Abstract
Cybersecurity has evolved significantly over the years, with a growing interest in biologically inspired models that emulate the immune system’s defense mechanisms. This paper provides a comparative analysis of various immunity-based approaches in cybersecurity, tracking their progression from their inception to the present. It explores the strengths and limitations of these methods across different cybersecurity areas, such as intrusion detection, malware analysis, and network protection. By reviewing foundational research, recent advancements, and existing challenges, this study aims to offer a well-rounded perspective on the effectiveness and constraints of immunity-driven strategies in protecting modern digital infrastructure. Additionally, it highlights emerging trends and future directions, stressing the importance of integrating these approaches with machine learning and other advanced technologies to strengthen cybersecurity resilience.
1. Introduction
With the rapid evolution and increasing sophistication of cyberattacks, traditional cybersecurity technologies are facing growing challenges in keeping up with the advanced and constantly changing tactics used by malicious actors. Modern cyberthreats are no longer limited to traditional malware; they now encompass a wide range of complex and evolving threats, such as ransomware, Advanced Persistent Threats (APTs), phish- ing campaigns, and data exfiltration. These attacks, often orchestrated by well-funded cybercriminal organizations or state-sponsored actors, are designed to exploit even the slightest vulnerabilities in systems, software, or human behavior. The rise of new attack vectors, including cloud environments, mobile applications, and Internet of Things (IoT) devices, has expanded the potential entry points for attackers, further complicating the cybersecurity landscape.
The sophistication of these attacks makes them particularly challenging for traditional cybersecurity systems, which typically rely on predefined rules, signatures, or known threat patterns to detect intrusions. Signature-based systems are less effective in detecting novel threats or polymorphic attacks, where malware constantly changes its form to avoid detection. Similarly, zero-day vulnerabilities pose significant risks, as they can remain undetected for long periods, leaving systems exposed to attackers. As cybercriminals continue to innovate and develop new techniques to bypass security defenses, the limitations of these traditional systems are becoming increasingly apparent.
In response to these challenges, there is an urgent need for more adaptive, dynamic, and intelligent security solutions. Cybersecurity systems must evolve to become more proactive, capable of identifying and mitigating threats in real time, even before they manifest fully.
An area of great promise in this quest for dynamic security is the inspiration drawn from the biological immune system, which has evolved over millions of years to protect organisms from a wide range of pathogens. The immune system’s ability to recognize and remember harmful agents, adapt to new threats, and mount an appropriate defense offers valuable insights into how cybersecurity can be transformed. By leveraging concepts like self–non-self-discrimination, pattern recognition, and adaptive responses, cybersecurity models can become more resilient and self-healing.
This paper will explore the key immunological concepts that have shaped cybersecurity thinking over the years and analyze their role in modern security operations. We will trace the development of these concepts and examine their application across various domains, including intrusion detection, malware analysis, and threat hunting. By highlighting both the strengths and limitations of biologically inspired methods, we will provide a comprehensive view of their potential in combating contemporary cyber threats. Additionally, we will explore how integrating immunological approaches with cutting edge technologies, such as machine learning, can lead to more sophisticated and adaptive cybersecurity solutions, capable of keeping pace with the ever-evolving landscape of cyber threats.
2. Methodology
This paper presents a qualitative review of research efforts that draw inspiration from the biological immune system to address challenges in cybersecurity. The goal is to identify and analyze representative immunity-based approaches, highlighting their core principles, application domains, and contributions.
2.1. Paper Selection Strategy
The review covers the period from 1994 to 2025. Research papers were identified through a targeted literature search using scholarly databases such as IEEE Xplore and Google Scholar. The search used combinations of the following keywords: “artificial immune system”, “immunity-inspired model” with “cybersecurity” “anomaly detection” “intrusion detection”.
To maintain focus and clarity, the initial version of this review adopted a year-by-year approach, aiming to include one representative paper per year. Papers were selected based on the following criteria:
- Relevance to immunity-inspired cybersecurity
- Clarity in the biological mechanism used
- Originality of the proposed approach
- Impact within the field
It is important to note that not all years are represented in the final selection. Some years were intentionally excluded either due to a lack of new contributions or to avoid redundancy with previously selected work. The intent was not to achieve exhaustive coverage, but rather to illustrate the evolution and diversity of approaches within the field.
2.2. Analysis Framework
Each selected paper was analyzed through a qualitative framework structured around five key dimensions: the immunity inspiration underlying the approach (e.g., negative selection, clonal selection), the specific cybersecurity application domain (such as intrusion detection or malware analysis), the limitations of the proposed method, and the overall key insights and contributions. This consistent analytical structure ensured a uniform basis for comparison across the selected works.
The outcomes of this analysis are synthesized in Table 1, which presents a concise summary of the main characteristics and contributions of each reviewed paper. To capture broader patterns and recurring challenges, a complementary overview is provided in Table 2, which highlights common limitations, the papers affected, the underlying issues, and suggested future directions. This dual-tabular approach supports both a detailed understanding of individual contributions and a higher-level synthesis of emerging trends within the field of immunity-inspired cybersecurity.

Table 1.
Comparative Analysis of Immunity-Inspired Cybersecurity Approaches.

Table 2.
Limitations and Future Directions in Immunity-Inspired Cybersecurity.
3. Results
The findings from the identified research are summarized in Table 1, which presents a comparative analysis of various immunity-inspired approaches. This table outlines the titles, main biological concepts utilized, specific cybersecurity applications, and key insights or findings, illustrating the diverse ways in which biological principles have been adapted to address modern cybersecurity challenges.
4. Discussion
The analysis reveals a significant transformation in research focus over the years, from early theoretical discussions to more recent, practical approaches. The comparison highlights that older research on biologically inspired cybersecurity models was dominated by Self/Non-Self-Discrimination [12,15,17], while more recent work explores Danger Theory, adaptive models, immune reflex, and distributed approaches in federated learning and embedded systems [2,8,11]. Cybersecurity applications mainly focus on intrusion detection (IDS) [7,11] and malware detection [8], with newer studies expanding into broader resilience frameworks [3,9] and federated learning [2]. Early research (pre-2010) was largely theoretical, emphasizing biological-cyber parallels, whereas post-2010 studies implemented AIS models in simulations and experiments. The latest works (2020–2024) integrate AI-driven, privacy-preserving cybersecurity solutions.
Biologically inspired cybersecurity approaches have been applied to various areas such as intrusion detection, malware analysis, and network protection, each leveraging immune system principles to enhance system resilience. In intrusion detection, systems often utilize negative selection algorithms and multi-layered immune mechanisms to detect threats. Malware detection similarly employs immune concepts like immune memory and danger theory to recognize malicious behavior patterns and adapt defenses. Meanwhile, network protection benefits from decentralized, self-organizing immune models that can autonomously manage threats in complex infrastructures, including critical systems like power grids and embedded devices.
5. Limitations and Future Work
The proposition of a genuine advance in any scientific domain presupposes a clear and critical understanding of the limitations inherent in preceding efforts. This section outlines the key limitations identified in current research and proposes directions for future work aimed at overcoming these obstacles and enhancing the operational viability of immune-based cybersecurity systems.
As immunity-inspired cybersecurity approaches continue to evolve, it is essential to address the inherent limitations these strategies face in practical implementation. Figure 1 presents a proportional overview of key challenges identified in the current literature, including issues related to real-world deployment, computational efficiency, and adaptability to the rapidly changing threat landscape. Each limitation is accompanied by proposed future directions aimed at overcoming these obstacles.
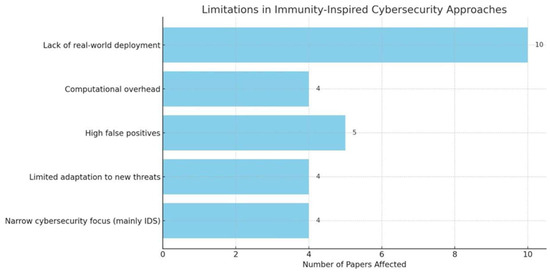
Figure 1.
Frequency of limitations across papers.
The bar chart shows that the biggest limitation lies in the lack of real-world deployment. This reflects a significant gap between experimental research and the practical application of immune-based systems in operational environments. Although these biologically inspired models demonstrate theoretical robustness, their limited adoption in live infrastructures raises concerns about their scalability, interoperability, and reliability under real-time conditions.
Other critical challenges—such as high false positive rates, limited adaptability to emerging threats, and computational overhead—further underscore the technical barriers that hinder the efficiency and responsiveness of these systems. While immune-inspired techniques offer adaptive potential, they often encounter performance degradation when exposed to dynamic threat environments, particularly when constrained by system resources. Additionally, the narrow scope of cybersecurity coverage suggests that many implementations are designed for specific threat types, limiting their generalizability across broader security domains.
Furthermore, computational overhead remains a significant concern, especially for resource-intensive algorithms such as negative selection. The high resource demands of these models constrain their feasibility in latency-sensitive environments, including cloud platforms and mission-critical applications, where performance and responsiveness are paramount.
These limitations emphasize the need for future research to address both theoretical and practical deficiencies in immunity-based cybersecurity. Priorities should include enhancing real-world applicability, optimizing resource efficiency, and expanding threat coverage to support broader and more scalable deployment.
To that end, fostering stronger collaboration between academic institutions and industry stakeholders is essential. Such partnerships can facilitate the co-development and validation of adaptive immune-based systems capable of functioning effectively in diverse, real-world conditions ranging from high-throughput enterprise networks to critical infrastructure systems.
In conclusion, while immunity-inspired cybersecurity presents a promising and innovative paradigm, realizing its full potential will require strategic efforts to bridge the gap between conceptual development and operational deployment. Addressing computational constraints and promoting interdisciplinary collaboration are pivotal to advancing these biologically inspired models into robust, efficient, and scalable security solutions.
6. Conclusions
Briefly, a comparison of biologically inspired cybersecurity approaches demonstrates a promising development in computer security as a significant departure from static, traditional defense measures to adaptive, dynamic systems inspired by biology. The findings from various studies show that these approaches using concepts of self–non-self-discrimination, adaptive responses, as well as danger theory illuminate new solutions for countering dynamic and sophisticated cyber-attacks.
But their existing limitations need to be understood such as limited applicability in practice, heavy computational cost, as well as limited application primarily focused on intrusion detection. Releasing the full potential of such biologically inspired techniques, however, rests on the upcoming studies being devoted to bringing practical, deployable solutions to the market that can be directly incorporated into existing cybersecurity measures. Both industry and academia must get to work to bridge the gap between theoretical models and practical applications. By surmounting challenges today and opening the doors for greater applicability of such methods, immunity-based cybersecurity has the potential to be at the forefront of securing digital systems from increasingly hostile cyberspace.
Author Contributions
Conceptualization, A.B. (Abir Bala); methodology, A.B. (Abir Bala), B.E.B. and A.B. (Ayoub Bahnasse); literaturesearch and screening, A.B. (Abir Bala); data extraction and analysis, A.B. (Abir Bala); validation, A.B. (Abir Bala), B.E.B. and A.B. (Ayoub Bahnasse);writing original draft preparation, A.B. (Abir Bala); writing review and editing, B.E.B., A.B. (Ayoub Bahnasse) and M.M.-E.; visualization, A.B. (Abir Bala); supervision, A.B. (Ayoub Bahnasse) and B.E.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article as all the data supporting the findings are available in the cited literature.
Conflicts of Interest
Abir Bala and Brahim El Bhiri were employed by the Harmony Technology. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Tallam, K. The Cyber Immune System: Harnessing Adversarial Forces for Security Resilience. arXiv 2025, arXiv:2502.17698. [Google Scholar] [CrossRef]
- Olarinde, M.O.; Abiona, A.A.; Ajinaja, M.O. Adaptive and privacy-preserving security for federated learning using biological immune system principles. Asian J. Comput. Sci. Technol. 2024, 13, 67–72. [Google Scholar] [CrossRef]
- Mustafa, H.M.; Sadanandan, S.K.; Srivastava, A.K.; Sarwari, A.R.; Reece, R. Building cyber-attack immunity in electric energy systems inspired by infectious disease ecology. IEEE Access 2024, 12, 175338–175356. [Google Scholar] [CrossRef]
- Schrom, E.; Kinzig, A.; Forrest, S.; Graham, A.L.; Levin, S.A.; Bergstrom, C.T.; Castillo-Chavez, C.; Collins, J.P.; De Boer, R.J.; Doupé, A.; et al. Challenges in cybersecurity: Lessons from biological defense systems. Math. Biosci. 2023, 362, 109024. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Z.; Li, T.; Hu, A. Research on endogenous security methods of embedded systems. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC), Chengdu, China, 11–14 December 2020. [Google Scholar]
- Forrest, S. Biology and Computers: Drawing Parallels Between Immunology and Cyber-Security. 2017. Available online: https://profsforrest.github.io/homepage/data/publications/2017-sc-article.pdf (accessed on 20 March 2025).
- Dutt, I.; Borah, S.; Maitra, I. Intrusion detection system using artificial immune system. Int. J. Comput. Appl. 2016, 144, 12. [Google Scholar] [CrossRef]
- Cossu, J.; ElAarag, H. Malware detection inspired by the human immune system and making use of honeytokens. In Proceedings of the Spring Simulation Multiconference, Alexandria, VA, USA, 12–15 April 2015; Available online: https://api.semanticscholar.org/CorpusID:10679031 (accessed on 4 January 2025).
- Stacey, B.C.; Bar-Yam, Y. Principles of security: Human, cyber, and biological. arXiv 2013, arXiv:1303.2682. [Google Scholar] [CrossRef]
- Biancaniello, P.; Holness, G.; Darvill, J.; Craven, M.J.; Lardieri, P.J. AIR: A Framework for Adaptive Immune Response for Cyber Defense. 2012. Available online: https://api.semanticscholar.org/CorpusID:14747952 (accessed on 13 February 2025).
- Greensmith, J.; Aickelin, U.; Twycross, J. Detecting danger: Applying a novel immunological concept to intrusion detection systems. arXiv 2010, arXiv:1002.0696. [Google Scholar] [CrossRef][Green Version]
- Ehret, C.; Ultes-Nitsche, U. Immune System-Based Intrusion Detection System. In Proceedings of the Information Security for South Africa, Johannesburg, South Africa, 7–9 July 2008; 2008. Available online: https://api.semanticscholar.org/CorpusID:364566 (accessed on 20 January 2025).
- Harmer, P.K.; Williams, P.D.; Gunsch, G.H.; Lamont, G.B. An artificial immune system architecture for computer security applications. IEEE Trans. Evol. Comput. 2002, 6, 252–280. [Google Scholar] [CrossRef]
- Kim, J.; Bentley, P.J. The Human Immune System and Network Intrusion Detection. 1999. Available online: https://api.semanticscholar.org/CorpusID:10912100 (accessed on 18 February 2025).
- Hofmeyr, S.A.; Forrest, S. Immunity by Design: An Artificial Immune System. 1999. Available online: https://api.semanticscholar.org/CorpusID:6215531 (accessed on 23 March 2025).
- Forresty, S.; Hofmeyry, S.A.; Somayajiy, A. Infect Recognize Destroy. 1996. Available online: https://api.semanticscholar.org/CorpusID:218464589 (accessed on 6 April 2025).
- Forrest, S.; Perelson, A.S.; Allen, L.; Cherukuri, R. Self-nonself discrimination in a computer. In Proceedings of the 1994 IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 16–18 May 1994; pp. 202–212. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).