Abstract
Unmanned aerial vehicle (UAV) communication using non-orthogonal multiple access-based coordinated direct and relay transmission (NOMA-CDRT) supports both massive connectivity and wide-area coverage, becoming a key technology for future emergency rescue communications. However, relay forwarding and high-quality line-of-sight links may subject UAV-aided NOMA-CDRT to multiple eavesdropping attempts by saboteurs. Therefore, we propose a multi-node joint jamming scheme using artificial noise (AN) for the UAV-assisted NOMA-CDRT to improve the system’s physical layer security. In the proposed scheme, the base station directly serves a nearby user while using a UAV relay to serve a disaster-affected user, and both the users and the UAV relay utilize AN to jointly interfere with eavesdroppers around the users. To accurately characterize and maximize the ergodic secrecy sum rate (ESSR) of the proposed scheme, we derive the corresponding closed-form expressions and design a joint power allocation and interference control (JPAIC) algorithm using particle swarm optimization. Simulations verify the correctness of the theoretical analysis, the ESSR advantage of the proposed scheme compared with the conventional NOMA-CDRT, and the effectiveness of the proposed JPAIC.
1. Introduction
Due to the advantages of wide-area coverage, cost-effectiveness, and deployment flexibility, unmanned aerial vehicle (UAV) communication has been regarded as a crucial enabling technology for future wireless communication networks [1,2,3,4]. UAVs can serve as aerial base stations (BSs) or relays to enhance communication service quality, offering substantial benefits in scenarios such as emergency rescue, post-disaster recovery, and remote area communication [5,6,7]. To further improve spectral efficiency and support massive connections, UAV communication has also been integrated with non-orthogonal multiple access (NOMA) in recent years. Compared with the conventional orthogonal multiple access (OMA), the performance superiority of NOMA is achieved by using power-domain superposition coding and successive interference cancellation (SIC), which allow for the transmission of multi-user signals on the same physical layer resources [8,9]. However, the inherent high-quality line-of-sight (LoS) links and the multi-user information contained in NOMA signals make legitimate nodes of UAV-based NOMA (UAV-NOMA) systems vulnerable to eavesdropping by saboteurs [10,11,12].
To ensure communication security of UAV-NOMA systems, researchers have made significant efforts in direct transmission scenarios. In [12], Zhao et al. proposed a secure transmission scheme for a UAV-NOMA system using multi-antenna beamforming and jointly optimizing power allocation and UAV hovering position. Qian et al. deployed a UAV to collect data from ground sensors and maximized the total secrecy throughput of the UAV-NOMA network by jointly optimizing the scheduling decisions of auxiliary devices and the transmission power of the sensors [13]. Wang et al. proposed a downlink multi-user secure transmission scheme for UAV-NOMA networks based on heterogeneous user needs, achieving the maximization of the minimum secrecy rate through the joint optimization of user scheduling, power allocation, and trajectory design [14]. In [15], Yu et al. derived approximate expressions for the secrecy and reliability outage probabilities of UAV-NOMA-based ultra-reliable and low latency communication networks. The authors in [16] proposed a protection zone scheme for mmWave UAV-NOMA systems to enhance physical layer security by excluding eavesdroppers. Lu et al. designed a secure communication scheme for UAV-NOMA-based mobile edge computing systems, and the authors maximized the security computation capacity by optimizing multiple parameters such as local computing and UAV trajectory [17]. Guo et al. combined UAV-NOMA with simultaneously transmitting and reflecting reconfigurable intelligent surfaces (STAR-RIS), and jointly optimized power control, transmission/reflection coefficients, and the deployment positions of UAV/STAR-RIS to maximize the uplink secure energy efficiency [18]. Diao et al. derived closed-form expressions for connection outage probability, secrecy outage probability, and effective secrecy throughput to characterize the security performance of UAV-NOMA systems with friendly UAV jammers [19]. Sun et al. investigated downlink mmWave simultaneous wireless information and power transfer (SWIPT)-enabled UAV-NOMA systems and derived the corresponding connection outage probability and secrecy outage probability [20]. In [21], Deng et al. optimized the trajectory of a UAV and the transmit power of ground users to ensure the secure and covert communication of the UAV-NOMA system under the threat of eavesdropping UAVs.
Moreover, existing research has investigated secure UAV-NOMA transmission in relay scenarios to promote the diversification of its applications and further improve the communication coverage. In [22], Diao et al. proposed a joint energy transfer and artificial noise (AN) scheme for UAV-NOMA systems in the presence of eavesdropping UAVs. Simulations demonstrated that the proposed scheme promotes green and secure communication in multi-UAV cases. Zhang et al. characterized the performance of a satellite–terrestrial communication system based on NOMA, SWIPT, and UAV relaying by deriving analytical expressions for the secrecy outage probability [23]. To study the security of UAV-NOMA-based cognitive relay systems, the authors in [24] designed an iterative algorithm to maximize the minimum average secrecy rate for secondary users. Zheng et al. derived a closed-form expression for the secrecy outage probability of an underlay cognitive radio-enabled downlink UAV-NOMA network, where the UAV acts as a relay to assist communication between the source and two destination users [25]. The authors in [26] investigated a cognitive multiple input multiple output UAV-NOMA system and minimized the outage probability of the secondary network by optimizing the transmission power and coordinates of the UAV as well as the NOMA power allocation coefficients.
In addition to the pure relay system mentioned above, coordinated direct and relay transmission (CDRT), which evolved from the two-way relay system with analog network coding, is also an important type of relay system [27,28]. Currently, the transmission scheme design for NOMA-based CDRT (NOMA-CDRT) systems has been widely studied, but only a few works focus on secure communication in NOMA-CDRT systems, and these are limited to ground cellular scenarios. For instance, Lv et al. in [29] considered a ground NOMA-CDRT system with one untrusted amplify-and-forward (AF) relay, and designed adaptive cooperative jamming schemes for both downlink and uplink to realize secure transmission. To evaluate the system security performance and provide more insights, Lv et al. further derived a closed-form lower bound of the ergodic secrecy sum rate (ESSR) for the ground NOMA-CDRT system in [30]. Moreover, Lei et al. in [31] introduced physical layer network coding into the untrusted AF relay-based NOMA-CDRT system and utilized inter-user interference and friendly interference signals to enhance system security.
The aforementioned research provides meaningful insights into improving the security of NOMA-CDRT systems, but challenges remain in secure UAV-aided NOMA-CDRT systems: (1) Existing research on secure NOMA-CDRT primarily focused on AF relay configurations and ground communication scenarios. Given the noise amplification characteristics of AF relays and the advantages of flexible UAV deployment, it is crucial to study the secure UAV-aided NOMA-CDRT systems using the decode-and-forward (DF) strategy [32]. However, to the best of our knowledge, no secure UAV-assisted NOMA-CDRT schemes employing DF relays have yet been identified. (2) Existing related work mainly addressed scenarios with untrusted relays and has not sufficiently explored secure NOMA-CDRT in the presence of multiple ground eavesdroppers. (3) The DF characteristics create multiple opportunities for eavesdroppers to intercept legitimate information, and the UAV LoS link further exacerbates this vulnerability.
Motivated by the above observations, this paper studies the secure transmission design and performance optimization of the UAV-aided NOMA-CDRT system with a DF relay. The contributions of this paper are as follows.
- This paper proposes a multi-node joint jamming (MNJJ) scheme using AN to achieve secure UAV-assisted NOMA-CDRT. In the proposed scheme, the BS uses NOMA to provide services to the nearby user while communicating with the disaster-affected user via a UAV relay. Both the users and the UAV collaboratively send AN to interfere with the surrounding eavesdroppers.
- To accurately characterize the security performance of the proposed scheme, we use double factorization and Gaussian–Chebyshev quadrature to derive the closed-form expressions of the ESSR under two conditions: when the legitimate nodes are aware of each other’s AN and when they are not.
- We design a joint power allocation and interference control (JPAIC) algorithm using particle swarm optimization (PSO) for the proposed MNJJ scheme. The proposed JPAIC determines the optimal scheme selection under different conditions and maximizes the ESSR. Simulations demonstrate the ESSR advantages of the proposed MNJJ over the conventional NOMA-CDRT (CNC) and the effectiveness of the proposed JPAIC.
To clearly present the research approach, Figure 1 provides a concise framework of our work. The remainder of this paper is organized as follows. Section 2 introduces the system model, and Section 3 presents the proposed MNJJ scheme. Section 4 provides the ESSR performance analysis and the proposed JPAIC. Section 5 gives the simulation results and Section 6 concludes the paper.
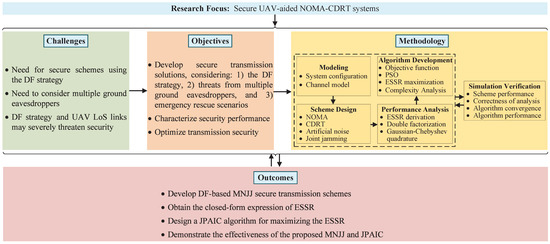
Figure 1.
A concise research framework of this paper.
Notation: and represent the probability density function (PDF) and cumulative distribution function (CDF) of the variable Z, respectively. represents a complex Gaussian distribution with mean zero and variance one. denotes the expectation operator, and represent the exponential integral function and the Gamma function, respectively. Denote . means replacing all instances of in with to obtain .
2. System Model
2.1. System Configuration
As shown in Figure 2, this paper investigates the physical layer security of a downlink UAV-aided NOMA-CDRT system, which consists of one BS, one DF-based UAV relay, two legitimate users (i.e., and ), and two eavesdroppers (i.e., and ). A typical application scenario for the considered system is emergency rescue. Specifically, when the BS in cell 2 is damaged or non-functional due to a sudden disaster or fault, the BS in cell 1 can use the UAV relay to serve while also communicating with its own cell user . There are potential eavesdroppers and near users and , respectively. These two eavesdroppers with strong computing power attempt to intercept any legitimate information. Assume that all devices are equipped with a single antenna and legitimate nodes can switch between half-duplex and full-duplex modes as needed. A transmission cycle consists of two time slots and . Both legitimate signals and AN have zero mean and unit variance.
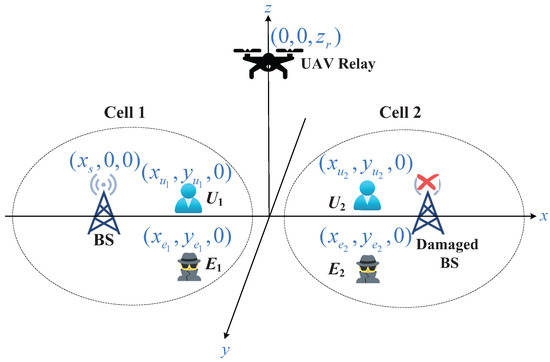
Figure 2.
Three-dimensional coordinate framework of a UAV-aided NOMA-CDRT system, including one BS, one UAV relay, two users, and two eavesdroppers.
Hereafter, the subscripts s, r, , , , , 1, and 2 represent the BS, UAV, , , , , , and , respectively. Figure 2 establishes a three-dimensional Cartesian coordinate framework, where the coordinate of the node i, , is expressed as . Without loss of generality, we assume that the BS and the UAV are in the plane, with the ground projection of the UAV at the origin of the plane. The UAV hovers at a fixed height during transmission. The distance between nodes i and , , is .
2.2. Channel Model
We assume that all channel links follow quasi-static block fading and include additive white Gaussian noise (AWGN) with zero mean and variance . Let represent the AWGN at node i during the k-th, , time slot. Define the channel coefficient, channel power, and path loss between ground nodes and , , during the k-th time slot as , , and , respectively. The small-scale fading of a ground-to-ground (G2G) link is modeled as a Rayleigh distribution, i.e., , while the corresponding path loss can be modeled as , where is the path loss coefficient at the unit reference distance, and is the path loss exponent, usually greater than two for G2G links. The parameter m/s is the speed of light and is the carrier frequency.
Similarly, we denote the channel coefficient, channel power, and path loss for the air-to-ground (A2G) link from the UAV to ground node as , , and , where and are the reference path loss coefficient and path loss exponent for A2G links, respectively. Specifically, we set and according to the Type B channel model described in [33], where , , is the angle of elevation. For suburban areas, we set , , dB, and dB. The small-scale fading of the A2G link is modeled as Nakagami-m fading with shape parameter m, which we consider as an integer for simplicity. The PDF and CDF of can be written as , and . Note that the channel modeling for ground-to-air (G2A) links is the same as for A2G links. Assume due to the typically greater distance between the BS and the UAV compared to the BS and .
3. Secure MNJJ Scheme Design
To enhance the system’s physical layer security, this section proposes an MNJJ scheme for the UAV-aided NOMA-CDRT system, as illustrated in Figure 3. The proposed MNJJ includes two time slots, detailed as follows.
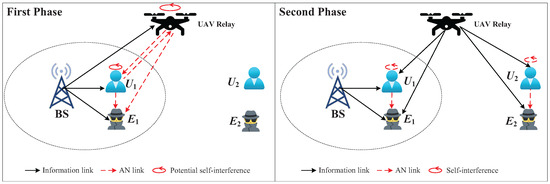
Figure 3.
Illustration of the proposed MNJJ scheme for a UAV-aided NOMA-CDRT system.
3.1. First Phase
In , the BS broadcasts a superposition coded signal , where is the transmission power of the BS, and and are the signals intended for and , respectively. Since requires UAV assistance, the power allocation coefficients are set as and . The UAV and switch to full-duplex mode and receive the signal from the BS while simultaneously sending AN and to interfere with . Here, we consider two cases: (1) Case I, where the legitimate nodes are unaware of each other’s AN, and (2) Case II, where legitimate nodes can know each other’s AN. When considering Case I, simultaneous sending of AN by the UAV and may interfere with each other. In Case II, legitimate nodes can use the known AN to eliminate the corresponding interference from other legitimate nodes by estimating channel and power parameters. To determine the optimal secure transmission method under different cases, we consider three types of the proposed MNJJ: both and the UAV turn on the jamming (i.e., NN), only turns on the jamming (i.e., NF), and only the UAV turns on the jamming (i.e., FN). The received signals at , the UAV, and in can be written as
and
where and are the self-interference channel coefficients at and the UAV in , respectively, and is the maximum interference power of each node. and indicate that the node turns off and turns on jamming in , respectively. When , the conditions and represent Case I and Case II. The interference power coefficient satisfies . Note that holds when , and holds when . The ratio of residual interference power resulting from self-interference cancellation to noise power , denoted as , is typically set in the range of 3 dB to 15 dB [34].
The user employs SIC to sequentially decode and . Therefore, the signal-to-interference-plus-noise ratios (SINRs) for decoding and at are written as
and
where , , and . Similarly, the UAV directly decodes treating as interference. The corresponding SINR can be written as
where . Based on (3), the eavesdropper may eavesdrop on both and in . Considering the worst case, we assume that has powerful computational capabilities and can directly distinguish signals and from the received signal [35]. The SINRs for to decode and can be written as
and
3.2. Second Phase
In , the UAV forwards the decoded with power to , and the BS sends a new signal to . At this time, attempts to intercept both and , while tries to intercept . By using the full-duplex mode, and simultaneously receive signals and transmit AN and with powers and to interfere with the corresponding eavesdroppers. Here, and denote the self-interference power coefficients at and in . Consequently, after self-interference cancellation, the received signal at can be expressed as . Since has prior information about , it can estimate and then cancel the interference term from . Based on this, the SINR for to decode in can be written as
where .
Similarly, the received signal at can be written as . Considering the worst case, can distinguish signals and . In this case, the SINRs for attempting to eavesdrop on and are written as
and
The user receives the relaying signal and its own AN. After self-interference cancellation, the received signal at can be written as . Therefore, the SINR for to decode is
Similarly, the received signal at can be expressed as . The SINR for to decode is given by
Note that the proposed scheme can be readily extended to a multi-antenna scenario using the existing transmit antenna selection technique [36]. The proposed scheme can be expanded to accommodate more users by utilizing existing user pairing methods, which helps manage system complexity within practical limits [37,38].
4. Performance Analysis and Optimization
This section derives the closed-form expressions for the ESSRs of the NN, NF, and FN for the proposed MNJJ under Case I and Case II to precisely characterize system security performance. Based on and , the achievable ergodic secrecy rate (ESR) for is [39,40,41,42]. Using and , the achievable ESR for is . The achievable ergodic rate of over the DF dual-hop link is limited by the weaker link. Additionally, needs to decode first and then decode in . Therefore, the achievable ergodic rate for at can be expressed as . The reception of at requires the assistance of the UAV relay, and thus, the achievable ergodic rate for at is also constrained by the poorer channel quality in the DF dual-hop link and can be expressed as . Due to the DF process of the UAV relay, has the opportunity to eavesdrop on during both and . Overall, if either or intercepts during the entire transmission period, it compromises communication security. Therefore, the achievable ergodic rate for at the eavesdroppers is given by . Based on this, the ESR for is .
For derivation, we present the following valid equations
and
where .
4.1. ESR for the Proposed MNJJ in Case I
4.1.1. NN in Case I
The following theorem provides the ESR of for the NN in Case I.
Theorem 1.
When legitimate nodes cannot know each other’s AN (i.e., Case I), the closed-form expression of the ESR for in the NN can be written as , where
and
where
, , , , , , , , and .
Proof.
See Appendix A. □
Based on (9) and (10), we let and . The CDFs of and can be easily obtained as and , where , , , and .
According to , the ergodic rate of at in the NN is , where , , , and . By using (6), (7), (11), (13), and , the ergodic rate of at the eavesdroppers in the NN can be rewritten as , where , , , and . Based on this, the ESR of for the NN in Case I is given in the following theorem.
Theorem 2.
In Case I, the closed-form expression of the ESR for in the NN can be written as , where
and
where , , . Additionally, we have
where , , , , , , , , , , , , , , , , , , , , , , and , , and are the complexity–accuracy trade-off parameters.
Proof.
See Appendix B. □
4.1.2. NF in Case I
When considering the NF in Case I, the conditions , , and hold. Based on , (5), and (8), the ESR of for the NF in Case I can be written as , where , , , and . When , degenerates into . Therefore, based on (A1), we can easily obtain . Using (14), (15), and [43] (Equation (3.352.4)), we can calculate as
By comparing and , we can use (23) to obtain
By observing (9) and (10), changes in the values of , , and have no effect on the SINRs for and to decode in . Hence, we have .
Let , , and . Based on , the ergodic rate of at for the NF in can be written as . Since , the CDF of can be directly obtained with the help of (A4), as shown by
Since is the same in both the NN and NF, we have . Using the order statistics and (20), the closed-form expression for is
where .
Moreover, based on , the ergodic rate of achieved by the eavesdroppers in this case can be rewritten as , where , , and . Recalling (22d), (22e), and (22f), we have , , and . Furthermore, utilizing (21), can be written as , where and .
Based on this, the ESR of for the NF in Case I is written as .
4.1.3. FN in Case I
Since , , and , the ESR of for the FN in Case I can be rewritten as , where , , , and . Following the similar steps in (A2), we have
and
Moreover, the ESR of for the FN in Case I is because and remain unchanged.
Based on and , the ergodic rates of achieved by and the eavesdroppers in this case can be rewritten as and , respectively, where , , , , , and . Therefore, we can obtain the CDFs of , , and by following similar derivation steps as in (22a), (22b), and (22c), which are given as
and
where .
Using the order statistics and (20), we have
where .
Similar to (22f), the CDF of can be given by .
4.2. ESR for the Proposed MNJJ in Case II
4.2.1. NN in Case II
The conditions , , and hold when considering for the NN in Case II. The SINRs and under these conditions are equivalent to and , respectively. Therefore, with the help of (17) and (23), the ESR for in this case can be directly written as .
The parameters , , and have no effect on and , and thus, the ESR for in this case is .
4.2.2. NF in Case II
For the NF in Case II, the conditions , , and hold. Under these conditions, the SINRs and become and , respectively. Based on (23) and (24), the ESR of in this case can be written as .
Similarly, the ESR for in this case can be directly given by .
Compared to the NF in Case I, only changes among the SINRs related to in the NF for Case II. Specifically, . Let . The CDF of can be written as
Based on , , and (37), the ESR of for the NF in Case II can be written as
4.2.3. FN in Case II
If turns off jamming and the UAV turns on jamming in , and the legitimate nodes are aware of each other’s AN, the SINRs and become and , respectively. The CDF of can be easily obtained as . Therefore, using (14) and [43] (Equation (3.352.4)), the ergodic rate of at in this case can be given by
Consequently, the ESR of in this case can be written as . Similar to , the ESR of for the FN in Case II can still be written as . In the FN, the SINRs related to are the same in Case I and Case II except for . The SINR in Case II is . Denote . The CDF of can be written as
4.3. ESSR for the Proposed MNJJ
Based on the derivation results in Section 4.1 and Section 4.2, the closed-form expression for the ESSR of the proposed MNJJ scheme under various cases can be uniformly expressed as
where .
4.4. The Proposed JPAIC Algorithm
This section focuses on maximizing the ESSR of the proposed MNJJ scheme by jointly optimizing the power allocation coefficients and interference power coefficients while ensuring the security of each signal transmission. Using the obtained as the objective function, we can formulate the corresponding mathematical optimization problem as
where represents the optimization accuracy of the variables to be optimized, (43a) restricts the range of power allocation coefficients to satisfy the downlink NOMA criteria, (43c) and (43d) specify the range of interference power coefficients and to comply with the state of interference activation or deactivation for the UAV and under different cases, (43e) ensures that and always have interference activated in and that the interference power does not exceed the preset maximum value, and (43f) guarantees that the ESRs of all signals are greater than zero.
The closed-form expression for the optimal solution of the power allocation coefficients and interference coefficients cannot be directly obtained for the above problem. Therefore, we design a JPAIC algorithm using PSO. As shown in Algorithm 1, the five variables to be optimized are treated as particles in a five-dimensional space. By iteratively searching the positions of multiple particles, the optimal fitness value (i.e., the maximum of ) can be obtained. Moreover, the computational complexity of the proposed JPAIC algorithm mainly depends on lines 4–17 in Algorithm 1. Therefore, the computational complexity of the proposed JPAIC algorithm can be easily obtained as , where represents the computational complexity primarily caused by addition and multiplication in (42).
| Algorithm 1 JPAIC Algorithm Using PSO |
|
5. Simulation Results
This section employs Monte Carlo simulations to verify the performance merits of the proposed MNJJ scheme and the proposed JPAIC algorithm, as well as the validity of the theoretical analysis. In the simulations, we consider two node location configurations: Location 1 and Location 2. In Location 1, the coordinates of the BS, UAV, , , , and are , , , , , and , respectively. In Location 2, these coordinates change to , , , , , and . We set the carrier frequency to GHz, , the maximum interference power to dBm, and the noise power to dBm. Additionally, we investigate the performance of the proposed MNJJ scheme under both fixed and optimal power allocation and interference control settings. For the fixed power setting (FPS), the fixed power allocation coefficients are and , and the fixed interference power coefficients are and . Specifically, we examine: (1) the NN with ; (2) the NF with and ; and (3) the NF with and . Unless otherwise specified, we set the shape parameter of the Nakagami-m channel to 2, the ratio of residual interference to noise power to dB [34], the optimization precision to , the particle swarm size to , and the number of iterations to . The markers “NN-I”, “NF-I”, “FN-I”, “NN-II”, “NF-II”, and “FN-II” in the following figures represent NN, NF, and FN in Case I and Case II, respectively. The marker “CNC-I” refers to the CNC scheme in Case I, with the CNC referenced in [27].
5.1. Case I
Figure 4 compares the ESSR of the proposed MNJJ scheme with three types (i.e., the NN, NF, and FN) with that of the CNC scheme in Case I. In this figure, the theoretical curves of the ESSR for the proposed MNJJ perfectly coincide with the corresponding simulation values, which validates the correctness of the theoretical analysis. Under different node location settings, the ranking of the ESSR from highest to lowest is consistently the NF, NN, FN, and CNC. The superiority in ESSR for the proposed MNJJ is attributed to multi-node joint jamming. Since legitimate nodes are unaware of each other’s AN in Case I, the simultaneous interference from the UAV and (i.e., the NN) excessively reduces the SINRs of and at the legitimate nodes. Based on this, the NN has a lower ESSR than the NF in Case I. Compared with the NF, only the UAV in the FN is enabled for interference, and the distance from the UAV to is much greater than the distance from to . Therefore, the UAV has the similar interference intensity on and in the FN, making it impossible to guarantee the secrecy rates of and . This fact, in turn, causes the ESSR of the FN to be slightly lower than that of the NN. Additionally, in the Location 2 configuration, the legitimate nodes and are closer to the corresponding information sources than the eavesdroppers, leading to a higher ESSR in Location 2 compared to Location 1. From the perspective of ESSR performance, the NF scheme is more suitable for Case I.
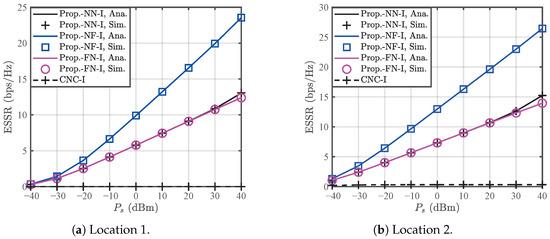
Figure 4.
Comparison of the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case I.
Figure 5 illustrates the impact of the shape parameter m of the A2G/G2A channel on the ESSRs for the proposed MNJJ and the CNC under dBm in Case I. From Figure 5, the proposed NF consistently achieves a higher ESSR than both the NN and FN for different values of m, and the ESSRs of the NN and FN are almost identical. These observations are consistent with the findings in Figure 4. The increase in m has a relatively small impact on the ESSR of each scheme. Typically, a larger m indicates better A2G/G2A channel quality. Since only the link related to in the legitimate links is affected by the A2G/G2A channel, and the ergodic rate of contributes relatively less to the ergodic sum rate, the effect of a larger m on the ergodic sum rate of the legitimate nodes is minimal. Additionally, the eavesdroppers are located near the legitimate users and the ergodic rate of being intercepted is also constrained by the weaker link in the DF two-hop link. Hence, the variation in m has no significant effect on the ergodic sum rate at the eavesdroppers. Based on this, all schemes exhibit good robustness to changes in m.
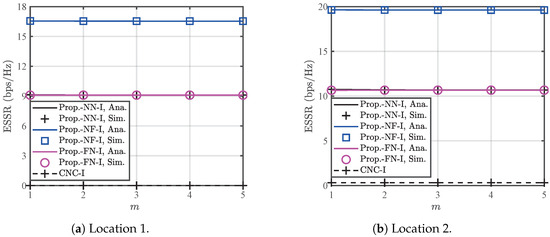
Figure 5.
Impact of the A2G/G2A channel shape parameter m on the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case I when dBm.
Figure 6 shows the variation in ESSR for each scheme under different strengths of the residual interference caused by full-duplex operation. The proposed NF consistently achieves the best ESSR across different values of . As increases, the ESSRs of the proposed NN, NF, and FN gradually decrease, while the ESSR of the CNC remains unchanged. This is because the proposed MNJJ is affected by residual self-interference, and an increase in residual interference strength reduces the ergodic rate of legitimate information without impacting the eavesdropper. In contrast, the CNC scheme is not influenced by these factors.
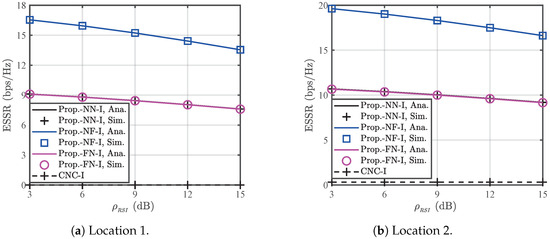
Figure 6.
Impact of on the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case I when dBm.
Figure 7 illustrates the variation in ESSR for the proposed MNJJ scheme with the number of iterations of the JPAIC algorithm, with the NN and NF in Case I as examples. The figure shows that the ESSR achieved by the proposed JPAIC algorithm quickly stabilizes after a relatively small number of iterations, indicating its good convergence performance. Note that this convergence analysis also applies to Case II.
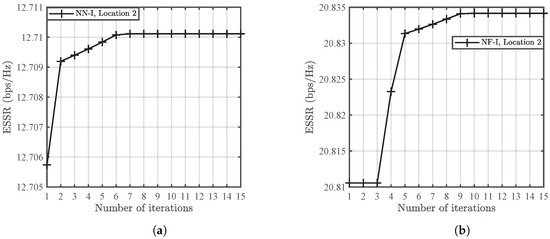
Figure 7.
Examples of the convergence analysis of the proposed JPAIC algorithm with dBm. (a) Example 1: NN in Case I with Location 2. (b) Example 2: NF in Case I with Location 2.
Figure 8 compares the ESSR of the proposed JPAIC algorithm with that of the FPS, where the proposed JPAIC maximizes the ESSR under the constraint of the ESR for each data stream. The coincidence of the ESSR curve with the corresponding theoretical optimal value (TOV) demonstrates the effectiveness of JPAIC, where the TOV is obtained via an exhaustive search under precision constraints. For the NN and NF, using the proposed JPAIC achieves a better ESSR compared to using FPS because it determines the optimal power allocation and interference power coefficients. An interesting observation is that in Location 1, the ESSR for the FN using both JPAIC and FPS is zero, as the FN struggles to meet the ESR constraints for all data streams. In Location 2, the FN only fails to ensure the security of all data streams at high transmission power. This is because, in Location 2, the legitimate nodes have better channel quality than the eavesdroppers for acquiring information, but high transmission power also allows the eavesdroppers to obtain more legitimate information.
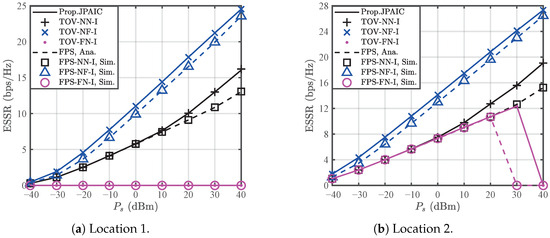
Figure 8.
Comparison of the ESSR performance of the proposed JPAIC algorithm and FPS in Case I.
5.2. Case II
Figure 9 shows the ESSRs for the CNC and the proposed MNJJ with the NN, NF, and FN under the condition that legitimate users are aware of each other’s AN. In Case II, the ESSR of the proposed MNJJ is superior to that of the CNC. Additionally, the proposed FN performs slightly better than the NN and NF at low to moderate transmission power, but the reverse is true at high transmission power. This is because interference initiated by and the UAV in weakens the achievable ergodic rates of and at the legitimate nodes due to self-interference, and the ergodic rate of contributes relatively less to the overall achievable ergodic rate. Therefore, the FN can more effectively achieve better ESSR at low to moderate transmission power. However, at high transmission power, the FN cannot prevent eavesdroppers from obtaining more legitimate information due to insufficient interference, resulting in a lower ESSR compared to the NN and NF. Overall, the FN is suitable for small in Case II, while the NF is a more robust choice under all conditions. Figure 10 shows the impact of the shape parameter m on the ESSR of each scheme in Case II. For reasons similar to those in Figure 5, the ESSR remains essentially unchanged with the increase in m. Figure 11 demonstrates that in Case II, the residual self-interference strength remains an important factor affecting the ESSR of the proposed MNJJ.
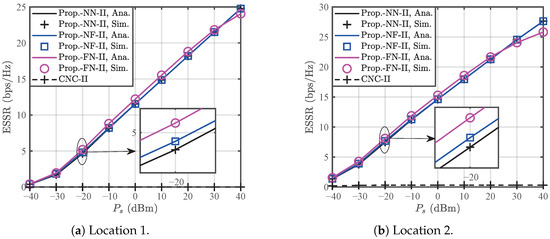
Figure 9.
Comparison of the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case II.
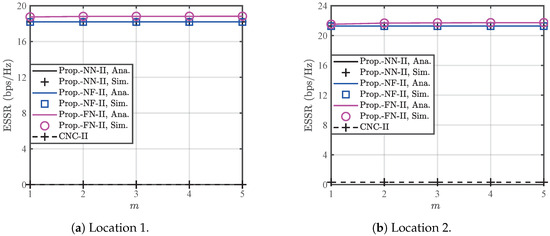
Figure 10.
Impact of the A2G/G2A channel shape parameter m on the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case II when dBm.
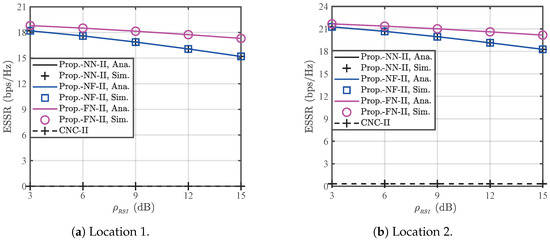
Figure 11.
Impact of on the ESSRs of the CNC scheme and the proposed MNJJ scheme with the NN, NF, and FN in Case II when dBm.
Figure 12 compares the ESSR of the proposed JPAIC with that of the FPS in Case II. From this figure, the effectiveness of the proposed JPAIC in optimizing the ESSR of the proposed MNJJ is validated. Notably, when legitimate users are closer to the corresponding information sources than the eavesdroppers, the FN scheme using the FPS fails to ensure secure transmission of all data streams at high transmission power. However, the proposed JPAIC can address this issue. Therefore, it is evident that the proposed JPAIC not only maximizes the ESSR of the proposed MNJJ but also enhances the robustness of the ESSR performance of the proposed MNJJ. Note that when global channel state information is available at the BS, the BS can use a mini phase before information transmission to send appropriate signaling to and the UAV to control whether and the UAV should turn on jamming. Based on the above simulation validation and discussion, we know that even if global channel state information is not available at the BS, the system can preset and the UAV to be in the turn-on jamming and turn-off jamming state (i.e., NF) during the first phase to achieve robust and good ESSR performance.
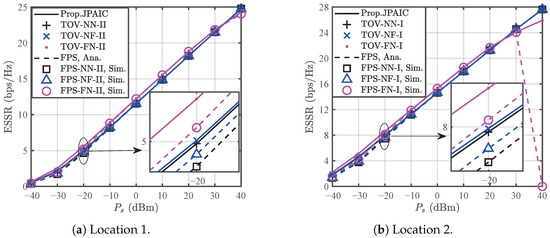
Figure 12.
Comparison of the ESSR performance of the proposed JPAIC algorithm and FPS in Case II.
6. Conclusions
This work investigated the physical layer secure transmission in a UAV-assisted NOMA-CDRT system for emergency rescue scenarios. In this system, the BS serves a user in its cell while also using a UAV relay to serve a user in a cell with damaged communication facilities, with eavesdroppers near all users threatening communication security. To ensure secure transmission, we proposed three types of AN-based MNJJ schemes for the considered system, namely NN, NF, and FN. Additionally, the closed-form expressions of the ESSR for the proposed MNJJ schemes were derived under the conditions where legitimate nodes are unaware of AN (i.e., Case I) and aware of AN (i.e., Case II). A JPAIC algorithm using PSO was also designed to further maximize the ESSR while ensuring the secure transmission of each data stream. The simulation results showed that the ESSR of the proposed MNJJ was superior to that of the CNC, and the proposed JPAIC maximized the ESSR of the proposed MNJJ and outperformed the FPS. Furthermore, in Case I, the NF was a preferable secure transmission scheme, while in Case II, the FN provided the best ESSR at low to moderate transmission power, but the NF remained a more robust choice across the entire transmission power range. In future work, we will extend the proposed scheme to multi-antenna scenarios and further enhance its security performance through beamforming design.
Author Contributions
Conceptualization, Y.X. and L.L.; methodology, Y.X. and S.J.; software, Y.X., S.J. and J.G.; validation, Y.X. and J.Z.; investigation, Y.X., J.Z. and L.L.; resources, S.J. and J.G.; data curation, Y.X.; writing—original draft preparation, Y.X. and S.J.; writing—review and editing, J.G., J.Z., L.L. and Z.Z.; supervision, Z.Z.; project administration, S.J. and Z.Z.; funding acquisition, Y.X., S.J., J.G., J.Z. and L.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Natural Science Foundation of Jiangsu Province under Grant BK20220438 and Grant BK20220439; in part by the National Natural Science Foundation of China under Grant 62301268; in part by the Natural Science Foundation of the Higher Education Institutions of Jiangsu Province under Grant 22KJB510033, under Grant 23KJB510031, and Grant 22KJB510005; in part by the Startup Foundation for Introducing Talent of NUIST under Grant 2023r015 and Grant 2023r134; in part by Henan Key Laboratory of Visible Light Communications under Grant HKLVLC2023-A01; and in part by the Henan Province Science and Technology Research Project under Grant 222102210097.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
This paper uses the following abbreviations:
| A2G | Air-to-ground |
| AF | Amplify-and-forward |
| AN | Artificial noise |
| AWGN | Additive white Gaussian noise |
| BS | Base station |
| CDF | Cumulative distribution function |
| CDRT | Coordinated direct and relay transmission |
| CNC | Conventional NOMA-CDRT |
| DF | Decode-and-forward |
| ESR | Ergodic secrecy rate |
| ESSR | Ergodic secrecy sum rate |
| FPS | Fixed power setting |
| G2A | Ground-to-air |
| G2G | Ground-to-ground |
| JPAIC | Joint power allocation and interference control |
| LoS | Line-of-sight |
| MNJJ | Multi-node joint jamming |
| NOMA | Non-orthogonal multiple access |
| OMA | Orthogonal multiple access |
| Probability density function | |
| PSO | Particle swarm optimization |
| SIC | Successive interference cancellation |
| SINR | Signal-to-interference-plus-noise ratio |
| STAR-RIS | Simultaneously transmitting and reflecting reconfigurable intelligent surface |
| SWIPT | Simultaneous wireless information and power transfer |
| TOV | Theoretical optimal value |
| UAV | Unmanned aerial vehicle |
Appendix A. Proof of Theorem 1
Proof. In this case, we have , , and . Therefore, by using , (5), and (8), the ergodic rates of at and for the NN in Case I can be expressed as and , respectively, where and . Based on [43] (Equation (3.351.3)), the CDF of can be calculated as
where , , and are defined in (18). Substituting (A1) into (14), and performing the double factorization operation according to (15), we obtain
where , , , and . By sequentially applying the variable substitution and [43] (Equation (3.351.4)) to , we obtain
Appendix B. Proof of Theorem 2
Proof. By using [43] (Equation (3.326.2)), the CDF of can be calculated as
where , , , and can be found in (22a) and Theorem 1.
Similarly, the CDF of can be written as
Applying the binomial expansion to and further utilizing [43] (Equation (3.326.2)), we can calculate (A5) as
where is defined in (22b), and , , and can be found in Theorem 1.
Using the binomial expansion and [43] (Equation (3.326.2)), the CDF of can be calculated as
where and can be found in Theorem 1.
Based on the order statistics, we can use (A4), (A5), and (A6) to obtain the CDF of as . Furthermore, we have for and for , where refers to Theorem 1.
Using (14) and Gaussian–Chebyshev quadrature, we can calculate as
Because and have the similar forms to , the CDFs and can be easily obtained by following the steps in (A7), which are provided in (22d) and (22e), respectively. Additionally, by comparing and , we find that the expression of for has a similar form to . Based on , , and (22a), the CDF of can be directly expressed as (22f).
Using the order statistics, we can calculate the CDF of as
According to (14), the ergodic rate of can be written as
Applying the Gaussian–Chebyshev quadrature to the first term of the above equation, and subsequently applying the variable substitution and Gaussian–Chebyshev quadrature to the second term, we obtain the expression for as given in (21). Combining and , we can obtain . □
References
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A Tutorial on UAVs for Wireless Networks: Applications, Challenges, and Open Problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Wang, D.; Yuan, L.; Pang, L.; Xu, Q.; He, Y. Age of Information-Inspired Data Collection and Secure Upload Assisted by the Unmanned Aerial Vehicle and Reconfigurable Intelligent Surface in Maritime Wireless Sensor Networks. Drones 2024, 8, 267. [Google Scholar] [CrossRef]
- Li, D.; Bao, N. Delay-Doppler Robust Spectrum Sharing of UAV and Terrestrial Systems Aided by Assistive Slots. IEEE Trans. Veh. Technol. 2021, 70, 7692–7704. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; de Cola, T.; Wang, J.-B.; Zhu, W.-P.; Cheng, J. Supporting IoT With Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE Internet Things J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D.; Popovski, P. Cellular, Wide-Area, and Non-Terrestrial IoT: A Survey on 5G Advances and the Road Toward 6G. IEEE Commun. Surv. Tutor. 2022, 24, 1117–1174. [Google Scholar] [CrossRef]
- Lou, Y.; Sun, R.; Cheng, J.; Qiao, G.; Wang, J. Physical-Layer Security for UAV-Assisted Air-to-Underwater Communication Systems with Fixed-Gain Amplify-and-Forward Relaying. Drones 2022, 6, 341. [Google Scholar] [CrossRef]
- He, Y.; Wang, D.; Huang, F.; Zhang, R.; Min, L. Aerial-Ground Integrated Vehicular Networks: A UAV-Vehicle Collaboration Perspective. IEEE Trans. Intell. Transp. Syst. 2024, 25, 5154–5169. [Google Scholar] [CrossRef]
- Wang, D.; Zhou, F.; Lin, W.; Ding, Z.; Al-Dhahir, N. Cooperative Hybrid Non-Orthogonal Multiple Access Based Mobile-Edge Computing in Cognitive Radio Networks. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 1104–1117. [Google Scholar] [CrossRef]
- Xu, Y.; Tang, J.; Li, B.; Zhao, N.; Niyato, D.; Wong, K.K. Adaptive Aggregate Transmission for Device-to-Multi-Device Aided Cooperative NOMA Networks. IEEE J. Sel. Areas Commun. 2022, 40, 1355–1370. [Google Scholar] [CrossRef]
- Wang, D.; Wu, M.; Chakraborty, C.; Min, L.; He, Y.; Guduri, M. Covert Communications in Air-Ground Integrated Urban Sensing Networks Enhanced by Federated Learning. IEEE Sensors J. 2024, 24, 5636–5643. [Google Scholar] [CrossRef]
- Li, X.; Wang, Q.; Zeng, M.; Liu, Y.; Dang, S.; Tsiftsis, T.A.; Dobre, O.A. Physical-Layer Authentication for Ambient Backscatter-Aided NOMA Symbiotic Systems. IEEE Trans. Commun. 2023, 71, 2288–2303. [Google Scholar] [CrossRef]
- Zhao, N.; Li, Y.; Zhang, S.; Chen, Y.; Lu, W.; Wang, J.; Wang, X. Security Enhancement for NOMA-UAV Networks. IEEE Trans. Veh. Technol. 2020, 69, 3994–4005. [Google Scholar] [CrossRef]
- Qian, L.P.; Zhang, W.; Wang, Q.; Wu, Y.; Yang, X. Alternative Optimization for Secrecy Throughput Maximization in UAV-Aided NOMA Networks. IEEE Wirel. Commun. Lett. 2022, 11, 2580–2584. [Google Scholar] [CrossRef]
- Wang, H.M.; Zhang, X. UAV Secure Downlink NOMA Transmissions: A Secure Users Oriented Perspective. IEEE Trans. Commun. 2020, 68, 5732–5746. [Google Scholar] [CrossRef]
- Yu, K.; Feng, Z.; Yu, J.; Chen, T.; Peng, J.; Li, D. Secure Ultra-Reliable and Low Latency Communication in UAV-Enabled NOMA Wireless Networks. IEEE Trans. Veh. Technol. 2024, 1–14. [Google Scholar] [CrossRef]
- Yapıcı, Y.; Rupasinghe, N.; Güvenç, İ.; Dai, H.; Bhuyan, A. Physical Layer Security for NOMA Transmission in mmWave Drone Networks. IEEE Trans. Veh. Technol. 2021, 70, 3568–3582. [Google Scholar] [CrossRef]
- Lu, W.; Ding, Y.; Gao, Y.; Chen, Y.; Zhao, N.; Ding, Z.; Nallanathan, A. Secure NOMA-Based UAV-MEC Network Towards a Flying Eavesdropper. IEEE Trans. Commun. 2022, 70, 3364–3376. [Google Scholar] [CrossRef]
- Guo, L.; Jia, J.; Chen, J.; Wang, X. Secure Communication Optimization in NOMA Systems With UAV-Mounted STAR-RIS. IEEE Trans. Inf. Forensics Secur. 2024, 19, 2300–2314. [Google Scholar] [CrossRef]
- Diao, D.; Wang, B.; Cao, K.; Dong, R.; Cheng, T. Enhancing Reliability and Security of UAV-Enabled NOMA Communications with Power Allocation and Aerial Jamming. IEEE Trans. Veh. Technol. 2022, 71, 8662–8674. [Google Scholar] [CrossRef]
- Sun, X.; Yang, W.; Cai, Y. Secure Communication in NOMA-Assisted Millimeter-Wave SWIPT UAV Networks. IEEE Internet Things J. 2020, 7, 1884–1897. [Google Scholar] [CrossRef]
- Deng, D.; Dang, S.; Li, X.; Ng, D.W.K.; Nallanathan, A. Joint Optimization for Covert Communications in UAV-Assisted NOMA Networks. IEEE Trans. Veh. Technol. 2024, 73, 1012–1026. [Google Scholar] [CrossRef]
- Diao, D.; Wang, B.; Cao, K.; Weng, J.; Dong, R.; Cheng, T. Secure Wireless-Powered NOMA Communications in Multi-UAV Systems. IEEE Trans. Green Commun. Netw. 2023, 7, 1205–1216. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, J.; Li, X.; Li, S.; Yuan, Z.; Pan, G. Secrecy Analysis for NOMA-Based Multi-Antenna Satellite-UAV-Terrestrial SWIPT Systems. IEEE Trans. Green Commun. Netw. 2024, 8, 672–685. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Hoang, T.M.; Tran, X.N. Secrecy Performance Optimization for UAV-Based Cognitive Relay NOMA System. IEEE Trans. Intell. Veh. 2024, 9, 4011–4024. [Google Scholar] [CrossRef]
- Zheng, X.; Zhang, J.; Pan, G. On Secrecy Analysis of Underlay Cognitive UAV-Aided NOMA Systems With TAS/MRC. IEEE Internet Things J. 2022, 9, 22631–22642. [Google Scholar] [CrossRef]
- Vo, V.N.; Nguyen, L.M.D.; Tran, H.; Dang, V.H.; Niyato, D.; Cuong, D.N.; Luong, N.C.; So-In, C. Outage Probability Minimization in Secure NOMA Cognitive Radio Systems With UAV Relay: A Machine Learning Approach. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 435–451. [Google Scholar] [CrossRef]
- Kim, J.B.; Lee, I.H. Non-Orthogonal Multiple Access in Coordinated Direct and Relay Transmission. IEEE Commun. Lett. 2015, 19, 2037–2040. [Google Scholar] [CrossRef]
- Xu, Y.; Cheng, J.; Wang, G.; Leung, V.C.M. Adaptive Coordinated Direct and Relay Transmission for NOMA Networks: A Joint Downlink-Uplink Scheme. IEEE Trans. Wirel. Commun. 2021, 20, 4328–4346. [Google Scholar] [CrossRef]
- Lv, L.; Jiang, H.; Ding, Z.; Yang, L.; Chen, J. Secrecy-Enhancing Design for Cooperative Downlink and Uplink NOMA with an Untrusted Relay. IEEE Trans. Commun. 2020, 68, 1698–1715. [Google Scholar] [CrossRef]
- Lv, L.; Li, Z.; Ding, H.; Zhou, Y.; Chen, J. Secure Coordinated Direct and Untrusted Relay Transmissions Via Interference Engineering. Sci. China Inf. Sci. 2022, 65, 182304. [Google Scholar] [CrossRef]
- Lei, H.; She, X.; Park, K.H.; Ansari, I.S.; Shi, Z.; Jiang, J.; Alouini, M.S. On Secure CDRT With NOMA and Physical-Layer Network Coding. IEEE Trans. Commun. 2023, 71, 381–396. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Chen, Y.; Zhao, N.; Ding, Z.; Alouini, M.S. Multiple UAVs as Relays: Multi-Hop Single Link Versus Multiple Dual-Hop Links. IEEE Trans. Wirel. Commun. 2018, 17, 6348–6359. [Google Scholar] [CrossRef]
- Gaafar, M.; Khafagy, M.G.; Amin, O.; Schaefer, R.F.; Alouini, M.S. Full-Duplex Relaying With Improper Gaussian Signaling Over Nakagami- m Fading Channels. IEEE Trans. Commun. 2018, 66, 64–78. [Google Scholar] [CrossRef]
- Liu, Y.; Qin, Z.; Elkashlan, M.; Gao, Y.; Hanzo, L. Enhancing the Physical Layer Security of Non-Orthogonal Multiple Access in Large-Scale Networks. IEEE Trans. Wirel. Commun. 2017, 16, 1656–1672. [Google Scholar] [CrossRef]
- Khan, A.S.; Chatzigeorgiou, I.; Lambotharan, S.; Zheng, G. Network-Coded NOMA with Antenna Selection for the Support of Two Heterogeneous Groups of Users. IEEE Trans. Wirel. Commun. 2019, 18, 1332–1345. [Google Scholar] [CrossRef]
- Xu, Y.; Cheng, J.; Wang, G.; Leung, V.C.M. Coordinated Direct and Relay Transmission for Multiuser Networks: NOMA or Hybrid Multiple Access? IEEE Wirel. Commun. Lett. 2021, 10, 976–980. [Google Scholar] [CrossRef]
- Xu, Y.; Li, B.; Zhao, N.; Chen, Y.; Wang, G.; Ding, Z.; Wang, X. Coordinated Direct and Relay Transmission with NOMA and Network Coding in Nakagami-m Fading Channels. IEEE Trans. Commun. 2021, 69, 207–222. [Google Scholar] [CrossRef]
- Jia, S.; Wang, R.; Xu, Y.; Lou, Y.; Zhang, D.; Sato, T. Secrecy Analysis of ABCom-Based Intelligent Transportation Systems with Jamming. IEEE Trans. Intell. Transp. Syst. 2024, 25, 2880–2892. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; He, Y.; An, K.; Zhong, X.; Chu, Z.; Xiao, P. Self-Powered Absorptive Reconfigurable Intelligent Surfaces for Securing Satellite-Terrestrial Integrated Networks. China Commun. 2024, 21, 276–291. [Google Scholar]
- Li, D.; Yang, X.; Zhou, F.; Wang, D.; Al-Dhahir, N. Mode Adaptive Secure UAV Relay Transmissions. IEEE Trans. Green Commun. Netw. 2023, 7, 787–799. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secrecy-Energy Efficient Hybrid Beamforming for Satellite-Terrestrial Integrated Networks. IEEE Trans. Commun. 2021, 69, 6345–6360. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic Press: New York, NY, USA, 2007. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).