Abstract
In the context of Industry 4.0, IoRT-aware BPs represent an attractive paradigm that aims to automate the classic business process (BP) using the internet of robotics things (IoRT). Nonetheless, the execution of these processes within the enterprises may be costly due to the consumed resources, recruitment cost, etc. To bridge these gaps, the business process outsourcing (BPO) strategy can be applied to outsource partially or totally a process to external service suppliers. Despite the various advantages of BPO, it is not a trivial task for enterprises to determine which part of the process should be outsourced and which environment would be selected to deploy it. This paper deals with the decision-making outsourcing of an IoRT-aware BP to the fog and/or cloud environments. The fog environment includes devices at the edge of the network which will ensure the latency requirements of some latency-sensitive applications. However, relying on cloud, the availability and computational requirements of applications can be met. Toward these objectives, we realized an in-depth analysis of the enterprise requirements, where we identified a set of relevant criteria that may impact the outsourcing decision. Then, we applied the method based on the removal effects of criteria (MEREC) to automatically generate the weights of the identified criteria. Using these weights, we performed the selection of the suitable execution environment by using the ELECTRE IS method. As an approach evaluation, we sought help from an expert to estimate the precision, recall, and F-score of our approach. The obtained results show that our approach is the most similar to the expert result, and it has acceptable values.
1. Introduction
In the last years, the world has seen a trend toward the incorporation of some emerging technologies, such as the IoT and robotics. In fact, this incorporation gives birth to the newest technology called the internet of robotic things (IoRT). The IoRT is defined as a cooperation between IoT and robotic technologies to increase the automation level. This technology has several advantages, noted as, for example, the machine-to-machine (M2M) communication. It managed to sweep several fields, such as the business process (BP). Thus, the business managers try to take advantage of the IoRT via its integration within the classic BP, which gives a new process generation called IoRT-aware business processes (IoRT-aware BPs) [1]. This integration will allow business managers to automate their process.
However, the IoRT-aware BPs need costly execution due to the high amount of data to be transferred in the network. Toward these issues, the enterprises attempt to apply a variety of process strategies and solutions. The outsourcing of the (BPs) called business process outsourcing (BPO) is one among the relevant existing strategies that aim to save cost, speed up production, and enhance the enterprise performance. This explains the increasing number of enterprises that have adopted the outsourcing strategy using different environments.
Among the externalized environments, the cloud is considered the most adopting one. According to the National Institute of standards and Technology (NIST) [2], the cloud is defined as a pay-as-you-go model that allows on-demand network access to a set of computing resources. It is characterized by its higher storage capacity and availability [3]. Moreover, it allows the enterprises to scale their services, which are gradually done, according to customer demand. Therefore, outsourcing processes to the cloud is a reasonable choice.
Despite its advantages, the cloud is not recommended for latency-sensitive applications, such as IoT applications (e.g., health care, smart home, and smart agriculture). This is due to the high latency added by network connections to data centers [4]. Toward this issue, fog computing emerged as a new paradigm to perform latency-sensitive applications. As defined by the OpenFog Consortium (OFC) (https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf, accessed on 5 May 2022), fog computing extends the cloud capabilities at the edge of the network. It includes devices, located in close proximity to the end devices, which are responsible for intermediate computation and storage between IoT and the cloud [5]. In the context of outsourcing IoRT-aware BPs, the fog provides interesting external service suppliers.
During the outsourcing of an IoRT-aware BP to the fog and/or cloud environments, the business experts must address several issues to correctly choose which parts of the processes are dedicated to be outsourcing and which adequate environment should be selected. This explains why the decision-makers within the enterprises spend about 80% of their time to decide on the suitability process parts that should be outsourced and its adequate environment [6]. Consequently, to make a properly outsourcing decision, the business experts must identify a set of criteria related to the outsourcing decision of each process part.
Our extensive literature exercise revealed that most of the existing approaches deal mainly with the decision-making of traditional BPs, such as [7,8,9,10,11,12,13]. Some recent works have addressed the decision-making of the BPs that embedded only the IoT technology (e.g., [14,15,16]). More research on the outsourcing of IoRT-aware BPs, on the other hand, is required. In addition, most existing approaches use the task as a unit to make their decision, which takes more time. Additionally, the literature review shows that most current approaches use fuzzy as an MCDM method, even though their results could be better because the fuzzy method relies heavily on inaccurate inputs. Based on the studied works, we note that in most cases, the approaches do not consider methods to generate the feature weights. In fact, the automatic generation weights allow the experts and decision-makers to increase the robustness of their MCDM method results following an automatic, logical, and systematic weight calculation. Furthermore, most outsourcing solutions consider the cloud environment to externalize business activities. However, few of them propose outsourcing the process to the fog environment despite its relevance.
Therefore, to close these gaps, we propose a decision-making approach for the BPs that integrates both IoT and robots in addition to classic BPs. In our approach, we consider fog and cloud environments to take advantage of their benefits, especially for the processes that are sensitive to latency. During this work, we looked at the main parts of BPO and came up with a list of criteria that must be looked at when an IoRT-aware BP is outsourced. This identification takes into account process, fog, and cloud requirements. Furthermore, we use single entry single exit (SESE) (https://eprints.qut.edu.au/70726/7/70726.pdf, accessed on 7 May 2022), rather than the task, to accelerate the outsourcing decision. Moreover, we applied the method based on the removal effects of criteria (MEREC) to automatically generate the identified criteria weights. ELECTRE IS uses the generated weights to select the adequate environment for the process outsourcing goal.
The remainder of the paper is organized as follows: Section 2 depicts the related work. Section 3 details our approach. The implementation, assessment, and result of the proposed approach are illustrated in Section 4. Section 5 targets the validation and robustness of our proposal. Finally, Section 6 summarizes our work and highlights its future directions.
2. Related Work
In the BP context, the outsourcing of a process allows business managers to enhance the performance of their enterprises, speed, and reduce production costs. Consequently, several researchers seek to outsource the process to external suppliers. We intend, in this section, to overview some of the existing approaches that deal with the process outsourcing.
To perform the review of the existing approaches, we considered a set of relevant criteria, as they are detailed in what follows:
- Business type: Presents the type of the outsourced BP. This criterion lets us distinguish the most considered process type that is used in the outsourcing operation. A process can be a classic BP or a process that is automated via the embedding of one or more technologies, such as IoT, robots, and so forth.
- MCDM method: Designates the multi-criteria decision-making method used to achieve the process-outsourcing decision. This criterion allows us to identify the most considered method to accomplish the process-outsourcing goal.
- Granularity: Gives the processing granularity (unit) that is considered during the process outsourcing. Indeed, it can be a task, a SESE (sub-process), and so forth. The task presents the smallest unit that can be taken into account during the process of outsourcing, while the SESE presents a set of tasks.
- Externalized environment: Refers to external suppliers that are used to execute such process task/SESE fragments to allow the enterprises to gain in productivity, costs, and performance. We are interested in this work in the cloud environment that is characterized by its storage capacity and availability. Moreover, the fog environment provides relevant capabilities to execute latency-sensitive applications.
- Weight method: A MCDM aims, generally, to evaluate a set of alternatives regarding a set of criteria. This evaluation is based on weights which allow the decision-makers to express their preference in terms of the importance of criteria. This criterion refers to the methods that are used to generate the weight used for the MCDM methods.
- Used properties: Presents a set of properties that are considered to achieve the process outsourcing decision. In this work, we realized an in-depth overview of the literature to identify the most considered proprieties for the outsourcing of a BP. Therefore, we distinguished the cost, security, availability, and latency proprieties. Indeed, the cost presents an ascertainment of the cost savings of the business managers. Security is among the most prominent proprieties that may prohibit enterprises from outsourcing to an external provider. This is caused by the fact that the supplier’s service has to control outsourced activities, particularly those that deal with customers’ personal information [6]. The availability propriety designates the time for which the task/SESE needs to be executed. However, latency is among the considered proprieties that correspond to the needed time to transfer data from the source to the external environment execution via the network.
Table 1 and Table 2 classify some of the surveyed works that deal with the process outsourcing, according to the different identified criteria.

Table 1.
Comparison of the studied approaches based on a set of criteria (Part 1).

Table 2.
Comparison of the studied approaches based on a set of criteria (Part 2).
Back to Table 1, we note that most of the studied approaches deal with the outsourcing of the classic BP. Nonetheless, new paradigms, such as IoT and robots, seem to be relevant for automating the BP via the elimination of human intervention. For example, Refs. [14,15] propose an architecture to support the outsourcing of the IoT-aware BP. Furthermore, we notice, from Table 1, that several of the studied approaches [7,8,9,13,18,20,21] are limited to the cloud environment to ensure the outsourcing of the process. However, the cloud is not recommended for latency-sensitive applications, such as IoT applications (e.g., health care, smart home, and smart agriculture). This is due to the high latency added by network connections to data centers [4]. We also notice that there is a lack of approaches that deal with the MCDM methods, despite their ability to decide on a set of alternatives according to a set of criteria. Moreover, we notice from this table that in most cases, the approaches that deal with the MCDM methods [9,15,16] do not take into account the weight generation method to automatically generate weights.
Back to Table 2, we note that most of the existing approaches (e.g., [7,8,9,21]) outsource the BP at the task level. However, in [20], the authors target the process outsourcing via the outsourcing of a set of sub-process (SESE) fragments rather than a task. Indeed, outsourcing the BP based on its sub-processes fragments allows, on one hand, to accelerate the outsourcing operation, and on the other hand, it allows to save the process workflow between tasks.
In summary, we denote from this comparison that the studied approaches deal mainly with the outsourcing of the classic BPs. Among these approaches, there are those that are limited to the cloud environment for outsourcing BPs. Moreover, applying the outsourcing in the smallest unit, which is the task, may be costly for the outsourcing operation and it cannot preserve as much of the process workflow between tasks. Furthermore, several of the studied approaches do not consider the MCDM during the process outsourcing decision, despite its ability to evaluate a set of alternatives regarding a set of criteria. The MCDM process can support decision-making by helping to structure the problem and offering all involved actors a common language for discussing and learning about the problem [27]. It has also the potential to enhance transparency and the analytic rigor of decisions regarding other optimization methods. Otherwise, the approaches that deal with the outsourcing of the BP using the MCDM techniques do not consider methods for the automatic generation of weights for the used criteria. Indeed, the weights allow the decision-makers to express their preference in terms of the importance of criteria during the evaluation of a set of alternatives.
To close the gaps mentioned above, we propose a decision-making approach for outsourcing the IoRT-aware business process divided into a set of SESE fragments. The SESE deals with a closed block that groups one or more tasks, and it is characterized by its properties, inputs, and outputs. It guarantees the speed of the outsourcing operation and allows the business managers to preserve the process workflow within the process as much as possible. Furthermore, we seek to benefit from the fog and cloud environments to outsource these fragments if they are sensitive to latency or require high computing capacity. During our proposal, we chose ELECTRE IS as a MCDM method to achieve our goal. It is one of the widespread MCDM selection methods characterized by its ability to manage the heterogeneity of types of criteria (e.g., cost and latency). Moreover, our approach is based on the automation of the values of the weights using the MEREC method, which shows its ability, reliability, and relative effectiveness.
3. Outsourcing of IoRT-Aware Business Process
In this section, we start with the identification of a set of criteria that are useful for making the right outsourcing decision. After that, we present the used environment to accomplish the outsourcing goal. Finally, we detail the used method for the proposed outsourcing approach.
3.1. Outsourcing Criteria
Our approach allows the outsourcing of some parts of the IoRT-aware BP, either to fog and/or cloud environments as an external supplier. To decompose the process to a set of parts (sub-processes), we applied the RPST (refined process structure tree) method that divides a process to a set of fragments named single entry single exit (SESE) fragments, preserving as far as possible the workflows of the BP. To properly outsource the SESE fragments, it is useful to specify their requirements that are considered input for the outsourcing decision. In this setting, we identified a set of criteria that seem to be relevant for the BP outsourcing for both fog and cloud. In what follows, we detailed these criteria.
3.1.1. Cost
Saving cost is among the attractive factors that encouraged the enterprises to outsource their process to external providers. In [6], the authors argued that process outsourcing is guided mainly by overhead costs, where the processes are selected by ascertaining how much money they may save. In this setting, we aim to consider the cost of the SESE fragments that relies on the estimation of process task cost (see Equation (4)). This latter is calculated according to its execution cost (), storage cost (), and transfer cost () (see Equations (1)–(3)). Equation (7) estimates the cost of a SESE, which is expressed on percentage. The represents the business manager’s expected cost for a SESE. Indeed, presents the cost of SESE tasks that are inserted on a sequence, parallel (AND), and inclusive (OR) patterns (see Equation (5)). In fact, a sequence pattern shows the order of flow elements within the process where each element has one input and one output (https://www.omg.org/spec/BPMN/2.0/PDF, accessed on 13 June 2022). The parallel pattern is used to synchronize and create parallel flows within a process. However, the inclusive pattern presents both parallel and alternative paths within the process. These patterns directly influence the process cost estimation, where we suggest, in our proposal, to additionally calculate how much those patterns tasks cost. However, gives the cost of SESE tasks that are inserted on an exclusive (XOR) pattern. This pattern presents alternative paths within a process flow. For this pattern kind, we consider the minimum cost to estimate the SESE cost (see Equation (6)).
3.1.2. Security
Implies the security level which is required for a SESE to accomplish its execution. According to [6], security is among the most prominent criteria that may prohibit enterprises from outsourcing to an external provider. This is caused by the fact that the supplier’s service has to control outsourced activities, particularly those that deal with customers’ personal information. To identify the threats, we used the Cloud Security Alliance (CSA) that allows the identification of the critical security cloud threats. These threats may also concern the fog environment. To estimate the security value of a SESE fragment, we start first at the estimation of the security value for a process task (see Equation (10)) that is calculated according to the number of the environment protection and the number of the threats that exist (see Equations (8) and (9)). Based on the of tasks values that constitute a SESE, we proposed Equation (11) to estimate the SESE security value , which is expressed in percentage.
3.1.3. Availability
Relying on the time for which IoRT-aware BP tasks need to be executed (i.e, ) and the that implies the execution of a task. Several tasks require being available for a long period, which promotes its outsourcing to an environment that ensures a higher availability value, such as the cloud. Toward the estimation of the availability value for a SESE fragment, we start by the estimation of the task availability value using its and (see Equation (12)). Then, we proposed Equation (13) to achieve the availability value for a SESE .
3.1.4. Latency
Latency corresponds to the needed time to transfer data from the source to the external environment execution, via the network. It is worthy to consider the latency as one among the IoRT-aware BP outsourcing criteria since this process is constituted by the IoT and robotic technologies that are sensitive to latency. In this work, we performed a thorough literature study, where we noticed that the latency of a task is calculated using its size and the bandwidth value (see Equation (14)). However, to estimate the latency value for a SESE , we propose Equation (17). It is based, on one hand, on the latency value for the SESE tasks that are inserted on a sequence, AND, and OR patterns (see Equation (15)), and on the other hand, on the latency value of the tasks that are inserted on a XOR pattern (see Equation (16)).
3.2. Characteristics of Fog and Cloud Environments
To make an appropriate decision for the outsourcing of the IoRT-aware BP, there is a need for an in-depth analysis of fog and cloud environment characteristics. In this setting, we carried out a thorough study in the literature to determine the main features of these environments with respect to the identified criteria. According to [5], we note that the cloud environment is characterized by its highest availability thanks to its data centers. In addition, it has a low-security level and high latency due to the far distance between the end-user devices. The higher latency value can increase the transfer cost which increases the cost. The fog has a high-security level with the lowest latency value, thanks to its proximity to the end-user devices compared to the cloud. Hence, the lowest latency makes the process cost less expensive. We also noticed, in our study, that the fog has low availability value due to its dynamicity. Nonetheless, the duality of the fog and cloud environments has medium security, availability, latency, and cost values. Moreover, it is necessary to note that during the outsourcing of an IoRT-aware BP, the business managers may choose to keep the core of their process without outsourcing if the process tasks require a higher security level.
3.3. Outsourcing Decision-Making
We presented in an earlier sub-section, the main criteria for the outsourcing of the IoRT-aware BP to the fog and/or cloud environments, which are considered an input of our outsourcing decision-making approach. We present in this sub-section the adopted method to generate weights for the used criteria and for the outsourcing of decision-dmaking.
3.3.1. Automatic Generation of Weights
Multi-criteria decision-making (MCDM) is a branch of operations research (OR) that aims, generally, to evaluate a set of alternatives regarding a set of criteria. This evaluation is based on weights which allow the decision-makers to express their preference in terms of the importance of criteria. During our proposal, we aim to avail from the MCDM methods to propose a decision-making approach for the outsourcing of an IoRT-aware BP to the fog and/or cloud environments. In this setting, we use the method based on the removal effects of criteria (MEREC) to generate the weights of our identified criteria [28]. This method helps the experts and decision-makers to raise the robustness of their MCDM method results following an automatic, logical, and methodical weights calculation [28]. In addition, MEREC shows its stability, reliability, and relative effectiveness in differentiating criteria weights compared to other weight-calculation methods, such as CRITIC (criteria importance through inter-criteria correlation) [28].
3.3.2. Multi Criteria Decision Method
Our approach aims to select for each SESE the suitable execution environment. In this setting, we avail from the ELECTRE IS method to achieve our goal. It is among the widespread MCDM selection method which is characterized by its ability to manage the heterogeneity type of criteria (e.g., cost and latency) [29]. It is qualified by its ability to scale the criteria heterogeneity, where it does not require data normalization [29]. Moreover, among the attractive benefits of the ELECTRE IS, we cite its introduced thresholds, which are respectively the indifference threshold (Q), preference threshold (P), and veto threshold (V) that aim to improve the selection results regarding other selection methods. These thresholds respect the condition presented in Equation (18).
ELECTRE IS is based on the concordance C between alternatives (see Equation (19)), where k presents the sum of the criteria weights and c presents the local concordance index for a criterion.
4. Implementation, Experimentation and Results
In this section, we intend to implement and experiment with the proposed IoRT-aware BP outsourcing decision-making method. During the implementation of our approach, we used the Java environment to develop both the MEREC and ELECTRE IS methods. However, during the experimentation of our proposal, we used an IoRT-aware BP on the agriculture field that we developed under the eclipse modeling framework (EMF) using the BPMN 2.0 modeler plug-in which is an open-source eclipse editor [30]. In what follows, we detail our decision-making approach implementation. Afterward, we present the proposed experimentation.
4.1. Implementation
During the implementation of our decision-making approach, we start with the weights generation using the MEREC method. The MEREC method is based, initially, on a decision matrix that shows the scores of each execution environment (alternative) regarding the identified property as presented in Table 3. For the cost, security, and availability properties, we use 1, 0.8, 0.5, and 0.1 to express respectively the very high, high, medium, and low scores. Nonetheless, for the latency property, we use 1, 0.5, 0.2, and 0.1 to designate, respectively, high, medium, low, and not applied scores. To achieve the MEREC implementation goal, we used the eclipse tool, which is an open-source software development project. This implementation gives 0.22 as a weight value for the cost property, 0.22 for the security property weight. As well, we obtain 0.22 and 0.34 as weight values, respectively, for availability and latency properties (see Figure 1).

Table 3.
Proposed decision matrix for MEREC method.
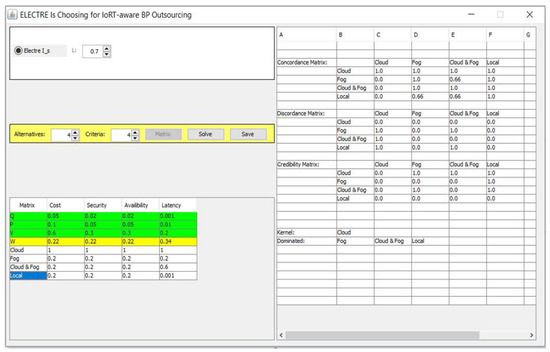
Figure 1.
IoRT-aware BP outsourcing interface using ELECTRE IS.
To select the suitable environment execution for a SESE that has its specific cost, security, availability, and latency values, we implemented an interface that is depicted in Figure 1 using the eclipse tool. This interface allows the users to express the SESE requirements in the intention to select its adopted environment execution.
4.2. Experimentation and Results
To better test our approach functionality, we conducted two experiments applied to an IoRT-aware BP in the agriculture field (see Figure 2). The used process presents an example of an IoRT-aware BP of a smart irrigation management system that intends to boost nutrient and water-use efficiency. Indeed, the process starts with the capture of temperature and soil moisture values using two sensors: capture temperature, and capture soil moisture. The captured values are stored using storage temperature value, and storage soil moisture value. Afterward, irrigation and grep decision-making is made through make irrigation and grep decision. In this setting, the process was finished either if there is no need for irrigation; otherwise, an irrigation request is launched called request launch irrigation, which activates an actuator to start the irrigation launch irrigation. Simultaneously, request picking weeds is launched, where it activates the robot to start the picking of weeds with launch picking weeds.
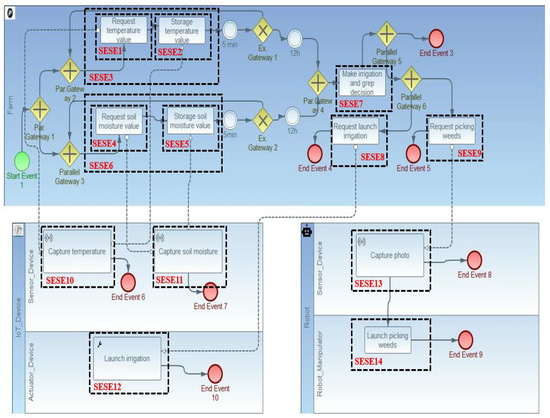
Figure 2.
IoRT-aware business process on agriculture field composed by 14 SESE fragments.
Using the RPST technique, we divided the process into a set of SESE fragments, where each SESE has its own requirements in terms of cost, availability, security, and latency.
During our work, we dealt with the process presented in Figure 2, where we used it in two different scenarios that have their specific SESE property values. The first one is based on the property values that are presented in Table 4, whereas the second is based on the SESE property values detailed in Table 5. In addition, these tables give an expert outsourcing result for each SESE. The expert has high expertise that allows it to assess the outsourcing of the SESE according to its cost, security, availability, and latency values.

Table 4.
Expert results for the outsourcing of each SESE according to cost, security, availability, and latency values for the first IoRT-aware BP scenario.

Table 5.
Expert results for the outsourcing of each SESE according to cost, security, availability, and latency values for the second IoRT-aware BP scenario.
4.2.1. Experimentation 1
Our first experimentation aims to compare the effectiveness of our proposed approach regarding other selecting methods. To achieve this end, we chose to compare our method regarding ELECTRE I, ELECTRE Iv, and PROMETHEE I. ELECTRE I, applied only on numerical properties. ELECTRE Iv is presented as an improvement of ELECTRE I by adding the Veto threshold [29]. However, PROMETHEE I is based exclusively on a concordance analysis [29]. During this experimentation, we involved an expert to compare the correspondence between the approach’s results and the expert one. In this setting, we used the Jaccard measure [31], which is calculated using Equation (20).
Figure 3 displays the comparison result of our proposed method regarding other selection methods, based on the property values that are presented in Table 4. We denote from this figure that our proposed method has the closest result to the expert one, regarding ELECTRE I, ELECTRE Iv, and PROMETHEE I methods. In other words, the result generated by our method is the most similar to the expert result. This is explained, on one hand, by the use of indifference, preference, and veto thresholds that aim to improve the selection results. On other hand, our proposed approach is based on the use of an automatically generated weight method. Indeed, the use of the MEREC method to generate the properties’ weight raises the robustness of our proposed method to generate correct results.
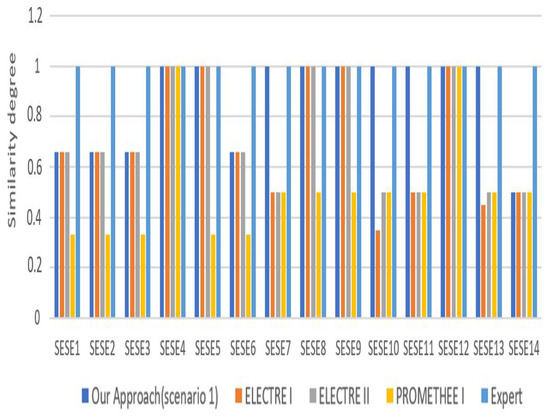
Figure 3.
Distance of our approach result compared to other approaches results and expert one (scenario 1).
Nonetheless, Figure 4 displays the comparison result of our proposed approach regarding other selection methods, based on the property values that are presented in Table 5, we notice from this figure that our approach gives the closest result to the expert one rather than the other ELECTRE I, ELECTRE Iv, and PROMETHEE I methods. Therefore, this result boosts the fact of the used thresholds and the MEREC method.
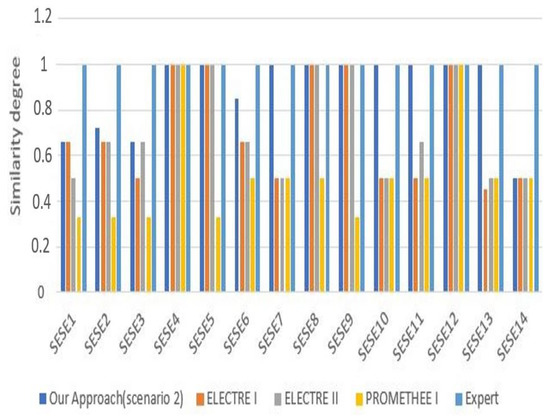
Figure 4.
Distance of our approach result compared to other approaches’ and expert results (Case 2).
4.2.2. Experimentation 2
During the second evaluation, we intend to compare the results of our approach based on MEREC weights with the use of some other weight values (see Table 6). More precisely, we intend, in this experimentation, to compare our approach based on the MEREC method regarding weight values presented in cases 1, 2, and 3 ( see Table 6), where each case specifies the values of the weights for the used criteria. This comparison is based on the estimation of precision, recall, and F-score values of the first scenario (see Figure 5) and the second one (see Figure 6).

Table 6.
Cost, security, availability, and latency weight values.
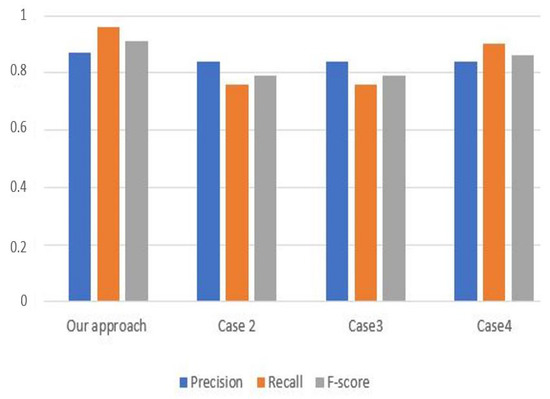
Figure 5.
Precision, Recall, and F-score estimation metrics based on criteria values of Table 4.
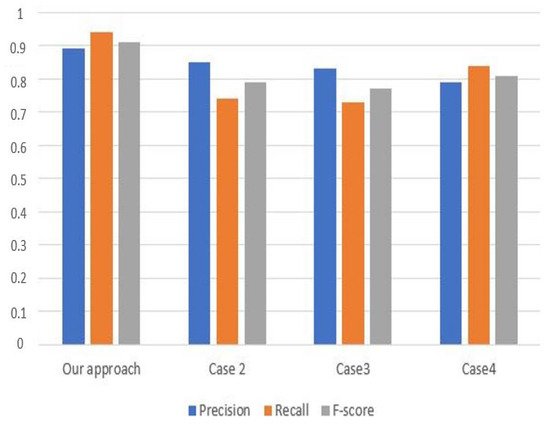
Figure 6.
Precision, Recall, and F-score estimation metrics based on property values of Table 5.
Figure 5 illustrates the estimation of the precision, recall, and F-score values of our approach for the first scenario. During this scenario, we notice that the precision of our approach reaches 0.87%, and the recall is equal to 0.96%, while the F-score estimates 0.91%. However, in the second scenario (see Figure 6), our approach reaches 0.89%, 0.94%, and 0.91% as the precision, recall, and F-score values, respectively.
We denote from Figure 5 and Figure 6 that our approach based on the MEREC method has the highest precision and recall values for both scenarios. Therefore, these figures show the reliability and the relative effectiveness of our approach in differentiating properties compared to other weight values.
5. Validation and Robustness
This section is dedicated to appreciating the validation and robustness of the proposed IoRT-aware BP outsourcing approach based on the ELECTRE IS method. Therefore, to perform this goal, we choose to compare our approach regarding the outsourcing method published in [16]. In their proposal, the authors took into account a set of six criteria, which are frequency, sensitivity, freshness, time, volume, and criticality, to perform the outsourcing of a goal of a thing to the fog and cloud (see Table 7). The frequency criterion refers to the data transfer rate from the thing to fog/cloud nodes, while the sensitivity refers to the nature of data exchanged between things and fog/cloud nodes. The freshness means how important data exchanged between things and fog/cloud nodes should be recent. The time criterion represents the latency delay that results from processing data at the thing until they are transferred to fog/cloud nodes. The volume criterion refers to the amount of data that tasks produce and outsource to fog/cloud nodes. However, the criticality criterion implies how important data tasks are concerning fog/cloud nodes’ demands. In summary, the considered criteria focus on the data outsourcing from the thing to the fog and/or cloud nodes concerning different aspects (e.g., location, time, and application needs).

Table 7.
Data-recipient selection criteria and interaction forms (HR: highly recommended, R: recommended, NR: not recommended, NA: not applicable) [16].
During their proposal, the authors adopted fuzzy logic as one of the MCDM techniques to select the adequate data recipient (e.g., fog only, cloud only, and fog/cloud). The authors justified their choice by the ability of fuzzy logic to handle the conflicting variables and the uncertainty degree of some criteria.
Throughout this section, we intend to compare the results of our approach based on the ELECTRE IS method to the proposal in [16]. Therefore, we applied their approach to the agriculture scenario presented above (see Figure 2), which constitutes a set of tasks. Based on their proposal, the result of the outsourcing is illustrated in Table 8. The table shows a mismatch between an expert’s expected results and the obtained ones in most cases. For instance, the task 10 approach, which has a regular stream with short gap frequency, very high sensitivity, low freshness, and real-time streaming with a very low volume and criticality, gives fog and fog/cloud as a result. At the same time, the expert estimates to keep this task locally.

Table 8.
Comparison between expert’s expected results and the obtained ones for the outsourcing of an IoRT-aware BP using the approach in [16].
To perform the comparison goal, we estimated the precision, recall, and F-score values using the details presented in Table 8 and the IoRT-aware BP scenario details presented in Table 4. The precision is the percentage of correctly classified predictive positive task samples. The recall refers to the rate of positive task samples that are correctly classified, while the F-score presents a measure that combines precision and recall [32].
During this evaluation, we notice that the precision value reaches 0.75%, and the recall is equal to 0.51%, while the F-score estimates 0.60% (see Table 9). Therefore, we deduce from this comparison that our proposal is more robust and relatively effective compared to their approach. The precision value of our approach reaches 0.87%, the recall is estimated to be 0.96%, and the F-score is equal to 0.91% (see Figure 5). The disparity obtained at the precision, recall, and F-score values can be explained by the set of the considered criteria for each approach, where the approach published in [16], focused on the data exchange and did not consider the cost and security requirements of fog/cloud nodes.

Table 9.
Precision, recall, and F-score estimated values for the tasks of the first IoRT-aware BP scenario using the approach in [16].
On the other hand, we are aware that our proposal has some flaws that should be fixed in future work. Our proposal needs to consider the human side involved in the administration and commitment processes. Each business depends mainly on the knowledge of its staff. Its employees’ capacity to meet its needs and accomplish its strategic goals determines whether the company succeeds or fails. Moreover, our proposed outsourcing approach is limited to design time execution. However, a business process is likely to be modified at runtime due to the dynamicity of IoT and robot devices. Therefore, it seems to be relevant to consider the scheduling of the process outsourcing. Indeed, the scheduling consists of planning the process outsourcing to allow the business managers to achieve their goals whenever the fog/cloud is available.
6. Conclusions
The outsourcing of an IoRT-aware BP to the fog and/or cloud environments presents several advantages to the enterprises, as it allows them to save their cost, and focus on their core competence. It consists of deploying partially or totally the process in an external execution environment. Despite these advantages, the outsourcing of an IoRT-aware BP is not a trivial task. Therefore, there is a crucial need in the decision-making outsourcing to determine which part of the process should be outsourced and which environment would be selected to deploy it. Toward these objectives, we identified in this paper a set of criteria for the IoRT-aware BP outsourcing in fog and/or cloud environments. In addition, we used the ELECTRE IS method based on the MEREC method for the weight generation to select the suitable environment for each SESE.
We also aim to propose a framework to take into account the human side involved in the administration and commitment process for the outsourcing decision of a BP. Moreover, we seek, in the future, to enhance our proposal by scheduling the process outsourcing to consider the dynamic changes of the IoT and/or robot devices, thereby allowing the business managers to achieve their goals in time.
Author Contributions
Conceptualization, N.F., I.B.L., M.R. and K.B.; methodology, N.F., I.B.L., M.R. and K.B.; software, N.F., I.B.L., M.R. and K.B.; validation, N.F., I.B.L., M.R. and K.B.; formal analysis, N.F., I.B.L., M.R. and K.B.; investigation, N.F., I.B.L., M.R. and K.B.; resources, N.F., I.B.L., M.R. and K.B.; data curation, N.F., I.B.L., M.R. and K.B.; writing—original draft preparation, N.F., I.B.L., M.R. and K.B.; writing—review and editing, N.F., I.B.L., M.R. and K.B.; visualization, N.F., I.B.L., M.R. and K.B.; supervision, K.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research has no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Fattouch, N.; Ben Lahmar, I.; Boukadi, K. A comprehensive architecture for an IoRT-aware Business Process outsourcing into Fog and Cloud computing. In Proceedings of the Tunisian-Algerian Joint Conference on Applied Computing (TACC), Tabarka, Tunisia, 18–20 December 2021; pp. 164–172. [Google Scholar]
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing. 2011. Available online: https://csrc.nist.gov/publications/detail/sp/800-145/final (accessed on 1 October 2022).
- Abdulqadir, H.R.; Zeebaree, S.R.; Shukur, H.M.; Sadeeq, M.M.; Salim, B.W.; Salih, A.A.; Kak, S.F. A study of moving from cloud computing to fog computing. Qubahan Acad. J. 2021, 1, 60–70. [Google Scholar] [CrossRef]
- Lahmar, I.B.; Boukadi, K. Resource Allocation in Fog Computing: A Systematic Mapping Study. In Proceedings of the 2020 Fifth International Conference on Fog and Mobile Edge Computing (FMEC), Paris, France, 20–23 April 2020; pp. 86–93. [Google Scholar]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Govindan, K.; Agarwal, V.; Darbari, J.D.; Jha, P. An integrated decision making model for the selection of sustainable forward and reverse logistic providers. Ann. Oper. Res. 2019, 273, 607–650. [Google Scholar] [CrossRef]
- Boukadi, K.; Grati, R.; Rekik, M.; Ben-Abdallah, H. Business process outsourcing to cloud containers: How to find the optimal deployment? Future Gener. Comput. Syst. 2019, 97, 397–408. [Google Scholar] [CrossRef]
- Ben Halima, R.; Kallel, S.; Ahmed Nacer, M.; Gaaloul, W. Optimal business process deployment cost in cloud resources. J. Supercomput. 2021, 77, 1579–1611. [Google Scholar] [CrossRef]
- Zarour, K.; Benmerzoug, D. A decision-making support for business process outsourcing to a multi-cloud environment. Int. J. Decis. Support Syst. Technol. (IJDSST) 2019, 11, 66–92. [Google Scholar] [CrossRef]
- Suresh, S.; Ravichandran, T. Value gains in business process outsourcing: The vendor perspective. Inf. Syst. Front. 2022, 24, 677–690. [Google Scholar] [CrossRef]
- Shi, Z.; Liu, S.; Wu, R. Incentive design with customer satisfaction for business process outsourcing: Multi-task vs. multi-agent. RAIRO-Oper. Res. 2021, 55, S401–S434. [Google Scholar] [CrossRef]
- Gaaloul, W.; Zhou, Z.; Panetto, H.; Zhang, L. Special issue on fog and cloud computing for cooperative information system management. Future Gener. Comput. Syst. 2020, 109, 704–705. [Google Scholar] [CrossRef]
- Asatiani, A.; Apte, U.; Penttinen, E.; Rönkkö, M.; Saarinen, T. Impact of accounting process characteristics on accounting outsourcing-Comparison of users and non-users of cloud-based accounting information systems. Int. J. Account. Inf. Syst. 2019, 34, 100419. [Google Scholar] [CrossRef]
- Kallel, A.; Rekik, M.; Khemakhem, M. IoT-fog-cloud based architecture for smart systems: Prototypes of autism and COVID-19 monitoring systems. Softw. Pract. Exp. 2021, 51, 91–116. [Google Scholar] [CrossRef]
- Stavrinides, G.L.; Karatza, H.D. A hybrid approach to scheduling real-time IoT workflows in fog and cloud environments. Multimed. Tools Appl. 2019, 78, 24639–24655. [Google Scholar] [CrossRef]
- Yahya, F.; Maamar, Z.; Boukadi, K. A multi-criteria decision making approach for cloud-fog coordination. In Advanced Information Networking and Applications, Proceedings of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020; Springer: Cham, Switzerland, 2020; pp. 1150–1161. [Google Scholar]
- Ge, L.; Wang, X.; Yang, Z. The strategic choice of contract types in business process outsourcing. Bus. Process. Manag. J. 2021, 27, 1569–1589. [Google Scholar] [CrossRef]
- Wakrime, A.A.; Boubaker, S.; Kallel, S.; Guermazi, E.; Gaaloul, W. A Formal Model for Configurable Business Process with Optimal Cloud Resource Allocation. J. Univ. Comput. Sci. 2021, 27, 693–713. [Google Scholar] [CrossRef]
- Halima, R.B.; Kallel, S.; Gaaloul, W.; Maamar, Z.; Jmaiel, M. Toward a correct and optimal time-aware cloud resource allocation to business processes. Future Gener. Comput. Syst. 2020, 112, 751–766. [Google Scholar] [CrossRef]
- Rekik, M.; Fourati, M.; Boukadi, K. Business process implementation through SaaS services composition. In Proceedings of the Tunisian Algerian Conference on Applied Computing (TACC 2021), Tabarka, Tunisia, 18–20 December 2021; pp. 37–48. [Google Scholar]
- Hadded, L.; Hamrouni, T. Optimal autonomic management of service-based business processes in the cloud. Soft Comput. 2022, 26, 7279–7291. [Google Scholar] [CrossRef]
- Jana, C.; Pal, M. A dynamical hybrid method to design decision making process based on GRA approach for multiple attributes problem. Eng. Appl. Artif. Intell. 2021, 100, 104203. [Google Scholar] [CrossRef]
- Jana, C.; Muhiuddin, G.; Pal, M.; Al-Kadi, D. Intuitionistic fuzzy dombi hybrid decision-making method and their applications to enterprise financial performance evaluation. Math. Probl. Eng. 2021, 2021, 3218133. [Google Scholar] [CrossRef]
- Jana, C.; Pal, M.; Wang, J. A robust aggregation operator for multi-criteria decision-making method with bipolar fuzzy soft environment. Iran. J. Fuzzy Syst. 2019, 16, 1–16. [Google Scholar]
- Jana, C.; Garg, H.; Pal, M. Multi-attribute decision making for power Dombi operators under Pythagorean fuzzy information with MABAC method. J. Ambient. Intell. Humaniz. Comput. 2022, 1–18. [Google Scholar] [CrossRef]
- Jana, C.; Pal, M. Assessment of enterprise performance based on picture fuzzy Hamacher aggregation operators. Symmetry 2019, 11, 75. [Google Scholar] [CrossRef]
- Köhler, B.; Ruud, A.; Aas, Ø.; Barton, D.N. Decision making for sustainable natural resource management under political constraints—The case of revising hydropower licenses in Norwegian watercourses. Civ. Eng. Environ. Syst. 2019, 36, 17–31. [Google Scholar] [CrossRef]
- Keshavarz-Ghorabaee, M.; Amiri, M.; Zavadskas, E.K.; Turskis, Z.; Antucheviciene, J. Determination of objective weights using a new method based on the removal effects of criteria (MEREC). Symmetry 2021, 13, 525. [Google Scholar] [CrossRef]
- Sałabun, W.; Wątróbski, J.; Shekhovtsov, A. Are mcda methods benchmarkable? a comparative study of topsis, vikor, copras, and promethee ii methods. Symmetry 2020, 12, 1549. [Google Scholar] [CrossRef]
- Fattouch, N.; Lahmar, I.B.; Boukadi, K. Towards a Meta-Modeling Approach for an IoRT-Aware Business Process. Commun. ECMS 2022, 36, 29–35. [Google Scholar]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and federated learning for privacy-preserved data sharing in industrial IoT. IEEE Trans. Ind. Inform. 2019, 16, 4177–4186. [Google Scholar] [CrossRef]
- Miao, J.; Zhu, W. Precision–recall curve (PRC) classification trees. Evol. Intell. 2022, 15, 1545–1569. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).