Abstract
Cyber threats are growing in scale and complexity, outpacing the capabilities of traditional security systems. Machine learning (ML) models offer enhanced detection accuracy but often rely on centralized data, raising privacy concerns. Federated learning (FL), by contrast, enables decentralized model training but suffers from scalability and latency issues. Hybrid AI models, which integrate ML and FL techniques, have emerged as a promising solution to balance performance, privacy, and scalability in cybersecurity. This systematic review investigates the current landscape of hybrid AI models, evaluating their strengths and limitations across five key dimensions: accuracy, privacy preservation, scalability, explainability, and robustness. Findings indicate that hybrid models consistently outperform standalone approaches, yet challenges remain in real-time deployment and interpretability. Future research should focus on improving explainability, optimizing communication protocols, and integrating secure technologies such as blockchain to enhance real-world applicability.
1. Introduction
Cyber incidents, such as the Equifax data breach, which exposed the personal information of millions, and the WannaCry ransomware attack, which crippled critical infrastructures worldwide, exemplify the evolving landscape of cyber threats [1,2,3]. These are not isolated events but rather indicative of a broader trend: modern cyberattacks are becoming more sophisticated, dynamic, and persistent, outpacing the capabilities of traditional defense mechanisms.
Conventional security tools such as firewalls and antivirus software are increasingly insufficient for detecting and mitigating advanced threats [4,5]. This has created an urgent need for adaptive security systems capable of real-time detection and response. To this end, Machine learning (ML) has emerged as a transformative approach. ML models excel at analyzing vast amounts of network data and identifying subtle patterns that may signal malicious behavior, often surpassing rule-based systems in accuracy and adaptability [6,7].
However, ML models typically rely on centralized data storage, raising concerns about data privacy, regulatory compliance, and the risk of data breaches [8,9]. The aggregation of sensitive information in centralized servers creates a critical vulnerability, particularly in sectors such as healthcare, finance, and critical infrastructure.
To address these privacy concerns, federated learning (FL) introduces a decentralized training paradigm. FL enables machine learning models to be trained across multiple edge devices or institutions without exposing raw data, thereby preserving privacy and supporting compliance with regulations like GDPR [10,11]. Despite these advantages, FL suffers from several limitations, including communication overhead, non-IID data heterogeneity, and reduced effectiveness in real-time or large-scale environments [12,13,14].
To overcome these respective shortcomings and synergistically leverage their strengths, federated machine learning (FML) models, which explicitly integrate ML and FL techniques, have emerged as a promising solution. Such systems are particularly promising in decentralized, privacy-sensitive, and dynamic environments like Internet of Things (IoT) networks, cloud computing, and smart grids. This paper presents a systematic review of federated machine learning (FML) models that combine ML and FL techniques for cybersecurity applications [15,16]. It critically evaluates these models across five key performance dimensions: accuracy, privacy preservation, scalability, explainability, and robustness to adversarial attacks. Unlike previous reviews that may have focused solely on ML or FL, or provided a broad overview of “Hybrid AI” without specific emphasis on the FL+ML/DL synergy, this systematic literature review provides an in-depth analysis of the unique architectural configurations, performance trade-offs, and critical research gaps specific to FML in cybersecurity [17]. By providing a nuanced understanding of these integrated approaches, this review aims to bridge existing knowledge gaps and identify novel future directions for robust and privacy-preserving cybersecurity solutions.
To guide this investigation and provide novel insights into the field, we formulate the following research questions:
- RQ1: What specific federated learning (FL) and machine learning (ML)/deep learning (DL) architectures and techniques are predominantly employed for various cybersecurity applications, and how do their configurations impact reported performance?
- RQ2: What are the key performance trade-offs (e.g., between accuracy, privacy, scalability, and robustness) inherent in current federated machine learning (FML) approaches when applied to diverse cybersecurity use cases, and how are these trade-offs currently managed in the literature?
- RQ3: To what extent do existing federated machine learning (FML) models in cybersecurity address the critical need for explainability, and what are the prevalent methods and their limitations in enhancing model interpretability for high-stakes cybersecurity decision-making?
- RQ4: What are the primary research gaps and emerging trends in federated machine learning (FML) for cybersecurity, and what novel solutions, such as alternative privacy-enhancing technologies beyond blockchain (e.g., multi-party computation), are critical to overcome existing limitations and enhance real-world applicability?
The remainder of this paper is organized as follows: Section 2 describes the methodology adopted for this review. Section 3 analyzes prior research in ML, FL, and hybrid AI models. Section 4 presents our evaluation and key findings. Section 5 discusses the implications of our analysis and highlights areas for improvement. Finally, Section 6 concludes the paper and outlines directions for future research.
2. Methodology
The methodology adopted in this systematic review was meticulously designed to ensure a comprehensive and rigorous analysis of the current state of research concerning the integration of federated learning (FL) and machine learning (ML) within cybersecurity applications. This section details the revised Search and Study Selection Strategy, as well as the refined Data Extraction and Synthesis Methods that guided the inclusion and analysis of relevant studies.
2.1. Search and Study Selection Strategy
The literature review aimed to identify high-quality, peer-reviewed journal articles published between 2015 and 2024 that focused on the synergistic integration of federated learning and machine learning/deep learning for cybersecurity. To ensure a comprehensive and exhaustive search, a wide range of academic databases was covered, including IEEE Xplore, SpringerLink, MDPI, ACM Digital Library, Scopus, PubMed, Web of Science, Wiley Online Library, ScienceDirect, Taylor & Francis Online, and ProQuest. These databases were selected for their extensive coverage of peer-reviewed articles in cybersecurity, artificial intelligence, and data analytics, ensuring the inclusion of impactful research contributions.
A systematic search strategy was meticulously developed using a precise combination of keywords to accurately capture the relevant literature on the integration of FL and ML/DL in cybersecurity. The primary search terms incorporated both general and specific terminology prevalent in the field, including (“Federated Learning” OR FL) AND (“Machine Learning” OR ML OR “Deep Learning” OR “DL”) AND (“Cybersecurity” OR “Threat Detection” OR “Intrusion Detection” OR “Malware Detection” OR “Fraud Detection” OR “Network Security” OR “Anomaly Detection”), along with specific terms such as “Federated Machine Learning” (FML) or FML, “Federated Deep Learning” (FDL) or FDL, “Horizontal Federated Learning” (HFL) or HFL, and “Vertical Federated Learning” (VFL) or VFL. Boolean operators (AND, OR) were consistently utilized to refine these queries, ensuring the identification of studies that specifically addressed the combination of federated learning with machine learning or deep learning for various cybersecurity mechanisms. Figure 1, generated using VOSviewer version 1.6.20 [18], visually represents the co-occurrence of key research terms in the initial pool of identified papers, illustrating the interconnectedness of these areas and guiding the refinement of our search strategy. This structured approach facilitated the identification of research studies exploring key dimensions such as accuracy, privacy preservation, scalability, explainability, and robustness in cybersecurity frameworks [18,19,20].
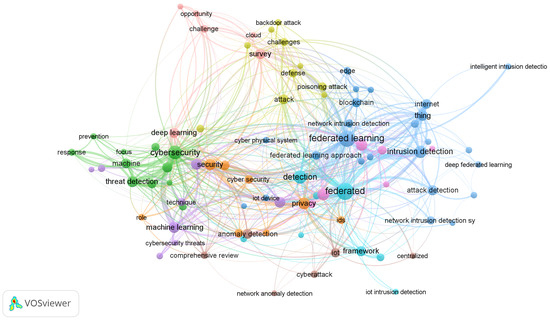
Figure 1.
Visualization of research trends in hybrid AI models for cybersecurity applications.
To maintain scientific rigor and reliability throughout the review process, a stringent set of inclusion and exclusion criteria was applied. Studies published between 1 January 2015 and 31 December 2024 that were peer-reviewed journal articles and written exclusively in English were considered for inclusion. Furthermore, studies were included if they explicitly proposed or evaluated models combining federated learning (FL) with machine learning (ML) or deep learning (DL) and focused on the application of these combined models within cybersecurity contexts, such as intrusion detection systems (IDS), malware analysis, fraud detection, network security, or anomaly detection. Finally, included studies had to provide sufficient evaluation metrics or discussions related to the five key dimensions: accuracy, privacy preservation, scalability, explainability, and robustness. Conversely, non-peer-reviewed literature (including grey literature like unpublished reports, whitepapers, or preprints), articles not subjected to formal peer review, or duplicate publications were excluded. Studies focusing solely on machine learning or deep learning without the explicit integration of federated learning were also excluded, as were those primarily concerned with the security of federated learning itself (e.g., data poisoning attacks on FL models) rather than the application of FL for cybersecurity threat detection or defense. Articles that did not provide sufficient methodological detail or empirical results relevant to the specified evaluation metrics were also excluded.
The study selection process strictly adhered to the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) guidelines, ensuring transparency, methodological rigor, and replicability throughout the review process. This process was divided into four distinct stages: Identification, Screening, Eligibility, and Inclusion. In the identification phase, the initial search using the refined keyword combinations across the targeted databases, resulted in the identification of 488 articles. Following automated and manual duplicate removal, a total of 395 unique records progressed to the screening phase. The screening phase involved a rigorous review of titles and abstracts to evaluate their alignment with the study’s objectives and the refined inclusion/exclusion criteria. Articles that did not explicitly address the combination of federated learning and machine learning/deep learning for cybersecurity applications were excluded, leading to the removal of 194 articles that lacked direct relevance or methodological focus. During the eligibility phase, the remaining 201 full-text articles were assessed for conformity with the predefined inclusion and exclusion criteria. Studies that failed to meet quality standards or did not provide sufficient evaluation metrics relevant to our five dimensions (accuracy, privacy, scalability, explainability, robustness) were excluded. A total of 97 articles were excluded during this phase for various reasons, including failure to meet quality assessment criteria 68 studies) and insufficient evaluation metrics (29 studies). Additionally, 19 articles could not be retrieved despite repeated attempts. Finally, in the inclusion phase, 85 studies were included in the systematic review for detailed analysis. These studies demonstrated strong methodological foundations and clear relevance to the application of FL+ML/DL in cybersecurity, particularly in enhancing intrusion detection systems (IDS), malware detection, anomaly detection, and network threat analysis. The entire study selection process is visually represented in the updated PRISMA flow diagram (see Figure 2), which outlines each step from identification to final inclusion, providing transparency and replicability in the selection methodology.
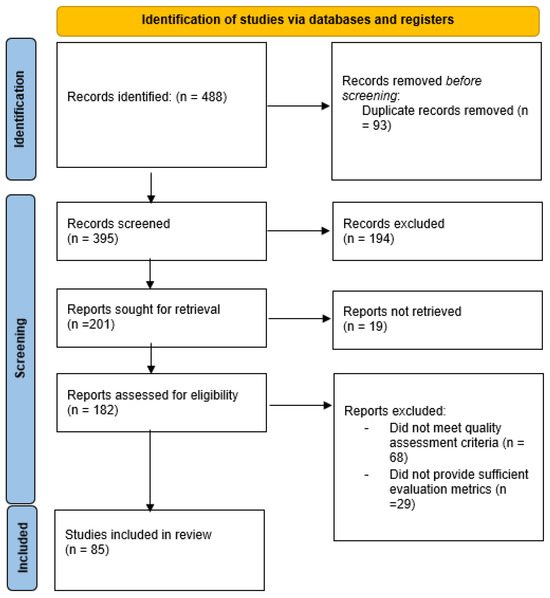
Figure 2.
Study selection process.
2.2. Data Extraction and Synthesis Methods
Data extraction was conducted systematically to ensure the accurate and consistent collection of key information from all included studies. A predefined data extraction template was utilized to gather critical details such as authors, publication year, study objectives, the specific FL+ML/DL techniques employed, reported evaluation metrics, and the cybersecurity application domains addressed [20]. This structured approach facilitated a coherent comparison of methodologies and outcomes across diverse studies.
The key techniques extracted included various machine learning (ML) algorithms (e.g., CNN, RNN, SVM, random forest), federated learning (FL) architectures (e.g., horizontal FL, vertical FL), and the specific configurations of their hybrid frameworks. These models were assessed for their application in cybersecurity, focusing on areas such as intrusion detection systems (IDS), malware detection, anomaly detection, and broader network security analysis. The systematic extraction of these methodologies enabled a structured comparison of different approaches, highlighting their reported effectiveness in addressing modern cybersecurity threats.
The performance of these models was evaluated based on five critical evaluation metrics, each reflecting a distinct dimension of model utility:
- Accuracy: The model’s reported ability to distinguish between normal and malicious activities with high precision, ensuring reliability in threat detection;
- Privacy Preservation: The reported capability to protect sensitive data during model training and inference, particularly significant in federated learning environments where raw data remains decentralized;
- Scalability: The reported capacity to handle large-scale datasets and real-time traffic analysis, a necessity for deployment in large networks and cloud infrastructures;
- Explainability: The reported transparency in decision-making processes, which is crucial for regulatory compliance and stakeholder trust; This metric assesses how well models provide interpretable insights into their decisions;
- Robustness: The reported resilience of the models against adversarial attacks, data perturbations, and variable operational environments, ensuring stable performance even in hostile conditions.
After the rigorous data extraction process, the collected information was systematically synthesized to derive comprehensive insights into the current state of federated learning and machine learning hybrid models in cybersecurity. This synthesis involved several steps.
A qualitative thematic analysis was performed, where extracted data points related to the employed techniques, specific applications, reported performance, and discussed challenges across the five-evaluation metrics were grouped into thematic categories. This allowed for the identification of recurring patterns, common strengths, specific limitations, and emerging trends within each dimension.
A comparative analysis was then conducted, where a cross-study comparison for each evaluation metric contrasted the reported performance and characteristics of standalone ML models, standalone FL models, and the identified hybrid FL+ML/DL models. This comparison aimed to highlight the synergistic benefits, specific trade-offs, and unique advantages of integrated approaches in different cybersecurity contexts.
Finally, through critical evaluation and gap identification, existing research gaps, unaddressed challenges, and promising future directions were systematically identified from the synthesized findings. Particular attention was paid to areas where current hybrid models demonstrated limitations (e.g., generalizability of high accuracy claims, true real-world scalability, comprehensive explainability beyond basic tools) or where further research could yield significant advancements. This approach ensured that the presented results are contextualized, acknowledging the experimental settings of the original studies, and framed within the broader research landscape. This comprehensive data extraction and synthesis methodology allowed for a robust understanding of the current research landscape, directly informing the answers to the formulated research questions and articulating the overall contribution of this systematic review.
3. Background and Related Work
This section establishes the foundational context for understanding federated machine learning (FML) in cybersecurity. It begins by outlining the applications and inherent challenges of traditional machine learning (ML) in securing cyber environments. Subsequently, it delves into the principles and specific challenges of federated learning (FL), setting the stage for the emergence of hybrid models. This is followed by an overview of prior systematic literature reviews in the domain, explicitly identifying the unique research gap that this current study addresses and justifying its distinctive contribution to the field.
3.1. Applications and Challenges of Machine Learning in Cybersecurity
In recent years, the research area of ML-based cybersecurity solutions has gained increasing attention for performing tasks such as intrusion detection, anomaly detection, and malware analysis. The different supervised learning-based algorithms that show outstanding performance and accuracy for threat detection are random forest and SVM [10,21,22], as their successful performance relies heavily on labeled data through which any new instance would be rightly classified. For instance, studies such as [21,22] have focused on the role of ML algorithms such as SVM and decision trees for robust classification performance, whereas [9] has explored the automation of threat detection using supervised methods. On the other hand, unsupervised approaches, including clustering algorithms, do a great job in finding new and unknown attack patterns by analyzing data distributions and deviations [23,24]. As shown in the table below (Table 1), ref. [24] focuses on malware and anomaly detection, hence giving ample evidence that clustering techniques may work for adaptive threat responses. Despite these strengths, ML models tend to depend upon centralized data storage, which is significantly vulnerable to breaches and raises substantial concerns pertaining to privacy. In addition, such centralization of systems raises scalability issues, hence limiting the deployment of ML models in large-scale, real-time cybersecurity environments where distributed and adaptive solutions are increasingly required [16,25,26]. For instance, ref. [25] discusses challenges related to IoT security risks, while [16] proposes a thematic framework that addresses the scalability needs of modern cybersecurity systems.

Table 1.
Applications and challenges of machine learning in cybersecurity.
3.2. Federated Learning: Principles and Challenges
Federated learning (FL) presents a decentralized paradigm that enables collaborative model training across distributed entities without sharing raw data, making it highly suitable for privacy-sensitive domains like cybersecurity [37,38]. As detailed in Table 2, FL is increasingly leveraged for diverse cybersecurity applications, including privacy-preserving threat detection in edge and cloud environments [37], real-time attack detection and trust management [39], and robust intrusion detection systems (IDS) even under adversarial conditions [40]. FL models are also actively applied for intrusion detection in heterogeneous IoT networks [41,42], enhancing overall IoT cybersecurity [43,44,45], and demonstrating superior performance over centralized methods in detecting cyber threats [46]. Specific implementations include RNN-based federated models for distributed intrusion detection [47,48], reviews of FL solutions for IoT intrusion detection [49,50], and systems integrating digital twins with FL for zero-day threat detection in IoT [51]. FL also supports scalable vertical learning frameworks for cybersecurity analytics [52] and offers general support for cybersecurity fundamentals, applications, and opportunities [38].
Despite its potential, FL still faces significant implementation challenges. These include high communication overhead, which can lead to network congestion and latency due to frequent model exchanges [43,53]. This complexity is compounded by data heterogeneity across distributed devices, making synchronization and consistent training a challenging task [54,55]. To address these issues, studies such as [53] propose dynamic aggregation to reduce bandwidth consumption, while [56] enhances model robustness through intelligent participant selection. In parallel, ref. [57] introduces real-time resource and data allocation strategies to improve efficiency in federated anomaly detection systems. A growing subset of FL research focuses on Vertical Federated Learning (VFL), where features—not data samples—are partitioned across entities [52,54]. These VFL frameworks are evaluated for their potential in handling distributed, vertically fragmented data in adversarial and real-world cybersecurity scenarios [54]. Collectively, these works emphasize the need for scalable, interpretable, and communication-efficient FL frameworks to meet the demands of modern cybersecurity landscapes.

Table 2.
Evaluating federated learning for cybersecurity solutions.
Table 2.
Evaluating federated learning for cybersecurity solutions.
| Ref. | Survey | Objective |
|---|---|---|
| [37] | Federated learning for cybersecurity | Comprehensive review of federated learning in edge and cloud computing for privacy-preserving threat detection. |
| [54] | Federated learning-based model to lightweight IDSs for heterogeneous IoT networks | Comprehensive survey on FL specifically for IDSs in IoT environments. |
| [39] | Federated learning for cybersecurity concepts | Explores real-time applications of federated learning in cybersecurity for attack detection and trust management. |
| [40] | Federated learning in adversarial environments: Testbed design and poisoning resilience in cybersecurity | Introduces a testbed to evaluate FL-based IDSs under adversarial conditions, focusing on poisoning resilience and anomaly detection. |
| [41] | Privacy-preserving federated learning for intrusion detection in IoT | Proposes a hybrid FL framework for intrusion detection in IoT networks that integrates homomorphic encryption and differential privacy. |
| [42] | Federated learning for privacy-preserving intrusion detection in IoT | Implements a FedAvg-based FL model across multiple IoT nodes for intrusion detection. |
| [43] | Federated learning in IoT cybersecurity | Discusses IoT cybersecurity challenges addressed by federated learning, such as latency and data privacy. |
| [44] | FL techniques for cybersecurity | Highlights privacy risks and mitigation strategies for federated learning in cybersecurity. |
| [45] | Federated learning support for cybersecurity | Provides a foundational overview of how FL can be leveraged to enhance cybersecurity. |
| [46] | Detecting cyber threats in IoT with FL | Demonstrates superior performance of FL over centralized learning in detecting IoT threats. |
| [58] | Deep learning and federated learning in cybersecurity | Reviews federated and deep learning approaches for enhanced cybersecurity and privacy. |
| [47] | FL-IDPP: A federated learning-based intrusion detection model for IoT | Introduces FL-IDPP, an RNN-based FL model that performs distributed intrusion detection in IoT networks. |
| [49] | IoT intrusion detection | Reviews intrusion detection solutions for IoT with a focus on FL, explainable AI, and social psychology methods. |
| [51] | Digital twin and federated learning enabled cyberthreat detection system for IoT networks | Combines digital twins and optimized FL to improve detection of zero-day threats in IoT with reduced latency and improved aggregation. |
| [50] | Federated learning for Internet of Things | Presents the FedIoT platform and FedDetect algorithm, showing how FL improves attack detection and system efficiency on real IoT devices. |
| [59] | Enhancing privacy-preserving intrusion detection with federated learning | Shows that FL-based models outperform centralized deep learning in detecting cyberattacks in privacy-sensitive environments. |
| [55] | Privacy-preserving federated learning-based intrusion detection for IoT | Develops a lightweight FL framework using FedAvg that maintains high detection rates across heterogeneous IoT environments. |
| [52] | A scalable vertical federated learning framework for analytics in the cybersecurity domain | Proposes and evaluates a vertical FL framework that is adaptable, privacy-compliant, and scalable for real-world cybersecurity analytics. |
| [38] | 2D federated learning model | Combines HFL and VFL for personalized human activity recognition in cyber-physical-social systems, with privacy-preserving homomorphic encryption. |
| [60] | Federated learning based approach to intrusion detection | Proposes an HFL-based IDS that increases detection rates across heterogeneous attacks while considering computational and bandwidth constraints. |
| [53] | An efficient federated learning system for network intrusion detection | Introduces dynamic weighted aggregation (DAFL) to improve HFL model accuracy and reduce communication overhead. |
| [56] | FedSBS: Participant-selection method for FL-based IDS | Enhances HFL by using score-based participant filtering to resist malicious clients and improve detection robustness. |
| [57] | Fed-FIDS: Federated learning for anomaly detection in IDS | Introduces real-time resource allocation and data selection modules to make HFL more efficient and accurate. |
3.3. Hybrid AI Models: A Conceptual Overview
Hybrid AI models that combine the predictive power of machine learning (ML) or deep learning (DL) with the privacy preserving architecture of federated learning (FL) offer a compelling solution to emerging cybersecurity challenges. These models are especially suitable for distributed and sensitive environments such as IoT networks and cyber-physical systems, where ensuring data confidentiality and maintaining real-time detection capabilities are vital. As summarized in Table 3, ref. [61] provides a broad review of hybrid ML + FL architectures, highlighting improvements in detection accuracy and privacy compliance. In adversarial contexts, ref. [62] evaluates vertical federated learning (VFL) using SplitNN in grid systems under DoS and data injection attacks, and [63] proposes a multi-agent VFL framework combining reinforcement learning techniques for robust cyber-physical protection. Ref. [64] introduces a hierarchical hybrid FL architecture integrating VFL, HFL, and transfer learning to support adaptive analytics in cybersecurity domains.
Several studies leverage hybrid DL models under FL. For example, ref. [65] uses CNN and BiLSTM within an HFL setting for zero-trust intrusion detection, and [66] merges HFL with gradient boosted trees to enhance interpretability. Moreover, refs. [67,68] demonstrate how federated deep learning (FDL) architectures achieve high performance and efficiency for IoT intrusion detection. Generative adversarial networks (GANs) are increasingly integrated with FL to improve robustness, as illustrated by [69], which combines GANs and FL for intrusion detection. Further, ref. [70] integrates FL with GANs and differential privacy for UAV networks, and [71] incorporates blockchain and differential privacy with federated GANs to ensure robust and transparent collaborative IDS in cyber-physical systems. Despite these advancements, scalability, communication efficiency, and explainability remain open research challenges, underscoring the need for continuous innovation in hybrid AI frameworks for cybersecurity.
Beyond the current applications and comparative performance, the landscape of federated machine learning (FML) in cybersecurity is continually evolving with new research directions and emerging trends. These advancements aim to overcome existing limitations inherent in standalone ML and FL approaches and to unlock novel capabilities for enhanced threat detection, robust privacy, and system resilience. By exploring more sophisticated architectural designs, novel algorithmic integrations, and synergistic combinations with other cutting edge technologies, FML is pushing the boundaries of what is possible in distributed and privacy sensitive cyber defense. Table 4 synthesizes these cutting-edge developments, categorizing them by their primary focus within the hybrid FL+ML/DL paradigm and highlighting their potential impacts as well as remaining challenges that require further investigation.

Table 3.
Hybrid AI models.
Table 3.
Hybrid AI models.
| Ref. | Title/Survey | Objective/Summary | Hybrid Components |
|---|---|---|---|
| [61] | A review on advancing cybersecurity frameworks by integrating machine intelligence with Federated Learning | Reviews hybrid cybersecurity architectures combining ML with FL, enhancing detection accuracy while maintaining privacy compliance. | ML + FL |
| [63] | An innovative multi-agent approach for robust cyber-physical systems using vertical Federated Learning | Introduces a VFL-based reinforcement learning framework using deep Q-networks and actor-critic agents for adversarial modeling in cyber-physical systems. | VFL + reinforcement learning (DQN, A2C agents) |
| [62] | Performance evaluation of vertical Federated Machine Learning against adversarial threats on wide-area control system | Evaluates VFL (via SplitNN) in grid systems under adversarial machine learning threats such as DoS and data injection attacks. | VFL + SplitNN (DL) |
| [64] | Federated learning architectures for credit risk assessment: A comparative analysis of vertical, horizontal, and transfer learning approaches | Introduces an adaptive hierarchical hybrid Federated Learning (HHFL) architecture potentially applicable to cybersecurity solutions. | Hierarchical FL (VFL, HFL, transfer learning components) |
| [66] | An interpretable Federated Learning-based network intrusion detection framework (FEDFOREST) | Combines gradient boosted decision trees (GBDT) with HFL to build a privacy-enhanced, interpretable, and effective IDS. | HFL + GBDT (ML) |
| [65] | A Federated Learning-based zero trust IDS for IoT | Uses CNN + BiLSTM under HFL to detect intrusions while maintaining zero-trust data confidentiality. | HFL + CNN (DL) + BiLSTM (DL) |
| [67] | Federated Deep Learning for collaborative intrusion detection | Introduces an FDL model using local DNNs and a novel Fed+ fusion algorithm for heterogeneous network traffic. | FDL + DNNs (DL) + Fed+ fusion algorithm |
| [68] | FDL for intrusion detection in consumer-centric IoT | Demonstrates high performance (up to 99.6%) in detecting multiple IoT attacks while preserving privacy and reducing training time. | FDL (implied DL) |
| [72] | FMDL: Federated mutual distillation learning | Proposes a defense against backdoor attacks in FL via private model personalization and distillation-based learning. | FL + distillation-based learning (ML) |
| [73] | Secure FML with flexible topology | Proposes a zero-trust, secure FML framework using confidential computing for privacy-preserving, auditable training. | FML + confidential computing |
| [74] | Swarm-FDL in Internet of Vehicles (IoV) | Merges swarm learning and FDL to reduce overhead and enhance model trustworthiness in IoV systems. | FDL + swarm learning |
| [75] | Federated Deep Learning for cyber security in the Internet of Things | Compares FDL models (CNN, RNN, DNN) across IoT datasets. | FDL (CNN, RNN, DNN) |
| [76] | Chained anomaly detection models for Federated Learning | Proposes blockchain-integrated FML for secure anomaly detection. | FML + blockchain |
| [77] | CYBRIA—Privacy-aware cybersecurity with Federated Learning | Introduces Cybria, a privacy-preserving FL framework with higher accuracy than centralized DNNs. | FL + DNNs |
| [78] | FLAD: Adaptive Federated Learning for DDoS attack detection | Develops an adaptive FDL approach for dynamic cybersecurity scenarios. | Adaptive FDL (DL) |
| [79] | GVFL attack study | Shows GNN-based VFL systems are vulnerable to adversarial attacks. | VFL + GNN (DL) |
| [69] | FEDGAN-IDS: Privacy-preserving IDS using GAN and Federated Learning | Combines GANs and FL to improve IDS in IoT environments. | FL + GAN (DL) |
| [80] | Fed-ANIDS | Uses autoencoder-based anomaly detection with FedProx, outperforming GAN-based FL models. | FL (FedProx) + autoencoder (DL) |
| [70] | FGA-IDS: A Federated Learning and GAN-augmented IDS for UAV networks | Proposes FGA-IDS for UAVs using FL, GANs, and differential privacy. | FL + GANs (DL) + differential privacy |
| [81] | An adaptive Federated Learning IDS based on GAN under IoT | Combines FL with GANs to detect anomalous IoT traffic. | FL + GANs (DL) |
| [82] | Federated intrusion detection on non-IID data for IIoT networks using GAN and RL | Addresses non-IID data with GANs and RL for client selection. | FL + GAN (DL) + RL (ML) |
| [71] | Enhanced collaborative intrusion detection using blockchain and decentralized FL with GANs | Combines blockchain, differential privacy, and GAN-based FL for IDS. | FL + GANs (DL) + blockchain + differential privacy |

Table 4.
Emerging trends in hybrid AI-driven cybersecurity.
Table 4.
Emerging trends in hybrid AI-driven cybersecurity.
| Theme | Subcategory | Key References | Focus/Findings | Limitations/Gaps |
|---|---|---|---|---|
| Hybrid AI Models | Multi-Modal Threat Detection | [69,70,71,81,82,83,84] | Combines hybrid ensembles or FL with GANs/RL for enhanced intrusion detection and richer threat modeling in diverse environments like IoT and UAV networks. | Computational overhead and interoperability issues in cross-platform systems. |
| Hierarchical FL Architectures | [52,64,85,86,87,88,89,90,91,92] | Introduces adaptive hierarchical hybrid federated learning (HHFL) architectures. Uses knowledge distillation-based FL framework to integrate diverse local models into a global ensemble across heterogeneous IoT networks. Shows HFL resists untargeted adversarial threats via hierarchical aggregation. Improves privacy and efficiency in IoT via multi-level aggregation. Offers decentralized control, enhancing defense and privacy. Integrates blockchain with HFL for secure collaborative IDS in IoT. Proposes reputation-based robust HFL scheme against poisoning in IoV. Reduces communication overhead and enhances accuracy with sparse networks. Improves anomaly detection in smart farms using hierarchical FL-transfer learning. Achieves strong privacy-performance tradeoffs for intrusion detection with scalable vertical FL. | Requires strict network coordination and high resource availability at edge nodes. Remains vulnerable to targeted attacks such as backdoors. | |
| Quantum & Attention-Based FL | [93,94,95,96] | Integrates quantum computing and attention networks with FL for enhanced cyber-attack detection, privacy, robustness, and secure training on quantum data. | High implementation complexity and nascent quantum infrastructure. | |
| Residual Network-Enabled FL | [97] | Applies ResNets within FL for network anomaly detection in industrial IoT, improving scalability and efficiency. | Still lacks extensive testing on adversarial examples and zero-day attacks. | |
| Ensemble Knowledge Distillation | [72,85,98,99,100,101,102,103,104,105] | Aggregates knowledge from diverse local models via distillation to enhance generalization, privacy, accuracy, and efficiency in heterogeneous FL settings, including defense against backdoor attacks. | Requires trust in teacher models; limited interpretability in the distilled outputs. | |
| FL with Differential Privacy | [70,71,106,107,108,109] | Combines FL with hybrid DP mechanisms to enhance privacy, accuracy, and fairness in secure model sharing, supporting adaptive cyber defense and threat intelligence. | Trade-offs between privacy strength and model performance; added latency. Limitations in gradient modification-based approaches. | |
| Neuro-Symbolic AI for Security | [110,111,112] | Integrates deep neural networks with symbolic knowledge for interpretable, adaptive, and robust cybersecurity solutions for threat detection, critical systems, and human-autonomy teaming. | Still lacks empirical validation in dynamic threat environments; integration with real-time cyber operations is early-stage. | |
| Agentic Hybrid AI | [63,82,113] | Develops autonomous cyber defense (ACD) agents using hybrid AI (RL, LLMs, rule-based systems) for proactive network defense, real-time threat intelligence, and secure vehicle communications. | Coordination challenges between multiple agent types, high training complexity, and need for real-time synchronization. | |
| Dynamic Retraining/Continual Learning Firewalls | [78,114,115] | Enables dynamic adaptation to evolving threats and real-time intrusion detection via FL with encrypted weights, incremental learning, ML/DL rule updates, and adaptive retraining for firewalls. | Model drift, concept evolution, and lack of standard benchmarks for evaluating continual learning in cyber settings. | |
| Other Advanced Hybrid FL Architectures | [48,62,65,67,68,73,74,75,76,77,116] | Introduces various advanced hybrid FL architectures for distributed intrusion detection, adversarial grid systems, zero-trust IDS, and enhanced threat identification, often integrating privacy and robustness features. | Integration complexity and evaluation challenges across diverse system settings with heterogeneous data and privacy levels. |
3.4. Prior Systematic Literature Reviews and Research Gaps
Existing systematic literature reviews (SLRs) and comprehensive surveys have significantly contributed to understanding various aspects of AI in cybersecurity. Some reviews focus broadly on machine learning applications in different cybersecurity domains, detailing algorithms, datasets, and general challenges [8,10,25,26,27,28,30,31]. Others concentrate on federated learning, exploring its fundamental principles, architectures, and inherent privacy and security challenges within the FL framework itself [37,39,40,43,54]. While valuable, these reviews often analyze ML and FL either in isolation or from a perspective that does not deeply explore their synergistic combination as a distinct class of “Hybrid AI Models” (specifically FL+ML/DL) [61,64,75,117,118,119,120,121,122,123].
Specifically, there is a gap in systematic reviews that thoroughly
- Precisely define and categorize the diverse architectural configurations and techniques of federated machine learning (FML) models in cybersecurity;
- Provide a structured comparative analysis of FML models across critical performance dimensions like accuracy, privacy, scalability, explainability, and robustness;
- Synthesize primary research gaps and emerging trends that are unique to the FML paradigm in cybersecurity, including the integration of advanced technologies like quantum computing, neuro-symbolic AI, and agentic AI, and novel privacy-enhancing techniques beyond basic differential privacy or blockchain.
This systematic review aims to fill this identified gap by offering a comprehensive and structured analysis of FML models in cybersecurity, providing a clearer taxonomy and a detailed synthesis of their current state, performance trade-offs, and crucial future directions.
4. Results and Analysis
The systematic evaluation of federated machine learning (FML) models, also referred to as FL+ML/DL hybrid models, reveals substantial advantages over standalone machine learning (ML) and federated learning (FL) systems across five key metrics: accuracy, privacy preservation, scalability, explainability, and robustness. As comprehensively illustrated in Table 5, these hybrid approaches effectively balance high-performance capabilities with stringent privacy requirements, directly addressing the inherent limitations of both centralized ML and traditional FL approaches. Their enhanced overall characteristics position them as a compelling solution for addressing the multifaceted challenges of modern cybersecurity applications, particularly in distributed systems and real-time threat detection environments.

Table 5.
Comparative evaluation of ML, FL, and hybrid AI models.
Accuracy represents a fundamental strength of FML models. While traditional machine learning models typically demonstrate reported accuracy around 85%, federated learning models improve upon this, achieving approximately 90% reported detection rates in various cybersecurity tasks. FML models, leveraging the synergistic integration of centralized learning’s precision with decentralized training’s adaptability, are reported to achieve the highest accuracy, reaching up to 99.9% on benchmark datasets for specific detection tasks such as intrusion detection and malware classification. This enhanced performance in identifying and mitigating both established and emerging threats underscores the capacity of hybrid models as valuable assets in contemporary cybersecurity strategies [47,59,62,63,67,68,75].
Privacy preservation constitutes a critical advantage of both FL and FML models. Inherently, federated learning enables decentralized model training without sharing raw data, ensuring data remains stored on local devices and significantly reducing risks associated with centralized storage. This architectural approach ensures compliance with regulatory frameworks such as GDPR while maintaining high performance standards. Advanced techniques, including homomorphic encryption, differential privacy, and secure aggregation, are commonly implemented in FML models to safeguard data integrity throughout training and inference processes, making them particularly appropriate for deployment in privacy-sensitive domains [41,43,65,66,70,71,82,107,108,109].
Scalability presents a significant challenge for standalone machine learning systems (often moderate) and traditional federated learning systems (often low-to-moderate), particularly in large-scale, real-time applications. FML models address this constraint by implementing optimized communication protocols, efficient resource allocation strategies, and lightweight architectures. Simulations and experimental studies conducted in IoT networks and distributed systems demonstrate reduced latency and increased throughput, highlighting the operational efficiency of hybrid frameworks. These enhancements make FML models especially suitable for managing the demands of extensive environments, enabling consistent performance in scenarios requiring immediate decision-making and processing [53,57,64,70,74,78,82,97,107].
Explainability remains an area requiring substantial improvement across all model types, particularly in hybrid AI frameworks. While interpretability tools such as SHAP (SHapley Additive Explanations) and LIME (Local Interpretable Model-Agnostic Explanations) are employed to enhance transparency in both FL and hybrid models, their integration into complex FML architectures remains limited. This limitation impacts transparency and usability, particularly in high-stakes decision-making contexts such as intrusion prevention and fraud detection, where understanding the rationale behind system decisions is essential. Advancing explainability mechanisms, including developing more seamless integration methods and enhancing model interpretability without compromising performance, will be crucial for building user trust and facilitating broader adoption of FML models in cybersecurity applications [80,85,99,100,101,102,103,104].
Robustness against adversarial attacks represents a significant advantage of hybrid AI models, often outperforming standalone ML and matching or exceeding FL. By combining centralized and decentralized training approaches, these frameworks demonstrate enhanced resilience to common vulnerabilities, including data poisoning and evasion attacks. The decentralized component mitigates the risk of widespread compromise, while the centralized element (or specific hybrid techniques) ensures consistent and accurate model updates. Furthermore, the adaptive capabilities of hybrid models enable effective responses to dynamic and evolving threat landscapes, ensuring reliable performance even in hostile environments. This combination of resilience and adaptability makes FML frameworks particularly valuable for maintaining security and reliability in challenging cybersecurity contexts [62,73,74,76,78,79].
In summary, research findings emphasize how FML techniques effectively balance performance and privacy preservation, scalability and explainability, and robustness addressing multiple challenges in modern cybersecurity more comprehensively than any single standalone approach. The comparative analysis presented in Table 5 illustrates these metrics, highlighting how hybrid models combine the pattern recognition strengths of ML with the distributed learning advantages of FL to achieve superior overall performance. While FL and FML models demonstrate high privacy preservation, and FML shows strong accuracy and robustness, optimizing scalability for large-scale and real-time environments and developing more comprehensive explainability frameworks remain areas requiring further development to enhance transparency and build user trust. Addressing these aspects will be essential for facilitating wider adoption and improving the efficiency of FML models in dynamic cybersecurity environments.
5. Discussion
This systematic review provides comprehensive insights into the evolving landscape of federated machine learning (FML) models, also referred to as FL+ML/DL hybrid models, within cybersecurity. The findings presented in Section 4, supported by the detailed analyses in Table 3, Table 4 and Table 5, offer a nuanced understanding of their performance, strengths, limitations, and future trajectory. This section addresses the formulated research questions and contextualizes the review’s contributions and limitations.
5.1. Addressing Research Questions
RQ1: What specific federated learning (FL) and machine learning (ML)/deep learning (DL) architectures and techniques are predominantly employed for various cybersecurity applications, and how do their configurations impact reported performance?
Our review identifies a diverse range of FML architectures and techniques predominantly employed in cybersecurity. Federated deep learning (FDL) models, integrating DNNs, CNNs, RNNs, and BiLSTM, are widely utilized for intrusion detection [48,65,67,68,75,77] and malware analysis [75]. Vertical federated learning (VFL) frameworks, often incorporating SplitNN [62] or reinforcement learning agents (e.g., DQN, A2C) [63], are applied in adversarial contexts and cyber-physical systems [62,63]. Beyond deep learning, traditional ML algorithms like gradient boosted decision trees (GBDT) are hybridized with HFL for interpretable intrusion detection [66]. The configuration of these architectures, particularly the choice of local ML/DL models and FL aggregation strategies, directly impacts reported performance, with FML models consistently outperforming standalone ML or FL across various metrics [59,67,68].
RQ2: What are the key performance trade-offs (e.g., between accuracy, privacy, scalability, and robustness) inherent in current federated machine learning (FML) approaches when applied to diverse cybersecurity use cases, and how are these trade-offs currently managed in the literature?
FML approaches inherently involve critical trade-offs. While FML achieves high accuracy (up to 99.9%) [67,68] and strong privacy preservation [41,42,43,48,64,65,66,70,71,77,82,107,108,109], challenges arise when balancing these with scalability and communication efficiency [46,47,53,57,60,70,78,97,104]. For instance, implementing stronger privacy mechanisms (e.g., differential privacy, homomorphic encryption) can introduce computational overhead or affect model accuracy. Similarly, addressing the challenges of data heterogeneity across distributed devices for robust training often requires complex aggregation strategies that impact synchronization and overall efficiency [86,87]. The literature manages these trade-offs through various optimization techniques, such as dynamic aggregation [53,78], lightweight architectures, and intelligent client selection.
RQ3: To what extent do existing federated machine learning (FML) models in cybersecurity address the critical need for explainability, and what are the prevalent methods and their limitations in enhancing model interpretability for high-stakes cybersecurity decision-making?
Explainability in FML models for cybersecurity remains an area requiring substantial development. While interpretability tools such as SHAP (SHapley Additive Explanations) and LIME (Local Interpretable Model-Agnostic Explanations) are employed to enhance transparency in both FL and hybrid models, their integration into complex FML architectures remains limited [66,72,80,85,99,100]. This limitation impacts transparency and usability, particularly in high-stakes decision-making contexts such as intrusion prevention and fraud detection, where understanding the rationale behind system decisions is essential. Advancing explainability mechanisms, including developing more seamless integration methods and enhancing model interpretability without compromising performance, will be crucial for building user trust and facilitating broader adoption of FML models in cybersecurity applications [101,102,103,104,105].
RQ4: What are the primary research gaps and emerging trends in federated machine learning (FML) for cybersecurity, and what novel solutions, such as alternative privacy-enhancing technologies beyond blockchain (e.g., multi-party computation), are critical to overcome existing limitations and enhance real-world applicability?
Our review identifies several primary research gaps and compelling emerging trends in FML for cybersecurity. Key gaps include the need for more extensive testing on adversarial examples and zero-day attacks, particularly for models involving residual networks [97]. Limitations persist in fully integrating FML with real-time cyber operations, and challenges in coordinating diverse agent types in agentic hybrid AI [63,82]. Model drift and the lack of standard benchmarks for continual learning in dynamic cyber settings also represent significant hurdles [78,114,115].
However, emerging trends offer promising solutions. Quantum-enhanced FL is exploring novel ways to boost accuracy, privacy, and robustness using quantum-inspired optimization and quantum cryptographic primitives [93,94,95]. Neuro-symbolic AI is gaining traction for its potential to provide interpretable and adaptive solutions by combining deep learning with symbolic knowledge [110,111,112]. Furthermore, agentic hybrid AI is developing autonomous defense agents using reinforcement learning and LLMs for proactive network defense. Beyond blockchain, integrating multi-party computation (MPC) or advanced homomorphic encryption more deeply with FML is critical for achieving even stronger privacy guarantees and enhancing real-world applicability without compromising performance. These novel solutions are essential for overcoming existing limitations and advancing the state of FML in cybersecurity.
5.2. Contributions and Limitations of This Review
This systematic literature review offers several significant contributions to the understanding of federated machine learning in cybersecurity. By rigorously defining and categorizing FML models, it provides a clearer taxonomy of hybrid approaches, moving beyond ambiguous “Hybrid AI” definitions. The comprehensive analysis across five key performance metrics (accuracy, privacy, scalability, explainability, robustness) offers a structured comparative overview, identifying both strengths and persistent challenges. Critically, this review synthesizes emerging trends and identifies specific research gaps, directly informing future research directions in this rapidly evolving field.
However, this review is subject to certain limitations. Its scope was limited to peer-reviewed journal articles published between 2015 and 2024, written exclusively in English. The conclusions drawn are based on the reported metrics and findings within the selected literature, and thus may reflect the experimental setups and datasets used in the original studies. While efforts were made to critically evaluate the literature, inherent biases or limitations in the original research might persist.
5.3. Implications and Future Work
The findings of this review underscore the immense potential of FML models to significantly enhance cybersecurity defenses. Their ability to balance high accuracy with privacy preservation makes them particularly suitable for sensitive applications. To fully realize this potential, future work should prioritize: (1) developing standardized metrics and benchmarks for evaluating FML performance across diverse, real-world cybersecurity datasets; (2) designing advanced, inherently interpretable FML architectures to improve explainability and foster trust in high-stakes environments; (3) exploring novel communication optimization and resource management techniques to enhance scalability in large, heterogeneous networks; and (4) empirically validating the practical benefits and overcoming the implementation complexities of integrating FML with cutting-edge technologies like quantum computing and advanced privacy-enhancing mechanisms. Addressing these areas will be pivotal in translating the promise of FML into robust and widely adopted cybersecurity solutions.
6. Conclusions
This systematic review underscores that federated machine learning (FML) models offer a compelling and balanced solution to the multifaceted challenges of modern cybersecurity. By synergistically integrating the strengths of machine learning (ML)/Deep Learning (DL) with federated learning (FL), these hybrid models significantly advance beyond traditional standalone approaches. The comprehensive analysis reveals their demonstrated superiority in achieving high detection accuracy, ensuring robust privacy preservation, and enhancing resilience against adversarial threats. FML models also show promising advancements in scalability, making them increasingly suitable for distributed and real-time cybersecurity applications.
Despite these considerable strides, the review identifies key areas requiring further research. Optimizing scalability for large-scale and highly heterogeneous networks remains a critical challenge, as does reducing communication overhead. Furthermore, improving explainability in complex FML architectures is essential to foster trust and facilitate high-stakes decision-making. Emerging trends, such as quantum-enhanced FL, neuro-symbolic AI, agentic hybrid AI, and dynamic retraining firewalls, offer promising avenues to address these limitations.
Ultimately, by rigorously defining the landscape of FML models and highlighting specific research gaps and emerging solutions, this review provides a foundational understanding for future empirical and theoretical work. Addressing the identified challenges and capitalizing on the inherent strengths of hybrid AI systems will be pivotal in translating the promise of FML into widely adopted, robust, scalable, and transparent cybersecurity solutions capable of combating the ever-evolving threat landscape.
Author Contributions
Conceptualization, J.-E.M., M.K. and Y.M.; methodology, J.-E.M., M.K. and Y.M.; software, J.-E.M.; validation, Y.M. and K.E.G.; formal analysis, J.-E.M.; investigation, J.-E.M.; resources, J.-E.M.; data curation, J.-E.M. and M.K.; writing—original draft preparation, J.-E.M. and Y.M.; writing—review and editing, J.-E.M., M.K., Y.M. and K.E.G.; visualization, J.-E.M.; supervision, Y.M.; project administration, Y.M.; funding acquisition, Y.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding. The APC was funded by the authors.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article as it is based on a systematic review of previously published literature. All referenced sources are publicly available and cited within the manuscript.
Acknowledgments
The authors would like to acknowledge the support of the LaSTI Laboratory at ENSA Khouribga, Sultan Moulay Slimane University, for providing access to academic resources and guidance throughout the research process. We also thank our colleagues for their constructive feedback during the manuscript revision phase.
Conflicts of Interest
The authors declare no conflicts of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| A2C | Actor-Critic |
| AI | Artificial Intelligence |
| BiLSTM | Bidirectional Long Short-Term Memory |
| CNN | Convolutional Neural Network |
| DDoS | Distributed Denial-of-Service |
| DL | Deep Learning |
| DQN | Deep Q-Learning |
| GAN | Generative Adversarial Network |
| GNN | Graph Neural Network |
| GDPR | General Data Protection Regulation |
| HAI | Hybrid AI |
| HHFL | Hierarchical Hybrid Federated Learning |
| IDS | Intrusion Detection System |
| IID | Independent and Identically Distributed |
| IoT | Internet of Things |
| FDL | Federated Deep Learning |
| FL | Federated Learning |
| FML | Federated Machine Learning |
| HE | Homomorphic Encryption |
| HFL | Horizontal Federated Learning |
| ML | Machine Learning |
| MPC | Multi-Party Computation |
| LIME | Local Interpretable Model-Agnostic Explanations |
| LLM | Large Language Models |
| RNN | Recurrent Neural Network |
| SHAP | SHapley Additive exPlanations |
| SLR | Systematic Literature Review |
| SplitNN | Split Neural Network |
| SVM | Support Vector Machine |
| VFL | Vertical Federated Learning |
References
- Saeed, S.; Altamimi, S.A.; Alkayyal, N.A.; Alshehri, E.; Alabbad, D.A. Digital transformation and cybersecurity challenges for business resilience: Issues and recommendations. Sensors 2023, 23, 6666. [Google Scholar] [CrossRef] [PubMed]
- Cassidy, A.A.T.J.; Fuad, A.; As Shofy, M.U.A. Emerging trends and challenges in digital crime: A study of cyber criminal tactics and countermeasures. TechComp Innov. J. Comput. Sci. Technol. 2024, 1, 38–45. [Google Scholar] [CrossRef]
- Cabaj, K.; Kotulski, Z.; Ksiezopolski, B.; Mazurczyk, W. Cybersecurity: Trends, issues, and challenges. EURASIP J. Inf. Secur. 2018, 2018, 10. [Google Scholar] [CrossRef]
- Mustapha, I.; Vaicondam, Y.; Jahanzeb, A.; Usmanovich, B.A.; Yusof, S.H.B. Cybersecurity challenges and solutions in the fintech mobile app ecosystem. Int. J. Interact. Mob. Technol. (iJIM) 2023, 17, 100–116. [Google Scholar] [CrossRef]
- Dickinson, B.; Chiock, M. Guest editorial: Countering security issues in the digital world. J. Pet. Technol. 2019, 71, 14–15. [Google Scholar] [CrossRef]
- Oh, S.H.; Jeong, M.K.; Kim, H.C.; Park, J. Applying reinforcement learning for enhanced cybersecurity against adversarial simulation. Sensors 2023, 23, 3000. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in Internet of Things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Martinez, J.; Iglesias Comesaña, C.; Nieto, P.G. Review: Machine learning techniques applied to cybersecurity. Int. J. Mach. Learn. Cybern. 2019, 10, 2823–2836. [Google Scholar] [CrossRef]
- Abrahams, T.O.; Okoli, U.; Obi, O.C.; Adewusi, A.O. Machine learning in cybersecurity: A review of threat detection and defense mechanisms. World J. Adv. Res. Rev. 2024, 21, 2286–2295. [Google Scholar] [CrossRef]
- Alzaabi, A.; Talib, M.A.; Nassif, A.B.; Sajwani, A.; Einea, O. A systematic literature review on machine learning in object detection security. In Proceedings of the 2020 IEEE 5th International Conference on Computing Communication and Automation (ICCCA), Greater Noida, India, 30–31 October 2020. [Google Scholar] [CrossRef]
- Han, W.; Peng, J.; Yu, J.; Kang, J.; Lu, J.; Niyato, D. Heterogeneous data-aware federated learning for intrusion detection systems via meta-sampling in artificial intelligence of things. IEEE Internet Things J. 2024, 11, 13340–13354. [Google Scholar] [CrossRef]
- Khraisat, A.; Alazab, A.; Singh, S.; Jan, T.; Gopez, A.J. Survey on federated learning for intrusion detection system: Concept, architectures, aggregation strategies, challenges, and future directions. ACM Comput. Surv. 2024, 57, 7. [Google Scholar] [CrossRef]
- Torre, D.; Chennamaneni, A.; Jo, J.; Vyas, G.; Sabrsula, B. Towards enhancing privacy-preservation of a federated learning CNN intrusion detection system in IoT: Method and empirical study. ACM Trans. Softw. Eng. Methodol. 2024, 34, 53. [Google Scholar] [CrossRef]
- Raza, M.; Saeed, M.J.; Riaz, M.B.; Sattar, M.A. Federated learning for privacy-preserving intrusion detection in software-defined networks. IEEE Access 2024, 12, 69551–69567. [Google Scholar] [CrossRef]
- Podešva, L.; Koch, M.; Luhan, J. Investment models for cybersecurity and information security of businesses—Systematic literature review. In Proceedings of the International Management Conference, Bucharest, Romania, 3–4 November 2022. [Google Scholar] [CrossRef]
- Khaw, T.Y.; Amran, A.; Teoh, A. Building a thematic framework of cybersecurity: A systematic literature review approach. J. Syst. Inf. Technol. 2024, 26, 234–256. [Google Scholar] [CrossRef]
- Monani, A.; Bhusnale, O.; Borade, K.; Madali, R. Analysing cyber threats: A comprehensive literature review on data-driven approaches. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2023, 9, 188–193. [Google Scholar] [CrossRef]
- Van Eck, N.J.; Waltman, L. Software survey: VOSviewer, a computer program for bibliometric mapping. Scientometrics 2010, 84, 523–538. [Google Scholar] [CrossRef] [PubMed]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Moher, D. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Amin, Z.M.; Anwar, N.; Shoid, M.S.M.; Samuri, S. A systematic literature review for modeling a cyber risk assessment framework. Environ.-Behav. Proc. J. 2024, 9, 189–195. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine learning and deep learning methods for cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Ali, R.; Ali, A.; Iqbal, F.; Khattak, A.; Aleem, S. A systematic review of artificial intelligence and machine learning techniques for cybersecurity. In Big Data and Security. ICBDS 2019. Communications in Computer and Information Science; Springer: Singapore, 2019; pp. 584–593. [Google Scholar] [CrossRef]
- Tulsyan, R.; Shukla, P.; Singh, T.; Bhardwaj, A. Cybersecurity threat detection using machine learning. Int. J. Sci. Res. Eng. Manag. 2024, 8, 1–6. [Google Scholar] [CrossRef]
- Kotadia, A.; Masalia, B.; Mehra, O.; Pathak, L. Machine learning for threat detection in software. Int. J. Innov. Sci. Res. Technol. 2024, 9, 2402–2413. [Google Scholar] [CrossRef]
- AlSalem, T.; Almaiah, M.A.; Lutfi, A. Cybersecurity risk analysis in the IoT: A systematic review. Electronics 2023, 12, 3958. [Google Scholar] [CrossRef]
- Laato, S.; Farooq, A.; Tenhunen, H.; Pitkamaki, T.; Hakkala, A.; Airola, A. AI in cybersecurity education: A systematic literature review of studies on cybersecurity MOOCs. In Proceedings of the 2020 IEEE 20th International Conference on Advanced Learning Technologies (ICALT), Tartu, Estonia, 6–9 July 2020. [Google Scholar] [CrossRef]
- Aiyanyo, I.D.; Samuel, H.W.; Lim, H. A systematic review of defensive and offensive cybersecurity with machine learning. Appl. Sci. 2020, 10, 5811. [Google Scholar] [CrossRef]
- Khaleel, Y.L.; Habeeb, M.A.; Albahri, A.S.; Al-Quraishi, T.; Albahri, O.; Alamoodi, A.H.; Layth, Y. Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods. J. Intell. Syst. 2024, 33, 20240153. [Google Scholar] [CrossRef]
- Thawait, N.K. Machine learning in cybersecurity: Applications, challenges, and future directions. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2024, 10, 16–27. [Google Scholar] [CrossRef]
- McCarthy, A.; Ghadafi, E.; Andriotis, P.; Legg, P. Functionality-preserving adversarial machine learning for robust classification in cybersecurity and intrusion detection domains: A survey. J. Cybersecur. Priv. 2022, 2, 154–190. [Google Scholar] [CrossRef]
- Handa, A.; Sharma, A.; Shukla, S. Machine learning in cybersecurity: A review. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2019, 9, e1306. [Google Scholar] [CrossRef]
- Dua, S.; Du, X. Data Mining and Machine Learning in Cybersecurity; Taylor & Francis: London, UK, 2011. [Google Scholar] [CrossRef]
- Salloum, S.; Alshurideh, M.; Elnagar, A.; Shaalan, K. Machine learning and deep learning techniques for cybersecurity: A review. In Proceedings of the International Conference on Artificial Intelligence and Computer Vision (AICV2020), Cairo, Egypt, 8–10 April 2020. [Google Scholar] [CrossRef]
- Liu, Q.; Li, P.; Zhao, W.; Cai, W.; Yu, S.; Leung, V.C.M. A survey on security threats and defensive techniques of machine learning: A data-driven view. IEEE Access 2018, 6, 12103–12117. [Google Scholar] [CrossRef]
- Ahmad, R.; Alsmadi, I. Machine learning approaches to IoT security: A systematic literature review. Internet Things 2021, 14, 100365. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.; Xu, M. A survey on machine learning techniques for cyber security in the last decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Emmanni, P.S. Federated learning for cybersecurity in edge and cloud computing. Int. J. Comput. Eng. 2024, 5, 27–38. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.J.; Yan, Z.; Wang, K. 2D Federated Learning for Personalized Human Activity Recognition in Cyber-Physical-Social Systems. IEEE Trans. Netw. Sci. Eng. 2022, 9, 3934–3944. [Google Scholar] [CrossRef]
- Alazab, M.; Rm, S.; Parimala, M.; Maddikunta, P.; Gadekallu, T.; Pham, Q.-V. Federated learning for cybersecurity concepts, challenges, and future directions. IEEE Trans. Ind. Inform. 2022, 18, 3501–3509. [Google Scholar] [CrossRef]
- Huang, H.J.; Iskandarov, B.; Rahman, M.; Otal, H.T.; Canbaz, M.A. Federated learning in adversarial environments: Testbed design and poisoning resilience in cybersecurity. arXiv 2024. [Google Scholar] [CrossRef]
- Vyas, A.; Lin, P.-C.; Hwang, R.-H.; Tripathi, M. Privacy-preserving federated learning for intrusion detection in IoT environments: A survey. IEEE Access 2024, 12, 127018–127050. [Google Scholar] [CrossRef]
- Azeez, S.D.; Ilyas, M.; Bako, I.M. Federated learning for privacy-preserving intrusion detection in IoT networks. In Proceedings of the 2024 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Istanbul, Turkiye, 23–25 May 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Ghimire, B.; Rawat, D. Recent advances on federated learning for cybersecurity and cybersecurity for federated learning for Internet of Things. IEEE Internet Things J. 2022, 9, 8229–8249. [Google Scholar] [CrossRef]
- Mahmoud, Q.H.; Sadaqat, M. Federated learning for cybersecurity in the Internet of Things: A comprehensive survey. Future Internet 2021, 16, 374. [Google Scholar] [CrossRef]
- Mohawesh, R.; Maqsood, S.; Jararweh, Y.; Salameh, H. Federated learning support for cybersecurity: Fundamentals, applications, and opportunities. In Proceedings of the 2023 International Conference on Intelligent Computing, Communication, Networking and Services (ICCNS), Valencia, Spain,, 19–22 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 50–56. [Google Scholar] [CrossRef]
- Ogundipe, M.; Shi, X. Detecting Cyber Threats and Enhancing Security in IoT Devices: A Federated Learning Approach. In Proceedings of the 2024 International Conference on Global Aeronautical Engineering and Satellite Technology (GAST), Marrakesh, Morocco, 24–26 April 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Wardana, A.A.; Sukarno, P. Taxonomy and survey of collaborative intrusion detection system using federated learning. ACM Comput. Surv. 2024, 57, 1–36. [Google Scholar] [CrossRef]
- Mazid, A.; Kirmani, S.; Manaullah; Yadav, M. FL-IDPP: A Federated Learning-Based Intrusion Detection Approach With Privacy Preservation. Trans. Emerg. Telecommun. Technol. 2024, 36, e70039. [Google Scholar] [CrossRef]
- Arisdakessian, S.; Wahab, O.A.; Mourad, A.; Otrok, H.; Guizani, M. A survey on IoT intrusion detection: Federated learning, game theory, social psychology, and explainable AI as future directions. IEEE Internet Things J. 2023, 10, 4059–4092. [Google Scholar] [CrossRef]
- Zhang, T.; He, C.; Ma, T.-S.; Ma, M.; Avestimehr, S. Federated learning for Internet of Things. In Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems, Coimbra, Portugal, 15–17 November 2021. [Google Scholar] [CrossRef]
- Salim, M.; Camacho, D.; Park, J. Digital Twin and federated learning enabled cyberthreat detection system for IoT networks. Future Gener. Comput. Syst. 2024, 161, 701–713. [Google Scholar] [CrossRef]
- Folino, F.; Folino, G.; Pisani, F.S.; Sabatino, P.; Pontieri, L. A scalable vertical federated learning framework for analytics in the cybersecurity domain. In Proceedings of the 2024 32nd Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Dublin, Ireland, 20–22 March 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 245–252. [Google Scholar] [CrossRef]
- Li, J.; Tong, X.; Liu, J.; Cheng, L. An efficient federated learning system for network intrusion detection. IEEE Syst. J. 2023, 17, 2455–2464. [Google Scholar] [CrossRef]
- Alsaleh, S.; Menai, M.; Al-Ahmadi, S. Federated Learning-Based Model to Lightweight IDSs for Heterogeneous IoT Networks: State-of-the-Art, Challenges, and Future Directions. IEEE Access 2024, 12, 134256–134272. [Google Scholar] [CrossRef]
- Mahmud, S.A.; Islam, N.; Islam, Z.; Rahman, Z.; Mehedi, S.T. Privacy-Preserving Federated Learning-Based Intrusion Detection Technique for Cyber-Physical Systems. Mathematics 2024, 12, 3194. [Google Scholar] [CrossRef]
- Neto, H.N.C.; Hribar, J.; Dusparic, I.; Fernandes, N.C.; Mattos, D.M.F. FedSBS: Federated-Learning participant-selection method for Intrusion Detection Systems. Comput. Netw. 2024, 244, 110351. [Google Scholar] [CrossRef]
- Yang, F.; Cao, Y.; Wen, B.; Comaniciu, C.; Subbalakshmi, K. Fed-FIDS: A efficient federated learning-based intrusion detection framework. In Proceedings of the MILCOM 2024–IEEE Military Communications Conference, Washington, DC, USA, 28 October–1 November 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 987–992. [Google Scholar] [CrossRef]
- Tareq, I.; Elbagoury, B.; El-Regaily, S.; El-Horbaty, E.S.M. A survey about deep learning and federated learning in cybersecurity. Period. Eng. Nat. Sci. (PEN) 2024, 12, 75–100. [Google Scholar] [CrossRef]
- Alazab, A.; Khraisat, A.; Singh, S.; Jan, T.; Alazab, M. Enhancing privacy-preserving intrusion detection through federated learning. Electronics 2023, 12, 1529. [Google Scholar] [CrossRef]
- Novikova, E.; Golubev, S.A. Federated learning based approach to intrusion detection. In Proceedings of the 2023 V International Conference on Control in Technical Systems (CTS), Saint Petersburg, Russia, 26–28 September 2023; IEEE: Piscataway, NJ, USA, 2024; pp. 160–163. [Google Scholar] [CrossRef]
- Patil, V.; Moolchandani, J.; Dubey, A. A review on advancing cybersecurity frameworks by integrating machine intelligence with federated learning. In Proceedings of the 2024 International Conference on IoT Based Control Networks and Intelligent Systems (ICICNIS), Bengaluru, India, 17–18 December 2024; pp. 180–187. [Google Scholar] [CrossRef]
- Tucker, E.; Hossain, R.; Singh, V. Performance Evaluation of Vertical Federated Machine Learning Against Adversarial Threats on Wide-Area Control System. In Proceedings of the 2024 Resilience Week (RWS), Austin, TX, USA, 3–5 December 2024; pp. 1–8. [Google Scholar] [CrossRef]
- Gaba, S.; Budhiraja, I.; Kumar, V.; Garg, S.; Hassan, M. An innovative multi-agent approach for robust cyber-physical systems using vertical federated learning. Ad Hoc Netw. 2024, 163, 103578. [Google Scholar] [CrossRef]
- Pingulkar, S.; Pawade, D. Federated Learning Architectures for Credit Risk Assessment: A Comparative Analysis of Vertical, Horizontal, and Transfer Learning Approaches. In Proceedings of the 2024 IEEE International Conference on Blockchain and Distributed Systems Security (ICBDS), Pune, India, 17–19 October 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Javeed, D.; Saeed, M.; Adil, M.; Kumar, P.; Jolfaei, A. A federated learning-based zero trust intrusion detection system for Internet of Things. Ad Hoc Netw. 2024, 162, 103540. [Google Scholar] [CrossRef]
- Dong, T.; Li, S.; Qiu, H.; Lu, J. An Interpretable Federated Learning-based Network Intrusion Detection Framework. arXiv 2022, arXiv:2201.03134. [Google Scholar] [CrossRef]
- Popoola, S.; Gui, G.; Adebisi, B.; Hammoudeh, M.; Gačanin, H. Federated Deep Learning for Collaborative Intrusion Detection in Heterogeneous Networks. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Norman, OK, USA, 27–30 September 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Popoola, S.; Imoize, A.; Hammoudeh, M.; Adebisi, B.; Jogunola, O.; Aibinu, A. Federated Deep Learning for Intrusion Detection in Consumer-Centric Internet of Things. IEEE Trans. Consum. Electron. 2023, 70, 1610–1622. [Google Scholar] [CrossRef]
- Tabassum, A.; Erbad, A.; Lebda, W.; Mohamed, A.; Guizani, M. FEDGAN-IDS: Privacy-preserving IDS using GAN and Federated Learning. Comput. Commun. 2022, 192, 299–310. [Google Scholar] [CrossRef]
- Zeng, Q.; Olatunde-Salawu, S.; Naït-Abdesselam, F. FGA-IDS: A Federated Learning and GAN-Augmented Intrusion Detection System for UAV Networks. In Proceedings of the 2024 IEEE International Conference on Collaboration and Internet Computing (CIC), Washington, DC, USA, 28–30 October 2024; pp. 50–59. [Google Scholar] [CrossRef]
- Liang, J.; Sadiq, M.; Yang, G.; Jiang, K.; Cai, T.; Ma, M. Enhanced Collaborative Intrusion Detection Using Blockchain and Decentralized FL with GANs. Eng. Appl. Artif. Intell. 2024, 135, 108862. [Google Scholar] [CrossRef]
- Sun, H.; Zhu, W.; Sun, Z.; Cao, M.; Liu, W. FMDL: Federated Mutual Distillation Learning for Defending Backdoor Attacks. Electronics 2023, 12, 4838. [Google Scholar] [CrossRef]
- Searle, R.; Gururaj, P.; Gaikwad, S.; Kannur, K. Secure federated machine learning with flexible topology and distributed privacy controls. SPIE Proc. 2023, 12542, 125420C. [Google Scholar] [CrossRef]
- Wang, Z.; Li, X.; Wu, T.; Xu, C.; Zhang, L. A Credibility-aware Swarm-Federated Deep Learning Framework in Internet of Vehicles. Digit. Commun. Netw. 2024, 10, 150–157. [Google Scholar] [CrossRef]
- Ferrag, M.; Friha, O.; Maglaras, L.; Janicke, H.; Shu, L. Federated Deep Learning for Cyber Security in the Internet of Things: Concepts, Applications, and Experimental Analysis. IEEE Access 2021, 9, 138509–138542. [Google Scholar] [CrossRef]
- Preuveneers, D.; Rimmer, V.; Tsingenopoulos, I.; Spooren, J.; Joosen, W.; Ilie-Zudor, E. Chained Anomaly Detection Models for Federated Learning: An Intrusion Detection Case Study. Appl. Sci. 2018, 8, 2663. [Google Scholar] [CrossRef]
- Thantharate, P.; Anurag, T. CYBRIA—Pioneering Federated Learning for Privacy-Aware Cybersecurity with Brilliance. In Proceedings of the 2023 IEEE 20th International Conference on Smart Communities: Improving Quality of Life using AI, Robotics and IoT (HONET), Boca Raton, FL, USA, 4–6 December 2023; pp. 56–61. [Google Scholar] [CrossRef]
- Corin, R.; Siracusa, D. FLAD: Adaptive Federated Learning for DDoS Attack Detection. arXiv 2023, arXiv:2205.06661. [Google Scholar] [CrossRef]
- Chen, J.; Huang, G.; Zheng, H.; Yu, S.; Jiang, W.; Cui, C. Graph-Fraudster: Adversarial Attacks on Graph Neural Network-Based Vertical Federated Learning. IEEE Trans. Comput. Soc. Syst. 2022, 10, 492–506. [Google Scholar] [CrossRef]
- Idrissi, M.; Alami, H.; Mahdaouy, A.; Mekki, A.; Oualil, S.; Yartaoui, Z.; Berrada, I. Fed-ANIDS: Federated learning for anomaly-based network intrusion detection systems. Expert Syst. Appl. 2023, 234, 121000. [Google Scholar] [CrossRef]
- Zhao, H.; Liu, L.; Fan, F.; Zhang, H.; Ma, Y. An Adaptive Federated Learning Intrusion Detection System Based on GAN under IoT. In Proceedings of the 2024 3rd Asia Conference on Algorithms, Computing and Machine Learning, Shanghai, China, 22–24 March 2024. [Google Scholar] [CrossRef]
- Quyen, N.H.; Duy, P.T.; Vy, N.C.; Hien, D.T.T.; Pham, V. Federated Intrusion Detection on Non-IID Data for IIoT Networks Using GAN and RL. In Proceedings of the AI Applications and Innovations, Wuhan, China, 25–27 October 2024; pp. 364–381. [Google Scholar] [CrossRef]
- Chatterjee, S.; Hanawal, M.K. Federated learning for intrusion detection in IoT security: A hybrid ensemble approach. arXiv 2021, arXiv:2106.15349. [Google Scholar]
- Chowdhury, Z.A.; Rahman, M.M.; Azhar, T. Advances in intrusion detection systems: Integrating machine learning, deep learning, IoT, and federated learning. Int. J. Comput. Appl. 2024, 186, 21–28. [Google Scholar] [CrossRef]
- Shen, J.; Yan, J.; Liu, B.; Sun, Y.; Wu, Y.; Wang, R. Effective intrusion detection in heterogeneous internet-of-things networks via ensemble knowledge distillation-based federated learning. arXiv 2024, arXiv:2401.11968. [Google Scholar]
- Alqattan, D.; Sun, R.; Liang, H.; Nicosia, G.; Snasel, V.; Ranjan, R.; Ojha, V. Security Assessment of Hierarchical Federated Deep Learning. arXiv 2024, arXiv:2408.10752. [Google Scholar] [CrossRef]
- Mohammadpour, M.; Mostafavi, S. Decentralized Federated Learning in IoT Environments: A Hierarchical Approach. In Proceedings of the 2023 13th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 1–2 November 2023; pp. 446–451. [Google Scholar] [CrossRef]
- Wainakh, A.; Guinea, A.; Grube, T.; Mühlhäuser, M. Enhancing Privacy via Hierarchical Federated Learning. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 7–11 September 2020; pp. 344–347. [Google Scholar] [CrossRef]
- Sarhan, M.; Lo, W.; Layeghy, S.; Portmann, M. HBFL: A Hierarchical Blockchain-based Federated Learning Framework for a Collaborative IoT Intrusion Detection. arXiv 2022, arXiv:2204.04254. [Google Scholar] [CrossRef]
- Zhou, H.; Zheng, Y.; Huang, H.; Shu, J.; Jia, X. Toward Robust Hierarchical Federated Learning in Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2023, 24, 5600–5614. [Google Scholar] [CrossRef]
- Gao, J.; Li, Y.; Zhao, Y.; Campbell, B. H-FedSN: Personalized Sparse Networks for Efficient and Accurate Hierarchical Federated Learning for IoT Applications. arXiv 2024, arXiv:2412.06210. [Google Scholar] [CrossRef]
- Praharaj, L.; Gupta, M.; Gupta, D. Hierarchical Federated Transfer Learning and Digital Twin Enhanced Secure Cooperative Smart Farming. In Proceedings of the 2023 IEEE International Conference on Big Data (BigData), Sorrento, Italy, 15–18 December 2023; pp. 3304–3313. [Google Scholar] [CrossRef]
- Subramanian, G.; Chinnadurai, M. Hybrid quantum enhanced federated learning for cyber attack detection. Sci. Rep. 2024, 14, 32038. [Google Scholar] [CrossRef]
- Ullah, S.; Shah, M.; Anjum, A. Quantum Enhanced Federated Learning with Differential Privacy. In Proceedings of the 2024 International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 9–10 December 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Chehimi, M.; Saad, W. Quantum Federated Learning with Quantum Data. In Proceedings of the ICASSP 2022–2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Singapore, 23–27 May 2022; pp. 8617–8621. [Google Scholar] [CrossRef]
- Kannan, E.; Ravikumar, S.; Carmel Mary Belinda, M.J.; Vijay, K. Revolutionizing Machine Learning Security: The Role of Quantum-Enhanced Federated Learning. In Proceedings of the 2024 International Conference on Emerging Research in Computational Science (ICERCS), Coimbatore, India, 12–14 December 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Chaurasia, N.; Ram, M.; Verma, P.; Mehta, N.; Bharot, N. A federated learning approach to network intrusion detection using residual networks in industrial IoT networks. J. Supercomput. 2024, 80, 18325–18346. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Sitnikova, E.; Aboutorab, N. X-IIoTID: A Connectivity-Agnostic and Device-Agnostic Intrusion Data Set for Industrial Internet of Things. IEEE Internet Things J. 2021, 9, 3962–3977. [Google Scholar] [CrossRef]
- Ning, W.; Qi, Q.; Wang, J.; Zhu, M.; Li, S.; Yang, G.; Liao, J. One Teacher is Enough: A Server-Clueless Federated Learning with Knowledge Distillation. IEEE Trans. Serv. Comput. 2024, 17, 2704–2718. [Google Scholar] [CrossRef]
- Zhang, L.; Shen, L.; Ding, L.; Tao, D.; Duan, L. Fine-tuning Global Model via Data-Free Knowledge Distillation for Non-IID Federated Learning. In Proceedings of the 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), New Orleans, LA, USA, 18–24 June 2022; pp. 10164–10173. [Google Scholar] [CrossRef]
- Gong, X.; Sharma, A.; Karanam, S.; Wu, Z.; Chen, T.; Doermann, D.; Innanje, A. Preserving Privacy in Federated Learning with Ensemble Cross-Domain Knowledge Distillation. arXiv 2022, arXiv:2209.04599. [Google Scholar] [CrossRef]
- Lyu, F.; Tang, C.; Deng, Y.; Liu, T.; Zhang, Y.; Zhang, Y. A Prototype-Based Knowledge Distillation Framework for Heterogeneous Federated Learning. In Proceedings of the 2023 IEEE 43rd International Conference on Distributed Computing Systems (ICDCS), Hong Kong, China, 18–21 July 2023; pp. 1–11. [Google Scholar] [CrossRef]
- Gohari, R.; Aliahmadipour, L.; Valipour, E. FedBrain-Distill: Communication-Efficient Federated Brain Tumor Classification Using Ensemble Knowledge Distillation on Non-IID Data. In Proceedings of the 2024 14th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 19–20 November 2024; pp. 49–54. [Google Scholar] [CrossRef]
- Wang, J.; Hu, J.; Mills, J.; Min, G.; Xia, M.; Georgalas, N. Federated Ensemble Model-Based Reinforcement Learning in Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 1848–1859. [Google Scholar] [CrossRef]
- Alharbi, E.; Marcolino, L.; Ni, Q.; Gouglidis, A. Robust Knowledge Distillation in Federated Learning: Counteracting Backdoor Attacks. arXiv 2025, arXiv:2502.00587. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Jalal, A.; Le, D.N.; Kumar, A. Federated learning with hybrid differential privacy for secure and reliable cross-IoT platform knowledge sharing. Secur. Priv. 2024, 7, e374. [Google Scholar] [CrossRef]
- Iqbal, M.; Tariq, A.; Adnan, M.; Din, I.; Qayyum, T. FL-ODP: An Optimized Differential Privacy Enabled Privacy Preserving Federated Learning. IEEE Access 2023, 11, 116674–116683. [Google Scholar] [CrossRef]
- Zhou, C.; Sun, Y.; Wang, D. Federated Learning with Gaussian Differential Privacy. In Proceedings of the 2020 2nd International Conference on Robotics, Intelligent Control and Artificial Intelligence, Shanghai, China, 17–19 October 2020. [Google Scholar] [CrossRef]
- Shan, F.; Mao, S.; Lu, Y.; Li, S. Differential Privacy Federated Learning: A Comprehensive Review. Int. J. Adv. Comput. Sci. Appl. 2024, 15. [Google Scholar] [CrossRef]
- Jalaeian, B.; Bastian, N. Neurosymbolic AI in Cybersecurity: Bridging Pattern Recognition and Symbolic Reasoning. In Proceedings of the MILCOM 2023–IEEE Military Communications Conference (MILCOM), Boston, MA, USA, 30 October–3 November 2023; pp. 268–273. [Google Scholar] [CrossRef]
- Yevdokymov, S. Neuro-symbolic models for ensuring cybersecurity in critical cyber-physical systems. Comput. Probl. Electr. Eng. 2024, 14, 42–50. [Google Scholar] [CrossRef]
- Rawat, D. Towards Neuro-Symbolic AI for Assured and Trustworthy Human-Autonomy Teaming. In Proceedings of the 2023 5th IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 1–4 November 2023; pp. 177–179. [Google Scholar] [CrossRef]
- Loevenich, J.; Adler, E.; Mercier, R.; Velazquez, A.; Lopes, R. Design of an Autonomous Cyber Defence Agent using Hybrid AI models. In Proceedings of the 2024 International Conference on Military Communication and Information Systems (ICMCIS), Koblenz, Germany, 23–24 April 2024; pp. 1–10. [Google Scholar] [CrossRef]
- Abdulboriy, A.; Shin, J. An Incremental Majority Voting Approach for Intrusion Detection System Based on Machine Learning. IEEE Access 2024, 12, 18972–18986. [Google Scholar] [CrossRef]
- Aswal, K.; Rajmohan, A.; Trc, A.; Mukund, S.; Panicker, V.; Dhivvya, J. Kavach: A Machine Learning based approach for enhancing the attack detection capability of firewalls. In Proceedings of the 2021 12th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kharagpur, India, 6–8 July 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Fotohi, R.; Aliee, F.; Farahani, B. A Lightweight and Secure Deep Learning Model for Privacy-Preserving Federated Learning in Intelligent Enterprises. IEEE Internet Things J. 2024, 11, 31988–31998. [Google Scholar] [CrossRef]
- Por, L.; Dai, Z.; Leem, S.; Chen, Y.; Yang, J.; Binbeshr, F.; Phan, K.; Ku, C. A Systematic Literature Review on AI-Based Methods and Challenges in Detecting Zero-Day Attacks. IEEE Access 2024, 12, 144150–144163. [Google Scholar] [CrossRef]
- Hosseinzadeh, M.; Hemmati, A.; Rahmani, A. Federated learning-based IoT: A systematic literature review. Int. J. Commun. Syst. 2022, 35, e5185. [Google Scholar] [CrossRef]
- Achuthan, K.; Ramanathan, S.; Srinivas, S.; Raman, R. Advancing cybersecurity and privacy with artificial intelligence: Current trends and future research directions. Front. Big Data 2024, 7, 1497535. [Google Scholar] [CrossRef] [PubMed]
- Ogundokun, R.; Misra, S.; Maskeliūnas, R.; Damaševičius, R. A Review on Federated Learning and Machine Learning Approaches: Categorization, Application Areas, and Blockchain Technology. Information 2022, 13, 263. [Google Scholar] [CrossRef]
- Akhter, N.; Mia, A.; Talukder, M. Python-Based Hybrid AI Models for Real-Time Grid Stability Analysis in Solar Energy Networks. Innov. Eng. J. 2024, 1, 10–70937. [Google Scholar] [CrossRef]
- Lo, S.; Lu, Q.; Wang, C.; Paik, H.; Zhu, L. A Systematic Literature Review on Federated Machine Learning. ACM Comput. Surv. (CSUR) 2020, 54, 1–39. [Google Scholar] [CrossRef]
- Khacha, A.; Aliouat, Z.; Harbi, Y.; Gherbi, C.; Saadouni, R.; Harous, S. Landscape of learning techniques for intrusion detection system in IoT: A systematic literature review. Comput. Electr. Eng. 2024, 120, 109725. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).