Abstract
This paper presents a novel five-dimensional three-leaf chaotic attractor and its application in image encryption. First, a new five-dimensional three-leaf chaotic system is proposed. Some basic dynamics of the chaotic system were analyzed theoretically and numerically, such as the equilibrium point, dissipative, bifurcation diagram, plane phase diagram, and three-dimensional phase diagram. Simultaneously, an analog circuit was designed to implement the chaotic attractor. The circuit simulation experiment results were consistent with the numerical simulation experiment results. Second, a convolution kernel was used to process the five chaotic sequences, respectively, and the plaintext image matrix was divided according to the row and column proportions. Lastly, each of the divided plaintext images was scrambled with five chaotic sequences that were convolved to obtain the final encrypted image. The theoretical analysis and simulation results demonstrated that the key space of the algorithm was larger than 10150 that had strong key sensitivity. It effectively resisted the attacks of statistical analysis and gray value analysis, and had a good encryption effect on the encryption of digital images.
1. Introduction
In recent years, chaotic and hyperchaotic systems that can produce various types and are suitable for secure communication have become topics of great interest in the fields of physics, biomathematics, and information security [1]. Compared with the traditional encryption method, the complex structure and dynamic behavior of chaotic attractors have a better encryption effect for digital image encryption [2]. Therefore, it has become more important to construct chaotic attractors with multiple scrolls. In the process of encrypting digital images, the core purpose is to change the position of pixels and the size of pixel values. Therefore, experts and scholars have proposed many encryption algorithms such as using chaotic sequences to perform bit disturb of images [3,4], using the chaotic sequence and image pixel value for the XOR operation [5,6], and scrambling the pixel [7,8,9]. A nonlinear state feedback controller was proposed in Reference [10] based on the original three-dimensional (3D) autonomous chaotic system to construct a new four-dimensional hyperchaotic system. An image encryption algorithm based on five-dimensional hyper-chaos and bit-level disturbance was proposed in Reference [11]. Chaotic image encryption algorithms based on bit-level scrambling and dynamic DNA coding were proposed in Reference [12]. Liu et al. [13] proposed an image encryption algorithm for bit position chaos on the upper four bits. On the basis of arranging the diffusion structure, to improve safety and sensitivity, a chaotic image encryption algorithm based on a breadth-first search and dynamic diffusion was proposed in Reference [14]. The cryptosystem in Reference [15] uses a diffusion layer and then positions the image in layers instead of byte permutations to disturb the position of the image pixels. A new chaotic system with hidden attractors and a chaotic-based image encryption algorithm with a random number generator was proposed in Reference [16]. To reduce the processing time, Enayatifar et al. [17] performed simultaneous replacement and diffusion steps for any pixel.
Many chaotic-based image encryption algorithms have been inspired by Fridrich’s method. Therefore, this architecture has become most well-known [18]. However, security of an efficient image encryption method is a fundamental issue in an image encryption algorithm. Recent cryptanalytical studies have proven that some chaos-based algorithms are not adequately secure to resist against a common attack such as Reference [19].
In the proposed scheme, the new five-dimensional chaotic system can generate three-leaf chaotic attractors in multiple directions. Simultaneously, its dynamic characteristics are analyzed. In the process of encryption, to increase the key space, we perform convolution operations on five chaotic sequences. Second, we scale the image matrix proportionally and scramble the image matrix for each segment separately. Through these processes, the difficulty of the exhaustive attack is increased. All except for the exhaustive method based on the explicit plaintext ciphertext mapping, the method will be invalid and have high security.
The rest of the paper is organized as follows. In Section 2, the chaotic system model is given. In Section 3, circuit design and experimental results are described. In Section 4, related knowledge is introduced. The encryption scheme is described in Section 5. Simulation results and performance analyses are reported in Section 6. Lastly, the conclusions are drawn in Section 7.
2. New Five-Dimensional Chaotic System
In 1994, Sprott [20] summarized many 3D chaotic systems. After analyzing these 3D chaotic systems, we propose a new 3D chaotic system. The system equations are as follows.
when a = −1, b = −3, c = 1, d = 1, e = 1, f = 1, system (1) is in a chaotic state.
Based on system (1), we introduce two controllers, w, v, and feedback w into the original controller y, feedback v into the original controller w, original controller x feedback into the new controller v, original controller y feedback into the new controller w, v, original controller z feedback to the new controller w, and feedback v to w. These six operations make the five controllers of this system interact with each other, which makes the relationship more complicated. The newly constructed five-dimensional chaotic system is as follows.
when parameters a = −1, b = −3, c = −3, d = 1.8, e = −5, the system is in a chaotic state.
2.1. Dissipative Analysis
Because of
Therefore, system (2) is dissipative, and convergence is in an exponential form of V0e−(a+c+e)t. Clearly, the volume element V0 shrinks to the volume V0e−(a+c+e)t at moment t. Now consider when . Each volume element that contains the system trajectory shrinks to 0 at an exponential rate a + c + e = −9.
2.2. Balance Point Analysis
Let x = y = z = w = v = 0, that is,
when , , , , , the three equilibrium points of system (2) obtained by Equation (4) are , , . The balance point is and the corresponding eigenvalues are . Therefore, is a stable focus, the balance point is , and the corresponding eigenvalues are , where are positive numbers. Therefore, the balance point is an unstable saddle focus, the balance point is , and the corresponding eigenvalues are where the real part of is positive, and the balance point is an unstable saddle focus.
2.3. Time Series Chart
When , , , , , the sequence diagram of the values changes over time , as shown in Figure 1. We can see that when the system parameters , , , , , system (2) is in a chaotic state.
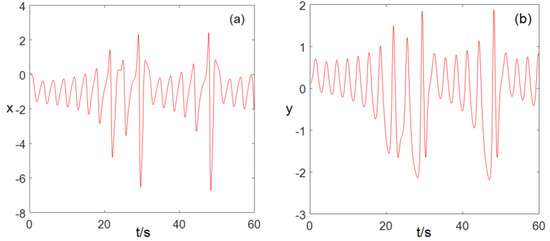
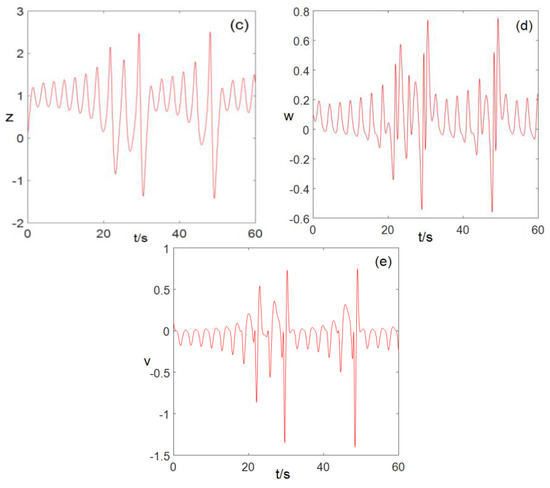
Figure 1.
Time series diagram (a) time series, (b) time series, (c) time series, (d) time series, (e) time series.
2.4. Phase Diagram Analysis
For system parameters , the 3D phase diagram generated by system (2) is shown in Figure 2. The resulting planar phase diagram is shown in Figure 3. It can be clearly seen from Figure 2 and Figure 3 that the chaotic system can generate three-leaf chaotic attractors in multiple directions.
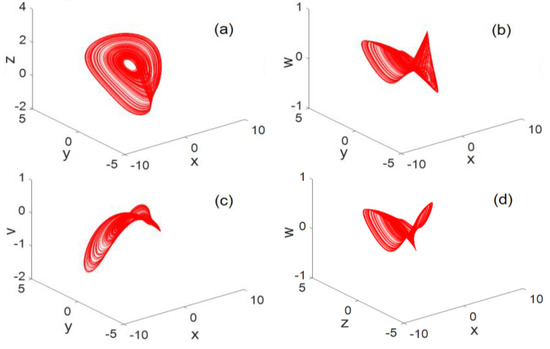
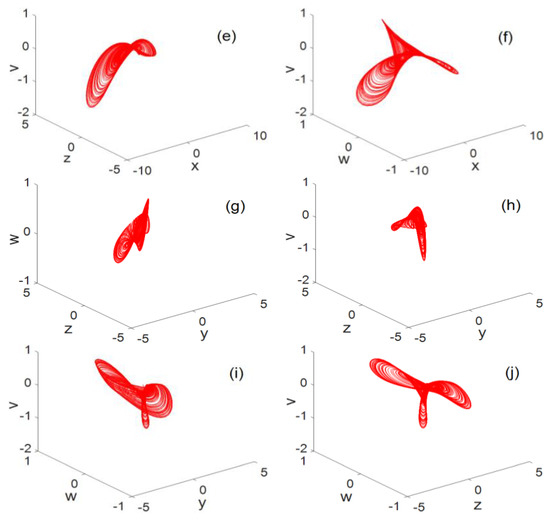
Figure 2.
3D phase diagram (a) 3D map, (b) 3D map, (c) 3D map, (d) 3D map, (e) 3D map, (f) 3D map, (g) 3D map, (h) 3D map, (i) 3D map, (j) 3D map.
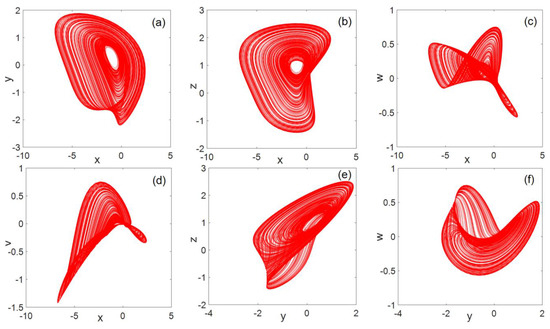
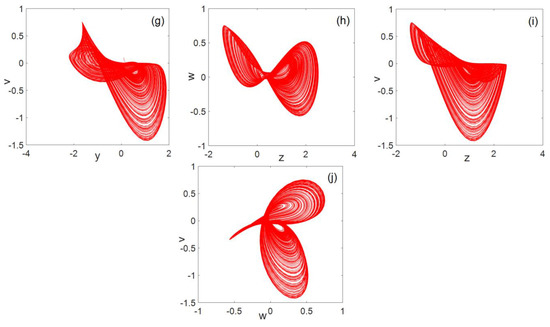
Figure 3.
Plane phase diagram (a) flat, (b) flat, (c) flat, (d) flat, (e) flat, (f) flat, (g) flat, (h) flat, (i) flat, and (j) flat.
2.5. Bifurcation Diagram
For the equation parameters , the bifurcation diagram of the change in parameter is shown in Figure 4. Figure 4 shows that, when the parameter , system (2) is in a chaotic state.
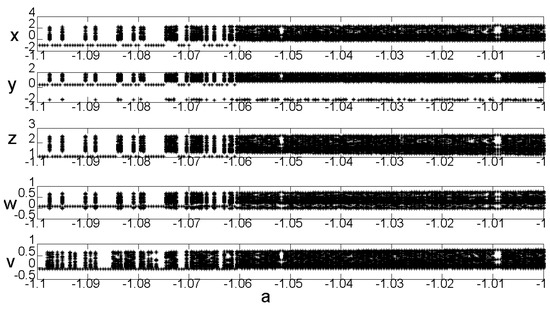
Figure 4.
System (2) bifurcation diagram with variable .
For equation parameters , , the bifurcation diagram of the change in parameter is shown in Figure 5. As can be seen from Figure 5, when the parameter , system (2) is in a chaotic state.
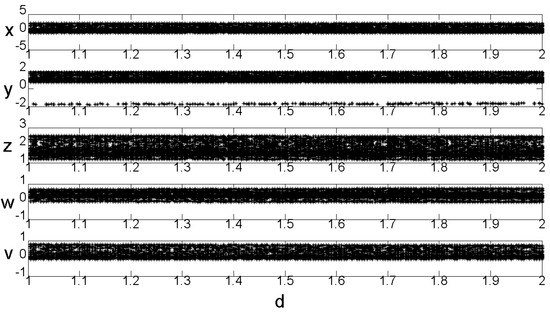
Figure 5.
System (2) bifurcation diagram with variable .
2.6. Power Spectrum Analysis
The power spectrum of the chaotic sequence is a continuum, and the calculation results of the sequence , and power spectrums of system (2) are shown in Figure 6a–d, respectively. It can be seen from Figure 6 that system (2) is in a chaotic state.
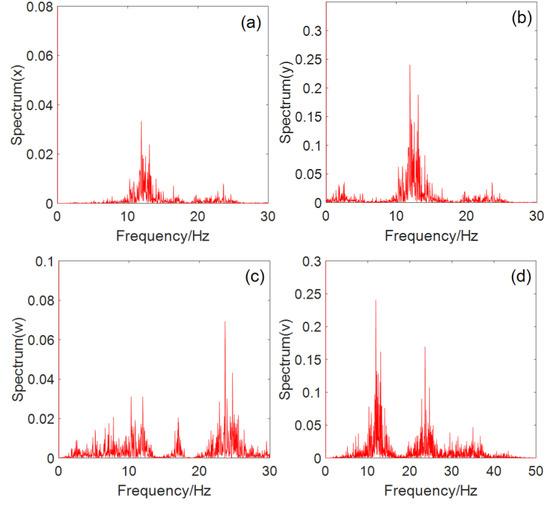
Figure 6.
System power spectrum: (a) power spectrum of the sequence, (b) power spectrum of the sequence, (c) power spectrum of the sequence, and (d) power spectrum of the sequence.
3. Circuit Design and Experimental Results
In this section, we design an analog circuit, as shown in Figure 7, which is mainly composed of an inverting adder, integrator, and inverter composed of an operational amplifier TL082CD. The power supply voltage of the operational amplifier TL082CD is . This circuit has a simple structure and is easy to implement. The experimental results for this circuit are shown in Figure 8. Figure 8a shows the plane, Figure 8b shows the plane, and Figure 8c shows the plane. It can be seen from the oscilloscope that the experimental results for the circuit for the three-leaf chaotic attractor in each plane were consistent with the results of the numerical simulation experiments.
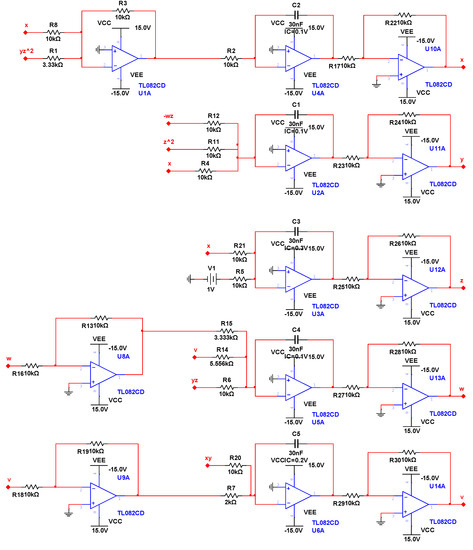
Figure 7.
Five-dimensional chaotic system circuit diagrams.
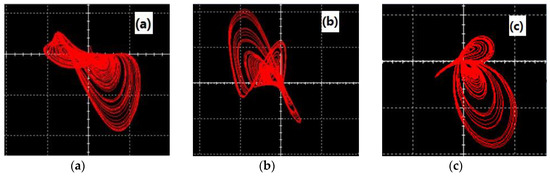
Figure 8.
Experimental results for the circuit (a) plane, (b) plane, and (c) plane.
4. Related Information
4.1. Convolution Operation
Let
is the convolution kernel of ,
is an matrix, where . Then a matrix is obtained by a convolution operation between matrix and convolution kernel .
The convolution operation steps are as follows.
Step 1: Extend matrix to an matrix with 0.
where , .
Step2: Obtain matrix using a convolution operation between matrix and convolution kernel , where
4.2. “Same OR” Operation
The “same OR” operation and the “exclusive OR” operation have the same effect. The “same OR” operation is defined as follows: when the input variables are the same, the output is 1, and when the input variables are different, the output is 0. The calculation results are presented in Table 1.

Table 1.
Result table for the “same OR” operation.
5. Algorithm Descriptions
5.1. Encryption Algorithm Description
The flow chart of the encryption is shown in Figure 9.
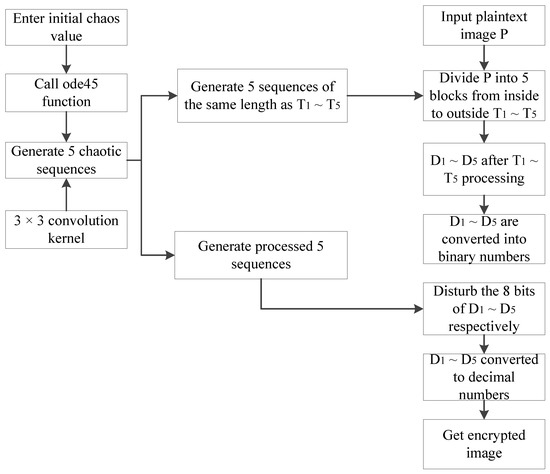
Figure 9.
Encryption flow chart.
Given an grayscale image , the encryption steps are as follows.
Step 1: Input a grayscale image , initial value of the chaotic system , and the step size .
Step 2: Find the total iteration time , where .
Step 3: Call the ode45 function, iterate system (2), and generate five chaotic sequences.
Step 4: The five chaotic sequences are treated separately as follows.
where is the value that starts from the 250th value of the chaotic sequence . Use to convert the fetched values into an matrix, and then multiply each element value of the matrix by
Step 5: Given a convolution kernel of .
Step 6: For the five matrices , obtained in step 4, apply the convolution operation with the given convolution kernel to obtain five matrices , .
Step 7: Divide grayscale image into five regions starting from the center area in the proportion . Input the value of using , and obtain n1. The formulas for mi and ni are as follows.
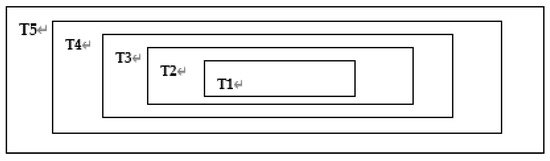
Figure 10.
Division of grayscale image .
Step 8: Divide the region in matrix according to the starting point and size of in grayscale image , as shown in Figure 11.
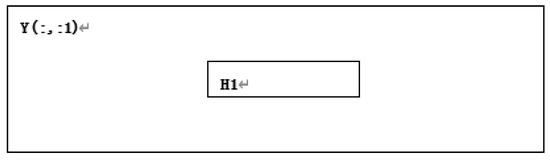
Figure 11.
divided from .
Step 9: Convert matrix and matrix sums of one row and column matrix and , respectively. is treated as follows.
Step 10: Combine and , and perform a bitwise “” operation to obtain matrix .
Step 11: Process as follows to obtain and .
Step 12: Convert matrix into binary matrix .
Step 13: Disturb each line of binary numbers in each row of , and then obtain matrix .
The disturbance formula is as follows.
where denotes all the columns of row of matrix and moves all elements of row vector clockwise by units.
Step 14: Disturb all column elements of , and then obtain . The disturbance formula is as follows.
where denotes all the rows of column of matrix C1 and circshift(A,k,1) moves all the elements of column vector A clockwise by k units.
Step 15: Convert binary number matrix C2 to decimal number matrix D1.
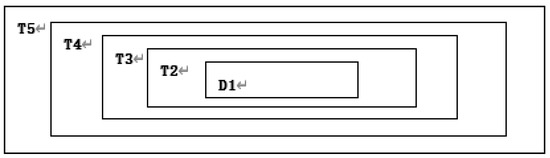
Figure 12.
Subtraction after replacing with .
Step 17: The area is taken out according to in the starting point and size in from , as shown in Figure 13.

Figure 13.
divided in .
Step 18: Convert matrix and matrix sums of one row and column matrix and , respectively. is treated as follows.
Step 19: Combine and , and perform a bitwise “same OR” operation to obtain matrix
Step 20: Process to obtain and as follows.
Step 21: Convert matrix into binary matrix .
Step 22: Scramble each row of binary numbers in to obtain matrix . The scrambling formula is as follows.
Step 23: Disturb all the column elements of to obtain . The scrambling formula is as follows.
Step 24: Convert binary number matrix to decimal number matrix .
Step 25: Replace area with . The result is shown in Figure 14.

Figure 14.
Subtraction after replacing with .
Step26: According to from the starting point and size in the , take the area from , as shown in Figure 15.

Figure 15.
is divided to obtain .
Step 27: Convert the matrices and into matrices and with one row and columns, respectively, and process as follows.
Step 28: Combine and , and perform a bitwise “same OR” operation to obtain matrix .
Step 29: Process as follows to obtain and .
Step 30: Convert matrix into binary matrix .
Step 31: Scramble the binary numbers in each row of to obtain matrix . The scrambling formula is as follows.
Step 32: Disturb all the column elements of to obtain . The scrambling formula is as follows.
Step 33: Convert binary number matrix to decimal number matrix .
Step 34: Replace area with . The result is shown in Figure 16.

Figure 16.
Subtraction after replacing with .
Step 35: Take region from according to the starting point and size of in , as shown in Figure 17.
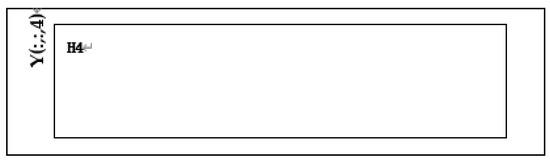
Figure 17.
is divided to obtain .
Step 36: Convert matrices and into matrices and with one row and columns, respectively, and process as follows.
Step 37: Combine and , and perform a bitwise “XOR” operation to obtain matrix .
Step 38: Process to obtain and as follows.
Step 39: Convert matrix into binary matrix .
Step 40: Scramble the binary numbers in each row in to obtain matrix . The scrambling formula is as follows.
Step 41: Disturb all the column elements of to obtain . The scrambling formula is as follows.
Step42: Convert binary number matrix to decimal number matrix .
Step43: Replace area with . The result is shown in Figure 18.
Figure 18.
Subtraction after replacing with .
Step 44: Convert matrix and to matrix and with one row and columns, respectively, and is treated as follows.
Step 45: Combine and , and perform a bitwise “same OR” operation to obtain matrix .
Step 46: Process as follows to obtain and .
Step 47: Convert matrix into binary matrix .
Step 48: Scramble the binary numbers in each row of to obtain matrix . The scrambling formula is as follows.
Step 49: Disturb all the column elements of . The scrambling formula is as follows.
Step 50: Convert binary number matrix to decimal number matrix , and is the final encrypted image. The result is shown in Figure 19.

Figure 19.
Encrypted image.
5.2. Decryption Algorithm Description
Step 1: Input the initial value of the chaotic system and step size , and find the total iteration time , where .
Step 2: Call the ode45 function, iterate system (2), and generate five chaotic sequences.
Step 3: The five chaotic sequences are treated as follows.
where is the value starting from the 250th value of chaotic sequence . Use to convert the fetched values into an matrix, and then multiply each element value of the matrix by .
Step 4: Regarding the matrix , of , the five obtained in the previous step convolution operation with the given convolution kernel of the encryption algorithm include five matrix , of are obtained.
Step 5: Divide the encrypted image of into five regions in proportion to the middle region, with , as shown in Figure 20.

Figure 20.
Division diagram for .
Step6: Restore in turn to obtain decrypted image .
6. Experimental Results and Analysis
6.1. Experiment Platform
The PC configuration was as follows: Intel(R) Core (TM) i5-6500 CPU @ 3.70 GHz 3.70 GHz, memory 8 GB, and Windows 7 64-bit operating system. The above encryption algorithm was implemented in a program in MATLAB R2014a.
6.2. Experimental Result
For the experiment, six types of grayscale images of classic images were selected: Lena, boat, baboon, peppers, couple, and leaf, which were all . This algorithm is also applicable to grayscale images of any sizes. The plaintext image, encrypted image, and decrypted image are shown in Figure 21.
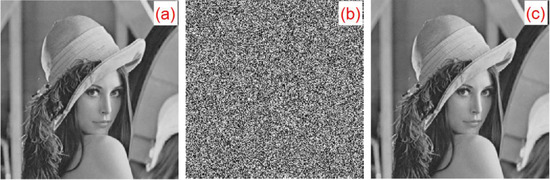
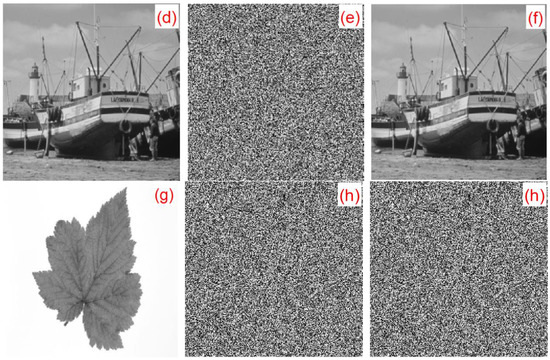
Figure 21.
Encrypted/decrypted experimental results: (a) Lena original image, (b) Lena encrypted image, (c) Lena decrypted image, (d) boat original image, (e) boat encrypted image, (f) boat decrypted image, (g) leaf original image, (h) leaf encrypted image, and (i) leaf decrypted image.
6.3. Key Space Analysis
The size of the key space is one of the most important factors that determines the strength of the image encryption algorithm. The larger the key space, the stronger the ability to resist brute force
attacks. The secret keys of this proposed encryption algorithm include five initial values and five system parameters . Since the precision is by computer with accuracy, the key space is . In addition, when the convolution kernel size is , the secret key also needs to consider nine convolution kernel parameters. Therefore, the total key space of the algorithm is much larger than . For a security encryption algorithm, its key space should be larger than [21]. Therefore, this algorithm was sufficiently secure.
6.4. Convolution Nuclear Sensitivity Analysis
In the encryption process, we multiplied each element of the five chaotic sequences produced by 1011 and performed convolution operations with the convolution kernel of . The convolution kernel of in this algorithm was . In the decryption process, when any of the parameters in the convolution kernel were slightly changed, the original image could not be successfully decrypted. When any parameter in the convolution kernel changed slightly with , the decrypted image was blurred, but the outline could be seen, as shown in Figure 22c. When any of the parameters in the convolution kernel was slightly changed with , the decrypted image could not substantially display the plaintext image information, as shown in Figure 22d. When any parameter in the convolution kernel changed slightly with , the plaintext image information could not be solved at all, as shown in Figure 22e. Taking the Lena image as an example, we made a slight change to the parameters of the second row and the second column of the convolution kernel: , , . The plaintext images, ciphertext images, and the corresponding decrypted images of , , and are shown in Figure 22.
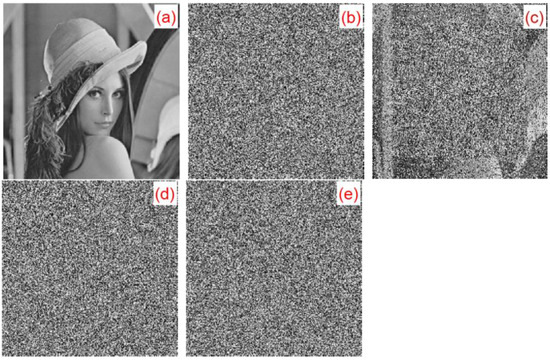
Figure 22.
decryption map: (a) Lena plaintext image, (b) corresponding decrypted image, (c) corresponding decrypted image, (d) corresponding decrypted image, and (e) corresponding decrypted image.
A small change in the convolution kernel can lead to a great change in the ciphertext. In this study, only the Lena image was used as an example. Figure 23 shows the sensitivity of this algorithm to convolution kernels. Figure 23a is a plaintext image. Figure 23b,c are convolution kernels, and for encrypted ciphertext image and , respectively. Figure 23d is the result of the correct decryption for using . Figure 23e,f show the results of and using the wrong convolution kernel and decryption, respectively. Figure 23 illustrates that, despite only minor changes between the convolution kernels and , the ciphertext images and could not be properly decrypted with the convolution kernels.
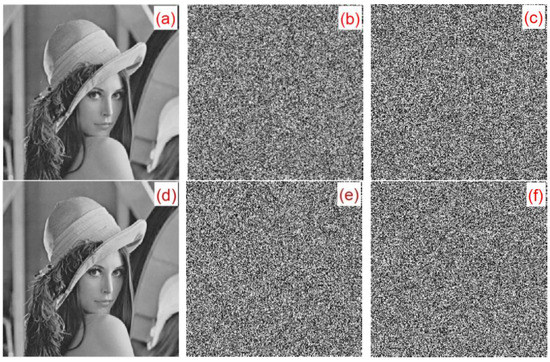
Figure 23.
Convolution nuclear sensitivity experiment analysis chart: (a) Plaintext image, (b) Ciphertext (convolution kernel ), (c) Ciphertext (convolution kernel ), (d) correct decryption result, (e) error decryption result using , and (f) error decryption result using .
The difference between the two images can also be measured by the pixel change rate (NPCR) and the normalized mean change intensity (UACI), which are described as Equations (29) and (30).
where ; is the size of the image. and are the pixel values at position . The larger the values of NPCR and UACI, the greater the difference between the two images. To better evaluate the sensitivity of the convolution kernel, we use Equations (29) and (30) to calculate the and of the encrypted images obtained by the slightly changed convolution kernels and the encrypted image obtained by the original convolution kernel . There are , , , , , . The and values between the obtained encrypted images are shown in Table 2. Table 2 shows that using the convolution kernel operation can greatly increase the key space of the algorithm.

Table 2.
Convolution nuclear sensitivity test results.
6.5. Key Sensitivity Analysis
A small change in the key results in a great change in the ciphertext, which is the key sensitivity. In the experiment, the Lena image was considered as an example. Figure 24 shows the sensitivity of the algorithm to the initial key. Figure 24a is a plaintext image. Figure 24b,c show the results of using keys and for encrypted ciphertext image and , respectively. Figure 24d shows the result of the correct decryption of using . Figure 24e,f show the results of and using the wrong decryption keys and , respectively. Figure 24 illustrates that, despite only minor changes between the keys and , the ciphertext images and could be decrypted correctly using the corresponding keys and .
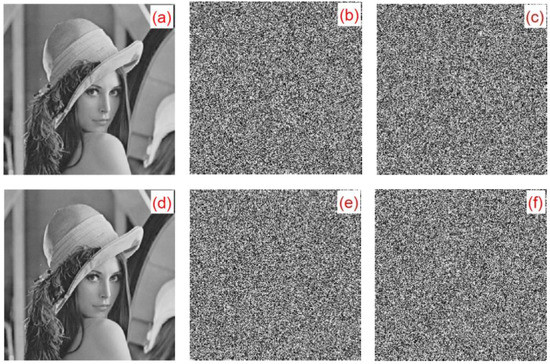
Figure 24.
Key sensitivity experiment analysis chart: (a) plaintext image, (b) ciphertext (key is ), (c) ciphertext (key is ), (d) Correct decryption result, (e) error decryption result using , and (f) error decryption result using .
To better evaluate the key sensitivity of the algorithm, we tested the and values between the keys and for the encrypted image using Equations (29) and (30). The test values in this study and those in the literature [4,14,17] are shown in Table 3. Table 3 shows that the algorithm had good test results, so the encryption algorithm proposed in this paper has good key sensitivity.

Table 3.
Key sensitivity test results.
6.6. Information Entropy Analysis
Information entropy is an important indicator of randomness, which reflects the distribution of gray values of images. The more uniform the gray value distribution, the larger the information entropy of the image. The information entropy calculation formula of an image is shown below.
where is the probability of and is the total number of . For grayscale images, the theoretical maximum value of information entropy is 8. The closer the image information entropy is to the theoretical maximum, the more random the image pixel gray value distribution is. The information entropy before and after the encryption of Lena, baboon, boat, peppers, couple, and leaf is shown in Table 4. The simulation results show that the pixel value distribution of the encrypted image was very uniform, and the algorithm had a good encryption effect.

Table 4.
Information entropy analysis for plaintext and encrypted images.
Considering the Lena image as an example, the information entropy after encrypting the image was compared with the information entropy in the literature [4,11,12,13,17]. The experimental results are shown in Table 5. Table 5 shows that the algorithm had a better encryption effect.

Table 5.
Information entropy comparison.
Global and local entropy [22] values of the encrypted image are tabulated in Table 6. From Table 6, it is clear that both the entropy values are closer to the optimal theoretical values (≈8). Furthermore, the obtained results are compared against the critical values at 5%, 1%, and 0.1% significance. From the above discussion, it can be concluded that the proposed encryption algorithm possesses high randomness and is robust against a statistical attack.

Table 6.
Global and local entropy analysis.
6.7. Histogram Analysis
A histogram can reflect the distribution of image pixel values very well. The flatter the histogram is, the more uniform the pixel value distribution is. Figure 25 shows histograms of the original images for Lena, baboon, and boat, and encrypted images.
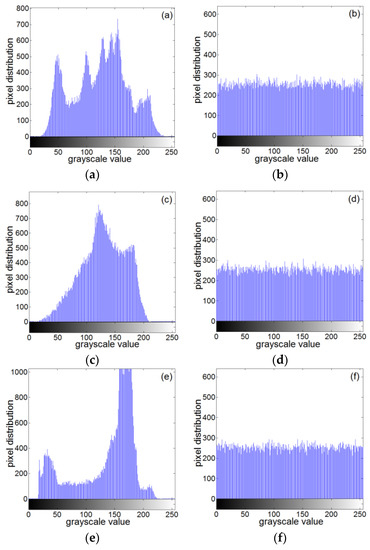
Figure 25.
Histogram of the plaintext image and ciphertext image: (a) histogram of Lena plaintext, (b) histogram of Lena ciphertext, (c) histogram of baboon plaintext, (d) histogram of baboon ciphertext, (e) histogram of the clear text of the boat, and (f) histogram of the boat ciphertext.
6.8. Histogram Statistics
The variance and standard deviation are metrics of dispersion implemented to support the results of visual inspection in graphic histograms. They measure how much the elements of a set of data vary with respect to each other around the mean. Two datasets may have the same average value (mean), but the variations can be drastically different [23].
The variance calculates the average difference between each of the values with respect to their central point (mean ). This average is calculated by squaring each of the differences and calculating its mean again. The squaring process is used to eliminate the negative signs and to increase the variance of dispersed (non-uniform) datasets. On the other hand, the more uniform the graphic histogram is, the lower the histogram variance is, which is determined with the following expression.
where:
is the frequency for each intensity value from 0–255 grayscale value of the histogram, is the histogram variance, and is the mean of the histogram. The standard deviation allows us to know the arithmetic average of fluctuations of the dataset with respect to the mean. It is determined with the square root of the histogram variance as follows.
where is the standard deviation of the histogram. In Table 7, the histogram variance and its standard deviation are presented for plain and encrypted images. Table 7 shows that the pixel values of the image encrypted by this algorithm are more uniform. This algorithm has a better encryption effect.

Table 7.
Histogram statistics with the variance and standard deviation of plain and encrypted images.
6.9. Correlation Analysis of Adjacent Pixels
A feature of digital images is the strong correlation of adjacent pixels. To calculate the correlation of adjacent pixels before and after encryption, 5000 sets of adjacent pixels were randomly selected in the horizontal, vertical, and diagonal directions of the plaintext and ciphertext images. The horizontal, vertical, and diagonal correlation coefficients were calculated using Equations (35).
The test results are shown in Table 8. The pixel correlation of the Lena plaintext image and ciphertext image in the horizontal direction, vertical direction, and diagonal direction are shown in Figure 26.

Table 8.
Test results for the correlation coefficient between plaintext and ciphertext images.
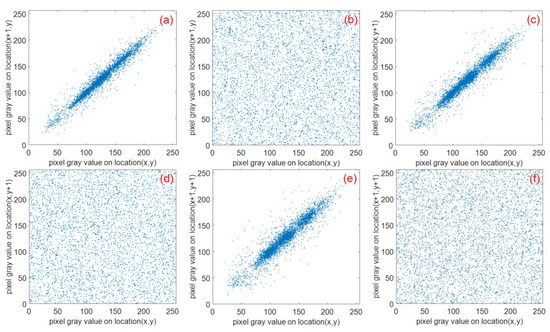
Figure 26.
Correlation analysis of the three directions before and after Lena image encryption: (a) and (b) horizontally adjacent, (c) and (d) vertically adjacent, (e) and (f) diagonally adjacent.
6.10. Robustness Analysis
6.10.1. Quality Metrics Analysis
Quality evaluation of digital images can use the Mean Squared Error () and Peak Signal-to-Noise Ratio () for measurement [23,24]. The is a parameter to measure the difference between two images, which is described as Equation (36).
where is the size of original image, is the original image, and is the encrypted image. The higher value of represents better encryption quality. This analysis is a useful test for a plain image and encrypted image with pixel values in the range of [0–255]. The (expressed in logarithmic scale and decibels) determines the ratio between the maximum possible power of a signal and the power of distorting noise that affects the quality of its representation. It is calculated by Equation (37).
The smaller the MSE value is, the larger the PSNR value is, which means that there is a high degree of similarity between the tested images. By calculation, the between the original image and the decrypted image is 0, and the value of is Inf. In this algorithm, the between the original Lena image and the decrypted image is 77,012, and is 9.265. The results show that the quality metrics of the tested images is good.
6.10.2. Occlusion Attack Analysis
In an occlusion attack, we choose 12.5%, 25%, and 50% of occlusion in an encrypted image. In Figure 27, the attack results are shown. For 12.5% of occlusion, the value is 7853 and the value is 9.1802. For 25% of occlusion, the value is 10,148 and the value is 8.0672. For 50% of occlusion, the value is 13,376 and the value is 6.8676. The results show that the proposed cryptographic algorithm can effectively resist occlusion attack.
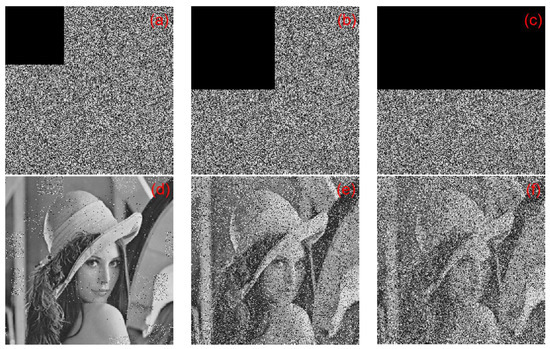
Figure 27.
The results of occlusion attack: (a) encrypted with 12.5% occlusion, (b) encrypted with 25% occlusion, (c) encrypted with 50% occlusion, (d) decrypted with 12.5% occlusion, (e) decrypted with 25% occlusion, and (f) decrypted with 50% occlusion.
6.10.3. Noise Attack Analysis
In order to verify the anti-noise performance of the proposed algorithm, Salt and pepper noise with different intensities was added to the encrypted image. The intensities were 10, 15, and 20, respectively, and they were then decrypted. The results are shown in Figure 28. For 10 of intensity, the value is 8758.9 and the value is 8.706. For 15 of intensity, the value is 9302.9 and the value is 8.446. For 20 of intensity, the value is 9866.8 and the value is 8.189. It can be seen that the original image can be basically recovered after the noise image is decrypted. Therefore, the proposed algorithm has a certain anti-noise attack capability.

Figure 28.
The results of noise attack analysis: (a) noise with 10 of intensity, (b) noise with 15 of intensity, and (c) noise with 20 of intensity.
7. Conclusions
In this paper, a five-dimensional chaotic system was proposed, which had a simple structure and was easy to implement. Basic dynamic analysis of the system was conducted, including the equilibrium point, phase diagram, bifurcation diagram, and power spectrum. Based on the theoretical analysis, a chaotic circuit was designed using the analog device amplifier TL082CD. The consistency of the numerical simulation results confirmed the feasibility of the method. Simultaneously, five chaotic sequences generated by the system were applied to the hybrid image encryption algorithm for physical chaotic encryption and advanced encryption standard encryption. In the algebraic encryption process, we performed convolution operations on five chaotic sequences, which was followed by convolution operations. The latter sequence was applied to the image scaled block encryption, and a numerical simulation experiment was conducted on the hybrid encryption system. The simulation results verified the correctness of the encryption algorithm. Therefore, the encryption algorithm proposed in this paper has a good application prospect in secure communication, particularly digital image encryption.
Author Contributions
Conceptualization, Z.Z.; Data curation, L.S.; Formal analysis, T.W. and M.W.; Methodology, T.W.; Software, T.W.; Validation, S.C.; Writing—original draft, T.W.; Writing—review & editing, T.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
Special Funds for “Double First-Class” Construction in Hubei Province supported the work.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Peng, Z.P.; Wang, C.H.; Yuan, L.; Luo, X.W. A novel four-dimensional multi-wing hyper-chaotic attractor and its application in image encryption. Acta Phys. Sin. Chin. Ed. 2014, 63, 506. [Google Scholar] [CrossRef]
- Liu, Y. Study on Chaos Based Pseudorandom Sequence Algorithm and Image Encryption Technique. Ph.D. Thesis, Harbin Institute of Technology, Harbin, China, 2015. [Google Scholar]
- Rui, L. New Algorithm for Color Image Encryption Using Improved 1D Logistic Chaotic Map. Open Cybern. Syst. J. 2015, 9, 210–216. [Google Scholar] [CrossRef]
- Sun, S. A Novel Hyperchaotic Image Encryption Scheme Based on DNA Encoding, Pixel-Level Scrambling and Bit-Level Scrambling. IEEE Photonics J. 2018, 10, 1–14. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Zhang, M. A fast chaos-based image encryption scheme with a novel plain image-related swapping block permutation and block diffusion. Multimed. Tools Appl. 2016, 76, 15561–15585. [Google Scholar] [CrossRef]
- Ahmad, J.; Khan, M.A.; Ahmed, F.; Khan, J.S. A novel image encryption scheme based on orthogonal matrix, skew tent map, and XOR operation. Neural Comput. Appl. 2017, 30, 3847–3857. [Google Scholar] [CrossRef]
- Ahmad, J.; Hwang, S.O. Chaos-based diffusion for highly autocorrelated data in encryption algorithms. Nonlinear Dyn. 2015, 82, 1839–1850. [Google Scholar] [CrossRef]
- Gao, T.; Chen, Z. Image encryption based on a new total shuffling algorithm. Chaos Solitons Fractals 2018, 38, 213–220. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Li, Y.; Tang, W.K.S.; Chen, G. Generating hyperchaos via state feedback control. Int. J. Bifurc. Chaos 2005, 15, 3367–3375. [Google Scholar] [CrossRef]
- Li, Y.; Wang, C.; Chen, H. A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt. Lasers Eng. 2017, 90, 238–246. [Google Scholar] [CrossRef]
- Zhang, X.; Feng, H.; Ying, N. Chaotic image encryption algorithm based on bit permutation and dynamic DNA encoding. Comput. Intell. Neurosci. 2017, 2017. [Google Scholar] [CrossRef]
- Liu, J.; Yang, D.; Zhou, H.; Chen, S. A digital image encryption algorithm based on bit-planes and an improved logistic map. Multimed. Tools Appl. 2017, 77, 10217–10233. [Google Scholar] [CrossRef]
- Qi, Y.; Wang, C. A New Chaotic Image Encryption Scheme Using Breadth-First Search and Dynamic Diffusion. Int. J. Bifurc. Chaos 2018, 28, 475. [Google Scholar] [CrossRef]
- Assad, S.E.; Farajallah, M. A new chaos-based image encryption system. Signal Process. Image Commun. 2015, 41, 144–157. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü.; Panahi, S.; Akgül, A.; Jafari, S.; Kaçar, S. A new chaotic system with hidden attractor and its engineering applications: Analog circuit realization and image encryption. Analog Integr. Circuits Signal Process. 2019, 98, 85–99. [Google Scholar] [CrossRef]
- Enayatifar, R.; Abdullah, A.H.; Isnin, I.F.; Altameem, A.; Lee, M. Image encryption using a synchronous permutation-diffusion technique. Opt. Lasers Eng. 2017, 90, 146–154. [Google Scholar] [CrossRef]
- Chen, J.X.; Zhu, Z.-L.; Fu, C.; Zhang, L.-B.; Zhang, Y. An image encryption scheme using nonlinear inter-pixel computing and swapping based permutation approach. Commun. Nonlinear Sci. Numer. Simul. 2015, 23, 294–310. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, C.; Li, Q.; Zhang, D.; Shu, S. Breaking a chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn. 2012, 69, 1091–1096. [Google Scholar] [CrossRef]
- Sprott, J. Some simple chaotic flows. Phys. Rev. E 1994, 50, 647–650. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Ravichandran, D.; Praveenkumar, P.; Rayappan, J.B.B.; Amirtharajan, R. DNA Chaos Blend to Secure Medical Privacy. IEEE Trans. Nanobiosci. 2017, 16, 850–858. [Google Scholar] [CrossRef] [PubMed]
- Murillo-Escobar, M.A.; Meranza-Castillón, M.O.; López-Gutiérrez, R.M.; Cruz-Hernández, C. Suggested Integral Analysis for Chaos-Based Image Cryptosystems. Entropy 2019, 21, 815. [Google Scholar] [CrossRef]
- Li, S.; Ding, W.; Yin, B.; Zhang, T.; Ma, Y. A Novel Delay Linear Coupling Logistics Map Model for Color Image Encryption. Entropy 2018, 20, 463. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).