight authentication and key agreement protocol for Internet of Things. Information Security and Cryptology (ISCISC). In Proceedings of the 2016 13th International Iranian Society of Cryptology Conference, Tehran, Iran, 7–8 September 2016; pp. 52–59. [Google Scholar]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Jiang, Q.; Chen, Z.; Li, B.; Shen, J.; Yang, L.; Ma, J. Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1061–1073. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J. Med. Syst. 2015, 39, 32. [Google Scholar] [CrossRef] [PubMed]
- Chang, C.C.; Le, H.D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Odelu, V.; Das, A.K.; Goswami, A. A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Ouafi, K.; Phan, R.C.W. Privacy of recent rfid authentication protocols. In International Conference on Information Security Practice and Experience; Springer: Berlin/Heidelberg, Germany, 2008; pp. 263–277. [Google Scholar]
- Shin, S.; Kwon, T. Two-Factor Authenticated Key Agreement Supporting Unlinkability in 5G-Integrated Wireless Sensor Networks. IEEE Access 2018, 6, 11229–11241. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Blanchet, B. Automatic verification of security protocols in the symbolic model: The verifier proverif. In Foundations of Security Analysis and Design VII; Springer: New York, NY, USA, 2014; pp. 54–87. [Google Scholar]
- Das, A.K. A secure and efficient user anonymity-preserving three-factor authentication protocol for large-scale distributed wireless sensor networks. Wirel. Pers. Commun. 2015, 82, 1377–1404. [Google Scholar] [CrossRef]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-to-peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Hellaoui, H.; Koudil, M.; Bouabdallah, A. Energy-efficient mechanisms in security of the internet of things: A survey. Comput. Netw. 2017, 127, 173–189. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H.; Sherratt, R. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).