Abstract
For image data, the processing of each pixel using a cryptographic hash function is linear, and the existing cryptographic hash function lacks parallel processing of image width and height. In order to improve the computational efficiency and ensure the security of the hash function in image cryptography, we design a 2D hyperchaotic map, whose good chaotic dynamics and randomness fully meet the needs of the hash function. Based on the proposed mapping, we propose an image-specific chaotic hash function for confusion diffusion and extraction in both width and height dimensions in parallel. The designed hash function of image cryptography can set some common hash lengths and also support the setting of key. For image data, the proposed method has higher computational efficiency than other common hash functions and has good encryption security and anti-collision characteristics.
MSC:
00A69; 94A60; 65P20
1. Introduction
The cryptographic hash function encrypts data of arbitrary length irreversibly into data of fixed length [1] and has important applications in the fields of message verification and digital signatures [2,3,4]. At present, the widely recognized safe hash functions include SHA-2 [5], which adopts block iteration, and SHA-3 [6] which adopts a sponge structure. For image data, these hash functions deal with linearly stored data, and the processing speed is proportional to the number of pixel data. With the increase in image resolution, the computational complexity of hash function increases square, so it is necessary to seek a secure hash function dedicated to the specific needs for processing image data.
Chaotic system provides a new solution for many encryption scenarios, and high randomness can be achieved by simple operation. Chaotic systems are used to develop novel image encryption schemes [7,8,9,10,11,12], speech encryption schemes [13,14,15], and secure communication schemes [16,17,18,19]. Figure 1 shows the bifurcation diagram of a part of traditional chaotic maps, from which it can be seen that there are problems of narrow chaos intervals and poor ergodicity. At the same time, traditional chaotic maps also show poor randomness; even after the systems completely enter the chaotic state, they will still produce false keys [20]. In order to meet the needs of the image security hash function, we need more random, ergodic, and sensitive maps.
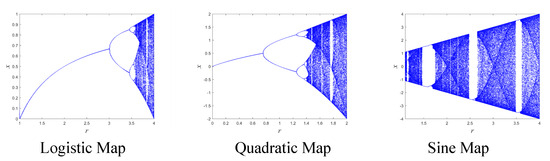
Figure 1.
Bifurcation diagrams of logistic map, quadratic map and sine map.
Hyperchaos exhibits positive Lyapunov exponents in multiple dimensions, thus being more sensitive to small perturbations and often exhibiting stronger complex chaotic behavior [21,22]. The construction of new hyperchaotic maps is a research hotspot at present. Wang et al. presented a novel two-dimensional cross hyperchaotic sine-modulation-logistic map (2D-CHSLM) aimed at enhancing image encryption schemes [23]. The 2D-CHSLM can be mathematically defined as Equation (1).
where and represent the state variables at iteration n, while r is a control parameter that influences the system’s chaotic behavior. (The symbols in Equations (2) and (3) have the same meaning). Wang et al. derived a novel chaotic two-dimensional hyperchaotic exponential adjusted logistic and sine map (2D-HELS) to enhance cryptographic applications [24]. The 2D-HELS can be mathematically defined as Equation (2).
Gao et al. proposed a novel two-dimensional cosine-logistic-sine map (2D-CLSM) aimed at addressing security shortcomings in existing image encryption schemes [25]. The 2D-CLSM can be mathematically defined as Equation (3).
These 2D hyperchaotic maps have greatly improved the performance of traditional chaotic maps. We hope to design a novel hyperchaotic map with more powerful performance by using nonlinear operations to further meet the needs of cryptography. In this study, we first design a new two-dimensional chaotic map and verify its superiority by using a variety of dynamic indicators and randomness tests. Based on the designed map, we propose a cryptographic hash function for image data and verify its excellent confusion diffusion characteristics and collision resistance. The main contributions of this paper can be summarized as follows:
- A novel 2D nondegenerate hyperchaotic map with two ideal positive Lyapunov exponents is proposed, and Testu01 tests its sequence randomness over existing related works.
- A special parallel cryptographic hash function for image data is designed based on 2D chaotic map, which ensures good security and exceeds the computational efficiency of existing general hash methods.
2. Proposed 2D Hyperchaotic Map
Constructing a highly cryptographically secure chaotic map requires the use of highly nonlinear operations. We select the structure of the classical Logistic chaotic map in the denominator and the structure of the existing work in the numerator. Sine operations, modulus operations, and remainder operations can achieve the stretching and folding of the motion trajectory of state points, ensuring the global bounded traversal of state variables [26]. The combination of the two can effectively ensure that the system presents a nondegenerate hyperchaotic state within a sufficiently large control parameter range, has good ergodicity, and avoids the generation of local windows and weak keys.
Combined with exponential, fractional, and other nonlinear operations, we transform the classical logistic map and design a new type of chaotic map, which is mathematically expressed by Equation (4):
where are state variables. The control parameter r is defined such that and serves to modulate the dynamical characteristics of the system. We named it 2D Exponential Fractional Logistic Hyperchaotic Map (2D-EFLHM). The bifurcation diagram of 2D-EFLHM for two state variables is presented in Figure 2, from which it can be seen that the system exhibits stable chaotic behavior.
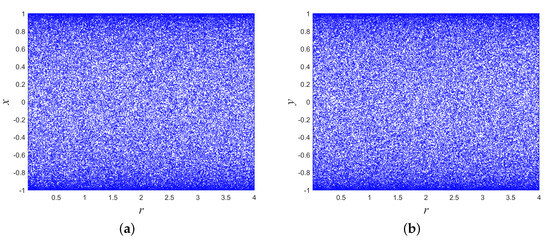
Figure 2.
Bifurcation diagrams for the state variables of proposed 2D-EFLHM, which indicate the strong chaotic behavior and complexity of our proposed system. (a) r–x. (b) r–y.
We selected three specific control parameters to present its phase portraits, as shown in Figure 3, showing complex attractor shapes and high-dimensional chaotic behavior and illustrating its applicability to the need for enhanced security and unpredictability.
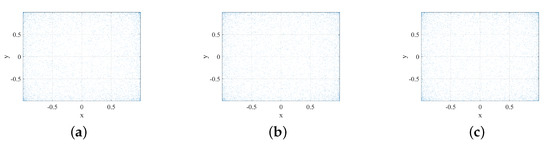
Figure 3.
Phase portraits of the 2D-EFLHM at three selected control parameters. (a) . (b) . (c) .
We further conducted qualitative analysis to demonstrate the chaotic performance of the map. Random control parameters and initial state variables were selected, and minor disturbances were applied to the system. The sequence visualization is shown in Figure 4. Even if there is a slight change in the initial state, the subsequent sequence will quickly undergo significant changes, thereby demonstrating the excellent chaotic characteristics of the system.
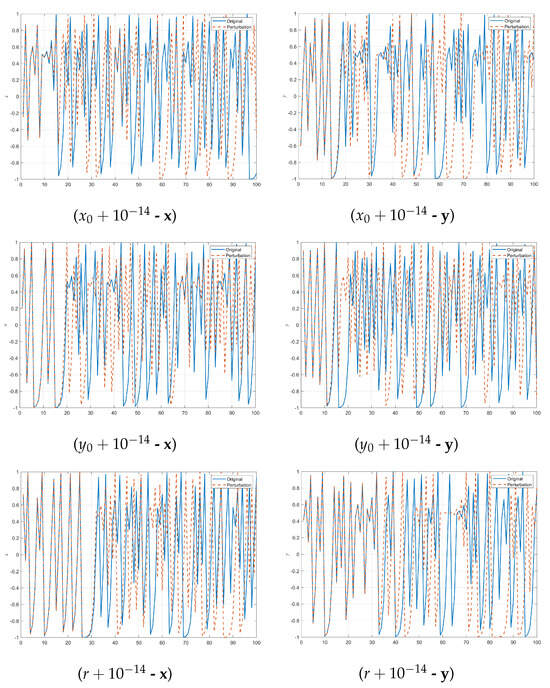
Figure 4.
Parameter and initial condition sensitivity. Random initial state variable ; control parameter .
After the qualitative analysis, in this section, we illustrate the chaotic characteristics and randomness of the system through rigorous dynamic indicators.
2.1. Lyapunov Exponent Analysis
The Lyapunov exponent quantifies the average separation velocity of nearby orbits, and a positive value indicates that the corresponding dimension of the system enters a chaotic state; the larger the value, the faster the trajectory separation. In the dynamical system , the mathematical definition of the Lyapunov exponent is given by Equation (5) [27].
Figure 5 shows that compared to other advanced chaotic systems, 2D-EFLHM has two positive Lyapunov exponents, and its value is higher, indicating that its chaotic behavior is more significant and stable.
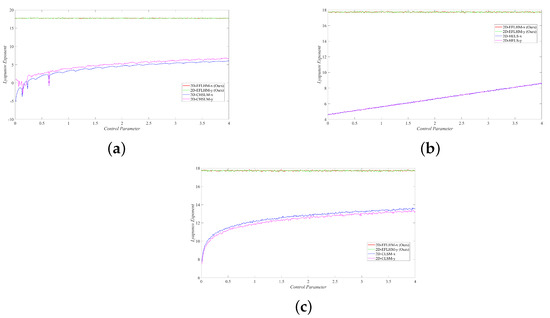
Figure 5.
Lyapunov exponents comparison. (a) 2D-EFLHM and 2D-CHSLM [23]. (b) 2D-EFLHM and 2D-HELS [24]. (c) 2D-EFLHM and 2D-CLSM [25].
2.2. Kolmogorov Entropy Analysis
Kolmogorov entropy estimates the complexity and chaos degree of a system by analyzing the relative distance changes between point pairs in phase space with different embedding dimensions. For a time series generated by a chaotic map, its Kolmogorov entropy can be calculated by Equation (6). It indicates different dimensions d and small thresholds that satisfy the distance being less than , which is the logarithm of the ratio of the number of points to each other [28].
Figure 6 shows the significant advantage of the 2D-EFLHM in terms of Kolmogorov entropy, indicating that its chaotic characteristics are higher and more suitable for application in the field of encryption.
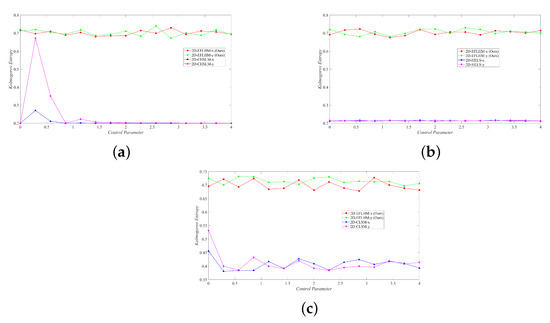
Figure 6.
Kolmogorov entropy comparison. (a) 2D-EFLHM and 2D-CHSLM [23]. (b) 2D-EFLHM and 2D-HELS [24]. (c) 2D-EFLHM and 2D-CLSM [25].
2.3. Approximate Entropy Analysis
ApEn is a statistical test indicator that measures the unpredictability of a time series, reflecting the likelihood that similar patterns in a time series will remain similar in the next state. For a time series , a sequence length m, and a tolerance threshold r, the sample entropy of ApEn can be calculated as follows [29]:
Figure 7 shows that the 2D-EFLHM also achieved competitive results in terms of Apen, with slightly higher values than other systems as the control parameters changed, indicating that the time series it generates is more difficult to predict.
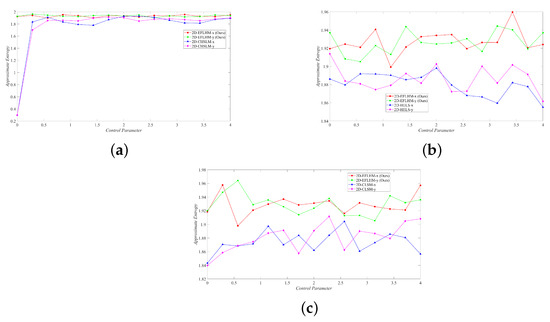
Figure 7.
ApEn comparison. (a) 2D-EFLHM and 2D-CHSLM [23]. (b) 2D-EFLHM and 2D-HELS [24]. (c) 2D-EFLHM and 2D-CLSM [25].
2.4. Complexity Analysis
complexity reflects the complexity of the system by assessing the volatility, which can be calculated as follows:
where is the mean of the entire series, and M is the total number of segments of length L [30]. Figure 8 compares the complexity of our designed 2D-EFLHM with that of other works, indicating that in the whole range of control parameters, 2D-EFLHM presents an ideal positive value, and its sequence is complex and difficult to predict, showing good pseudo-randomness.
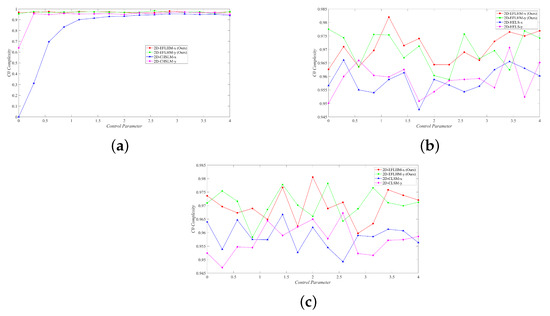
Figure 8.
complexity comparison. (a) 2D-EFLHM and 2D-CHSLM [23]. (b) 2D-EFLHM and 2D-HELS [24]. (c) 2D-EFLHM and 2D-CLSM [25].
2.5. Correlation Dimension Analysis
The correlation dimension provides the dimension information occupied by the attractor in the phase space of a chaotic system and is a measure to quantify the fractal structure and complexity of the chaotic attractor. A higher value indicates more complex and higher-dimensional chaotic dynamic behavior [31]. The correlation dimension is denoted as D and can be calculated as follows:
where N is the total number of embedded vectors, and r is the set small threshold.
Figure 9 shows that the designed 2D-EFLHM has a stable and higher correlation dimension, indicating that it has more complex fractal attractors and dynamic behaviors and exhibits stronger chaotic characteristics.
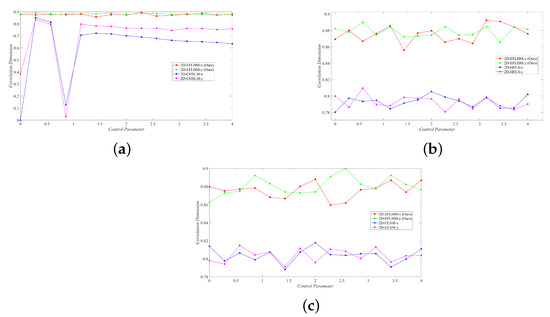
Figure 9.
Correlation dimension comparison. (a) 2D-EFLHM and 2D-CHSLM [23]. (b) 2D-EFLHM and 2D-HELS [24]. (c) 2D-EFLHM and 2D-CLSM [25].
2.6. Randomness Analysis
For cryptographic applications, the randomness of the mapping is a more important index. Testu01 is a widely recognized rigorous randomness testing tool, which is divided into small crush, crush, and big crush according to the difficulty of testing [32]. We randomly selected the initial value and effective control parameters of maps, multiplied the resulting chaotic sequence by a gain, and then tested its randomness, and the results are shown in Table 1.

Table 1.
Comparison of randomness test results. The number in parentheses is the number of failures.
Compared to the other maps, the designed 2D-EFLCM has fewer test failures and more stable high randomness under various conditions.
3. Parallel Image Cryptographic Hash Function
3.1. Key Generation
We took the control parameters and initial conditions of the 2D-EFLHM as the key and mapped the 128-bit key to the system state according to the rules of Algorithm 1.
| Algorithm 1 Key generation for 2D-EFLHM. |
|
Therefore, our hash function supports setting the key; when there is no key, we set a default key according to Equation (15).
3.2. Hash Value Generation
The idea of the proposed hash function is to process the image data in parallel and use chaotic map 2D-EFLHM to absorb the data and then extract them step by step. The detailed procedure is presented in Algorithm 2.
The multiplier was chosen because the sequence produced by the 2D-EFLHM according to the result of Testu01 had the highest randomness. Equation (16) can be used to implement the modular operation of large and medium integers quickly.
| Algorithm 2 Parallel image data hash function based on 2D-EFLHM (main algorithm). |
|
4. Security and Efficiency
4.1. Hash Values of Image Variants
We first performed a qualitative analysis to verify the validity of the hash function and preliminarily verify the sensitivity to input changes. Consider following five scenarios, with the results shown in Figure 10:

Figure 10.
Image variants for testing Algorithm 2.
- Scenario 1: Initial image named couple.
- Scenario 2: Gaussian noise with a ratio of 0.01 is added to the initial image.
- Scenario 3: Gaussian noise with a ratio of 0.1 is added to the initial image.
- Scenario 4: Change 1 bit to the initial image; the pixel pointed by the arrow has changed (left).
- Scenario 5: Change 1 bit to the initial image; the pixel pointed by the arrow has changed (right).
Table 2, Table 3 and Table 4 give the output for all the cases outlines above. The verification algorithm is effective; even if the input image is only slightly changed, the output hash value information will change fundamentally.

Table 2.
Image variants and hash values (128-bit).

Table 3.
Image variants and hash values (256-bit).

Table 4.
Image variants and hash values (512-bit).
4.2. Strict Avalanche Criteria (SAC) and Randomness
SAC refer to changes regarding any bit of the input data and half of the output data, which are important parts of the confusion diffusion in cryptography theory [34]. To test the SAC security of Algorithm 2, we constructed the following experiment:
- Select the original image: Couple.
- Change a single bit in the image.
- Calculate the Hamming distance between the hash values before and after the modification.
- Repeat N times.
All Hamming distances computed are denoted as (); some statistics are introduced for , where P represents the bit change rate, is the standard deviation of H, and is the standard deviation of P:
For different N values, the experimental data are shown in Table 5. In Figure 11, we visualize the case of . It can be seen that even if the input is only slightly changed by 1 bit, the output hash value has nearly half of the bits flipped, showing excellent diffusion performance.

Table 5.
SAC experiment results.
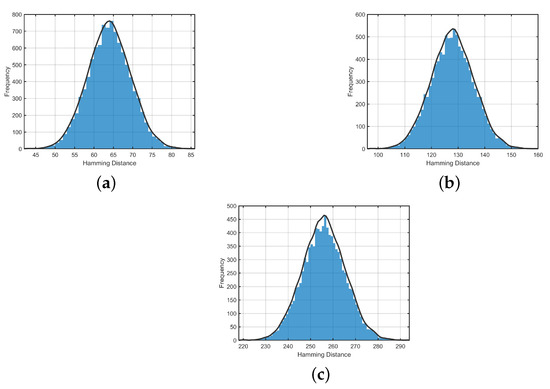
Figure 11.
Histogram visualization of Hamming distance. (a) 128-bit output. (b) 256-bit output. (c) 512-bit output.
We made a comparison using two generic secure hash functions and related chaotic hash functions using the same experimental conditions, and the results are shown in Table 6, where our work achieved competitive results.

Table 6.
SAC comparison with other algorithms (256-bit output, ).
The preimage attack requires that the output hash value does not contain any statistical information associated with the input, and the adversary cannot judge the input data from the hash value. Therefore, we hope that the output hash value is completely pseudo-random. We selected the hash value generated by the above experiment and tested its randomness using the NIST SP 800-22 suite [38]. The results as shown in Table 7 show that the generated hash value has very good randomness, and the input content cannot be inferred from the hash value.

Table 7.
The output hash value randomness test result.
4.3. Collision Attack
The second preimage attack is when two different inputs are found to produce the same hash output, which is called a collision. A good hash function must have strong anti-collision property. We constructed experiments similar to SAC:
- Select the original image: Couple.
- Change a single bit in the image.
- If there are two consecutive identical hexadecimal numbers in the same position (equivalent to an ASCII character), it is recorded as ONE hit.
- Count the number of hits.
- Repeat 2048 times.
The results of the experiments are shown in Figure 12, Figure 13 and Figure 14, from which we can see that it is very difficult to have a collision and have competitive results compared to other security algorithms.
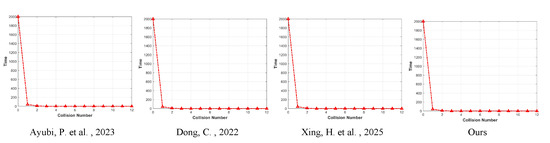
Figure 12.
Comparison of collision test results (128 bits). Ayubi, P. et al., 2023—[35] Dong, C., 2022—[36] Xing, H. et al., 2025—[37].
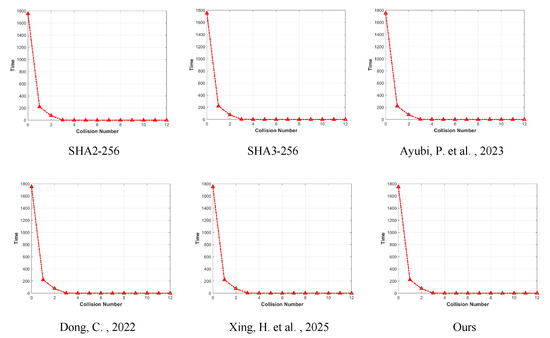
Figure 13.
Comparison of collision test results (256 bits). Ayubi, P. et al., 2023—[35] Dong, C., 2022—[36] Xing, H. et al., 2025—[37].
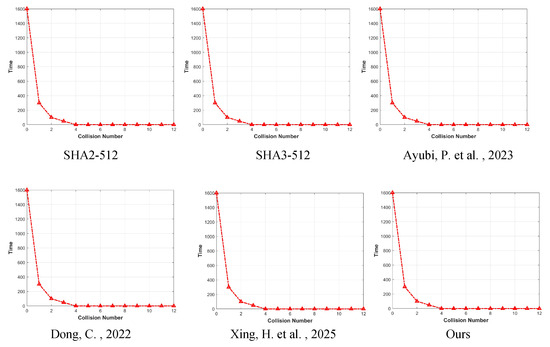
Figure 14.
Comparison of collision test results (512 bits). Ayubi, P. et al., 2023—[35] Dong, C., 2022—[36] Xing, H. et al., 2025—[37].
4.4. Computational Complexity Analysis
We designed a special hash function for image data, which realizes the parallel processing of two dimensions for the first time, and the computational complexity of image resolution is linear. The computational complexity and image resolution of common hash functions are squared, so Algorithm 2 has a special efficiency advantage for processing image data.
5. Conclusions
We constructed a nondegenerate hyperchaotic map 2D-EFLHM whose sequence randomness surpasses many similar works and exhibits excellent synthetic chaotic characteristics. Based on the powerful performance of 2D-EFLHM, we designed an image-specific hash function, which has excellent confusion diffusion performance, randomness and collision resistance, and which can resist many common attacks.
The designed hash function is highly suitable for processing high-resolution image data and is suitable for the primary usage scenarios of computing resources. However, the implementation of the chaotic map is based on computer floating-point simulation, so its application in the case where Ethereum smart contracts only support integers and fixed-point numbers will be limited. Future work could explore the application of 2D-EFLHM to other cryptographic domains and could also focus on specialized hash functions for other multimedia data.
Author Contributions
Method, M.Q.; Writing—original draft preparation, M.Q.; writing—review and editing, D.W.; software, D.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data presented in this study are available upon request from the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| 2D-CHSLM | two-dimensional cross hyperchaotic sine-modulation-logistic map |
| 2D-HELS | two-dimensional hyperchaotic exponential adjusted logistic and sine map |
| 2D-CLSM | two-dimensional cosine-logistic-sine map |
| 2D-EFLHM | two-dimensional exponential fractional logistic hyperchaotic map |
References
- Yang, Y.; Wan, H.; Yan, X.; Zhao, M.; Zeng, J.; Li, B. Parallel cryptographic hash function based on cellular automata and random diffusion model. Appl. Soft Comput. 2025, 169, 112546. [Google Scholar] [CrossRef]
- Shen, S.; Yang, H.; Dai, W.; Zhang, H.; Liu, Z.; Zhao, Y. High-Throughput GPU Implementation of Dilithium Post-Quantum Digital Signature. IEEE Trans. Parallel. Distrib. Syst. 2024, 35, 1964–1976. [Google Scholar] [CrossRef]
- Yang, W.; Fan, J.; Zhang, F. An Efficient Aggregate Signature Scheme with Designated Verifier Based on the Schnorr Signature in Healthcare Wireless Sensor Networks. IEEE Internet Things J. 2024, 11, 33788–33797. [Google Scholar] [CrossRef]
- Zhou, X.; Zhou, T.; Tian, Y.; Zhong, W.; Yang, X. Linearly Homomorphic Signature Scheme with High-Signature Efficiency and Its Application in IoT. IEEE Internet Things J. 2024, 11, 38126–38136. [Google Scholar] [CrossRef]
- FIPS PUB 180-4; Secure Hash Standard (SHS). National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2012. [CrossRef]
- FIPS PUB 202; SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2015. [CrossRef]
- Mansouri, A.; Sun, P.; Lv, C.; Zhu, Y.; Zhao, X.; Ge, H.; Sun, C. A secure medical image encryption algorithm for IoMT using a Quadratic-Sine chaotic map and pseudo-parallel confusion-diffusion mechanism. Expert Syst Appl. 2025, 270, 126521. [Google Scholar] [CrossRef]
- Gao, Q.; Zhang, X. Multiple-image encryption algorithm based on a new composite chaotic system and 3D coordinate matrix. Chaos Solitons Fractals 2024, 189, 115587. [Google Scholar] [CrossRef]
- Tong, X.; Liu, X.; Zhang, M.; Wang, Z. A high-quality visual image encryption algorithm utilizing the conservative chaotic system and adaptive embedding. Chaos Solitons Fractals 2024, 188, 115581. [Google Scholar] [CrossRef]
- Guang, Y.; Ding, Q. Dynamics analysis of a novel parametrically controllable symmetric multi-scroll chaotic system and FPGA design of an image encryption system. Chaos Solitons Fractals 2024, 188, 115572. [Google Scholar] [CrossRef]
- Su, Y.; Wang, X.; Gao, H. Chaotic image encryption algorithm based on bit-level feedback adjustment. Inf. Sci. 2024, 679, 121088. [Google Scholar] [CrossRef]
- Ding, D.; Zhu, H.; Zhang, H.; Yang, Z.; Xie, D. An n-dimensional polynomial modulo chaotic map with controllable range of Lyapunov exponents and its application in color image encryption. Chaos Solitons Fractals 2024, 185, 115168. [Google Scholar] [CrossRef]
- Huang, Y.; Li, C.; Li, Z.; Zhang, Q. Efficient speech encryption algorithm based on three-dimensional quadratic exponential robust chaos. Appl. Acoust. 2025, 235, 110672. [Google Scholar] [CrossRef]
- Huang, Y.; Wang, L.; Li, Z.; Zhang, Q. A new 3D robust chaotic mapping and its application to speech encryption. Chaos Solitons Fractals 2024, 184, 115038. [Google Scholar] [CrossRef]
- Herbadji, D.; Herbadji, A.; Haddad, I.; Kahia, H.; Belmeguenai, A.; Derouiche, N. An enhanced logistic chaotic map based tweakable speech encryption algorithm. Integration 2024, 97, 102192. [Google Scholar] [CrossRef]
- Feng, J.; Jiang, L.; Yan, L.; Yi, A.; Pan, W. 64-Gbit/s Optical-Domain Encrypted Chaotic Secure Communication Over 110-km Commercial Fiber. IEEE Photonics Technol. Lett. 2025, 37, 425–428. [Google Scholar] [CrossRef]
- Zhu, P.; Wang, H.; Zhang, Y. A Novel Secure Enhancement Chaotic Communication System Based on Merging Conversion Structure for Physical-Layer Encryption. IEEE Commun. Lett. 2023, 27, 2914–2918. [Google Scholar] [CrossRef]
- Sun, J.; Sun, C.; Wang, Z.; Wang, Y. Biosignals Secure Communication Scheme with Filtering of Active Control Projection Synchronization of Biological Chaotic Circuits with Different Orders Based on DNA Strand Displacement. IEEE Trans. Biomed. Circuits Syst. 2023, 17, 470–482. [Google Scholar] [CrossRef]
- Chen, G.; Yang, X.; Wang, Y.; Zhang, X. Impulsive control for synchronization of chaotic neural networks with multiple time-varying delays and its applications to secure communications. Inf. Sci. 2025, 694, 121702. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, Y.; Bao, H.; Lan, R.; Hua, Z. nD-CS: A circularly shifting chaotic map generation method. Chaos Solitons Fractals 2024, 181, 114650. [Google Scholar] [CrossRef]
- Wang, M.; Ding, J.; Zhang, X.; Iu, H.H.C.; Li, Z. A new construction method of N-dimensional discrete sine hyperchaotic map. Nonlinear Dyn. 2025, 113, 1879–1893. [Google Scholar] [CrossRef]
- Wang, X.; Cao, Y.; Xu, X.; Mou, J. A novel memristor-coupled hyperchaotic map: Dynamical analysis, linear transform control and encryption application. Eur. Phys. J. Plus 2024, 139, 480. [Google Scholar] [CrossRef]
- Wang, M.; Teng, L.; Zhou, W.; Yan, X.; Xia, Z.; Zhou, S. A new 2D cross hyperchaotic Sine-modulation-Logistic map and its application in bit-level image encryption. Expert Syst. Appl. 2025, 261, 125328. [Google Scholar] [CrossRef]
- Wang, M.; Fu, X.; Teng, L.; Yan, X.; Xia, Z.; Liu, P. A new 2D-HELS hyperchaotic map and its application on image encryption using RNA operation and dynamic confusion. Chaos Solitons Fractals 2024, 183, 114959. [Google Scholar] [CrossRef]
- Gao, X.; Liu, X. CLSM-IEA: A novel cosine-logistic-sine map and its application in a new image encryption scheme. Signal Image Video Process. 2024, 18, 3063–3077. [Google Scholar] [CrossRef]
- Si, Y.; Liu, H.; Chen, Y. Constructing a 3D Exponential Hyperchaotic Map with Application to PRNG. Int. J. Bifurcation Chaos 2022, 32, 2250095. [Google Scholar] [CrossRef]
- Hayashi, K. Chaotic nature of the electroencephalogram during shallow and deep anesthesia: From analysis of the Lyapunov exponent. Neuroscience 2024, 557, 116–123. [Google Scholar] [CrossRef]
- Zou, T.; Zhao, C.; Caraballo, T. Statistical solutions and Kolmogorov entropy for the lattice long-wave–short-wave resonance equations in weighted space. Commun. Nonlinear Sci. Numer. Simul. 2023, 127, 107516. [Google Scholar] [CrossRef]
- Zahid, M.U.; Nisar, M.D.; Shah, M.H. Radio Frequency Fingerprint extraction based on Multiscale Approximate Entropy. Phys. Commun. 2022, 55, 101927. [Google Scholar] [CrossRef]
- Cao, Y.; Cai, Z.; Shen, E.; Shen, W.; Chen, X.; Gu, F.; Shou, T. Quantitative analysis of brain optical images with 2D C0 complexity measure. J. Neurosci. Methods 2007, 159, 181–186. [Google Scholar] [CrossRef]
- Tian, H.; Guo, K. Chaotic characteristic analysis and prediction of bottleneck-delay time series under the Internet macro-topology. Eur. Phys. J. Plus 2024, 139, 494. [Google Scholar] [CrossRef]
- L’Ecuyer, P.; Simard, R. TestU01: A C Library for Empirical Testing of Random Number Generators. ACM Trans. Math. Softw. 2007, 33, 22. [Google Scholar] [CrossRef]
- Lin, Z.; Liu, H. An improved key expansion algorithm based on a 2D discrete hyper chaotic map with memristor. Eur. Phys. J. Spec. Top. 2024, 233, 1373–1380. [Google Scholar] [CrossRef]
- Xu, Y.; Zhao, M.; Liu, H. Design an irreversible key expansion algorithm based on 4D memristor chaotic system. Eur. Phys. J. Spec. Top. 2022, 231, 3265–3273. [Google Scholar] [CrossRef]
- Ayubi, P.; Setayeshi, S.; Rahmani, A.M. Chaotic Complex Hashing: A simple chaotic keyed hash function based on complex quadratic map. Chaos Solitons Fractals 2023, 173, 113647. [Google Scholar] [CrossRef]
- Dong, C. Constructing a discrete memristor chaotic map and application to hash function with dynamic S-Box. Eur. Phys. J. Spec. Top. 2022, 231, 3239–3247. [Google Scholar] [CrossRef]
- Xing, H.; Min, R.; Li, S.; Yang, Z.; Yang, Y. Hyperchaotic hashing: A chaotic hash function based on 2D linear cross-coupled map with parallel feedback structure. Sci. Rep. 2025, 15, 5462. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, N.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; NIST SP 800-22 Rev. 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).