Abstract
The rapid growth of Internet of Things (IoT) devices and the emergence of 5G/6G networks have created major challenges in secure and reliable data transmission. Traditional cryptographic algorithms, while robust, often suffer from high computational complexity and latency, making them less suitable for large-scale, real-time applications. This paper proposes a chaos-based encryption framework that uses the Sprott chaotic oscillator to generate secure and unpredictable signals for encryption. To achieve accurate synchronization between the transmitter and the receiver, two bio-inspired metaheuristic algorithms—the Pachycondyla Apicalis Algorithm (API) and the Penguin Search Optimization Algorithm (PeSOA)—are employed to identify the optimal control parameters of the Sprott system. This optimization improves synchronization accuracy and reduces computational overhead. Simulation results show that PeSOA-based synchronization outperforms API in convergence speed and Root Mean Square Error (RMSE). The proposed framework provides robust, scalable, and low-latency encryption for IoT and 5G/6G networks, where massive connectivity and real-time data protection are essential.
1. Introduction
The rapid expansion of Internet of Things (IoT) deployments and the growing diversity of modern communication infrastructures have generated a strong demand for lightweight and reliable security mechanisms. Many IoT nodes operate under stringent energy and computational constraints, which limits their ability to implement conventional cryptographic algorithms efficiently. As a result, alternative approaches that offer security with reduced computational overhead have attracted significant research interest.
Chaos-based secure communication is one such direction. Traditional cryptographic algorithms, including the Advanced Encryption Standard (AES) [1], the Data Encryption Standard (DES) [2], and the International Data Encryption Algorithm (IDEA), provide well-established security guarantees. However, their implementation on low-power IoT platforms may incur non-negligible latency and resource usage, especially when the protected data streams exhibit high redundancy or strong temporal correlation. This limitation has encouraged the exploration of complementary techniques based on classical encryption [3,4,5], neural networks [6], information theory [7], evolutionary computing [8], artificial intelligence [9,10], and, in particular, chaos theory [11,12,13,14].
Since the pioneering work of Pecora and Carroll [15], chaotic synchronization has been widely investigated for secure communication [16]. With the availability of low-cost embedded platforms, recent studies have demonstrated real-time implementations of chaotic oscillators and adaptive synchronization controllers [17,18]. Among the various chaotic models, the Sprott oscillator stands out for its mathematical simplicity, low computational cost, and rich dynamical behavior [19], making it an attractive candidate for lightweight physical-layer security in IoT systems.
A central requirement in synchronization-based secure communication is achieving fast and accurate convergence between the master and slave oscillators. Many existing synchronization schemes rely on adaptive or multi-loop controllers, which may increase implementation complexity and reduce practical feasibility in constrained IoT environments [20]. To address these challenges, this work introduces a synchronization-based chaotic communication framework using the Sprott oscillator, in which the intrinsic parameters and coupling gains are jointly optimized using two bio-inspired metaheuristic algorithms: the Pachycondyla Apicalis Algorithm (API) [21] and the Penguin Search Optimization Algorithm (PeSOA) [22]. These algorithms efficiently explore the parameter space and yield improved synchronization accuracy and faster convergence, even in the presence of noise and parameter uncertainty.
The main contributions of this work can be summarized as follows:
- A lightweight chaos-based secure communication framework tailored to the constraints of low-power IoT systems, relying on continuous-time synchronization of the Sprott oscillator.
- A unified joint-optimization strategy for estimating the intrinsic chaotic parameters and the coupling gains using the API and PeSOA metaheuristic algorithms.
- Demonstration that the PeSOA-based optimization achieves faster convergence and lower synchronization error compared to API.
- Robustness evaluation under noisy channels and perturbed initial states, showing stable synchronization and reliable data recovery.
- A positioning of the proposed framework with respect to recent developments in chaos-based secure communication, highlighting its low complexity and practical applicability in resource-constrained environments.
The remainder of this paper is organized as follows. Section 2 reviews related work on chaotic systems, secure communication, and bio-inspired optimization. Section 3 describes the k-Sprott chaotic oscillator. Section 4 presents the synchronization and masking mechanism. Section 5 details the API and PeSOA optimization algorithms. Section 6 reports simulation results and comparative analyses. Finally, Section 7 concludes the paper and outlines directions for future research.
2. Related Work
Chaos theory has been widely investigated in secure communication due to its sensitivity to initial conditions, broadband spectral characteristics, and complex nonlinear dynamics. Early synchronization strategies, such as the adaptive scheme of Liao and Tsai [23], demonstrated that stable chaotic synchronization can effectively support secure communication channels. Hou et al. further examined the synchronization properties of Sprott systems and confirmed their suitability for chaotic masking in secure transmission scenarios [24].
Recent studies have increasingly incorporated intelligent and data-driven techniques to enhance synchronization performance. Zhang et al. proposed an RBFNN–PSO approach capable of synchronizing the Sprott B system under external noise, achieving robustness for image-encryption tasks [25]. Yau et al. used particle swarm optimization to perform chaotic synchronization in wireless environments, illustrating the feasibility of lightweight synchronization-based cryptosystems [26]. Liu and Zuo introduced a deep adaptive synchronization mechanism combining neural models with optimization strategies, enabling high-precision tracking of chaotic trajectories [27].
Bio-inspired and swarm intelligence techniques have also been explored in secure communication. Maamri et al. applied ant colony optimization for parameter estimation in Chua’s oscillator, demonstrating that metaheuristics can substantially improve synchronization accuracy [28]. Neurobiological principles have inspired additional synchronization controllers; for instance, Samimi et al. employed a Brain Emotional Learning (BEL) model to achieve chaos synchronization for secure data transmission [29].
Beyond single-loop strategies, multi-level and cooperative synchronization architectures have been proposed. Zourmba et al. introduced a multi-level synchronization scheme designed to enhance confidentiality in secure communication systems [30]. Dinu compared Lorenz and Rössler dynamics in cryptographic contexts, emphasizing the importance of selecting suitable chaotic attractors to ensure synchronization stability and security [31]. In a related direction, Özkurt applied interpretable AI techniques to analyze chaotic time-series in industrial robots, illustrating the potential of explainable models in complex dynamical environments [32].
Chaos-based communication has also been studied in cyber–physical systems. Chen et al. proposed a chaotic masking protocol that simultaneously provides secure communication and intrusion detection [33]. At the IoT networking level, several works have highlighted the challenges posed by constrained hardware platforms and emphasized the importance of lightweight security mechanisms. Alharby et al. investigated security–energy trade-offs in IoT nodes, underscoring the need for cryptographic schemes with reduced computational cost [34].
Despite these advances, prior work has not jointly optimized the intrinsic parameters of the Sprott oscillator together with its coupling gains using bio-inspired search strategies such as API and PeSOA. Moreover, previous studies have not examined optimization-driven synchronization within the specific constraints of IoT communication, where robustness and low computational complexity are often more critical than high throughput. The present study addresses these gaps by proposing a unified synchronization and optimization framework tailored to lightweight and resource-efficient secure communication.
3. K–Sprott Oscillator
Chaotic oscillators have attracted significant attention due to their rich nonlinear dynamics and their applicability in secure communications [35], system identification [36,37], control theory, and modern cryptographic frameworks [38]. Among the various chaotic systems proposed in the literature, the Sprott family of oscillators stands out for its structural simplicity, ease of hardware implementation, and ability to generate complex attractors even under minimal mathematical formulations [39,40].
J. C. Sprott introduced nineteen minimal chaotic flows, labeled alphabetically from A to S, each exhibiting distinct dynamical characteristics despite their compact structure [19]. In this work, we consider the K–Sprott oscillator, whose mathematical model is defined as follows:
where a, b, and c are real-valued system parameters that strongly influence the system dynamics.
To illustrate the intrinsic dynamics of the K–Sprott system, Figure 1 presents the three-dimensional phase portrait and the corresponding time series of the state variables , , and for the representative parameter set , , and . The resulting trajectories exhibit sensitive dependence on initial conditions and broadband oscillatory behavior, which are key properties that make Sprott systems suitable for secure communication and signal masking applications.

Figure 1.
Chaotic behavior of the K–Sprott oscillator with , , and . The blue curve represents the chaotic attractor, while the remaining panels show the time evolution of the state variables , , and .
4. Encryption and Synchronization Process
In chaos-based secure communication, reliable transmission relies on establishing a stable functional relationship between two nonlinear dynamical systems. This mechanism, known as generalized synchronization, allows the receiver (slave) to reproduce the trajectory generated by the transmitter (master) [15]. Once synchronization is achieved, the masked information signal can be retrieved with high fidelity.
Figure 2 illustrates the chaotic masking strategy considered in this work. The master Sprott oscillator generates a chaotic carrier, to which the information signal is added.
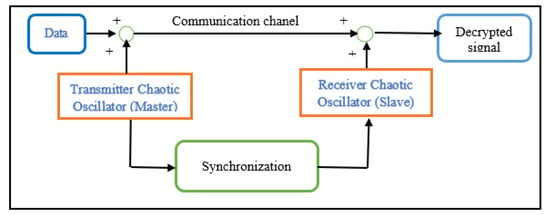
Figure 2.
Chaotic masking scheme used for secure transmission and recovery.
A slave oscillator with a similar structure attempts to track the master dynamics and recover the transmitted data after synchronization.
Synchronization is achieved using a diffusive full-state feedback controller:
where . This control law injects the instantaneous state error into the slave dynamics and promotes convergence of the synchronization error when appropriate gains are selected.
We emphasize that the controller is not updated during the RK4 numerical integration. Instead, both the control gains and the intrinsic Sprott parameters are jointly optimized at each iteration of the API or PeSOA metaheuristic algorithm. During each iteration, a candidate parameter vector is evaluated by integrating the master–slave Sprott systems with RK4 and computing the long-term synchronization error.
The master system is governed by the nonlinear dynamics
where is the state vector and denotes the intrinsic parameters of the Sprott system.
The receiver (slave) system follows the same structure but includes an external control input:
To ensure synchronization between the two chaotic systems, a diffusive full-state feedback controller is applied:
where is the vector of control gains. Because the Sprott oscillator is third-order, the synchronization error involves three state components. The controller injects these errors into the slave dynamics and drives the error toward convergence when the gains are properly chosen.
The synchronization error is defined as
and its evolution is governed by
The fourth-order Runge–Kutta (RK4) scheme is used solely to integrate the master–slave Sprott system for any candidate parameter set. Parameter tuning is not performed through numerical integration but exclusively through two bio-inspired optimization algorithms, API and PeSOA. Both methods operate on a unified decision vector
which gathers the intrinsic parameters and the diffusive control gains.
For each candidate , the master and slave oscillators are simulated using RK4, and synchronization accuracy is evaluated through a long-term error-based cost function. The metaheuristics iteratively update to minimize this cost, jointly estimating the intrinsic parameters and the coupling gains required to ensure complete synchronization and correct recovery of the masked signal.
Figure 3 summarizes the overall communication process, where the optimization stage precedes message reconstruction to ensure fast and reliable synchronization.

Figure 3.
Flowchart of the proposed chaotic synchronization and secure communication mechanism.
The synchronization performance is quantified using the cost function
which provides a uniform measure of convergence across all state variables.
Table 1 summarizes the admissible parameter ranges of the Sprott system and the integration step used in the simulations. These ranges ensure chaotic behavior while enabling stable numerical integration.

Table 1.
Simulation parameters for the synchronization process.
5. Optimization-Based Synchronization and Stability Analysis
5.1. Pachycondyla Apicalis Algorithm (API)
The Pachycondyla Apicalis (API) algorithm is a bio-inspired optimization method derived from the foraging strategy of the ant species Pachycondyla apicalis. This algorithm was originally introduced by Monmarché, Venturini, and Slimane, who demonstrated that the ants’ hunting-site exploration and abandonment mechanism can be translated into an efficient search procedure [41]. In their model, each ant maintains a set of hunting sites around the nest and repeatedly explores, evaluates, and updates these sites according to their success. Figure 4 provides a simplified illustration of this exploration principle.

Figure 4.
Exploration mechanism in the Pachycondyla Apicalis (API) algorithm.
In the context of optimization, each ant represents a potential solution. During the search process, ants explore their neighborhood, retain promising hunting sites, and discard those that repeatedly fail. When all ants agree that the current nest position is no longer optimal, the nest is relocated to the best site found so far, enabling global exploration while preserving local improvement capacities.
The overall global foraging strategy is summarized in Algorithm 1, while the local exploration behavior of each ant is detailed in Algorithm 2.
| Algorithm 1 Global Foraging Strategy of the API Algorithm |
|
| Algorithm 2 Local Foraging Behavior of an Ant |
|
5.2. Penguin Search Optimization Algorithm (PeSOA)
The Penguin Search Optimization Algorithm (PeSOA) is a bio-inspired metaheuristic that models the cooperative foraging behavior of penguin colonies. In nature, penguins dive in groups, adjust their trajectories according to previously successful dives, and communicate information about profitable feeding zones. PeSOA translates this collective strategy into an optimization process where each penguin represents a candidate solution exploring a specific region of the search space.The PeSOA algorithm imitates the foraging behavior of penguins [36,42].
At initialization, the population is divided into several subgroups, each assigned to a distinct exploration area. Within each subgroup, penguins update their positions using three main mechanisms: (i) local improvement based on their previous dive, (ii) movement toward the best solution found by the subgroup, and (iii) random perturbations to preserve exploration capability. An energy-like variable, referred to as the oxygen reserve, limits the number of consecutive dives and naturally balances exploration and exploitation. When a candidate solution improves its fitness, the penguin replenishes oxygen and continues exploring; otherwise, oxygen decreases until a new dive strategy is required. Throughout the search, the global best solution is continuously updated as penguins share information across groups. The procedure terminates when either the maximum number of iterations is reached or the convergence criterion is satisfied, as described in Algorithm 3.
| Algorithm 3 Penguin Foraging Strategy (PeSOA) |
|
5.3. Lyapunov Stability Analysis
The reliability of the proposed synchronization-based secure communication scheme depends directly on the stability of the error dynamics between the master and slave K–Sprott oscillators. In the following, Lyapunov theory is employed in two complementary ways: (i) to verify that the master oscillator operates in a chaotic regime suitable for encryption, and (ii) to demonstrate the stability of the synchronization process required for successful decryption.
Figure 5 presents the cumulative Lyapunov exponents of the master K–Sprott attractor over an 80 s simulation interval. The spectrum exhibits one strictly positive exponent, one approximately zero exponent, and one negative exponent. This configuration is the classical hallmark of deterministic chaos, confirming that the K–Sprott oscillator provides the high-entropy dynamics required to ensure sensitivity, diffusion, and unpredictability in the chaotic masking process.
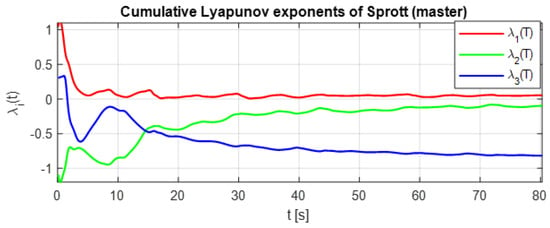
Figure 5.
Lyapunov exponents of the K–Sprott system for the optimized parameters.
Let and denote the master and slave state vectors, and define the synchronization error as
A standard Lyapunov candidate is the quadratic function
which is positive definite for all . The sign of its time derivative determines whether the synchronization error decreases with time.
The control input applied to the slave system,
implements a diffusive full–state feedback law. The gains are not derived analytically; they are part of the parameter vector
which is optimized by the API and PeSOA metaheuristic algorithms. During each optimization iteration, a candidate is evaluated by integrating the master–slave K–Sprott system using RK4 and computing the resulting synchronization error. The bio-inspired algorithms then update to minimize this error, thereby automatically selecting the controller gains that ensure convergence.
Under the optimized gains , the Lyapunov derivative satisfies
for sufficiently small . This strict negativity demonstrates contraction of the error system and guarantees that the slave trajectory converges to the master trajectory, thus stabilizing the synchronization manifold.
To complement this local Lyapunov-function-based stability result, the transverse Lyapunov exponent of the synchronization error system is computed numerically. A negative transverse exponent indicates exponential decay of perturbations, whereas a positive value signals divergence. Simulations show that both API and PeSOA yield negative transverse exponents, with PeSOA achieving the most negative value—consistent with its faster convergence and lower RMSE.
This stability is preserved in the presence of practical impairments such as additive white Gaussian noise and mismatched initial conditions. When moderate AWGN is added to the encrypted signal, the PeSOA- optimized system maintains a negative transverse exponent, confirming resilience against channel disturbances. Furthermore, the system remains highly sensitive to incorrect initialization: if the receiver does not use the correct optimized parameters, the transverse exponent becomes positive, synchronization collapses, and message recovery becomes impossible—thus preventing unauthorized access.
Having established both the chaotic nature of the master system and the stability of the optimized synchronization scheme, the next section evaluates how effectively the API and PeSOA algorithms enhance master–slave synchronization. Since accurate synchronization is a prerequisite for successful chaotic masking and reliable data recovery, we now examine the synchronization error, convergence rate, and the influence of the optimized coupling gains.
6. Results and Discussion
Compared with several existing chaotic synchronization techniques—which may rely on multi-layer architectures, fixed chaotic parameters, or computationally demanding adaptive controllers—the method proposed in this work adopts a lightweight design based on the joint optimization of the intrinsic parameters of the Sprott oscillator and its coupling gains. By combining the strengths of API and PeSOA, the framework achieves rapid synchronization, low RMSE, and stable behavior under noise and parameter variations. These properties make the method suitable for secure communication in resource-constrained IoT settings, where robustness and computational efficiency are often more critical than high data rates.
To contextualize the proposed approach, Table 2 summarizes several representative synchronization methods from the literature and contrasts their design principles, computational requirements, and performance characteristics with those of the present work.

Table 2.
Comparative summary of representative chaotic synchronization methods.
Overall, the results demonstrate that metaheuristic-based joint optimization offers a practical compromise between synchronization accuracy, robustness, and implementation simplicity. The proposed framework is developed without relying on multi-level or deep-learning-based synchronization schemes, while achieving strong performance across a range of operating conditions. This makes it a suitable candidate for secure physical-layer communication in resource-limited IoT environments.
The analysis begins by confirming that the Sprott oscillator preserves its chaotic behavior under all tested configurations. This validation is essential, as the unpredictability, broadband spectrum, and sensitivity to initial conditions of the chaotic carrier form the foundation of synchronization-based masking mechanisms.
In this work, the API and PeSOA metaheuristic algorithms are employed to address a coupled identification–synchronization problem involving the Sprott system. The unknown quantities are grouped into a single decision vector
where denote the intrinsic coefficients of the oscillator and represent the diffusive coupling gains required to drive the slave system toward the master trajectory. For each candidate vector , the master–slave model is numerically integrated and a synchronization cost—defined as the mean squared deviation between the trajectories—is evaluated.
The exploration strategies of the two bio-inspired optimizers enable systematic navigation of the parameter space. PeSOA imitates cooperative diving behavior to guide the search, whereas API models reinforced foraging. Through iterative refinement, both algorithms adjust the six unknown parameters until the synchronization error is minimized. Once the intrinsic parameters and coupling gains are optimized, the slave oscillator closely replicates the master trajectory, enabling robust chaotic masking at the transmitter and accurate reconstruction at the receiver. This optimization stage therefore forms a central component of the proposed secure communication framework.
For the API configuration, the optimizer uses artificial ants and a local search depth of , providing a suitable balance between exploration efficiency and computational cost—an important consideration for resource-constrained IoT devices. The PeSOA configuration employs five groups of six penguins () with an initial oxygen level of , enabling reliable convergence within modest computational time.
To ensure persistent chaotic behavior, the parameters of the Sprott model are restricted to the practical intervals , , and . A sampling step of ms is adopted to provide an adequate compromise between numerical accuracy and integration speed, ensuring that the chaotic trajectories remain well resolved while keeping the computational load manageable. Likewise, the adoption of a 500-sample simulation horizon ensures that each optimization cycle remains tractable, particularly when repeated across many iterations.
These choices reflect practical constraints encountered in IoT and embedded implementations, where computational resources are limited and synchronization must be achieved efficiently. The resulting parameter configuration is therefore consistent with both the operational characteristics of resource-limited communication devices and the numerical requirements of evaluating chaotic synchronization.
Table 3 summarizes the main simulation settings, including the hyperparameters of API and PeSOA as well as the operating ranges of the k-Sprott chaotic system.

Table 3.
Practical simulation parameters for the API and PeSOA algorithms optimizing the K-Sprott system in IoT scenarios.
The following figure illustrates the data signal, highlighting the transformed representation of the original information.
As clarified in Figure 6, the data signal used in our simulation is a randomly generated test sequence introduced solely for evaluating the performance of the proposed metaheuristic–optimized synchronization and decryption process.
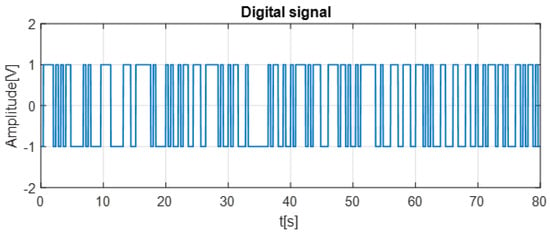
Figure 6.
Data signal used as the input message before chaotic encryption.
Figure 7 illustrates the comparison between the original data signal and the encrypted signal generated using the chaotic K–Sprott oscillator. The encrypted signal forms a highly irregular and broadband chaotic trajectory. This behavior results from the chaotic masking process.
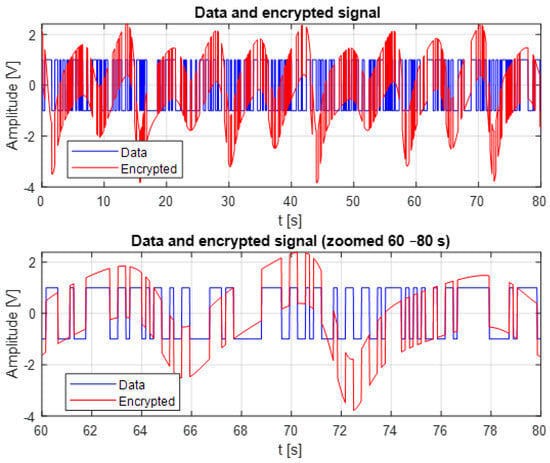
Figure 7.
Encrypted signal compared to the original data signal.
The superposition of the two signals shows that the chaotic component dominates the encrypted signal, effectively hiding the structure of the original data. As a result, no visible pattern, statistical regularity, or amplitude transition can be exploited to infer the underlying information without proper synchronization between the master and slave oscillators. This masking property represents a key security feature of chaos-based encryption.
The zoomed segment (60–80 s) further demonstrates how the chaotic waveform overwrites all recognizable characteristics of the data signal. Even fine transitions in the original data are fully embedded within the chaotic dynamics, confirming strong diffusion and obfuscation. At the same time, the embedded information remains recoverable at the receiver side, provided that accurate synchronization is maintained. These results show that the proposed chaotic masking scheme ensures an effective balance between confidentiality and recoverability, making it suitable for lightweight real-time secure communication.
In Figure 8, the identification of the control parameters is illustrated using the API and PeSOA algorithms in the synchronization process. This step is essential because accurate parameter estimation directly impacts the ability of the slave chaotic system to track the dynamics of the master system. Without precise parameter tuning, synchronization errors can occur, leading to instability and poor performance in chaos-based communication systems.
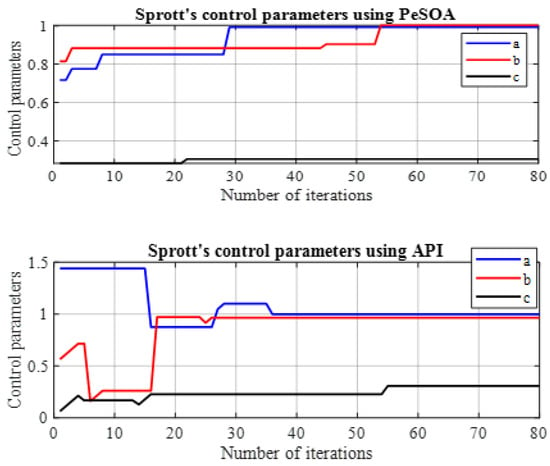
Figure 8.
Identification of the K–Sprott control parameters using API and PeSOA algorithms in the synchronization process.
As shown in Figure 8, this process requires several iterations to identify the control parameters and is applied to a signal whose duration is .
The parameters and initial conditions of the K–Sprott oscillator are summarized in Table 4.

Table 4.
K–Sprott oscillator parameters, initial conditions, and numerical integration setup.
For each configuration, the master–slave system was numerically integrated over a full 500-bit encrypted transmission. In all cases, the system trajectories remained bounded, non-periodic, and highly sensitive to initial conditions—three key indicators of chaotic behavior. Furthermore, the Lyapunov trends obtained for each parameter set were consistent with the baseline configuration, confirming that variations in do not shift the system outside the chaotic region.
The selected integration steps (0.09–0.11 ms) provided numerically stable RK4 integration while preserving a temporal resolution compatible with practical IoT sampling constraints. Importantly, these values of did not alter the qualitative chaotic dynamics: synchronization and decryption performance remained stable across all tested configurations.
To further evaluate the robustness of the proposed communication framework, additional experiments were performed under additive channel noise and perturbed initial conditions for both master and slave oscillators. Such tests are essential for validating synchronization reliability in realistic IoT and wireless environments, where noise, parameter uncertainty, and drift are unavoidable. The results demonstrate that the optimized parameters , obtained via API and PeSOA, maintain stable convergence even in the presence of moderate AWGN. The decrypted signal remains accurate, and the synchronization error consistently exhibits a negative Lyapunov exponent, confirming that the error dynamics continue to contract toward zero despite stochastic disturbances.
The system also retains its intrinsic sensitivity to initial conditions—a desirable security property—while still enabling successful synchronization when the legitimate receiver uses the correct optimized parameters. When the receiver operates with mismatched or perturbed initial conditions, synchronization fails and the transmitted message cannot be reconstructed. This behavior confirms that the framework combines two essential features: (i) robustness against physical channel noise, and (ii) inherent security against unauthorized receivers due to instability of the error dynamics under incorrect initialization.
The objective function was specifically formulated to optimize all intrinsic and coupling parameters through the two bioinspired metaheuristics: PeSO and API. The PeSOA simulates the cooperative hunting behavior of penguins, enabling an efficient balance between exploration and exploitation, the API algorithm models the foraging behavior of Pachycondyla apicalis ants, allowing broad exploration of the search space, Through iterative adjustment of and the coupling gains , both algorithms minimize the master–slave synchronization error. Improved synchronization directly enhances the stability and accuracy of the chaotic masking process, ensuring secure transmission and reliable recovery of the encrypted signal at the receiver.
A detailed performance comparison between the two algorithms, based on the RMSE histograms provide further insight: the API algorithm produces a wider and more dispersed error distribution, reflecting slower convergence and greater variability. In contrast, PeSOA generates a compact, low-RMSE distribution, demonstrating higher efficiency, numerical stability, and convergence reliability.
After multiple simulation trials, these trends remain consistent: both algorithms eventually converge, but PeSOA does so more rapidly, with fewer fluctuations, and while exploring the same search domain. Consequently, PeSOA achieves higher accuracy and offers a more robust and effective approach for optimizing chaotic synchronization.
Overall, the results confirm that PeSOA explores the solution space more efficiently and determines optimal synchronization gains with higher precision. Its improved robustness and reliability make it particularly suitable for chaotic communication systems operating in noisy or resource-constrained IoT environments.
The results shown in Figure 9 highlight the relevance of the proposed synchronization framework for IoT communication scenarios that require stable timing and low-latency data exchange. In such contexts, maintaining accurate synchronization between the transmitter and the receiver is essential to ensure reliable and secure information transfer. A smooth and decreasing RMSE profile reflects effective alignment of the chaotic systems over time. The comparative results indicate differences in convergence behavior between the PeSOA- and API-based synchronization strategies, which is an important consideration for time-sensitive IoT applications such as industrial automation, medical monitoring, and sensor-based systems.
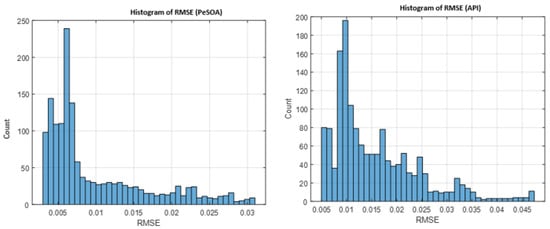
Figure 9.
Statistical distribution of the synchronization error (RMSE) for PeSOA and API algorithms.
The histogram further examines the statistical behavior of the synchronization error over multiple trials. The RMSE distribution obtained using the PeSOA algorithm appears more concentrated around lower values, suggesting a consistent synchronization performance under the considered numerical and dynamical conditions. In contrast, the API algorithm exhibits a wider spread with more occurrences of higher RMSE values, reflecting greater variability and reduced stability. Such fluctuations may degrade communication reliability when channel conditions are uncertain or slightly perturbed.
Overall, the histogram analysis confirms that PeSOA provides a more stable and predictable synchronization process, making it a more suitable candidate for secure and efficient chaotic communication in IoT environments.
To further evaluate the synchronization quality achieved by both algorithms, the Hilbert transform is employed to analyze the instantaneous amplitude and phase of the master and slave chaotic signals. The Hilbert transform is particularly suitable for nonlinear and time-varying signals such as those generated by the Sprott system. By constructing the analytic signal , one can extract the instantaneous amplitude and phase , providing deeper insight into the dynamical coherence between transmitter (master) and receiver (slave).
Figure 10 presents the instantaneous amplitude, instantaneous phase, and phase difference for the PeSOA (top panels) and API (bottom panels) algorithms. The difference in synchronization performance is clearly visible.
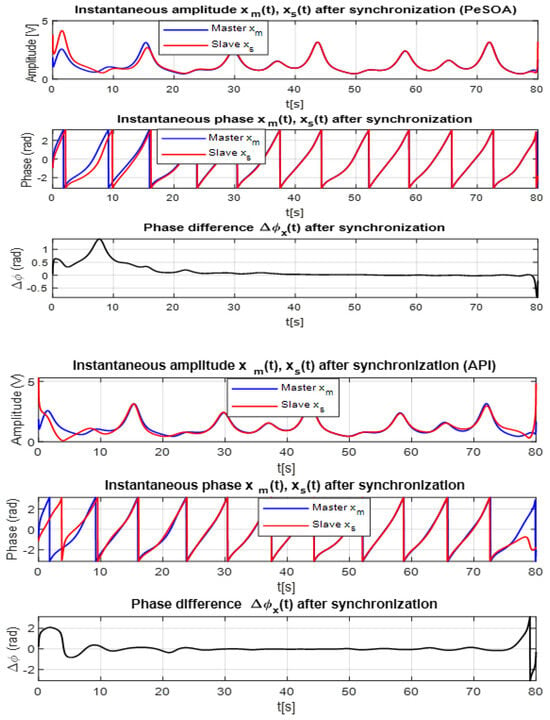
Figure 10.
Comparison of Hilbert transforms for master and slave signals using API and PeSOA algorithms. The top panels correspond to PeSOA and the bottom panels to API.
For the PeSOA-based synchronization, the master and slave amplitudes almost perfectly overlap, and the corresponding instantaneous phases remain closely aligned throughout the entire time interval. The phase difference rapidly converges toward zero and remains stable, indicating that the slave system accurately tracks the master with minimal deviation. This behavior confirms a high-quality synchronization process.
In contrast, the API-based synchronization exhibits noticeable divergence between the master and slave amplitudes, and the instantaneous phase alignment is less consistent. The resulting phase difference shows larger fluctuations and slower decay, reflecting lower synchronization accuracy and reduced stability compared to PeSOA.
The Hilbert-transform analysis confirms that PeSOA achieves more precise and reliable synchronization. This improved phase coherence is particularly important in secure chaotic communication systems, where even small phase mismatches can cause decoding errors or information loss. The strong phase alignment obtained with PeSOA directly contributes to more robust and consistent message recovery under practical communication conditions.
To illustrate the data transmission mechanism used in this work, Figure 11 presents an example of chaotic masking that is independent of the chosen synchronization algorithm. In this figure, the encrypted signal is obtained by adding the original data to the chaotic waveform generated by the master oscillator. Because the data is directly embedded in the chaotic fluctuations, it becomes visually indistinguishable within the irregular red curve. The received signal in black corresponds to the encrypted waveform after passing through an AWGN channel; its overall shape remains similar, showing that the chaotic masking technique used in this work preserves the structure of the signal even under noisy transmission conditions.
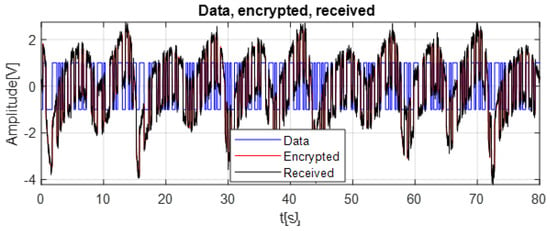
Figure 11.
Comparison of Original Data, Encrypted Chaotic Signal, and Received Noisy Signal.
Figure 12 illustrates the error in the received signal before synchronization, caused by encryption using a chaotic signal. The error signal exhibits irregular and unpredictable fluctuations, which are characteristic of the chaotic nature of the encryption process. These fluctuations indicate a significant mismatch between the transmitted and received signals.

Figure 12.
Error in the received signal before synchronization.
The decrypted signal after synchronization using the API and PeSOA algorithms are shown in Figure 13, this figure presents the original data signal (blue), the encrypted signal generated by combining the data with the K-Sprott chaotic signal prior to transmission (red), and the decrypted signal reconstructed after the synchronization process (green). The results obtained using the PeSOA algorithm are displayed in the upper panels, while those corresponding to the API algorithm are shown in the lower panels. To further evaluate the synchronization accuracy and decryption quality, a zoomed-in view of the interval to is provided for each algorithm. These visualizations clearly highlight the ability of both approaches to recover the transmitted information, with noticeable variations in performance between the two methods.
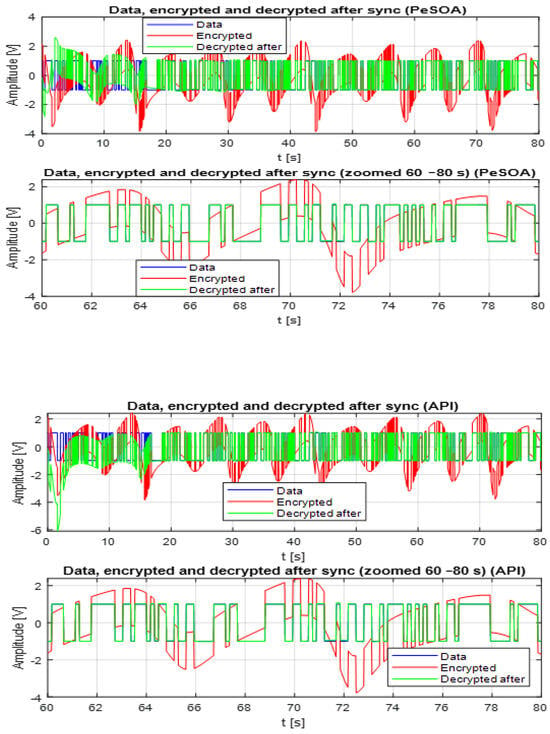
Figure 13.
Decrypte Signal using PeSOA and API.
In both Algorithms, the errors converge toward zero, as shown in Figure 14, indicating that the synchronization process was successful and that the transmitted and received signals are nearly identical. Notably, the smoother and faster decay observed with PeSOA highlights its superior performance over API in minimizing synchronization errors and ensuring accurate signal transmission.
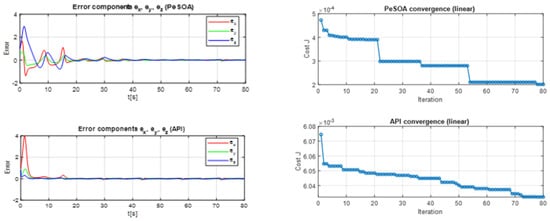
Figure 14.
Evolution of Synchronization Errors and Cost Function Convergence for PeSOA and API.
Figure 15 illustrates the synchronization behavior between the master and slave Sprott systems obtained using the PeSOA-optimized controller. In the 3D phase portrait (left panel), the two trajectories initially exhibit different paths during a short transient period, after which the slave trajectory gradually converges toward that of the master. Once the transient phase ends, the two curves completely overlap, indicating that the synchronization error has vanished and that both systems evolve identically. This result is confirmed in the right panel, where the state–state projection approaches the diagonal line, demonstrating complete synchronization. Such convergence is essential in secure chaotic communication: only when the receiver reproduces the master dynamics with high accuracy can the masked data be correctly extracted and decrypted. Therefore, the behavior shown in Figure 15 validates the effectiveness of the proposed synchronization scheme for reliable secure data transmission.
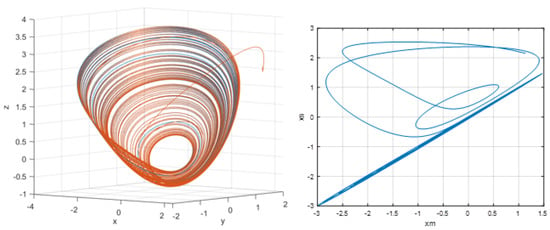
Figure 15.
Synchronization of the master and slave Sprott systems using the PeSOA algorithm. The left panel shows the 3D phase portrait, where the slave trajectory converges toward the master attractor. The right panel presents the corresponding state-space projection ,
The 3D phase portrait (left panel) clearly demonstrates that the trajectories of the master (blue) and slave (red) systems completely overlap, indicating that the synchronization error has converged to zero. This confirms that the slave system is able to precisely track the chaotic dynamics of the master, which is a fundamental requirement for the reliable decryption of transmitted signals.
Unlike recent studies such as the OptiSecure-3D algorithm [43], which focuses primarily on image encryption using chaotic maps and deep learning techniques, or the DTSPC diagnostic method introduced by Lin and Pattanayak [44] for quantitatively measuring synchronization complexity, the proposed work addresses the fundamental problem of chaotic system synchronization. By optimizing the control parameters through bio-inspired algorithms (API and PeSOA), our approach improves the stability and accuracy of the master-slave systems, providing a robust foundation for secure and real-time chaotic communication.
Both algorithms exhibit adaptive mechanisms—reinforcement and relocation in API, and cooperative diving and regrouping in PeSOA—that reflect the type of rapid adjustments required in practical communication systems operating under strict latency, limited computational resources, and channel perturbations. These examples therefore not only clarify the internal functioning of the algorithms but also emphasize their suitability for secure chaotic synchronization in realistic 5G/6G and IoT environments. 1—API (Alternative Illustration Method) Instead of presenting raw numerical iterations, the process showing how API progressively refines the parameter vector. Each ant represents a candidate set of k-Sprott parameters and coupling gains. During the first iterations, ants explore widely separated regions of the parameter space, producing significantly different synchronization errors. As the algorithm proceeds, the best-performing ant reinforces its search direction by locally perturbing its hunting site, while ants with persistently poor performance abandon their current sites and relocate to unexplored regions. This mechanism naturally drives the population toward the region of the parameter space where the synchronization error decreases most rapidly. After several cycles, all ants converge to a narrow band of parameter values, and the error stabilizes at its minimum value. This example is included to illustrate how the reinforcement/abandonment mechanism effectively balances exploration and exploitation while improving synchronization accuracy. 2—PeSOA (Alternative Illustration Method) At the beginning, individual penguins dive at different depths, generating trial solutions with diverse performance levels. The penguin achieving the lowest synchronization error becomes the leader of the colony. Subsequently, the other penguins adjust their positions by moving toward this leader, while still performing localized dives to refine their trajectories. Over successive iterations, the colony progressively contracts around the best parameter region, and the synchronization error decreases monotonically. This behavior demonstrates how PeSOA combines global exploration (via deep dives) with local refinement (via regrouping) to accelerate convergence. The example illustrates how the colony’s cooperative dynamics guide the optimization toward stable and accurate synchronization.
The parameter settings of the metaheuristic optimization algorithms used in this study are summarized in Table 5.

Table 5.
Metaheuristic settings for parameter identification.
The optimization behavior illustrated in the API and PeSOA examples is motivated by practical constraints commonly encountered in IoT and URLLC scenarios. In such environments, synchronization is typically required under stringent latency budgets, limited computational resources, and the presence of channel perturbations. The iterative adjustment mechanisms of both algorithms—reinforcement and relocation in API, and cooperative diving and regrouping in PeSOA—are conceptually aligned with adaptive strategies considered for communication in noisy and time-constrained conditions. These dynamics facilitate the identification of parameter configurations leading to reduced synchronization error, in line with latency requirements typically associated with URLLC and the energy-efficiency considerations of IoT devices. Consequently, the presented examples illustrate the operational behavior of the optimization algorithms and their relevance to chaos-based secure communication frameworks in modern 5G/6G-oriented environments.
6.1. Throughput and Latency Analysis
The intrinsic throughput of the proposed chaos-based communication scheme was evaluated for two operating modes corresponding to BPSK and QPSK symbol mapping. In the configuration adopted in this study, the chaotic encoder produces approximately 200 bps in BPSK mode and around 1000 bps (1 kbps) in QPSK mode. These values represent the raw bitstream generated by the chaotic masking mechanism and are determined by the chosen sampling interval and the number of samples per symbol required for stable synchronization.
It is important to emphasize that the chaotic masking operates as an analog-domain security layer and does not modify the physical-layer modulation or framing of the underlying IoT transceiver. As a result, the achievable radio-layer throughput remains governed by the PHY configuration of the communication device. In many IoT scenarios—including massive machine-type communications (mMTC) and reduced-capability (RedCap) services within emerging 5G/6G systems—the exchanged payloads consist of low-rate measurements or short control packets. In such cases, robustness, low computational cost, and energy efficiency are typically more critical than very high throughput.
The intrinsic data rate of the chaotic encoder is therefore compatible with these categories of applications, which often operate far below the maximum available PHY-layer capacity. Table 6 summarizes the intrinsic chaotic throughput and provides representative IoT physical-layer rates from the literature [45]. While the chaotic layer produces a relatively low-rate encrypted stream, it does not introduce additional latency or throughput penalties at the radio interface. This makes the proposed scheme suitable for low-rate but security-sensitive IoT and future communication services that require lightweight physical-layer protection.

Table 6.
Intrinsic throughput of the proposed chaotic encoder and representative IoT PHY-layer rates.
6.2. Evaluation of Sensitivity to Initial Conditions
The influence of initial-condition mismatch on the synchronization performance was examined for both the PeSOA-optimized controller and the API-based configuration. The key performance indicators are summarized in Table 7.

Table 7.
Synchronization performance comparison between PeSOA and API.
The PeSOA-based controller exhibited stronger dynamical stability, as confirmed by its more negative Lyapunov exponent and its lower tail RMSE and MSE. These values indicate rapid contraction of the synchronization error and reliable convergence to the synchronized state. Under nominal conditions, PeSOA achieved a post-decryption BER of 1.0%, and the BER remained below 5% even when the receiver initial conditions were perturbed by 20%. This demonstrates a high degree of robustness to initialization uncertainty.
The API-based configuration also achieved synchronization but with weaker stability characteristics. Its Lyapunov exponent was closer to zero, and its steady-state error was approximately twice that of PeSOA. The BER after decryption increased to 1.6%, and sensitivity to initial-condition mismatch was higher, with a BER of 6.4% for a 20% perturbation. The significantly larger optimized gains produced by API suggest a more aggressive and less stable control response, consistent with its higher synchronization error.
Overall, the results indicate that PeSOA provides superior synchronization accuracy, stronger dynamical contraction, and better robustness to initial-condition perturbations compared to API. This makes PeSOA a more suitable optimization strategy for chaos-based secure communication systems.
To contextualize these findings within the broader security landscape of IoT and emerging communication technologies, Table 8 provides a qualitative comparison of representative security mechanisms and communication schemes commonly considered in constrained environments.

Table 8.
Comparative analysis of security mechanisms relevant to IoT and low-rate services in emerging communication systems.
Table 8 summarizes the main characteristics of representative security mechanisms considered for IoT and low-rate service classes in emerging communication systems. URLLC-oriented secure IoT communication frameworks [45] are designed to provide high reliability and stringent latency guarantees, but their associated security processing and system complexity may pose challenges for highly resource-constrained IoT nodes. Lightweight chaos-based encryption schemes [11] and secure wireless IoT communication approaches based on chaos synchronization [26] aim to achieve a more balanced trade-off between computational efficiency and security, which improves their applicability in embedded and wireless environments.
Chaotic encryption and synchronization schemes [16,20], by contrast, typically rely on low-complexity nonlinear dynamics and can exhibit inherent robustness under noisy transmission conditions. Building on these principles, the proposed chaotic masking approach combined with API/PeSOA-based parameter optimization achieves low processing latency, stable synchronization behavior, and robustness to parameter mismatch within the considered scenarios. These characteristics indicate that the proposed method could be considered a lightweight security mechanism for IoT applications and low-rate services in future communication infrastructures, especially in scenarios where energy efficiency and reduced computational overhead are relevant.
In addition to the mechanisms summarized in Table 8, several complementary studies have investigated latency modeling and resource allocation in next-generation communication networks [46,47], as well as the analysis, synchronization, and secure communication capabilities of nonlinear and chaotic systems [48,49,50,51], providing a broader context for the considered security and synchronization approaches.
7. Conclusions
This work presents a chaos-based secure communication framework built upon the K–Sprott oscillator and enhanced through two bio-inspired optimization algorithms, Pachycondyla Apicalis (API) and the Penguin Search Optimization Algorithm (PeSOA). By jointly tuning the intrinsic chaotic parameters and the coupling gains, the proposed approach enables accurate synchronization while maintaining low computational cost, making it suitable for lightweight security in constrained environments.
Simulation results indicate that the PeSOA-optimized configuration consistently outperforms the API-based solution, achieving faster convergence, lower synchronization error, and improved robustness to variations in initial conditions. These properties are particularly relevant for IoT devices and for low-rate services in emerging communication infrastructures, where simplicity, robustness, and energy efficiency are often more critical than high throughput.
The automatic adaptation of the synchronization parameters contributes to the practical applicability of the framework, especially in embedded platforms with limited processing capabilities. The resulting synchronization stability and modest computational requirements highlight the potential of the proposed scheme as a lightweight physical-layer security mechanism for applications such as biomedical monitoring, environmental sensing, industrial automation, and smart-grid data acquisition.
Future work will explore hardware implementation on FPGA or low-power microcontroller platforms, alongside real-world experimentation under realistic wireless-channel conditions. These developments aim to evaluate the scalability, energy efficiency, and practical feasibility of the proposed chaos-based communication framework within next-generation IoT and future communication systems.
Author Contributions
Conceptualization, F.M.; methodology, F.M.; formal analysis, H.D. and F.B.; writing—review and editing, S.B., M.A.A. and I.B.; supervision, A.S. and Y.A.; writing—original draft preparation, F.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
All data used in this study are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Nechvatal, J.; Barker, E.; Bassham, L.; Burr, W.; Dworkin, M.; Foti, J.; Roback, E. Report on the Development of the Advanced Encryption Standard (AES). J. Res. Natl. Inst. Stand. Technol. 2001, 106, 511–577. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential Cryptanalysis of DES-like Cryptosystems. In Advances in Cryptology—Proceedings of CRYPTO ’90; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1990; pp. 2–21. [Google Scholar]
- Astillero, R. Optimizing Advanced Encryption Standard (AES) for Enhanced File Security in University Networks Using Dynamic Key Expansion. Technol. A Glob. J. Technol. Dev. Sci. Innov. 2024, 3, 51–59. [Google Scholar] [CrossRef]
- George, A.; Dubal, A. Analysis of Image Encryption Using Triple DES. Int. J. Res. Appl. Sci. Eng. Technol. 2024, 12, 1557–1563. [Google Scholar] [CrossRef]
- Giovani, E.S.; Sapri, S.; Jumadi, J. Implementation of the International Data Encryption Algorithm (IDEA) in Web-Based Database Security. J. Komput. Indones. 2023, 2, 125–130. [Google Scholar] [CrossRef]
- Dong, T.; Huang, T. Neural Cryptography Based on Complex-Valued Neural Network. IEEE Trans. Neural Netw. Learn. Syst. 2020, 31, 4999–5004. [Google Scholar] [CrossRef] [PubMed]
- Zolfaghari, B.; Bibak, K.; Koshiba, T. The Odyssey of Entropy: Cryptography. Entropy 2022, 24, 266. [Google Scholar] [CrossRef]
- Abdellah, A.; Jarjar, M.; Kattass, M.; Rrghout, H.; Jarjar, A.; Benazzi, A. Genetic Algorithm Using Feistel and Genetic Operator Acting at the Bit Level for Images Encryption. Int. J. Saf. Secur. Eng. 2024, 14, 15–27. [Google Scholar] [CrossRef]
- Zahoor, M.; Fawad, A.; Jayasundar, D.; Balasubramanian, S.; Raparthi, M.; Nair, R. Biometric Encryption: Integrating Artificial Intelligence for Robust Authentication. J. Ballist. 2023, 35, 25–33. [Google Scholar] [CrossRef]
- Rajavel, D.; Periyasamy, S. Scrambling Algorithm for Encryption of Text Using Cube Rotation Artificial Intelligence Technique. In Proceedings of the 2016 International Conference, Istanbul, Turkey, 1–3 June 2016; pp. S251–S256. [Google Scholar]
- Liu, W.; Sun, K.; Zhu, C. A Fast Image Encryption Algorithm Based on Chaotic Map. Opt. Lasers Eng. 2016, 84, 26–36. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Pan, C.; Huang, X. An Effective Framework for Chaotic Image Encryption Based on 3D Logistic Map. Secur. Commun. Netw. 2018, 2018, 1–11. [Google Scholar] [CrossRef]
- Chen, J.-X.; Zhu, Z.-L.; Fu, C.; Yu, H. An Improved Permutation-Diffusion Type Image Cipher with a Chaotic Orbit Perturbing Mechanism. Opt. Express 2013, 21, 27873–27890. [Google Scholar] [CrossRef]
- Yao, S.; Zhao, Y.; Zhang, A.; Hu, S.; Shao, H.; Zhang, C.; Su, L.; Abdelzaher, T. Deep Learning for the Internet of Things. IEEE Comput. 2018, 51, 32–41. [Google Scholar] [CrossRef]
- Pecora, L.M.; Carroll, T.L. Synchronization in Chaotic Systems. Phys. Rev. Lett. 1990, 64, 821–823. [Google Scholar] [CrossRef] [PubMed]
- Lin, C.-Y.; Wu, S.-C.; Kuo, P.-H.; Huang, M.-J.; Hong, S.-W.; Yau, H.-T. Application of Chaotic Encryption and Decryption in Wireless Transmission from Sensory Toolholders on Machine Tools. IEEE Sens. J. 2023, 23, 11453–11468. [Google Scholar] [CrossRef]
- Gokyildirim, A.; Akgul, A.; Calgan, H.; Demirtas, M. Parametric Fractional-Order Analysis of Arneodo Chaotic System and Microcontroller-Based Secure Communication Implementation. AEU-Int. J. Electron. Commun. 2024, 175, 155080. [Google Scholar] [CrossRef]
- Aljaedi, A.; Alharbi, A.R.; Aljuhni, A.; Alghuson, M.K.; Alassmi, S.; Shafique, A. A Lightweight Encryption Algorithm for Resource-Constrained IoT Devices Using Quantum and Chaotic Techniques with Metaheuristic Optimization. Sci. Rep. 2025, 15, 14050. [Google Scholar] [CrossRef]
- Sprott, J.C. Some Chaotic Flows. Phys. Rev. E 1994, 50, R647–R650. [Google Scholar] [CrossRef] [PubMed]
- Gularte, K.H.M.; Alves, L.M.; Vargas, J.A.R.; Maranhão, J.P.A.; Carvalho, G.C.; Alfaro, S.C.A.; Romero, J.F.A. A Chaotic Synchronization Scheme for Information Security. In Proceedings of the 13th International Conference on Signal Processing and Communication Systems (ICSPCS), Gold Coast, Australia, 16–18 December 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Djibrilla, A.; Kountche, N.; Monmarché, N.; Slimane, M. The Pachycondyla Apicalis Ants Search Strategy for Data Clustering Problems. In Proceedings of the International Symposium SIDE 2012, Zakopane, Poland, 29 April–3 May 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 3–11. [Google Scholar] [CrossRef]
- Gheraibia, Y.; Moussaoui, A.; Yin, P.Y.; Papadopoulos, Y.; Maazouzi, S. PeSOA: Penguins Search Optimisation Algorithm for Global Optimisation Problems. Int. Arab J. Inf. Technol. 2019, 16, 371–379. [Google Scholar]
- Liao, T.-L.; Tsai, S.-H. Adaptive Chaotic Synchronization and Performance Analysis. Chaos Solitons Fractals 2000, 11, 1387–1396. [Google Scholar] [CrossRef]
- Kuo, H.-H.; Yen, H.-H.; Lin, J.-C. Synchronization of Discrete Sprott Chaotic Systems and Its Application in Secure Communication. In Proceedings of the 3rd IIAE International Conference on Intelligent Systems and Image Processing (ICISIP 2015), Fukuoka, Japan, 2–5 September 2015; The Institute of Industrial Applications Engineers: Fukuoka, Japan, 2015. [Google Scholar] [CrossRef]
- Zhang, Y.; Zeng, J.; Yan, W.; Ding, Q. RBFNN–PSO Intelligent Synchronisation Method for Sprott B Chaotic Systems with External Noise and Its Application in an Image Encryption System. Entropy 2024, 26, 855. [Google Scholar] [CrossRef]
- Yau, H.-T.; Hung, T.-H.; Hsieh, C.-C. Bluetooth-Based Chaos Synchronization Using Particle Swarm Optimization and Its Applications to Image Encryption. Sensors 2012, 12, 7468–7484. [Google Scholar] [CrossRef]
- Liu, J.; Zuo, T. Deep Adaptive Chaos Synchronization Based on Optimization Algorithm. IEEE Access 2025, 13, 38671–38684. [Google Scholar] [CrossRef]
- Maamri, F.; Bouras, M.; Djellab, H.; Bououden, S. Using Chua’s Chaotic Oscillator in Encryption Communication by ACO Identifications. In Proceedings of the 12th International Conference on Information Systems and Advanced Technologies (ICISAT 2022), Istanbul, Turkey, 22–23 July 2022; Lecture Notes in Networks and Systems. Laouar, M.R., Balas, V.E., Lejdel, B., Eom, S., Boudia, M.A., Eds.; Springer: Cham, Switzerland, 2023; Volume 624. [Google Scholar] [CrossRef]
- Samimi, M.; Majidi, M.H.; Khorashadizadeh, S. Secure Communication Based on Chaos Synchronization Using Brain Emotional Learning. AEU-Int. J. Electron. Commun. 2020, 127, 153424. [Google Scholar] [CrossRef]
- Zourmba, K.; Wamba, J.; Fortuna, L. Multi-Level Synchronization of Chaotic Systems for Highly-Secured Communication. Electronics 2025, 14, 2592. [Google Scholar] [CrossRef]
- Dinu, A. From Chaos to Security: A Comparative Study of Lorenz and Rössler Systems in Cryptography. Cryptography 2025, 9, 58. [Google Scholar] [CrossRef]
- Özkurt, C. Interpretable AI Analysis of Chaos Systems Distribution in Time Series Data from Industrial Robotics. Turk. J. Eng. 2024, 8, 656–665. [Google Scholar] [CrossRef]
- Chen, T.; Cecilia, A.; Astolfi, D.; Wang, L.; Liu, Z.; Su, H. Chaotic Masking Protocol for Secure Communication and Attack Detection in Remote Estimation of Cyber-Physical Systems. IFAC-PapersOnLine 2024, 58, 79–84. [Google Scholar] [CrossRef]
- Alharby, S.; Harris, N.; Weddell, A.; Reeve, J. The Security Trade-Offs in Resource-Constrained Nodes for IoT Applications. Int. J. Electr. Comput. Energ. Electron. Commun. Eng. 2018, 12, 52–59. [Google Scholar]
- Maamri, F.; Bououden, S.; Chadli, M.; Boulkaibet, I. The Pachycondyla Apicalis Metaheuristic Algorithm for Parameter Identification of Chaotic Electrical Systems. Int. J. Parallel Emerg. Distrib. Syst. 2018, 33, 490–502. [Google Scholar] [CrossRef]
- Maamri, F.; Bououden, S.; Boulkaibet, I. Identification of Chua’s Chaotic Circuit Parameters Using Penguins Search Optimisation Algorithm. Cyber-Phys. Syst. 2022, 8, 233–260. [Google Scholar] [CrossRef]
- Maamri, F.; Bououden, S.; Boulkaibet, I. An Ant Colony Optimization Approach for Parameter Identification of Piezoelectric Resonator Chaotic System. In Proceedings of the 16th IEEE International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Monastir, Tunisia, 21–23 December 2015; pp. 811–816. [Google Scholar] [CrossRef]
- Kanter, I.; Butkovski, M.; Peleg, Y.; Zigzag, M.; Aviad, Y.; Reidler, I.; Rosenbluh, M.; Kinzel, W. Synchronization of Random Bit Generators Based on Coupled Chaotic Lasers and Application to Cryptography. Opt. Express 2010, 18, 18292–18302. [Google Scholar] [CrossRef]
- Gokyildirim, A. Circuit Realization of the Fractional-Order Sprott K Chaotic System with Standard Components. Fractal Fract. 2023, 7, 470. [Google Scholar] [CrossRef]
- Vaidyanathan, S. Global Chaos Synchronization of Sprott-L and Sprott-M Systems by Active Control. Int. J. Control Theory Comput. Model. 2012, 2, 21–35. [Google Scholar] [CrossRef]
- Monmarché, N.; Venturini, G.; Slimane, M. On How Pachycondyla Apicalis Ants Suggest a New Search Algorithm. Future Gener. Comput. Syst. 2000, 16, 937–946. [Google Scholar] [CrossRef]
- Gheraibia, Y.; Moussaoui, A. Penguins Search Optimization Algorithm (PeSOA). In Proceedings of the 26th International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems (IEA/AIE 2013), Amsterdam, The Netherlands, 17–21 June 2013; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2013; Volume 7906, pp. 222–231. [Google Scholar] [CrossRef]
- Tiwari, A.; Singh, R.; Sharma, S.; Verma, P. A Compressed Image Encryption Algorithm Leveraging Optimized 3D Chaotic Maps for Secure Image Communication. Sci. Rep. 2025, 15, 95995. [Google Scholar] [CrossRef]
- Lin, Z.; Pattanayak, A.K. A Chaos Synchronization Diagnostic: Difference Time Series Peak Complexity (DTSPC). Entropy 2024, 26, 1085. [Google Scholar] [CrossRef] [PubMed]
- Iqbal, A.; Khurshaid, T.; Nauman, A.; Rhee, S.-B. Energy-Aware Ultra-Reliable Low-Latency Communication for Healthcare IoT in Beyond 5G and 6G Networks. Sensors 2025, 25, 3474. [Google Scholar] [CrossRef] [PubMed]
- Coll-Perales, B.; Lucas-Estañ, M.C.; Shimizu, T.; Gozalvez, J.; Higuchi, T.; Avedisov, S. End-to-End V2X Latency Modeling and Analysis in 5G Networks. IEEE Trans. Veh. Technol. 2023, 72, 5094–5109. [Google Scholar] [CrossRef]
- Salh, A.; Ngah, R.; Hussain, G.A.; Alhartomi, M.; Boubkar, S.; Shah, N.S.M.; Alsulami, R.; Alzahrani, S. Bandwidth Allocation of URLLC for Real-Time Packet Traffic in B5G: A Deep-RL Framework. ICT Express 2024, 10, 270–276. [Google Scholar] [CrossRef]
- Nana, B.; Woafo, P.; Domngang, S. Chaotic Synchronization with Experimental Application to Secure Communications. Commun. Nonlinear Sci. Numer. Simul. 2009, 14, 2266–2276. [Google Scholar] [CrossRef]
- Khattar, D.; Sirohi, M.; Bansal, R. Comparative Analysis of Two Novel Chaotic Systems, and Validation of Hybrid Function Projective and Complete Synchronization Using Active-Adaptive Control. Phys. Scr. 2024, 99, 125244. [Google Scholar] [CrossRef]
- Mobayen, S.; Kingni, S.T.; Pham, V.T.; Nazarimehr, F.; Jafari, S. Analysis, Synchronization and Circuit Design of a New Highly Nonlinear Chaotic System. Int. J. Syst. Sci. 2018, 49, 617–630. [Google Scholar] [CrossRef]
- Li, Y.; Chen, Y.; Xie, F.; Zhang, B.; Qiu, D.; Cheng, C. Nonlinear Model and Characteristic Analysis of High Frequency Oscillator. AEU-Int. J. Electron. Commun. 2023, 165, 154647. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.