Abstract
We study the problem of locally encoded secure distributed batch matrix multiplication (LESDBMM), where M pairs of sources each encode their respective batches of massive matrices and distribute the generated shares to a subset of N worker nodes. Each worker node computes a response from the received shares and sends the result to a sink node, which must be able to recover all M batches of pairwise matrix products in the presence of up to S stragglers. Additionally, any set of up to X colluding workers cannot learn any information about the matrices. Based on the idea of cross-subspace (CSA) codes and CSA null shaper, we propose the first LESDBMM scheme for batch processing. When the problem reduces to the coded distributed batch matrix multiplication (CDBMM) setting where and every source distributes its share to all worker nodes, the proposed scheme achieves performance matching that of the cross-subspace alignment (CSA) codes for CDBMM in terms of the maximum number of tolerable stragglers, communication cost, and computational complexity. Therefore, our scheme can be viewed as a generalization of CSA codes for CDBMM to the LESDBMM setting.
1. Introduction
The rapid advancement of big data processing and artificial intelligence technology has created substantial demand for low-latency computation of large-scale batch matrix multiplication, thereby motivating the emergence of the coded distributed batch matrix multiplication (CDBMM) problem. CDBMM aims to enable efficient and reliable distributed computation of a sequence of matrix products by leveraging coding techniques to mitigate the impact of stragglers. Specifically, the sources encode two batches of matrices and into shares, which are then distributed to N worker nodes. Each worker then computes a response from received shares and sends it to a sink node. Some worker nodes may fail to send their response in time due to unforeseen factors such as network latency, hardware failures, or resource contention; these nodes are referred to as stragglers. The sink node must be able to recover the desired matrix multiplication results from the received responses, provided that the number of stragglers remains within a tolerable limit. Early approaches adopt Maximum Distance Separable (MDS) codes [1] and simply replicate half of the matrices unchanged across all worker nodes without encoding, leading to high computational overhead at workers. To reduce worker complexity, polynomial codes [2] introduced algebraic encoding via polynomial evaluation, achieving the optimal recovery threshold under a specific matrix partitioning strategy, namely, partitioning matrix row-wise and matrix column-wise for each . Subsequent works such as MatDot and PolyDot codes [3] further optimized the trade-off between communication load and recovery threshold by exploiting matrix partitioning along both rows and columns. Generalized PolyDot [4] improve the recovery threshold of PolyDot codes by a factor of 2, while Entangled Polynomial (EP) codes [5] generalize polynomial codes to support arbitrary matrix partitioning and achieve the same recovery threshold as Generalized PolyDot. Building on EP codes, the scheme in [6] designed a flexible coding strategy that dynamically adapts to the number of stragglers and optimizes download cost by utilizing all non-straggling workers. Lagrange Coded Computing (LCC) [7] extends these ideas to general batched computations using polynomial interpolation over finite fields, supporting both straggler resilience and privacy. Generalized Cross-Subspace Alignment (GCSA) codes [8] provides a powerful unifying framework that simultaneously supports arbitrary matrix partitioning and batch processing, achieving the best known performance. Meanwhile, the growing demand for privacy protection has motivated the study of secure distributed batch matrix multiplication (SDBMM). To prevent adversaries from learning information about the two batches of matrices and from the shares distributed to a subset of worker nodes, SDBMM requires any X colluding worker to not learn any information about the input matrices. Early secure extensions adapt polynomial codes to the SDBMM setting [9,10]. GASP codes [11] optimize download cost by tailoring the degrees of encoding polynomials to the partition parameters and the security threshold X. The authors of [12] propose two SDBMM schemes: one based on structured secret sharing and another built upon CSA codes. Generalized PolyDot codes are extended to SDBMM in [13], offering a tunable trade-off between recovery threshold and communication cost, and this framework is further generalized in [14] to support arbitrary collusion patterns. Bivariate polynomial codes are adapted to SDBMM in [15], balancing upload cost against average worker computation time. More recently, algebraic geometry codes have been employed to construct SDBMM schemes [16]. For scenarios requiring source privacy, where even the sink must remain ignorant of the input matrices and , polynomial sharing [17] uses secret sharing among workers to protect the inputs. However, it requires each worker node to securely exchange intermediate products with all others, resulting in significant inter-worker communication overhead. GCSA-NA codes [18] address this issue by allowing workers to pre-share randomness that is independent of the input matrices, thereby reducing inter-worker communication by orders of magnitude. Finally, the scheme in [19] improves upon X-secure GCSA [8] by achieving a lower recovery threshold for certain values of the security parameter X.
While the aforementioned CDBMM and SDBMM frameworks have achieved remarkable progress in straggler mitigation and security guarantees, they commonly rely on a crucial yet often unrealistic assumption: that every source node can distribute encoded shares to all worker nodes. This full-connectivity assumption greatly simplifies code design but fails to reflect practical distributed computing environments, such as edge computing clusters, federated learning systems, or data centers with hierarchical network topologies, where communication links may be restricted due to bandwidth limitations, access control policies, or physical proximity constraints. It is precisely this gap between the idealized model of CDBMM and real-world deployment scenarios that motivates our work. When source–worker connectivity becomes partial, the conventional global encoding strategies (e.g., EP codes, LCC codes) are no longer directly applicable, as each source can only influence a subset of workers. This necessitates a new coding paradigm that respects the locality of encoding while preserving straggler tolerance and security, naturally leading to the formulation of the locally encoded secure distributed batch matrix multiplication (LESDBMM) problem. The LESDBMM problem involves M pairs of source nodes , , ⋯, , N worker nodes, and one sink node. The sink node can communicate with all worker nodes, while each pair of source nodes is connected only to a subset of worker nodes. The communication connectivity between all source nodes and worker nodes is globally known. Each pair of source nodes and encodes their batches of matrices and and distributes the generated shares exclusively to its connected worker nodes; such an encoding pattern is referred to as “local encoding pattern”. The worker nodes must remain oblivious to the values of the matrices . Any set of up to X colluding workers must learn no information about these matrices. Each worker node computes a response from the received shares and sends it to the sink node. The sink node must be able to recover the desired matrix multiplication as long as the number of stragglers does not exceed S. This work aims to construct an efficient and straggler-tolerant LESDBMM scheme. The key challenge lies in leveraging the local encoding pattern to design an encoding scheme, such that the interference across different encoding subsets can be aligned into as few dimensions as possible, thereby minimizing the communication cost required for interference elimination during decoding. Furthermore, the decoding scheme must mitigate the impact of randomly occurring stragglers on the locally encoded structure.
A closely related problem is the problem of X-secure T-private linear computation based on graph-based replicated/MDS-coded storage (GXSTPLC) [20]. In the GXSTPLC problem, K messages are partitioned into M message sets, and the messages of each message set are restricted to be distributed among a subset of N servers in a securely coded form. Any set of X colluding servers must not disclose any information about the stored messages. A user wishes to privately compute a linear combination of all messages. To this end, the user sends queries to the servers and recovers the desired linear combination from the answer returned by servers. In this process, all servers must remain available, and any T colluding server must learn nothing about the coefficients of the linear combination. Ref. [20] proposes the first asymptotic capacity achieving the GXSTPLC scheme for replicated storage based on the idea of cross-subspace alignment (CSA) and a structure inspired by dual generalized Reed–Solomon (GRS) codes, demonstrating the optimality of CSA codes and dual GRS codes for interference alignment across message sets in this setting. Ref. [21] proposes a GXSTPLC scheme for MDS-coded storage based on CSA codes and exploits the idea of CSA null shaper, rather than using dual GRS codes, to enable interference alignment across message sets. When applied to the case of replicated storage, its rate matches the asymptotic capacity established in [20]. In fact, there is a connection between the LESDBMM problem and the GXSTPLC problem. If we let be a row vector and be a column vector, the desired matrix multiplication then degenerates into M batches of pairwise vector inner products. By thinking of as the symbols of each message in the message set and as corresponding coefficients, any GXSTPLC scheme automatically yields an LESDBMM scheme. This work focuses on extending the batch vector inner product scheme yielded by the MDS-GXSTPLC scheme [21] to an LESDBMM scheme applicable to matrix multiplication of arbitrary dimensions and enabling it to tolerate stragglers.
The main contribution of this work is the first LESDBMM scheme based on batch processing. Our scheme utilizes CSA codes and CSA null shaper to achieve interference alignment across encoding subsets. We evaluate the scheme in terms of the straggler threshold (i.e., maximum number of tolerable stragglers), upload cost, download cost, encoding complexity, worker node computation complexity, and decoding complexity. By comparing with the baseline scheme, we demonstrate that the optimization of download cost achieved by our scheme is non-trivial. Moreover, by adjusting the parameter , we can achieve a trade-off between performance metrics of the encoding and decoding phases. When the problem degenerates to the CDBMM setting, where and all source nodes can distribute their shares to all workers, the performance of our scheme matches that of the CSA codes for CDBMM [8]. Hence, our scheme can be viewed as a generalization of the CSA codes for CDBMM to the LESDBMM setting.
The remainder of this paper is organized as follows. Section 2 formally defines the problem of locally encoded secure distributed batch matrix multiplication. Section 3 presents the main result. Section 4 presents the proof of our main result along with an illustrative example. Section 5 concludes the paper and discusses future research directions.
Notation: Bold symbols are used to denote vectors and matrices, while calligraphic symbols denote sets. Following the convention, let the empty product be the multiplicative identity and the empty sum be the additive identity. For any two positive integers , denotes the set . We use the shorthand notation for . For an index set , denotes the set . For a subset of integers , denotes its element in ascending order. For an matrix and two integers , denotes the element at the row and the column of . denotes the zero matrix of size . The notation suppresses polylog terms; i.e., can be replaced with if the field supports the Fast Fourier Transform (FFT) and with if it does not.
2. Problem Statement
Consider the LESDBMM problem as shown in Figure 1 with M pairs of source nodes , , ⋯, and N worker nodes . Each source node , generates a batch of matrices , where for all , . Each source node , generates a batch of matrices , where for all , . A sink node with limited computing power demands . For this purpose, the sink node requires each source node to encode and send its matrices to N worker nodes and have them assist in computing matrix multiplications. Due to constrained communication links between the source nodes and the worker nodes, each pair of source nodes can only send their encoded matrices to a subset of N worker nodes denoted as , , i.e., . The collection of sets is referred to as “local encoding pattern”. We can equivalently define the dual representation of the local encoding pattern. For all , let us define the index set of encoded batches of matrices that are available at worker node n as .
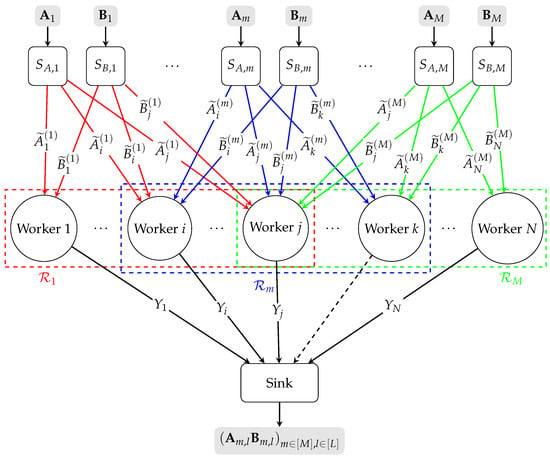
Figure 1.
Conceptual diagram of the LESDBMM problem with M pairs of source nodes, N worker nodes, and local encoding pattern . The worker node k is a straggler. The ellipsis between two nodes indicates that the intermediate nodes between them have been omitted. Lines in different colors represent distinct local connectivity patterns between different sources and the workers. Dashed lines connecting a worker to the sink indicate that the worker is straggling and cannot return any information to the sink.
Each source node encodes the matrices according to functions and generates the shares , where for all , is sent to worker node n. Each source node encodes the matrices according to functions and generates the shares , where for all , is sent to worker node n. The shares of M batches of matrices are generated independently, i.e.,
Any group of up to X colluding worker nodes cannot learn any information about the matrices ; i.e., for all ,
Upon receiving shares , each worker node computes a response according to function , i.e.,
and sends to the sink node.
The sink node must be able to decode the desired products in the presence of up to S stragglers. Let denote the index set of the fastest worker nodes that send responses to the sink node. For any subset , according to decoding function , we have
Let us denote . We say that form an LESDBMM scheme against S stragglers. To evaluate the performance of an LESDBMM scheme defined above, we consider the straggler threshold, the communication cost, and computation complexity. The straggler threshold S is defined as the maximum number of tolerable stragglers. The communication cost includes upload cost and download cost D, defined as follows:
where counts the number of symbols from needed to represent C. The computation complexity includes encoding complexity , worker node computation complexity , and decoding complexity . and are defined as the order of the number of finite field arithmetic operations required to compute and , normalized by . is defined as the order of the number of finite field arithmetic operations required to compute , normalized by . is defined as the order of the number of finite field arithmetic operations required to compute , normalized by .
3. Main Result
Consider a hypergraph with vertex set and hyperedge set , where each vertex represents a worker node and each hyperedge indicates that the vertices it contains share a common piece of information. Suppose that consists of K connected components, denoted by for . For all , let denote the index set of the hyperedges contained in , i.e., .
The main result of this work is stated in the following theorem.
Theorem 1.
For LESDBMM over the finite field with N worker nodes, local encoding pattern , positive integers such that and , the following straggler threshold, communication cost, and computation complexity can be achieved:
where for all , .
Remark 1.
If hypergraph is connected, we have the straggler threshold and the decoding complexity . It can be seen that the straggler threshold is determined by the minimum number of worker nodes that any source node can communicate with. When the problem degenerates to the CDBMM setting; i.e., when and , the straggler threshold, upload cost, download cost, encoding complexity, computation complexity of all worker nodes, and decoding complexity achieved by Theorem 1 match those of CSA codes for CDBMM [8].
Remark 2.
We say that two pairs of source nodes and are related if the sets of worker nodes connected to them belong to the same connected component; i.e., there exists , such that . When the connectivity between a given pair of source nodes and the worker nodes is too sparse (i.e., is too small) and the number of pairs of source nodes related to is excessively large, condition cannot be satisfied even when we set , rendering Theorem 1 inapplicable. A trivial approach to resolving this problem is to exclude the source node pairs possessing this property from the original local encoding pattern and handle the computational tasks of each of these pairs of source nodes separately. However, this scheme evidently incurs significant communication and computational overhead.
Remark 3.
The parameter directly governs key performance trade-offs: increasing reduces upload cost, encoding complexity at the source nodes, and worker node computation complexity, but it decreases the straggler threshold and increases download cost and decoding complexity at the sink node.
Remark 4.

Compared to the baseline scheme shown in Table 1, our scheme achieves a lower download cost under the same , at the expense of a potentially reduced straggler threshold. However, because the baseline scheme lacks interference alignment across encoding subsets, its download cost remains higher than that of our scheme, even when its parameter is increased to reduce the straggler threshold to match ours. For instance, in the motivating example described in Section 4.1 with a straggler threshold of 1 and worker node 2 failing, our scheme achieves a download cost of , whereas the baseline requires .

Table 1.
Performance comparison of a baseline scheme and our scheme. The baseline scheme independently encodes and , computes, and decodes for each pair of source nodes using CSA codes [8] in a straightforward manner. , ranges over all subsets of such that for all .
4. The Proof of Theorem 1
4.1. Motivating Example
To make the general proof more accessible, let us consider a motivating example as shown in Figure 2 where we have pairs of source nodes , , and , worker nodes, batch size , and security level . The local encoding pattern for this example is . Accordingly, we have , for all , , and for all . For all , source node generates a batch of matrices as follows:
Source node generates a batch of matrices as follows:
The hypergraph has two connected components and , thus . Let us set , then we have ; i.e., the scheme can tolerate one straggler.
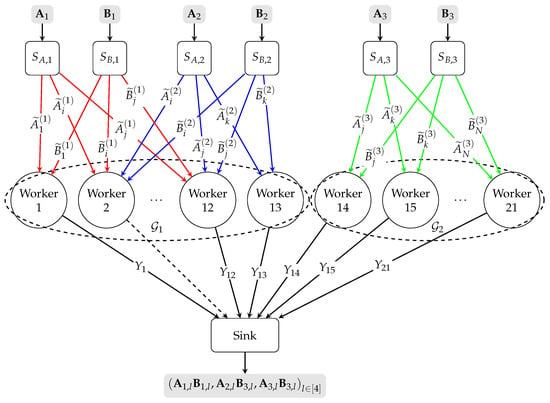
Figure 2.
Conceptual diagram of the LESDBMM problem with pairs of source nodes, worker nodes, and local encoding pattern . The hypergraph has two connected components and . The worker node 2 is a straggler. The ellipsis between two nodes indicates that the intermediate nodes between them have been omitted. Lines in different colors represent distinct local connectivity patterns between different sources and the workers. Dashed lines connecting a worker to the sink indicate that the worker is straggling and cannot return any information to the sink.
Let be 33 distinct elements from , thus we need . For all , let us define
4.1.1. Encoding
For all , let us define the following constants:
Let be six uniformly i.i.d. random matrices over ; let be six uniformly i.i.d. random matrices over .
For all , the share uploaded to worker node n by source node is constructed as follows:
where
The share uploaded to worker node n by source node is constructed as follows:
where
Note that any single worker node cannot reveal any information about the matrices and due to the random noise matrices .
The upload cost is
The encoding complexity is
Note that under the settings of this example, the straggler threshold for the baseline scheme is 1. The uploaded shares to worker node n by source nodes and in the baseline scheme are the same as those in (19) and (24), respectively, making the upload cost of the baseline scheme identical to that given in (27) and (24). Additionally, the encoding complexity of the baseline scheme matches that provided in (29) and (30).
4.1.2. Computing
For all , let us define . For all , let us define .
The response is constructed as
For all , the response is constructed as
The response is constructed as
Therefore, for all , the response can be formally written as
For all , the response is constructed as
Specifically, for all , we obtain
where for all , are obtained by combining the like terms. For all , we obtain
where , , for all , are obtained by combining the like terms.
Therefore, for all , can be written as
where for all , . For all , can be written as
The worker node computation complexity is
Furthermore, under the settings of this example, the response generated by worker node n, in the baseline scheme is , meaning the computational complexity at worker node n is the same as that shown in (47).
4.1.3. Decoding
Let us assume that the worker node 2 is a straggler. The sink node downloads the responses . In the following, we demonstrate that the desired matrix products can be recovered from .
For all , we can rewrite in the following matrix form:
Because the terms are distinct, the square Cauchy–Vandermonde matrices on the RHS of (48) and (49) have full rank, and the desired terms can be recovered by solving linear systems in (48) and (49) and removing the coefficients .
The download cost is
The decoding complexity is at most . Lastly, under the settings of this example, the destination node in the baseline scheme downloads the responses , resulting in a download cost of . According to (41), the decoding complexity for recovering from , from , and from is .
4.2. The General Scheme
We require . Let be distinct elements from . For all , let us define
where L matrices from either or are partitioned into ℓ sub-batches, each containing matrices.
4.2.1. Construction of Encoding Functions
In this subsection, we present the construction of encoding functions and . For all , let us define the following constants:
Let be a total of uniformly i.i.d. random matrices over ; let be a total of uniformly i.i.d. random matrices over .
For all , the share uploaded to worker node n by source node is constructed as follows:
where for all ,
and the share uploaded to worker node n by source node is constructed as follows:
where for all ,
and for all , the matrices and are, respectively, encoded via an MDS code to produce shares. Their shares are X-secure due to the MDS()-coded random noise matrices and .
The upload cost is
The encoding procedure can be considered as products of Cauchy–Vandermonde matrices and vectors. By fast algorithms [22], the encoding complexity is
4.2.2. Construction of Worker Nodes Computing Functions
In this subsection, we present the construction of computing functions . For all , let us define
For all , the response sent to the sink node by worker node n is constructed as follows:
Note that for all , , thus . For each , we obtain
where (65) holds according to (55) and (57), and the fact that for all and , we obtain ; thus, . (66) is obtained by combining like terms; for all , the undesired terms are various linear combinations of products of matrices , whose exact forms are irrelevant. In (67), for all , . In (68), we combine like terms again. For all , let us set . In (69), for all , . For all , is the remainder of the polynomial division (with respect to ); , where is the remainder of the polynomial division (with respect to ).
The worker node computation complexity is
Remark 5.
By the definition of connected components in hypergraphs, every hyperedge , satisfies , and for any vertex , all hyperedges containing v belong exclusively to . This structural property has a direct implication for the LESDBMM problem: for each , the matrices and , are shared only among the worker nodes in , and conversely, each worker node in receives shares exclusively from matrices . Consequently, the recovery of the matrix products can be accomplished solely using the responses from the worker nodes in , together with computing functions and the corresponding decoding strategy. Importantly, this recovery process is independent of the workers outside as well as the decoding strategies employed in other connected components.
Remark 6.
For any , although only the worker nodes in hold shares of the matrices and , the use of the CSA null shaper () ensures that every worker node n in possesses the terms , as illustrated in (65). Moreover, the CSA null shaper preserves the structure of CSA encoding: the desired symbols are aligned with the Cauchy terms, while the undesired interference terms are aligned with the Vandermonde terms, as shown in (68). Consequently, the problem of decoding the matrix products reduces to the problem of CSA decoding without encoding locality in the presence of stragglers [8].
4.2.3. Construction of Decoding Functions
In this subsection, we present the construction of decoding functions . For all , let us define , representing the non-stragglers among worker nodes ; note that . The sink node downloads the responses . For all , let us define
For all , we can rewrite the downloaded symbols in the following matrix form:
Because the terms are distinct, the square Cauchy–Vandermonde matrix on the RHS of (73) has full rank, and the desired terms can be recovered by solving linear systems in (73) and removing the coefficients . This completes the proof of the correctness of the decoding functions. The download cost is
By fast algorithms [23], the complexity of solving a linear system defined by a Cauchy- Vandermonde matrix is ; thus, the decoding complexity is at most
5. Concluding Remarks
This work proposes the first LESDBMM scheme based on the idea of CSA codes and CSA null shaper, which can be viewed as a generalization of CSA codes for CDBMM [8] to the LESDBMM setting. The proposed scheme can be further extended in two promising directions. First, following the approach of [8], which combines CSA codes for CDBMM with EP codes to obtain GCSA codes, one can generalize our construction to support matrix partitioning while preserving batch processing capabilities. Second, by allowing the worker nodes to share common randomness that is independent of the input matrices (as in [18]), the scheme can be enhanced to guarantee information-theoretic privacy: the sink node learns nothing about the input matrices beyond the desired matrix products. In addition, the current design focuses on the worst-case scenario, assuming that the number of stragglers reaches the maximum tolerable threshold. However, in practice, the number of stragglers is unpredictable; it is worthwhile to explore how to fully leverage all available worker nodes to further improve both computation and communication efficiency.
Author Contributions
Conceptualization, H.J. and Z.J.; methodology, H.J. and Z.J.; formal analysis, H.J.; investigation, H.J.; writing—original draft preparation, H.J.; writing—review and editing, H.J. and Z.J.; supervision, Z.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded in part by the National Natural Science Foundation of China under grant number 62201080.
Data Availability Statement
The data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| LESDBMM | Locally Encoded Secure Distributed Batch Matrix Multiplication |
| CSA | Cross-Subspace Alignment |
| GCSA-NA | Generalized Cross-Subspace Alignment with Noise Alignemnt |
| CDBMM | Coded Distributed Batch Matrix Multiplication |
| MDS | Maximum Distrance Separable |
| EP | Entangled Polynomial |
| LCC | Lagrange Coded Computing |
| GCSA | Generalized Cross-Subspace Alignment |
| SDBMM | Secure Distributed Batch Matrix Multiplication |
| GXSTPLC | X-Secure T-Private Linear Computation Based on Graph-Based Replicated Storage |
| GRS | Generalized Reed–Solomon |
References
- Lee, K.; Lam, M.; Pedarsani, R.; Papailiopoulos, D.; Ramchandran, K. Speeding Up Distributed Machine Learning Using Codes. IEEE Trans. Inf. Theory 2018, 64, 1514–1529. [Google Scholar] [CrossRef]
- Yu, Q.; Maddah-Ali, M.; Avestimehr, S. Polynomial codes: An optimal design for high-dimensional coded matrix multiplication. Adv. Neural Inf. Process. Syst. 2017, 30. [Google Scholar]
- Dutta, S.; Fahim, M.; Haddadpour, F.; Jeong, H.; Cadambe, V.; Grover, P. On the Optimal Recovery Threshold of Coded Matrix Multiplication. IEEE Trans. Inf. Theory 2020, 66, 278–301. [Google Scholar] [CrossRef]
- Dutta, S.; Bai, Z.; Jeong, H.; Low, T.M.; Grover, P. A Unified Coded Deep Neural Network Training Strategy based on Generalized PolyDot codes. In Proceedings of the 2018 IEEE International Symposium on Information Theory (ISIT), Vail, CO, USA, 17–22 June 2018; pp. 1585–1589. [Google Scholar] [CrossRef]
- Yu, Q.; Maddah-Ali, M.A.; Avestimehr, A.S. Straggler Mitigation in Distributed Matrix Multiplication: Fundamental Limits and Optimal Coding. IEEE Trans. Inf. Theory 2020, 66, 1920–1933. [Google Scholar] [CrossRef]
- Li, W.; Chen, Z.; Wang, Z.; Jafar, S.A.; Jafarkhani, H. Flexible Distributed Matrix Multiplication. IEEE Trans. Inf. Theory 2022, 68, 7500–7514. [Google Scholar] [CrossRef]
- Yu, Q.; Li, S.; Raviv, N.; Kalan, S.M.M.; Soltanolkotabi, M.; Avestimehr, S.A. Lagrange coded computing: Optimal design for resiliency, security, and privacy. In Proceedings of the 22nd International Conference on Artificial Intelligence and Statistics, Naha, Japan, 16–18 April 2019; pp. 1215–1225. [Google Scholar]
- Jia, Z.; Jafar, S.A. Cross Subspace Alignment Codes for Coded Distributed Batch Computation. IEEE Trans. Inf. Theory 2021, 67, 2821–2846. [Google Scholar] [CrossRef]
- Chang, W.T.; Tandon, R. On the Capacity of Secure Distributed Matrix Multiplication. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, H.; Lee, J. Secure Distributed Computing With Straggling Servers Using Polynomial Codes. IEEE Trans. Inf. Forensics Secur. 2019, 14, 141–150. [Google Scholar] [CrossRef]
- D’Oliveira, R.G.L.; El Rouayheb, S.; Karpuk, D. GASP Codes for Secure Distributed Matrix Multiplication. IEEE Trans. Inf. Theory 2020, 66, 4038–4050. [Google Scholar] [CrossRef]
- Kakar, J.; Ebadifar, S.; Sezgin, A. On the Capacity and Straggler-Robustness of Distributed Secure Matrix Multiplication. IEEE Access 2019, 7, 45783–45799. [Google Scholar] [CrossRef]
- Aliasgari, M.; Simeone, O.; Kliewer, J. Private and Secure Distributed Matrix Multiplication With Flexible Communication Load. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2722–2734. [Google Scholar] [CrossRef]
- Yao, Y.; Liu, N.; Kang, W.; Li, C. Secure Distributed Matrix Multiplication Under Arbitrary Collusion Pattern. IEEE Trans. Inf. Forensics Secur. 2023, 18, 85–100. [Google Scholar] [CrossRef]
- Hasırcıoǧlu, B.; Gómez-Vilardebó, J.; Gündüz, D. Bivariate Polynomial Codes for Secure Distributed Matrix Multiplication. IEEE J. Sel. Areas Commun. 2022, 40, 955–967. [Google Scholar] [CrossRef]
- Makkonen, O.; Saçıkara, E.; Hollanti, C. Algebraic Geometry Codes for Secure Distributed Matrix Multiplication. IEEE Trans. Inf. Theory 2025, 71, 2373–2382. [Google Scholar] [CrossRef]
- Akbari-Nodehi, H.; Maddah-Ali, M.A. Secure Coded Multi-Party Computation for Massive Matrix Operations. IEEE Trans. Inf. Theory 2021, 67, 2379–2398. [Google Scholar] [CrossRef]
- Chen, Z.; Jia, Z.; Wang, Z.; Jafar, S.A. GCSA Codes With Noise Alignment for Secure Coded Multi-Party Batch Matrix Multiplication. IEEE J. Sel. Areas Inf. Theory 2021, 2, 306–316. [Google Scholar] [CrossRef]
- Zhu, J.; Yan, Q.; Tang, X. Improved Constructions for Secure Multi-Party Batch Matrix Multiplication. IEEE Trans. Commun. 2021, 69, 7673–7690. [Google Scholar] [CrossRef]
- Jia, H.; Jia, Z. The Asymptotic Capacity of X-Secure T-Private Linear Computation With Graph Based Replicated Storage. IEEE Trans. Inf. Theory 2024, 70, 5269–5288. [Google Scholar] [CrossRef]
- Liu, Y.; Jia, H.; Jia, Z. On the Storage–Communication Trade-Off in Graph-Based X-Secure T-Private Linear Computation. Entropy 2025, 27, 975. [Google Scholar] [CrossRef] [PubMed]
- Pan, V.Y. Structured Matrices and Polynomials: Unified Superfast Algorithms; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Finck, T.; Heinig, G.; Rost, K. An inversion formula and fast algorithms for Cauchy-Vandermonde matrices. Linear Algebra Appl. 1993, 183, 179–191. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).