Abstract
Twin-field quantum key distribution (TF-QKD) can break the repeaterless linear bound and possess the measurement-device-independent security, and thus seems very promising in practical applications of quantum secure communication. In most reported TF-QKD protocols, light sources are assumed to possess trusted and fixed photon number distributions (PND), which are unrealistic assumptions in practical applications. Fortunately, the light source monitoring (LSM) method is proposed to circumvent this problem by actively adjusting the attenuation coefficient and monitoring the photon number distribution of light sources. However, the active light source monitoring (ALSM) method may induce additional modulation errors due to imperfect attenuation devices, deteriorating practical performances of TF-QKD systems. In this manuscript, we propose a passive light source monitoring (PLSM) scheme for TF-QKD, and employ the sending-or-not-sending (SNS) TF-QKD as an example for illustration. Simulation results show that our present work can greatly exceed both the original SNS protocol and the ALSM scheme when light source fluctuations and modulation errors are taken into account.
1. Introduction
Quantum key distribution (QKD) allows two legitimate parties, Alice and Bob, to share secure keys based on the laws of quantum physics. The security of BB84 protocol was proven in theory by many scientists [1,2,3,4,5,6,7]. However, there are still some loopholes in the measurement devices. To remove those attacks directed on the measurement devices, the measurement-device-independent quantum key distribution (MDI-QKD) [8] was put forward. Thereafter, a lot of related experiments and theories have been done on MDI-QKD, making it more efficient and practical [9,10,11,12,13]—just its key rate is still limited by the fundamental limit of channel capacities without quantum repeaters, e.g., the Pirandola–Laurenza–Ottaviani–Banchi (PLOB) bound [14,15].
Recently, Lucamarini et al. proposed the twin-field quantum key distribution (TF-QKD) protocol [16], which can break the PLOB bound [14,15] and make the rate distance dependence change from a linear to square root. Up to date, many variants of TFQKD protocols have been proposed and experimentally demonstrated [17,18,19,20,21,22,23,24,25,26,27,28]. However, some assumptions are made for the sources in most reported works, i.e., with a trusted and fixed photon-number distribution (PND), which usually can not be satisfied in practical implementations. Those unreasonable assumptions will inevitably compromise the security of practical QKD systems. To solve the problem, the light source monitoring (LSM) method was put forward and experimentally realized by actively modulating local attenuator into different losses [29,30], hereafter called the active light source monitoring (ALSM) scheme. However, unfortunately, the ALSM scheme will bring new loopholes and then deteriorate practical performances of TF-QKD systems during intensity modulation processes due to imperfections of attenuated devices.
In this paper, we propose a passive light source monitoring (PLSM) scheme for TF-QKD, which is accomplished by a passive monitoring module consisting of a beam splitter and two detectors at the source side. Through the PLSM module, we can obtain four monitoring events by two local detectors and then precisely estimate the bounds of source distributions. Specifically, we employ the sending-or-not-sending (SNS) TFQKD [18,31,32,33] as an example for illustration. Compared with the ALSM method, our PLSM method can passively monitor the PND and dramatically exceed the performance of ALSM when modulation errors are considered.
2. PLSM Scheme in SNS−TFQKD
In this section, we describe the SNS−TFQKD scheme [18,31,32,33] with PLSM. The schematic of the setup is shown in Figure 1, where it involves two senders, Alice and Bob, and one untrustworthy third party (UTP), Charlie. The detailed process of the SNS−TFQKD with a four-intensity decoy-state PLSM scheme can be described as follows:
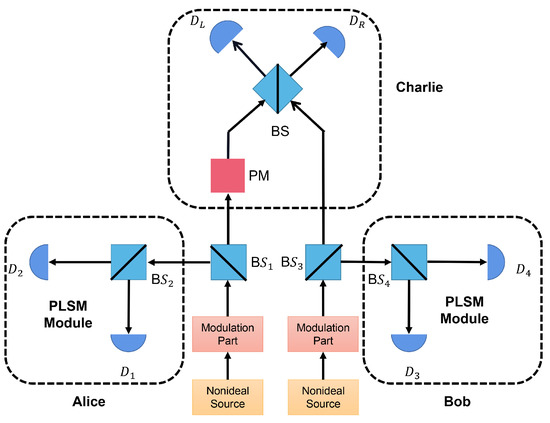
Figure 1.
Schematic of the SNS−TFQKD system with PLSM. The PLSM module consists of a beam splitter (BS) and two local single-photon detectors.
Step 1. Alice and Bob do some preparatory work before sending the pulse: they send a reference coherent light to Charlie, and Charlie performs phase compensation.
Step 2. The N pulses generated by Alice and Bob are encoded by a modulation module, which contains a phase modulator (PM) and an intensity modulator (IM). During this process, each pulse is randomly chosen as the X (decoy) or Z (signal) window. At any time window i, Alice (Bob) independently determines whether it is a decoy window or a signal window. If the decoy window is chosen, she (he) prepares state and sends it to Charlie, . If the signal window is selected, Alice (Bob) sends states to Charlie with a probability of , and with a probability of for not sending, where the are global phases of the coherent states.
Step 3. The pulses are split into two modes, where the idler mode is for performing PLSM and the signal mode is for encoding information and sending it to Charlie. The idler mode is further split by a local beam splitter and then sent into two local detectors. As a result, four detection events can be obtained. For example, in Alice’s PLSM module, these events can be denoted as l: x, neither or clicks; y, only clicks; z, only clicks; w, and both and click.
Step 4. Charlie measures all received states with a beam splitter and two detectors ( and ), and then announces the effective measurement outcome, i.e., which detector clicks.
Step 5. Alice and Bob announce the local detection events l and the kind of window (X window or Z window) for each pulse. In addition, the intensity and encoding phases (, ) in the X basis should also be disclosed.
Step 6. Alice and Bob use the data in the X basis to estimate channel parameters, and they randomly select some bits in the Z basis for the error test and use the remaining bits to extract the final secure keys.
In this protocol, Z basis is defined as the time window when both Alice and Bob choose the signal window; X basis is denoted as the time window when both Alice and Bob choose the same decoy window (with intensity ), and, simultaneously, the random phases , prepared in the window satisfy
Here, is determined by the size of the phase slice chosen by Alice and Bob. In addition, the effective measurement outcome denotes that only one detector ( or ) clicks.
In the PLSM module, when the event l occurs, the idler state is projected into , where denotes the photon number distribution of the weak coherent state (WCS) with mean photon number , , and is the probability of an n-photon state projecting into event l given by [34,35]
where and are the dark counting rate and detection efficiency of the local detectors at the sender’s side (Alice and Bob), respectively, and t is the transmittance of and . Here, for simplicity, we assume that two local detectors in PLSM module have the same detection efficiency and dark count rate, which means , . Define as the photon number distribution under different counting events.
Then, we estimate the upper and lower bounds of probabilities of different photon-number states, i.e., the vacuum state, the one-photon state and the two-photon state. By measuring the idler mode, the gain of four events can be obtained as
According to the derivation presented in Appendix A, the estimations of , are given by
where represents the lower or upper bounds on the probability of having the n-photon state given the mean photon number .
In the SNS−TFQKD, Alice and Bob simultaneously send photon pulses to the untrustworthy third party (UTP) Charlie. According to Ref. [36], the decoy-state method is still applicable under unknown PND conditions; the lower bound of the single-photon counting rate and the upper bound of the single-photon error rate can be estimated as
Here, we set , , and , are the counting rate and the bit error rate of a state with intensity sent in decoy windows, respectively. In addition, the relationships between and are set by [30]
Finally, the secure key rate is
where represents the probability that Alice (Bob) chooses to send out a signal pulse (it can be preset in the protocol); is the binary Shannon entropy function; is the lower bound of the probability of single photons in the signal state; and refer to the gain and the average quantum bit error of pulses with intensity u sent in signal windows.
3. Numerical Simulations and Analysis
In the following, we perform numerical simulations for the original SNS−TFQKD [18], the SNS−TFQKD with ALSM [30] and the SNS−TFQKD with PLSM. In simulations, the gain and the quantum bit error of decoy states in X basis in Equations (9) and (10) are expressed as
where is the counting rate of twin-field states entering into the correct (wrong) detector; denotes the total channel transmittance, where and s are the loss coefficient and the length of channels, respectively; and each refer to the efficiency and the dark count rate of detectors at Charlie’s side, respectively. is the phase difference between the twin-field states prepared by Alice and Bob; is the size of the phase slice and M is the number of phase slices; represents the optical misalignment error, is the counting rate of the vacuum state, and . The average quantum bit error and the counting rate for the signal states can be respectively expressed as:
Here, is the 0-order hyperbolic Bessel function of the first kind [31].
In the following, we do comparisons among three schemes, the original SNS−TFQKD, the ALSM SNS−TFQKD, and the present PLSM SNS−TFQKD, by using either ideal light sources without intensity fluctuations or practical light sources with intensity fluctuations. In addition, we also analyze the effect of modulation error on the ALSM scheme. The basic device parameters are shown in Table 1 [30].

Table 1.
The basic system parameters used in our numerical simulations. : the loss coefficient of fiber at telecommunication wavelength (dB/km); and are the efficiency and dark count rate of detectors at Charlie’s side; : the misalignment error of the QKD system; f: the error correction efficiency; M: the number of phase slices.
In ALSM, the attenuation coefficients are set as , , . For a fair comparison, in our scheme, the detection efficiency in PLSM module is set as . In addition, the dark count rate of local detectors in ALSM and PLSM is set with the same value denoted as as listed in row a of Table 1. In addition, we adopt the local search algorithm (LSA) [9] to optimize the parameters . The numerical simulation results are presented in Figure 2, Figure 3 and Figure 4.
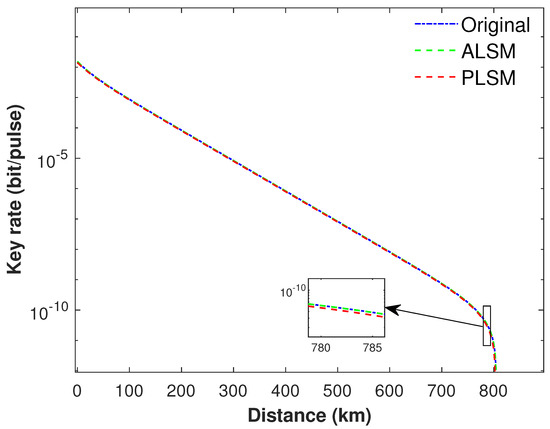
Figure 2.
The secure key rate of different monitoring method using a set of parameters in row a of Table 1. The blue solid curve represents the original SNS−TFQKD; the red dash curve denotes our present PLSM SNS−TFQKD; and the green dash curve is the ALSM SNS−TFQKD. In addition, the variation trend of the key rate ranging between 780 km and 785 km is illustrated in the inset. It shows that our proposal can offer a key rate comparable to both the original SNS−TFQKD and the ALSM SNS−TFQKD when using photon sources without fluctuations.
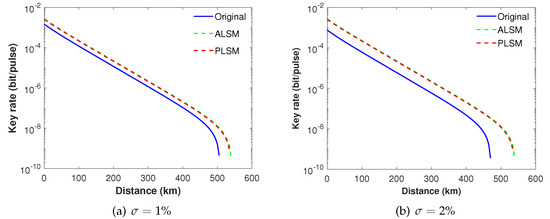
Figure 3.
The secure key rate of different schemes with intensity fluctuation in (a) and in (b) when intensity modulation errors are not taken into account.
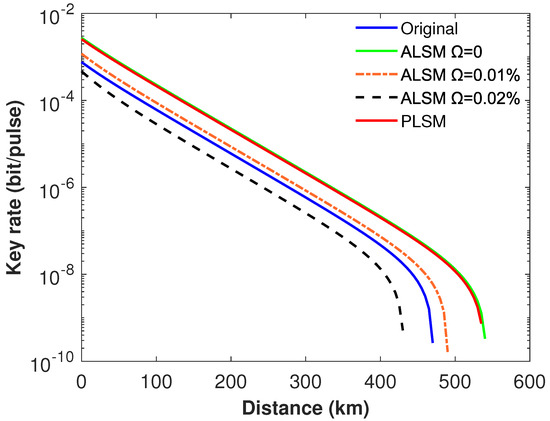
Figure 4.
The secure key rate of different monitoring methods when different modulation errors are taken into account. Here, parameters in line b of Table 1 and the intensity fluctuation are used. The blue solid curve represents the original SNS−TFQKD; the green solid curve is the ALSM SNS−TFQKD when ; the red solid curve denotes the PLSM SNS−TFQKD; the orange dotted-dash curve and the black dash curve denote the ALSM SNS−TFQKD with modulation errors and , respectively.
The performance of different monitoring methods with ideal sources without intensity fluctuations are presented in Figure 2. Simulation results show that the performance of our proposed PLSM SNS−TFQKD is comparable to both the original SNS−TFQKD and the ALSM SNS−TFQKD. It is also clear that the maximum transmission distance of all schemes exceeds 800 km. In addition, if actively odd-parity pairing (AOPP) [33] of post data processing is adopted, it can further improve the distance and key rate of SNS−TFQKD significantly.
However, in realistic implementations, the fluctuation of light sources is a common phenomenon in QKD systems [37,38]; therefore, it should be taken into account. In general, the signal from light sources can be considered as a coherent state, whose intensity usually possesses a Gaussian distribution:
where and represent the mean value and standard deviation, respectively. Define the fluctuation coefficient as , and can be rewritten as
After calculating and simplifying, the counting rate of four events can be reformulated as
On the other hand, and will change if light fluctuations are considered, which can be expressed as [36]
Then, the counting rate and the quantum bit error of decoy states in X basis can be respectively re-expressed as
Then, and can be rewritten as [7]
In the following, we compare the performance of SNS−TFQKD with various schemes under different fluctuation coefficients .
In order to simulate the realistic condition, we use a set of practical system parameters in row b of Table 1 [16]. In the realistic condition, the coefficient of light intensity fluctuation is usually greater than [39]; therefore, we set coefficient of intensity fluctuations as and .
As we can see from Figure 3a,b, when intensity fluctuations are taken into account, both ALSM and our present PLSM can show much better performance compared with the original SNS TF-QKD protocol. For example, when or , both ALSM and our present PLSM only slightly decrease its key rate and transmission distance, while the original SNS TF-QKD protocol rapidly drops its key rate and transmission distance.
In practice, when switching between different coefficients, it may bring into modulation errors in the ALSM scheme. We define the attenuation coefficients modulation error as , then , , where and are the upper bound and lower bound of attenuation coefficients. Based on [30], in ALSM has been reestimated in Appendix B. The simulation results are shown in Figure 4, and it is obvious that our scheme can show much better performance than the ALSM scheme when the modulation error is accounted. For example, when we reasonably set , the maximum transmission distance drops from 540 km to 435 km for the ALSM scheme, while it still remains constant for our PLSM scheme. Obviously, the ALSM scheme is very susceptible to intensity modulation errors.
4. Conclusions
In this paper, we propose a PLSM scheme for TF-QKD, which is accomplished by implementing a passive monitoring module consisting of a beam splitter and two detectors at the source side. Through the PLSM module, we can obtain four kinds of monitoring events with two local detectors and can then precisely estimate the bounds of source distributions. We build a theoretical model and carry out corresponding numerical simulations. Simulation results show that our present work can outperform the original SNS−TFQKD protocol when there are existing intensity fluctuations in the light sources. Moreover, it shows much better performance than the reported ALSM scheme when modulation errors are taken into account. Therefore, our present work can not only reduce assumptions on the source distribution in former TF-QKD protocols, but also close the additional loopholes existing in the former active monitoring scheme, and thus seems very promising in practical implementations of QKD in the near future.
Author Contributions
Conceptualization, C.Z., H.Y., X.Z., J.L. and Q.W.; Writing—original draft, X.Q.; Writing—review & editing, X.Q. All authors have read and agreed to the published version of the manuscript.
Funding
We gratefully acknowledge the financial support from the National Key R&D Program of China (2018YFA0306400, 2017YFA0304100), the National Natural Science Foundation of China (12074194, U19A2075, 12104240, 62101285), the Leading-edge technology Program of Jiangsu Natural Science Foundation (BK20192001), the Natural Science Foundation of Jiangsu Province (BK20210582), NUPTSF (NY220122, NY220123), and the Postgraduate Research & Practice Innovation Program of Jiangsu Province (SJCX21_0260).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors are grateful to the anonymous reviewers for their constructive suggestions and comments.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Upper Bound and Lower Bound of Pn (μ) in PLSM
In this appendix, in order to obtain , we use the gain of four events by measuring the idler mode:
With Equation (A1), we have
When setting , we can obtain
Combining Equations (A2) and (A3) to eliminate the parameter :
then is obtained as
According to Equations (A1) and (A2), we scale appropriately and change the equation to an inequality as
Using Equations (A9) and (A12) to eliminate the parameter , we obtain the upper bound of
The lower bound of can be obtained by using and in Equation (A11), and the upper bound can be obtained by using and in Equation (A9):
Appendix B. Upper Bound and Lower Bound of Pn (μ) in ALSM
According to Ref. [29], we set as the probabilities of the single photon detector not responding with for source , which can be described as
and then we set , . When considering the modulation errors, can be reestimated as
Then these reestimated PNDs are used in ALSM SNS−TFQKD to calculate the final secure rate.
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661–663. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Mayers, D. Unconditional security in quantum cryptography. JACM 2001, 48, 351–406. [Google Scholar] [CrossRef]
- Lo, H.-K.; Chau, H.-F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 1999, 283, 2050. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bennett, C.H.; Bessette, F.; Brassard, G.; Salvail, L.; Smolin, J. Experimental quantum cryptography. J. Cryptol. 1992, 5, 3. [Google Scholar] [CrossRef]
- Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 2005, 94, 230503. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.-K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [Green Version]
- Xu, F.; Xu, H.; Lo, H.-K. Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 052333. [Google Scholar] [CrossRef] [Green Version]
- Curty, M.; Xu, F.; Cui, W.; Lim, C.C.W.; Tamaki, K.; Lo, H.-K. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 2014, 5, 3732. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yu, Z.-W.; Zhou, Y.-H.; Wang, X.-B. Statistical fluctuation analysis for measurement-device-independent quantum key distribution with three-intensity decoy-state method. Phys. Rev. A 2015, 91, 032318. [Google Scholar] [CrossRef] [Green Version]
- Zhou, Y.-H.; Yu, Z.-W.; Wang, X.-B. Making the decoy-state measurement-device independent quantum key distribution practically useful. Phys. Rev. A 2016, 93, 042324. [Google Scholar] [CrossRef] [Green Version]
- Jiang, C.; Yu, Z.-W.; Hu, X.-L.; Wang, X.-B. Higher key rate of measurement-device-independent quantum key distribution through joint data processing. Phys. Rev. A 2021, 103, 012402. [Google Scholar] [CrossRef]
- Tamaki, K.; Lo, H.-K.; Wang, W.-Y.; Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv 2018, arXiv:1805.05511. [Google Scholar]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 15043. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lucamarini, M.; Yuan, Z.-L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400. [Google Scholar] [CrossRef] [PubMed]
- Ma, X.; Zeng, P.; Zhou, H. Phase-matching quantum key distribution. Phys. Rev. X 2018, 8, 031043. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.-B.; Yu, Z.-W.; Hu, X.-L.T. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef] [Green Version]
- Cui, C.; Yin, Z.Q.; Wang, R.; Chen, W.; Wang, S.; Guo, G.-C.; Han, Z.-F. Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 2019, 11, 034053. [Google Scholar] [CrossRef] [Green Version]
- Curty, M.; Azuma, K.; Lo, H.-K. Simple security proof of twin-field type quantum key distribution protocol. Npj Quantum Inf. 2019, 5, 64. [Google Scholar] [CrossRef]
- Lin, J.; Lütkenhaus, N. Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 2018, 98, 042332. [Google Scholar] [CrossRef] [Green Version]
- Maeda, K.; Sasaki, T.; Koashi, M. Repeaterless quantum key distribution with efficient finite-key analysis overcoming the rate-distance limit. Nat. Commun. 2019, 10, 3140. [Google Scholar] [CrossRef] [Green Version]
- Minder, M.; Pittaluga, M.; Roberts, G.L.; Lucamarini, M.; Dynes, J.F.; Yuan, Z.L.; Shields, A.J. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 2019, 13, 334. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, Z.-W.; Zhang, W.; Guan, J.Y.; Chen, J.-P.; Zhang, C.; Hu, X.-L.; Li, H.; Chen, T.-Y.; You, L.; et al. Experimental twin-field quantum key distribution through sending or not sending. Phys. Rev. Lett. 2019, 123, 100505. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wang, S.; He, D.-Y.; Yin, Z.-Q.; Lu, F.-Y.; Cui, C.-H.; Chen, W.; Zhou, Z.; Guo, G.-C.; Han, Z.-F. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 2019, 9, 021046. [Google Scholar] [CrossRef] [Green Version]
- Zhong, X.; Hu, J.; Curty, M.; Qian, L.; Lo, H.-K. Proof-of-principle experimental demonstration of twin-field type quantum key distribution. Phys. Rev. Lett. 2019, 123, 100506. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fang, X.-T.; Zeng, P.; Liu, H. Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 2020, 14, 422. [Google Scholar] [CrossRef]
- Chen, J.-P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.L.; Guan, J.-Y.; Yu, Z.-W.; Xu, H.; Lin, J.; et al. Sending-or-not-sending with independent lasers: Secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef] [Green Version]
- Qiao, Y.; Wang, G.; Li, Z.; Xu, B.; Guo, H. Monitoring an untrusted light source with single-photon detectors in measurement-device-independent quantum key distribution. Phys. Rev. A 2019, 99, 052302. [Google Scholar] [CrossRef]
- Qiao, Y.; Wang, G.; Li, Z.; Xu, B.; Guo, H. Sending-or-not-sending twin-field quantum key distribution with light source monitoring. Entropy 2019, 22, 36. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Jiang, C.; Yu, Z.-W.; Hu, X.L.; Wang, X.-B. Unconditional security of sending or not sending twin-field quantum key distribution with finite pulses. Phys. Rev. Appl. 2019, 12, 024061. [Google Scholar] [CrossRef] [Green Version]
- Zhang, C.H.; Zhang, C.M.; Wang, Q. Twin-field quantum key distribution with modified coherent states. Opt. Lett. 2019, 44, 1468–1471. [Google Scholar] [CrossRef]
- Xu, H.; Yu, Z.-W.; Jiang, C.; Hu, X.L.; Wang, X.-B. Sending-or-not-sending twin-field quantum key distribution: Breaking the directtransmission key rate. Phys. Rev. A 2020, 101, 042330. [Google Scholar] [CrossRef]
- Wang, Q.; Zhang, C.-H.; Wang, X.-B. Scheme for realizing passive quantum key distribution with heralded single-photon sources. Phys. Rev. A 2016, 93, 032312. [Google Scholar] [CrossRef]
- Zhang, C.-H.; Wang, D.; Zhou, X.-Y.; Wang, S.; Zhang, L.-B.; Yin, Z.-Q.; Chen, W.; Han, Z.-F.; Guo, G.-C.; Wang, Q. Proof-of-principle demonstration of parametric down-conversion source based quantum key distribution over 40 dB channel loss. Opt. Express 2018, 26, 25921. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.-B.; Peng, C.-Z.; Zhang, J.; Yang, L.; Pan, J.-W. General theory of decoy-state quantum cryptography with source errors. Phys. Rev. A 2008, 77, 042311. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Qi, B.; Lo, H.-K.; Qian, L. Security Analysis of an untrusted source for quantum key distribution: Passive approach. New J. Phys. 2010, 12, 023024. [Google Scholar] [CrossRef]
- Wang, X.-B. Decoy-state quantum key distribution with large random errors of light intensity. Phys. Rev. A 2007, 75, 052301. [Google Scholar] [CrossRef] [Green Version]
- Xu, F.; Zhang, Y.; Zhou, Z.; Chen, W.; Han, Z.; Guo, G. Experimental demonstration of counteracting imperfect sources in a practical one-way quantum-key-distribution system. Phys. Rev. A 2009, 80, 062309. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).