Abstract
Due to the superiority of quantum computing, traditional cryptography is facing a severe threat. This makes the security evaluation of cryptographic systems in quantum attack models both significant and urgent. For symmetric ciphers, the security analysis heavily relies on cryptanalysis tools. Thus, exploring the use of quantum algorithms in traditional cryptanalysis tools has garnered considerable attention. In this study, we utilize quantum algorithms to improve impossible differential attacks and design two quantum automated tools to search for impossible differentials. The proposed quantum algorithms exploit the idea of miss-in-the-middle and the properties of truncated differentials. We rigorously prove their validity and calculate the quantum resources required for their implementation. Compared to the existing classical automated cryptanalysis, the proposed quantum tools have the advantage of accurately characterizing S-boxes while only requiring polynomial complexity, and can take into consideration the impact of the key schedules in a single-key model.
Keywords:
quantum cryptanalysis; symmetric cryptography; impossible differential attack; automated analysis MSC:
94A60
1. Introduction
The development of quantum computers has progressed steadily. As soon as quantum computers are successfully built, traditional cryptography will be severely threatened. By utilizing Shor’s algorithm [1], adversaries possessing quantum computers can break public key cryptosystems built on the integer factorization problem, such as the RSA scheme widely used in secure communication. Apart from public key cryptography, studies on the cryptanalysis of symmetric cryptography against quantum adversaries have also achieved many outstanding results. By utilizing Grover’s algorithm, one can achieve a quadratic speed-up when searching unordered databases [2]. Therefore, to restore the same ideal security as that in a classical setting, the key lengths of symmetric ciphers must be doubled in the quantum setting.
The exhaustive attack can only evaluate the ideal security margin of cryptographic schemes. To accurately grasp the quantum security of currently used symmetric schemes, we also need to investigate other possible quantum attacks. In this direction, Simon’s algorithm [3] is frequently used. Kuwakado and Morri first applied Simon’s algorithm to attack the Feistel structure and proposed a three-round quantum distinguisher [4]. Then they also attacked the Even–Mansour cipher using a similar idea and successfully recovered the key [5]. The authors of [6] forged messages of the CBC-MAC scheme using the method presented in [4]. Kaplan et al. also further developed the results in [4] and attacked several symmetric systems, including GCM, PMAC, and CLOC [7]. Both [6,7] proved the correctness of the quantum distinguisher even if the Feistel structure has round functions that are not permutations.
Leander and Alexander embedded Simon’s algorithm into Grover’s algorithm in order to identify the correct key of the FX structure [8]. Following this attack strategy, Dong and Wang broke Feistel schemes and obtained the key using the quantum distinguisher shown in [4]. Afterward, they applied the same strategy to extract the key of the generalized Feistel cipher [9,10]. The above attacks were all implemented under the quantum version of the chosen plaintext model, also known as the model [11,12,13]. In this attack model, the cryptographic oracle can be queried with superposition states. The authors of [14] studied quantum-related-key notions in which quantum adversaries can use superposition states of related keys to query oracles. Hosoyamada et al. then further investigated quantum-related-key notion and recovered the key of the two-round Even–Mansour algorithm [15]. Jaques et al. analyzed the complexity of Grover’s algorithm when attacking AES [16].
Apart from specific quantum attacks, studying quantum versions of cryptanalysis tools (such as integral, differential, and linear analyses) is also essential. Zhou et al. utilized Grover’s algorithm for differential attacks [17]. Kaplan et al. subsequently used Grover’s algorithm to enhance some variants of differential attacks and linear attacks [18]. Xie et al. made use of the Bernstein–Vazirani algorithm to search for high-probability differentials [17]. The authors of [19] implemented quantum collision attacks on Whirlpool and AES-MMO schemes via differential characteristics. Dong et al. enhanced truncated differential analysis through quantum algorithms and broke the Grstl-512 scheme and the AES-MMO cipher [20].
Our contributions. In this paper, we study the applications of Simon’s algorithm to cryptanalysis tools for symmetric ciphers. We bring the superiority of quantum computing into traditional impossible differential analysis, and design quantum automated tools to search for impossible differentials. First, we propose a basic quantum algorithm that can find impossible differentials by imitating the classical impossible differential technique. Subsequently, by allowing the differentials to be truncated, we present another improved quantum algorithm. We provide the correctness proofs for the proposed algorithms and evaluate their quantum complexities. The proposed quantum tools offer several advantages, as follows:
- The quantum algorithms can be implemented in the Q1 attack model, without any query to the quantum encryption or decryption oracle. In contrast, many other quantum attacks [4,5,6,7,9,10] require adversaries to perform quantum queries with superposition states. Our quantum tools are much easier to realize and, thus, more practical.
- Classical automated impossible differential cryptanalysis tools include the UID tool [21], U-tool [22], WW-tool [23], MILP tool [24], and SAT tool [25]. When faced with large-scale S-boxes, these classical automated tools either do not describe the construction of S-boxes and simply treat them as bijections or only describe the reduced differential distribution table of S-boxes. So far, there is no classical automated tool that can fully characterize large-scale S-boxes. Even in the case where S-boxes are only partially described, the searching space usually expands rapidly as the number of rounds increases, making it impossible to search many rounds. Our quantum automated tools fully leverage the parallel advantages of quantum computing, allowing for the complete characterization of S-boxes while maintaining complexity within polynomial time. They can fully characterize any nonlinear functions, and the complexity increases linearly with respect to the number of rounds.
- Most classical automated impossible differential cryptanalysis tools cannot take the key schedule into account in a single-key model. However, our tools include the key schedule when implementing the quantum circuit of encryption, allowing the impact of the key schedule on differential propagation types to be fully considered. Specifically, in a related-key model [26], the attacker can introduce a key differential so that the propagation of this differential in both the key schedule and encryption process is accounted for when searching for impossible differentials. This approach provides a more accurate characterization of differential propagation and helps identify more or longer impossible differentials. However, the single-key model is more practical and more commonly used since the related key model requires too much power from the attacker. In a single-key model, the master key is not allowed to introduce a differential to the key. Therefore, most classical automated tools for searching distinguishers ignore the impact of the key schedule and simply treat the subkeys of different rounds as independent constants. The process of searching for distinguishers lacks the analysis of key schedules. In contrast, although our quantum tools are also in a single-key model, they treat the entire encryption algorithm, including the key schedule, as a black box, and the state of the master key is a part of the input. The encryption of the input superposition state includes the calculation of the key schedule. All subkeys are obtained by running the key schedule on the master key. Thus, the connection between different subkeys is fully considered, which helps to accurately characterize the differential propagation.
Comparison with related works. A periodic function constructed based on a block cipher will yield a quantum distinguisher when combined with Simon’s algorithm [4,5,6,7]. Owing to this, Xiang et al. proposed a classical algorithm for constructing periodic functions using existing probability-1 truncated differentials and applied this method to two block ciphers [27]. The algorithm they designed to identify periodic functions is a classical algorithm. Their method does not involve searching for truncated differentials, but only uses truncated differentials that already exist to construct periodic functions. In contrast, we study how to utilize quantum algorithms to identify impossible differentials. To achieve this goal, we construct a quantum algorithm for probability-1 truncated differentials based on Simon’s algorithm. Our work has different goals from those of [27]. One is to identify impossible differentials, whereas the other is to construct periodic functions. The methods used are also different. One uses classical algorithms, whereas the other uses quantum algorithms.
2. Preliminaries
We present a simple overview of the necessary concepts and their related results.
2.1. Quantum Attack Models
are two arbitrary positive integers. is a Boolean function. If the unitary operation
is realized by a quantum circuit, we say that this circuit evaluates F quantumly. Any vectorial Boolean function can be evaluated by a quantum circuit constructed with gates in a finite but universal set of unitary gates. Such a set is referred to as a universal gate set [28]. For example, the phase gate S, Hadamard gate H, non-Clifford gate T, and controlled-NOT quantum gate form a universal gate set. Each gate in this set is calculated as a single operation. For any vectorial Boolean function F, let the notation denote the number of quantum universal gates required to implement .
Two common attack models for adversaries are considered when analyzing the quantum security of cryptographic primitives [12]. One is the Q1 attack model, where adversaries can utilize quantum computers to perform offline computations but can only make classical online queries. The other is the Q2 attack model, where adversaries can also execute quantum queries. Specifically, a Q2 adversary can also make queries to cryptographic primitives with inputs in superposition states and obtain the quantum states of their outputs. The Q2 attack model is stricter in terms of the adversaries’ ability because querying the quantum oracles of cryptographic systems is usually not easy to realize in practice.
2.2. Simon’s Algorithm
Given and a private vector satisfying
Simon’s algorithm [3] was originally used to solve the period s. If a function has such a period, we say that it meets Simon’s promise. Finding s requires at least classical queries when using classical algorithms, whereas Simon’s algorithm only requires quantum queries. With the quantum circuit of F, Simon’s algorithm requires repeating the steps below:
- 1.
- Prepare an -qubit quantum state . We apply the Hadamard transform to the left register, obtaining the following:
- 2.
- We implement the unitary operator of F and obtain the following state:
- 3.
- We measure the last register to obtain a vector ; subsequently, the remaining registers will be as follows:
- 4.
- We perform Hadamard operators on the above state, obtaining the following:
- 5.
- We measure this state. If a vector satisfies , its amplitude must be 0. The measurement result always satisfies .
The process of Simon’s algorithm involves repeating the above subroutine times, yielding vectors that are perpendicular to s and are linearly independent. Using linear algebraic knowledge, we can easily compute s.
A quantum circuit illustration of Simon’s subroutine (steps 1–5) is shown in Figure 1. Running steps 1–5 requires Hadamard operators and 1 execution of the unitary operator . Therefore, there are qubits and gates in total in Simon’s algorithm when run on F.
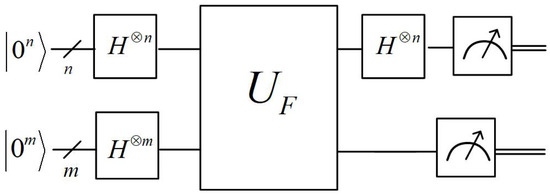
Figure 1.
Circuit illustration of Simon’s algorithm.
In the cryptanalysis scenario, it is not always easy to construct a Boolean function that satisfies Simon’s promise. Even if a periodic function is constructed, unwanted collisions not caused by this period may occur. Kaplan et al. relaxed Simon’s promise and proved the following theorem [7].
Theorem 1
([7]). If satisfies for a period and some constant , where we have the following:
then by repeating the subroutine times, the probability that Simon’s algorithm returns s is not less than .
2.3. Linear Structure
We will transform the problem of seeking impossible differentials into a problem of seeking linear structures.
Definition 1
([29]). Given a function , is named a linear structure if we have the following:
for some vector . In other words, is constant.
For any , satisfying Equation (2), we refer to the pair as F’s linear structure duad. If b is a zero vector , then a is called F’s period. If , are two linear structure duads of F, then we have the following:
Thus, remains as one of F’s linear structure duad. All of F’s linear structure duads form a subspace within the vector space . This subspace is referred to as the linear structure space and is denoted by .
For any vectors , if there is satisfying , then is said to make a “match” of F at x. Being a linear structure duad is equivalent to causing matches of F at all points .
3. A Basic Quantum Tool for Finding Impossible Differentials
We present a universal quantum algorithm that finds impossible differentials of an arbitrary block cipher. The main idea is to use probability-1 differentials to construct impossible differentials. Since probability-1 differentials of an encryption function are also its linear structure duads, we can find them by constructing a quantum algorithm that finds linear structure duads. We first show a quantum algorithm that finds linear structure duads; based on this algorithm, we propose a basic quantum tool for impossible differentials.
3.1. Finding Linear Structure Duads via Simon’s Algorithm
is the linear structure space of function as defined in Section 2.3. Namely,
We aim to obtain . The value of m does not need to be equal to n. We define a new function as follows:
For any duad , if is G’s period, it will also be F’s linear structure duad. Therefore, F’s linear structure duads can be found using Simon’s algorithm. Based on this analysis, we propose Algorithm 1, referred to as FindStruct, which is used to identify linear structure duads, as follows:
| Algorithm 1 Algorithm FindStruct |
| Input: a parameter c and the access to the quantum unitary operator of a function . Output: the linear structure space .
|
The quantum computing part of the FindStruct algorithm involves repeating steps 2–6 independently for times. We refer to steps 2–6 as the FindStruct subroutine. Its quantum circuit is shown in Figure 2. Steps 1–7 involve executing Simon’s subroutine times on to independently obtain vectors . We expect that, as with the original Simon’s algorithm, the periods of G are orthogonal to ; thus, we can obtain the periods of G by solving Equation (5), which are also linear structure duads of F. Theorem 1 provides the conditions for Simon’s algorithm to output the periods. Therefore, for the FindStruct algorithm to successfully output , the G function must satisfy this condition. However, G may have more than one period since function F may have more than one linear structure duad, or the length of G’s output may not be equal to that of the input. Therefore, simply applying Theorem 1 is insufficient to justify the soundness of the FindStruct algorithm. To address this, we define a new parameter, . Function is defined as follows:
It is obvious that . If is in ; that is, if it is F’s linear structure duad, then it will cause a match of F at each point . If , then the number of matches caused by will be less than . The closer the value of is to zero, the fewer matches that the vector not in can cause. Theorem 2 shows the validity of Algorithm 1 (FindStruct).
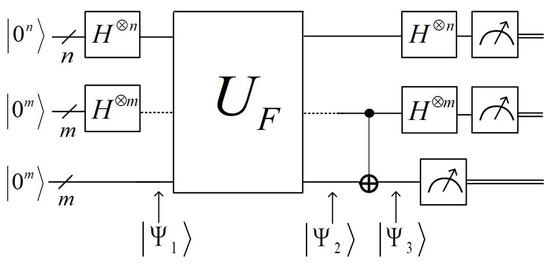
Figure 2.
Quantum circuit of the FindStruct subroutine.
Theorem 2.
Let L be the solution set output by the FindStruct algorithm run on with a parameter, c, then . Moreover, if there is a constant, , such that , then the probability of being equal to L is no less than .
The idea of proving Theorem 2 is almost the same as that of Theorem 1 in [7], with the exception of cases where the function has multiple periods or linear structures, as well as cases where the lengths of the output and input are unequal, need to be considered. The proof is presented in Appendix A.
According to Theorem 2, setting c greater than ensures that the probability of the FindStruct algorithm outputting vectors not in decreases exponentially with n. The condition implies that the vectors that are not linear structure duads of F should not cause too many matches, or in other words, vectors that are not periods of G defined in Equation (3) should not cause too many collisions.
3.2. Quantum Tool for Impossible Differentials
The method of finding impossible differentials involves finding probability-1 differential characteristics that propagate, respectively, from the input end and the output end of the cipher but cannot match when they meet [30].
is an arbitrary block cipher that has r rounds. E denotes the round function. The block size is n and the key space is . For each , the output of on plaintext x is . Our goal is to obtain impossible differentials of . Namely, we find , such that we have the following:
We divide into two functions, . Here, and . Let be the inverse function of . As shown in Figure 3, if is a differential of , is a differential of , satisfying the following:
and , then will be an impossible differential of . Therefore, to identify impossible differentials of , we only need to obtain differentials of and with a probability of 1.
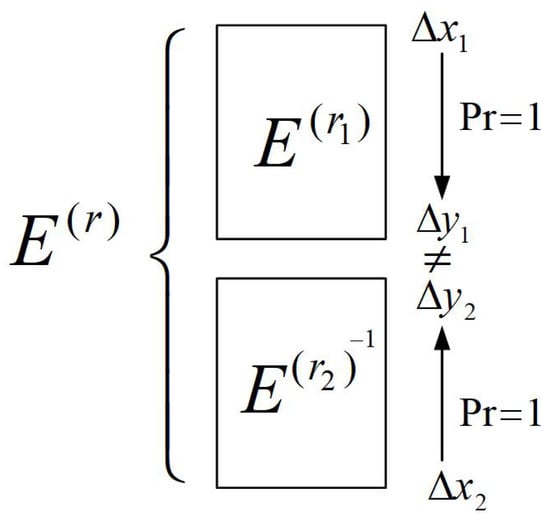
Figure 3.
Construction idea of impossible differentials.
For any t-round block cipher that has a key length of m and block size n, we treat both the plaintext and key as inputs of , then the function, i.e.,
is public and completely determined. The Q1 adversaries can construct the unitary operator
themselves. As
if is ’s linear structure duad, then will be identified as ’s differential of probability-1. Thus, we can use the FindStruct algorithm to obtain ’s differentials of probability-1, with the additional requirement that the first m bits of the linear structures be 0. This can be achieved by adding additional equations to Equation (5) when Algorithm 1 (FindStruct) is run on .
The following Algorithm 2 is designed to search impossible differentials.
| Algorithm 2 FindImpoDiff algorithm |
| Input: a parameter c and a cipher . ( is the key space.) Output: Impossible differentials of .
|
Figure 4 shows the flowchart of Algorithm 2 (FindImpoDiff). Steps 3–4 are used to identify the differentials of . Steps 5–6 are used to identify the differentials of . Since and are public and determinate functions, the adversary can execute the unitary operators and when invoking the FindStruct subroutine.
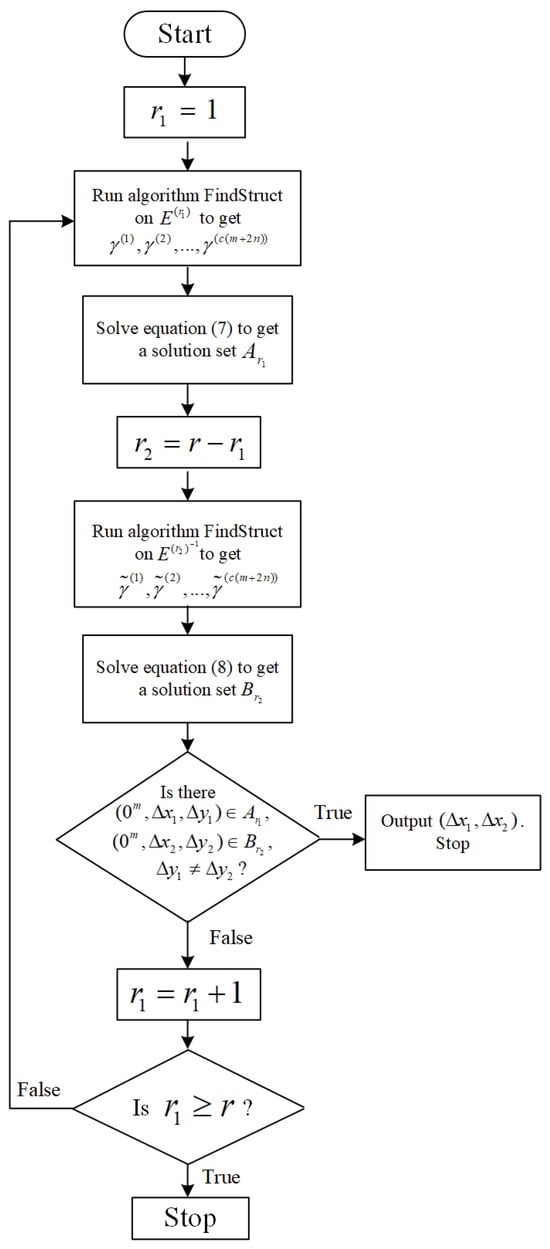
Figure 4.
Flowchart of Algorithm 2 (FindImpoDiff).
Given a block cipher , we define
where is a t-round reduced version of and is defined by Equation (6); as follows:
where denotes the linear structure space of . denotes the maximum number of matches that vectors not in the linear structure duads of can cause. Therefore, the smaller the parameter is, the fewer matches the vectors not in the linear structure duads of the reduced version of can cause. According to Theorem 2, the following theorem holds:
Theorem 3.
Block cipher satisfies for a constant . If executing the FindImpoDiff algorithm on with parameter c outputs , the probability of being ’s impossible differential is no less than , where m is the key length and n is the block size.
According to Theorem 3, setting c greater than guarantees that the probability of the FindImpoDiff algorithm outputting vectors that are not impossible differentials decreases exponentially with n.
Notably, according to Theorem 2, any linear structure duad of whose first m bits are zero must belong to the solution set . On the other hand, being a linear structure duad of is equivalent to being a probability-1 differential of . Thus, all probability-1 differentials of must be in the set . Similarly, all probability-1 differentials of must be in the set . Therefore, all impossible differentials linked by two differentials of probability-1 as in Figure 3 must be output by the FindImpoDiff algorithm. This holds even if the condition is not satisfied. The condition is used only to ensure that the probability of incorrectly outputting a vector that is not an impossible differential is exponentially small.
3.3. Complexity of Algorithm 2 (FindImpoDiff)
Since quantum computers have not yet been built, we cannot obtain actual execution results of the proposed quantum tools on specific block ciphers. The corresponding simulation would require, at a minimum, a polynomial quantum execution of a block cipher, which is currently too large for simulation. For quantum attacks, as actual running or simulation of the attacks is not yet possible, validation is often demonstrated by rigorously deriving the success probability and complexity [2,3,7,8]. Theorem 2 establishes the lower bound of the success probability for the FindImpoDiff algorithm. The process of Algorithm 2 (FindImpoDiff) does not involve quantum queries and, thus, can be executed by Q1 adversaries. We evaluate the complexity by calculating the number of qubits and quantum gates needed.
In Algorithm 2 (FindImpoDiff), finding probability-1 differentials of requires executing the FindStruct subroutine on for times. Each execution includes Hadamard gates, n CNOT gates, and one unitary operator . Finding probability-1 differentials of requires executing the FindStruct subroutine on for times. Each execution includes Hadamard gates, n CNOT gates, and one unitary operator . Thus, the number of Hadamard gates in Algorithm 2 (FindImpoDiff) is as follows:
The number of CNOT gates in Algorithm 2 (FindImpoDiff) is as follows:
Algorithm 2 (FindImpoDiff) also requires executing the unitary operators and times for each . As explained in Section 2.1, and denote the numbers of universal gates required to implement and , respectively. We have the following:
Algorithm 2 (FindImpoDiff) additionally requires executing the quantum circuit of for times. The quantum resources used to implement Algorithm 2 (FindImpoDiff) are listed in Table 1.

Table 1.
The quantum resources of Algorithm 2 (FindImpoDiff) and Algorithm 3 (FindImpoDiff2) 1.
We then calculate the number of qubits needed for Algorithm 2 (FindImpoDiff). Running the FindStruct subroutine on requires qubits. Running the FindStruct subroutine on also requires qubits. Due to the reusability of qubits, qubits are sufficient to execute the FindImpoDiff algorithm.
In addition to the quantum computing part, Algorithm 2 (FindImpoDiff) also involves solving linear equations. Solving Equation (7) is equivalent to solving the following equation:
Here, denotes the i-th bit of (). This linear system contains unknowns and equations. The complexity of solving this linear system using Gaussian elimination is . Similarly, the complexity of solving Equation (8) is also . Thus, by omitting a constant coefficient, the complexity of the classical computing part of Algorithm 2 (FindImpoDiff) is as follows:
Therefore, the classical computing part has a complexity of .
| Algorithm 3 Algorithm 2 (FindImpoDiff) |
| Input: a parameter c and a block cipher where . Output: Impossible differentials of .
|
4. Quantum Attacks Based on Truncated Differentials
For some block ciphers, it is almost impossible to identify a differential of which the probability is strictly 1. Thus, many attacks that have been proposed consider the truncated probability-1 differentials. For truncated differentials [31], only partial bits instead of the full differentials are certain. For many block ciphers, such as SAFERK64 [32] and Camellia [33], truncated differential analysis can attack more rounds than traditional differential analysis, or the attack complexity is greatly reduced when attacking the same number of rounds. In this section, we improve the FindImpoDiff algorithm by allowing the differentials with a probability of 1 to be truncated differentials.
4.1. Improved Algorithm for Impossible Differentials
To improve Algorithm 2 (FindImpoDiff), we allow the unmatched probability-1 differentials to be truncated differentials when applying the miss-in-the-middle method. That is, only partial bits of the probability-1 differentials are predicted.
Let denote a truncated differential of , where . Suppose , , then for . The notation “∗” indicates that the corresponding bits of the input or output differences are undetermined. If /, then we refer to the i-th bit (the determined bit of /), otherwise, we refer to it as the undetermined bit of /. A truncated difference can actually be regarded as a set of full differences. Let
The truncated input difference is equivalent to the set , and the truncated output difference is equivalent to the set . If a full input difference is included in the set ; that is, for all where , then is said to coincide with the truncated input difference , and denoted as . Similarly, if a full output difference is in the set , then coincides with the truncated output difference , and is denoted as . Two truncated differentials, , are said to contradict each other if there exists an satisfying , and .
The probability of the truncated differential is the conditional probability, expressed as follows:
If this differential probability is equal to one, we refer to as a probability-1 truncated differential of .
We still divide , where . Let be the i-th component function of , as follows:
Similarly, denotes the i-th component function of . If the truncated differential of has probability-1, the truncated differential of also has probability-1, and contradicts with , then will be ’s impossible differential. These conditions imply that there exists such that and are probability-1 differentials of and , respectively, and (). In this case, will be ’s impossible differential, as shown in Figure 5. Thus, we only need to traverse i to identify the differentials of and with probability-1. This can be performed using the FindStruct algorithm to identify their linear structures. According to these analyses, we designed an improved algorithm that finds impossible differentials, which is named Algorithm 3 (FindImpoDiff2).
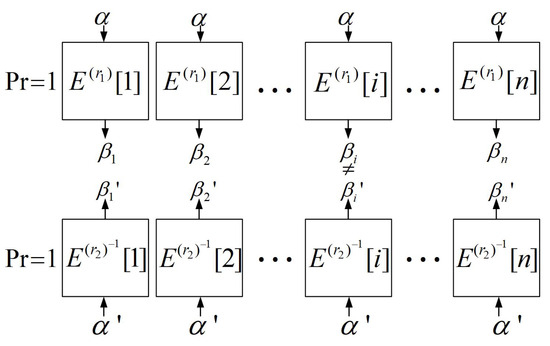
Figure 5.
Illustration of how truncated differentials constitute an impossible differential.
Figure 6 shows the flowchart of Algorithm 3 (FindImpoDiff2). Algorithm 3 (FindImpoDiff2) traverses from 1 to , dividing into , and then traverses i from 1 to n to obtain differentials of and , which have probability-1 but lead to a contradiction in the middle. We define the following:
where is the t-round reduced cipher of , is the i-th component function of , and is defined as Equation (6). That is, we have the following:
where is the linear structure space of . According to Theorem 2, the following theorem holds.
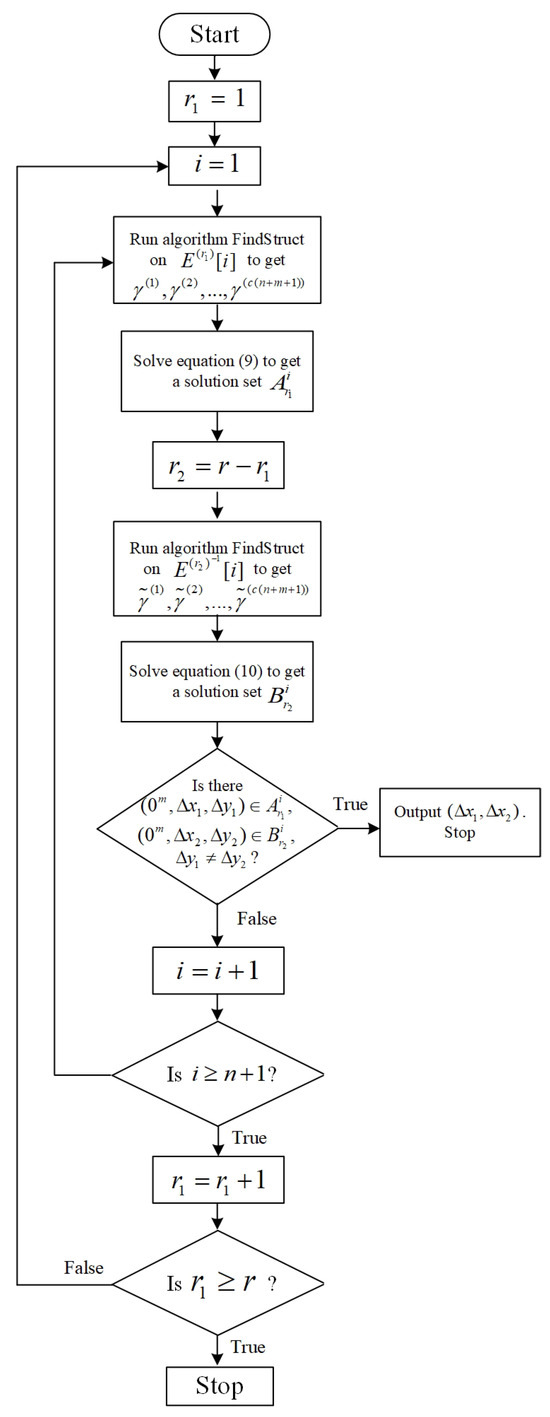
Figure 6.
Flowchart of Algorithm 2 (FindImpoDiff).
Theorem 4.
is the block cipher whose round number is r, the block size is n, and the key length is m. denotes the constant . If is output by Algorithm 3 (FindImpoDiff2) when running on , then the probability of being an impossible differential of is no less than .
According to Theorem 4, setting c greater than guarantees that Algorithm 3 (FindImpoDiff2) outputs impossible differentials of .
4.2. Complexity of Algorithm 3 (FindImpoDiff2)
The process of the FindImpoDiff algorithm does not involve quantum queries and, thus, can be executed by Q1 adversaries. We still evaluate the complexity by calculating the amounts of qubits and quantum gates.
In Algorithm 3 (FindImpoDiff2), finding probability-1 differentials of requires executing steps 1–7 of Algorithm 1 (FindStruct) on with parameter c. This requires Hadamard gates, CNOT gates, and executions of the unitary operator . Similarly, finding probability-1 differentials of requires Hadamard gates, CNOT gates, and executions of the unitary operator . Thus, the number of Hadamard gates in Algorithm 3 (FindImpoDiff2) is as follows:
The number of CNOT gates in Algorithm 3 (FindImpoDiff2) is as follows:
Algorithm 3 (FindImpoDiff2) also requires the execution of the unitary operators and times for each , and . We have the following:
Algorithm 3 (FindImpoDiff2) additionally requires executing the quantum circuit of for times. The quantum resources used to implement Algorithm 2 (FindImpoDiff) are listed in Table 1.
Running the FindStruct subroutine on requires qubits. Running the FindStruct subroutine on also requires qubits. Because of the reusability of qubits, qubits are enough for Algorithm 3 (FindImpoDiff2).
We compare classical automated tools to search for impossible differentials with the proposed quantum tools in Table 2, where the SAT problem is the Boolean satisfiability problem and MILP is the abbreviation for mixed-integer linear programming. As shown in Table 2, the UID tool, U-tool, and WW-tool cannot characterize the impact of S-boxes. The MILP tool can only describe small S-boxes. The SAT tool can describe big S-boxes but the impact of S-boxes can only be partially characterized. In contrast, the quantum algorithms we propose can fully characterize nonlinear functions, including S-boxes of any size. The MILP tool and SAT tool need to solve the MILP problem and SAT problem, respectively, both of which are NP-complete. In contrast, the proposed quantum algorithms only need to solve linear equations, which cost polynomial complexity using Gaussian elimination.
It is difficult to directly compare the complexity of classical tools for searching impossible differentials with quantum tools on specific block ciphers. The search for impossible differentials does not constitute a complete attack in itself. The identified impossible differentials are used to eliminate incorrect keys during the subsequent key recovery phase. The complexity of a classical attack is generally measured by the number of calculations and the number of chosen plaintexts required in the online key recovery phase, rather than by the calculations or time needed to identify the distinguishers in the early phase. In fact, the practicality of classical tools for searching impossible differentials on specific ciphers is determined by whether the search can be completed within a reasonable timeframe, rather than by adhering to a strict complexity formula. For example, the authors of [34] show that searching for impossible differentials of 14-round PRESENT-80 can be accomplished, but the search for 15 rounds could not be completed even after 20 days, leading the authors to finally terminate the search for 15 rounds. Classical automated tools for searching various distinguishers are usually compared using the number of rounds of specific ciphers that can be searched. However, in quantum attacks, since quantum computers have not been built yet, we cannot obtain the actual execution results of the quantum tools. Thus in quantum attacks, the success probability and complexity (the number of qubits and gates) are rigorously computed to measure the efficiency. Although the cost of a quantum operation is different from that of a classical operation, it is generally believed that polynomial-level quantum complexity is far superior to exponential classical complexity. This is why Shor’s algorithm has attracted widespread attention and even led to research on post-quantum cryptography.
Block cipher Camellia has 24 rounds [35]. The longest impossible differential of Camellia found so far has eight rounds [36]. It is found through theoretical derivation and does not involve any construction of S-boxes. Since the scale of the S-boxes in Camellia is 8-bit, no classical automated tool has yet been able to find longer impossible differentials by characterizing the S-boxes. AES-128 cipher has 10 rounds [37]. By the partial description of S-boxes, the SAT tool can accomplish a five-round search for impossible differentials of AES-128 [38]. However, the full description of S-boxes or the search for more rounds cannot be realized in an affordable time. Block cipher Midori-128 has 20 rounds [39]. The S-boxes applied by Midori-128 have eight bits. But each eight-bit S-box is actually constructed by two four-bit S-boxes. By the full description of four-bit S-boxes, the MILP tool can accomplish an eight-round search for impossible differentials of Midori-128 [40]. The search for more rounds cannot be realized in an affordable time. From the above examples, it can be seen that classical automated tools have difficulty increasing the number of rounds since they need to solve problems like MILP or SAT. However, our quantum tools only require polynomial complexity when applied to all the block ciphers mentioned above, even if the S-boxes are fully characterized. Moreover, as shown in Table 1, the number of qubits and gates required increases linearly with the number of rounds. This shows the superiority of quantum tools.
Some prior works have also investigated the use of quantum algorithms to enhance classical analytic tools. We list some representative examples in Table 3 for comparison. The goals of the second and third quantum tools in Table 3 are not to identify differentials or linear approximations, but to use Grover’s algorithm to accelerate the search for subkeys in the key recovery stage of traditional differential analysis and linear analysis.

Table 2.
Comparisons with classical automated tools.
Table 2.
Comparisons with classical automated tools.
| Tools | Description of Nonlinear Components | Problems Need to Solve | Ref. |
|---|---|---|---|
| UID tool | No | / | [21] |
| U-tool | No | / | [22] |
| WW-tool | No | Linear equations system | [23] |
| MILP-tool | Full description of small S-boxes (≤ 6-bit) | MILP problem | [40,41] |
| SAT-tool | Partial description of big S-boxes (8-bit) | SAT problem | [38] |
| Quantum tools | Any nonlinear functions | Linear equations system | This paper |

Table 3.
Quantum cryptanalysis tools.
Table 3.
Quantum cryptanalysis tools.
| Cryptanalysis Tool to Be Enhanced | Goal of Quantum Algorithms | Underlying Quantum Algorithm Used | Ref. |
|---|---|---|---|
| Differential cryptanalysis | Find high-probability differentials | Bernstein–Vazirani algorithm | [42,43] |
| Differential cryptanalysis | Accelerate the key search | Grover’s algorithm | [18] |
| Linear cryptanalysis | Accelerate the key search | Grover’s algorithm | [18] |
| Zero correlation linear cryptanalysis | Find zero correlation linear approximations | Bernstein–Vazirani algorithm | [44] |
| Impossible differential cryptanalysis | Find impossible differentials | Simon’s algorithm | This paper |
4.3. Simulation
We use a simple Boolean function as an example to simulate the process of using the FindStruct algorithm to identify linear structure duads (i.e., probability-1 differentials). This demonstrates the validity of the FindStruct algorithm. The main process of Algorithm 2 (FindImpoDiff) involves repeating the FindStruct algorithm multiple times. According to the principle of miss-in-the-middle, as long as the outputs of the FindStruct algorithm are indeed probability-1 differentials, then the outputs of Algorithm 2 (FindImpoDiff) must be impossible differentials. Therefore, the validity of Algorithm 2 (FindImpoDiff) is also justified.
Specifically, we choose function as an example, whose truth table is shown in Table 4. We use Qiskit to simulate the FindStruct algorithm on F. This requires repeating the FindStruct subroutine to obtain measurement results . The corresponding quantum circuit diagram generated by Qiskit is shown in Figure 7. The middle part of the circuit realizes the unitary operator of F.

Table 4.
Truth table of F.
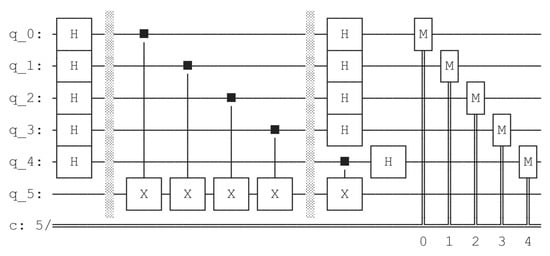
Figure 7.
Quantum circuit diagram generated by Qiskit.
Because the number of simulations for quantum algorithms is often set at 1024 or 2048, we chose to simulate 1024 times. As shown in Figure 8, the measurement results only yield two values: 00000 or 11111. Computing the following equation, i.e.,
yields a fundamental solution system, as follows:
where are the unknowns. Therefore, {(0000,0), (1100,0), (1010,0), (1001,0) (0110,0), (0011,0), (0101,0), (1111,0), (1000,1), (0100,1), (0010,1), (0001,1) (1110,1), (1011,1), (1101,1), (0111,1)} should all be probability-1 differentials (linear structure duals) of F. It is easy to verify that these pairs are indeed probability-1 differentials of F.
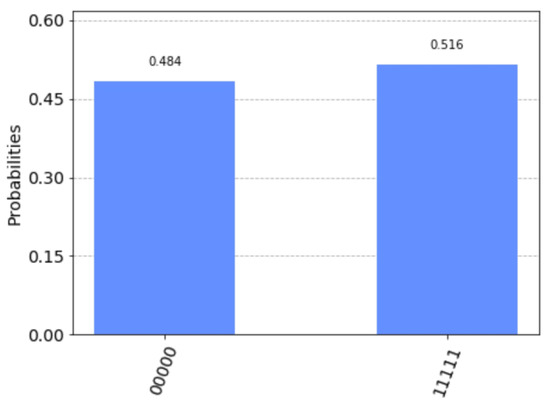
Figure 8.
Measurement results simulated by Qiskit.
5. Results and Discussion
In this work, we developed quantum automated cryptanalysis tools to search for impossible differentials. Our tools combine the impossible differential attack with Simon’s algorithm. We rigorously prove that, if an impossible differential of the block cipher is linked by two truncated differentials with probability-1, the proposed quantum algorithms must be able to output these impossible differentials in polynomial time. To analyze the complexity, we calculate the number of various quantum operators required in the quantum algorithms and summarized them in Table 1. Since the round number, r, as shown in each dataset in Table 1, has a degree of 1, the complexity of the proposed algorithms increases linearly with the number of rounds.
Our quantum cryptanalysis tools do not require any query to the encryption or decryption oracle and can be implemented in the Q1 model. Thus, they can be easily realized using quantum computers. Compared with the classical automated impossible differential cryptanalysis, our quantum automated tools fully utilize the superiority of quantum computing, allowing for complete characterization of any nonlinear functions while maintaining complexity within polynomial time. Moreover, the proposed quantum cryptanalysis tools take the key schedule into account in a single-key model, thereby compensating for the shortcomings of traditional tools.
A natural direction for further research is to enhance the cryptanalysis tools proposed in this study to reduce quantum resource consumption, or to enhance other cryptanalysis methods with quantum algorithms, such as integral and linear attacks. Combining cryptanalysis tools with Grover’s algorithm may also be a direction worth exploring.
Author Contributions
Conceptualization, H.X. and Q.X.; methodology, H.X., Q.X., K.W. and L.Y.; validation, H.X. and Y.L.; formal analysis, H.X., K.W. and L.Y.; writing—original draft preparation, H.X. and Q.X.; writing—review and editing, H.X. and Y.L.; visualization, H.X. and K.W.; funding acquisition, H.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Beijing Natural Science Foundation (no. 4234084) and the Open Research Fund of Key Laboratory of Cryptography of Zhejiang Province (no. ZCL21012).
Data Availability Statement
The original contributions presented in this study are included in the article; further inquiries can be directed to the corresponding author.
Conflicts of Interest
Author L.Y. was employed by the company Information Industry Information Security Evaluation Center, The 15th Research Institute of China Electronics Technology Group Corporation. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest. The authors declare that this study received funding from Beijing Natural Science Foundation (no. 4234084). The funder had the following involvement with the study: Conceptualization, methodology, validation, formal analysis, writing—original draft preparation, writing—review and editing, visualization.
Appendix A
Theorem A1.
Let L be the solution set output by the FindStruct algorithm run on with a parameter, c, then . Moreover, if there is a constant, , such that , then the probability of being equal to L is no less than .
Proof
We first prove that . To do this, we only need to prove that each linear structure must be a solution to Equation (5). In step 5 of the FindStruct algorithm, the state
is measured and the measurement result is denoted as z. Then there are , such that . We define the set, i.e.,
then the first two registers of are collapsed to the state . Obviously, . For any , let , then , and
Thus,
Since the linear structure duads of F cause matches of F at all points , for each , is in . Suppose that is the basis of space , then for any , we have the following:
Therefore,
In addition to linear structures, there may be other vectors causing a match at . Let denote such vectors. Namely, but . Thus, for any ,
So, is also in the set . Suppose are two of these vectors, i.e., they both cause a match at but are not in . Since is a linear space, the following two sets, i.e.,
are either equal or have no intersection at all. Therefore, the measurement in step 5 of the FindStruct algorithm causes the first two registers of to collapse into a state with the following form:
where are the vectors that cause matches at but not in . Denoting , , this state can be written as follows:
In step 6, after performing a Hadamard gate , the first two registers are as follows:
where we omit the global coefficient . For any , if there exists such that , then the amplitude of in the above quantum state is zero. Therefore, the FindStruct algorithm always outputs a random value such that for all , which means must be in the solution space L of Equation (5). Thus, we have .
Then, we prove the probability that is no less than as long as . means that there is a vector , which is a solution to Equation (5) but not in . Thus, we have the following:
where are outputs of the FindStruct subroutine and are independent and identically distributed random variables. To calculate the probability , all measurements of the FindStruct subroutine are moved to the end. According to the principle of deferred measurement, this does not change the outputs. Therefore, the state without being measured is as follows:
The probability of satisfying is as follows:
According to Lemma 1 in [7], the following holds:
Thus,
Combining Equation (A1), we have the following:
□
References
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Simon, D.R. On the power of quantum computation. SIAM J. Comput. 1997, 10, 1474–1483. [Google Scholar] [CrossRef]
- Kuwakado, H.; Morii, M. Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2682–2685. [Google Scholar]
- Kuwakado, H.; Morii, M. Security on the quantum-type Even-Mansour cipher. In Proceedings of the Information Theory and Its Applications, Honolulu, HI, USA, 28–31 October 2012; pp. 312–316. [Google Scholar]
- Santoli, T.; Schaffner, C. Using Simon’s algorithm to attack symmetric-key cryptographic primitives. Quantum Inf. Comput. 2017, 17, 65–78. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Breaking symmetric cryptosystems using quantum period finding. In Proceedings of the Advances in Cryptology—CRYPTO 2016, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 207–237. [Google Scholar]
- Leander, G.; May, A. Grover Meets Simon–Quantumly Attacking the FX-construction. In Proceedings of the Advances in Cryptology—ASIACRYPT 2017, Hong Kong, China, 3–7 December 2017; Springer: Cham, Switzerland, 2017; pp. 161–178. [Google Scholar]
- Dong, X.; Wang, X. Quantum key-recovery attack on Feistel structures. Sci. China Inf. Sci. 2018, 10, 240–246. [Google Scholar] [CrossRef]
- Dong, X.; Wang, X. Quantum cryptanalysis on some generalized Feistel schemes. Sci. China Inf. Sci. 2019, 62, 22501:1–22501:12. [Google Scholar] [CrossRef]
- Damgård, I.; Funder, J.; Nielsen, J.B.; Salvail, L. Superposition attacks on cryptographic protocols. In Proceedings of the International Conference on Information Theoretic Security, Cham, Switzerland, 28–30 November 2013; pp. 142–161. [Google Scholar]
- Boneh, D.; Zhandry, M. Secure signatures and chosen ciphertext security in a quantum computing world. In Proceedings of the Advances in Cryptology—CRYPTO 2013, Santa Barbara, CA, USA, 18–22 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 361–379. [Google Scholar]
- Gagliardoni, T.; Hlsing, A.; Schaffner, C. Semantic security and indistinguishability in the quantum world. In Proceedings of the Advances in Cryptology—CRYPTO 2016, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 60–89. [Google Scholar]
- Roetteler, M.; Steinwandt, R. A note on quantum related-key attacks. Inf. Process. Lett. 2015, 115, 40–44. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Aoki, K. On quantum related-key attacks on iterated Even-Mansour ciphers. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, 102, 27–34. [Google Scholar] [CrossRef]
- Jaques, S.; Naehrig, M.; Roetteler, M.; Virdia, F. Implementing Grover Oracles for Quantum Key Search on AES and LowMC. In Proceedings of the Advances in Cryptology—EUROCRYPT 2020, Zagreb, Croatia, 10–14 May 2020; Springer: Cham, Switzerland, 2020; pp. 280–310. [Google Scholar]
- Zhou, Q.; Lu, S.; Zhang, Z.; Sun, J. Quantum differential cryptanalysis. Quantum Inf. Process. 2015, 14, 2101–2109. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Quantum differential and linear cryptanalysis. IACR Trans. Symmetric Cryptol. 2016, 2016, 71–94. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Sasaki, Y. Finding Hash Collisions with Quantum Computers by Using Differential Trails with Smaller Probability than Birthday Bound. In Proceedings of the Advances in Cryptology—EUROCRYPT 2020, Zagreb, Croatia, 10–14 May 2020; Springer: Cham, Switzerland, 2020; pp. 249–279. [Google Scholar]
- Dong, X.; Sun, S.; Shi, D.; Gao, F.; Wang, X.; Hu, L. Quantum Collision Attacks on AES-Like Hashing with Low Quantum Random Access Memories. In Proceedings of the Advances in Cryptology—ASIACRYPT 2020, Daejeon, Republic of Korea, 7–11 November 2020; Springer: Cham, Switzerland, 2020; pp. 727–757. [Google Scholar]
- Luo, Y.; Lai, X.; Wu, Z.; Gong, G. A unified method for finding impossible differentials of block cipher structures. Inf. Sci. 2014, 263, 211–220. [Google Scholar] [CrossRef]
- Kim, J.; Hong, S.; Sung, J.; Lee, S.; Lim, J.; Sung, S. Impossible differential cryptanalysis for block cipher structures. In Proceedings of the 4th International Conference on Cryptology, New Delhi, India, 8–10 December 2003. [Google Scholar]
- Wu, S.; Wang, M. Automatic search of truncated impossible differentials for word oriented block ciphers. In Proceedings of the Progress in Cryptology—INDOCRYPT 2012, Kolkata, India, 9–12 December 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 283–302. [Google Scholar]
- Liu, Y.; Xiang, Z.; Chen, S.; Zhang, S.; Zeng, X. A Novel Automatic Technique Based on MILP to Search for Impossible Differentials. In Proceedings of the Applied Cryptography and Network Security (ACNS 2023), Kyoto, Japan, 19–22 June 2023; Springer: Cham, Switzerland, 2023; pp. 119–148. [Google Scholar]
- Sun, L.; Wang, M. SoK: Modeling for large s-boxes oriented to differential probabilities and linear correlations. IACR Trans. Symmetric Cryptol. 2023, 2023, 111–151. [Google Scholar] [CrossRef]
- Winternitz, R.; Hellman, M. Chosen-key attacks on a block cipher. Cryptologia 1987, 11, 16–20. [Google Scholar] [CrossRef]
- Xiang, Z.; Wang, X.; Yu, B.; Sun, B.; Zhang, S.; Zeng, X.; Shen, X.; Li, N. Links between Quantum Distinguishers Based on Simon’s Algorithm and Truncated Differentials. IACR Trans. Symmetric Cryptol. 2024, 2024, 296–321. [Google Scholar] [CrossRef]
- Nielsen, M.; Chuang, I. Quantum Computation and Quantum Information, 1st ed.; Cambridge University Press: Cambridge, MA, USA, 2000. [Google Scholar]
- Li, H.; Yang, L. A quantum algorithm to approximate the linear structures of Boolean functions. Math. Struct. Comput. Sci. 2016, 28, 1–13. [Google Scholar] [CrossRef]
- Biham, E.; Biryukov, A.; Shamir, A. Cryptanalysis of Skipjack reduced to 31 rounds using impossible differentials. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 12–23. [Google Scholar]
- Knudsen, L.R. Truncated and higher order differentials. In Proceedings of the Fast Software Encryption: Second International Workshop, Leuven, Belgium, 1–16 December 1994; Springer: Berlin/Heidelberg, Germany, 1994; pp. 196–211. [Google Scholar]
- Wu, H.; Bao, F.; Deng, R.H.; Ye, Q. Improved truncated differential attacks on SAFER. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 18–22 October 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 133–147. [Google Scholar]
- Kanda, M.; Matsumoto, T. Security of Camellia against truncated differential cryptanalysis. In Proceedings of the Fast Software Encryption: 8th International Workshop, Yokohama, Japan, 2–4 April 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 286–299. [Google Scholar]
- Sun, S.; Hu, L.; Wang, P.; Qiao, K.; Ma, X.; Song, L. Automatic security evaluation and (related-key) differential characteristic search: Application to SIMON, PRESENT, LBlock, DES (L) and other bit-oriented block ciphers. In Proceedings of the 20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 158–178. [Google Scholar]
- Aoki, K.; Ichikawa, T.; Kanda, M.; Matsui, M.; Moriai, S.; Nakajim, J.; Tokita, T. Camellia: A 128-bit block cipher suitable for multiple platforms—Design and analysis. In Proceedings of the 7th SAC, Selected Areas in Cryptography (SAC 2000), Waterloo, ON, Canada, 14–15 August 2000; Springer: Berlin/Heidelberg, Germany, 2012; pp. 39–56. [Google Scholar]
- Jia, K.; Wang, N. Impossible differential cryptanalysis of 14-round camellia-192. In Proceedings of the 21st Australasian Conference on Information Security and Privacy, Melbourne, VIC, Australia, 4–6 July 2016; Springer: Cham, Switzerland, 2016; pp. 363–378. [Google Scholar]
- Sanchez-Avila, C.; Sanchez-Reillol, R. The Rijndael block cipher (AES proposal): A comparison with DES. In Proceedings of the IEEE 35th Annual International Carnahan Conference on Security Technology, London, UK, 16–19 October 2001; pp. 229–234. [Google Scholar]
- Hu, X.; Li, Y.; Jiao, L.; Tian, S.; Wang, M. Mind the propagation of states: New automatic search tool for impossible differentials and impossible polytopic transitions. In Proceedings of the 26th International Conference on the Theory and Application of Cryptology and Information Security, Daejeon, Republic of Korea, 7–11 December 2020; Springer: Cham, Switzerland, 2020; pp. 415–445. [Google Scholar]
- Banik, S.; Bogdanov, A.; Isobe, T.; Shibutani, K.; Hiwatari, H.; Akishita, T.; Regazzoni, F. Midori: A block cipher for low energy. In Proceedings of the 21st International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 411–436. [Google Scholar]
- Sasaki, Y.; Todo, Y. New impossible differential search tool from design and cryptanalysis aspects: Revealing structural properties of several ciphers. In Proceedings of the 36th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Paris, France, 30 April–4 May 2017; Springer: Cham, Switzerland, 2017; pp. 185–215. [Google Scholar]
- Cui, T.; Chen, S.; Jia, K.; Fu, K.; Wang, M. New Automatic Search Tool for Impossible Differentials and Zero-Correlation Linear Approximations. Cryptology ePrint Archive. 2016. Available online: https://eprint.iacr.org/2016/689 (accessed on 1 May 2022).
- Li, H.; Yang, L. Quantum differential cryptanalysis to the block ciphers. In Proceedings of the 6th International Conference on Applications and Techniques in Information Security, Beijing, China, 4–6 November 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 44–51. [Google Scholar]
- Xie, H.; Yang, L. Using Bernstein-Vazirani algorithm to attack block ciphers. Des. Codes Cryptogr. 2019, 87, 1161–1182. [Google Scholar] [CrossRef]
- Zhang, K.; Shang, T.; Tang, Y.; Liu, J. Zero-correlation linear analysis for block ciphers based on the Bernstein-Vazirani and Grover algorithms. Quantum. Inf. Process 2024, 23, 289. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).