Abstract
A wide range of recent studies are focusing on current issues of financial fraud, especially concerning cybercrimes. The reason behind this is even with improved security, a great amount of money loss occurs every year due to credit card fraud. In recent days, ATM fraud has decreased, while credit card fraud has increased. This study examines articles from five foremost databases. The literature review is designed using extraction by database, keywords, year, articles, authors, and performance measures based on data used in previous research, future research directions and purpose of the article. This study identifies the crucial gaps which ultimately allow research opportunities in this fraud detection process by utilizing knowledge from the machine learning domain. Our findings prove that this research area has become most dominant in the last ten years. We accessed both supervised and unsupervised machine learning techniques to detect cybercrime and management techniques which provide evidence for the effectiveness of machine learning techniques to control cybercrime in the credit card industry. Results indicated that there is room for further research to obtain better results than existing ones on the basis of both quantitative and qualitative research analysis.
Keywords:
algorithms; credit card; database; fraud; financial organization; machine learning; dataset 1. Introduction
Online services are more common in the new age. A major contributor of online services is in the banking industry, where services are shifting more towards digital banking. Digital banking provides an ease to the customer to transfer funds, online shopping and many other activities [1]. This digitization is not only fruit for the customer but banks are also facilitated with this change [2]. Cybercrime became more common and severe due to transfer of manual work into digital. Cyber security is now capturing more attention both in industry and research. Cyber-criminal activities are increasing at fast speeds and becoming more sophisticated. This paper is designed to present a systematic literature review of machine learning techniques and analysis techniques in management science to lower cybercrime. Cybercrime is a major challenge to many financial organizations. The impacts of cybercrime are dangerous to an organization’s assets [3]. Cybercrime raised globally by 50% from 2018 to 2020 which is equal to an amount of under USD 1 trillion [4].
Fraud is an act of obtaining financial benefits or services illegally by wrong or criminal deception. Credit card fraud is the unauthorized way of performing transactions without the approval of a card’s owner. There are many types of credit card fraud, such as application fraud and merchant fraud. Credit card fraud can be categorized in a number of ways, as bankruptcy, theft or stolen cards, counterfeit fraud and application fraud as said by [5]. Online financial fraud has gained prominence in the past few years to comply with the growing electronic commerce economy. A lot of fraud prevention strategies have been designed to prevent this offence and yet the statistics provided by global fraud reports suggest that more research is needed in the area of credit card fraud.
Moreover, financial crimes are increasing every day and no organization is immune from being victims of fraudsters [6]. Financial organizations are under serious threat of online fraud due to an increase in the usage of electronic commerce. Credit card transactions are conducted by using cards physically, mostly at point of sale, and by internet, where digital transactions are processed with the details of a card and card holder [7]. Plastic cards are used for cashless payments to buy goods and services. Everyone can shop remotely by using credit cards from home. Banks and financial firms that deal with plastic cards should pay attention to this hot issue, which not only minimizes their revenue but is also dangerous for their reputations [8]. Electronic transactions have raised significantly due to the increase in trends of online shopping from e-businesses, such as Amazon, eBay, and Ali-baba [9].
In addition, a very innovative and interesting sub field of computers is artificial intelligence algorithms. These algorithms learn from data with little human intervention. The two major branches of machine learning are supervised and unsupervised learning. Machine learning techniques have successful application in many fields of life, such as weather prediction, computational intelligence, medical, and fraud detection. Machine learning algorithms are playing a vital role in overcoming cybercrime in the finance sector [10]. Credit card fraud detection is the best way to analyze the efficiency and effectiveness of machine learning algorithms. Many single and hybrid approaches of machine learning are applicable to the decline in credit card fraud [11].
The credit card fraud detection problem has a number of challenges, such as variation in a card holder’s spending nature, high number of genuine and low number of fraudulent transactions, which is known as class imbalance, where a small number of transactions are timely checked by investigators [12].
This research aims to perform a systematic literature review on cybercrime from the perspective of machine learning, datasets used for analysis, performance metrics and data collection methods in finance and more focused towards the credit card industry. The study reviews current research articles from five famous databases. This is the first systematic literature available on cybercrime in finance with two dimensions, one is machine learning with details of datasets and second is analysis methods and data collection techniques with performance metrics. The previous studies only focused on one dimension. This paper is helpful for the researchers as it supports categorizations and aggregation of literature which can lead to a clear way forward for future research.
2. Literature Review
Fraud is an unauthorized access to a financial account either for personal benefits or financial loss. Financial fraud has captured attention with far reaching significance in the government, corporate administrations, and financial firms. Millions of pounds are lost each year in e-commerce due to credit card fraud. For instance, global brands suffered from USD 18.30 billion loss in credit card fraud in 2015. This value increased to USD 20.18 billion in the year 2016. For cards issued in the euro area only, the total value of fraudulent card transactions amounted to €1.03 billion. Only in Europe the card frauds in 2019 were 1.03billion in European currency [13]. A vital element is to achieve maximum success against opponents by using minimum resources. The rapid increase in the rate of credit card use is one of the main reasons that increases the number of financial fraud occurrences every year. Hence after, both the client and issuer of credit card suffer from heavy loss due to credit card fraud, and this situation will become worse in coming years [14]. Fraud detection is a method of monitoring the behavior of a user in order to avoid unwanted conditions in credit card transactions. Fraud detection is not only concerned with the uncovering of such unwanted activities, but also making decisions timely and quickly to avoid damage [15,16]. Recently, many fraud detection solutions and software have emerged to prevent fraud in businesses, including credit card, retail, e-commerce, insurance, and industry.
Machine learning techniques are one of the prominent and popular approaches used to solve the problem of credit fraud detection. Authors in [17] have categorized ML techniques as supervised and unsupervised algorithms. SML algorithms require training data to build a model for the test data. These algorithms are very popular in credit card fraud detection but are difficult to implement and train. On the other hand, unsupervised learning techniques do not require training data, as these algorithms learn from input data without labeling; however, there is a problem of data storage while using unsupervised learning [10]. The third approach used by the researchers is hybrid ML algorithms. Hybrid learning, also known as blended learning, is a combination of algorithms to improve efficiency, but it is tricky to work it with advanced mining applications.
A vital part of cybercrime research in the banking sector is played by the datasets. A number of datasets are explored with deep investigation [18]. Digital services in the banking sector and cybercrime were the main catalysts of this study. Cybercrime committers are becoming smarter, so to control these crimes they should be detected efficiently and effectively in rum time. Research on the need for updated and more recent datasets was also performed [19]. The importance of datasets was also highlighted [20] by examining anomaly detection techniques. Another study focused datasets and their role with supervised machine learning algorithms to elaborate their importance in the training of algorithms [21]. Datasets were also tested on the efficiency of machine learning algorithms [22].
3. Research Gaps
The main research gaps filled by this article are summarized as follows. Firstly, this article focused not only on which machine algorithms are used by most researchers, but also the performance metrics. Secondly, the research focuses on the datasets used by previous researchers and proposes new issue for real time datasets which can be more beneficial for researchers for analysis, which will ultimately be helpful for organizations to control cybercrime.
4. Research Motivations
A vital element is to achieve maximum success against opponents by using minimal resources. Every economy is using its own tools to mitigate cybercrime in the financial sector, but the results are almost the same. It is not very important that an economy have a lot of resources, but the important factor is efficient and effective utilization of these resources against cybercrime [8]. Cybercrime in the credit card industry is growing with every sun rise. To overcome the threat on card holders and on merchants, financial organizations are trying to design automatic, efficient and user-friendly monitoring systems [5]. There is a need for satisfactory mitigation factors against cybercrime in finance [23].
Now, it is necessary to analyze new methods, trends and counter-measures in the credit card cybercrime detection era to empower the systems that are working on credit card fraud. For smoothness in remote financial transactions, to guarantee the authenticity of credit card transaction and to shield the privacy of card holders, there is a need for more investigation [24]. Machine learning techniques enable efficient cybercrime detection, primarily with real-world datasets. These techniques are helpful to capture unauthorized transactions in a timely and effective way, which will ultimately reduce the amount of loss occurring every year in financial organizations due to cybercrime [11].
Research Objectives
Based on the research motivations as we discussed above, to shed some light on applications and successes of machine learning algorithms in credit card fraud detection, we have systematically analyzed previous literature on machine learning algorithms in cybercrime detection in the area of finance. The aim of this study is to provide the latest knowledge for financial organizations. The research work in this article will be helpful for developers and organizations to design and implement more efficient and effective monitoring tools for cybercrime detection in the credit card industry.
The call of articles by some high impact journals is evidence for the need of more research on this topic. Subsequent research queries are:
- RQ1.
- What were the major algorithms that captured the attention of previous researchers?
- RQ2.
- What were the research objectives in the area of cybercrime in credit cards?
- RQ3.
- What were the performance metrics used in most research papers?
- RQ4.
- What were the data collection techniques used by the researchers?
- RQ5.
- What are the keywords of the articles, either related to our research or not?
- RQ6.
- What research gaps can lead to new research in the future?
To explain these queries the authors performed a synthetic literature assessment dedicated to machine learning and cybercrime in credit cards. Research articles were collected over ten years of publications from five major databases and then an extraction process was conducted on up to date papers.
5. Methodology
This section will enlighten our methodology for this paper. The main objective of this investigation is to systematically scrutinize the newfangled research on cybercrime in credit cards and machine learning algorithms, their key elements and relationship studies that are up to date. The purpose and effect of the studies are examined in a systematic manner to accomplish the goal. A systematic literature review is a trustworthy, transparent and applicable way of collecting and examining large amounts of evidence from previous research. Structured content analysis, according to [25], is used in this research. A scientific technique to assess the themes of communication is known as structured content analysis. It is very helpful in providing a comprehensive literature review.
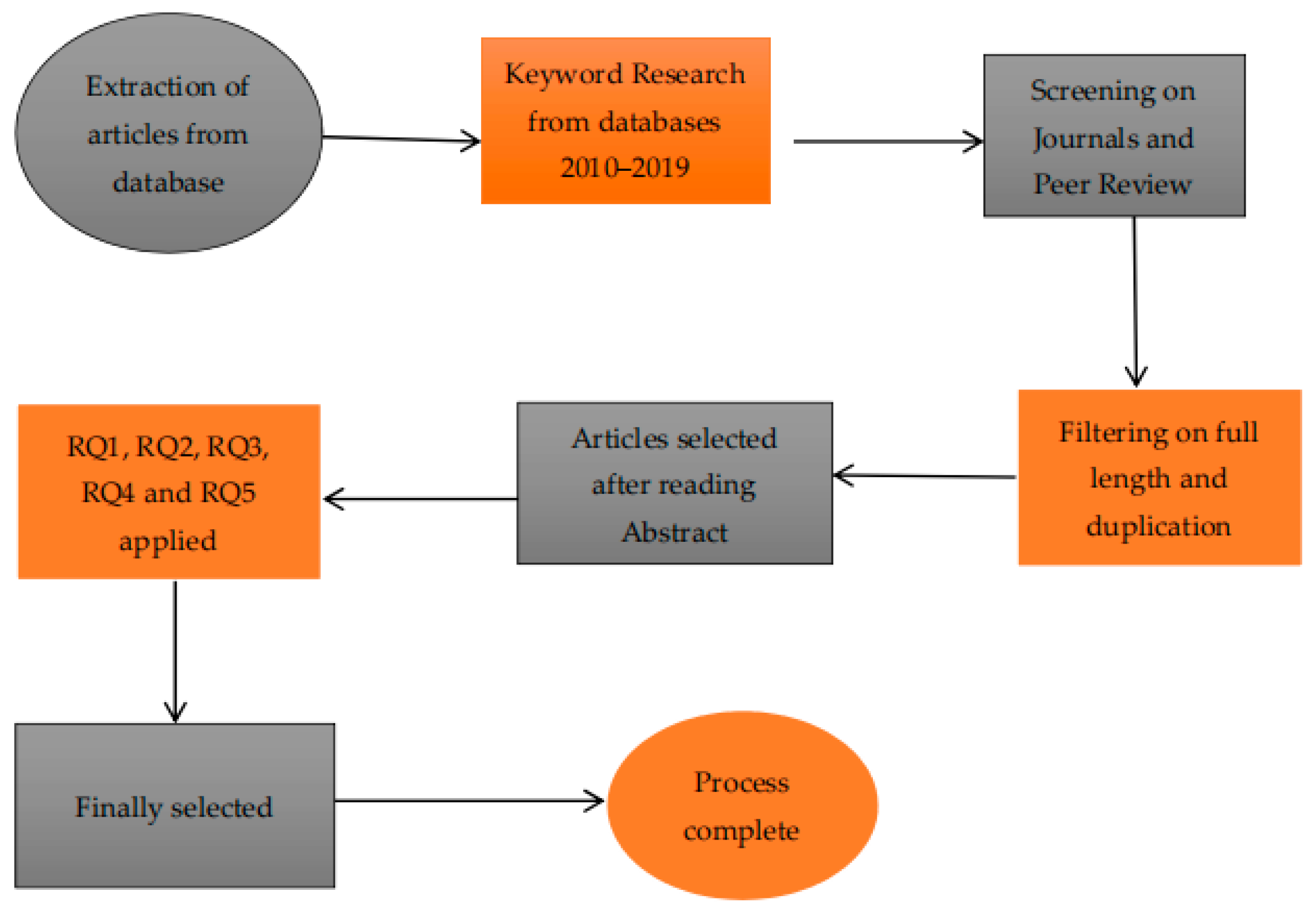
Figure 1 explains our proposed methodology. As it indicates, we started with a selection of articles from five English databases and then our search was filtered from 2010 to 2019, so that the authors gathered updated and new articles. Authors applied screening on search, with a focus on full length articles. After removing duplication, abstracts of articles were analyzed to obtain closer articles to this study. Then, by applying RQ1, RQ2, RQ3, RQ4 and RQ5, further articles were refined.
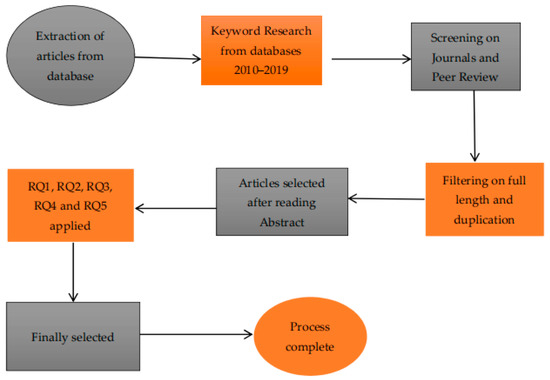
Figure 1.
Detailed methodology.
Furthermore, four main steps recommended by [25] to lead a literature review were also applied in this research. These steps are: data gathering, descriptive investigation, identification of category and examining data. These steps are followed and then elaborated in the results of the findings.
5.1. Data Collection
This section describes the data to be examined and also components of examination. Articles included in this research work are important studies published in the English language. For this purpose, authors have selected five databases, named as Emerald Insight, IEEE, Springer, Science Direct and Wiley Library. Further research is refined by the keywords which are most appropriate for our paper. The time span included in this research is 10 years, from 2010 to 2019. The details of the keywords, followed by our research, are shown in Table 1.

Table 1.
Structured keywords.
5.2. Descriptive Analysis
In descriptive analysis, assessment of formal characteristics is performed to provide history for the evaluation of each study. The attributes that are included in this research paper are title, publication date, author’s details, techniques used in the paper, purpose of the article, journal, datasets used in the article, performance metrics used by the authors and future directions of articles.
5.3. Category Identification
As consistent with the previous literature methodology, articles are selected with supervised, unsupervised machine learning techniques, regression and correlation models, and some literature review articles. Researchers also examined articles with data collection both with the real time datasets and with secondary, as datasets are very important in experiments and evidence gathering. Mostly, studies are based on performance of machine learning algorithms in fraud detection and some studies are survey based.
5.4. Material Evaluation
In this section the articles selected from previous sections are identified. The main focus of each article is the use of machine learning algorithms, supervised or unsupervised, single or hybrid approach, in fraud detection during online credit card transactions. Research focused from the very general broad concept of financial fraud and then became narrower towards credit card fraud. All the results are combined from articles into this single study.
5.4.1. Selection of Articles
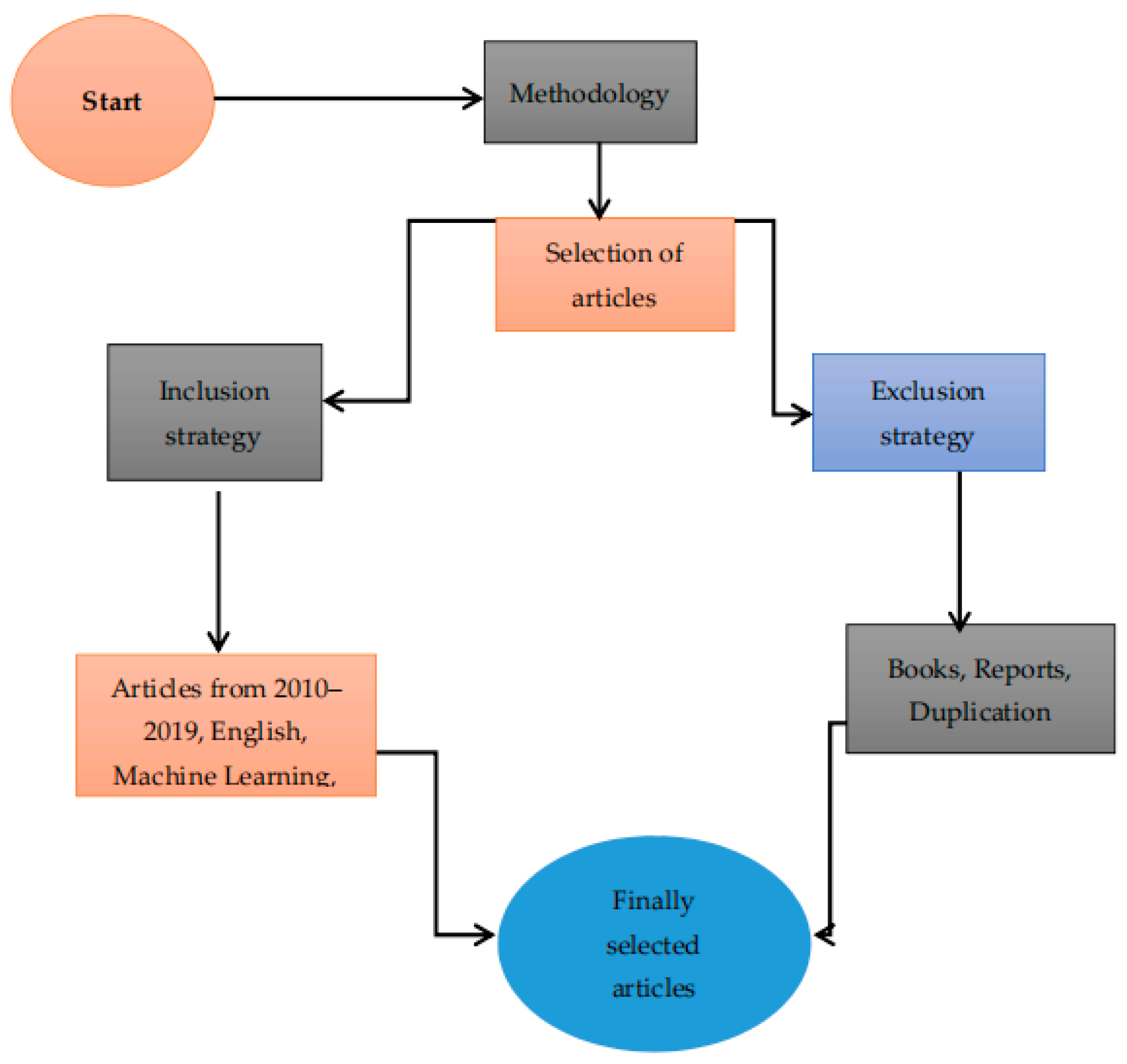
To achieve fine results, inclusion and exclusion strategies are applied in this article, as shown by Figure 2.
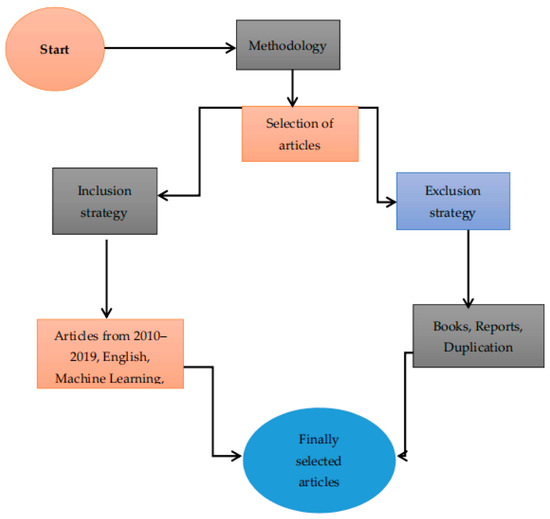
Figure 2.
Selection of articles.
5.4.2. Inclusion Strategy
Research papers published from January 2010 to January 2019 are collected for the synthesis of literature. Manuscripts not published until January 2019 are not included. Articles focusing on financial fraud and then articles addressing fraud detection through machine learning are included. Only articles published in the English language on both addressing management and machine learning are selected.
5.4.3. Elimination Strategy
Books, technical reports and working papers are excluded in the review to maintain the quality of literature. After reading abstracts and conclusions the articles that do not address cybercrime in the financial sector and fraud detection through machine learning are also eliminated from this research.
6. Results
This segment illuminates the outcomes after conducting descriptive investigation, data assessment and category identification. Citations, year of publication, and methodology for study are highlighted by the descriptive investigation.
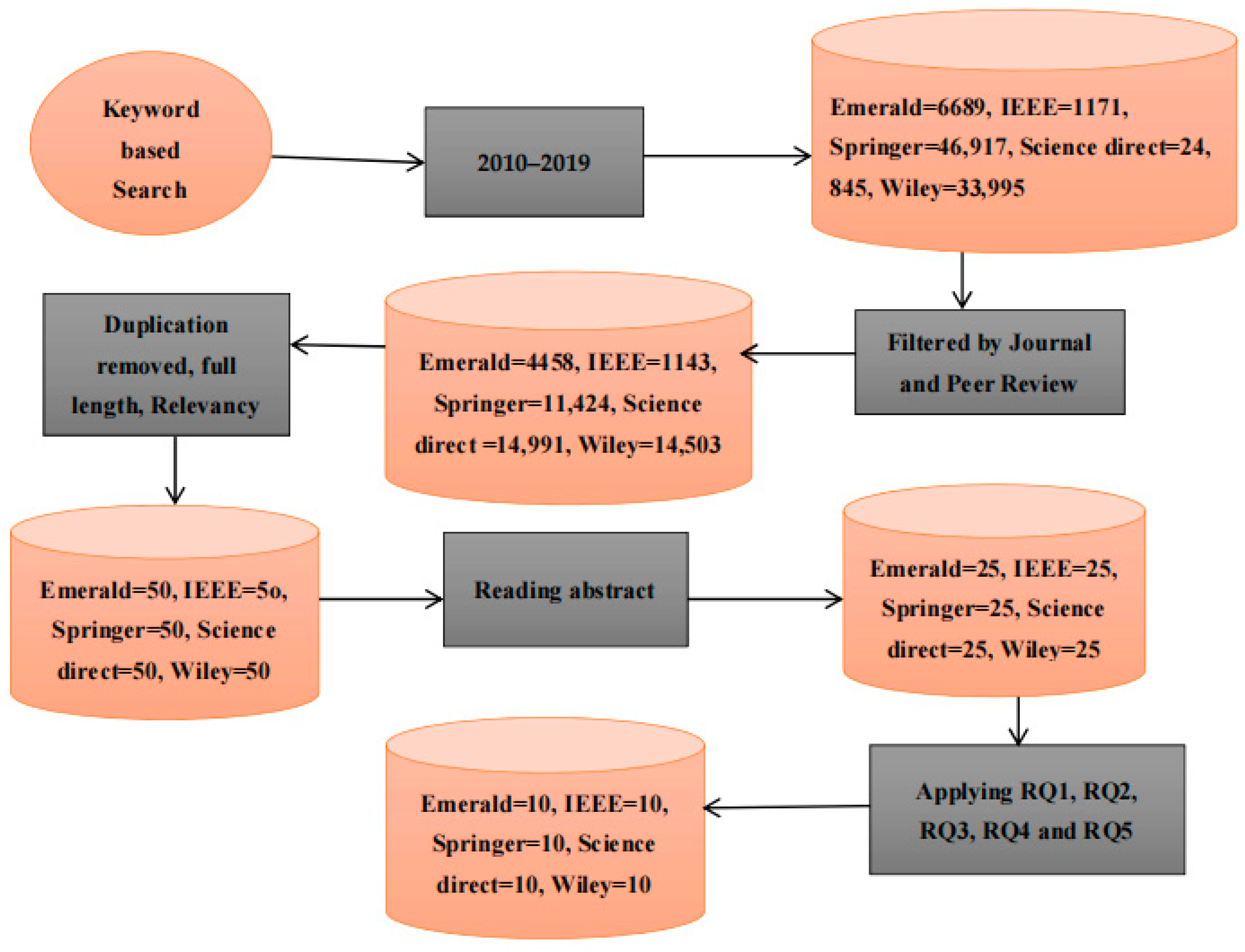
Structured keywords are used in the search process as shown by Figure 3. The articles from 2010 to 2019 are included at the start of search; books, magazine, reports, and articles are all from Emerald (6689), IEEE (1171), Springer (46,917), Science Direct (24,845) and Wiley (33,995). Filters are applied to this large amount of data by only selecting articles and after that article details are as Emerald (4458), IEEE (1143), Springer (11,424), Science Direct (14,991) and Wiley (14,503). Applying the extraction process again by up to date, full length articles, by RQ1, RQ2, RQ3, RQ4, RQ5 and RQ6, after removing duplication, 25 articles are selected from each database. Again, screening is conducted by reading the abstracts of all 125 articles and then 10 articles are selected from every database that are more appropriate to this topic.
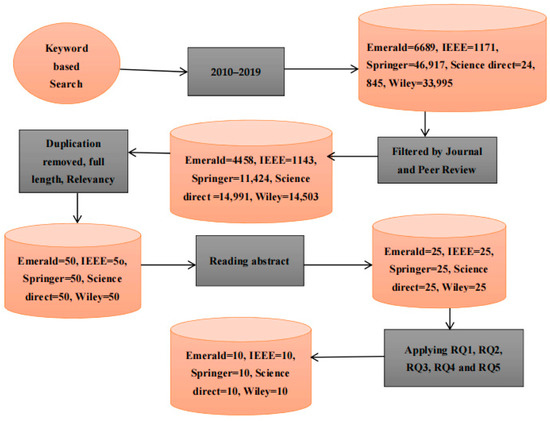
Figure 3.
Detailed process.
6.1. Analysis Based on Frequency of Publication
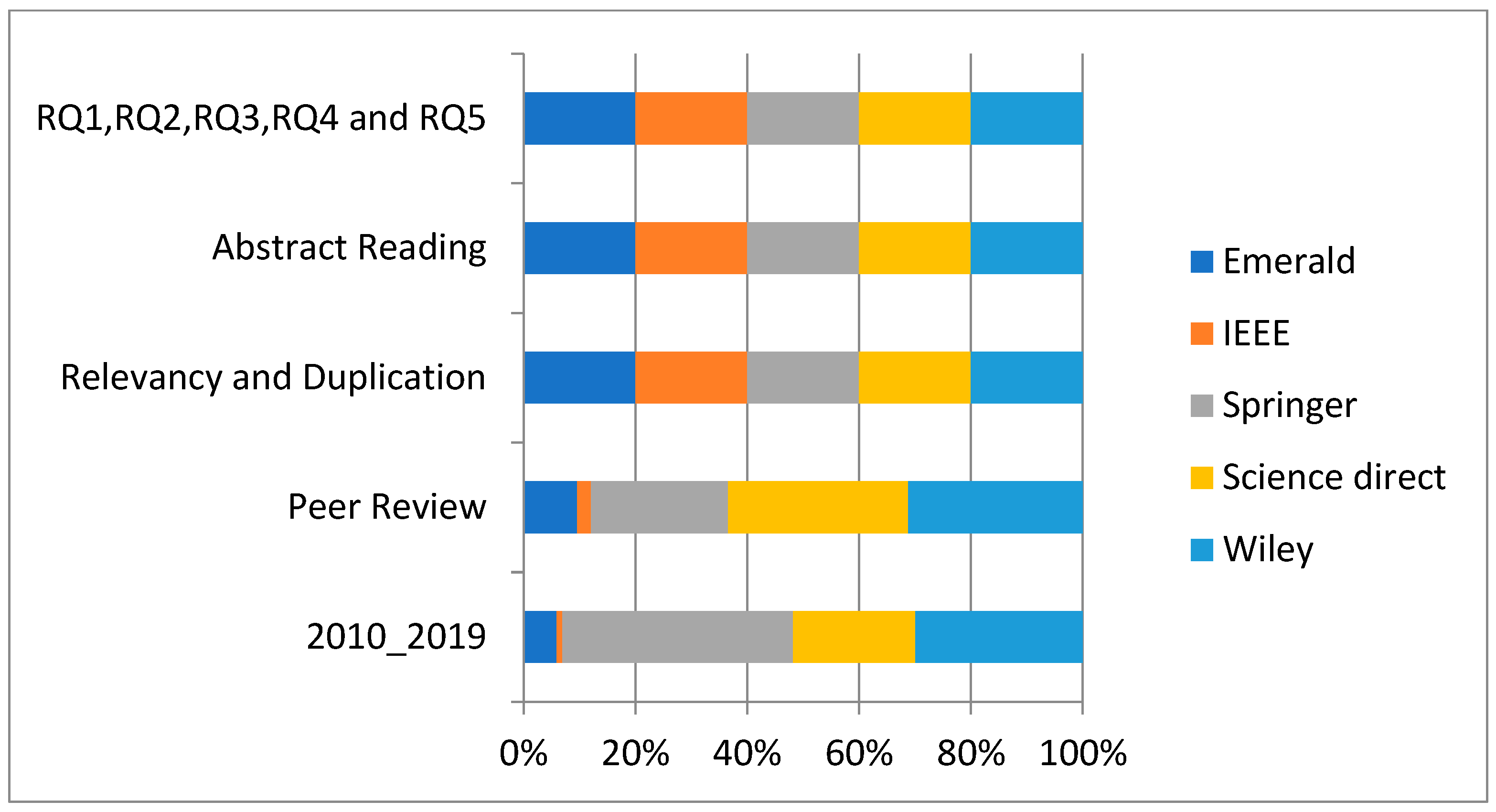
The section elaborates the results from descriptive analysis, publications over time span and database. Figure 4 clarifies that the Wiley database has published higher numbers of research articles addressing the issue of credit card fraud and machine learning, Science Direct falls second in publication frequency. The third database on number of publications is Springer, and fourth is Emerald. IEEE has the lowest number of publications.
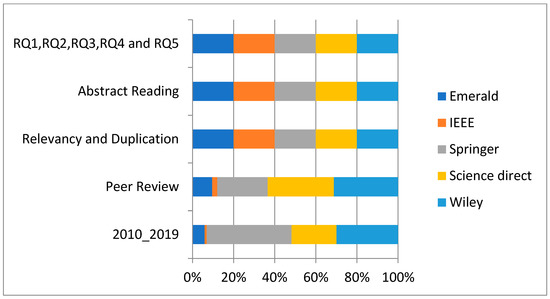
Figure 4.
Detail of publication frequency.
Figure 4 signifies the graphical representation of articles in five databases from the year span of 2010 to 2019.
6.2. Analysis Based on Techniques
The techniques used in previous research, title and year of research and details of researcher are highlighted in these sections.
Table 2 provides information about the most commonly used machine learning techniques. Supervised machine learning techniques were used by majority of researchers. The frequently explored machine learning techniques in the area of fraud detection are neural network, PCA, support vector machine, Naïve Bayes, adaptive boosting, random forecast, artificial immune system, artificial neural network, decision tree, genetic algorithm, k-nearest neighbor, bagging, Multi-layer Perceptron and Hidden Markov model. Single and hybrid approaches were used to find fraud more effectively and efficiently.

Table 2.
Techniques in previous research.
6.3. Analysis Based on Purpose and Datasets
The purpose of research is the main focus while reading any study. In this section, purpose of previous research is provided in a very comprehensive way. Datasets play a vital role in the findings of any research. Here the datasets are the main focus, and they were taken from primary or secondary sources for the analysis of credit card fraud detection.
Table 3 elaborates the aim of the previous researchers and data used by them for analysis. In the field of fraud detection, real world data are more important, but it is difficult to obtain real fraud data from any organization. The main objectives were to deal with challenges, such as dealing with class imbalance, to find the most efficient techniques, handling of complex problems, customer behaviors and feature engineering. Primary as well as secondary data were used for experiments to provide evidence on the role of machine learning methodologies to solve the problem of financial fraud. Primary data were the concern of the majority of researchers.

Table 3.
Purpose and datasets in previous work.
6.4. Analysis Based on Performance Measures and Future Directions
This section throws light on the performance measures adopted by scholars in the past and will suggest directions for the next research.
Table 4 explains the performance measures and future directions in the area of credit card fraud detection. Performance evaluation was conducted by examining accuracy, true positive rate, false positive rate, true negative rate, F-Measure, recall, precision, mean, median, mode, standard deviation, error rate, area under curve, alert rate, beta and by value of P. The future directions suggested by the researchers are base rate, classifier performance, cost, class imbalance, knowledge extractions, integration of different techniques, new strategies of feature engineering, and techniques that can be examined with multi-dimensional data, focusing on execution time to identify fraud.

Table 4.
Performance measures and future directions in previous studies.
6.5. Analysis Based on Journals and Conferences
Journal and conferences of papers and frequency of publications with respect to the journals are presented in this segment.
The studies that are included for this systematic review of credit card fraud and machine learning are represented by Table 5. These studies are from different journals and conferences. Minimum studies included from one journal or conference is one and maximum is five.

Table 5.
Articles published in journal and conferences.
7. Conclusions
Research on fraud detection through machine learning is a very hot topic from the last decade. Definitely, it is observed that a significant amount of research is conducted, but still there is a need for more future research in fraud detection. This article is an effort to enhance the knowledge of the research by conducting a wide-ranging systematic literature review. Five databases are selected and then articles from these databases are included in this research. An extraction process is applied to the articles and finally selected articles are included in the study. The research gaps in previous research show that several issues need to be focused on more in the future, such as class imbalance, high dimensions, consumption time, accurate fraud detection, and decrease in false alarms.
The systematic literature review is conducted in this article as a review of past research from the five famous databases. The main focus is on the machine learning techniques, performance metrics and datasets used by the researchers. The analyses examined in this article clearly shows that primary datasets are real time and primary datasets are more important to generate better outcomes. The secondary datasets presented by the different online repositories are less effective for the presentation of actual problems.
The databases are summarized and then categorized according to the perspective of cybercrime and machine learning techniques, performance metrics, and datasets that would be helpful for financial firms to understand cybercrime in detail. This article can contribute to cybercrime awareness and security frameworks of banks. Moreover, this paper emphasized the availability of primary datasets in the area of machine learning. Machine learning algorithms can provide effective results with real datasets and researchers can also pay more attention to the actual problem after the analysis of real data. This study is beneficial for future researchers as it highlights the need for real datasets. Mostly researchers focused on neural networks and regression analysis in management analysis methods.
Furthermore, this article is very helpful for future research and mentions the main issues in the area of fraud detection by using machine learning. These issues are handling complex data, imbalance data, real time response, customer behavior, spending patterns, customer awareness, and impact of social, technological and administration. The performance metrics that can be explored in future research include false positive, true positive, response time of algorithms and area under the curve. Our paper is very helpful as it is knowledge based on up to date research which can be very beneficial for researchers, especially those dealing with fraud detection.
Future work in this study can be conducted as it has a lot of limitations. This study focused on a list of keyword-based searches for this literature review. Further in depth studies will be performed with more keywords. Secondly, we just focus on five repositories; other repositories will be explored in future. Thirdly, our time span is from 2010 to 2019; time will be expanded with further research. Furthermore, this research is focused on articles, but in the next work financial reports, non-English articles and PhD theses could be included. There should be proper reporting on cybercrime to generate more real time datasets. The banks should be more aware that if there will be a greater availability of real time data, then there will be more understanding of the issue. The researchers can also conduct in depth analysis on primary data availability in the field of fraud detection.
Author Contributions
Conceptualization, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Data curation, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Formal analysis, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Funding acquisition, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Investigation, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Methodology, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Project administration, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Resources, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Software, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Supervision, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Validation, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Visualization, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Writing—original draft, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L.; Writing—review & editing, R.M.D., R.F., F.J., P.N.M., M.N.M. and G.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Instituto Politécnico de Lisboa.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
We thank Instituto Politécnico de Lisboa for providing funding for this study.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Khan, S.; Zeeshan, A.; Gul, A.; Haider, S.A. Islamic banking system of Pakistan: Comparison between perception and experience. Acad. Strateg. Manag. J. 2021, 20, 1–6. [Google Scholar]
- Hyde, A.M. E-BANKING: Review of literature. Prestige e-J. Manag. Res. 2015, 2, 2. [Google Scholar]
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. Eurasip. J. Inf. Secur. 2020, 8, 8. [Google Scholar] [CrossRef]
- Cremer, F.; Sheehan, B.; Fortmann, M.; Kia, A.N.; Mullins, M.; Murphy, F.; Materne, S. Cyber risk and cybersecurity: A systematic review of data availability. Geneva Pap Risk Insur. Issues Pract. 2022, 47, 698–736. [Google Scholar] [CrossRef] [PubMed]
- Khattri, V.; Singh, D.K. Parameters of automated fraud detection techniques during online transactions. J. Financ. Crime 2018, 25, 702–720. [Google Scholar] [CrossRef]
- Krambia-Kapardis, M.; Christodoulou, C.; Agathocleous, M. Neural networks: The panacea in fraud detection. Manag. Auditing J. 2010, 25, 659–678. [Google Scholar] [CrossRef]
- Jie, W.; Poulova, P.; Haider, S.A.; Sham, R.B. Impact of internet usage on consumer impulsive buying behavior of agriculture products: Moderating role of personality traits and emotional intelligence. Front. Psychol. 2022, 13, 951103. [Google Scholar] [CrossRef]
- Prabowo, H.Y. Building our defence against credit card fraud: A strategic view. J. Money Laund. Control. 2011, 14, 371–386. [Google Scholar] [CrossRef]
- Zheng, L.; Liu, G.; Yan, C.; Jiang, C. Transaction Fraud Detection Based on Total Order Relation and Behavior Diversity. IEEE Trans. Comput. Soc. 2018, 5, 796–806. [Google Scholar] [CrossRef]
- Alloghani, M.; Al-Jumeily, D.; Mustafina, J.; Hussain, A.; Aljaaf, A.J. A Systematic Review on Supervised and Unsupervised Machine Learning Algorithms for Data Science. In Supervised and Unsupervised Learning for Data Science. Unsupervised and Semi-Supervised Learning; Berry, M., Mohamed, A., Yap, B., Eds.; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Randhawa, K.; Loo, C.K.; Seera, M.; Lim, C.P.; Nandi, A.K. Credit Card Fraud Detection Using AdaBoost and Majority Voting. IEEE Access 2018, 6, 14277–14284. [Google Scholar] [CrossRef]
- Dal Pozzolo, A.; Boracchi, G.; Caelen, O.; Alippi, C.; Bontempi, G. Credit Card Fraud Detection: A Realistic Modeling and a Novel Learning Strategy. IEEE Trans. Neural Networks Learn. Syst. 2018, 29, 8. [Google Scholar]
- European Central Bank, Euro System, Executive Summary. Available online: https://www.ecb.europa.eu/pub/cardfraud/html/ecb.cardfraudreport202110~cac4c418e8.en.html (accessed on 11 December 2020).
- Awoyemi, J.O.; Oluwadare, S.A. Credit card fraud detection using Machine Learning Techniques: A Comparative Analysis. In Proceedings of the 2017 International Conference on Computing Networking and Informatics (ICCNI), Lagos, Nigeria, 29–31 October 2017. [Google Scholar]
- Ali, A.; Iqbal, S.; Haider, S.A.; Tehseen, S.; Anwar, B.; Sohail, M.; Rehman, K. Does governance in information technology matter when it comes to organizational performance in Pakistani public sector organizations? Mediating effect of innovation. SAGE Open. 2021, 11, 21582440211016557. [Google Scholar] [CrossRef]
- Vipul, P.; Umesh, K.L. A Survey on Different Data Mining & Machine Learning Methods for Credit Card Fraud Detection. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 3, 320–325. [Google Scholar]
- Chauhan, T.; Rawat, S.; Malik, S.; Singh, P. Supervised and Unsupervised Machine Learning based Review on Diabetes Care. In Proceedings of the 2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 19–20 March 2021; pp. 581–585. [Google Scholar] [CrossRef]
- Kilincer, I.F.; Ertam, F.; Abdulkadir, S. Machine learning methods for cyber security intrusion detection: Datasets and comparative study. Comput. Netw. 2021, 188, 107840. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 20. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. MQTT set, a new dataset for machine learning techniques on MQTT. Sensors 2020, 20, 17. [Google Scholar] [CrossRef]
- Mahfouz, A.; Abuhussein, A.; Venugopal, D.; Shiva, S. Ensemble classifers for network intrusion detection using a novel network attack dataset. Future Internet 2020, 12, 180. [Google Scholar] [CrossRef]
- Iwasokun, G.B.; Akinyede, R.O.; Fadamiro, C.F.; Bello, O.A. Factor analysis of financial crime-related issues. J. Financ. Crime 2019, 26, 113–130. [Google Scholar] [CrossRef]
- Bai, F.; Chen, X. Analysis on the new types and countermeasures of credit card fraud in mainland China. J. Financ. Crime 2013, 20, 267–271. [Google Scholar] [CrossRef]
- Seuring, S.; Gold, S. Conducting content-analysis based literature reviews in supply chain management. Supply Chain Manag. Int. J. 2012, 17, 544–555. [Google Scholar] [CrossRef]
- Whitty, M.T. Predicting susceptibility to cyber-fraud victimhood. J. Financ. Crime 2019, 26, 277–292. [Google Scholar] [CrossRef]
- Omar, N.; Johari, Z.A.; Smith, M. Predicting fraudulent financial reporting using artificial neural network. J. Financ. Crime 2017, 24, 362–387. [Google Scholar] [CrossRef]
- Adewumi, O.A.; Akinyelu, A.A. A hybrid firefly and support vector machine classifier for phishing email detection. Kybernetes 2016, 45, 977–994. [Google Scholar] [CrossRef]
- Lin, W.-C.; Ke, S.-W.; Tsai, C.-F. Top 10 data mining techniques in business applications: A brief survey. Kybernetes 2017, 46, 1158–1170. [Google Scholar] [CrossRef]
- Sun, Y.; Davidson, I. Influential factors of online fraud occurrence in retailing banking sectors from a global prospective: An empirical study of individual customers in the UK and China. Inf. Comput. Secur. 2015, 23, 3–19. [Google Scholar] [CrossRef]
- Phua, C.; Smith-Miles, K.; Lee, V.; Gayler, R. Resilient Identity Crime Detection. IEEE Trans. Knowl. Data Eng. 2012, 24, 533–546. [Google Scholar] [CrossRef]
- Lee, Y.J.; Yeh, Y.R.; Wang, Y.C.F. Anomaly Detection via Online Oversampling Principal Component Analysis. IEEE Trans. Knowl. Data Eng. 2013, 25, 7. [Google Scholar] [CrossRef]
- Gadi, M.F.A.; Wang, X.; do Lago, A.P. Comparison with Parametric Optimizationin Credit Card Fraud Detection. In Proceedings of the Seventh International Conference on Machine Learning and Applications, San Diego, CA, USA, 11–13 December 2008. [Google Scholar]
- Huang, D.; Mu, D.; Yang, L.; Cai, X. CoDetect: Financial Fraud Detection With Anomaly Feature Detection. IEEE Access 2018, 6, 19161–19174. [Google Scholar] [CrossRef]
- Qiu, S.; He, H.-Q. Machine Learning- and Evidence Theory-Based Fraud Risk Assessment of China’s Box Office. IEEE Access 2018, 6, 75619–75628. [Google Scholar] [CrossRef]
- Charleonnan, A. Credit Card Fraud Detection Using RUS and MRN Algorithms. In Proceedings of the 2016 Management and Innovation Technology International Conference (MITiCON-2016), Bang-San, Thailand, 12–14 October 2016. [Google Scholar]
- Melo-Acosta, G.E.; Duitama-Muñoz, F.; Arias-Londoño, J.D. Fraud Detection in Big Data using Supervised and Semi-supervised Learning Techniques. In Proceedings of the IEEE Colombian Conference on Communications and Computing (COLCOM), Cartagena, Colombia, 16–18 August 2017. [Google Scholar]
- Adewumi, A.O.; Akinyelu, A.A. A Survey of Machine-Learning and Nature-Inspired Based Credit Card Fraud Detection Techniques. Int. J. Syst. Assur. Eng. Manag. 2017, 8, 937–953. [Google Scholar] [CrossRef]
- Bekirev, A.S.; Klimov, V.V.; Kuzin, M.V.; Shchukin, B.A. Payment Card Fraud Detection Using Neural Network Committee and Clustering. Opt. Mem. Neural Netw. 2015, 24, 193–200. [Google Scholar] [CrossRef]
- Jain, A.K.; Gupta, B.B. A machine learning based approach for phishing detection using hyperlinks information. J. Ambient Intell. Humaniz. Comput. 2018, 10, 2015–2028. [Google Scholar] [CrossRef]
- Somasundaram, A.; Reddy, S. Parallel and incremental credit card fraud detection model to handle concept drift and data imbalance. Neural Comput. Appl. 2018, 31, 3–14. [Google Scholar] [CrossRef]
- Wei, W.; Li, J.; Cao, L.; Ou, Y.; Chen, J. Effective detection of sophisticated online banking fraud on extremely imbalanced data. World Wide Web 2013, 16, 449–475. [Google Scholar] [CrossRef]
- Zhou, H.; Chai, H.F.; Qiu, M.L. Fraud detection within bankcard enrollment on mobile device based payment using machine learning. Front. Inf. Technol. Electron. Eng. 2018, 19, 1537–1545. [Google Scholar] [CrossRef]
- Dheepa, V.; Dhanapal, R. Hybrid Approach for Improvising Credit Card Fraud Detection Based on Collective Animal Behaviour and SVM. In International Symposium on Security in Computing and Communication; Springer: New York, NY, USA, 2013. [Google Scholar]
- Ade, P.K. Logistic Regression Learning Model for Handling Concept Drift with Unbalanced Data in Credit Card Fraud Detection System. In Proceedings of the Second International Conference on Computer and Communication Technologies, Hyderabad, India, 24–26 July 2015. [Google Scholar]
- Mohammed, R.; Wong, K.-W.; Shiratuddin, M.F.; Wang, X. Scalable Machine Learning Techniques for Highly Imbalanced Credit Card Fraud Detection: A Comparative Study. In PRICAI 2018: Trends in Artificial Intelligence; Springer: New York, NY, USA, 2018. [Google Scholar]
- Krause, N.F.-T. Neural Network Rule Extraction to Detect Credit Card Fraud. International Conference on Engineering Applications of Neural Networks; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Gómez, J.A.; Arévalo, J.; Paredes, R.; Nin, J. End-to-end neural network architecture for fraud scoring in card payments. Pattern Recognit. Lett. 2018, 105, 175–181. [Google Scholar] [CrossRef]
- Chandra, S.; Throckmorton, W.J. Financial fraud detection using vocal, linguistic and financial cues. Decis. Support Syst. 2015, 74, 78–87. [Google Scholar]
- Carneiro, N.; Figueira, G.; Costa, M. A data mining-based system for credit-card fraud detection in e-tail. Decis. Support Syst. 2017, 95, 91–101. [Google Scholar] [CrossRef]
- Lin, C.C.; Chiu, A.A.; Huang, S.Y.; Yen, D.C. Detecting the Financial statement fraud: The anaylsis of the differences between the data mining and expert’s judgments. Knowl.-Based Syst. 2015, 89, 459–470. [Google Scholar] [CrossRef]
- de Sá, A.G.; Pereira, A.C.; Pappa, G.L. A customized classification algorithm for credit card fraud detection. Eng. Appl. Artif. Intell. 2018, 72, 21–29. [Google Scholar] [CrossRef]
- Bahnsen, A.C.; Aouada, D.; Stojanovic, A.; Ottersten, B. Feature Engineering Strategies for Credit Card Fraud Detection. Expert Syst. Appl. 2016, 51, 134–142. [Google Scholar] [CrossRef]
- Jurgovsky, J.; Granitzer, M.; Ziegler, K.; Calabretto, S.; Portier, P.E.; He-Guelton, L.; Caelen, O. Sequence classification for credit card fraud detection. Expert Syst. Appl. 2018, 100, 234–245. [Google Scholar] [CrossRef]
- Zareapoor, M.; Shamsolmoali, P. Application of Credit Card Fraud Detection: Based on Bagging Ensemble Classifier. Procedia Comput. Sci. 2015, 48, 679–685. [Google Scholar] [CrossRef]
- West, J.; Bhattacharya, M. Some Experimental Issues in Financial Fraud Mining. The International Conference on Computational Science. Procedia Comput. Sci. 2016, 80, 1734–1744. [Google Scholar] [CrossRef]
- Chouiekh, A.; Haj, E.H.I.E. ConvNets for Fraud Detection analysis. The First International Conference On Intelligent Computing in Data Sciences. Procedia Comput. Sci. 2018, 127, 133–138. [Google Scholar] [CrossRef]
- Bandaragoda, T.R.; Ting, K.M.; Albrecht, D.; Liu, F.T.; Zhu, Y.; Wells, J.R. Isolation-basedanomaly detectionusing nearest-neighbor ensembles. Comput. Intell. 2017, 34, 968–998. [Google Scholar] [CrossRef]
- Kültür, Y.; Çağlayan, M.U. Hybrid approaches for detecting credit card fraud. Expert Syst. 2016, 34, e12191. [Google Scholar] [CrossRef]
- Ahmadian Ramaki, A.; Rasoolzadegan, A.; Javan Jafari, A. A systematic review on intrusion detection based on the Hidden Markov Model. Stat. Anal. Data Min. ASA Data Sci. J. 2018, 11, 111–134. [Google Scholar] [CrossRef]
- Song, X.P.; Hu, Z.H.; Du, J.G.; Sheng, Z.H. Application of Machine Learning Methods to Risk Assessment of Financial Statement Fraud: Evidence from China. J. For. 2014, 33, 611–626. [Google Scholar] [CrossRef]
- Vasarhelyi, T.S. Predicting credit card delinquencies: An application of deep neural networks Intelligent system in Accounting. Financ. Manag. 2018, 25, 174–189. [Google Scholar]
- Whiting, D.G.; Hansen, J.V.; McDonald, J.B.; Albrecht, C.; Albrecht, W.S. Machine learning methods for detecting patterns of management fraud. Comput. Intell. 2012, 28, 505–527. [Google Scholar] [CrossRef]
- Wong, N.; Ray, P.; Stephens, G.; Lewis, L. Artificial immune systems for the detection of credit card fraud: An architecture, prototype and preliminary results. Inf. Syst. J. 2012, 22, 53–76. [Google Scholar] [CrossRef]
- Stahl, F.; Jordanov, I. An overview of the use of neural networks for data mining tasks. Wiley Interdiscip. Rev. Data Mining Knowl. Discov. 2012, 2, 193–208. [Google Scholar] [CrossRef]
- Wang, G.P.; Yang, J.X.; Li, R. Imbalanced SVM-Based Anomaly Detection Algorithm for Imbalanced Training Datasets. ETRI J. 2017, 39, 621–631. [Google Scholar] [CrossRef]
- Twitchell, D.P.; Fuller, C.M. Advancing the assessment of automated deception detection system: Incorporating the base rate and cost into system evaluation. Inf. Syst. J. 2018, 29, 738–761. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).