Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry
Abstract
1. Introduction
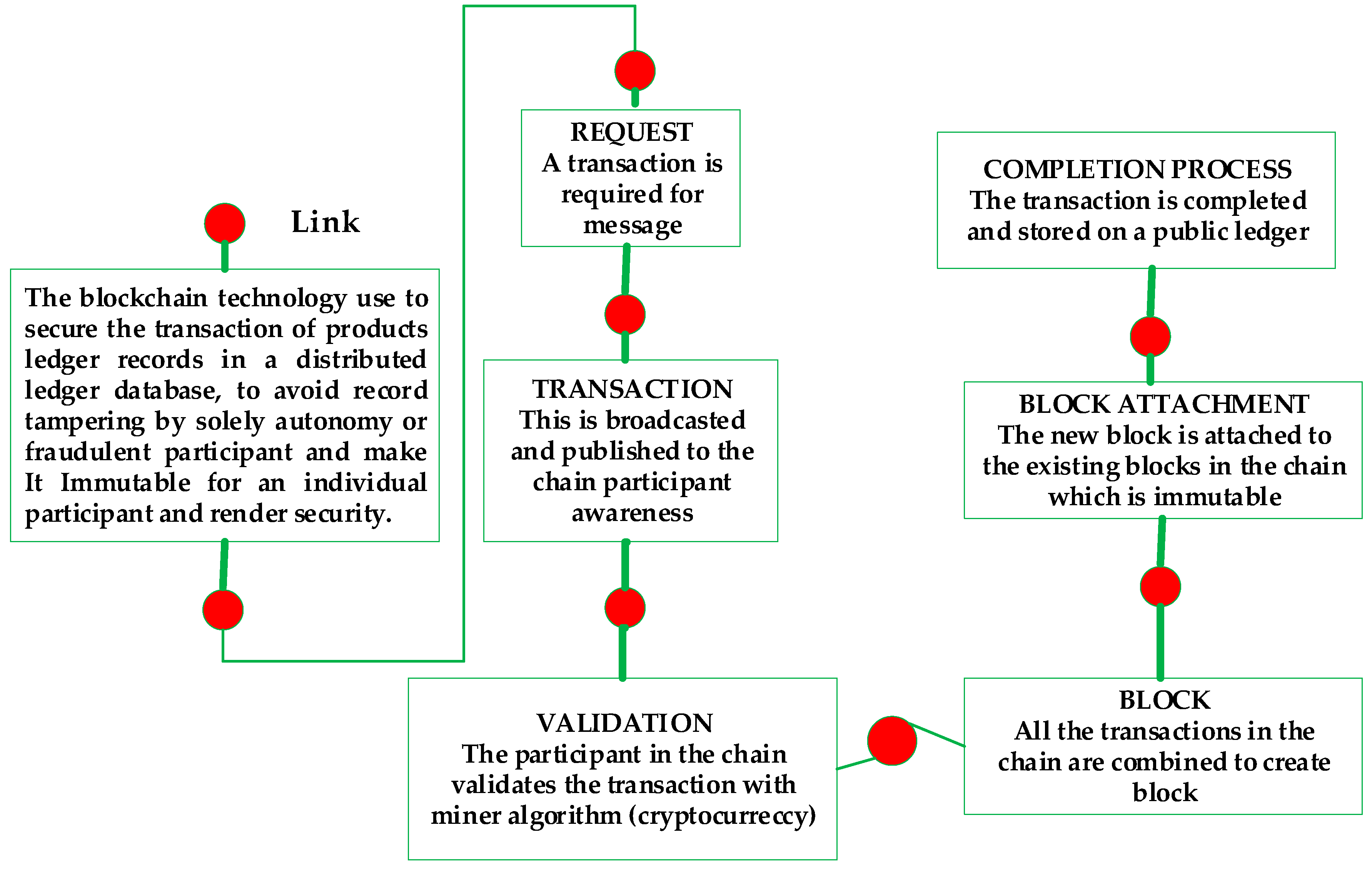
2. Blockchain and Informatics Technology Investigation
| y | is the vehicle longitudinal velocity (m/s) |
| r | is the yaw rate (%) |
| the wheel steering angle of the vehicle (rad) | |
| is the front wheels stiffness when curve (N/rad) | |
| is the rear wheels stiffness when curve (N/rad) | |
| is the length between CoG to front axle (m) | |
| is the length between CoG to rear axle (m) | |
| m | the mass of vehicle (kg) |
| Inertia moment around the Z-axis (kg/m2) |
| the mean speed at time t on the road section j in (m/s) | |
| is driver perception and response time (s) | |
| the vehicle distance + gap between vehicle | |
| g | is the acceleration due to gravity rate, 9.8 (m/s) |
| the frictional-road parameter at time period t on the road section j | |
| the level of road section j link during collection period t (%) | |
| t | is collection time period (s) |
| j | number of road sections. |
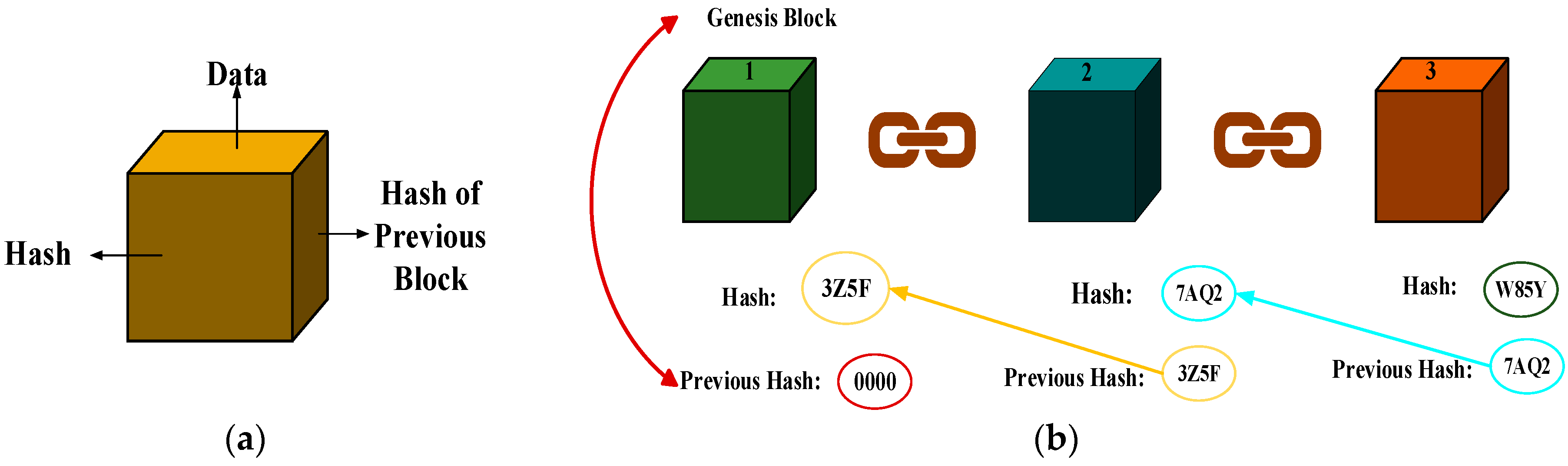
2.1. Blockchain Technology Types
- The public permissioned blockchain is a transparent and open permissioned-based Litecoin system, which allows anyone to update or review anything at a time required. This technology allows anybody to participate in managing the blockchain as public. It is also known as a permissioned blockchain without any centralized authority required for the verification process as found in the Ethereum, Litecoin, and Bitcoin technology [30]. This type of technology allows complete node running, easy transaction, review, or audit the blockchain by any participant in the Bitcoins/Litecoin (BTC/LTC) chain of blockchain explorer.
- Private blockchain is an advanced Bitcoin technology that is managed centrally by an individual or organization for adequate security. This permissioned-based blockchain does not allow negotiation of the distributed network management as found in the BankChain practices. This technology does not allow anyone to run a full node and start mining and does not grant transactions access or review/audit by anyone or individual on the blockchain. The private blockchain is a permissioned-based design for central authority and process authentication.
- The Consortium or Federated Blockchain eliminates the sole autonomy in the private blockchain by making sure there is more than one person in charge of chain management. Different authorities come together to make decisions that are good for the network such as a group of companies or representatives of individuals involved. It is also known as the hybrid blockchain because it combines both the characteristics of a public blockchain and the private blockchain. The R3 companies (New York City, NY, USA) and Energy Web Foundation (EWF) are open source and scalable blockchain platforms.
2.2. Secure Hashing Algorithm (SHA-1)
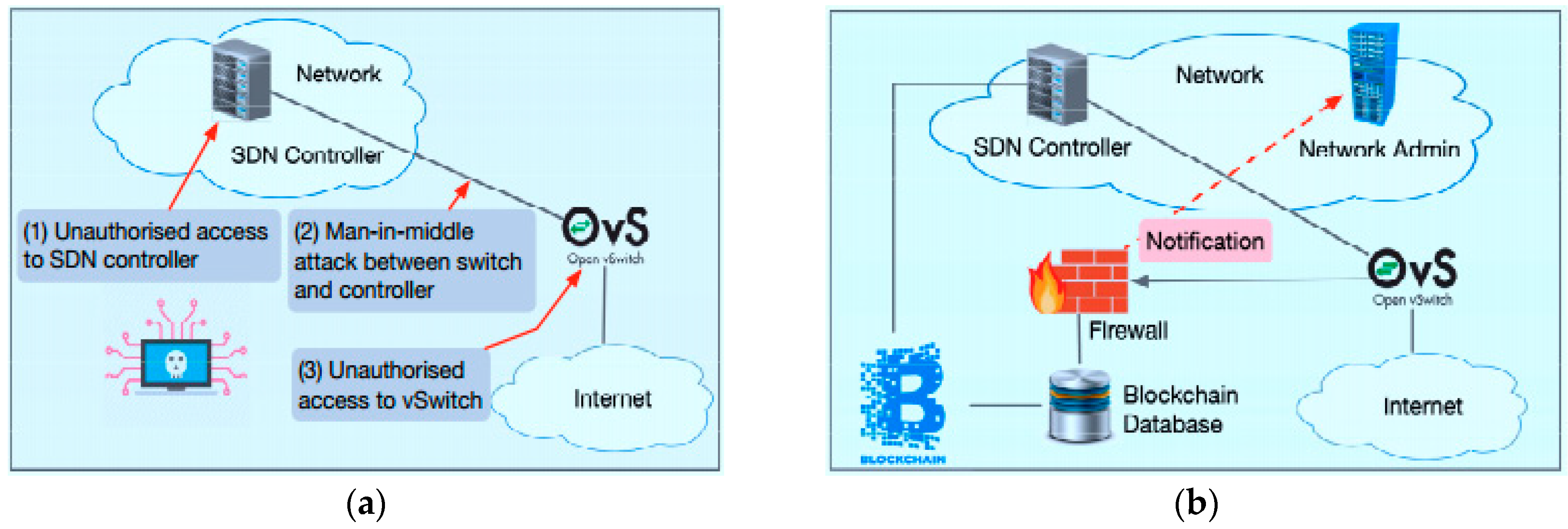
2.3. Problems Statement
3. Materials and Methods
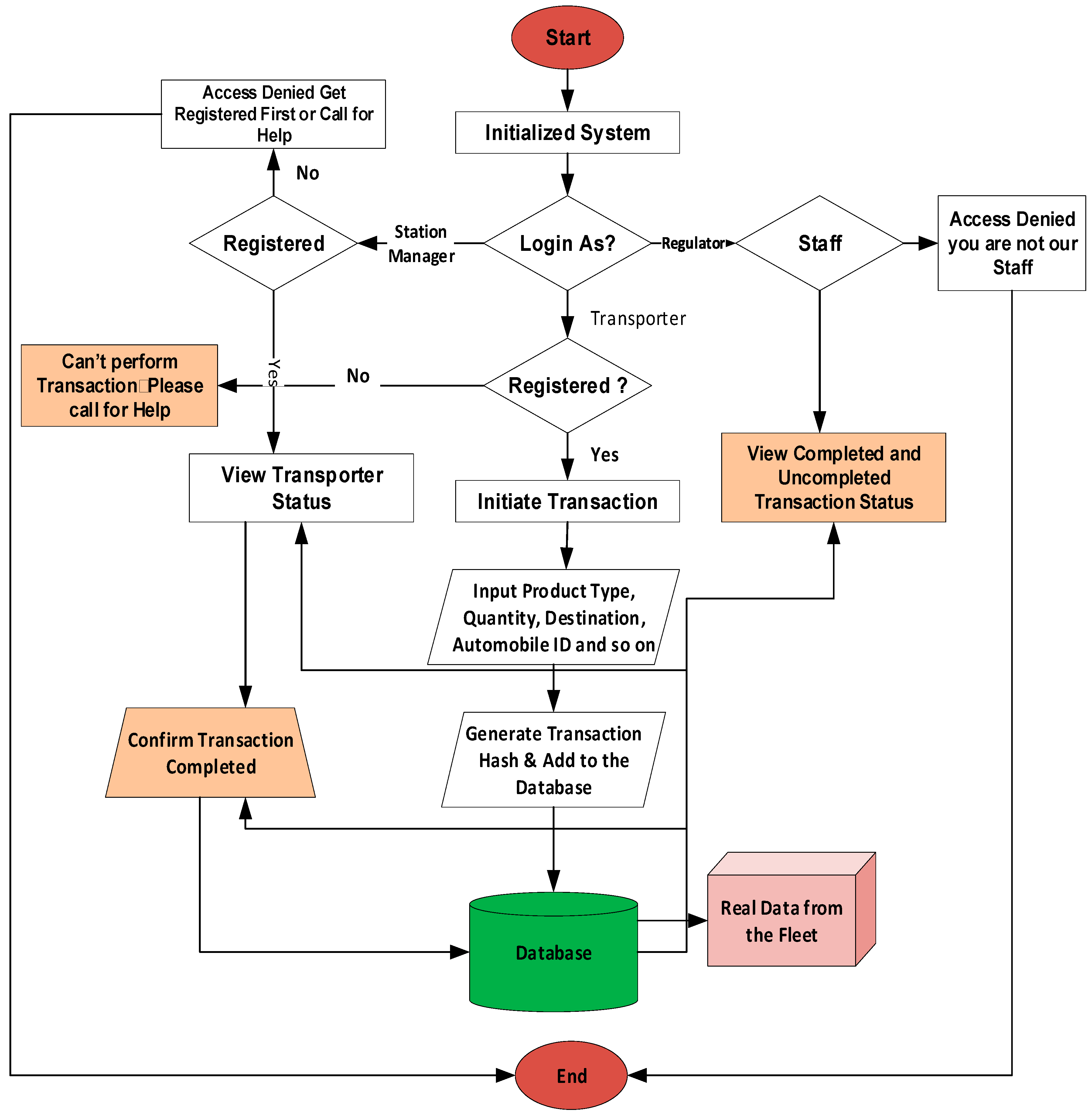
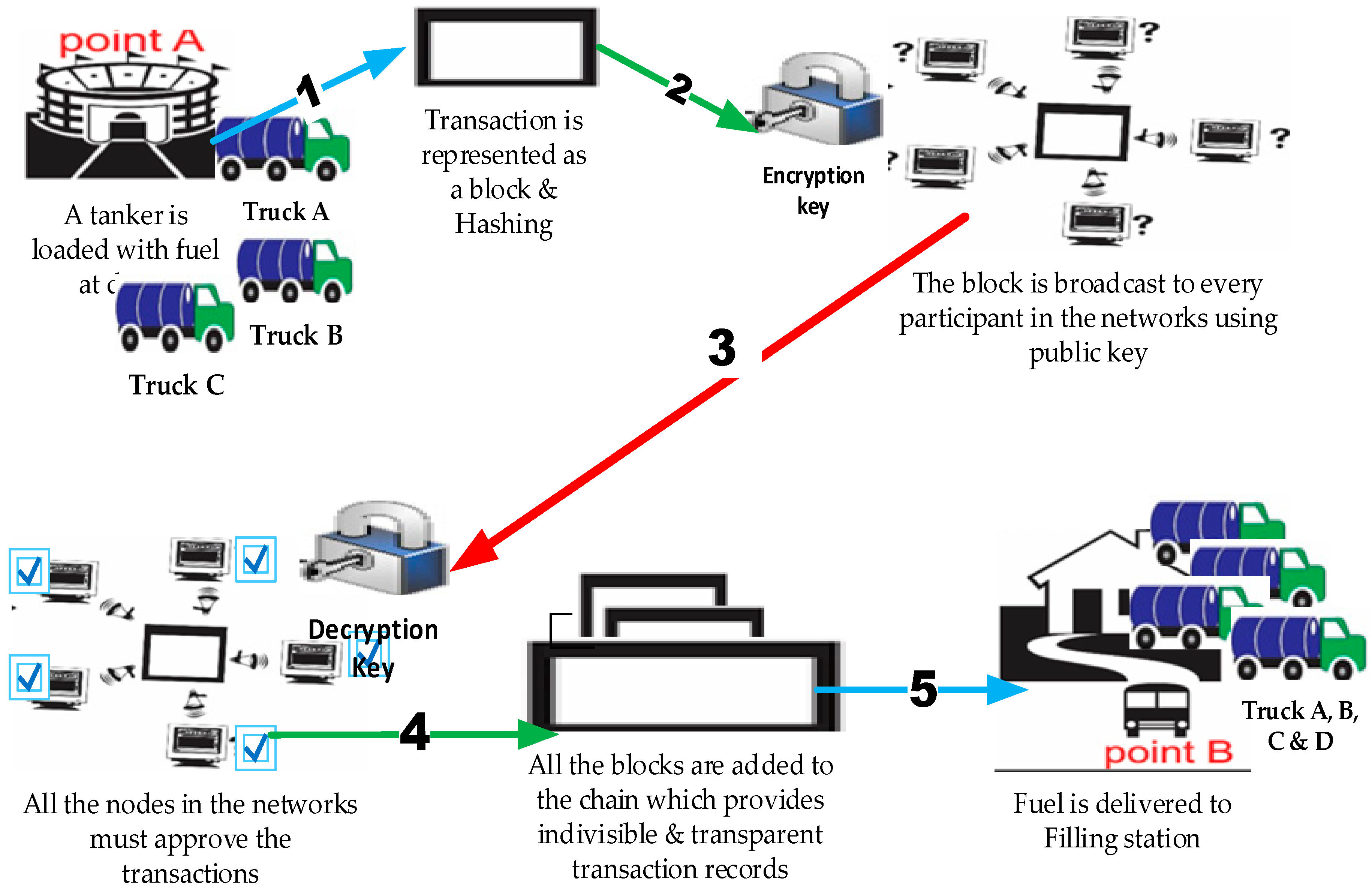
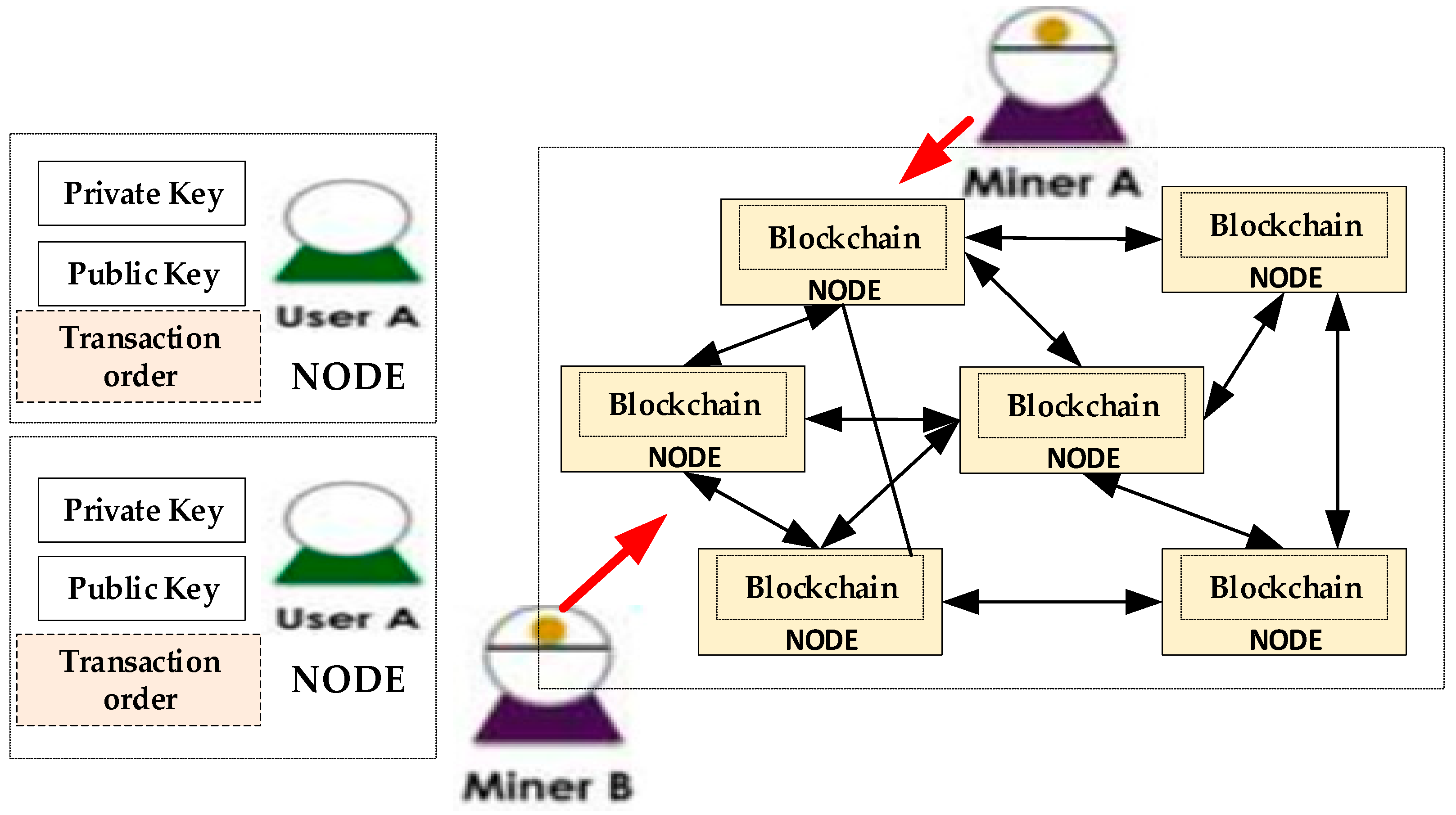
3.1. Blockchain Transactions Architecture for Petroleum Product Distribution
- Open Ledger Belief (OLB): This help every participant in this network/chain to see and aware of transaction and its content on the chain and then validate using mining (public key). Here are the procedures.
- i.
- The oil and gas products are transported between points A and B through the third-party (automobile conveyance).
- ii.
- The third-party (automobile conveyance) is not trusted with 44,000 L of transaction from point A to point B. The transaction relation between two parties is expressed as => φ and attached with link.
- iii.
- All transactions in the chain are validated using a public key for every participant agreement in the network.
- Decentralized ledger coding (DLC): This database helps govern the transaction in the chain/network with consensus agreement on the record updates without central authority or third-party negotiation. It has timestamp with unique credentials signature which makes all the transaction history in the chain immutable. These procedures are involved in the operation principle of DLC.
- i.
- Broadcasting and publishing a copy of transaction to the network as follows, φ, φ φ φ.
- ii.
- Synchronize the copy to ensure that transaction gets to all participants in the chain/network.
- iii.
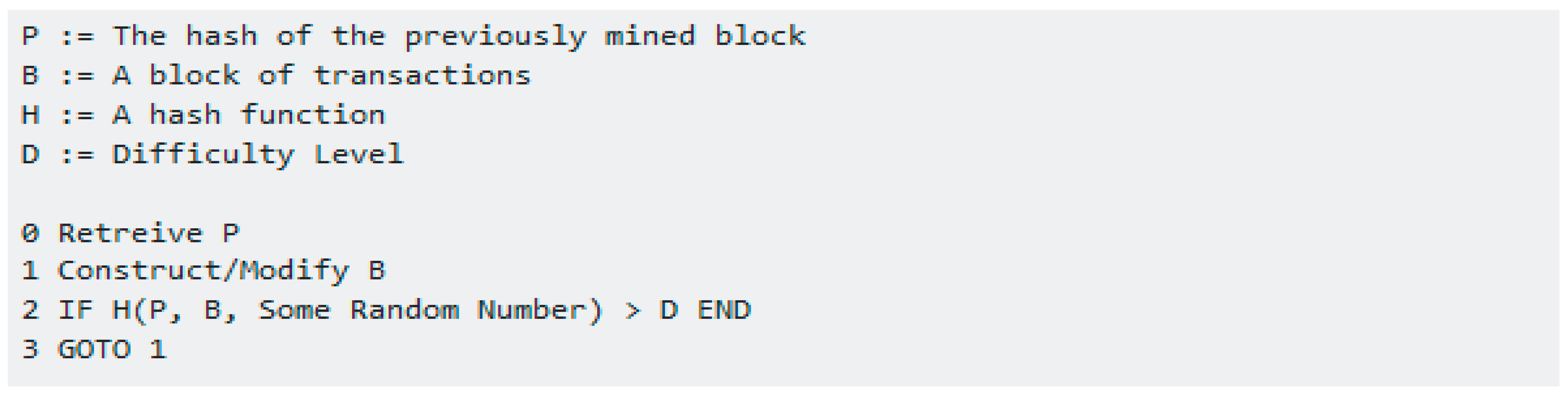
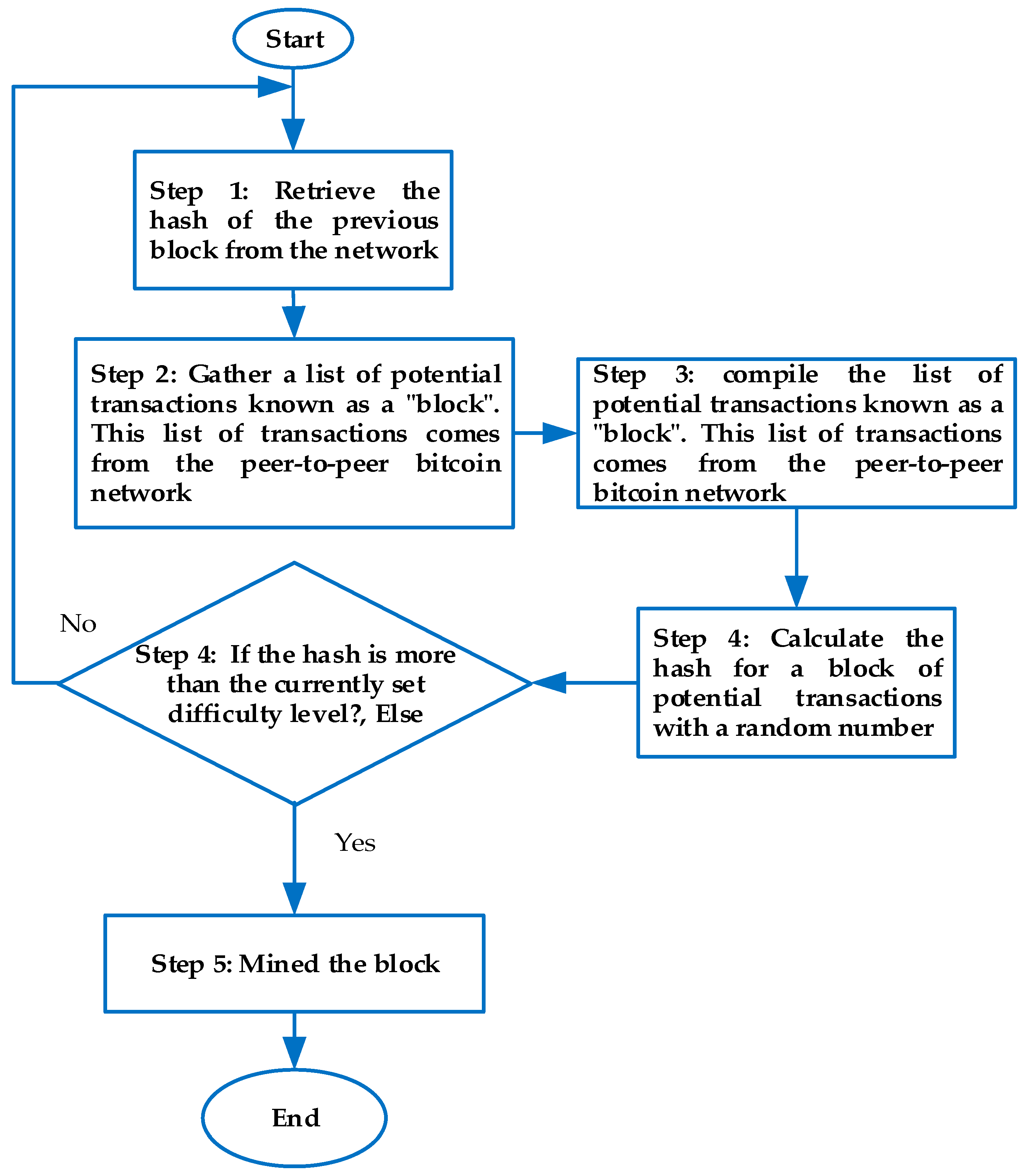
- Use a mining algorithm to validate the transaction by computing random hash number generation as a special key used by every participant in the network.
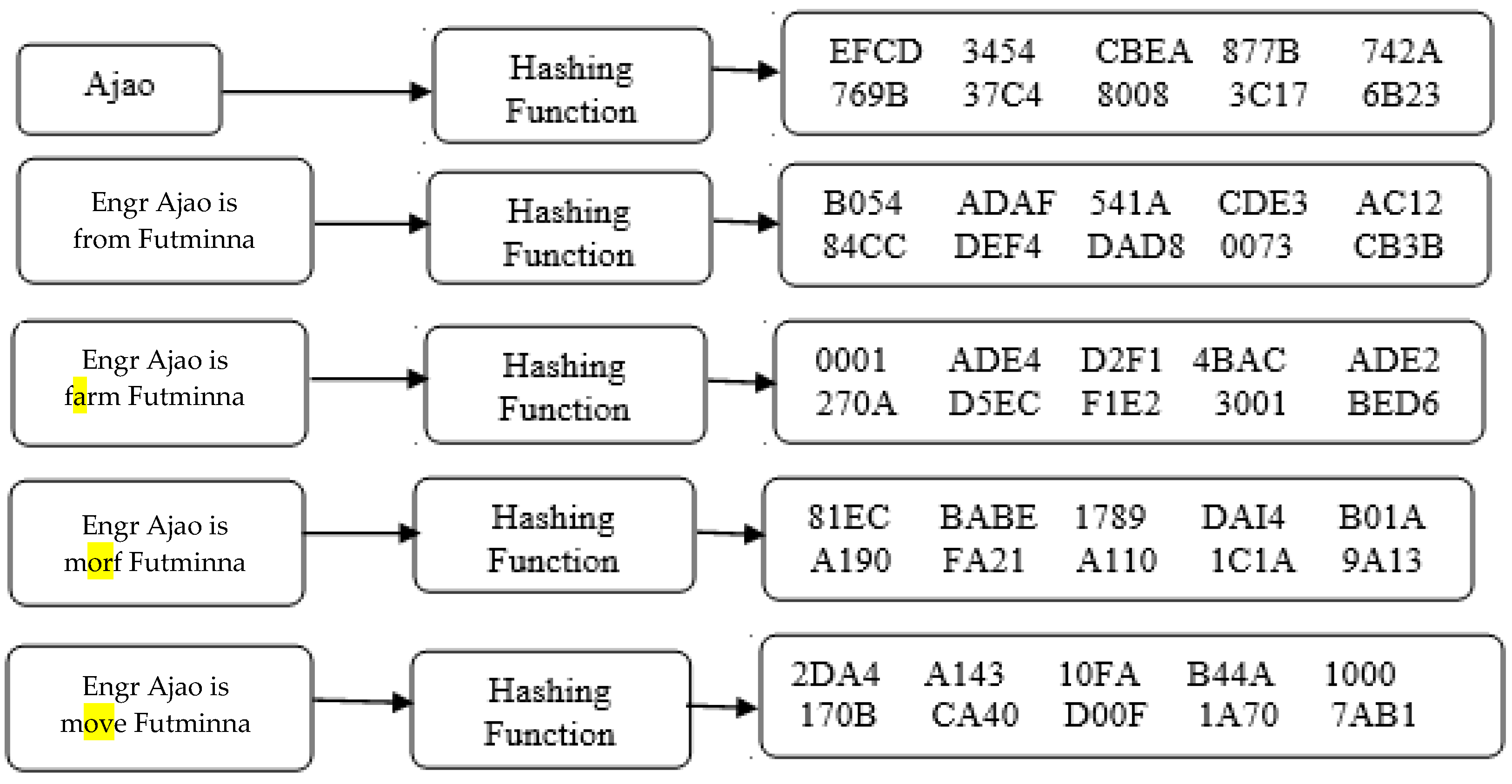
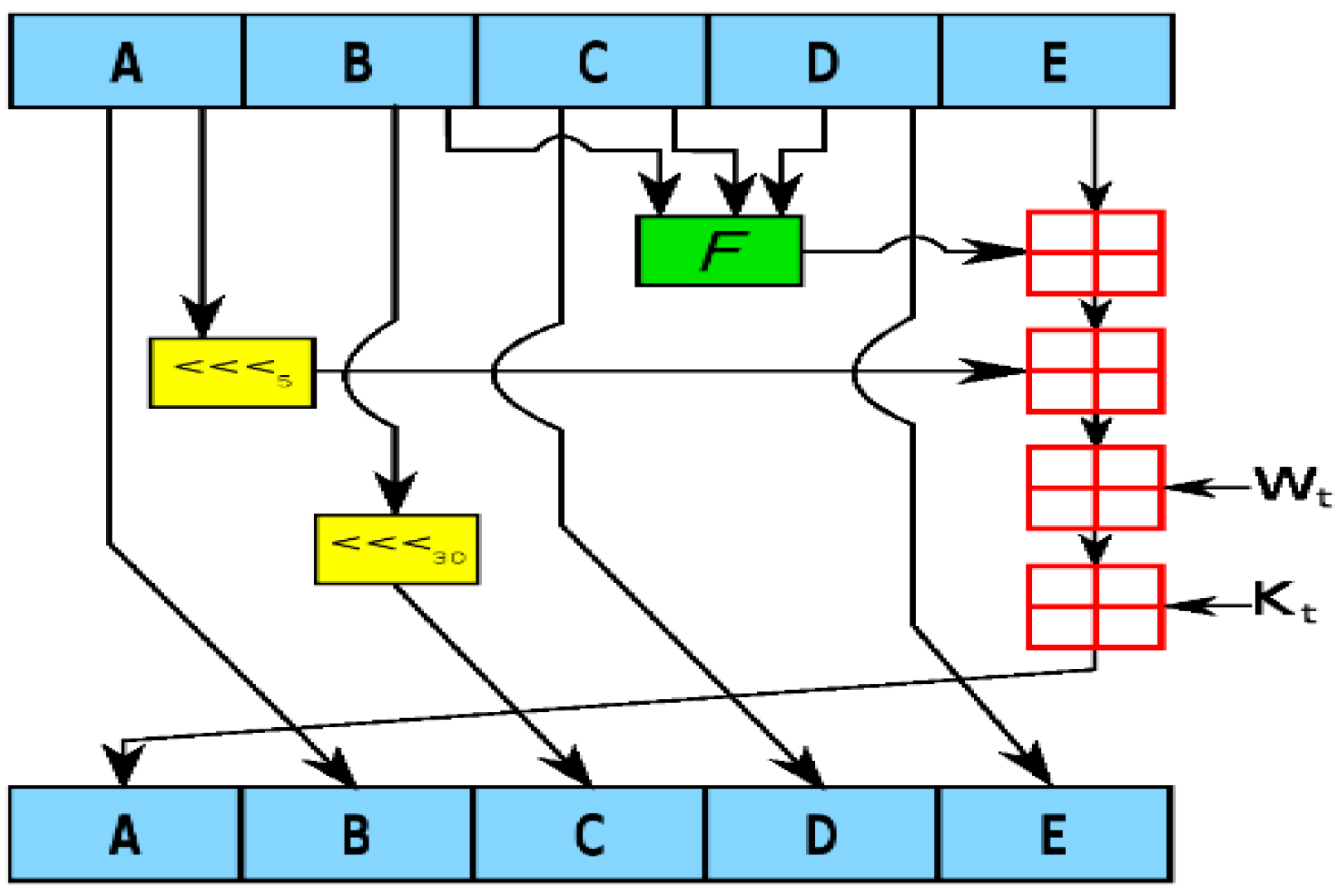
3.2. Crypto Hash Algorithm Functions
- Cryptotrack: 6BD736F1C2DC0B566812B92B7C47EBA39BCD5222
- cryptotrack: 5AA13558D0CCA00C53EDD39427392545046DB597
- 1:
- Takes input text and splits it into an array of the characters’ ASCII codes.
- 2:
- Converts ASCII codes to binary.
- 3:
- Pad zeros to the front of each bit until they are 8 bits long.
- 4:
- Join them together and append them to one (1).
- 5:
- Pad the binary message with zeros until its length is 512 mod 448.
- 6:
- Take binary 8-bit ASCII code array from step 3 and get its length in binary.
- 7:
- Pad with zeros until it is 64 characters.
- 8:
- Append to your previously created binary message from step 5.
- 9:
- Break the message into an array of chunks of 512 characters.
- 10:
- Break each chunk into subarray of sixteen 32-bit words.
- 11:
- Loop through each chunk array of sixteen 32-bit words and extend each array to 80 words using bitwise operations.
- 12:
- Initialize some variables.
- 13:
- Looping through each chunk: bitwise operations and variable reassignment.
- 14:
- Convert each of the five resulting variables to hexadecimal.
- 15:
- Append them together and the result is your hash value or message digest.
3.3. Crypto Hash Computation (SHA-1)
- SHA-1
- (“Cryptotrack”) denotes 6BD736F1C2DC0B566812B92B7C47EBA39BCD5222
- SHA-1
- SHA-1(“cryptotrack”) means 5AA13558D0CCA00C53EDD39427392545046DB597
3.4. Mining Algorithm and Pseudocode-Based Blockchain
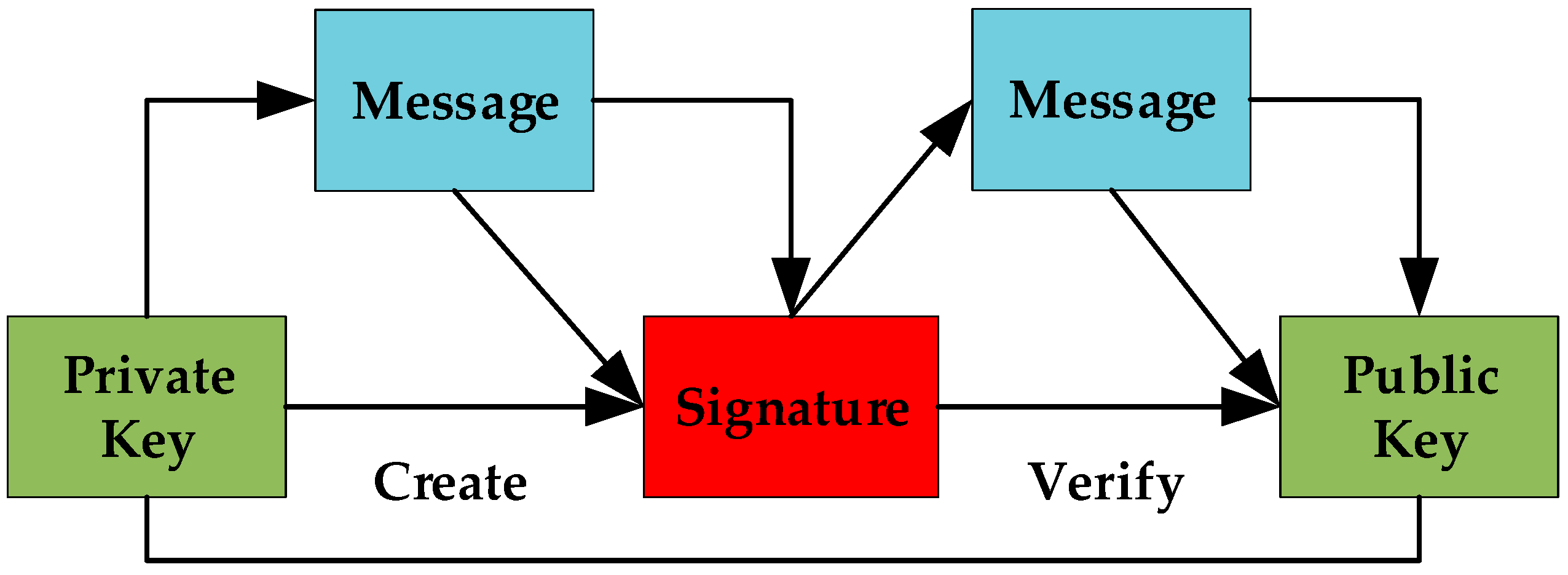
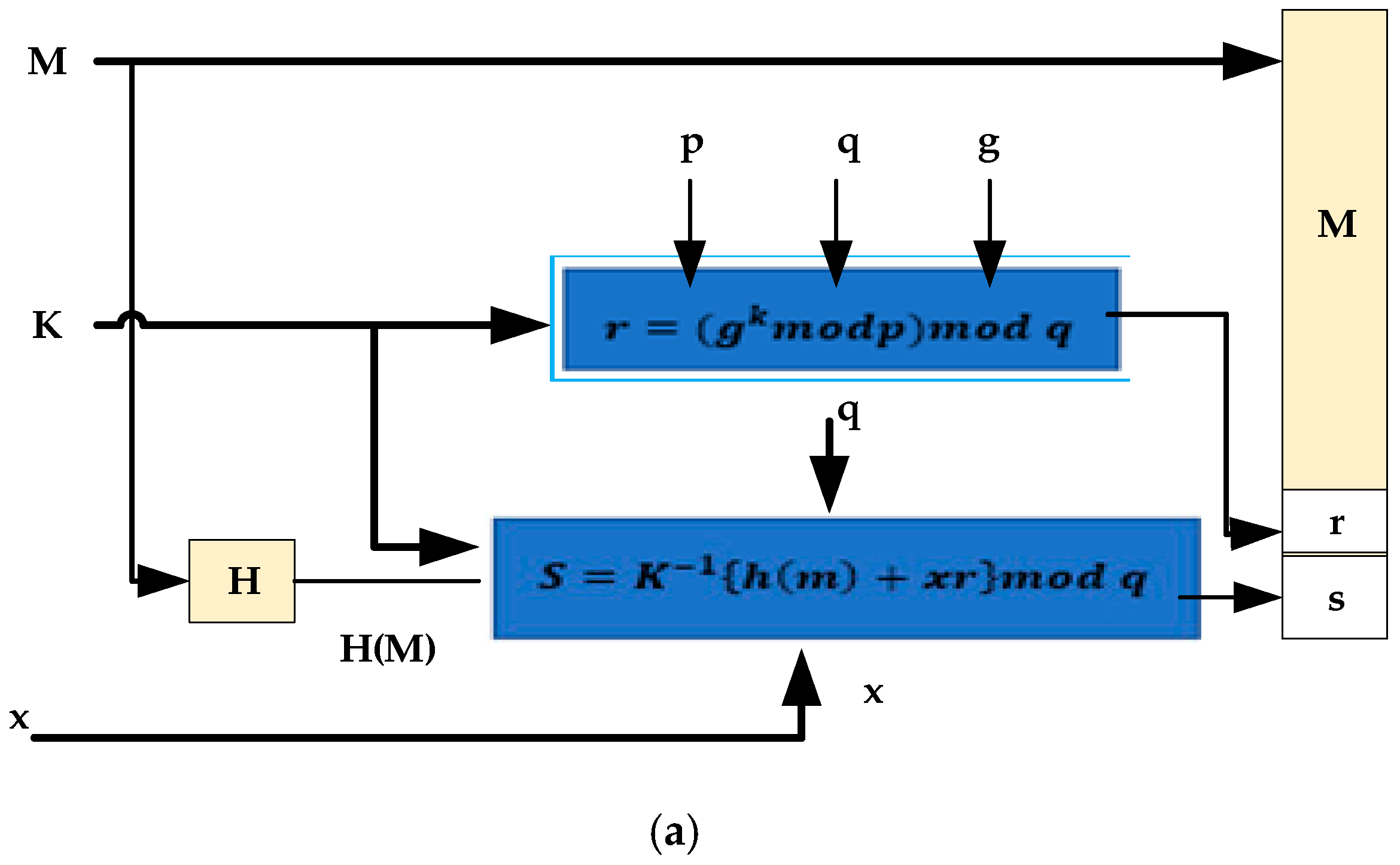
3.5. Cryptographic Algorithm for Key Management in Blockchain Technology
| 1. Key generation procedure/Algorithm | |
| Step 1. | Signing message |
| i. | Start with shared the global public key values (p, q, g) |
| ii. | Select about 160-bit prime number (q) |
| iii. | Select a large prime number (p) with 2^ (L-1) < p < 2^l, where L will be equal to 512 to 1024 bits and is a multiple of 64 such that q is a 160-bit prime divisor of p-1 |
| iv. | Select h, then find g=h^((p-1)/q) mod p, where 1<h<p-1 and h^((p-1)/q) mod p>1 |
| Step 2. | Select a private key and compute the public keys |
| i. | Select a random private key such that: x < q |
| ii. | Compute the public key such that: |
| 2. Creation of Signature | |
| Step1. | Signing of a message M, the sender: |
| i. | Creates a random signature key (k), such that k < q |
| ii. | Creation of k must be random, one-time password (OTP) and destroyed after used |
| Step 2 | Computation of signature pair |
| i. | |
| ii. | |
| iii. | The signature (r, s) and message M (Transaction) will be send |
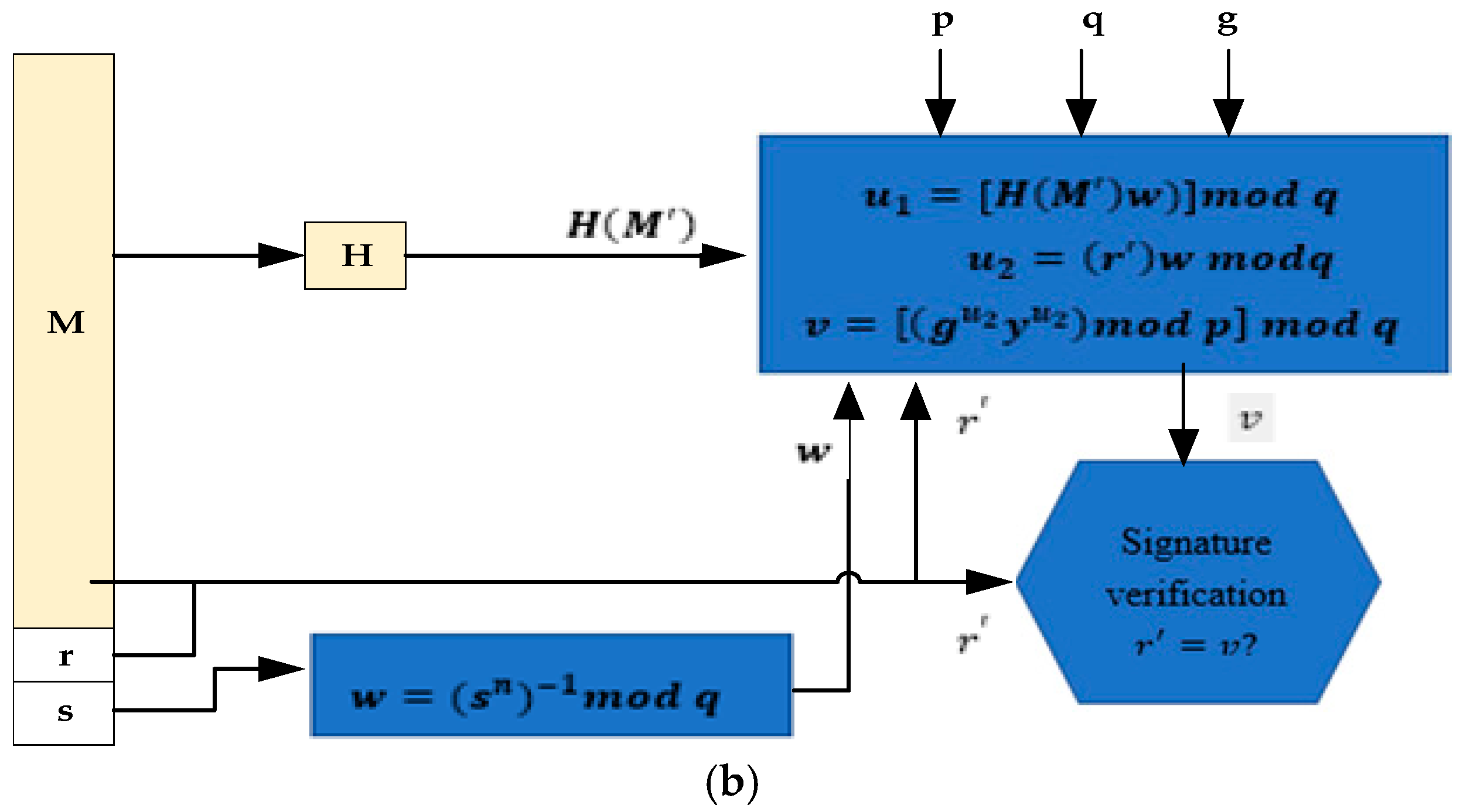
| 3. Verification of Signature | |
| i. | While receiving message (M) with signature (r, s) |
| ii. | Then, to verify a recipient transaction signature, use the following computation. |
| iii. | If v = r, then transaction signature is confirmed |
| End the process. |
| p | is , |
| q | |
| s | , |
| x | used as a private key |
| y | |
| k | |
| r, s | is the signature for signing, where , and |
| v, r | v = r is the verification, mod q |
| M | Message to be signed |
| H(M) | Hash of M using SHA-1 |
| M’, r, s’ | the received varieties or copy of M, r, s. |
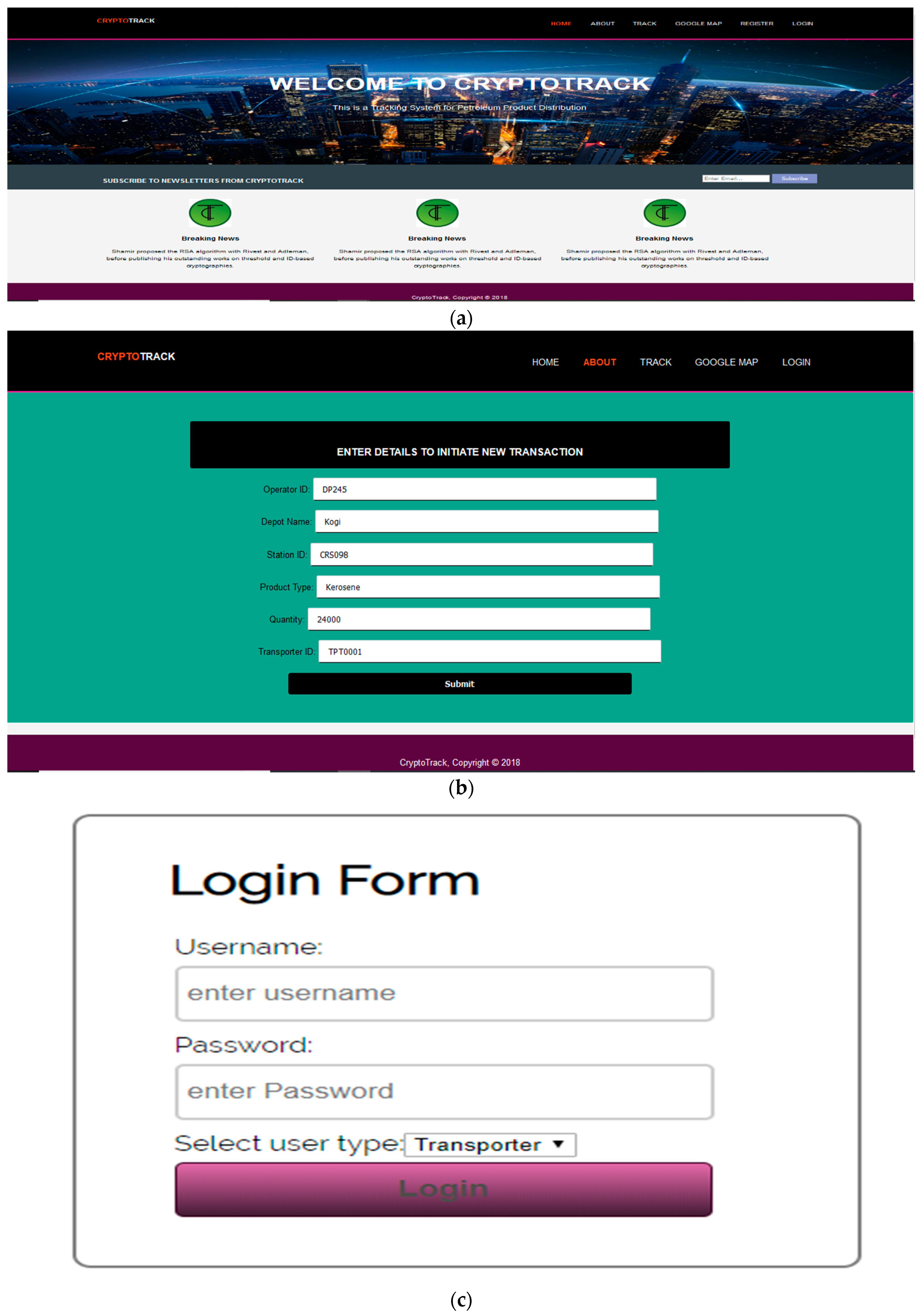
3.6. Implementation of (Telematics) an In-Vehicle Tracking System Prototype
4. Results and Discussion
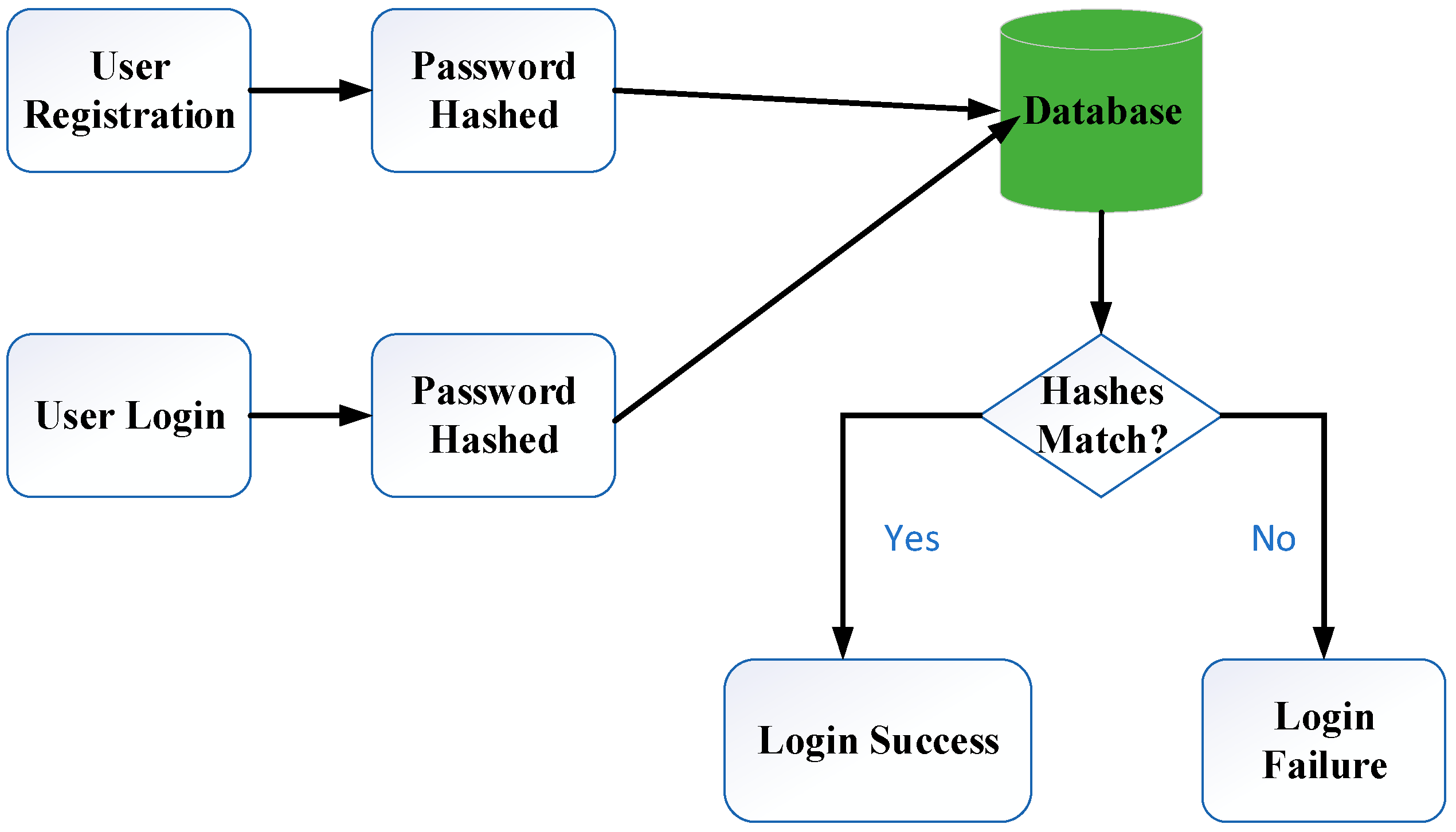
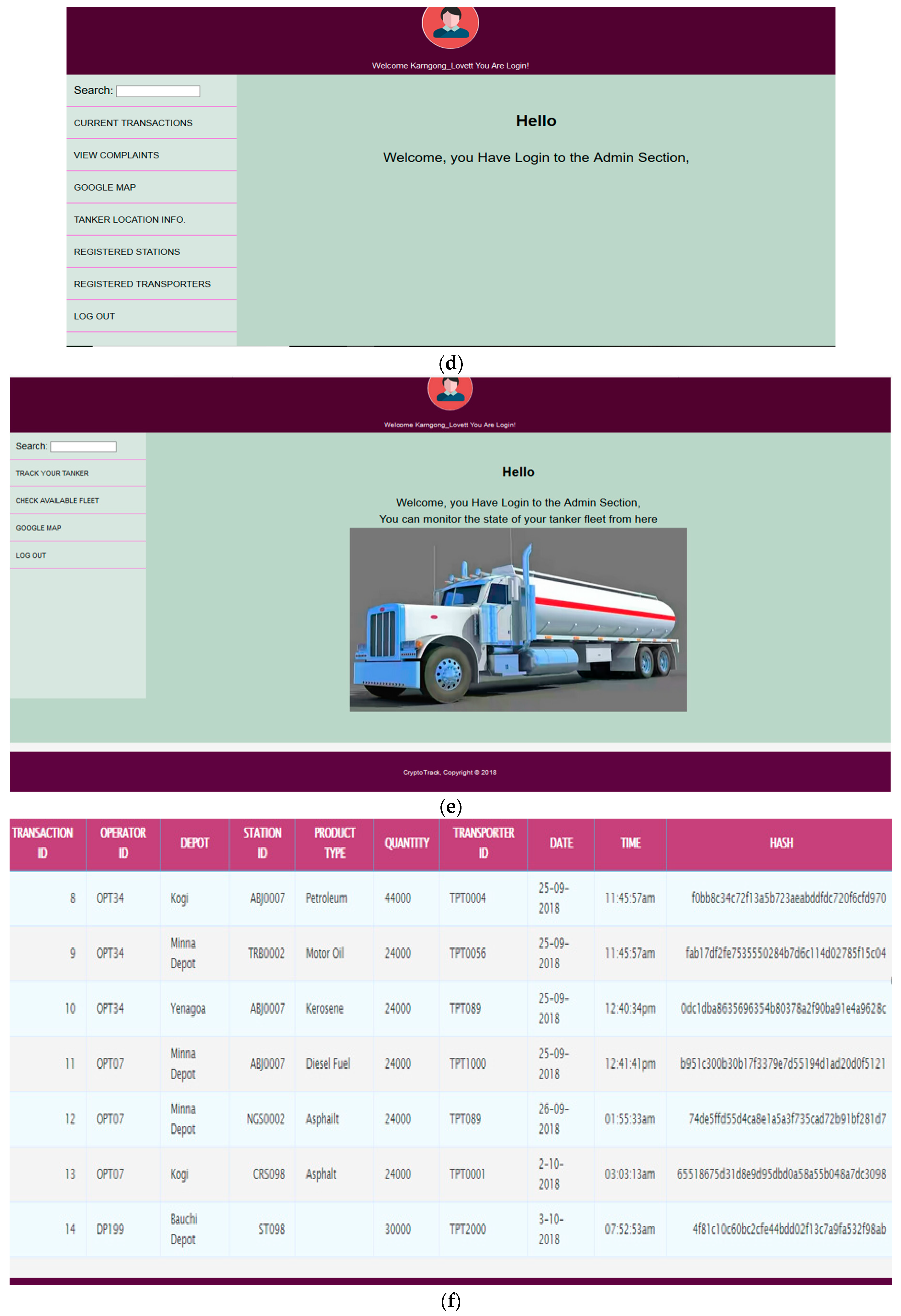
4.1. Development of Crypto Hash Decentralized Ledger
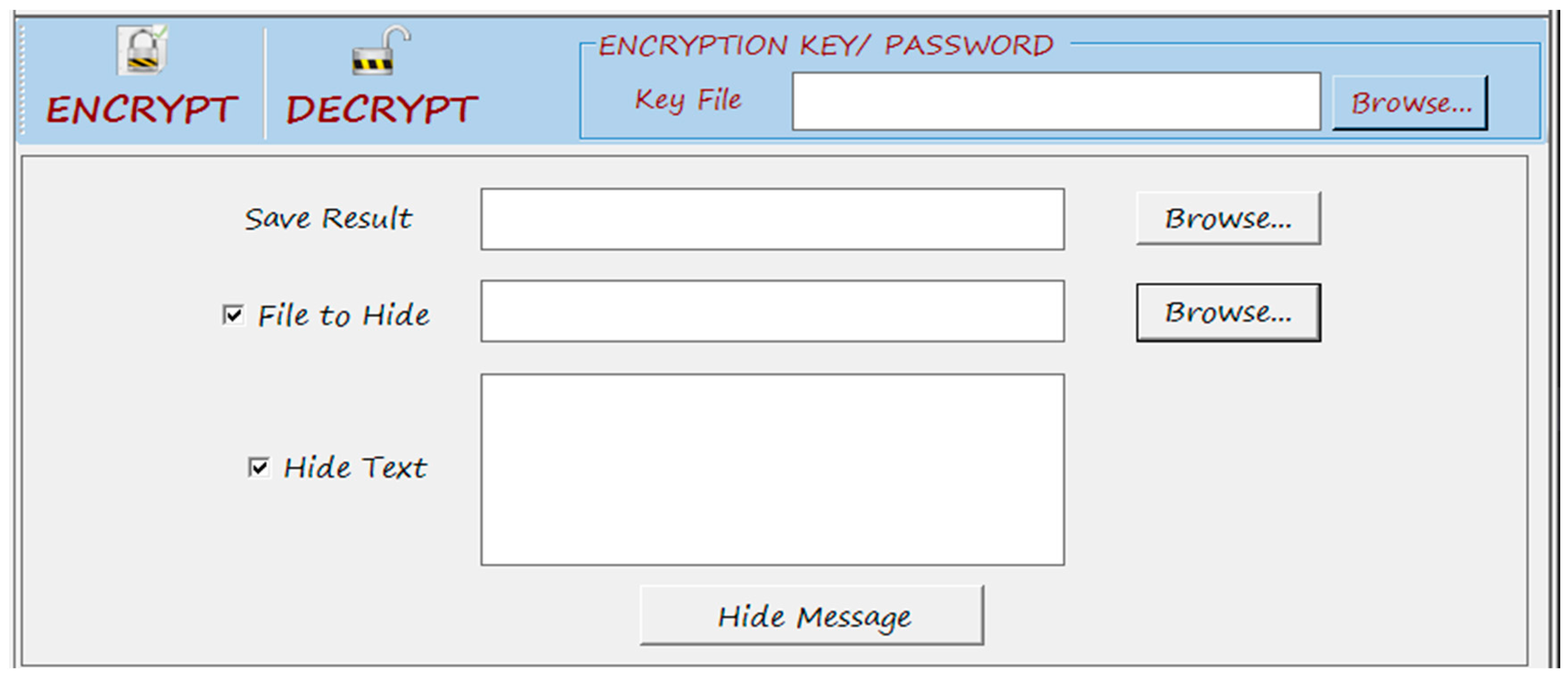
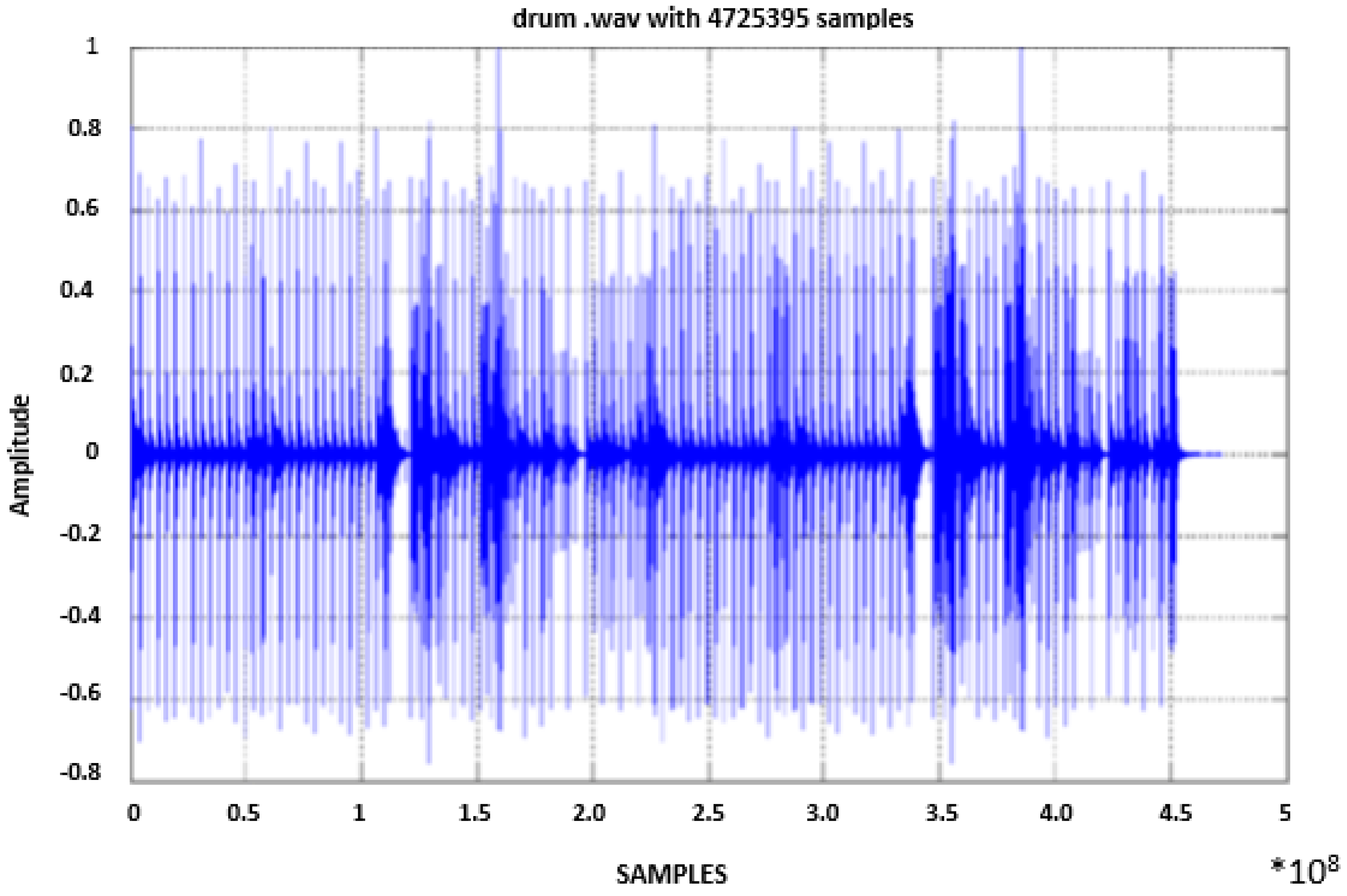
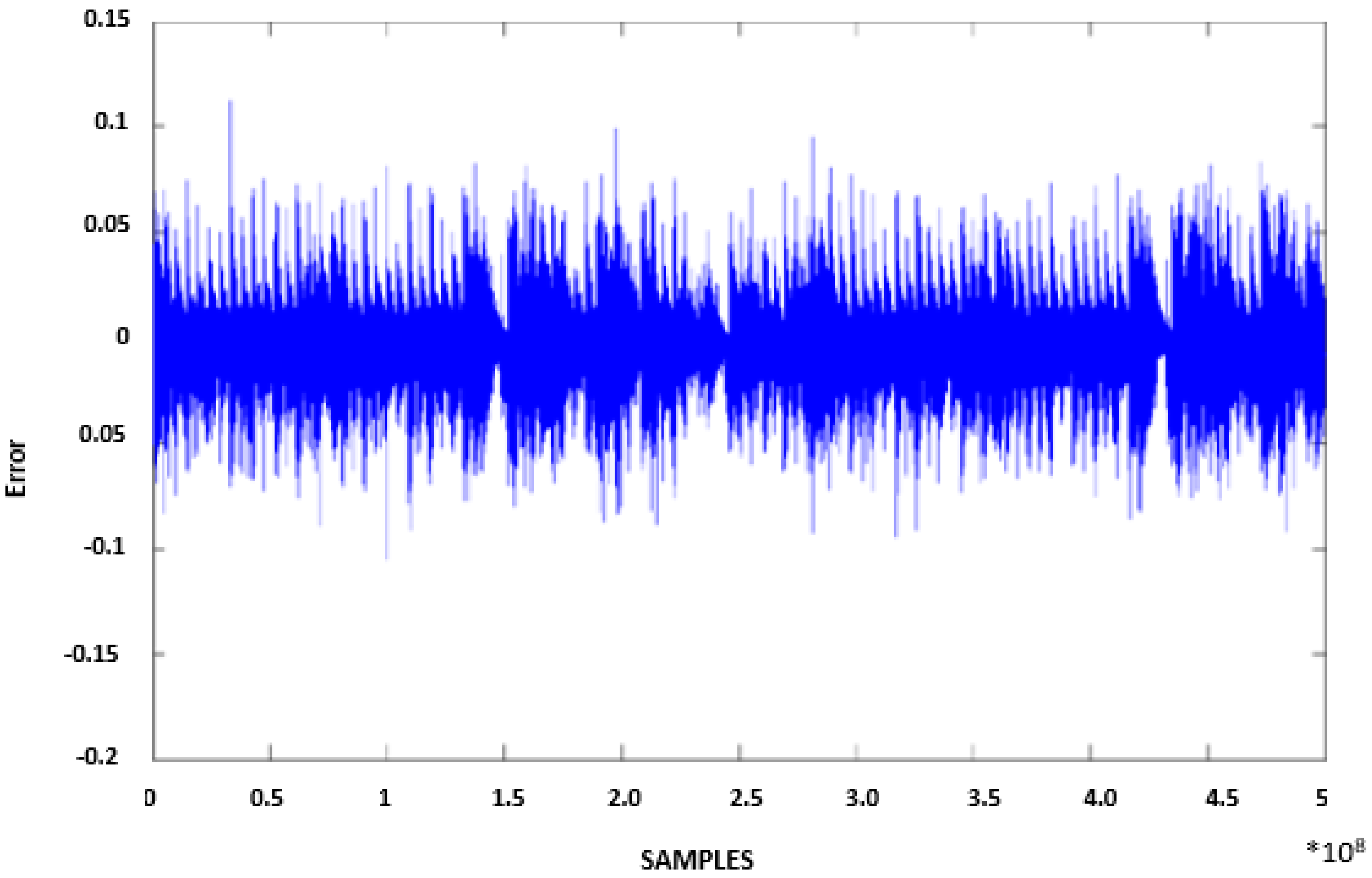
4.2. Encryption and Decryption Algorithm Testing and Results Using WAVE
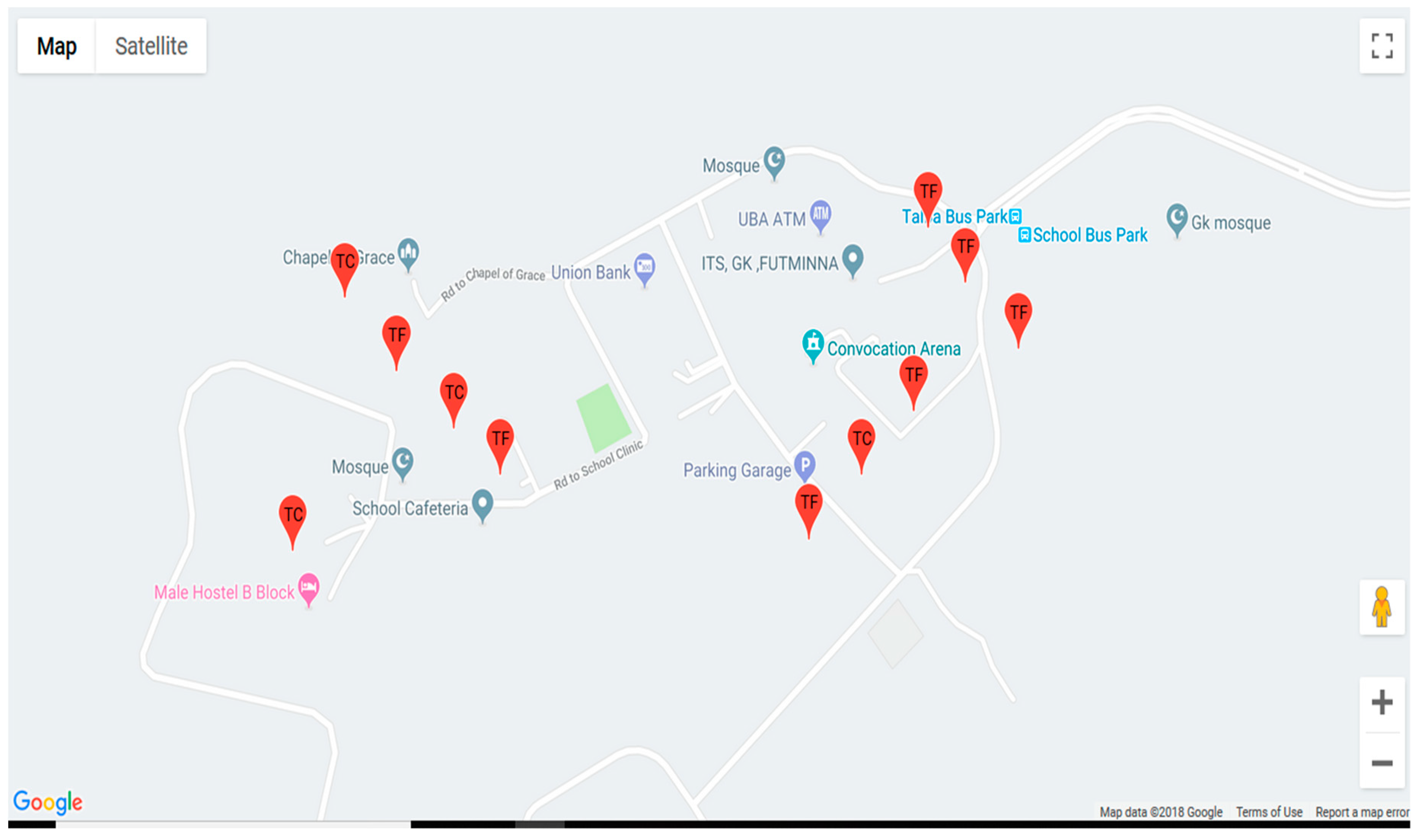
4.3. Testing and Results of Implemented Automobile Based Telematics
4.4. Performance Evaluation Testing of the Crypto Hash System
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Nwoba, O.E.; Abah, E.O. Impact of crude oil revenue (cor) on economic growth in nigeria (1960–2010). IOSR J. Hum. Soc. Sci. 2017, 22, 85–99. [Google Scholar]
- Özturkoglu, Ö.; Lawal, O. The integrated network model of pipeline, sea and road distribution of petroleum product. Int. J. Optim. Control Theor. Appl. 2016, 6, 151–165. [Google Scholar] [CrossRef]
- Aminu, S.A.; Olawore, O.P. Empirical investigation of challenges of distribution of premium motor spirit (PMS) in federal capital territory (Fct), abuja and environs, Nigeria. Int. J. Manag. Sci. Humanit. 2014, 2, 17–59. [Google Scholar]
- Ajao, L.A.; Adedokun, E.A.; Nwishieyi, C.P.; Adegboye, M.A.; Agajo, J.; Kolo, J.G. An anti-theft oil pipeline vandalism detection. Int. J. Eng. Sci. Appl. 2018, 2, 41–46. [Google Scholar]
- Adegboye, M.A.; Fung, W.-K.; Karnik, A. Recent advances in pipeline monitoring and oil leakage detection technologies: principles and approaches. Sensors 2019, 19, 2548. [Google Scholar] [CrossRef] [PubMed]
- Basu, S.; Waymire, G.B. Record-keeping and human evolution. Account. Horiz. 2006, 20, 201–229. [Google Scholar] [CrossRef]
- Bacina, M.; Partner, P.; Alderman, P. The Era of Digital Trust. Available online: https://www.legaler.com/.../Blockchain-for-Lawyers-eBook.pdf (accessed on 10 December 2018).
- Diego, R.; Giovanni, S. Beyond bitcoin: A critical look at blockchain-based systems. Cryptography 2017, 1, 15. [Google Scholar]
- Lavanya, B.M. Blockchain technology beyond bitcoin: An overview. Int. J. Comput. Sci. Mob. Appl. 2018, 6, 76–80. [Google Scholar]
- Ajao, L.A.; Agajo, J.; Olaniyi, O.M.; Jibril, I.Z.; Sebiotimo, A.E. A Secure Tracking Automobile System for Oil and Gas Distribution using Telematics and Blockchain Techniques. J. Electr. Comput. Eng. Innov. 2019, 7, 171–177. [Google Scholar]
- Marr, B. A Very Brief History of Blockchain Technology Everyone Should Read; Forbes: New York, NY, USA, 2018. [Google Scholar]
- Vestergaard, C. Better than a floppy the potential of distributed ledger technology for nuclear safeguards information management, innovative approaches to peace and security from the stanley foundation. Anal. Brief. 2018, 1, 1–8. [Google Scholar]
- Hardjono, T.; Lipton, A.; Pentland, A. Towards a Design Philosophy for Interoperable Blockchain System; Springer: Berlin, Germany, 2018; pp. 1–27. [Google Scholar]
- Derhab, A.; Guerroumi, M.; Maglaras, L.; Ferrag, M.A.; Mukherjee, M.; Khan, F.A. BLOSTER: Blockchain-based system for detection of fraudulent rules in software-defined networks. In Proceedings of the 6th International Symposium for ICS & SCADA Cyber Security Research 2019, Athens, Greece, 10–12 September 2019; pp. 1–3. [Google Scholar]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Int. Things J. 2019, 6, 2188–2204. [Google Scholar] [CrossRef]
- Kogias, E.K.; Jovanovic, P.; Gailly, N.; Khoffi, L.; Gasser, L.; Ford, B. Enhancing bitcoin security and performance with strong consistency via collective signing. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 279–296. [Google Scholar]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A technical survey on decentralized digital currencies. IEEE Commun. Surv. Tutor. 2016, 18, 2084–2123. [Google Scholar] [CrossRef]
- Chima, C.M.; Hills, D. Supply-chain management issues in the oil and gas industry. J. Bus. Econ. Res. 2007, 5, 27–36. [Google Scholar] [CrossRef]
- Kshetri, N. Can blockchain strengthen the internet of things. IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Ekblaw, A.; Azaria, A.; Halamka, J.D.; Lippman, A. A case study for blockchain in healthcare: Medrec prototype for electronic health records and medical research data. Proc. IEEE Open Big Data Conf. 2016, 13, 1–13. [Google Scholar]
- Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology, In Service Systems and Service Management (ICSSSM). In Proceedings of the 13th IEEE International Conference, Kunming, China, 24–26 June 2016; pp. 1–6. [Google Scholar]
- Micheal, C. What is Telematics, Geotab Inc., 2018. Available online: https://www.geotab.com/blog/what-is-telematics/ (accessed on 8 January 2018).
- Handel, P.; Skog, I.; Wahlstrom, J.; Bonawiede, F.; Welch, R.; Ohlsson, J.; Ohlsson, M. Insurance telematics: Opportunities and challenges with the smartphone solution. Int. Trans. Syst. Manag. IEEE 2014, 6, 57–70. [Google Scholar] [CrossRef]
- García, C.R.; Quesada-Arencibia, A.; Cristóbal, T.; Padrón, G.; Alayón, F. Systematic development of intelligent systems for public road transport. Sensors 2016, 16, 1104. [Google Scholar] [CrossRef]
- Winter, A.; Baldi, S. Real-Life implementation of a GPS-Based path-following system for an autonomous vehicle. Sensors 2018, 18, 3940. [Google Scholar] [CrossRef]
- Awan, M. Compensation of Low Performance Steering System Using Torque Vectoring. Ph.D. Thesis, Cranfield University, Bedfordshire, UK, 2012. [Google Scholar]
- Isermann, R. Diagnosis methods for electronic controlled vehicles. Veh. Syst. Dyn. 2001, 36, 77–117. [Google Scholar] [CrossRef]
- Jang, J.A.; Kim, H.S.; Cho, H.B. Smart roadside system for driver assistance and safety warnings: Framework and applications. Sensors 2011, 11, 7420–7436. [Google Scholar] [CrossRef]
- Khatwani, S. Different Types of Blockchains in the Market and Why We Need Them. Available online: https://coinsutra.com/different-types-blockchains/ (accessed on 15 September 2018).
- DataFlair Team, Blockchain Tutorial. 2018. Available online: https://data-flair.training/blogs/bitcoin-and-cryptocurrency-technologies (accessed on 14 September 2018).
- Kumar, S.; Gupta, P. A comparative analysis of sha and MD5 algorithm. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 4492–4495. [Google Scholar]
- Gligoroski, D.; Markovski, S.; Knapskog, S.J. A secure hash algorithm with only 8 folded sha-1 steps. Int. J. 194 Comput. Sci. Netw. Secur. 2006, 6, 194–205. [Google Scholar]
- Manuel, S. Classification and generation of disturbance vectors for collision attacks against SHA-1. Des. Codes Cryptogr. 2011, 59, 247–263. [Google Scholar] [CrossRef]
- White, B.; Kreuz, T.; Simons, S. Midstream. In Compression Machinery for Oil and Gas; Klaus, B., Rainer, K., Eds.; Gulf Professional Publishing: Houston, TX, USA, 2019; pp. 387–400. [Google Scholar]
- Adrian, A.; Cendana, M.; Dian, S.; Permana, H. Diffie-Hellman Key Exchange Modification using Blowfish Algorithm to Prevent Logjam Attack. J. Telecommun. Electron. Comput. Eng. 2018, 10, 1–7. [Google Scholar]
- Oluwade, O.R.; Olaniyi, O.M.; Abdulsalam, Y.S.; Ajao, L.A. Entropy management technique in lightweight cryptographically secured smart home. In Proceedings of the 12th International Multi-Conference on ICT Applications (AICTTRA, 2018), Ile-Ife, Nigeria, 15 September 2018; pp. 258–265. [Google Scholar]
- Hulsing, A. Digital signature schemes and the random oracle model. Technische Universiteit Eindhoven. Available online: https://www.win.tue.nl/applied_crypto/2016/20161115_ROM_Signatures.pdf (accessed on 23 September 2016).
- Sene, I.; Ciss, A.A.; Niang, O. I2PA: An Efficient ABC for IoT. Cryptography 2019, 3, 16. [Google Scholar] [CrossRef]
- Hülsing, A. Digital Signature Schemes and the Random Oracle Model. Available online: https://www.win. tue.nl/applied_crypto/2016/20161115_ROM_Signatures.pdf. (accessed on 23 September 2016).
- Liu, J.K.; Baek, J.; Zhou, J.; Yang, Y.; Wong, J.W. Efficient online/offline identity-based signature for wireless sensor network. Int. J. Inf. Secur. 2010, 9, 287–296. [Google Scholar] [CrossRef]


| S/N | Conveyance ID | Quantity (Liter) | Transaction ID | Destination Area ID | B |
|---|---|---|---|---|---|
| 1 | Ϗ | 44,000 | Minna (M) | => φ | |
| 2 | 𝜛 | 33,000 | Lokoja (λ) | φ | |
| 3 | µ | 11,000 | Bida (ϐ) | φ | |
| 4 | Ύ | 33,000 | Ilorin (ζ) | φ | |
| 5 | ₤ | 44,000 | Okene () | φ |
| Id | Tanker_ID | Time | Date | Satellite Number | HDOP | Liquid Level | Speed | Latitude | Longitude |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 865210031078669 | 06:15:44 | 08/10/2018 | 5 | 2.19 | 66 | 0.35 | 9.531407 | 6.451446 |
| 2 | 865210031078669 | 06:16:17 | 08/10/2018 | 6 | 1.92 | 89 | 0.37 | 9.531438 | 6.451479 |
| 3 | 865210031078669 | 06:16:50 | 08/10/2018 | 5 | 1.98 | 89 | 0.59 | 9.531368 | 6.451441 |
| 4 | 865210031078669 | 06:17:23 | 08/10/2018 | 6 | 2.03 | 89 | 0.44 | 9.531471 | 6.451372 |
| 5 | 865210031078669 | 06:17:56 | 08/10/2018 | 5 | 1.6 | 97 | 1.19 | 9.531489 | 6.451346 |
| 6 | 865210031078669 | 07:55:25 | 08/10/2018 | 5 | 2.56 | 100 | 1.2 | 9.530928 | 6.451571 |
| 7 | 865210031078669 | 07:55:58 | 08/10/2018 | 4 | 9.51 | 100 | 1.81 | 9.531051 | 6.451568 |
| 8 | 865210031078669 | 07:56:32 | 08/10/2018 | 5 | 2.5 | 100 | 1.04 | 9.530858 | 6.451453 |
| 9 | 865210031078669 | 07:57:05 | 08/10/2018 | 8 | 2.5 | 100 | 1.5 | 9.530884 | 6.45146 |
| 10 | 865210031078669 | 07:57:38 | 08/10/2018 | 6 | 4.99 | 100 | 1.98 | 9.531068 | 6.451518 |
| 11 | 865210031078669 | 07:58:11 | 08/10/2018 | 5 | 4.94 | 100 | 2.85 | 9.530917 | 6.451497 |
| 12 | 865210031078669 | 07:58:44 | 08/10/2018 | 6 | 2.48 | 100 | 1.87 | 9.530988 | 6.45146 |
| 13 | 865210031078669 | 18:20:29 | 08/10/2018 | 9 | 0.81 | 48 | 0.2 | 9.531387 | 6.451231 |
| 14 | 865210031078669 | 18:21:02 | 08/10/2018 | 9 | 0.88 | 0 | 0.15 | 9.531398 | 6.451261 |
| 15 | 865210031078669 | 18:21:35 | 08/10/2018 | 10 | 0.82 | 0 | 1.11 | 9.53142 | 6.451247 |
| 16 | 865210031078669 | 18:22:08 | 08/10/2018 | 10 | 0.78 | 0 | 0.2 | 9.531483 | 6.451261 |
| 17 | 865210031078669 | 18:22:41 | 08/10/2018 | 9 | 0.87 | 0 | 0.74 | 9.531522 | 6.451264 |
| 18 | 865210031078669 | 18:23:14 | 08/10/2018 | 10 | 0.87 | 0 | 2.63 | 9.531484 | 6.451257 |
| 19 | 865210031078669 | 18:23:47 | 08/10/2018 | 10 | 0.98 | 0 | 2.57 | 9.531505 | 6.451173 |
| 20 | 865210031078669 | 18:24:20 | 08/10/2018 | 10 | 0.78 | 0 | 0.44 | 9.531486 | 6.451322 |
| 21 | 865210031078669 | 18:24:53 | 08/10/2018 | 9 | 0.85 | 0 | 0.61 | 9.531514 | 6.451376 |
| 22 | 865210031078669 | 18:25:26 | 08/10/2018 | 9 | 0.85 | 0 | 0.61 | 9.531542 | 6.451425 |
| 23 | 865210031078669 | 18:25:59 | 08/10/2018 | 5 | 1.82 | 0 | 14.26 | 9.531661 | 6.451532 |
| 24 | 865210031078669 | 18:26:32 | 08/10/2018 | 7 | 2.88 | 0 | 8.72 | 9.531518 | 6.451762 |
| 25 | 865210031078669 | 18:27:06 | 08/10/2018 | 0 | 99.99 | 0 | 14.93 | 9.531453 | 6.452001 |
| 26 | 865210031078669 | 18:27:40 | 08/10/2018 | 9 | 1.01 | 0 | 4.63 | 9.531857 | 6.451674 |
| 27 | 865210031078669 | 18:28:13 | 08/10/2018 | 8 | 0.9 | 0 | 0.24 | 9.531544 | 6.451401 |
| 28 | 865210031078669 | 00:37:47 | 09/12/2018 | 9 | 0.98 | 0 | 0.74 | 9.531361 | 6.451714 |
| 29 | 865210031078669 | 00:38:34 | 09/12/2018 | 9 | 0.85 | 0 | 0.11 | 9.531422 | 6.451569 |
| 30 | 865210031078669 | 00:39:21 | 09/12/2018 | 9 | 0.88 | 0 | 0.06 | 9.531407 | 6.451598 |
| 31 | 865210031078669 | 00:40:08 | 09/12/2018 | 9 | 0.8 | 0 | 0.33 | 9.53139 | 6.451566 |
| 32 | 865210031078669 | 00:40:55 | 09/12/2018 | 11 | 0.76 | 0 | 0.17 | 9.531413 | 6.451585 |
| 33 | 865210031078669 | 00:41:42 | 09/12/2018 | 9 | 0.99 | 0 | 0.48 | 9.531431 | 6.45158 |
| 34 | 865210031078669 | 00:42:29 | 09/12/2018 | 10 | 0.88 | 0 | 1 | 9.531427 | 6.4516 |
| 35 | 865210031078669 | 00:43:16 | 09/12/2018 | 10 | 0.92 | 0 | 0.63 | 9.531411 | 6.45163 |
| 36 | 865210031078669 | 00:44:03 | 09/12/2018 | 9 | 0.92 | 0 | 1.98 | 9.531393 | 6.451665 |
| Actual Coordinate Values | GPS Coordinate Values | ||||
|---|---|---|---|---|---|
| Location (Address) | Latitudinal Coordinate | Longitudinal Coordinate | Latitudinal Coordinate | Longitudinal Coordinate | No of Satellite Captured |
| ICT Complex | 6.451576 | 9.531347 | 6.451829 | 9.531222 | 4 |
| Engineering Complex | 6.449162 | 9.533510 | 6.449241 | 9.533539 | 8 |
| E-exam Center | 6.449688 | 9.536088 | 6.449667 | 9.536154 | 9 |
| ITS Center | 6.452325 | 9.535278 | 6.452507 | 9.535301 | 5 |
| Agric Complex | 6.451862 | 9.533240 | 6.451966 | 9.533134 | 7 |
| Senate Building | 6.452790 | 9.534655 | 6.452748 | 9.52748 | 6 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ajao, L.A.; Agajo, J.; Adedokun, E.A.; Karngong, L. Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry. J 2019, 2, 300-325. https://doi.org/10.3390/j2030021
Ajao LA, Agajo J, Adedokun EA, Karngong L. Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry. J. 2019; 2(3):300-325. https://doi.org/10.3390/j2030021
Chicago/Turabian StyleAjao, Lukman Adewale, James Agajo, Emmanuel Adewale Adedokun, and Loveth Karngong. 2019. "Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry" J 2, no. 3: 300-325. https://doi.org/10.3390/j2030021
APA StyleAjao, L. A., Agajo, J., Adedokun, E. A., & Karngong, L. (2019). Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry. J, 2(3), 300-325. https://doi.org/10.3390/j2030021





