Abstract
Data hiding in digital images is a potent solution for covert communication, embedding sensitive data into cover images. However, most existing methods are tailored for one-to-one scenarios, which present security risks. To mitigate this vulnerability, we introduce an innovative one-to-two data hiding scheme that employs a two-tier bit-flipping strategy to embed sensitive data in dual images. This process produces two stego images which are then transmitted to two distinct recipients who cannot extract any sensitive data alone. The sensitive data can only be extracted when the two recipients trust each other. Through this method, we can secure the stego images. The experimental results illustrate that our method achieves an excellent data payload while maintaining high visual quality.
MSC:
68P27
1. Introduction
With the proliferation of sensitive data being shared online, covert communication becomes imperative to ensure secure transmission. In response, data hiding technology has emerged as a solution to embed sensitive data within cover media [1]. However, traditional data hiding methods often cause irreversible damage to the cover media. To address this issue, reversible data hiding (RDH) schemes have been developed to allow the restoration of the original cover media after extracting sensitive data.
As digital images are ubiquitous in multimedia applications, numerous reversible data hiding (RDH) techniques have emerged in recent years. These techniques can be categorized into four types based on the processing domain: spatial domain-based methods, transform domain-based methods, compressed domain-based methods, and encryption domain-based methods. The spatial domain-based techniques [2,3,4,5,6,7,8,9,10,11,12,13] involve modifying pixel values directly to embed secret data into images. Transform domain-based techniques [14,15,16,17] convert plaintext images into frequency coefficients first and embed secret data by modifying these coefficient values. Compressed domain-based approaches [18,19,20,21,22] leverage the compressed codes of digital images as carriers for data embedding. With the rapid evolution of cloud technology, encryption domain-based methods have emerged. These techniques involve encrypting the cover image before transmission through a public channel and ensuring the confidentiality of images while concealing sensitive data [23,24,25].
However, the methods mentioned above are designed for a one-to-one model where there is only one sender and one recipient throughout the entire process. One significant concern with these approaches is that they grant the recipient considerable influence over the stego image, potentially compromising the confidentiality and integrity of the embedded data. To address this problem, the dual-image RDH method has been introduced. In 2015, Qin et al. [26] proposed a dual-image reversible data hiding (RDH) method based on the exploiting modification direction (EMD) technique. In their method, secret data are embedded into the pixels of the first cover image using the EMD technique, while the pixels of the second cover image are adaptively adjusted according to the modifications made to the first image. Later, Lu et al. [27] introduced a method to mitigate image distortion, where the value of the secret data are reduced using the center folding strategy. The reduced secret data are then embedded into two cover images using the averaging method. On this basis, Yao et al. [28] further enhanced the embedding capacity without introducing any additional distortion. In 2018, Jana et al. [29] introduced a novel RDH method for dual-image utilizing the (7, 4) Hamming code. Their approach involves adjusting the redundant Least Significant Bits (LSBs) of a block of seven pixels with an odd parity. The secret data are then embedded by introducing errors caused by tampering in suitable positions, and leveraging the properties of the Hamming code. Based on the characteristics of the EMD matrix, Chen et al. [30] embedded one secret bit and a base-5 digit into a cover pixel to generate a pixel pair and assigned to two stego images. In 2023, Kim et al. [31] employed a (3, 1) Hamming code and an optimal pixel adjustment process (OPAP) to embed secret data into the dual images. In this one-to-two model, two stego images are generated and transmitted to two recipients. In this case, the two recipients can extract the embedded sensitive data only if they establish trust in each other. By distributing sensitive data across two stego images and requiring mutual trust between the two recipients for extraction, the dual-image RDH method enhances security in covert communication scenarios. However, existing methods often have limitations in embedding capacity, which may not be sufficient for applications requiring large data payloads. Therefore, there is an urgent need for advancements in dual-image reversible data hiding techniques to accommodate these high-capacity application demands.
Given the necessity for greater embedding capacity, we present a novel two-tier bit-flipping embedding strategy within the dual-image RDH framework. The original image is transformed to form two cover images first. Then, pixels from the corresponding positions of the cover images are paired. Afterward, sensitive data are embedded using a two-tier bit-flipping strategy where the bits of the pixel pairs undergo a bit-flipping process. The resulting stego images are transmitted to the recipients who cannot extract private information from the stego image alone. Sensitive data can only be extracted when they trust each other. Our method is applicable to common public communication channels such as email and Facebook. An application example is given in Figure 1. The contributions of the proposed scheme are outlined below:
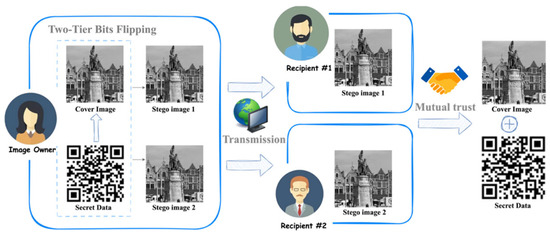
Figure 1.
The application example of the proposed scheme.
- (1)
- We introduce a two-tier bit-flipping embedding strategy for covert communication.
- (2)
- The proposed dual-image RDH method is better suited for covert communication scenarios than single-image RDH methods.
- (3)
- Our scheme surpasses existing methods in embedding capacity while maintaining high image quality.
The subsequent sections of this paper are structured as follows: Section 2 introduces a state-of-the-art dual-image-based RDH method. Section 3 elaborates on the proposed two-tier bit-flipping embedding strategy. Experimental results and discussions are provided in Section 4. Finally, Section 5 concludes this scheme.
2. Related Works
In this section, we introduce a reversible data hiding scheme based on dual images proposed by Kim et al. [31]. Their scheme employs a (3, 1) Hamming code and an optimal pixel adjustment process (OPAP) [32] in data embedding. It consists of two essential components: cover image generation and data embedding.
2.1. Generation of Two Cover Images
Given a grayscale image of size where the pixels are denoted as , two cover images and are generated based on this grayscale image. The details are outlined below. The Equations (1)–(5) are all derived from [31].
Step 1: Read a pixel in the grayscale image and assign into pixel and , where and .
Step 2: Construct a 3-bits codeword from the pixel pair by
Step 3: Compute the syndrome of the codeword using
where
Step 4: Flip the -th bit of the codeword when to obtain the error correction codeword with .
Step 5: Update the pixel pair to the cover pixel pair by
and
Step 6: Backfill the updated pixel pair to their corresponding positions.
Step 7: Repeat Steps 1–6 until all pixel pairs have been processed, resulting in the generation of two cover images, and .
2.2. Secret Data Embedding
After obtaining these two cover images and , they are utilized for embedding secret data. The details of this process are explained below.
Step 1: Read pixels from the corresponding positions of the two cover images and to form the pixel pair , where and .
Step 2: Divide the secret data into 2-bit segments.
Step 3: Construct a 3-bits codeword of the pixel pair by Equation (1).
Step 4: Compute the syndrome of the codeword using Equation (2).
Step 5: Perform an exclusive-OR operation between the syndrome and a secret segment to obtain a re-computed syndrome .
Step 6: Flip the bit of the codeword to obtain the error-corrected codeword .
Step 7: Update the pixel pair to the stego pixel pair by Equations (3)–(5).
Step 8: Backfill the updated pixel pair to their corresponding positions.
Step 9: Repeat Steps 1–8 until all pixel pairs have been processed, resulting in the generation of two stego images, and .
Essentially, this method reconstructs the least significant bits (LSBs) of original pixel pairs into the error correction codeword of (3, 1) Hamming code to generate cover pixel pairs. During the embedding process, the error correction codeword is adjusted based on the secret segment, resulting in the creation of stego pixel pairs. Additionally, the image distortion is reduced by modifying pixel pairs using OPAP technology.
3. Proposed Scheme
In this section, the proposed covert communication scheme for dual images is described in detail. Its flowchart is given in Figure 2. In this scheme, the image owner embeds secret data into a grayscale image through a two-tier bit-flipping embedding strategy to generate two stego images. Subsequently, these two stego images are independently transmitted to two separate recipients. In cases where mutual trust is established between the two recipients, they can accurately extract the secret data and losslessly recover the cover image.
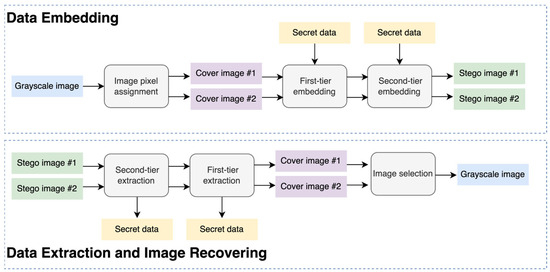
Figure 2.
The flowchart of the proposed scheme.
3.1. Two-Tier Bit-Flipping Embedding Strategy
Given a grayscale image of size , the pixels are represented by . As the grayscale image allows 256 distinct intensities, each pixel can be transformed as an 8-bit pixel binary bitstream . The secret data are embedded into the grayscale image using a two-tier bit-flipping embedding strategy as follows:
Step 1: Assign the grayscale image into two cover images and .
Step 2: Divide the secret data into two-bit secret segments.
Step 3: Read pixels from the corresponding locations of the two cover images and to form the pixel pairs .
Step 4: Embed two secret segments into each pixel pair using the two-tier bit-flipping embedding strategy.
Step 4.1: Embed the first secret segment into the pixel pair by the first-tier embedding resulting in the updated pixel pair .
Step 4.2: Embed the second secret segment into the updated pixel pair by the second-tier embedding resulting in the stego pixel pair .
Step 5: Repeat Step 4 until all pixel pairs are processed.
Step 6: Backfill with the stego pixel pairs to their corresponding positions in the two stego images, and .
The rules for the first-tier and the second-tier embeddings are provided in Algorithms 1 and 2, respectively. Here, flips the bit , sets the bit to the value , returns the updated value after processing , and represents the exclusive-or operation. In essence, our two-tier bit-flipping embedding strategy involves executing the bit-flipping within a pixel pair to embed secret data. In the first-tier embedding, we may flip bit , bit , or both and bits depending on the values of the secret bits illustrated in Figure 3a. Consequently, the updated pixel pair is obtained. Moving to the second-tier embedding, bit flips occurred among , , and bits are depicted in Figure 3b. Note that the 7-th bits of the pixel pair may undergo bit flipping in both tiers. To indicate the state of the bit 7 after the first-tier embedding, serves as a label before the bit-flipping in the second tier by checking whether and are the same or not. That is, when and when . The second-tier embedding results a stego pixel pair . After processing all pixel pairs, the resulting stego pixel pairs are backfilled into their corresponding positions in the stego images and . The two stego images are totally transmitted to two recipients and afterwards, each of whom is aware of the specific stego image they receive (see Algorithms 1 and 2).
| Algorithm 1: The first-tier embedding. | |
| Input: | Original pixel pair ( and the first secret segment . |
| Output: | Updated pixel pair . |
| 1: | If |
| 2: | |
| 3: | Else if |
| 4: | |
| 5: | Else if |
| 6: | |
| 7: | Else if |
| 8: | |
| 9: | End |
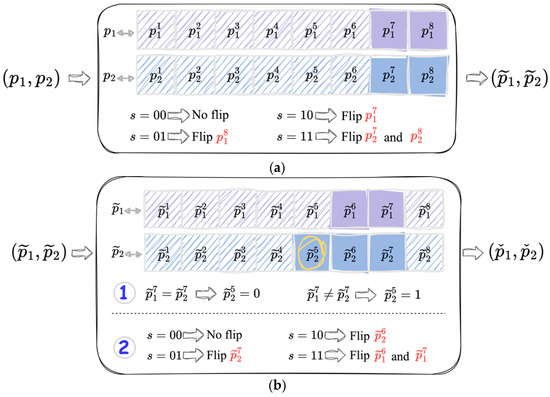
Figure 3.
Schematic of the two-tier bit-flipping embedding strategy. (a) The first-tier. (b) The second-tier, where “1” and “2” are two distinct steps.
| Algorithm 2: The second-tier embedding. | |
| Input: | Updated pixel pair and the second secret segment . |
| Output: | Stego pixel pair . |
| 1: | If |
| 2: | |
| 3: | Else if |
| 4: | |
| 5: | Else if |
| 6: | |
| 7: | Else if |
| 8: | |
| 9: | End |
To illustrate the process of the two-tier bit-flipping embedding, we present two examples in Figure 4. In Figure 4a, the given pixel pair is utilized to embed the secret segments “01” and “10”. We first embed the secret segment “01” into the pixel pair by flipping . The first tier embedding leads to the updated pixel pair . Subsequently, we set , indicating that . Following this, the secret segment “10” is embedded by flipping . The second-tier embedding yields the stego pixel pair . In Figure 4b, the given pixel pair is employed to embed the secret segments “10” and “11”. The embedding process begins by flipping to embed the secret segments “10”. This operation results in the updated pixel pair . Since , we then set . The stego pixel pair is attained by flipping and .
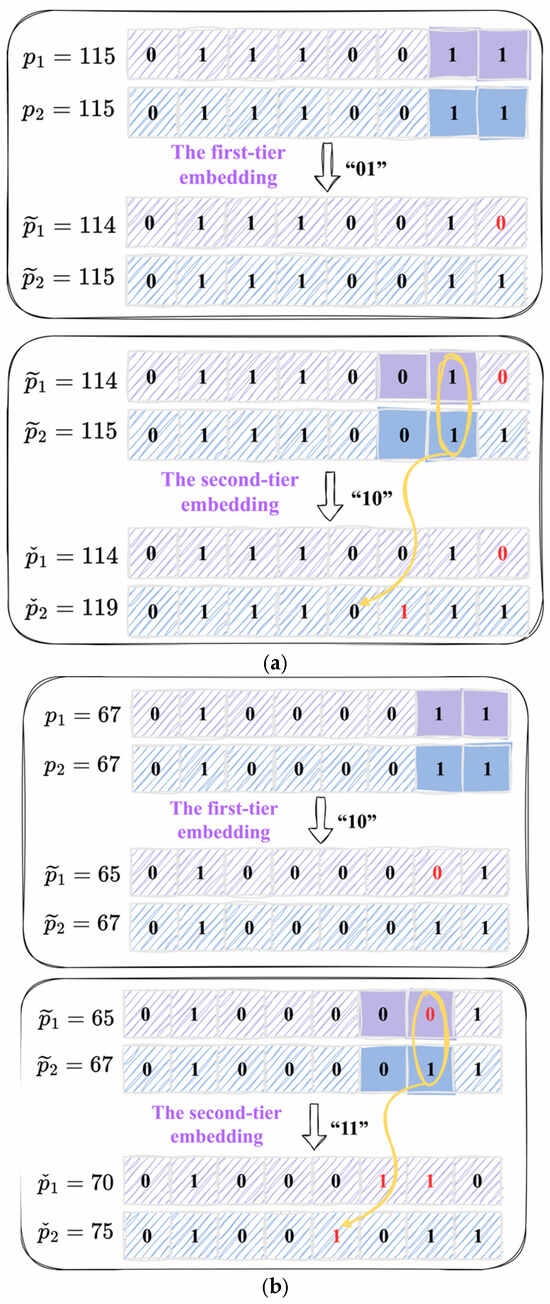
Figure 4.
Two numerical examples of two-tier bit-flipping embedding strategy. (a) The first numerical example. (b) The second numerical example.
3.2. Data Extraction and Image Recovering
Despite the recipients receiving their stego images, they are incapable of discerning any information about the secret data. Only when mutual trust is established between the two recipients, they can extract the secret segments accurately and recover the original grayscale image losslessly. In this section, it is assumed that the two recipients and have established mutual trust. The process of data extraction and image recovery is as follows:
Step 1: Read pixels from the corresponding positions of the two stego images and to form pixel pairs .
Step 2: Extract two secret segments from each stego pixel pair and retrieve the original pixel pair.
Step 2.1: Extract the second secret segment from the stego pixel pair and retrieve the updated pixel pair .
Step 2.2: Extract the first secret segment from the updated pixel pair and retrieve the original pixel pair .
Step 3: Repeat Step 2 until all pixel pairs have been processed.
Step 4: Concatenate all the extracted secret segments to obtain the secret data.
Step 5: Backfill the original pixel pairs into their corresponding positions to generate two cover images and .
Step 6: Choose one of the cover images to serve as the original grayscale image .
The rules of data extraction and image recovery are provided in Algorithms 3 and 4, respectively. Essentially, the data extraction and image recovery are the inverse process of data embedding. Therefore, we initially extract the secret segments and retrieve the pixel pair from the second tier, followed by the first tier. In the second tier, we begin by evaluating the patten of , , , and to determine the flipped bits within , , and , as illustrated in Figure 5a. Note that indicates the state of the 7-th bits before the second-tier embedding. After confirming the pattern, we extract the embedded secret segment , reflip the flipped bits, and set to the value of . These steps lead to the updated pixel pair . In the first-tier, we extract the embedded secret segment and reflip the flipped bits of , , and to obtain the original pixel pair , as shown in Figure 5b. After processing all pixel pairs, the resulting stego pixel pairs are backfilled into their corresponding positions, thus generating the cover images and . Finally, the secret segments are concatenated to form secret data and one of the cover images and are used as the original cover image .
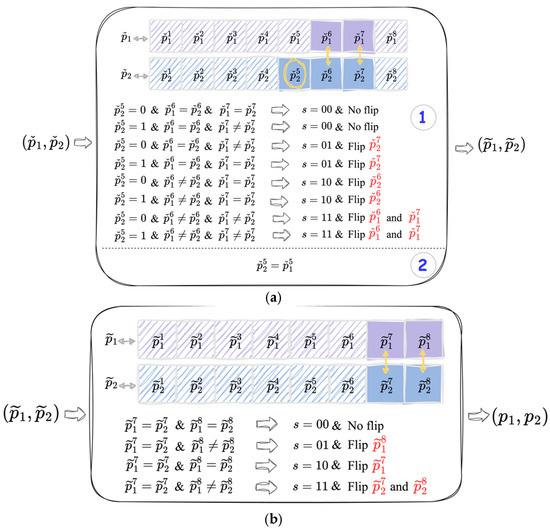
Figure 5.
Schematic of the data extraction and image recovering. (a) The second-tier, where “1” and “2” are two distinct steps. (b) The first-tier.
It is important to emphasize that neither recipient can independently extract the secret data or recover the original image. Both recipients must collaborate and share their stego images and to accurately retrieve the embedded secret segments and restore the original pixel pairs. Additionally, any attempt by either recipient to alter the pixel values within their respective stego images will lead to failures of the data extraction and image recovery processes. This interdependent mechanism significantly enhances the reliability and security of our method, ensuring that the embedded secret data remain protected and the original image can only be accurately recovered through the cooperation and mutual trust of both recipients (see Algorithms 3 and 4).
| Algorithm 3: The second-tier secret data extraction and pixel pair retrieve. | |
| Input: | Stego pixel pair . |
| Output: | Updated pixel pair and the second secret segments . |
| 1: | If ( || ( |
| 2: | . |
| 3: | |
| 4: | Else if ( || ( |
| 5: | . |
| 6: | |
| 7: | Else if ( || ( |
| 8: | . |
| 9: | |
| 10: | Else if ( || |
| 11: | . |
| 12: | |
| 13: | End |
| Algorithm 4: The first-tier secret data extraction and pixel pair retrieve. | |
| Input: | Updated pixel pair . |
| Output: | Original pixel pair and the first secret segments . |
| 1: | If |
| 2: | . |
| 3: | |
| 4: | Else if |
| 5: | . |
| 6: | |
| 7: | Else if |
| 8: | . |
| 9: | |
| 10: | Else if |
| 11: | . |
| 12: | |
| 13: | End |
To illustrate the process of the data extraction and image recovery, we present two examples in Figure 6. In Figure 6a, we extract the secret segments and retrieve original pixel pair from the given pixel pair . Due to , and , we extract the secret segment “10” and flip . Subsequently, we set to the value of . Through these steps, we obtain the updated pixel pair . Based on and , we then extract the secret segment “01” and flip and generate the original pixel pair . For the pixel pair in Figure 6b, we first extract the secret segment “11”, flip and , and set to the value of . After these procedures, we obtain the updated pixel pair . Based on and , we extract the secret segment “10” and flip and generate the original pixel pair .
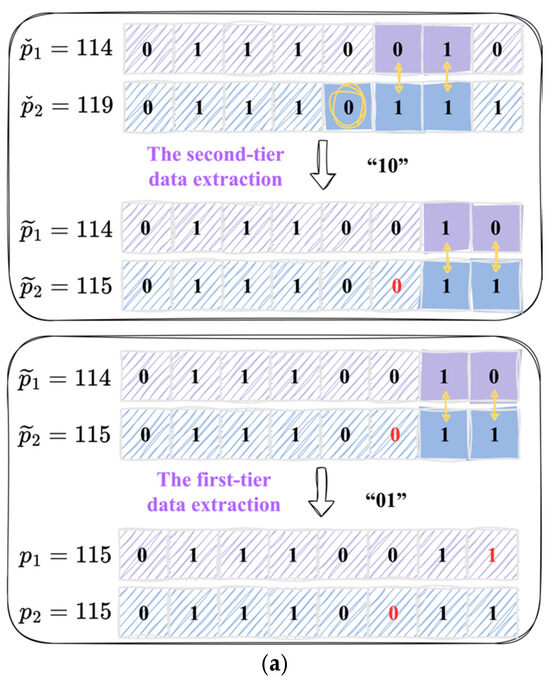
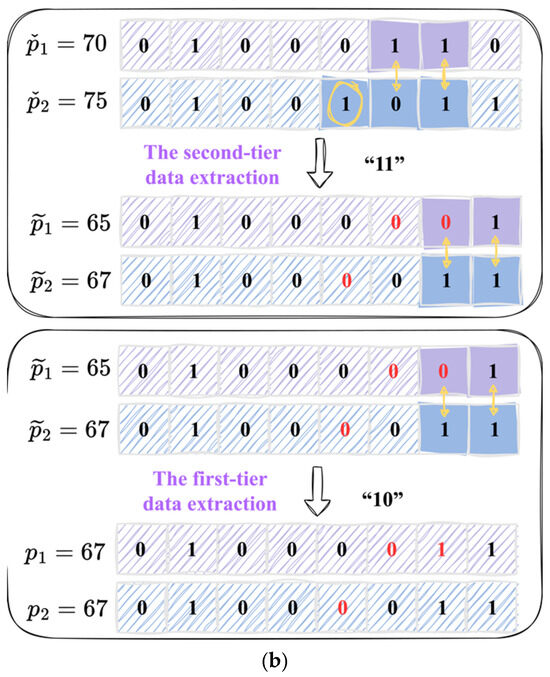
Figure 6.
Two numerical examples of the data extraction and image recovering. (a) The first numerical example. (b) The second numerical example.
3.3. Distortion Discussion
In essence, our approach accomplishes data embedding by flipping the 6th, 7th, and 8th bits of the pixel pairs obtained from the cover images and . In our embedding strategy, we assume a uniform distribution of 0s and 1s in the secret data, implying that the probabilities of our secret segments being “00”, “01”, “10”, and “11” are equal. For our method, the maximum distortion for the pixel is 7 occurring when “01” is embedded in the first tier, followed by the embedding of “11” in the second tier with non-canceling flips. In this case, the distortion for is 0. Additionally, the maximum distortion for is 15, happening when “11” is embedded for the first time, followed by “10”, and the flips are non-canceling. In this case, the distortion for is 0. Except for the above two cases, the embedding flips result in minor distortions. Therefore, we believe that our approach will result in an acceptable level of distortion. Moreover, we suggest re-evaluating the flipping strategy in cases which the distributions of 0s and 1s of the secret data are not equally distributed with one value occurring more frequently. This redesign is intended to further optimize the impact of bit-flipping on image quality.
4. Experimental Results
To evaluate the proposed method, we conducted an extensive set of experiments. Firstly, we assessed the visual effectiveness of the proposed approach. Secondly, we discussed the data payload. Furthermore, we performed a security analysis. Lastly, we provided comparisons with several state-of-the-art schemes to demonstrate the advantages of our proposed approach.
In our experiments, we selected four images from the “UCID” [33] dataset, as illustrated in Figure 7, to showcase the outcomes. Additionally, we employed the “Kodak” [34] dataset for a general evaluation. Finally, we used four classic grayscale images for performance comparisons. The sizes of all test images used in the experiment were adjusted to grayscale images. Moreover, to comprehensively illustrate the performance of the proposed scheme, we also evaluated the performance of the one-tier bit-flipping strategy in our experiments, which refers to a method without the second-tier embedding.

Figure 7.
The four test images selected from the datasets “UCID”. (a) Toys, (b) Lego, (c) Sahara, and (d) Snoopy.
4.1. Visual Effectiveness
To showcase the visual quality of the stego images, we present the results obtained by applying one-tier bit-flipping and two-tier bit-flipping strategies to the test images in Figure 8 and Figure 9, respectively. From a visual perspective, both stego images and stego images cannot be distinguished from the original image.

Figure 8.
The stego images for the test images in Figure 7 with full data payload. (a–d) obtained by one-tier bit-flipping strategy. (e–h) obtained by two-tier bit-flipping strategy.

Figure 9.
The stego images for the test images in Figure 7 with full data payload. (a–d) obtained by one-tier bit-flipping strategy. (e–h) obtained by two-tier bit-flipping strategy.
In addition to visual observation, we also quantified the visual quality using the Peak Signal-to-Noise Ratio (PSNR) [35] and Structural Similarity Index (SSIM) [36]. The corresponding results are provided in Figure 8 and Figure 9. Observing Figure 8, when employing the one-tier bit-flipping strategy, the PSNR values of the stego images exceed 47 dB, and the SSIM values surpass 0.997. With the two-tier bit-flipping strategy, the PSNR values remain above 46 dB, and the SSIM values exceed 0.997. Our findings indicate that the introduction of the second-tier embedding does not significantly degrade the image quality of the stego images . When examining Figure 9 for stego images , one-tier bit-flipping strategy yields the PSNR values exceeding 47 dB, and SSIM values exceeding 0.997. However, the PSNR values dropped to approximately 32.7 dB, and the SSIM values are about 0.95 with the two-tier bit-flipping strategy. Clearly, there are noticeable numerical decreases but they remain acceptable. We applied both one-tier and two-tier bit-flipping strategies to 24 images from the “Kodak” dataset for a general evaluation. The PSNR and SSIM results are presented in Figure 10 and Figure 11, respectively. The outcomes indicate that the proposed method maintains stable PSNR and SSIM values within an acceptable range, demonstrating its reliability.
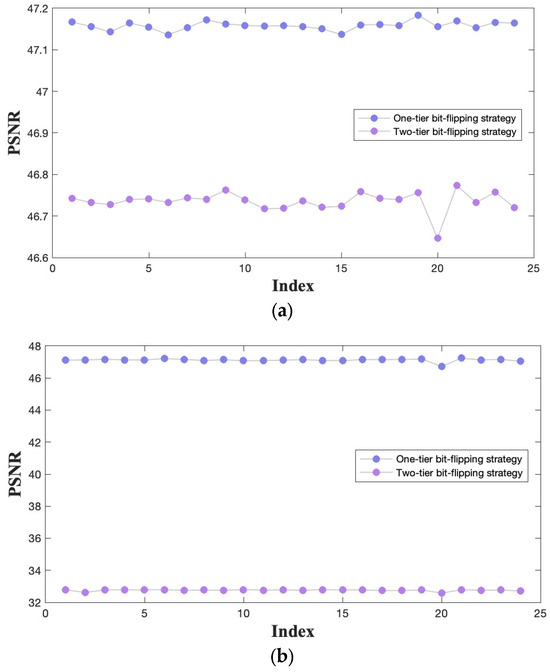
Figure 10.
The PSNR results for images from the “Kodak” dataset. (a) Stego images . (b) Stego images .
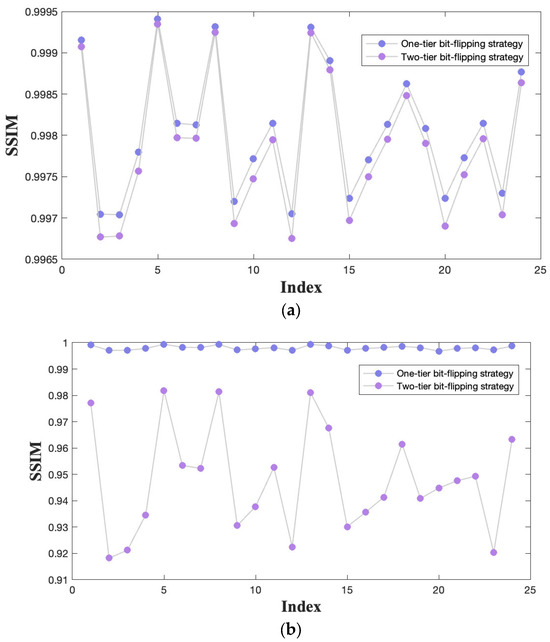
Figure 11.
The SSIM results for images from the “Kodak” dataset. (a) Stego images . (b) Stego images .
4.2. Data Payload
To evaluate the data payload of our proposed scheme, we quantify it in terms of embedding rate (ER) measured in bits per pixel (bpp). Our method involves duplicating a grayscale image into two cover images to embed secret data. Each pixel pair can hold 4 bits of secret data, resulting in an average data payload of 2 bits per pixel. Importantly, this data payload remains consistent across all tested images, regardless of their complexity, demonstrating the adaptability of our method to various image scenarios. However, such a large data payload may not always be necessary in practical applications. Therefore, we suggest opting for the one-tier bit-flipping strategy in such scenarios, which achieves a data payload of 1 bpp.
4.3. Security Analysis
We also discussed the security aspects of the proposed method, focusing on the imperceptibility of stego images. We first employ the histogram to measure pixel changes. The results are provided in Figure 12. From the results, it can be observed that after the first-tier embedding, the histograms exhibit negligible changes, indicating that the first layer of embedding has minimal impact on the images. After the second-tier embedding, there are noticeable changes in the histograms, but these changes remain within acceptable limits. In addition, we introduced image entropy [37] as a crucial metric. The results are provided in Table 1. From the data, it can be observed that when employing the one-tier bit-flipping strategy, the image entropy of both stego images and closely aligns with that of the original grayscale image. With the two-tier bit-flipping strategy, stego images maintains high similarity to the original grayscale images in terms of image entropy, stego images exhibit slightly different, albeit minimal. The close numerical proximity suggests that the embedded secret data have not significantly impacted the original image, thus demonstrating the imperceptibility of the stego images. Furthermore, we illustrate the general entropy distribution results in Figure 13, where the medians of the five violin plots closely align, indicating similarity in data distribution among these images.
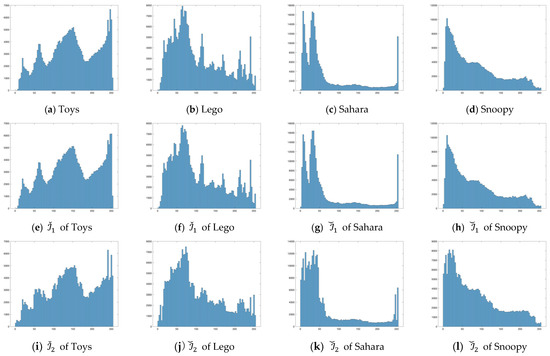
Figure 12.
The histograms for test images in Figure 7 and the corresponding stego images. (a–d) shows the histograms of the four original images in in Figure 7. (e–h) show the histograms of the corresponding stego images , respectively. (i–l) show the histograms of the corresponding stego images , respectively.

Table 1.
Information entropy of images at different stages.
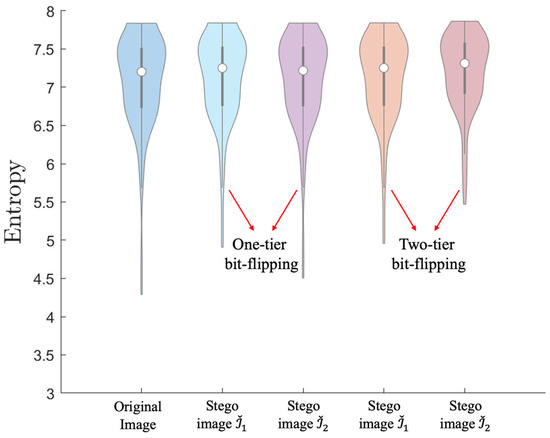
Figure 13.
The distribution of image entropy for images from the “Kodak” dataset.
4.4. Time Efficiency Analysis
To evaluate the performance of our proposed method, we conducted a time efficiency analysis using various test images. The analysis focused on two primary processes: data embedding and data extraction with image recovery. The results are presented in Table 2. The results demonstrate a reasonable time efficiency for both data embedding and extraction processes, making the proposed scheme suitable for practical applications requiring efficient data hiding and retrieval without significant delay.

Table 2.
Time efficiency of test images.
4.5. Comparisons
To showcase the effectiveness of our approach, we compared the proposed method with existing methodologies [22,23,24,25,26,27]. In our comparison, we selected four classic grayscale images, “Lena”, “Peppers”, “Barbara”, and “Goldhill” as test images. The comparison results are provided in Table 3. Upon examining Table 3, we observed that our proposed method achieved a significantly higher embedding rate (ER) across all test images compared to existing methods. Although some of the PSNR and SSIM values are slightly lower than those of other methods, the visual quality remains within an acceptable range. This demonstrates that our method effectively balances a high embedding capacity with reasonable visual quality.

Table 3.
Comparisons with the existing methods and our proposed method.
5. Conclusions
In this paper, we utilize a two-tier embedding strategy to embed secret data. Specifically, we perform specific bit flips on paired pixels in dual images to embed the secret data. The resulting images are then distributed to two different recipients. Extraction of the embedded secret data requires recipients to establish mutual trust. Experimental results demonstrate that our method achieves a data payload of 2 bits per pixel. Additionally, we have evaluated the visual fidelity of the stego images against four classic grayscale images, ‘Lena’, ‘Peppers’, ‘Barbara’, and ‘Goldhill’. achieves an average PSNR exceeding 46 dB and SSIM greater than 0.99, while averages above 32 dB and SSIM values surpassing 0.94. This capability is crucial for applications requiring efficient data transmission without perceptible degradation in image quality. In our future work, we plan to explore further enhancements in the visual quality of stego images while maintaining a high data payload.
Author Contributions
Conceptualization, C.-C.C. (Chin-Chen Chang) and C.-C.C. (Ching-Chun Chang); methodology, C.-C.C. (Chin-Chen Chang) and C.-C.C. (Ching-Chun Chang); software, S.X.; validation, S.X.; formal analysis, S.X.; investigation, S.X.; resources, C.-C.C. (Chin-Chen Chang); data curation, S.X.; writing—original draft preparation, S.X.; writing—review and editing, J.-C.L., C.-C.C. (Chin-Chen Chang) and C.-C.C. (Ching-Chun Chang); visualization, S.X. and J.-C.L.; supervision, C.-C.C. (Chin-Chen Chang); project administration, C.-C.C. (Chin-Chen Chang) and C.-C.C. (Ching-Chun Chang); funding acquisition, C.-C.C. (Chin-Chen Chang). All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Bender, W.; Gruhl, D.; Morimoto, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Chang, C.; Lin, M.; Hu, Y. A fast and secure image hiding scheme based on LSB substitution. Int. J. Pattern Recognit. Artif. Intell. 2002, 16, 399–416. [Google Scholar] [CrossRef]
- Chan, C.; Cheng, L. Hiding data in images by simple LSB substitution. Pattern Recognit. 2004, 37, 469–474. [Google Scholar] [CrossRef]
- Yang, C. Inverted pattern approach to improve image quality of information hiding by LSB substitution. Pattern Recognit. 2008, 41, 2674–2683. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, W.; Zhao, Z.; Wang, E. PVO-based reversible data hiding using bit plane segmentation and pixel expansion. J. Inf. Secur. Appl. 2023, 79, 103649. [Google Scholar] [CrossRef]
- Chen, Y.; Sun, W.; Li, L.; Chang, C.; Wang, X. An efficient general data hiding scheme based on image interpolation. J. Inf. Secur. Appl. 2020, 54, 102584. [Google Scholar] [CrossRef]
- Kim, H.; Sachnev, V.; Shi, Y.; Nam, J.; Choo, H. A novel difference expansion transform for reversible data embedding. IEEE Trans. Inf. Forensics Secur. 2008, 3, 456–465. [Google Scholar]
- Dragoi, I.; Coltuc, D. Local-prediction-based difference expansion reversible watermarking. IEEE Trans. Image Process. 2014, 23, 1779–1790. [Google Scholar] [CrossRef]
- Coatrieux, G.; Pan, W.; Cuppens-Boulahia, N.; Cuppens, F.; Roux, C. Reversible watermarking based on invariant image classification and dynamic histogram shifting. IEEE Trans. Inf. Forensics Secur. 2012, 8, 111–120. [Google Scholar] [CrossRef]
- Li, X.; Li, B.; Yang, B.; Zeng, T. General framework to histogram-shifting-based reversible data hiding. IEEE Trans. Image Process. 2013, 22, 2181–2191. [Google Scholar] [CrossRef] [PubMed]
- Peng, F.; Li, X.; Yang, B. Improved PVO-based reversible data hiding. Digit. Signal Process. 2014, 25, 255–265. [Google Scholar] [CrossRef]
- Qu, X.; Kim, H. Pixel-based pixel value ordering predictor for high-fidelity reversible data hiding. Signal Process. 2015, 111, 249–260. [Google Scholar] [CrossRef]
- Akhtarkavan, E.; Majidi, B.; Salleh, M.; Patra, J. Fragile high-capacity data hiding in digital images using integer-to-integer DWT and lattice vector quantization. Multimed. Tools Appl. 2020, 79, 13427–13447. [Google Scholar] [CrossRef]
- Thanki, R.; Borra, S. A color image steganography in hybrid FRT–DWT domain. J. Inf. Secur. Appl. 2018, 40, 92–102. [Google Scholar] [CrossRef]
- Wang, X.; Chang, C.; Lin, C.; Chang, C. Privacy-preserving reversible data hiding based on quad-tree block encoding and integer wavelet transform. J. Vis. Commun. Image Represent. 2021, 79, 103203. [Google Scholar] [CrossRef]
- Meng, L.; Liu, L.; Wang, X.; Tian, G. Reversible data hiding in encrypted images based on IWT and chaotic system. Multimed. Tools Appl. 2022, 81, 16833–16861. [Google Scholar] [CrossRef]
- Xiao, M.; Li, X.; Ma, B.; Zhang, X.; Zhao, Y. Efficient reversible data hiding for JPEG images with multiple histograms modification. IEEE Trans. Circuits Syst. Video Technol. 2020, 31, 2535–2546. [Google Scholar] [CrossRef]
- Weng, S.; Zhou, Y.; Zhang, T.; Xiao, M.; Zhao, Y. General framework to reversible data hiding for JPEG images with multiple two-dimensional histograms. IEEE Trans. Multimed. 2022, 25, 5747–5762. [Google Scholar] [CrossRef]
- Zhang, X.; Pan, Z.; Zhou, Q.; Fan, G.; Dong, J. A reversible data hiding method based on bitmap prediction for AMBTC compressed hyperspectral images. J. Inf. Secur. Appl. 2024, 81, 103697. [Google Scholar] [CrossRef]
- Lin, J.; Lin, C.C.; Chang, C.C. Reversible steganographic scheme for AMBTC-compressed image based on (7, 4) hamming code. Symmetry 2019, 11, 1236. [Google Scholar] [CrossRef]
- Wang, X.; Liu, J.C.; Chang, C.C. A novel reversible data hiding scheme for VQ codebooks. Secur. Priv. 2023, 6, e315. [Google Scholar] [CrossRef]
- Xu, S.; Horng, J.; Chang, C.; Chang, C. Reversible data hiding with hierarchical block variable length coding for cloud security. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4199–4213. [Google Scholar] [CrossRef]
- Yao, Y.; Wang, K.; Chang, Q.; Weng, S. Reversible data hiding in encrypted images using global compression of zero-valued high bit-planes and block rearrangement. IEEE Trans. Multimed. 2023, 26, 3701–3714. [Google Scholar] [CrossRef]
- Zhang, Q.; Chen, K. Reversible data hiding in encrypted images based on two-round image interpolation. Mathematics 2023, 12, 32. [Google Scholar] [CrossRef]
- Qin, C.; Chang, C.; Hsu, T. Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimed. Tools Appl. 2015, 74, 5861–5872. [Google Scholar] [CrossRef]
- Lu, T.; Wu, J.; Huang, C. Dual-image-based reversible data hiding method using center folding strategy. Signal Process. 2015, 115, 195–213. [Google Scholar] [CrossRef]
- Yao, H.; Qin, C.; Tang, Z.; Tian, Y. Improved dual-image reversible data hiding method using the selection strategy of shiftable pixels’ coordinates with minimum distortion. Signal Process. 2017, 135, 26–35. [Google Scholar] [CrossRef]
- Jana, B.; Giri, D.; Mondal, S. Dual image based reversible data hiding scheme using (7,4) hamming code. Multimed. Tools Appl. 2018, 77, 763–785. [Google Scholar] [CrossRef]
- Chen, X.; Hong, C. An efficient dual-image reversible data hiding scheme based on exploiting modification direction. J. Inf. Secur. Appl. 2021, 58, 102702. [Google Scholar] [CrossRef]
- Kim, C.; Yang, C.; Zhou, Z.; Jung, K. Dual efficient reversible data hiding using Hamming code and OPAP. J. Inf. Secur. Appl. 2023, 76, 103544. [Google Scholar] [CrossRef]
- Kim, C.; Yang, C.N. Self-embedding fragile watermarking scheme to detect image tampering using AMBTC and OPAP approaches. Appl. Sci. 2023, 11, 1146. [Google Scholar] [CrossRef]
- Schaefer, G.; Stich, M. UCID: An uncompressed color image database. In Storage and Retrieval Methods and Applications for Multimedia; SPIE Proceedings: San Jose, CA, USA, 2004; pp. 472–480. [Google Scholar]
- Kodak, E. Kodak Lossless True Color Image Suite (Photocd Pcd0992). Volume 6. Available online: http://r0k.us/graphics/kodak (accessed on 15 November 1999).
- Smith, S. Digital Signal Processing: A Practical Guide for Engineers and Scientists; Newnes: San Francisco, CA, USA, 2003; ISBN 9780750674447. [Google Scholar]
- Lowe, D. Distinctive image features from scale-invariant key points. Int. J. Comput. Vis. 2004, 60, 91–110. [Google Scholar] [CrossRef]
- Tsai, D.Y.; Lee, Y.; Matsuyama, E. Information entropy measure for evaluation of image quality. J. Digit. Imaging 2008, 21, 338–347. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).