Abstract
This study proposes a general approach to protect graphs using co-secure domination within jump graphs. In the context of graphs, a dominating set is a group of vertices that are either directly linked or connected to all other vertices within the graph. The minimum cardinality of the dominating set in a graph G is called the domination number . A set of a graph G is called a co-secure dominating set, if, for all there exists a node and in so that dominates the graph G. , the co-secure domination number, is the cardinality of a co-secure dominating set with minimum vertices within the graph G. It is a notable protective strategy in which the nodes that are attacked or damaged in an interconnection network can be replaced with alternative nodes to ensure network security. In a jump graph , the vertices are the edges of G and the adjacency of the vertices of are given by the condition that these edges are not adjacent in G. This paper explains how and are related for the jump graph of various graph classes. The study further determines the exact value for of specific standard graphs. Additionally, the study characterizes and a tight bond is identified for , particularly for G with specific conditions.
MSC:
05C69; 90B18
1. Introduction
Graph theory provides a framework for modeling interconnection networks as simple graph .
We denote cardinality of a vertex set as and the cardinality
of the edges as in . In interconnection networks, the network components
such as computers, routers, and nodes are represented as vertices while the connections
or communication links between them as the edges of the graph. This representation
facilitates the analysis and implementation of security strategies within interconnection
networks [1,2]. It aids in identifying critical nodes, assessing network vulnerabilities, designing redundant backup nodes for critical elements, implementing intrusion detection systems, and mitigating potential threats or attacks.
Domination in graphs plays a vital role in protecting interconnection networks. A set of G is a dominating set (DS), if every vertex in V is either in D or is directly linked to at least one vertex in D [3]. The strategical placement of mobile guards at particular vertices of the network secures an interconnection network from a variety of attacks and that set of guards forms a dominating set. The smallest number of guards needed to protect the entire network is the domination number (DN), and it is denoted by . To enhance network resilience against node failures or attacks, various domination variants have emerged [4]. Co-secure domination (CSD) is one such variant that provides an additional layer of protection to the network by allowing the replacement of attacked or damaged nodes with an alternative one without affecting the criterion for dominating set [5]. The co-secure domination number (CSDN) is the minimum number of guards required to secure the network by providing backup mobile guards. The historical basis of the concept of graph protection as well as various strategies for optimizing the existing models are described in [4,5,6]. A characterization of Mycielski graphs with = 2 and 3 is given in [7,8]. An iterative formula for calculating the CSDN of Sierpinski networks is given in [9].
The essential graph concepts utilized in this paper are outlined below. For additional explanations on these basic concepts and key results related to domination, please refer to [3]. The degree of a vertex , denoted by , signifies the number of edges incident with v in a graph G. The maximum number of edges incidents with a vertex in G is and the minimum number of edges incidents with a vertex is denoted by . The open neighborhood of a vertex v is defined as and its closed neighborhood is denoted by , which is the set . The number of neighbors of an edge is called the , where . Let and ; if , then u is a T- external private neighbor (epn) of v. The set of all T-epns of v is represented by [5]. For all the vertices is the of u and the maximum eccentricity is the of the graph denoted by . That is, . The circumference of a graph is defined as the length of the longest cycle, denoted as .
Various symbols are used to denote distinct graph classes. The path graph is represented as , the cycle graph as , and the complete graph as , where n indicates the number of vertices. Additionally, denotes the complete bipartite graph with two sets, one containing m vertices and the other containing n vertices, and denotes the star graph. The Cartesian product of two graphs , and , denoted by , is the graph with the vertex set , and any two vertices are adjacent if and only if either and or and . The vertex corona product of G and H is the graph , obtained by taking one copy of G, called the center graph, copies of H, called the outer graph, and making the vertex of G adjacent to every vertex of the copy of H, where . The vertex corona product is one of the well-known graph products. It has many real time applications in chemistry, computer, and social networks.
Line Graphs and Jump Graphs
The line graph of an undirected graph G is another graph in which each edge in G is a vertex in [10]. Two vertices in are adjacent if the corresponding edges of G are incident, and vice versa. This graph is also called the ’edge graph’ because it focuses on the connections between the edges of the original graph [11,12]. Some observations about the line graph of certain graph classes used in this article are given here [13].
- ;
- ;
- .
This article examines the CSDN of jump graphs , which are the complements of edge-independent edge graphs or line graphs [10]. Chartrand et al. [13] presented the concept of the jump graph and the domination number of these graphs was discussed by Maralabhavi et al. [14]. The domination number of the jump graphs was discussed in [14].
Figure 1 illustrates the transformation of G into its . The edges of G serve as the vertices of . It is to be noted that edges that are adjacent in G are not adjacent in . Bold vertices indicate the dominating vertices. It is clear that all vertices in the original graph and its jump graph are either bold or adjacent to bold vertices.
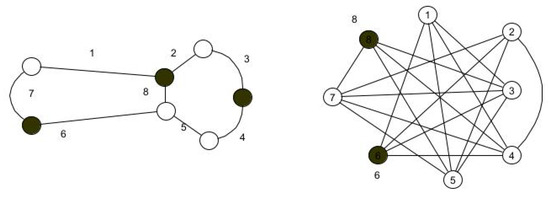
Figure 1.
(left) Graph G. (right) Jump graph .
This paper includes the following observations:
- The determination of the exact values of the CSDN for jump graphs of specific standard graphs;
- The calculation of the CSDN of jump graphs derived from various graphs classes, such as Windmill, Barbell, Sunlet, Helm, and Lict graphs;
- The characterization of jump graphs with a CSDN of 2;
- The establishment of a tight bond for the CSDN of jump graphs;
- An investigation of the relationship between the CSDN of a jump graph and its underlying graph, particularly under specific conditions related to the graph’s circumference and other parameters.
2. CSDN of Jump Graphs
A set of a jump graph is called a co-secure dominating set (CSDS) if for every there exists a vertex and in the compliment of S such that dominates . The cardinality of the smallest co-secure dominating set is represented by , which is the co-secure domination number (CSDN) of the jump graph. If has isolated vertices, then CSDS does not exist.
Preliminary findings and observations about the CSDN of the line graph of , , and are summarized in [5,15]: , , and .
Bounds and Exact Values for CSDN of Jump Graphs
The analysis of of certain graph families results in the following theorem. It is easy to prove the following two theorems.
Theorem 1.
- 1.
- 2.
- .
- 3.
- .
- 4.
- If G is a Spider tree or a Lobster tree with , .
- 5.
- for all
- 6.
- For the Wheel Graph
A careful analysis of CSDN with the jump graphs of distinct graph classes yielded the following result.
Corollary 1.
For a connected graph G with n vertices, then .
3. Characterization of CSDN of Jump Graphs in Various Graph Classes
The jump graphs of certain derived graphs were analyzed for their CSDN, and a characterization of for these derived graphs was conducted. Graph families under consideration are (i) Cartesian product of graphs, (ii) Windmill graphs, (iii) Barbel graphs, (iv) line graphs, (vi) Sunlet graphs, and (vii) Helm graphs.
Theorem 2.
if G is any one of the following three graph families:
- (i)
- G has no pendant vertices or G is a tree, and
- (ii)
- It is an Eulerian graph with
Proof.
Case (i): Suppose G has no pendant vertices and .
Consider a graph G with n vertices without isolated vertices, , m edges and . Let be the longest path in G and be the edges in G. By definition, the edges , , , …, are vertices in . For the vertices and in , , , …, and , , , , …, [13]. Choose a subset , where . Since all the vertices of are either in S or in or in , S is a dominating set for . The vertex can be replaced by the vertex so that the set ( is a dominating set of . The vertex can be replaced by , since the vertex , and the set { }) ∪ {} is a dominating set.
Thus, the set is a CSDS of with cardinality 2. This is the minimum CSDS because removing a vertex from S disrupts the dominating property of the graph. Hence, .
Case (ii): For any tree T with
Let be a path of maximum length in the tree T with pendant vertices and whose supporting edges are and , respectively. The edges of T are the vertices in and the total number of vertices in . Consider the set . Since in , by definition of jump graphs, and . Thus, Hence, S is a DS of and . There exists a vertex so that . Thus, the vertex replaces the vertex . S is a CSDS since , and Thus, .
Similarly, , where the vertex Thus replaces in S. Since a single vertex in S cannot dominate all vertices in , the minimum cardinality is at least two. Thus, . Thus, , by the above arguments.
Case (iii): Suppose G is an Eulerian graph,
By definition, if G is an Eulerian graph, the graph possesses a closed trail that traverses each edge exactly once. The trail is a closed path with a diameter greater than 3 for . Hence, as proved in Case (i) of this theorem, □
The following theorem identifies specific graph classes in which .
Figure 2 illustrates the cartesian product (c) of the graphs (a) and (b)
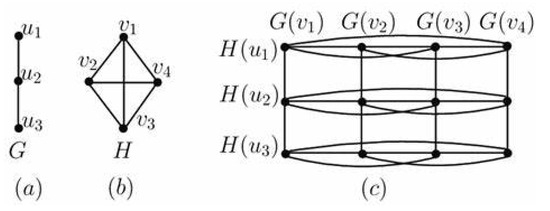
Figure 2.
(a) (b) (c) .
Theorem 3.
= if G is belonging to any one of the following graph families:
- (i)
- The cartesian product of graphs—.
- (ii)
- Windmill graph.
- (iii)
- Barbell graph.
Proof.
- (i)
- Consider the graph , where or or and or or or .We know that the Cartesian product of and is the grid graph , and N is the set of all natural numbers. We take . By definition of the Cartesian product of graphs, has vertices and edges. Thus the has vertices. The edges in can be , where and respectively. Choose a subset of , where . dominates all the vertices of . The vertex can be replaced by Also, the vertex can be replaced by the vertex in Thus, is a CSDS and its cardinality is 2. It is a minimum dominating set since a single vertex cannot dominate Hence, =A similar proof can be applied to the graph Let the edges in be respectively, where and It is obvious that the set is a DS of and . The vertex can be replaced by the vertex . Similarly, can be replaced by Removing a single vertex from will violate the definition of the dominating set of . HenceThus, can be a DS as well as CSDS with cardinality two.Similarly, using the above arguments, we can prove thatand .
- (ii)
- Windmill graph.Consider a windmill graph where Because all the complete graphs share this universal vertex, the domination number of the windmill graph is The bold vertex in Figure 3 shows this.
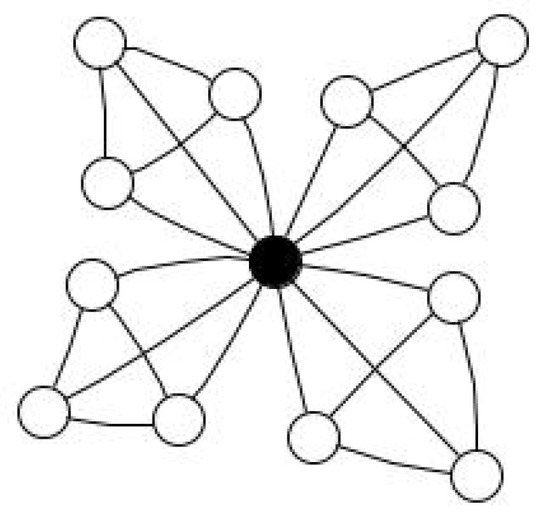 Figure 3. Windmill Graph with .Now, consider the jump graph of the windmill graph. Choose any two non-adjacent edges, excluding the edges incident with the universal vertex, to form a DS Every vertex in is dominated by . Any non-adjacent edge in may replace the vertex in , with the exception of the edges incident with the universal vertex in . In the same way, any non-adjacent edge in that is not incident with the edge can be used to substitute the vertex . This set has cardinality two, making it a CSDS. Furthermore, the required condition for DS is violated when one vertex is removed from . Therefore, .
Figure 3. Windmill Graph with .Now, consider the jump graph of the windmill graph. Choose any two non-adjacent edges, excluding the edges incident with the universal vertex, to form a DS Every vertex in is dominated by . Any non-adjacent edge in may replace the vertex in , with the exception of the edges incident with the universal vertex in . In the same way, any non-adjacent edge in that is not incident with the edge can be used to substitute the vertex . This set has cardinality two, making it a CSDS. Furthermore, the required condition for DS is violated when one vertex is removed from . Therefore, . - (iii)
- Barbell graph.We know that in a complete graph with n vertices, . Since two complete graphs are connected by a bridge, two end vertices of the bridge can be taken into the set , which is clearly a DS. The vertices u and v can be replaced by any x or y and , and hence is CSDS and hence Create a set by taking two edges that are non-incident with the bridge , where and . The edge is adjacent to all edges of and is adjacent to all edges of in because every edge in a complete graph is adjacent to every other edge. One of the DS of can be taken as . The vertex can be replaced by any edge of that is not incident with the bridge , and the vertex can be replaced by any edge of that is not incident with the bridge , where and . because removing a single vertex from the set would violate the condition of a dominating set. Hence, as a result.Figure 4 shows an illustration in which a Barbel graph and is its jump graph are given. The edges of the given graph (left figure) become the vertices in the jump graph (right figure) and the edge in the graph is a vertex that is adjacent to and in . The dominating vertices in the graph G and its jump graph are marked with bold vertices. □
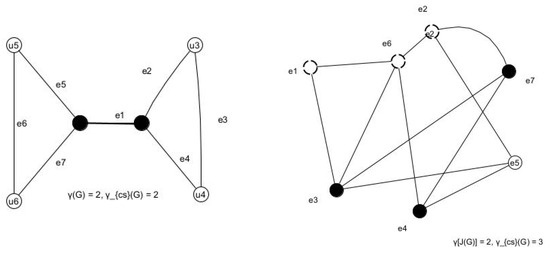 Figure 4. (left) Barbel Graph. (right) Jump graph of Barbel graph.
Figure 4. (left) Barbel Graph. (right) Jump graph of Barbel graph.
Based on our analysis, it can be demonstrated that for any graph G from the family shown in the Figure 5, we have . These graphs have a minimum degree and satisfy .
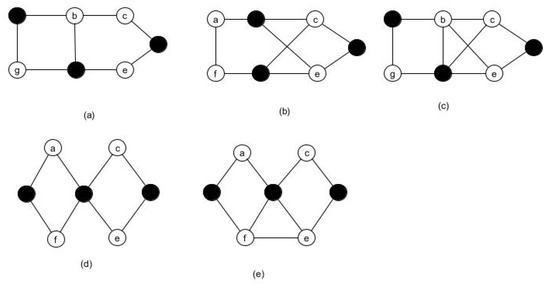
Figure 5.
A family of graphs (a–e) with .
Corollary 2.
If with , then =
Muddebihal and Kulli introduced the concept of lict graphs in [16]. Lict graphs are the middle graphs of path graphs with [17]. Lict graphs and their corresponding jump graphs were examined for their CSDN. The lict graph is illustrated in Figure 6.
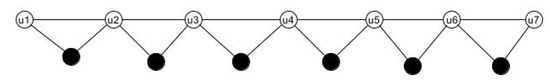
Figure 6.
Lict graph.
Theorem 4.
For a connected lict graph with and , then .
Proof.
Consider the given graph as a lict graph which is the middle graph of the path graph By definition, consists of vertices and edges. The vertex set of be . Consider the sets , where is defined as if n is odd and , if n is even. The set is a dominating set of , since every vertex in (. Every third vertex in the path graph is in the DS . The vertex can be replaced by for , so that the new set is a DS. Thus, is a CSDS. , and by removing a single vertex from the set, is no longer a DS.
Hence, CSDN of lict graph
Now, consider the jump graph of lict graphs. For all lict graphs , the and hence, by Theorem 3, □
Generalisation of CSDN of Jump Graphs
The following theorem provides a generalization of the CSDN for the jump graphs of all connected graphs with a maximum degree and circumference
Theorem 5.
For any connected graph G, with and ,
Proof.
It is obvious that for all connected graphs with . We divide the graph families based on the diameter.
- Case 1:
- .In this class of graphs, since , every vertex in G is adjacent to every other vertex. Since at least two edges in G are non adjacent. Hence, for This can be illustrated by taking the cases of any complete graph . It is clear that . Thus,
- Case 2:
- , , and
- Case 2 (i):
- Graphs without pendant vertices.Clearly, the DS of G will contain u, the vertex with the maximum degree. Take any edge to the DS of , provided the edge is not incident with the vertex u. Since , the edge is adjacent to all edges in G except the edges that are incident to in G. Let dominate all the edges incident to in G. The set is a DS. It is possible to replace by the vertex , where is incident at the vertex . But the set cannot dominate all vertices in . Hence, , where dominates all the edges incident on the vertex u of G. Thus, .
- Case 2 (ii):
- Graphs with pendant vertices.Here, we consider the vertex with a maximum degree in G. Those edges in G that are not incident to the vertex with a maximum degree can enter the DS of . We consider graphs with a single pendant vertex because an increase in the number of pendant edges increases the . As the increases, since the number of non-incident vertices with a maximum degree vertex is equal to the edges in + no. of pendant edges in G. The maximum value of DN and CSDN is 4.
- Case 3:
- Graphs withIn this case, we consider the graphs without pendant vertices and with pendant vertices.
- Case 3 (i):
- Graphs without pendant vertices.Here, non-adjacent edges to the maximum degree vertex have to be considered. At least three vertices are needed to form a CSDS. Thus, the maximum value of CSDN of is 4.
- Case 3 (ii):
- Graphs with pendant vertices.In this case, we consider the edges not adjacent or incident to the vertex with a maximum degree in G, including the pendant edges as well. Since , we can choose at least 3 edges from these sets to dominate . Consequently, the co-secure domination number is at most
- Case 4:
- Graphs withIn this case as well, we examine both graphs with and without pendant vertices.
- Case 4 (i):
- Graphs with , without pendant vertices.If G has , the Theorem 4 provides a thorough explanation that for all connected graphs without pendant vertices,
- Case 4 (ii):
- Graphs that have with pendant vertices.Consider the helm graph containing 4 pendant vertices, where . Here, the domination number, and the CSDN, , are 4 and 5, respectively. The pendant edges connected to the principle diagonal edges can be included in the DS of leading to The CSDN becomes As both the diameter and circumference increase, it is observed thatExample: Consider the Helm graph with diameter and pendant vertices in the Figure 7. The jump graph of the same graph is plotted in Figure 8. The dominating vertices are since all other vertices in are in .
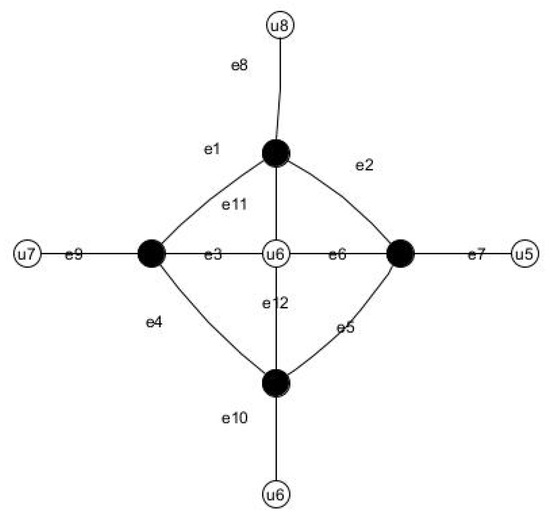 Figure 7. Helm graph.
Figure 7. Helm graph.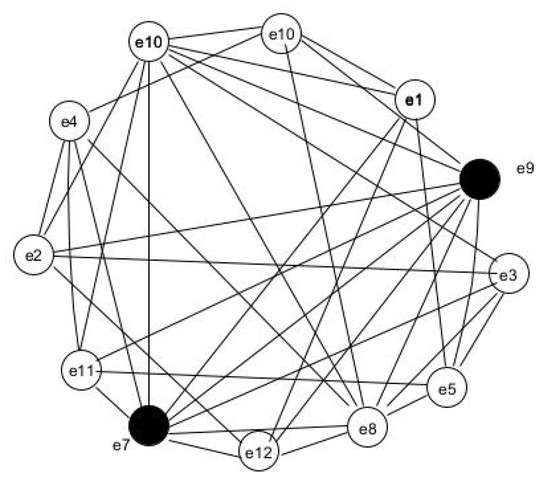 Figure 8. Jump graph of Helm graph.The pendant vertices will surely enter the DS, and the central vertex will dominate all the other vertices. Thus . All the pendant vertices and the central vertex can be replaced with the supporting vertex, and hence CSDN = 5. When we take the jump graph, since the diameter of the graph is , by Theorem 2, .
Figure 8. Jump graph of Helm graph.The pendant vertices will surely enter the DS, and the central vertex will dominate all the other vertices. Thus . All the pendant vertices and the central vertex can be replaced with the supporting vertex, and hence CSDN = 5. When we take the jump graph, since the diameter of the graph is , by Theorem 2, .
□
Corollary 3.
For all graphs G, where G is connected, where is the maximum degree of a vertex in .
Corollary 4.
If four pendant edges are attached to any of the closed graphs say, cycle graph , complete graph , or wheel graph , then the jump graphs of these graphs have, .
Theorem 6.
For graphs G with pendant vertices, and circumference ,
Proof.
Consider a connected graph G with k pendant vertices and circumference It is true that [5]. Choose a subset , where are two pendant edges of G that do not share a common edge. Clearly, this set dominates all the vertices of . Since the two pendant edges of G do not share a common edge and , each vertex in can be replaced by another pendant edge in G, which is in the , and hence . By theorem it is clear that Thus, , because and and , when . □
We consider the jump graph of Sunlet graphs and Helm graphs [18]. These graphs show and . Analysing the jump graphs of these two graphs for the co-secure domination number, we obtain The result is demonstrated in following figure. The sunlet graph shown in Figure 9 and its jump graph is given in Figure 10. We can see that for a sunlet graph G in the Figure 9, the black vertices are the dominating vertices as well as co-secure dominating vertices. Hence, The jump graph in the Figure 9 clearly explains , where the CSDS of is
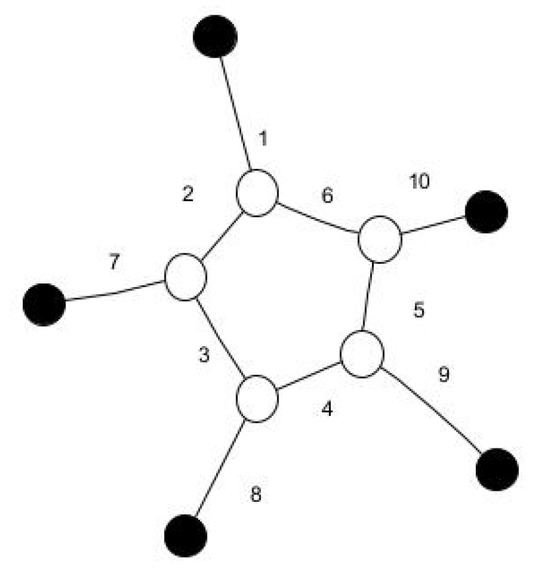
Figure 9.
Sunlet graph, CSDN = 5.
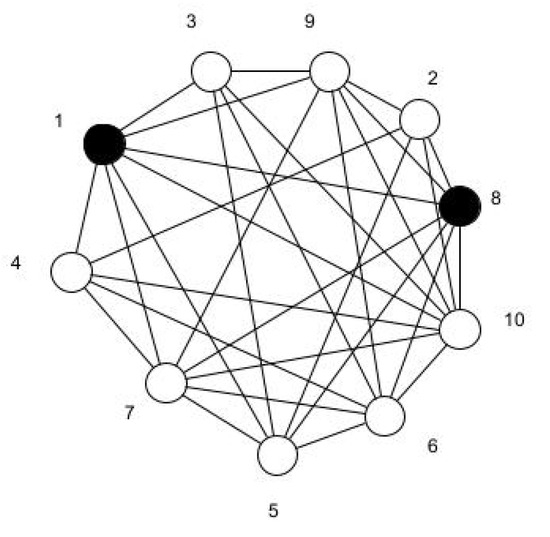
Figure 10.
Sunlet jump graph, CSDN = DN = 2.
4. Conclusions
This paper examines across various graph classes and its relationship with other graph parameters. We provide exact values of for certain standard graphs and characterize jump graphs with . Additionally, we establish a tight bond on , particularly for jump graphs derived from other graphs and those with pendant vertices under specified conditions. This method has significant applications in analyzing and implementing security strategies within interconnection networks. In the domain of cyber-security, co-secure domination involves identifying critical nodes where guards should be stationed to maintain network stability. If a guard is compromised or needs to be relocated, another guard must immediately replace them to ensure continuous security. This approach is crucial for protecting network security against attacks or failures. By applying these mathematical concepts, cyber-security professionals can develop more effective defense systems to safeguard critical network infrastructure.
Author Contributions
Conceptualization, M.P., R.R.I. and K.S.; methodology, M.P. and R.R.I.; resources, M.P. and K.S.; writing—original draft preparation, M.P. and R.R.I.; writing—review and editing, M.P., R.R.I., K.S. and A.A.; funding acquisition, A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by King Khalid University, project under grant number RGP.2/372/45.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Acknowledgments
The authors thank the reviewers for their valuable suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Hsu, L.-H.; Lin, C.-K. Graph Theory and Interconnection Networks; CRC Press: Boca Raton, FL, USA, 2008. [Google Scholar]
- Widmayer, P.; Neyer, G.; Eidenbenz, S. (Eds.) Graph-Theoretic Concepts in Computer Science. In Proceedings of the 25th International Workshop, WG’99, Ascona, Switzerland, 17–19 June 1999; Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Haynes, T.W.; Hedetniemi, S.; Slater, P. Fundamentals of Domination in Graphs; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar]
- Cockayne, E.J.; Grobler, P.J.P.; Grundlingh, W.R.; Munganga, J.; Van Vuuren, J.H. Protection of a graph. Util. Math. 2005, 67, 19–32. [Google Scholar]
- Arumugam, S.; Ebadi, K.; Manrique, M. Co-secure and secure domination in graphs. Util. Math. 2014, 94, 167–182. [Google Scholar]
- Klostermeyer, W.F.; Mynhardt, C.M. Protecting a graph with mobile guards. Appl. Anal. Discret. Math. 2016, 10, 1–29. [Google Scholar] [CrossRef]
- Manjusha, P.; Chithra, M.R. Co-secure domination in Mycielski graphs. J. Comb. Math. Comb. Comput. 2020, 113, 289–297. [Google Scholar]
- Nayana, P.G.; Iyer, R.R. On secure domination number of generalized Mycielskian of some graphs. J. Intell. Fuzzy Syst. Prepr. 2023, 44, 1–11. [Google Scholar] [CrossRef]
- Manjusha, P.; Iyer, R.R. Application of Co-Secure Domination in Sierpinski Networks. In Proceedings of the 2022 IEEE 4th PhD Colloquium on Emerging Domain Innovation and Technology for Society (PhD EDITS), Bangalore, India, 4–5 November 2022. [Google Scholar]
- Basavanagoud, B.; Mathad, V. Graph equations for line graphs, jump graphs, middle graphs, splitting graphs and line splitting graphs. Mapana J. Sci. 2010, 9, 53–61. [Google Scholar] [CrossRef]
- Sastry, D.V.S.; Raju, B.S.P. Graph equations for line graphs, total graphs, middle graphs and quasi-total graphs. Discret. Math. 1984, 48, 113–119. [Google Scholar] [CrossRef][Green Version]
- Venkatachalapathy, M.; Kokila, K.; Abarna, B. Some trends in line graphs. Adv. Theor. Appl. Math. 2016, 11, 171–178. [Google Scholar]
- Chartrand, G.; Hevia, H.; Jarrett, E.B.; Schultz, M. Subgraph distances in graphs defined by edge transfers. Discret. Math. 1997, 170, 63–79. [Google Scholar] [CrossRef][Green Version]
- Maralabhavi, Y.B.; Anupama, S.B.; Goudar, V.M. Domination Number of JUMP Graph; Hikari Ltd.: Rousse, Bulgaria, 2013; Volume 8, pp. 753–758. [Google Scholar]
- Beineke, L.W.; Bagga, J.S. Line Graphs and Line Digraphs; Springer: Berlin/Heidelberg, Germany, 1990. [Google Scholar]
- Muddebihal, M.H.; Kulli, V.R. Lict and Litact graph of a graph. J. Anal. Comput. 2006, 3, 33–43. [Google Scholar]
- Basavanagoud, B.; Mathad, V.N. Graph equations for line graphs, jump graphs, middle graphs, litact graphs and lict graphs. Acta Cienc. Indica Math. 2005, 31, 735. [Google Scholar]
- Frucht, R. Graceful numbering of wheels and related graphs. Ann. N. Y. Acad. Sci. 1979, 319, 219–229. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).