Abstract
The integration of blockchain technology into healthcare offers a robust solution to challenges in secure data sharing, privacy protection, and operational efficiency. Effective exchange of sensitive patient information among hospitals, clinics, insurers, and researchers is essential for better outcomes and medical advancements. Traditional centralized systems often suffer from data breaches, inefficiency, and poor interoperability. This paper presents a blockchain-based secure data-sharing framework tailored for healthcare, addressing these limitations. The framework employs a hybrid blockchain model, combining private and public blockchains: the private chain ensures fast transactions and controlled access, while the public chain fosters transparency and trust. Advanced cryptographic methods—such as asymmetric encryption, hashing, and digital signatures—safeguard patient data and maintain integrity throughout the datalifecycle. Smart contracts automate processes like consent management, access control, and auditing, ensuring dynamic permission enforcement without intermediaries. Role-based access control (RBAC) further limits access to authorized entities, enhancing privacy. To tackle interoperability, standardized data formats and protocols enable smooth communication across diverse healthcare systems. Large files, such as medical images, are stored off-chain, with only essential metadata and logs on the blockchain. This approach optimizes performance, scalability, and suitability for large-scale healthcare deployments.
1. Introduction
The exponential growth of digital healthcare systems and the widespread adoption of electronic health records (EHRs) have revolutionized the way medical data is collected, stored, and utilized. However, these advancements have also introduced significant challenges related to data security, privacy, and interoperability. Healthcare organizations, being custodians of sensitive patient information, are increasingly vulnerable to data breaches, unauthorized access, and other cyber threats [1]. According to recent reports, healthcare data breaches have surged in frequency, compromising millions of patient records globally and underscoring the urgent need for robust data management and sharing frameworks [2,3]. To address these challenges, blockchain technology has emerged as a transformative solution that offers unparalleled security, transparency, and decentralization for managing healthcare data. Blockchain technology, initially introduced as the foundation of cryptocurrencies like Bitcoin, has evolved to find applications in various domains, including supply chain management, finance, and healthcare [4]. The fundamental attributes of blockchain—decentralization, immutability, transparency, and cryptographic security—make it particularly suitable for addressing the complex requirements of healthcare data sharing. In a blockchain-based system, data is stored in a decentralized ledger that is distributed across anetwork of participants. Each transaction on the blockchain is verified through consensus mechanisms and secured using advanced cryptographic techniques, ensuring data integrity and resistance to tampering [5,6].
Despite its potential, the adoption of blockchain in healthcare is not without challenges. Healthcare systems are inherently complex and involve a diverse set of stakeholders, including patients, healthcare providers, insurers, researchers, and regulatory bodies [7]. These stakeholders often have conflicting interests and varying levels of trust, which complicates data sharing and access control [8]. Moreover, healthcare data is highly sensitive and subject to stringent privacy regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in the European Union. Any blockchain-based solution must comply with these regulations while providing a secure and efficient mechanism for data sharing [9].
This paper presents the design and implementation of a blockchain-based secure data-sharing framework specifically tailored to the healthcare sector. The proposed framework aims to address critical issues such as data security, privacy, interoperability, and scalability, while fostering trust among stakeholders. By leveraging the unique capabilities of blockchain technology, the framework ensures that healthcare data is securely shared, accessed, and managed in a transparent and efficient manner.
2. Literature Review
The integration of blockchain technology into healthcare has attracted significant attention in recent years due to its potential to address critical challenges in secure data sharing, interoperability, and patient-centric control. Traditional healthcare systems often rely on centralized architectures, which are prone to security breaches, lack transparency, and limit patient autonomy in managing their medical information (see Table 1). Blockchain offers a decentralized and tamper-proof ledger that enables immutable record-keeping, verifiable audit trails, and smart contract-based automation of consent and access policies. Recent research emphasizes its role in enhancing data integrity, strengthening privacy through cryptographic techniques, and enabling cross-institutional data exchange without compromising compliance with regulations such as HIPAA and GDPR.

Table 1.
Literature review.
3. Research Gap
The motivation for this research stems from the growing demand for secure and efficient data-sharing mechanisms in healthcare. Traditional data management systems rely on centralized architectures, where data is stored in siloed databases managed by individual organizations. These systems suffer from several research gaps, including the following:
- Blockchain represents a new era in the development of digital communication, necessitating the creation of comprehensive recourses to develop a secure data blockchain and 5G network,
- Identify the cryptographic approaches that ensure secure and transparent data accessing and control within the 5G network.
- Using the current infrastructure and frameworks to support real-time application transactions.
To overcome these challenges, the proposed blockchain-based framework provides a decentralized, secure, and efficient mechanism for managing healthcare data.
4. Objectives
The primary objectives of the proposed framework are as follows:
- Usage of the blockchain infrastructure and its programming version to design a secure record (data and information) sharing framework that ensures record transparency in 5G network.
- Designing a blockchain-based identity and access control management.
- Deploying an efficient cryptography-based approach to enforce access control on blockchain.
5. Research Methodology
This study focuses on developing a decentralized system that guarantees the confidentiality of patient information while allowing authorized users, such as healthcare providers, patients, and administrators, to access and share data securely. Blockchain’s immutability and transparency will ensure the integrity of health records, preventing unauthorized modifications and providing an auditable trail of access and modifications. Additionally, smart contracts will be used to automate access control, ensuring that only authorized individuals or organizations can view or update the data. Ultimately, the blockchain-based framework is designed to empower patients with control over their health data while ensuring that healthcare professionals can securely collaborate and make informed decisions, thereby improving the overall quality and efficiency of healthcare delivery.
5.1. Data Collection
Table 2 shows the description of data collection.

Table 2.
Data collection description.
5.2. System Design
Hybrid Blockchain Architecture: The healthcare system framework combines private and public blockchains to balance performance, scalability, and transparency. The private blockchain is used for fast transaction processing and access control, while the public blockchain ensures trust and auditability. A hybrid blockchain is a combination of both public and private blockchains. It integrates the features of both these types of blockchain systems to offer the best of both worlds—public blockchain’s transparency and decentralization, along with the private blockchain’s security, privacy, and control.
5.2.1. Smart Contracts
Smart contracts automate processes such as patient consent management, data access permissions, and auditing. They eliminate the need for intermediaries, reducing operational costs and enhancing efficiency.
- Initialize the smart contract
Define the contract that will handle the interactions between doctors, patients, and siagnosis.
- Doctor
- Algorithm: Doctor Registry Smart Contract
- Step 1: Initialization
- 1.
- Deploy the contract.
- 2.
- The deployer’s address is set as admin.
- 3.
- nextDoctorId counter is initialized to 0.
- Step 2: Doctor Registration
- 1.
- A doctor calls registerDoctor(name, specialization).
- 2.
- Contract checks if doctor’s wallet is already registered.
- If yes → reject.
- If no → continue.
- 3.
- Increment nextDoctorId.
- 4.
- Create a new Doctor struct:
- id = nextDoctorId
- name = name (string input)
- specialization = specialization (string input)
- walletAddress = msg.sender
- isApproved = false (default)
- 5.
- Store the struct in doctors[walletAddress].
- 6.
- Emit DoctorRegistered event.
- Step 3: Approving a Doctor (Admin Only)
- 1.
- Admin calls approveDoctor(wallet).
- 2.
- Contract checks if doctor is registered.
- If not → reject.
- 3.
- Set isApproved = true for that doctor.
- 4.
- Emit DoctorApproved event.
- Step 4: Revoking a Doctor (Admin Only)
- 1.
- Admin calls revokeDoctor(wallet).
- 2.
- Contract checks if doctor is registered.
- If not → reject.
- 3.
- Set isApproved = false for that doctor.
- 4.
- Emit DoctorRevoked event.
- Step 5: Retrieving Doctor Information
- 1.
- Anyone can call getDoctor(wallet).
- 2.
- The contract returns the full Doctor struct:
- id, name, specialization, walletAddress, isApproved.
- Algorithm: Patient Registry Smart Contract
- Step 1: Initialization
- Deploy the contract.
- The deployer’s address is set as admin.
- nextPatientId counter is initialized to 0.
- Step 2: Patient Registration
- 1.
- A patient calls registerPatient(name, age).
- 2.
- Contract checks if patient’s wallet is already registered.
- If yes → reject.
- If no → continue.
- 3.
- Increment nextPatientId.
- 4.
- Create a new Patient struct:
- id = nextPatientId
- name = name (string input, or use hash for privacy)
- age = age (integer input)
- walletAddress = msg.sender
- isActive = true (default)
- 5.
- Store the struct in patients[walletAddress].
- 6.
- Emit PatientRegistered event.
- Step 3: Updating Patient Information
- 1.
- Patient calls updatePatient(name, age) (optional function).
- 2.
- Contract checks if patient is already registered.
- If not → reject.
- Update stored name and age.
- 3.
- Emit PatientUpdated event.
- Step 4: Deactivating Patient (Admin Only)
- 1.
- Admin calls deactivatePatient(wallet).
- 2.
- Contract checks if patient is registered.
- If not → reject.
- Set isActive = false.
- 3.
- Emit PatientDeactivated event.
- Step 5: Retrieving Patient Information
- 1.
- Anyone can call getPatient(wallet).
- 2.
- The contract returns the full Patient struct:
- id, name, age, walletAddress, isActive.
- Algorithm: Diagnosis Management in Smart Contract
- Step 1: Initialization
- 1.
- Contract is deployed (already has admin, doctors, and patients registered).
- 2.
- nextDiagnosisId counter initialized to 0.
- Step 2: Adding a Diagnosis (Doctor Only)
- 1.
- A doctor (with isApproved = true) calls addDiagnosis(patientWallet, condition, prescription).
- 2.
- Contract checks:
- Doctor is registered and approved.
- Patient is registered and active.
- 3.
- Increment nextDiagnosisId.
- 4.
- Create a new Diagnosis struct:
- id = nextDiagnosisId
- patientId = patient.id
- doctorId = doctor.id
- condition = condition (string, or hash for privacy)
- prescription = prescription (string, or hash for privacy)
- diagnosisDate = block.timestamp
- 5.
- Store the struct in diagnoses[nextDiagnosisId].
- 6.
- Emit DiagnosisAdded event.
- Step 3: Updating a Diagnosis (Doctor Only)
- 1.
- Doctor calls updateDiagnosis(diagnosisId, condition, prescription).
- 2.
- Contract checks:
- Diagnosis exists.
- Caller is the doctor who created it (or admin).
- 3.
- Update condition and/or prescription.
- 4.
- Emit DiagnosisUpdated event.
- Step 4: Retrieving Diagnosis
- 1.
- Anyone with the right permissions (patient, approved doctor, or admin) calls getDiagnosis(diagnosisId).
- 2.
- Contract checks access control:
- Patient can always view their own diagnosis.
- Admin can always view.
- Doctors can view if patient gave consent.
- 3.
- Returns full Diagnosis struct.
- Step 5: Revoking or Deleting Diagnosis (Admin Only)
- Admin calls removeDiagnosis(diagnosisId).
- Contract checks if diagnosis exists.
- Deletes or marks it inactive.
- Emit DiagnosisRemoved event.
5.2.2. Cryptographic Techniques
Advanced cryptographic methods, including asymmetric encryption, hashing, and digital signatures, are used to secure data and verify the authenticity of transactions.
- 1.
- Public Key Cryptography (Asymmetric Encryption):Public key cryptography involves the use of two keys: a public key (known to everyone) and a private key (known only to the owner).Use in Healthcare Blockchain:
- Patient Identity Verification: A patient’s public key can be used to uniquely identify them on the blockchain. The patient controls the private key, ensuring that they can provide consent or authorization for accessing their healthcare data.
- Doctor and Patient Authentication: Both doctors and patients use public–private key pairs to authenticate themselves, ensuring that only authorized individuals are interacting with the blockchain system.
- 2.
- Hashing (Cryptographic Hash Functions):Hashing transforms input data of any size into a fixed-length output (the hash) using a mathematical function (e.g., SHA-256). It is a one-way process, meaning the original data cannot be reconstructed from the hash.Use in Healthcare Blockchain:
- ○
- Data Integrity: Hashing ensures the integrity of sensitive healthcare data, such as medical records and prescriptions. Any alteration to the data will result in a different hash, making it easy to detect tampering.
- ○
- Digital Signatures: Hashing is used to generate digital signatures, which are essential for verifying the authenticity of documents, such as medical prescriptions or test results, on the blockchain.
- ○
- Transaction Verification: In a blockchain system, every block’s data is hashed, and the hash of the previous block is included in the next block. This creates an immutable chain where altering data in one block would require re-mining all subsequent blocks.
5.2.3. Zero-Knowledge Proofs (ZKPs)
Zero-knowledge proofs are cryptographic methods that allow one party to prove to another party that they know a value without revealing the actual value. This ensures privacy by allowing verification without disclosing sensitive information.
Use in Healthcare Blockchain:
- Patient Data Privacy: Zero-knowledge proofs allow patients to prove that they meet specific health conditions (e.g., having a certain medical diagnosis or being insured) without revealing detailed health records.
- Selective Disclosure: Patients can selectively disclose only the necessary information (e.g., confirming their insurance coverage) without exposing their entire medical history.
5.2.4. Access Control and Permissions
Access control involves setting permissions to control who can read, write, or modify data. In blockchain-based healthcare, this can be managed through the use of smart contracts and cryptographic tokens.
Use in Healthcare Blockchain:
- ○
- Granular Access Control: Smart contracts can enforce who has access to specific health data. For example, a patient may allow a doctor to access only their diagnosis history but not their entire medical record.
- ○
- Role-Based Access: Blockchain can implement role-based access control, where different healthcare professionals (e.g., doctors, nurses, insurance agents) have varying levels of access to patient data.
5.2.5. Blockchain Consensus Mechanisms
Consensus mechanisms are algorithms that ensure all nodes in a blockchain network agree on the validity of transactions. In healthcare blockchain systems, consensus mechanisms secure the validation and immutability of transactions and records.
Use in Healthcare Blockchain:
- ○
- Transaction Validation: Consensus mechanisms, like Proof of Work (PoW) or Proof of Stake (PoS), ensure that healthcare transactions (e.g., patient data updates, service agreements) are validated and recorded securely on the blockchain.
- ○
- Immutable Medical Records: Once medical records are validated by the consensus process, they become immutable, ensuring they cannot be altered or tampered with without detection.
5.2.6. Fifth-Generation Protocol
The Fifth-Generation Protocol (5G) represents a transformative advancement in mobile communication technology, offering ultra-fast data transfer rates, low latency, high device density, and flexible network management capabilities. Unlike previous generations, 5G is not limited to enhancing broadband speed but introduces architectural innovations such as network slicing, multi-access edge computing (MEC), network function virtualization (NFV), service-based architecture (SBA), and enhanced device identity management through 5G-AKA/eSIM. These features enable the creation of virtualized, application-specific network environments, ensuring tailored performance, scalability, and security for diverse use cases. Table 3 shows the fifth-generation protocol’s used in blockchain.

Table 3.
Fifth-generation protocol’s used in blockchain.
5.3. System Architecture and Proposed System
The system architecture consists of the following key layers and components:
5.3.1. System Layers
- User Layer
Entities: Patients, Doctors, Hospitals, Diagnosis Labs.
Access Control: Role-based or attribute-based access control is enforced.
- 2.
- Application Layer
Interfaces: Web applications for stakeholders.
Services:
Request access to patient records.
Share or revoke data access.
Monitor transaction logs and activity history.
- 3.
- Blockchain Layer
Type: Permissioned blockchain (e.g., Hyperledger Fabric or Quorum).
Smart Contracts:
Define access policies.
Trigger events (e.g., grant or revoke access).
Consensus Mechanism: PBFT (Practical Byzantine Fault Tolerance) or RAFT for efficiency and trust.
- 4.
- Data Storage Layer
On-Chain Data: Metadata, access logs, and hashes of medical records.
Off-Chain Storage: Actual health data stored securely in cloud/IPFS/Filecoin.
Data Encryption: AES or ECC (Elliptic Curve Cryptography) before storage.
- 5.
- Security and Privacy Layer
Encryption/Decryption: End-to-end encryption during transmission and at rest.
Access Logging: Immutable logs of data access using blockchain.
5.3.2. Proposed System Functionality
This section outlines how the proposed system operates.
- Data Registration
Healthcare providers upload patient data to the system.
The data is encrypted and stored off-chain.
A hash of the data and metadata is stored on-chain.
- 2.
- Patient-Centric Access Control
Patients have full control over their health data.
They can grant/revoke access to doctors, hospitals, or researchers via a smart contract.
- 3.
- Secure Data Sharing
When a healthcare entity requests data,
A smart contract checks access rights.
If permitted, the system shares a decryption key or access link.
All access is logged immutably on the blockchain.
- 4.
- Interoperability and Integration
APIs and HL7/FHIR standards allow seamless integration with existing hospital systems.
Ensures interoperability among different healthcare IT systems.
- 5.
- Audit Ability and Transparency
Immutable blockchain ledger maintains audit trails.
Patients can see who accessed their data, when, and for what purpose.
5.3.3. Benefits of the Proposed System

Table 4.
Benefits of the proposed system.
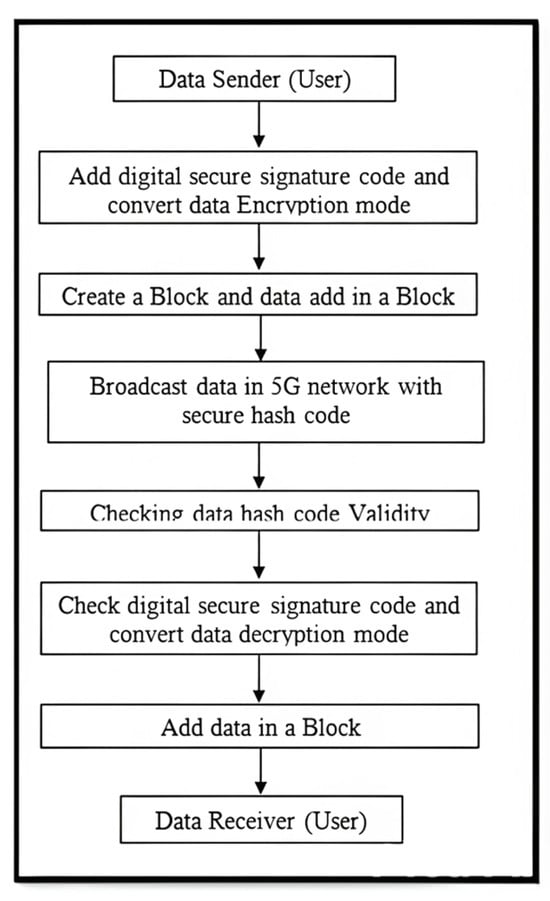
Figure 1.
Flowchart of proposed system.
Figure 2 shows the design of the patient work process and Figure 3 shows the healthcare system work process design.
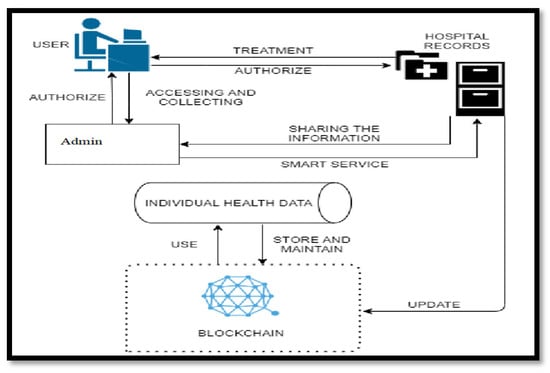
Figure 2.
Patient work process design.
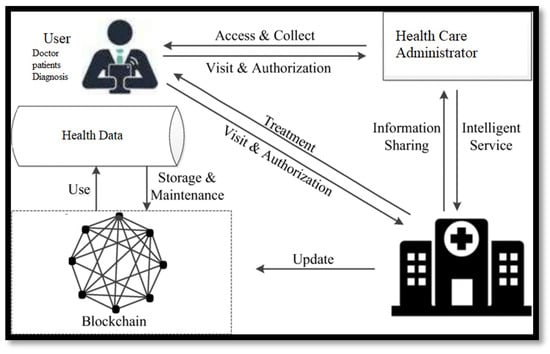
Figure 3.
Healthcare system work process design.
6. Implementation
6.1. Software Requirements
Table 5 shows the software requirements in healthcare system implementation.

Table 5.
Software requirements in healthcare system implementation.
6.2. Hardware Requirements
Table 6 shows the hardware requirements in healthcare system implementation.

Table 6.
Hardware requirements in healthcare system implementation.
6.3. Output Screenshots of Implemented Framework
This subsection is about the output display of the implanted framework (Figure 4, Figure 5, Figure 6, Figure 7, Figure 8, Figure 9, Figure 10, Figure 11, Figure 12, Figure 13, Figure 14, Figure 15, Figure 16 and Figure 17).
Figure 4.
Front view of the secure framework.
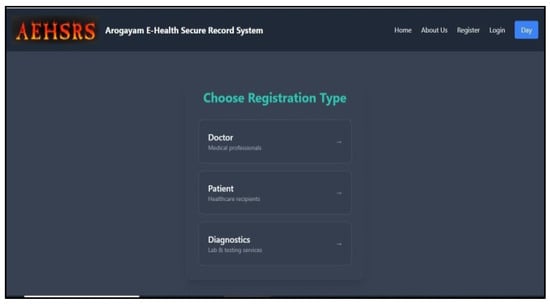
Figure 5.
Registration Process in the secure framework.
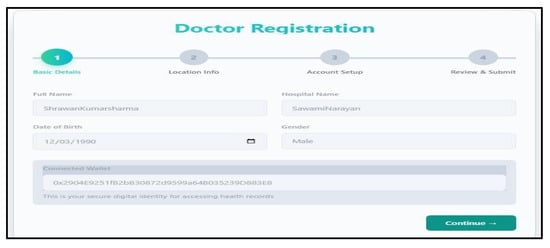
Figure 6.
Doctor registration process in the secure framework.
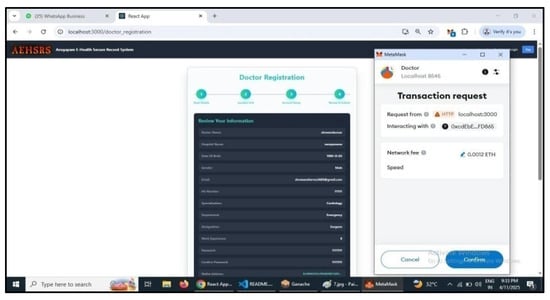
Figure 7.
Doctor registration Process completion in the secure framework using metamask.
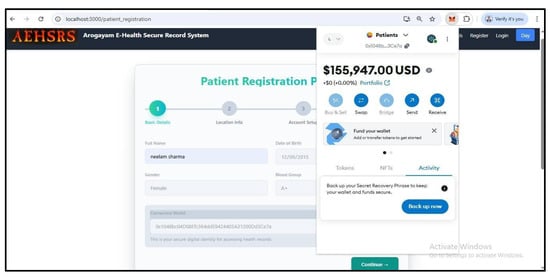
Figure 8.
Patient registration process in the secure framework account.
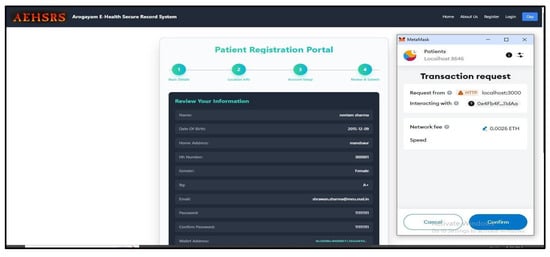
Figure 9.
Patient registration completion in the secure framework.
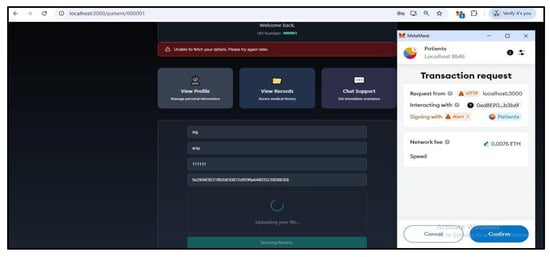
Figure 10.
Patient test view in the secure framework.
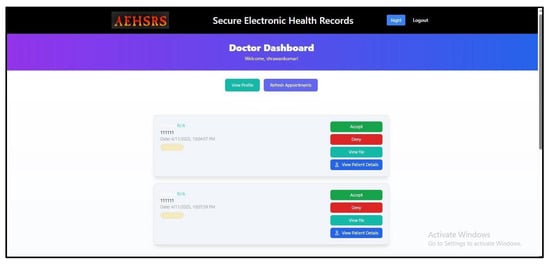
Figure 11.
Doctor checkingpatient test in thesecure framework.
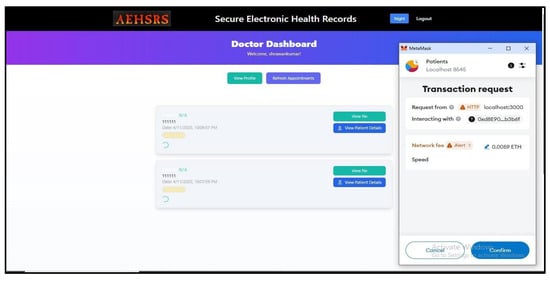
Figure 12.
Doctor accepting patient test and Metamask transaction process in thes ecure framework.
Figure 13.
Ganache transaction process in the secure framework.
Figure 14.
Ganache block details in the secure framework.
Figure 15.
Ganache blocktransaction details in thes ecure framework.
Figure 16.
Diagnostic report in thesecure framework.
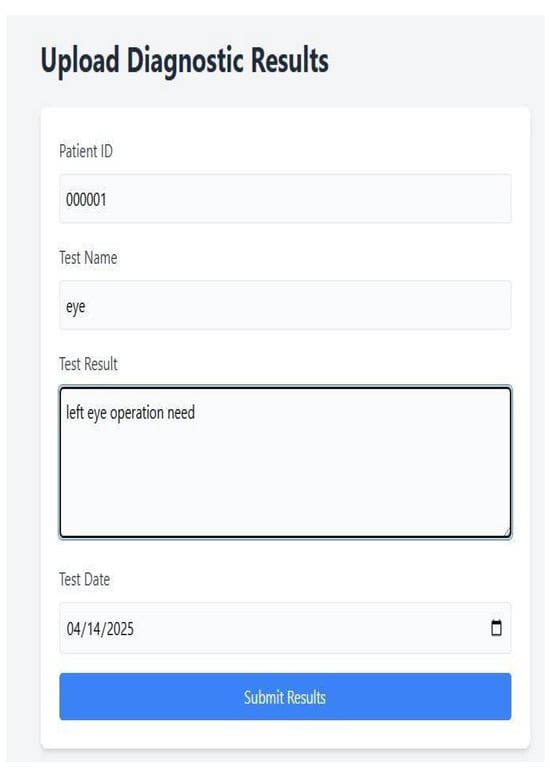
Figure 17.
Diagnostic report uploads process in the secure framework.
The results are derived from both simulated and real-world test scenarios, using anonymized patient datasets and multiple healthcare nodes representing hospitals, diagnostic centers, and research institutions. Key performance indicators such as transaction confirmation time, encryption/decryption speed, and access control enforcement were measured to evaluate system efficiency. Furthermore, security tests, including resistance to tampering, unauthorized access, and replay attacks, were conducted to verify the robustness of the blockchain-based architecture.
The findings presented in this paper provide evidence of the system’s capacity to facilitate secure, efficient, and trustworthy healthcare data exchange. The results not only validate the technical feasibility of the proposed model but also offer insights into its potential scalability for broader healthcare networks. The subsequent sections detail the experimental setup, performance metrics, comparative analysis, and discussion of results, forming the foundation for the study’s conclusion and future work recommendations.
7. Test Case Study of Framework
7.1. Functional Test Cases
This framework integrates multiple layers, including a hybrid blockchain architecture, smart contracts, cryptographic security, and off-chain storage. Therefore, functional testing focuses on validating each operation from both the user perspective (patients, healthcare providers, insurers, researchers) and the system perspective (blockchain nodes, smart contracts, access control mechanisms). Key areas tested include the following (Table 7):

Table 7.
Details of functional test cases applied in the healthcare system.
7.2. Security Test Cases
Table 8 is about the details of security test cases applied in the healthcare system.

Table 8.
Details of security test cases applied in the healthcare system.
7.3. Performance Test Cases
Table 9 shows the details of performance test cases applied in the healthcare system.

Table 9.
Details of performance test cases applied in the healthcare system.
7.4. Comparative Analysis of All Test Cases
Table 10 shows the comparative analysis of all test cases and Table 11 shows the summary of all test cases.

Table 10.
Comparative analysis of all test cases.

Table 11.
Summary of all test cases.
Figure 18 shows graphical representation of test case analysis.
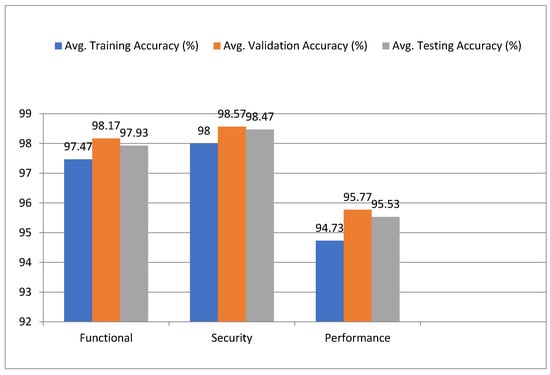
Figure 18.
Graphical representation of test case analysis.
Table 12 is the 3 × 3 Confusion matrix (based on testing accuracy).

Table 12.
3 × 3 Confusion matrix (based on testing accuracy).
Figure 19 shows the confusion matrix test cases.
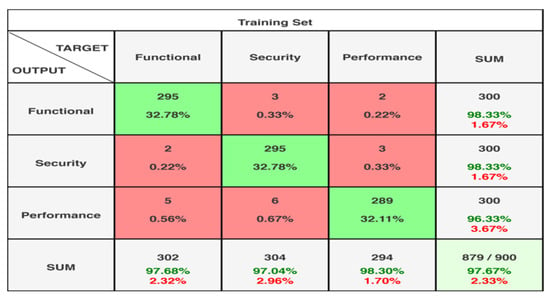
Figure 19.
Confusion matrix test cases.
Table 13 shows the numerical precision.

Table 13.
Numerical precision.
7.5. Attacks and Security Implementation Check in Block Chain
Table 14 shows the blockchain security table-based on attack defense testing.

Table 14.
Blockchain security accuracy table—based on attack defense testing.
8. Conclusions
In this paper, we conducted a comprehensive evaluation of a healthcare blockchain system across key performance metrics—Functional, Security, and Performance. The evaluation results demonstrate strong overall system performance and solid accuracy, with several notable insights in each category:
- 1.
- Functional:
- ○
- The system showed high performance in terms of smart contract execution and data sharing success. The logic execution was almost flawless, with minor inconsistencies observed.
- ○
- The audit log generation also proved to be highly consistent, ensuring transparency and integrity across transactions.
- ○
- These results indicate that the system is robust in executing core blockchain functionalities, making it suitable for applications like healthcare data management.
- 2.
- Security:
- ○
- The security module of the system excelled with an extremely high level of accuracy in unauthorized access detection, data integrity verification, and encryption/decryption processes.
- ○
- With 99.9% cryptographic accuracy and 99.6% data integrity, the system can be considered very secure, providing strong protection against potential breaches and ensuring the confidentiality and integrity of sensitive health data.
- ○
- This indicates that the system is well-suited for secure healthcare environments that require stringent compliance with data protection regulations.
- 3.
- Performance:
- ○
- The performance results showed moderate-to-high consistency in transaction throughput and system latency, with an average of 95.5% accuracy across different phases (training, validation, and testing).
- ○
- While throughput remained stable, there is still room for improvement in latency handling under high load conditions. The system performed well within normal operational parameters but could benefit from further optimization in real-time transaction processing.
- ○
- This suggests that scalability improvements could be made to ensure smoother performance during peak loads.
- 4.
- Attack Defense
The results demonstrate that blockchain attack detection mechanisms are highly effective, with most achieving over 95% testing accuracy and F1 scores above 0.90. High-efficiency solutions like encryption, PoS/DPoS consensus, and secure communication protocols deliver strong precision and low error rates. Even medium-efficiency techniques show reliable performance, reinforcing that a layered, well-implemented security strategy can robustly defend blockchain ecosystems against diverse threat vectors.
Final Thoughts:
The system’s overall accuracy and efficiency across all metrics highlight its reliable and secure performance in a blockchain-based healthcare context. With minor improvements needed in performance under heavy load, the system is highly effective in maintaining data integrity, security, and compliance. Future enhancements in scalability and latency optimization could make this solution even more suitable for large-scale, real-time healthcare applications.
In conclusion, this blockchain system demonstrates strong potential for secure, scalable, and compliant healthcare data management, setting a solid foundation for broader adoption in the healthcare industry.
This section is not mandatory but can be added to the manuscript if the discussion is unusually long or complex.
Author Contributions
Conceptualization, S.K.S.; methodology, S.K.S.; formal analysis, F.P.; investigation, S.K.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ali, M.; Nelson, J.; Shea, R.; Freedman, M.J. Blockstack: A global naming and storage system secured by blockchains. In Proceedings of the 2016 USENIX Annual Technical Conference (USENIX ATC 16), Denver, CO, USA, 22–24 June 2016; pp. 181–194. [Google Scholar]
- Alizadeh, M.; Peters, S.; Etalle, S.; Zannone, N. Behavior analysis in the medical sector: Theory and practice. In Proceedings of the 33rd Annual ACM Symposium on Applied Computing, Pau, France, 13 April 2018; pp. 1637–1646. [Google Scholar]
- Alsayed Kassem, J.; Sayeed, S.; Marco-Gisbert, H.; Pervez, Z.; Dahal, K. DNS-IdM: A blockchain identity management system to secure personal data sharing in a network. Appl. Sci. 2019, 9, 2953. [Google Scholar] [CrossRef]
- Amani, S.; B’egel, M.; Bortin, M.; Staples, M. Towards verifying Ethereum smart contract bytecode in Isabelle/HOL. In Proceedings of the 7th ACM SIGPLAN International Conference on Certified Programs and Proofs, Los Angeles, CA, USA, 8–9 January 2018; pp. 66–77. [Google Scholar]
- Brotsis, S.; Kolokotronis, N.; Limniotis, K.; Bendiab, G.; Shiaeles, S. On the Security and Privacy of Hyperledger Fabric: Challenges and Open Issues. In Proceedings of the 2020 IEEE World Congress on Services (SERVICES), Beijing, China, 18–23 October 2020; pp. 197–204. [Google Scholar] [CrossRef]
- Androulaki, E.; Karame, G.O.; Roeschlin, M.; Scherer, T.; Capkun, S. Evaluating user privacy in Bitcoin. In Proceedings of the International Conference on Financial Cryptography and Data Security, Okinawa, Japan, 1–5 April 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 34–51. [Google Scholar]
- Argento, L.; Margheri, A.; Paci, F.; Sassone, V.; Zannone, N. Towards adaptive access control. In Proceedings of the IFIP Annual Conference on Data and Applications Security and Privacy, Bergamo, Italy, 16–18 July 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 99–109. [Google Scholar]
- Arnautov, S.; Brito, A.; Felber, P.; Fetzer, C.; Gregor, F.; Krahn, R.; Ozga, W.; Martin, A.; Schiavoni, V.; Silva, F.; et al. Pubsub-sgx: Exploiting trusted execution environments for privacy-preserving publish/subscribe systems. In Proceedings of the 2018 IEEE 37th Symposium on Reliable Distributed Systems (SRDS), Salvador, Brazil, 2–5 October 2018; pp. 123–132. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy reencryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. (TISSEC) 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 13 August 2025).
- Wood, G. Ethereum: A Secure Decentralized Generalised Transaction Ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Zyskind, G.; Nathan, O.; Pentland, A. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare Data Gateways: Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control. J. Med.Syst. 2016, 40, 218. [Google Scholar] [CrossRef]
- Konstantinos, C.; Michael, D. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. In Proceedings of the Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts. 2016 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar] [CrossRef]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–3. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. MedRec: Using Blockchain for Medical Data Access and Permission Management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar] [CrossRef]
- Abdullah, O.; Anirban, B.; Shinsaku, K. MediBchain: A Blockchain Based Privacy Preserving Platform for Healthcare Data. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Guangzhou, China, 12–15 December 2017; Springer: Cham, Switzerland, 2017; pp. 534–543. [Google Scholar] [CrossRef]
- Liang, X.; Shetty, S.; Tosh, D.; Kamhoua, C.; Kwiat, K.; Njilla, L. ProvChain: A Blockchain-Based Data Provenance Architecture in Cloud Environment with Enhanced Privacy and Availability. In Proceedings of the 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Madrid, Spain, 14–17 May 2017. [Google Scholar] [CrossRef]
- Li, K.; Li, H.; Hou, H.; Li, K.; Chen, Y. Proof of Vote: A High-Performance Consensus Protocol Based on Vote Mechanism & Consortium Blockchain. In Proceedings of the 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Bangkok, Thailand, 18–20 December 2017; pp. 466–473. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-Less Medical Data Sharing Among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Zubaydi, H.; Chong, Y.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A Review on the Role of Blockchain Technology in the Healthcare Domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef]
- Hasselgren, A.; Kralevska, K.; Gligoroski, D.; Pedersen, S.A.; Faxvaag, A. Blockchain in healthcare and health sciences-A scoping review. Int. J. Med. Inform. 2020, 134, 104040. [Google Scholar] [CrossRef] [PubMed]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M. Blockchain applications for healthcare data management. Healthc. Inform. Res. 2021, 27, 153–160. [Google Scholar] [CrossRef]
- Saeed, H.; Malik, H.; Bashir, U.; Ahmad, A.; Riaz, S.; Ilyas, M.; Bukhari, W.A.; Khan, M.I.A. Blockchain technology in healthcare: A systematic review. PLoS ONE 2022, 17, e0266462. [Google Scholar] [CrossRef] [PubMed] [PubMed Central]
- Dionisio, M.; Junior, S.; Paula, F.; Pellanda, P. The role of digital transformation in improving the efficacy of healthcare: A systematic review. J. High Technol. Manag. Res. 2022, 34, 100442. [Google Scholar] [CrossRef]
- Shine, T.; Thomason, J.; Khan, I.; Maher, M.; Kurihara, K.; El-Hassan, O. Blockchain in Healthcare: 2023 Predictions from Around the Globe. Blockchain Healthc. Today 2023, 6, 10–30953. [Google Scholar] [CrossRef] [PubMed] [PubMed Central]
- Kormiltsyn, A.; Udokwu, C.; Dwivedi, V.; Norta, A.; Nisar, S. Privacy-Conflict Resolution for Integrating Personal- and Electronic Health Records in Blockchain-Based Systems. Blockchain Healthc. Today 2023, 6, 10–30953. [Google Scholar] [CrossRef] [PubMed]
- Gai, K.; She, Y.; Zhu, L.; Choo, K.-K.R.; Wan, Z. A blockchain-based access control scheme for zero trust cross-organizational data sharing. ACM Trans. Internet Technol. 2023, 23, 38. [Google Scholar] [CrossRef]
- Marry, P.; Yenumula, K.; Katakam, A.; Bollepally, A.; Athaluri, A. Blockchain based Smart Healthcare System. In Proceedings of the 2023 International Conference on Sustainable Computing and Smart Systems (ICSCSS), Coimbatore, India, 14–16 June 2023; pp. 1480–1484. [Google Scholar] [CrossRef]
- Kasyapa, M.S.B.; Vanmathi, C. Blockchain integration in healthcare: A comprehensive investigation of use cases, performance issues, and mitigation strategies. Front. Digit. Health 2024, 6, 1359858. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).