Abstract
Because of the substantial progress in quantum computing technology, the safety of traditional cryptologic schemes is facing serious challenges. In this study, we explore the quantum safety of the lightweight cipher MIBS and propose quantum key-recovery attacks on the MIBS cipher by utilizing Grover’s algorithm and Bernstein–Vazirani algorithm. We first construct linear-structure functions based on the 5-round MIBS cipher according to the characteristics of the linear transformations, and then we obtain a quantum distinguisher of the 5-round MIBS cipher by applying Bernstein–Vazirani algorithm to the constructed functions. Finally, utilizing this distinguisher and Grover’s algorithm, we realize a 7-round key-recovery attack on the MIBS cipher, and then we expand the attack to more rounds of MIBS based on a similar idea. The quantum attack on the 7-round MIBS requires 156 qubits and has a time complexity of . An 8-round attack requires 179 qubits and has a time complexity of . Compared with existing quantum attacks, our attacks have better time complexity when attacking the same number of rounds.
MSC:
94A60
1. Introduction
There has been substantial progress in quantum computer development in recent years. Experts in physics, quantum computing, and computer architecture are committed to realizing quantum computers. While quantum computing may bring benefits to research in many fields, it also brings challenges, especially for cryptography.
The key difference in quantum computing from classical information computing and processing is parallelism, which comes from the principle of superposition. This parallelism superiority makes it possible to execute a great quantity of computational paths simultaneously on quantum computers, so that some computational problems that cannot be solved by electronic computers may be solved by quantum computers. For example, factoring large integers will be solvable on quantum computers by utilizing Shor’s algorithm [1]; however, the security of some widely used public key algorithms is built on it.
Apart from public key schemes, symmetric cryptography is under the threat of quantum attacks as well. Grover’s algorithm [2] is the most representative example. It can be used for any unstructured search and brings a quadratic speedup. Searching a specific marked target in an M-element database using Grover’s algorithm needs only complexity, while classical algorithms need at least complexity. Another famous example is Simon’s algorithm [3], which was introduced to find periods. It is also frequently applied to cryptanalysis of symmetric ciphers. At first, Simon’s algorithm was exploited to distinguish between a Feistel structure and a random function [4,5,6]. Afterwards, it was also utilized to find the key of the Even-Mansour (EM) scheme [6,7]. Lender et al. then utilized Grover’s algorithm and Simon’s algorithm simultaneously to extract the keys of FX ciphers [8]. Dong and Wang applied a similar method to attack a Feistel cipher [9] and the generalized Feistel cipher [10]. As for the Substitution–Permutation Network (SPN) structure, quantum attacks on the Advanced Encryption Standard (AES) algorithm were investigated by Jaques et al. [11]. Halak et al. evaluated the computation costs and performance of several quantum-attack-resilient cryptographic algorithms [12]. Recently, the research on the cryptanalysis of symmetric schemes has begun to pay attention to the Bernstein–Vazirani (BV) algorithm [13] and has obtained some good results [14,15].
In addition to the specific attacks on certain symmetric ciphers, analytic tools for symmetric ciphers must also be investigated for accurate security evaluation. In this direction, Grover’s algorithm was used to accelerate the search involved in differential attacks [11,16], and it was also used in the search part of linear attacks and their variants [17]. Afterwards, the BV algorithm was exploited for finding differentials [14,18,19]. Zhou and Yuan combined the BV algorithm and Grover’s algorithm for attacking Feistel ciphers [15]. Their attack strategy was inspired by the attack presented in [8,9], the main innovation being that it uses BV algorithm to distinguish the functions with nonzero linear structures from random functions instead of using Simon’s algorithm to distinguish functions with nonzero periods from random functions. Quantum algorithms are also applied to the collision attack on Hash functions [20,21]. Quantum cryptanalysis under the related-key model has also been studied [22,23]. The attacks mentioned above all exhibit the acceleration superiority of quantum algorithms in symmetric cryptanalysis over classical algorithms.
In this study, we investigate quantum attacks on the MIBS cipher, which is a lightweight algorithm with a Feistel structure and designed specifically for constrained environments [24]. First, by analyzing the characteristics of the MIBS cipher, we construct linear-structure functions based on the 5-round encryption of the MIBS cipher. Then, we combine this function with the BV algorithm to construct a distinguisher of the 5-round MIBS cipher. Afterwards, we utilize Grover’s algorithm and this distinguisher to implement a 7-round key-recovery attack on the MIBS cipher. Based on a similar idea, we further use the same distinguisher to implement 8-round and 9-round key-recovery attacks on the MIBS cipher. The 7-round, 8-round, and 9-round attacks require 156, 179, and 194 qubits, respectively, and their complexity are , , and , respectively. Compared with existing quantum attacks, the quantum attacks presented in this article have the minimum complexity when attacking the same number of rounds. Our work further explores the “BV-meet-Grover’’ attack strategy and helps to evaluate the security of the MIBS cipher.
We first construct a periodic function based on the 5-round encryption, and then we combine Simon’s algorithm with the found periodic function to obtain a 5-round quantum distinguisher. As the number of rounds increases, the encryption function becomes more complex, making it increasingly difficult to find periodic functions. The 5-round distinguisher is the longest distinguisher we can find. Using the constructed 5-round distinguisher to attack 7-round, 8-round, and 9-round MIBS requires guessing 21, 44, and 64 bits of subkeys, respectively. The complexity of the 10-round attack exceeds that of the key exhaustive attack. Therefore, we only provide 7-round, 8-round, and 9-round attacks on MIBS.
2. Preliminaries
2.1. Mibs Block Cipher
Lightweight cipher MIBS applies a standard Feistel structure [24]. Each block has 64 bits, and the key length supports 80-bit and 64-bit. We only consider the 64-bit version in this paper. MIBS has 32 rounds. Figure 1 shows the encryption structure of one round. and are the left branch and right branch of the input of the i-th round, respectively. and are the left branch and right branch of the output of the i-th round, respectively. is the i-th subkey (). In the i-th round, and are input to the function F, and the XOR of and the output of F is the left branch of the output. The right branch of the output directly takes the value of . All operations appearing in MIBS are nibble-based. A nibble contains four bits.
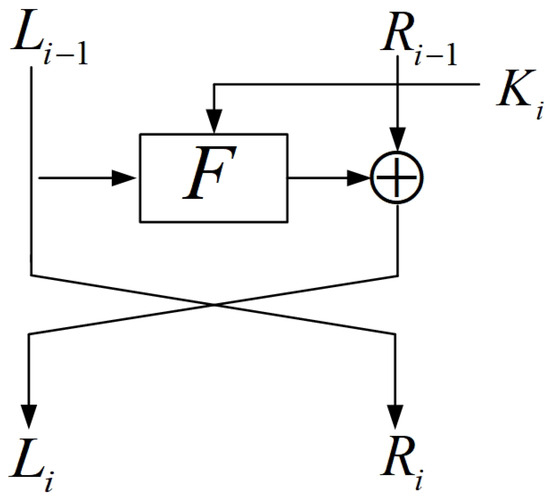
Figure 1.
The i-th round function of MIBS.
Suppose the plaintext is , then the encryption process of MIBS is as follows:
- Divide M into two 32-bit parts .
- For , computewhere is the subkey of the i-th round generated by the key scheduling, and function F is defined below.
- Output the ciphertext . (The ciphertext is obtained by exchanging the left and right branches of the output of the last iteration.)
The function maps eight nibbles to eight nibbles:
where S is the substitution transformation, M and P are the mixing layer and the permutation layer, respectively. The S layer implements 8 identical Sboxes of 4 bits, all denoted s.
The definition of the Sbox s is presented in Table 1.

Table 1.
SBox s.
The M layer mixes 8 nibbles using the XOR operation:
where
The P layer rearranges the input 8 nibbles in the order given in Table 2. That is, the P transformation is defined as
where

Table 2.
P transformation.
For the convenience of cryptanalysis, we combine the transformations P and M. Let , which is a linear transformation and operates as follows:
where
The construction of F is depicted in Figure 2. denotes the input of function F. First, the input is XORed with the 32-bit subkey . Then, all nibbles are performed on 8 identical Sboxes s, respectively. The output of the Sboxes are denoted as . Subsequently, F performs transformation on these nibbles. is composed of XOR operations and position permutations as defined in Equation (1). We mark the transformation with a dashed box.
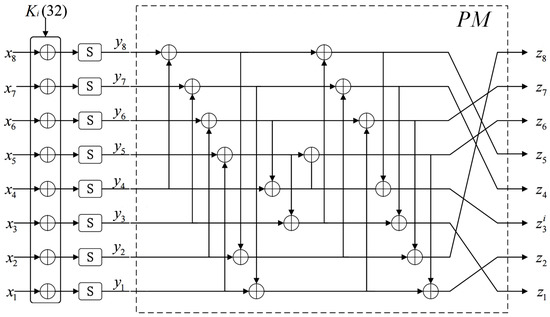
Figure 2.
Construction of the function F.
The attack on the MIBS cipher needs to use the inverse of .
where
The matrix forms of and are
The key scheduling of MIBS generates 32 32-bit round keys . Suppose the user key . K is stored in a 64-bit key register . Initialize the state of the register as , i.e., . The round key in the i-th round is equal to the leftmost 32 bits of the current register. Namely,
After extracting the round key , update the register as follows:
where denotes rotation to the right, and denotes the j-th to the i-th bits of the register. is the Sbox defined in Table 1.
2.2. Bernstein–Vazirani Algorithm
The BV algorithm was introduced to find a secret vector when given the function [13]. The steps of the BV algorithm are illustrated in Figure 3.
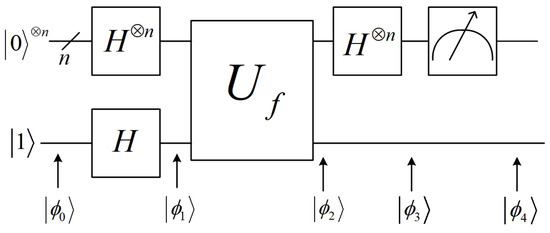
Figure 3.
BV algorithm.
The notation H in Figure 3 denotes the Hadamard gate, which maps the state to the state and maps the state to the state . The notation is a product of n Hadamard gates. Performing on gives the state
The notation denotes the unitary operator of f, which operates as follows:
The symbol at the end of the first quantum wire in Figure 3 denotes a measurement. Suppose a quantum state is measured, where is a complex number and called the amplitude of , then for any vector , the probability of the measurement result being x is equal to . The quantum states in Figure 3 are defined as follows:
The last equation holds because
After measurement, the output is with a probability of 1.
2.3. Linear Structure
Definition 1.
For a Boolean function , is called a linear structure of f if
holds for some .
If in Equation (2) is the n-dimensional zero vector , then is also called a period of f. If a function has a nonzero period, we call it a periodic function. If a function has a nonzero linear structure, we call it a linear structure function. Particularly, for the case , Li et al. presented a quantum algorithm that can determine whether f has a nonzero linear structure in polynomial time [19].
Theorem 1
([19]). Any nonzero linear structure of must be output by Algorithm 1. Conversely, taking , any vector output by Algorithm 1 is a linear structure of f except a negligible probability.
| Algorithm 1 Algorithm for finding linear structures of single-output functions |
| Input: quantum oracle of , a polynomial . |
| Output: a linear structure of f. |
| 1: Define a set ; |
| 2: for p = 1, 2, ⋯, p(n) do |
| 3: Execute BV algorithm on f, obtaining a vector ω; |
| 4: Let ; |
| 5: end for |
| 6: Solve the equation and obtain two solution sets Ci for both i = 0, 1; |
| 7: if then |
| 8: Output “Not linear structure function”; |
| 9: else |
| 10: Output C0 and C1; |
| 11: end if |
2.4. Grover’s Algorithm
Grover’s algorithm [2] was introduced for unstructured search. Suppose the set to be searched is , and is the target vector. In a classical setting, it takes a time of to find u, while in a quantum setting, using Grover’s algorithm only takes a time of . Grover’s algorithm has three steps:
- Prepare the quantum stateby applying Hadamard transform.
- Construct the quantum oracle of functionoperates as
- Let . Perform Grover’s iteration for times to obtain
- Return u.
When implementing Grover’s algorithm, the quantum oracle of the function is given, which operates as follows:
The oracle can be constructed based on as in Figure 4. Given the input state , performs on and the auxiliary state . Then, the whole quantum state is
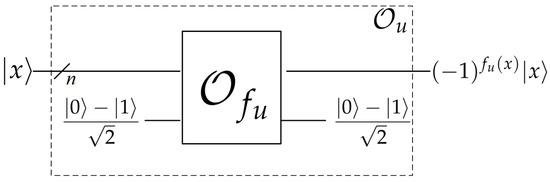
Figure 4.
The construction of .
The last equation holds because when , the state of the second register remains unchanged, while when , the state of the second register becomes , which brings a negative sign. Then discards the second register and outputs the state of the first register.
3. Quantum Distinguisher of MIBS
One of the common methods for attacking block ciphers by quantum algorithms is to first construct a quantum distinguisher by Simon’s algorithm or the BV algorithm, and then utilize Grover’s algorithm to extract the correct key based on the constructed distinguisher. Specifically, Simon’s algorithm can quickly determine whether a function is a periodic function. To obtain a distinguisher, the attacker first constructs a periodic function by using part of the encryption algorithm. Then, when the queried oracle is the block cipher, implementing Simon’s algorithm on the constructed function should output a period. When the queried oracle is a random function, applying Simon’s algorithm on the constructed function outputs a nonzero period with a negligible probability. Based on this significant difference, the attacker can distinguish between the block cipher and random function. In the phase of key recovery, the attacker guesses the round keys of several rounds after the distinguisher and uses the guessed keys to decrypt the ciphertexts obtained by querying. If the guessed round keys are correct, then the distinguisher performed on the partly decrypted ciphertexts should identify them as the outputs of a block cipher. If the round keys are incorrect, the partly decrypted ciphertexts are equivalent to the outputs of a random function. Thus, the distinguisher should identify them as outputs of a random function. By traversing all possible round keys, the attacker can recognize the correct key. In this process, Grover’s algorithm can provide speedup. This attack strategy is called “Grover-meet-Simon” [8,9,10].
Similar to Grover-meet-Simon, the strategy “Grover-meet-BV” is also used [15]. In a Grover-meet-BV attack, the attacker constructs a linear-structure function instead of a periodic function and uses the BV algorithm to distinguish functions with nonzero linear structures from random functions, instead of using Simon’s algorithm to distinguish functions with nonzero periods from random functions. Except for this point, other parts of these two attacks are the same. According to this attack strategy, we first construct a linear-structure function based on a 5-round encryption of MIBS; then, we present a 5-round quantum distinguisher of MIBS using this linear structure function and BV algorithm.
3.1. A Linear-Structure Function Based on 5-Round MIBS
In this subsection, we construct a linear-structure function based on 5-round MIBS. For the convenience of derivation, let be the F transformation in the i-th round, and let the S layer in the i-th round be , as presented in Figure 5. All s (’s) operate in the same way. The left-branch input in the i-th round is , and the right branch is .
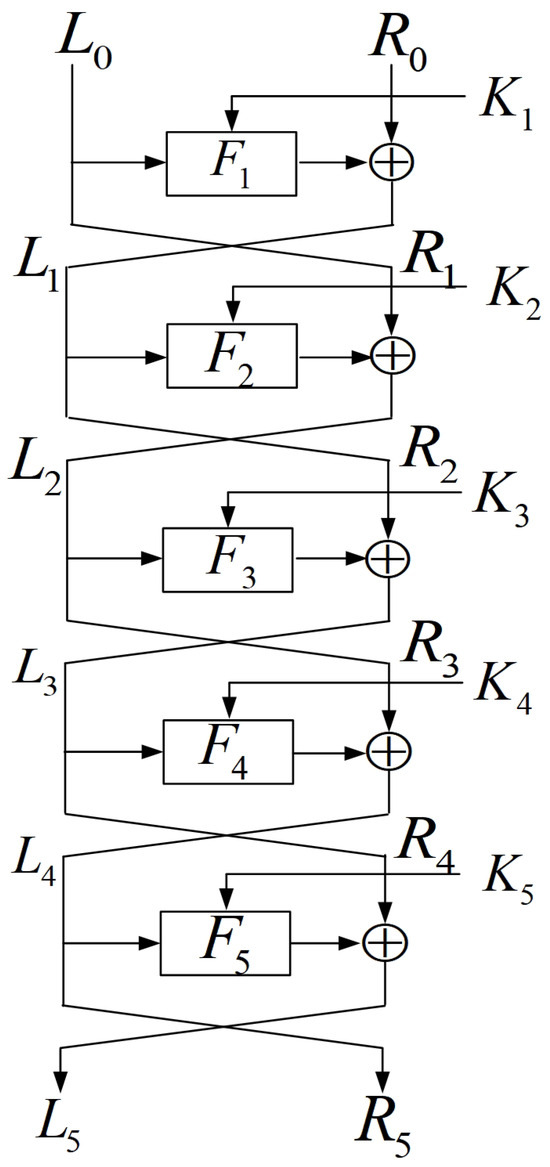
Figure 5.
Illustration of 5-round distinguisher.
According to Figure 5, it holds that
Select two arbitrary constant vectors such that . For any variables and , let the input of the 5-round MIBS be
where , when , and when . is defined as in Equation (1). We use to construct a linear-structure function. Due to Equation (3), for computing , we should first compute and . Let be the j-th nibble of the i-th round key . That is,
It holds that
where , is a constant, and the notation indicates that the corresponding nibble is a constant. The values of different nibbles marked with may be different, but they are all restricted to constants that do not depend on variables x and d. Then,
Therefore,
where . Since
we have
Before further deriving the linear-structure function, we first give Lemma 1.
Lemma 1.
Let , where and ; then, the value of the 5th nibble of is only related to the value of ∗.
Proof.
According to the construction of the transformation,
where indicates that the corresponding nibble is a constant, and indicates that the value of the corresponding nibble is a function of ∗. Different nibbles marked with may be different functions of ∗, but their values are all restricted to only depend on the variable ∗. Notations and are used to indicate the state of the corresponding nibbles, not a specific vector or function. The last equality holds since is a constant. Then,
Then,
Therefore,
where “?” means that the state of corresponding nibbles is uncertain. Due to the above equation, the 5th nibble of is in the state ; thus, its values are only related to ∗. The notation means that every nibble marked with is a function of ∗. The does not refer to a specific function, but rather indicates that the values of the corresponding nibbles depend only on the value of ∗. It represents a kind of state of nibbles rather than a specific function. The symbols in the 2nd, 3rd, and 5th nibbles of indicate that these three nibbles are all functions of ∗, and their values depend only on ∗, but they are not necessarily the same function. □
According to Lemma 1, we define the function
where
and , i.e., the ciphertext after a 5-round encryption of MIBS. is the inverse function of . is the 5th nibble of . .
Theorem 2.
Function is a linear-structure function, and is its linear structure. Specifically,
where and are constants.
3.2. 5-Round Quantum Distinguisher
We have constructed a linear-structure function based on the 5-round encryption of MIBS. Combining this with the quantum algorithm, which can determine whether a function is a linear-structure function, we can obtain a quantum distinguisher of 5-round MIBS.
Based on Algorithm 1, Xie and Yang constructed a quantum algorithm that can determine whether a function has linear structures [14]. We present this quantum algorithm below.
Theorem 3
([14]). If is a linear-structure function, then except with a negligible probability, Algorithm 2 on f with will output a linear structure of f.
| Algorithm 2 [14] Algorithm for finding linear structures of multiple-output functions |
| Input: quantum oracle of , a polynomial . (.) |
| Output: a linear structure of f. |
| 1: for do |
| 2: Run Algorithm 1 on with ; |
| 3: if Algorithm 1 returns “Not linear structure function” then |
| 4: Output “Not linear structure function”; |
| 5: else |
| 6: Let , where and are the outputs of Algorithm 1; |
| 7: end if |
| 8: end for |
| 9: if then |
| 10: Return “Not linear structure function”; |
| 11: else |
| 12: Randomly choose a nonzero vector and return ; |
| 13: end if |
In a quantum distinguishing attack on 5-round MIBS, a quantum oracle is available, which implements either the encryption of 5-round MIBS or a random function . Since the linear-structure function G is defined only using the right part of the output of , it is assumed that the attacker can query the oracle, which merely returns the right branch . Such assumption is commonly used in quantum distinguishing attacks [4,5,6]. Moreover, in the following key-recovery attack, we show how to construct such oracle via the oracle of complete encryption. Thus, the attacker can query by implementing either the operator
or the operator
where is the the encryption function of 5-round MIBS, which only returns the right 32 bits, and is a random function.
A quantum distinguisher of is a quantum algorithm that can distinguish whether implements or a random function . In order to construct a quantum distinguisher, an intuitive idea is to construct the oracle of function G based on
and then run Algorithm 2 on to determine whether it is the oracle of a linear-structure function, thereby determining whether is the encryption of 5-round MIBS. If implements , then Algorithm 2 will return a linear structure of G; otherwise, if implements , then its probability of outputting a linear structure of G is negligible.
Figure 6 shows how to construct the oracle of function G based on . The unitary operator is composed of 32 gates and works as follows:
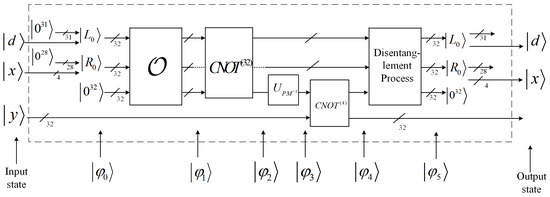
Figure 6.
Construction of .
Similarly, is composed of 4 gates and works as follows:
The unitary operator is defined as
and can be realized as shown in Figure 7. The input of is combined with 31 auxiliary states to form the state , and the input is combined with 28 auxiliary states to form the state . The states in Figure 6 are defined as below.
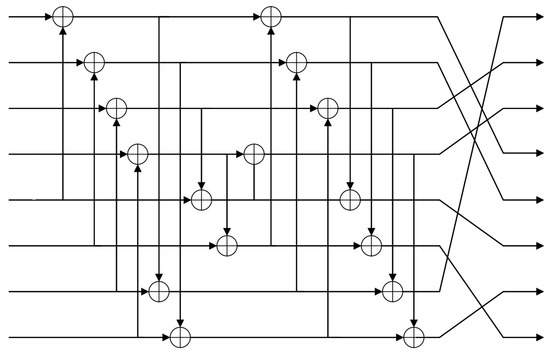
Figure 7.
Quantum circuit of .
Therefore, when is the oracle of , it holds that
When is the oracle of random function , it holds that
The disentanglement process is to disentangle the registers denoted , , and from the registers of the auxiliary states. Thus, after this process, the state will be
if is the oracle of , or
if is the oracle of random function . Since is a random function from 64 bits to 32 bits, can also been seen as a random function mapping 5 bits to 4 bits given input . Let denote the random function from 5 bits to 4 bits; then, we have
when is the oracle of . The output state of shown in Figure 6 is
The quantum oracle has been constructed; then, we present the quantum distinguisher of 5-round MIBS. Given the access to the oracle , the distinguisher works as follows:
- (1)
- Construct the oracle based on as in Figure 6;
- (2)
- Implement Algorithm 2 using oracle ;
- (3)
- If Algorithm 2 returns a linear structure, output ; otherwise, output .
The output indicates that is the oracle of , and output indicates that is the oracle of random function . According to Theorem 2, can correctly distinguish the 5-round MIBS from a random function.
4. Key-Recovery Attack
We first give a 7-round key-recovery attack on MIBS utilizing the distinguisher proposed in Section 3.2. We consider a chosen plaintext attack, where the oracle of the 7-round MIBS is available. Namely, the oracle
can be queried by an attacker. Through querying , the attacker can obtain the superposition state of the ciphertexts after 7-round encryption; then, the attacker guesses the relevant bits of the 6th- and 7th-round keys and decrypts the ciphertexts for two rounds to obtain the ciphertexts of (). Therefore, for each guessed candidate round key of the 6th and 7th rounds, the attacker can use it to decrypt 2 rounds to obtain oracle , which is the oracle of when the guessed key is right, and is the oracle of the random function when the guessed key is wrong. Using the distinguisher defined in Section 3.2 with queries to can determine whether the guessed round key bits are right. If the round key bits are right, will output ; otherwise, it will output .
The key is how to compute using the least bits of and given the ciphertext . Since
to construct oracle , we actually only need to compute the 5th nibble of instead of the entire . Therefore, we can slightly change the way to generate so that we do not need the entire . can still be constructed from using the method in Section 3.2, except that is no longer the oracle of the entire , but only the part of required for computing . This does not bring any essential differences but can void guessing the unnecessary key bits during key-recovery attack. As shown in Figure 8, it holds that
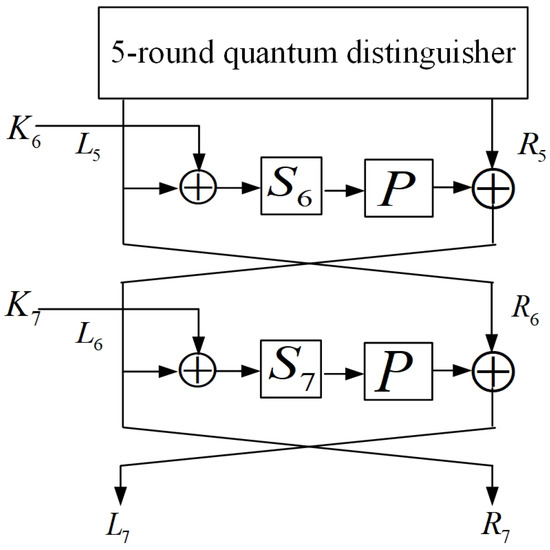
Figure 8.
Illustration of key-recovery attack.
Since and are known, according to the definition of , to compute , we only need to guess the 1st, 3rd, 4th, 5th, and 8th nibbles of . Therefore, , are enough for computing the value of or . There are 24 bits needed to be guessed. Considering the key scheduling, there may exist repetitive bits.
Table 3 shows the repetition bits of the subkeys in 7–10 rounds generated as the key scheduling. Suppose the state of the key register in the 6th round of key scheduling is
then, and . Here, we omit the Sbox transformation since the determined transformation does not affect the amount of bits that is required to be guessed. According to Table 3, the 2nd, 3rd, and 4th bits of are the same as the 1st, 2nd, and 3rd bits of . Thus, in fact, we only need to guess 21 key bits:
where denotes the 8th, 5th, 4th, and 3rd nibbles and the 1st bit of the 1st nibble of .

Table 3.
Repetition of round key bits.
Define
Given the oracle of , by decrypting under the relevant keys in the 6th and 7th rounds, it is easy to obtain the oracle of . Then, we can construct the oracle of using a similar method in Section 3.2. The oracle of can play the role of in the distinguisher . Thus, will output when is the correct 21-bit key and output when is the wrong 21-bit subkey. Taking as the oracle in Grover’s algorithm, it will search for the right key bits: .
According to [8], this key-recovery attack needs a total of
qubits, where is the number of bits of the subkeys to be recovered, is the input length of the linear structure function G, is the output length of G, and . , , , and . Thus, this attack requires 156 qubits. The time complexity is .
Consider attacking 8-round MIBS using the same distinguisher. By similar derivation, to compute based on the ciphertext , we need to guess the subkeys
According to Table 3, has 9 repetitive bits, so there are only 44 bits to be recovered. According to Equation (11), an 8-round key-recovery attack requires 179 qubits. The corresponding time complexity is .
By similar derivation, a 9-round attack requires 194 qubits, and the time complexity is . A 10-round attack requires 199 qubits, and the time complexity is . The authors in [25] also presented quantum attacks on MIBS. The time complexity of their 7-round, 8-round, and 9-round attacks is , , and , respectively. The complexity of our attacks proposed in this article is lower.
5. Results and Discussion
In this article, we proposed quantum attacks on the MIBS cipher based on the BV algorithm. Specifically, we first fully utilize the characteristics of the linear transformations of the MIBS cipher to construct a linear-structure function. Then, we use the fact that the BV algorithm can quickly determine whether a function has nonzero linear structures to design a 5-round quantum distinguisher for the MIBS cipher, which can effectively distinguish the encryption of the 5-round MIBS cipher from a random function. Subsequently, by analyzing the key scheduling of the MIBS cipher, we find the repeated bits between round keys. Combined with Grover’s algorithm, we realize a 7-round key-recovery attack on MIBS and generalize the attack to more rounds. The quantum attack on 7-round MIBS requires 156 qubits and has a time complexity of . The 8-round attack requires 179 qubits, and the time complexity is . Compared with the existing quantum attacks, our attack has the smallest time complexity. We believe this study contributes to evaluating the safety of the MIBS cipher in the quantum world and helps to further explore the "BV-meet-Grover" attack strategy.
For further research, how to reduce the resource consumption and time complexity of the attacks on the MIBS cipher is worth studying. We can also study the applications of the BV algorithm and other quantum algorithms to key-recovery attacks on various block ciphers. Quantum attacks on other symmetric primitives, such as hash functions and stream ciphers, are also a meaningful direction. For example, we can apply the quantum attack strategies introduced in [20,21] to attack other hash functions [26,27]. We can also apply quantum algorithms to enhance the classical attacks on stream ciphers that have been proposed [28,29] or to attack other cryptographic schemes [30,31].
Author Contributions
Conceptualization, H.X. (Huiqin Xie), Z.Z. and H.X. (Huiqin Xie); Formal analysis, H.X. (Huiqin Xie), Z.Z., K.W. and Y.L.; Funding acquisition, H.X. (Huiqin Xie); Investigation, H.X. (Huiqin Xie), K.W. and H.X. (Huiqin Xie); Methodology, H.X. (Huiqin Xie) and Z.Z.; Validation, H.X. (Huiqin Xie) and Y.L.; Visualization, H.X. (Huiqin Xie) and H.X. (Hongcai Xin); Writing—original draft, H.X. (Huiqin Xie), Z.Z. and H.X. (Huiqin Xie); Writing—review and editing, H.X. (Huiqin Xie). All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Beijing Natural Science Foundation (no. 4234084), the Open Research Fund of Key Laboratory of Cryptography of Zhejiang Province (no. ZCL21012) and Fundamental Research Funds for the Central Universities (no. 328202202).
Data Availability Statement
The original contributions presented in this study are included in the article, and further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Shor, P.W. Algorithms for Quantum Computation: Discrete Logarithms and Factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A Fast Quantum Mechanical Algorithm for Database Search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Simon, D.R. On the power of quantum computation. SIAM J. Comput. 1997, 10, 1474–1483. [Google Scholar] [CrossRef]
- Kuwakado, H.; Morii, M. Quantum Distinguisher between the 3-Round Feistel Cipher and the Random Permutation. In Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2682–2685. [Google Scholar]
- Santoli, T.; Schaffner, C. Using Simon’s algorithm to attack symmetric-key cryptographic primitives. Quantum Inf. Comput. 2017, 17, 65–78. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Breaking Symmetric Cryptosystems Using Quantum Period Finding. In Proceedings of the CRYPTO’16, Barbara, CA, USA, 14–18 August 2016; pp. 207–237. [Google Scholar]
- Kuwakado, H.; Morii, M. Security on the Quantum-type Even-Mansour Cipher. In Proceedings of the Information Theory and its Applications, Honolulu, HI, USA, 28–31 October 2012; pp. 312–316. [Google Scholar]
- Leander, G.; May, A. Grover Meets Simon–Quantumly Attacking the FX-construction. In Proceedings of the ASIACRYPT’17, Hong Kong, China, 3–7 December 2017; pp. 161–178. [Google Scholar]
- Dong, X.; Wang, X. Quantum key-recovery attack on Feistel structures. Sci. China Inf. Sci. 2018, 10, 240–246. [Google Scholar] [CrossRef]
- Dong, X.; Wang, X. Quantum cryptanalysis on some generalized Feistel schemes. Sci. China Inf. Sci. 2019, 62, 22501:1–22501:12. [Google Scholar] [CrossRef]
- Jaques, S.; Naehrig, M.; Roetteler, M.; Virdia, F. Implementing Grover Oracles for Quantum Key Search on AES and LowMC. In Proceedings of the EUROCRYPT’20, Zagreb, Croatia, 10–14 May 2020; pp. 280–310. [Google Scholar]
- Halak, B.; Gibson, T.; Henley, M.; Botea, C.B.; Heath, B.; Khan, S. Evaluation of performance, energy, and computation costs of quantum-attack resilient encryption algorithms for embedded devices. IEEE Access 2024, 12, 8791–8805. [Google Scholar] [CrossRef]
- Bernstein, E.; Vazirani, U. Quantum complexity theory. SIAM J. Comput. 1997, 26, 1411–1473. [Google Scholar] [CrossRef]
- Xie, H.; Yang, L. Using Bernstein-Vazirani algorithm to attack block ciphers. Des. Codes Cryptogr. 2019, 87, 1161–1182. [Google Scholar] [CrossRef]
- Zhou, B.; Yuan, Z. Quantum key-recovery attack on Feistel constructions: Bernstein-Vazirani meet Grover’s algorithm. Quantum Inf. Process. 2021, 20, 330. [Google Scholar] [CrossRef]
- Zhou, Q.; Lu, S.; Zhang, Z.; Sun, J. Quantum differential cryptanalysis. Quantum Inf. Process. 2015, 14, 2101–2109. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Quantum Differential and Linear Cryptanalysis. In Proceedings of the Fast Software Encryption, Bochum, Germany, 20–23 March 2016; pp. 71–94. [Google Scholar]
- Li, H.; Yang, L. Quantum Differential Cryptanalysis to the Block Ciphers. In Proceedings of the 6th International Conference on Applications and Techniques in Information Security, Beijing, China, 4–6 November 2015; pp. 44–51. [Google Scholar]
- Li, H.; Yang, L. A quantum algorithm to approximate the linear structures of Boolean functions. Math. Struct. Comput. Sci 2018, 28, 1–13. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Sasaki, Y. Finding Hash Collisions with Quantum Computers by Using Differential Trails with Smaller Probability than Birthday Bound. In Proceedings of the EUROCRYPT’20, Zagreb, Croatia, 10–14 May 2020; pp. 249–279. [Google Scholar]
- Dong, X.; Sun, S.; Shi, D.; Gao, F.; Wang, X.; Hu, L. Quantum Collision Attacks on AES-Like Hashing with Low Quantum Random Access Memories. In Proceedings of the ASIACRYPT’20, Daejeon, Republic of Korea, 7–11 November 2020; pp. 727–757. [Google Scholar]
- Roetteler, M.; Steinwandt, R. A note on quantum related-key attacks. Inf. Process. Lett. 2015, 115, 40–44. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Aoki, K. On quantum related-key attacks on iterated Even-Mansour ciphers. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, 102, 27–34. [Google Scholar] [CrossRef]
- Izadi, M.; Sadeghiyan, B.; Sadeghian, S.S.; Khanooki, H.A. MIBS: A New Lightweight Block Cipher. In Proceedings of the International Conference on Cryptology and Network Security—CANS, Kanazawa, Japan, 12–14 December 2009; pp. 334–348. [Google Scholar]
- Li, Y.; Lin, H.; Yi, Z.; Xie, H. Quantum Cryptanalysis of MIBS. J. Cryptologic Res. 2021, 8, 989–998. [Google Scholar]
- Hannusch, C.; Horváth, G. Properties of Hash Functions based on Gluškov Product of Automata. J. Autom. Lang. Comb. 2021, 26, 55–65. [Google Scholar]
- Grassi, L.; Khovratovich, D.; Rechberger, C.; Roy, A.; Schofnegger, M. Poseidon: A New Hash Function for Zero-Knowledge Proof Systems. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual Event, 11–13 August 2021; pp. 519–535. [Google Scholar]
- Domosi, P.; Horvath, G.; Molnar, F.T.; Kovacs, S.; Diene, A. A side-channel attack against an automata theory based stream cipher. Logic Lang. Algebr. Syst. Relat. Areas Comput. Sci. 2021, 2193, 64–72. [Google Scholar]
- Mascia, C.; Piccione, E.; Sala, M. An algebraic attack on stream ciphers with application to nonlinear filter generators and WG-PRNG. Adv. Math. Commun. 2024, 18, 1710–1722. [Google Scholar] [CrossRef]
- Dömösi, P.; Hannusch, C.; Horváth, G. A cryptographic system based on a new class of binary error-correcting codes. Tatra Mt. Math. Publ. 2019, 73, 83–96. [Google Scholar]
- Drǎgoi, V.F.; Szocs, A. Structural Properties of Self-dual Monomial Codes with Application to Code-Based Cryptography. In Proceedings of the 18th IMA International Conference on Cryptography and Coding, Virtual Event, 14–15 December 2021; pp. 16–41. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).