Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol
Abstract
1. Introduction
1.1. Our Contribution
- At first, we present several serious security attacks against the Amin et al.’s scheme [15]. Our proposed attacks include de-synchronization, user impersonation, user traceability and session disclosure attacks.
- In order to increase the security level offered by Amin et al.’s protocol, we remedy the security faults found in their scheme.
- The security of the proposed scheme has be scrutinized from a formal and informal point of view. The attacks mentioned in Amin et al.’s protocol and other common security attacks have been considered in the design of the new protocol.
- The efficiency of our proposal is higher than the offered by Amin et al.’s scheme. Therefore, our scheme can be used for resource constrained sensors as the ones employed in HWSNs.
1.2. Paper Organization
2. Related Work
3. Preliminaries and Notations
3.1. Notations
3.2. Fuzzy Extractor
- The generation procedure (): given a biometric input , this probabilistic algorithm generates a secret key and a non-secret string , i.e., .
- The reproduction procedure (): given the noisy input and the corresponding auxiliary string , this algorithm is able to recover the same key as in the generation process, i.e., .
4. Review of Amin et al.’s Scheme
4.1. Pre-Deployment Phase
4.2. User Registration Phase
- Step 1.
- chooses an identity , attaches to it a personal credentials (e.g., social security number), and submits both values to the .
- Step 2.
- If the does not find in the database, it generates and calculates and . Both values () are stored in a new smartcard and the device is handed over to .
- Step 3.
- Once receiving the smartcard, chooses a password and then uses a sensor device to obtain his biometric information and finally writes to the .
- Step 4.
- uses the fuzzy extractor technique to calculate , it then computes , , , , and deletes .
4.3. Login Phase
- Step 1.
- inserts into the terminal and then enters and and also uses the sensor device to imprint his biometric information .
- Step 2.
- retrieves and computes , and . verifies the correctness of . If so, concludes , and ; otherwise, denies .
- Step 3.
- generates and computes , , and — represents the current timestamp.
4.4. Authentication and Session Key Agreement Phase
- Step 1.
- After receiving the message in login phase, the checks whether the timestamp condition holds, being the current time of . If the condition is fulfilled, the aborts the connection. Otherwise, it calculates and then decodes , and . It then computes and checks the validity of the received . If so, the identifies to as an authorized user. If not, it aborts the connection.
- Step 2.
- Then, calculates , , and . then sends the tuple to .
- Step 3.
- Upon receiving the message , checks the validity of timestamp . If , it terminates the connection. Otherwise, computes , and the and verifies the validity of received . If it is invalid, then aborts the session. Otherwise, it generates and computes as a session key and then computes and . Then, sends the tuple to .
- Step 4.
- Once the message is received, the verifies the freshness of . If , aborts the connection. Otherwise, it decodes and calculates the session key . It then computes to verify the correctness of the received . If the above verification fails, then discontinues the session. Otherwise, it calculates and forwards the message to .
- Step 5.
- Once the message is received, checks whether the condition is satisfied. If it is not fulfilled, aborts the session. Otherwise, it calculates , and to verify the correctness of the received . Now the entities are mutually authenticated and a session key has been negotiated.
4.5. Update Phase
- Step 1.
- computes and sends it to as a confirmation message. After receiving the message, decodes and updates and , where . It then computes , and and sends the tuple to .
- Step 2.
- After receiving the message , calculates to check the validity of the received . If so, it extracts and and computes . Then, rewrites to instead of previous .
4.6. Post-Deployment Phase
4.7. Password Recovery Phase
4.8. Password Change Phase
- Step 1.
- inserts in to the terminal and enters along with biometric information .
- Step 2.
- uses the fuzzy extractor technique to calculate , it then computes and . If , then requests to enter a new password at ; otherwise, aborts this procedure.
- Step 3.
- Now, calculates , , , and replaces with .
4.9. Smartcard Revocation Phase
- Step 1.
- submits and a personal credential (e.g., social security number) to the smartcard issuer.
- Step 2.
- If the smartcard issuer can find in the database, it generates and calculates and . It then writes into a new smartcard and delivers it to the user .
- Step 3.
- Once is received, chooses a password , receives new biometric information from the sensor and writes to the .
- Step 4.
- uses the fuzzy extractor technique to calculate . It then computes , , , and , and implants into and deletes .
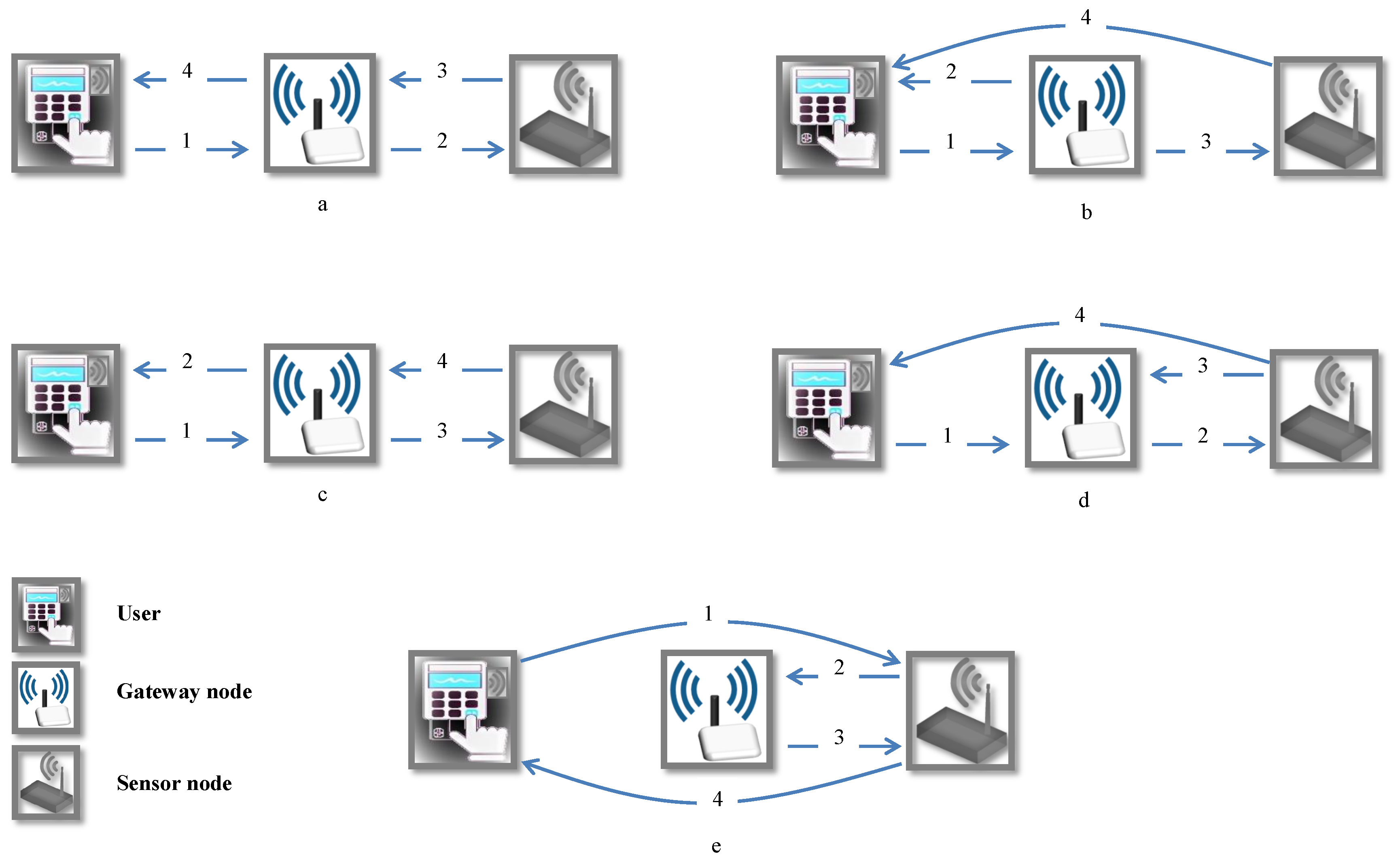
5. Security Analysis of Amin et al.’s Protocol
5.1. User Impersonation Attack
- A eavesdrops on the message sent by to the , then he changes the value to .
- After receiving the message in the login phase, the checks two issues: (1) timestamp condition and (2) validity of the received , which does not depend on . Thus, the accepts these two conditions and computes and . It then calculates . Now, the believes that A is an authorized user.
- Then, calculates and then computes , and and sends the tuple to .
- check the correctness of timestamp and computes , and and checks validity of the received . It generates and computes as a session key and then computes and . Now, the also believes that A is an authorized user and sends the tuple to .
- The checks the validity of . It decodes and computes the session key . It then computes and checks validity of the received and computes and sends the message to which is the adversary. At this point, the adversary sends the random number to as a confirmation message. After receiving the message, uses the message to obtain which is the random number. Due to the absence of any checking process, it employs this value to compute , and and then sends the tuple to the adversary.
5.2. De-Synchronization Attack
- A eavesdrops on the message from session 1;
- A eavesdrops on the message from session 2;
- A obtains from equation ;
- In Step 6 of the authentication phase, A intercepts and modifies them to , and ;
- A sends the tuple to ;
- calculates and then checks validity of the received . Then, it extracts and and computes . Then, rewrites to instead of previous .
5.3. User Traceability Attack
- Step 1.
- In round n, A sends an and eavesdrops on messages , , , and ;
- Step 2.
- The adversary A selects two users and and sends a and depending on the random bit the adversary A receives a corresponding to users ;
- Step 3.
- A sends an and eavesdrops on messages , , , and ;
- Step 4.
- A guesses the random bit if with a probability higher than a random coin flip following the procedure described below.
- Step 5.
- We have,,,
- As is constant and the user does not update it,
- If , then .
- Step 6.
- As a result, we can express ;
5.4. Session Key Disclosure Attack
- A eavesdrops on messages and ;
- A obtains from equation ;
- A obtains from equation ;
- A computes the session key using the .
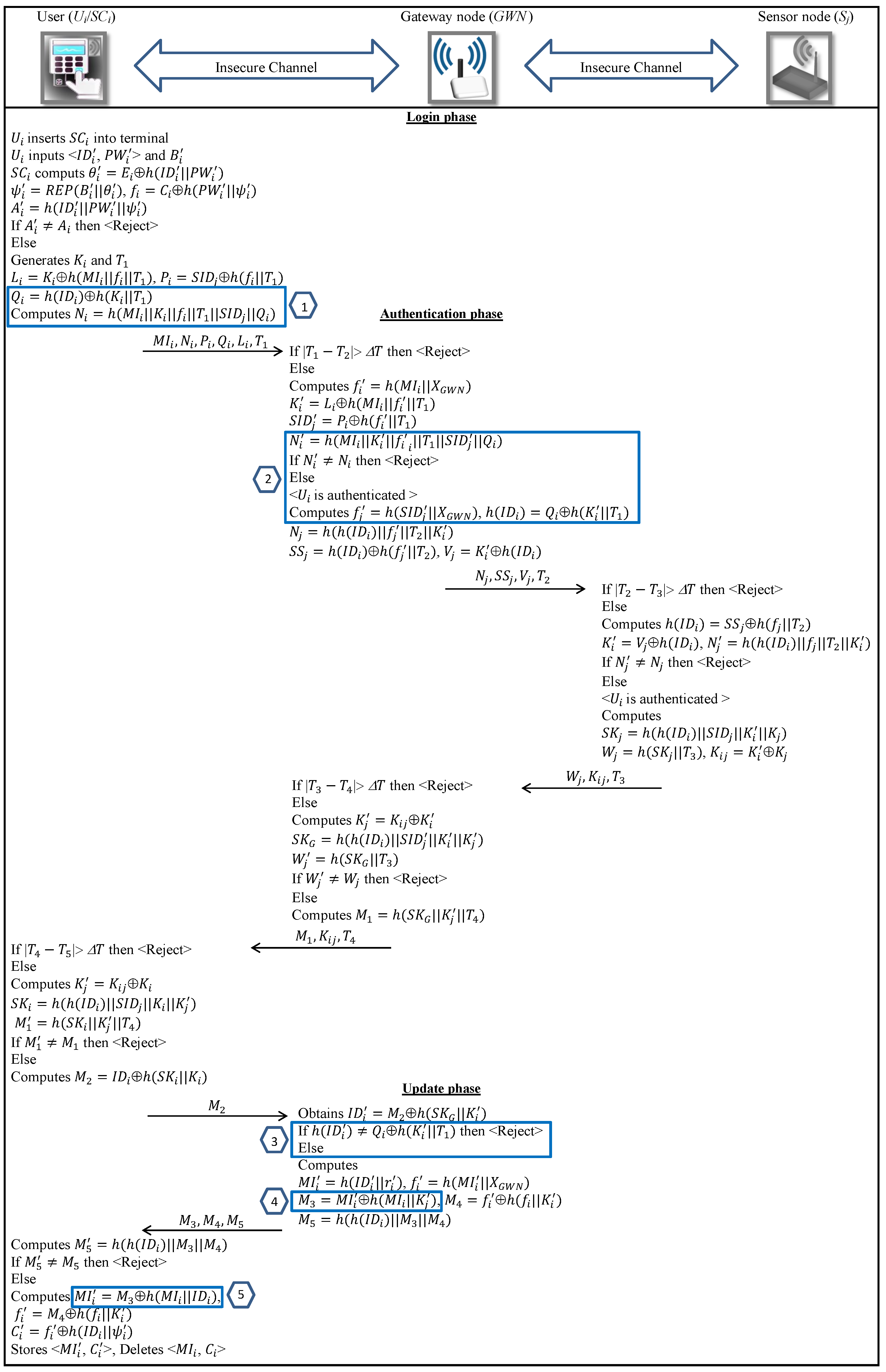
6. Our Proposed Protocol
6.1. Login Phase
- Step 1.
- inserts into the terminal and then enters and and also uses the sensor device to imprint his biometric information .
- Step 2.
- retrieves and computes , and . checks validity of . If so, implies , and ; otherwise, denies .
- Step 3.
- generates and calculates , , and , being the current timestamp.
6.2. Authentication and Session Key Agreement Phase
- Step 1.
- Once the message is received in the Login phase, the checks whether the timestamp condition holds. If the condition is fulfilled, the terminates the connection. Otherwise, it calculates and then decodes and . It then calculates and checks validity of the received . If so, the identifies to as an authorized user. If not, it terminates the connection.
- Step 2.
- Then, obtains and calculates and then computes , and , being the current timestamp. then forwards the tuple to .
- Step 3.
- Once the message is received, checks validity of the timestamp . If , it terminates the connection. Otherwise, calculates , and and checks validity of the received . If the verification fails, then aborts the session. Otherwise, it generates and computes as the session key and then computes and . Finally, sends the tuple to .
- Step 4.
- Once the message is received, the verifies the correctness of . If , aborts the connection. Otherwise, it decodes and computes the session key . It then computes and checks the validity of the received . If the above verification fails, then discontinues the session. Otherwise, it calculates and forwards the message to .
- Step 5.
- Once the message is received, checks whether the condition is satisfied. If it does not fulfilled, ends the session. Otherwise, it calculates , and and checks the validity of . At this point, the entities are mutually authenticated and a session key has been negotiated.
6.3. Update Phase
- Step 1.
- computes and sends it to as a confirmation message. After receiving the message, decodes and checks if the condition holds. If the verification fails, then aborts the session. Otherwise, it updates and , where . It then computes , and and sends the tuple to .
- Step 2.
- After receiving the message , calculates and then checks validity of . If so, it extracts and and computes . Then, rewrites to instead of previous .
7. Security Analysis of the Proposed Protocol
7.1. Informal Security Analysis
7.1.1. Stolen Smartcard Attack
7.1.2. Offline Password Guessing Attack
7.1.3. Privileged Insider Attack
7.1.4. Offline Identity Guessing Attack
7.1.5. User Impersonation Attack
7.1.6. Gateway Node Impersonation Attack
7.1.7. Sensor Node Impersonation Attack
7.1.8. Session Key Security
7.1.9. User Anonymity
7.1.10. Preserving User Untraceability
7.1.11. Replay Attack
7.2. Formal Security Analysis
8. Performance Comparison
8.1. Security Features’ Comparison
8.2. Overall Computational Overhead Comparison
8.3. Computational Cost and Execution Time
9. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Jiang, Q.; Ma, J.; Yang, C.; Ma, X.; Shen, J.; Chaudhry, S.A. Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput. Electr. Eng. 2017, 63, 182–195. [Google Scholar] [CrossRef]
- Karl, H.; Willig, A. Protocols and Architectures for Wireless Sensor Networks; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Yarvis, M.; Kushalnagar, N.; Singh, H.; Rangarajan, A.; Liu, Y.; Singh, S. Exploiting heterogeneity in sensor networks. In Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies, INFOCOM 2005, Miami, FL, USA, 13–17 March 2005; Volume 2, pp. 878–890. [Google Scholar]
- Castiglione, A.; D’Arco, P.; De Santis, A.; Russo, R. Secure group communication schemes for dynamic heterogeneous distributed computing. Future Gener. Comput. Syst. 2017, 74, 313–324. [Google Scholar] [CrossRef]
- Zhong, H.; Shao, L.; Cui, J.; Xu, Y. An efficient and secure recoverable data aggregation scheme for heterogeneous wireless sensor networks. J. Parallel Distrib. Comput. 2018, 111, 1–12. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Pal, V.; Singh, G.; Yadav, R. Effect of Heterogeneous nodes location on the performance of clustering algorithms for wireless sensor networks. Procedia Comput. Sci. 2015, 57, 1042–1048. [Google Scholar] [CrossRef]
- Castiglione, A.; Palmieri, F.; Fiore, U.; Castiglione, A.; De Santis, A. Modeling energy-efficient secure communications in multi-mode wireless mobile devices. J. Comput. Syst. Sci. 2015, 81, 1464–1478. [Google Scholar] [CrossRef]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of ‘two-factor user authentication in wireless sensor networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Nyang, D.; Lee, M.K. Improvement of Das’s Two-Factor Authentication Protocol in Wireless Sensor Networks. IACR Cryptol. ePrint Arch. 2009, 2009, 631. [Google Scholar]
- Sun, D.Z.; Li, J.X.; Feng, Z.Y.; Cao, Z.F.; Xu, G.Q. On the security and improvement of a two-factor user authentication scheme in wireless sensor networks. Pers. Ubiquitous Comput. 2013, 17, 895–905. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Kumar, N.; Choo, K.K.R. An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 2017, 104, 133–144. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; Volume 1. [Google Scholar]
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2016, 9, 171–183. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Mir, O.; Munilla, J.; Kumari, S. Efficient anonymous authentication with key agreement protocol for wireless medical sensor networks. Peer-to-peer Netw. Appl. 2017, 10, 79–91. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Adavoudi-Jolfaei, A.; Ashouri-Talouki, M.; Aghili, S.F. Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer-to-peer Netw. Appl. 2017, 1–17. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Arasteh, S.; Aghili, S.F.; Mala, H. A new lightweight authentication and key agreement protocol for Internet of Things. Information Security and Cryptology (ISCISC). In Proceedings of the 2016 13th International Iranian Society of Cryptology Conference, Tehran, Iran, 7–8 September 2016; pp. 52–59. [Google Scholar]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Jiang, Q.; Chen, Z.; Li, B.; Shen, J.; Yang, L.; Ma, J. Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1061–1073. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J. Med. Syst. 2015, 39, 32. [Google Scholar] [CrossRef] [PubMed]
- Chang, C.C.; Le, H.D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Odelu, V.; Das, A.K.; Goswami, A. A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Ouafi, K.; Phan, R.C.W. Privacy of recent rfid authentication protocols. In International Conference on Information Security Practice and Experience; Springer: Berlin/Heidelberg, Germany, 2008; pp. 263–277. [Google Scholar]
- Shin, S.; Kwon, T. Two-Factor Authenticated Key Agreement Supporting Unlinkability in 5G-Integrated Wireless Sensor Networks. IEEE Access 2018, 6, 11229–11241. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Blanchet, B. Automatic verification of security protocols in the symbolic model: The verifier proverif. In Foundations of Security Analysis and Design VII; Springer: New York, NY, USA, 2014; pp. 54–87. [Google Scholar]
- Das, A.K. A secure and efficient user anonymity-preserving three-factor authentication protocol for large-scale distributed wireless sensor networks. Wirel. Pers. Commun. 2015, 82, 1377–1404. [Google Scholar] [CrossRef]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-to-peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Hellaoui, H.; Koudil, M.; Bouabdallah, A. Energy-efficient mechanisms in security of the internet of things: A survey. Comput. Netw. 2017, 127, 173–189. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H.; Sherratt, R. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar]

| Notation | Description |
|---|---|
| The i- user | |
| The gateway node | |
| The smartcard of | |
| The j- sensor node | |
| Multiplicative group, where q is a large prime, | |
| Identity of | |
| Identity of | |
| Secret key of | |
| Secret key linked to | |
| Secret key linked to | |
| Password linked to | |
| Biometric trait linked to | |
| Nonce generated by | |
| Nonce generated by | |
| Session key | |
| Fuzzy extractor operations | |
| Outputs of algorithm | |
| Timestamp | |
| Allowable transmission delay | |
| One-way hash function | |
| ⊕ | Bitwise XOR operation |
| || | Concatenation operation |
| Notation | Description |
|---|---|
| P believes a proposition X | |
| P receives a message X | |
| P sent a message X | |
| P and X share the secret key k and only these two entities can use k to prove its identity to each other. | |
| It means that X is fresh | |
| Encryption of X using the secret k | |
| Hash computation of X using the secret k | |
| P and Q share a secret k | |
| If P then Q |
| Security Features | Amin et al. [15] | Yeh et al. [32] | Xue et al. [7] | Das [44] | Jiang et al. [33] | Das [45] | Gope et al. [24] | Ours |
|---|---|---|---|---|---|---|---|---|
| Protection of user untraceability | No | No | No | Yes | Yes | Yes | No | Yes |
| Resistance against replay attack | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes |
| Resistance against user impersonation attack | No | No | No | Yes | No | Yes | Yes | Yes |
| Resistance against gateway node impersonation attack | Yes | No | No | No | No | No | Yes | Yes |
| Resistance against sensor node impersonation attack | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Resistance to de-synchronization attack | No | No | No | No | No | No | Yes | Yes |
| Support of dynamic node addition | Yes | No | No | Yes | No | Yes | Yes | Yes |
| Robustness against insider attack | Yes | Yes | No | Yes | No | Yes | Yes | Yes |
| Robustness against stolen smartcard attack | Yes | No | No | Yes | No | Yes | Yes | Yes |
| User anonymity | Yes | No | No | No | Yes | Yes | Yes | Yes |
| Resistance against identity guessing attack | Yes | No | No | Yes | Yes | Yes | Yes | Yes |
| Support of three-factor security | Yes | No | No | Yes | No | Yes | No | Yes |
| Supports correct password update | Yes | No | No | Yes | No | Yes | No | Yes |
| Resistance against session key disclosure attack | No | Yes | Yes | Yes | Yes | Yes | No | Yes |
| Scheme | User | GW | Sensor Node | Total Cost | Rough Estimation |
|---|---|---|---|---|---|
| Amin et al. [15] | 43 ms | ||||
| Yeh et al. [32] | 100 ms | ||||
| Xue et al. [7] | 23 ms | ||||
| Das [44] | 38 ms | ||||
| Jiang et al. [33] | 23 ms | ||||
| Das [45] | 43 ms | ||||
| Gope et al. [24] | 20 ms | ||||
| Ours |
| Scheme | Computational Cost | Execution Time |
|---|---|---|
| Amin et al. [15] | 1.08 Ws | 4.24 ms |
| Yeh et al. [32] | 3.21 Ws | 26.56 ms |
| Xue et al. [7] | 1.35 Ws | 5.3 ms |
| Das [44] | 1.53 Ws | 7.8 ms |
| Jiang et al. [33] | 1.35 Ws | 5.3 ms |
| Das [45] | 1.35 Ws | 5.3 ms |
| Gope et al. [24] | 0.81 Ws | 3.18 ms |
| Ours | 1.08 Ws | 4.24 ms |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aghili, S.F.; Mala, H.; Peris-Lopez, P. Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol. Sensors 2018, 18, 3663. https://doi.org/10.3390/s18113663
Aghili SF, Mala H, Peris-Lopez P. Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol. Sensors. 2018; 18(11):3663. https://doi.org/10.3390/s18113663
Chicago/Turabian StyleAghili, Seyed Farhad, Hamid Mala, and Pedro Peris-Lopez. 2018. "Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol" Sensors 18, no. 11: 3663. https://doi.org/10.3390/s18113663
APA StyleAghili, S. F., Mala, H., & Peris-Lopez, P. (2018). Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol. Sensors, 18(11), 3663. https://doi.org/10.3390/s18113663





