Abstract
The security of passwords generated by the graphic lattices is based on the difficulty of the graph isomorphism, graceful tree conjecture, and total coloring conjecture. A graphic lattice is generated by a graphic base and graphical operations, where a graphic base is a group of disjointed, connected graphs holding linearly independent properties. We study the existence of graphic bases with odd-graceful total colorings and show graphic lattices by vertex-overlapping and edge-joining operations; we prove that these graphic lattices are closed to the odd-graceful total coloring.
1. Introduction and Preliminary
1.1. Introduction
Considering current text passwords, once the password file is leaked, most of the plaintext passwords can be quickly deciphered using current cracking techniques, and personal privacy and property will face serious losses. Topological authentication is a new technique based on topological coding, a mixed branch of discrete mathematics, number theory, algebraic group, graph theory, and so on. This technology is more and more widely used in real life; for example, the user identity authentication of the smart-phone adopts a graphic password [1,2]. Johnson et al. proposed a picture signature password to determine access to computing devices or services [3]. Wang et al. [4] designed a topological code consisting of a topological structure and graph colorings. According to the order of vertex-edge-vertex, Yao et al. [5] arranged the labels or colors of each edge and two end-vertices of a graph G, with p vertices, and q edges in a topological matrix of order ; that is
where f represents a function to obtain the colors of the vertices and edges. The topological matrix of G can derive number strings that can be used as digital-based passwords, and the preset coloring f can be needed during authentication, called topological authentication. It is feasible to generate passwords by topological coding, because its deciphering process involves NP-hard problems, for instance, the graph isomorphism problem and the graceful tree conjecture. Tian et al. [6] proved that the passwords generated by the labeling of a graph can resist brute force attacks, dictionary attacks, guessing attacks, reproduction attack, and denial of service attacks.
The lattice-based cryptosystem is based on NP-Hard or NP-C problems [7,8], which makes lattice-based cryptosystem a core research field in cryptosystems against quantum attacks. A lattice is defined as the set of all integer combinations
of n linearly independent vectors in with , where Z is the integer set, m is the dimension, and n is the rank of the lattice, and the vector group is called a lattice base. Lattice theory involves the Shortest Vector Problem [9], Shortest Independent Vector Problem, Successive Minimum Problem [10], Closet Vector Problem, and other difficult problems. The security of the lattice-based cryptology depends on the difficulty of the difficult problems in classical number theory and computational complexity theory [11], many difficult problems in the lattice have been proven to be NP-hard, so this mechanism is generally considered to be resistant to the attacks from quantum computers when it is used in cryptanalysis and design.
Inspired by the ability of lattice-based cryptology to resist supercomputers and quantum computers, we propose graphic lattices for the encryption of network models or complex systems. According to the method of topological coding, large-scale graphs are more reliable than small-scale graphs. Therefore, it is necessary to generate large-scale graphs from existing small-scale graphs for identification. The graphic lattice combines operations and topological coding of the graphic base to generate the topological coding of a large-scale graph [12,13]. In this paper, we extend the theoretical tool of topological coding from graph labeling to graph coloring and define a new type of coloring for building graphic lattices and providing topological coding based on new coloring.
1.2. Preliminary
The graphs described in this paper are graphs that do not contain double edges. The labeling of a graph G refers to , there is always for any pair of vertices . The coloring of the graph G means that a function , such that for some two vertices [14]. The degree of a vertex u of a -graph G is denoted as , where represents the neighbor set of the vertex u, and a vertex having degree one is called a leaf. For simplicity of description, we write , where , is a positive integer.
A graph G admits a proper total coloring if it satisfies the following conditions [15,16]. For , then
(1) for each edge ;
(2) for ;
(3) for .
The symbols used in this paper are shown in Table 1, and the other notations and terminologies not mentioned here can be found in [15,17].

Table 1.
Abbreviations.
Definition 1.
A -graph G admits a total coloring , if it satisfies
(1) Each edge is colored as ;
(2) The edge color set is ;
(3) The vertex color set is .
Then f is called a quasi-odd-graceful total coloring if (1) and (2) hold, and f is called an odd-graceful total coloring if the above three conditions are met. Furthermore, if the vertex set of the -graph G can be divided into with , so that each edge satisfies and , besides, is true, then we call f a set-ordered odd-graceful total coloring.
Several examples are shown in Figure 1 for understanding Definition 1. Similar to the definition of a lattice, we give the definition of a graphic lattice.
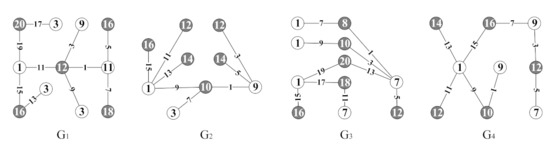
Figure 1.
Four graphs , , , admit set-ordered odd-graceful total colorings.
Definition 2.
Let be a graphic base composed of n linearly independent graphic vectors under a graphical operation “◊”, where each is a colored/uncolored graph, and is a set of colored/uncolored graphs of λ vertices and μ edges with respect to , and . We write the resulting graph obtained by performing a graphical operation ◊ on a graph H and the graphic base with , denoted as . In general, the graph set
with is called a graphic lattice, a graphic lattice base, p is the dimension and n is the rank of . Moreover, is called a linear graphic lattice if every , each of base and are forests or trees. A colored tree-graph lattice is full-rank in Equation (3).
Based on the following two graphical operations, some large-scale graphs containing odd-graceful total colorings can be obtained, which increases the cryptographic space.
Definition 3.
For two graphs, and , the two types of graphical operations related to the vertices and edges are as follows.
(1) Vertex-overlapping operation refers to overlapping a vertex u in graph with a vertex v in graph to form a new vertex w, then the neighbors of w are the union of the neighbors of u and the neighbors of v; the operation is denoted as .
(2) Edge-joining operation means adding a new edge between a vertex u in the graph and a vertex v in the graph , the operation is expressed as .
2. Graphic Lattices with Odd-Graceful Total Colorings
Lemma 1.
Each tree admits a quasi-odd-graceful total coloring.
Proof.
Let be the number of edges of a tree T, we proceed with the proof by induction on the number of edges of tree T. When , T has one edge , there is a quasi-odd graceful total coloring defined as: , and . Suppose that this lemma is true for the tree with edges, then, when , we suppose that the vertex u is a leaf of tree T and its neighbor is vertex v. Because the tree admits a quasi-odd-graceful total coloring so that the edge color set of tree is , based on this fact, we define a coloring f of tree T as follows: for , and , obviously, . Therefore, the edge color set of tree T is just , which means that f is a quasi-odd-graceful total coloring of tree T. The lemma follows induction. □
2.1. Results Based on the Vertex-Overlapping Operation
Given a graphic base with disjoint graphs , and a connected graph H with n vertices, we overlap a vertex u of graph H with a vertex of graph into a new vertex for , the resulting connected graph is called a, H-graph, denoted as .
Theorem 1.
Each of a graphic base and another connected bipartite graph H with n vertices admits a set-ordered odd-graceful total coloring for , then the H-graph is a connected bipartite graph and admits a set-ordered odd-graceful total coloring.
Proof.
The numbers of vertices and edges of the connected bipartite graph in the graphic base are and . Suppose that is the bipartition of vertex set of , where , and . According to the assumption in the theorem, each connected bipartite graph admits a set-ordered odd-graceful total coloring , so holds true, without a loss of generality, we have for , and for .
Let be the vertices of the connected bipartite graph H, and , the vertex bipartition of the graph H is denoted as , where and . Because H admits a set-ordered odd-graceful total coloring , we can get , and .
We overlap a vertex of graph H with a vertex of each graph into a new vertex to obtain a connected H-graph, and let , for , . We first define another total coloring g of the graph H as: for , for , then each edge is colored as
So the edge color set of graph H is . Next, we give each graph of the base a new total coloring.
Overlap the vertex of graph and the vertex of graph H into a vertex , and the vertex is recolored as
The other vertices of graph can be colored as
Thereby, the edge color set of graph is just .
For graph , overlapping the vertex of and the vertex of graph H into a vertex , the new color of vertex is
we also have
hence, the edge can be colored as
We get the edge color set of the graph as . Generally, we overlap the vertex of graph T and the vertex of graph H into a vertex , and recolor the vertices and edges of connected bipartite graph for , where , we have
the other vertices in the graph can be colored as
so the coloring of edge is
Thereby, we get the set as for . Based on the above coloring process, we also get an edge color set , the maximum value of colors used is
The above part has given the new total colorings of graphs , , ⋯, . Further, we recolor the graphs in the following. For each graph with , we perform the vertex-overlapping operation on the vertex of and the vertex of H, then we determine a new total coloring of , .
Recolor vertex as
and other vertices of graph as
Each edge of the graph is recolored as
Therefore, the edge color set is
We recolor the vertex as
and recolor other vertices in the graph as
Obviously, we get the edge color set . In general, for , we have
We color each edge of graph as
thus, we get the edge color set of the graph ,
.
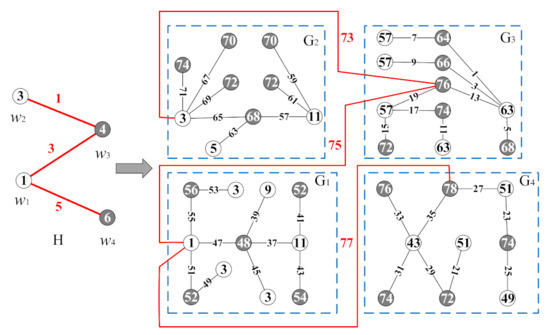
By recoloring the graph H and the graphs in the graphic base , we obtain the vertex color set of H-graph to be , the edge color set of the H-graph to be . Thereby, we claim that g is a set-ordered odd-graceful total coloring of graph . An example of the proof process of Theorem 1 is shown in Figure 2.

Figure 2.
An example for illustrating the proof of Theorem 2.
□
2.2. Results Based on the Edge-Joining Operation
We divide the graphs obtained by edge operation into two categories according to the number of newly added edges between the graphs and in the graphic base , where and .
2.2.1. Single-Series Graphs
A single-series graph is obtained by connecting a vertex of the graph and a vertex of the graph with a new edge for , abbreviated as , contains all of the newly added edges.
Theorem 2.
Each in a graphic base is a connected bipartite graph and admits a set-ordered odd-graceful total coloring; then a single-series graph admits a set-ordered odd-graceful total coloring.
Proof.
Suppose that is the bipartition of vertex set of connected bipartite graph in the graphic base , where , and , . Since graph admits a set-ordered odd-graceful total coloring , the colors of all of the vertices can be arranged as . The edge color set of graph under coloring is
Let and , we define another total coloring g of graph as follows: for , for . Generally, when , we have for .
Recolor vertex in the graph as
then the color of edge is
the edge color set of graph is . Then, we recolor vertex in the graph as
then the coloring of edge in the graph can be expressed as
hence the edge color set of graph is .
When , we recolor the vertex as
and color the edge by
We can calculate that the edge color set of each graph for as
Combining the following two equations
we can get , and the condition , then we have
For , we connect two vertices and with a new edge to obtain a connected single-series graph , the set means . We can obtain the following color set under total coloring g,
By the above deduction, the color set of the single-series graph is
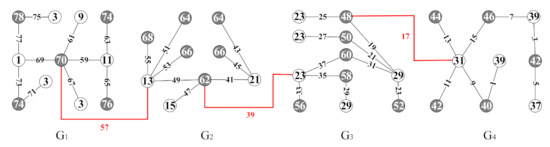
where . We let and , then is the vertex set bipartition of , in conclusion, g is a set-ordered odd-graceful total coloring of the single-series graph . An example of the proof process of Theorem 2 is shown in Figure 3.

Figure 3.
A single-series graph, made by the four graphs shown in Figure 1, admits a set-ordered odd-graceful total coloring.
□
2.2.2. Multiple-Series Graphs
There is only one edge between two adjacent graphs and in the single-series graph for . However, when the number of new edges between two graphs and is not equal to 1, but new edges, the resulting graph is called a multiple-series graph, represents the edge set of between and in graphic base .
Theorem 3.
Each in a graphic base admits a set-ordered odd-graceful total coloring, then the multiple-series graph admits a set-ordered odd-graceful total coloring.
Proof.
According to the assumptions in the theorem, the connected bipartite graph admits a set-ordered odd-graceful total coloring , we suppose that is the bipartition of the vertex set of the connected bipartite graph , where , and , . Arrange the colors of all vertices as follows
then the edge color set of graph is
The multiple-series graph is generated by iterations. First of all, we define another total coloring for the two graphs and in graphic base . Let represents the number of new edges added between and . We have for , and for , also for , and for ; therefore, the edge color set in the connected graph is , the coloring of the edge can be further calculated as , then , we can get Moreover, we have
and . In addition,
For , we get the following inequality from the above derivation,
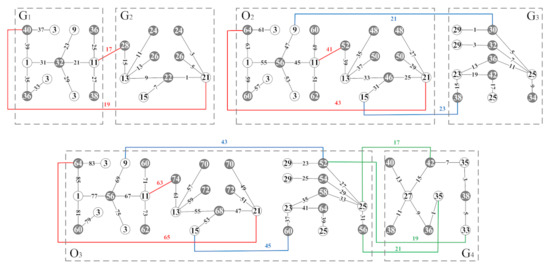
Obviously, is the vertex bipartition of the connected graph , where and . The edge or satisfies the above inequality conditions form a set , so that , we claim that is a set-ordered odd-graceful total coloring of . Next, let , then consider the total coloring of connected graph and graph . According to the above method, the edge set can be obtained, which is the set of all edges between and ; thereby, we can obtain a set-ordered odd-graceful total coloring of , in this way, the theorem is proven. An example of the proof process of Theorem 3 is shown in Figure 4.

Figure 4.
An example for illustrating the proof of Theorem 3.
□
3. Conclusions
This paper studies the existence of graphic bases with odd-graceful total colorings and shows graphic lattices by vertex-overlapping operations and edge-joining operations; further, we prove that these graphic lattices are closed to the odd-graceful total coloring. If the password generated by the graphic lattices is used to encrypt important information, then the problem of determining the graph isomorphism and some coloring conjectures will be involved in the process of decryption, so it is not easy to crack it, in addition, it has the characteristics of diverse and simple generation methods.
The theoretical research of graphic lattice and its corresponding key design has great practical significance, the topological authentication generated by combining the topological structure of graph with labeling or a coloring can be used to obtain honeywords [6], and can be used in fields, such as cryptographic design [18], topological coding [19] and network information security [20,21]. Our future work will further promote the concept of the graphic lattices, not limited to odd-graceful total coloring, but combines the topological structure of the graph with different new colorings or new labelings, and uses the graphic lattices to generate more authentication passwords.
Author Contributions
Created and conceptualized the idea, B.Y. and J.S.; writing—original draft preparation, J.S. and H.S.; writing—review and editing, J.S. and B.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Key Research and Development Plan under Grant No. 2019YFA0706401 and the National Natural Science Foundation of China under Grants No. 61632002, No. 61872166, No. 61662066 and the National Natural Science Foundation of China Youth Project under Grants No. 61902005, No. 62002002.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ming, J.; Ai, H.; Wang, K.Y.; Le, Z.Y. Two-way graphic password for mobile user authentication. IEEE Int. Conf. Cyber Secur. Cloud Comput. 2016, 476–481. [Google Scholar] [CrossRef]
- Shen, S.S.; Chang, C.T.; Lin, S.H.; Chien, W. The Enhanced Graphic Pattern Authentication Scheme Via Handwriting identification. In Proceedings of the 2019 IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 3–6 October 2019; pp. 150–153. [Google Scholar] [CrossRef]
- Johnson, J.J.; Seixeiro, S.; Pace, Z.; van der Bogert, G.; Gilmour, S.; Siebens, L.; Tubbs, K. Picture Gesture Authentication. U.S. Patent 8,650,636, 9 December 2014. [Google Scholar]
- Wang, H.Y.; Xu, J.; Ma, M.Y.; Zhang, H. A new type of graphical passwords based on odd-elegant labelled graphs. Secur. Commun. Netw. 2018, 2018, 1–11. [Google Scholar] [CrossRef] [Green Version]
- Yao, B.; Zhao, M.; Zhang, X.; Mu, Y.; Sun, Y.; Zhang, M.; Yang, S.; Ma, F.; Su, J.; Wang, H.; et al. Topological coding and topological matrices toward network overall security. arXiv 2019, arXiv:190901587. [Google Scholar]
- Tian, Y.Z.; Li, L.X.; Peng, H.P. Achieving flatness: Graph labeling can generate graphical honeywords. Comput. Secur. 2021, 104, 102212. [Google Scholar] [CrossRef]
- Micciancio, D.; Regev, O. Lattice-based cryptography. In Post-Quanturn Cryptography; Bernstein, D.J., Buchmann, J., Dahmen, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 147–191. [Google Scholar]
- Wang, X.Y.; Liu, M.J. Survey of lattice-based cryptography. J. Cryptologic Res. 2014, 1, 13–27. [Google Scholar]
- Khot, S. Hardness of approximating the shortest vector problem in lattices. J. Comput. Syst. sci. 2006, 72, 206–219. [Google Scholar] [CrossRef] [Green Version]
- Blömer, J. Closest vectors, successive minima, and dual HKZ-bases of lattices. In International Colloquium on Automata, Languages & Programming; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1853, pp. 248–259. [Google Scholar] [CrossRef]
- Schneider, M. Analysis of Gauss-Sieve for Solving the Shortest Vector Problem in Lattices; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; pp. 89–97. [Google Scholar]
- Yao, B.; Wang, H.Y.; Su, J.; Sun, H. Graphic lattices for constructing high-quality networks. In Proceedings of the IEEE 5th Information Technology and Mechatronics Engineering Conference, Chongqing, China, 12–14 June 2020; pp. 1726–1730. [Google Scholar] [CrossRef]
- Yao, B. Graphic lattices and matrix lattices of topological coding. arXiv 2020, arXiv:2005.03937. [Google Scholar]
- Sánchez-Arroyo, A. Determining the total coloring number is NP-hard. Discret. Math. 1989, 78, 315–319. [Google Scholar]
- Bondy, J.A.; Murty, U.S.R. Graph Theory with Application; Elsevier Science Publishing Co., Inc.: Amsterdam, The Netherlands, 1976. [Google Scholar]
- Bollobás, B. The Modern Graph Theory; Springer: Berlin, Germany, 1998. [Google Scholar]
- Gallian, J.A. A Dynamic Survey of Graph Labeling. Electron. J. Comb. 2016, 19, 1–418. [Google Scholar]
- Lavanya, S.; Saravanakumar, N.M.; Vijayakumar, V.; Thilagam, S. Secured key management scheme for multicast network using graphical password. Mob. Netw. Appl. 2019, 24, 1152–1159. [Google Scholar] [CrossRef]
- Singh, U.P.; Chouhan, S.S.; Jain., S. Images as graphical password: Verification and analysis using non-regular low-density parity check coding. Int. J. Inf. Technol. 2020, 1–41. [Google Scholar] [CrossRef]
- Mu, Y.R.; Yao, B. Exploring topological graph passwords of information security by chinese culture. In Proceedings of the IEEE 3rd Advanced Information Technology, Elextronic and Automation Control Conference, Chongqing, China, 12–14 October 2018; pp. 1648–1652. [Google Scholar] [CrossRef]
- Su, J.; Sun, H.; Wang, H.Y.; Yao, B. Topological public-key cryptography based on graph image-labellings for information security. In Proceedings of the IEEE International Conference on Information Technology, Big Data and Artificial Intelligence, Chongqing, China, 6–8 November 2020; pp. 366–370. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).