Abstract
With the rapid development of Internet of Things (IoT) technology, the number of IoT users is growing year after year. IoT will become a part of our daily lives, so it is likely that the security of these devices will be an important issue in the future. Quantum computing is maturing, and the security threat associated with quantum computing will be faced in the transmissions of IoT devices, which mainly use wireless communication technologies. Therefore, to ensure the protection of transmitted data, a cryptographic algorithm that is efficient in defeating quantum computer attacks needs to be developed. In this paper, we propose a device authentication and secure communication system with post-quantum cryptography (PQC) for AIoT environments using the NTRU and Falcon signature mechanism, which can resist quantum computer attacks and be used in AIoT environments to effectively protect the confidentiality, integrity, and non-repudiation of transmitted data. We also used Raspberry Pi to simulate AIoT devices for implementation.
1. Introduction
Artificial intelligence (AI) has the potential to have widespread impacts and applications, and its development has been rapidly growing, including the implementation of strategies, policies, and their adoption [1,2]. The energy consumption of 5G networks can be reduced while still allowing for communication among a large number of devices, such as hundreds or thousands of sensors in Internet of Things (IoT) networks [2,3]. Although the 5G-IoT environment introduces potential possibilities in developments and applications in many fields due to the convenience and quality of services, the security and privacy of transmitted data are of utmost importance because data in IoT networks are transmitted through wireless communication [4]. Because wireless networks are easily attacked compared with wire networks, serious information security events will be faced by wireless networks, such as privacy leakage, man-in-the-middle attacks, data tempering, etc. The rapid progress of AIoT has led to the discussion on security concerns due to the distinct networking structure and method of acquiring and storing data [5,6]. Continuously capturing and gathering data increases security risks because devices are always online, and adversaries have unlimited opportunities to attack AIoT systems.
Quantum computing technology has attracted researchers and famous manufacturers’ attention, such as IBM, Google, Microsoft, Hon Hai Precision Industry, Alibaba, etc., and has been developed rapidly; quantum computing technology will change people’s daily life [7]. On the other hand, the risk of traditional cryptographic mechanisms being broken by quantum computing technology via Shor’s algorithm [8] is increasing. Post-quantum cryptography (PQC) is a cryptographic solution that can prevent attacks from quantum computers using modern computers to prevent such risks before quantum computers are produced rapidly. The proposed scheme utilized one PQC mechanism called the number theory research unit (NTRU) [9] and fast-Fourier lattice-based compact signatures over the NTRU (the Falcon signature mechanism) [10] to design secure communication mechanisms.
Due to the reasons above, we designed and evaluated a device authentication and secure communication system with PQC for AIoT environments. We utilized the NTRU [9] and Falcon signature mechanisms [10] because both can resist attacks from quantum computers with better speeds of encryption, decryption, and sign mechanisms than those of traditional cryptographic mechanisms [11]. In summary, the proposed scheme can protect the security and privacy of transmitted data while resisting attacks from quantum computers. The remaining sections of the paper are outlined below. AIoT, post-quantum cryptography, the NTRU [9], and the Falcon signature [10] are introduced in Section 2. Section 3 introduces the proposed scheme, and security and performance analysis are detailed in Section 4 and Section 5, respectively. Section 6 describes system implementation. We present a discussion on the research results and limitations of this research in Section 7. Finally, the conclusion is drawn in Section 8.
2. Related Works
We introduce and review AIoT, post-quantum cryptography, the NTRU [9], and the Falcon signature [10] in this section.
2.1. AIoT
In many areas, AIoT is expected to improve the quality of services of the industry because devices in the Internet of Things have the ability to simulate human intelligence and support decision making by continuously learning from large amounts of data [5,12]. AIoT opens up possibilities for applications in all kinds of fields because of its transparency, agility, and adaptability [6,12]. The adoption of AIoT ends up on top of the to-do list of many applications, such as smart homes, smart factories, smart cities, and so on [12,13,14,15,16,17,18,19]. However, AIoT also provides opportunities for adversaries. Once an AIoT system is established, all related devices will exist in the network until the system is shut down. Adversaries can attack any device in wireless networks through various means, such as eavesdropping, the tempering of transmitted data, impersonation, etc. The proposed scheme is designed to be implemented in AIoT environments for transmitted data protection and device authentication.
2.2. Post-Quantum Cryptosystem
The development of quantum computing is expected to have a huge impact on information technology in the future. One of the applications, called quantum cryptanalysis, will be a serious threat to information security because of its ability to attack public key cryptosystems, such as RSA, the Diffie–Hellman cryptosystem, elliptic curve cryptography (ECC), etc., through Shor’s algorithm [8]. The post-quantum cryptosystem can be a solution for resisting attacks from quantum computers. The post-quantum cryptosystem has advantages, which are listed below. First, the costs of establishment and development are lower than that of a quantum cryptosystem. The post-quantum cryptosystem can be executed by modern computers and systems. Second, public key encryption and digital signature mechanisms can be applied by post-quantum cryptosystems. Post-quantum cryptosystems include lattice-based, hash-based, code-based, multivariate, and supersingular elliptic curve isogeny cryptography. As the matter of fact, post-quantum cryptosystems will replace traditional public key cryptosystems soon. The proposed scheme utilizes lattice-based cryptosystems to design a secure communication mechanism.
2.3. NTRU
The NTRU is a latticed-based public key cryptosystem including encryption and signature [9]. The security of the NTRU depends on the shortest vector problem (SVP) in the lattice. The SVP is defined as the discovery of a datum point that has the shortest distance from the base point [9]. The NTRU can resist attacks from Shor‘s algorithm [8] while maintaining attractive features, such as better encryption and decryption speed, smaller key size, and higher security compared with those of traditional cryptosystems [9]. The NTRU is proven as one of the quantum-resistant cryptographic algorithms by National Institute of Standards and Technology (NIST) [9,20]. Although the NTRU has failed to compete among the post-quantum cryptography standardization finalists, it is still widely used because of its advantages over other lattice based cryptography systems [9,20,21]. The NTRU is more efficient than traditional cryptographic mechanisms and can be implemented in devices with restricted resources, such as AIoT, embedded devices, etc. [22,23,24]. A property comparison of RSA, ECC, and NTRU [9] is presented in Table 1 [25]. Compared with RSA and ECC, all algorithms can achieve an encryption and signature mechanism, but RSA cannot achieve a key exchange mechanism. The NTRU has a faster encryption speed than RSA and ECC. RSA and the NTRU are easier to use in key distribution than ECC is. Among the three algorithms, only the NTRU is a quantum-resistant cryptographic algorithm.

Table 1.
Property comparison of RSA, ECC, and NTRU [25].
ECC and the NTRU [9] can provide the same security level as RSA can with a shorter key length, so ECC and the NTRU [9] need much less storage and a much shorter transmission time. These attractive features are advantages for devices with restricted resources. Compared with RSA, ECC, and the NTRU [9], ECC has the shortest key length at the same security level. The NTRU [9] has a shorter key length than RSA does under a security level of 192 bits and 256 bits. The comparison of key lengths of RSA, ECC, and the NTRU [9] at different security levels is shown in Table 2 [26] and Figure 1 [26].

Table 2.
Key length of RSA, ECC, and NTRU with different security levels [26].
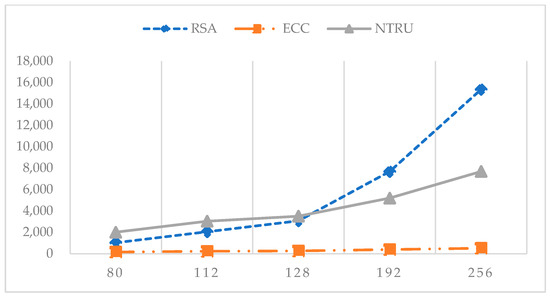
Figure 1.
Key length of RSA, ECC, and NTRU with different security levels [26].
Although the NTRU [9] needs more time to generate a key, the NTRU [9] needs less time to encrypt and decrypt than ECC does at a security level of 80 bits. The NTRU [9] is faster than ECC is in key generation, encryption, and decryption at a security level of 112 bits and beyond. The execution times of ECC and the NTRU [9] at different security levels are shown in Table 3 [26]. The proposed scheme utilized the NTRU [9] for encryption and decryption mechanisms. For details of the NTRU, readers can refer to Hoffstein et al.’s work [9].

Table 3.
Execution time of ECC and NTRU with different security levels [26].
2.4. Falcon Signature Mechanism
The Falcon signature mechanism adopts a trapdoor function named fast Fourier sampling [10]. The Falcon signature mechanism is also proven by NIST to be one of the quantum-resistant cryptographic algorithms [10,20]. The security of the Falcon signature mechanism is based on the short integer solution (SIS) [10]. Features of the Falcon signature mechanism [10] are listed as below. First, the Falcon signature mechanism [10] utilizes discrete Gaussian sampling over the integers, which is able to avoid the key exposure problem while generating multiple signatures. Second, signatures generated by the Falcon signature mechanism [10] are shorter than those generated by other lattice-based signature mechanisms with the same public key length. Third, the Falcon signature mechanism [10] can generate thousands of signatures in a few seconds with a verification speed about 5 to 10 times faster than that of other signature mechanisms. Forth, the Falcon signature mechanism [10] allows the use of long-term security parameters with the same time complexity under degree n. Although the Falcon signature mechanism [10] is intended to defend against quantum computer attacks, due to its high efficiency, its [10] use has become widespread. For details of the Falcon signature mechanism, readers can refer to Fouque et al.’s work [10]. The proposed scheme utilized the Falcon signature mechanism [10] for message verification.
3. Proposed Scheme
We design and evaluate a device authentication and secure communication system with PQC for AIoT environments. IoT devices in the proposed system capture and send data through wireless networks to the gateway. The gateway can be a mobile phone, an IoT gateway, a stand-alone laptop computer, etc. After receiving data from IoT devices, the gateway transmits data to the server.
3.1. System Structure
The system of the proposed scheme includes IoT devices, a gateway, a server, and a smart token. The smart token stores the private key and parameters of the gateway securely and output parameters after decryption and signing mechanisms come into effect. After that, data will be sent to server. The system structure of the proposed scheme is illustrated in Figure 2.
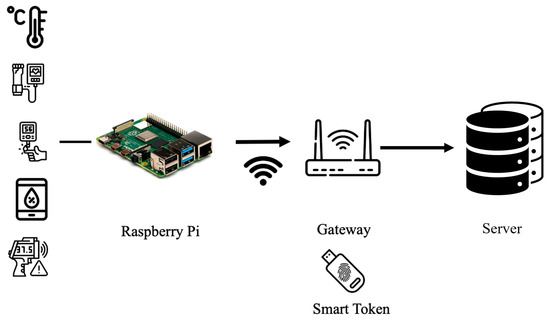
Figure 2.
System structure of proposed scheme.
The proposed scheme includes four phases. In the preliminary phase, the system generates essential parameters and functions. IoT devices are registered on the server using a MAC address, and the server generates and distributes private keys, public keys, and initial values to IoT devices in the registration phase through a secure channel. In an IoT device’s gateway communication phase, it captures and encrypts data with the public key of the gateway, and then generates a signature with the private key of the IoT device itself. Then, the IoT device sends encrypted data and the signature to the gateway. The gateway verifies the signature using the public key of the IoT device and decrypts data using the private key in the smart token. In the gateway’s server communication phase, the gateway sends encrypted data and the signature to the server. After receiving encrypted data and verifying the signature, the server stores the encrypted data and signature. Notations of the proposed scheme are shown in Table 4.

Table 4.
Notations of proposed scheme.
3.2. Preliminary
A truncated polynomial, R, with degree is defined as , where N is a positive integer and the highest degree of R. q and p are positive integers. q and p are coprime, and p is smaller than q.
3.3. IoT Devices’ Gateway Communication Phase
An IoT device captures and encrypts data with the public key of the gateway, and then generates a signature with the private key of the IoT device itself. Then, the IoT device sends the encrypted data and signature to the gateway. The gateway verifies the signature using the public key of the IoT device and decrypts data using the private key in the smart token. The gateway is a receiver in the phase. The gateway has an NTRU-based private and public key, obtaining this by randomly choosing polynomials f and g, which have to be secret. The gateway obtains the private keys ( and ) and public key, . Detailed descriptions are given in the following and illustrated in Figure 3.
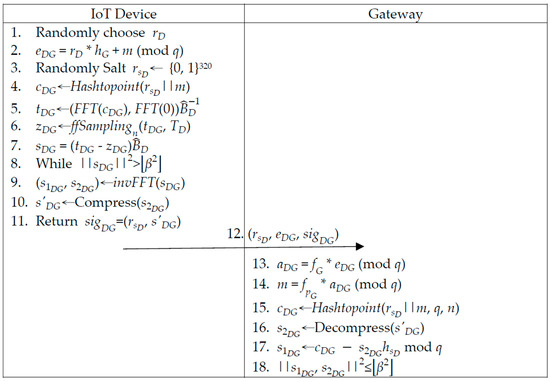
Figure 3.
IoT devices’ gateway communication phase.
Step 1: The IoT device randomly chooses polynomial and computes encrypted data, .
Step 2: The IoT device randomly generates salt and utilizes and m to generate . Then, the IoT device computes (, , ) via fast Fourier transforming () and fast-Fourier sampling () functions and checks if is in bound via .
Step 3: The IoT device utilizes to generate ( and ) via inverse fast Fourier transforming. is compressed to string . After that, the IoT device generates signature and sends (, and ) to the gateway.
Step 4: After receiving (, and ), the gateway computes . The coefficient of will be between and . Then, the gateway utilizes to recover m.
Step 5: The gateway utilizes (, , and ) to generate and decompress to . Then, the gateway utilizes (, , and ) to compute and checks if ( and ) is in bound via or rejects verification.
3.4. Gateways’ Server Communication Phase
The gateway sends the encrypted data and signature to the server. Detailed descriptions are given in the following and illustrated in Figure 4.
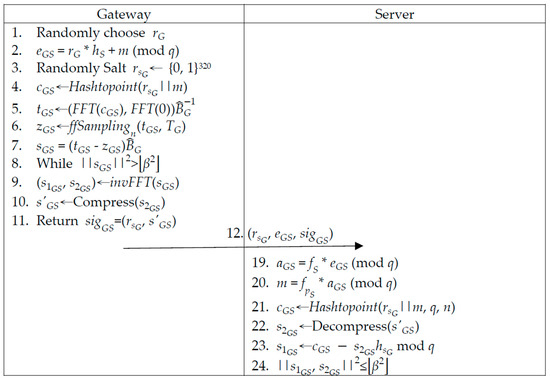
Figure 4.
Gateways’ server communication phase.
Step 1: The gateway randomly chooses polynomial and computes the encrypted data, .
Step 2: The gateway randomly generates salt and utilizes and m to generate . Then, the gateway computes (, and ) using and , and checks if is in bound via .
Step 3: The gateway utilizes to generate ( and ) via inverse fast Fourier transform. is compressed to string . After that, the gateway generates signature and sends (, and ) to the server.
Step 4: The after receiving (, and ), the server computes . The coefficient of will be between and . Then, the server utilizes to recover m.
Step 5: The server utilizes (, , and ) to generate and decompress to . Then, the server utilizes (, , and ) to compute and checks if ( and ) is in bound via or rejects verification.
4. Security Analysis
We analyze the proposed scheme below.
4.1. Correctness
Receivers in the proposed scheme (the gateway and server) compute polynomials and , respectively, where coefficients in both polynomials are between and . The whole computation is represented in Equation (17). After that, receivers recover message m, resulting in Equation (18). While recovering message m, because , the recovery of message m will be successful.
4.2. Confidentiality
If an adversary aims to recover a message through sniffing in the IoT device’s gateway communication phase, the adversary must have knowledge of the private key of gateway according to Equation (7). is stored in the smart token securely. Similarly, we can prove that an adversary cannot recover message m in the gateway’s server communication phase because they lack knowledge of the private key of server according to Equation (15). As a result, the proposed scheme can achieve confidentiality.
4.3. Integrity
Assuming that an adversary aims to modify transmitted messages, they must forge the signature generated through the Falcon signature mechanism [10]. The adversary cannot generate a signature without knowing the private key of gateway and server . As a result, integrity can be achieved by verifying the signatures.
4.4. Non-Repudiation
Because of the utilization of the signature mechanism, the IoT device and gateway cannot deny sending the message. IoT devices use private key polynomial vectors for signatures ( and ) to generate as a part of signature , and the gateway verifies using public key polynomial vectors for the signature of IoT device . Because can only be verified using , IoT devices cannot deny sending the message to the gateway. By the same token, the gateway cannot deny sending the message to the server. As a result, non-repudiation can be achieved.
5. Performance Analysis
We analyzed the performance of NTRUEncrypt [9,27] and the Falcon signature mechanisms [10,28] with different security levels utilized in the proposed scheme. We used a personal computer (PC) with an i7-7000 3.60 GHZ 8-core central processing unit (CPU, Intel Corporation, Santa Clara, US), 32 GB random-access memory (RAM, Kingston Technology Corporation, Fountain Valley, CA, USA), and Windows 10 Education as an operation system (OS, Microsoft Corporation, Washington, DC, USA). We also used a Raspberry Pi 3B module (Raspberry Pi Foundation, Cambridge, UK) with an ARM Cortex-A53 1.4 GHz 4-core CPU (Arm Holdings plc, Cambridge, UK), 1 GB RAM (Micron Technology, Inc., Boise, US), and Raspberry Pi OS (Raspberry Pi Foundation, Cambridge, UK). We executed NTRUEncrypt [9,27] and Falcon signature mechanisms [10,28] with different security levels and recorded the execution time. Results of the performance analysis of the NTRUEncrypt [9,27] and Falcon signature mechanisms [10,28] are shown in Table 5 and Table 6, respectively. As a result, the time required to execute NTRUEncrypt [9,27] on a PC is less than 2 s, while in Raspberry Pi 3B, the time required is less than 20 s. Executing the Falcon signature mechanism [10,28] on a PC takes less than 3 s, but executing Falcon-512 in Raspberry Pi 3B takes about 5 times longer than executing Falcon-256 does.

Table 5.
Performance analysis of NTRUEncrypt.

Table 6.
Performance analysis of Falcon signature mechanism.
According to the results above, we can estimate the execution time of the proposed scheme with different security levels. We defined as the time required for the IoT device to execute NTRUEncrypt [9,27], as the time the gateway requires to execute NTRUEncrypt [9,27], and as the time the server requires to execute NTRUEncrypt [9,27]. We also defined as the time the IoT device takes to execute the Falcon signature mechanism [10,28]. We defined as the time the gateway takes to execute the Falcon signature mechanism [10,28], and as the time the server takes to execute the Falcon signature mechanism [10,28]. Results of the computational complexity and performance time of the proposed scheme are shown in Table 7. In an IoT device’s gateway communication phase, the IoT device will take 24.409 s, and the gateway will take 1.5582 s with a medium level of NTRUEncrypt [9,27] and Falcon-64 [10,28]. If the highest level of NTRUEncrypt [9,27] and Falcon-512 [10,28] is applied in the IoT device’s gateway communication phase, the IoT device will take 229.74 s, and the gateway will take 4.6346 s. The execution of the IoT device’s gateway communication phase will take 25.9627 to 234.3746 s. In the gateway’s server communication phase, the gateway and server will take 1.5582 s separately with a medium level of NTRUEncrypt [9,27] and Falcon-64 [10,28]. If the highest level of NTRUEncrypt [9,27] and Falcon-512 [10,28] is applied in the gateway’s server communication phase, the gateway and server will take 4.6346 s separately. The execution of the gateway’s server communication phase will take 3.1164 to 9.2692 s. Compared with other research on similar system structures, the proposed scheme takes much more time. For examples, Shang et al.’s scheme takes at least 0.895 ms [29], and Zhang et al.’s scheme takes 0.75 s [30]. However, the proposed scheme achieves encryption, signature, and device authentication at once, so the number of execution rounds is smaller than that in Shang et al.’s [29] and Zhang et al.’s scheme [30] while maintaining security features. Moreover, the proposed scheme applies quantum-resistant cryptographic algorithms: the NTRU [9] and Falcon signature mechanism [10]. A performance analysis of the proposed scheme is shown in Table 7.

Table 7.
Performance analysis of proposed scheme.
6. System Implementation
We utilized Raspberry Pi 3B with temperature and humidity sensor module DHT11 as an IoT device, a PC as a gateway, and a server. We used Python as the programing language for gathering data, NTRUEncrypt [9,27], and Falcon signature mechanisms [10,28]. The PC was connected to a smart token that stored private keys of the gateway. We installed VMWare ESXi in the server and executed a virtual machine with Ubuntu Linux as the OS, with 2 GB RAM and a 50 GB hardware capacity, and MySQL phpMyAdmin for storing the information on device registration, the cipher, and the signature. Table 8 presents specifications of the proposed system, and Figure 5 illustrates the system implementation structure of the proposed system.

Table 8.
Specifications of proposed system.
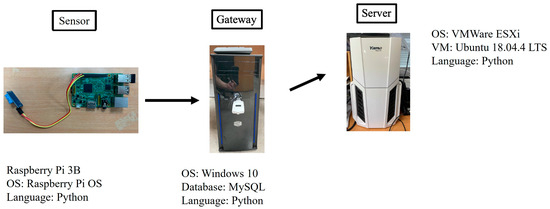
Figure 5.
System implementation structure of proposed system.
Raspberry Pi was registered in the server first (Figure 6), and the server stored information on Raspberry Pi in the database utilizing the hostname and MAC address (Figure 7). We can see that Raspberry Pi’s information (Figure 6) will appear in server (Figure 7) if Raspberry Pi registered successfully.
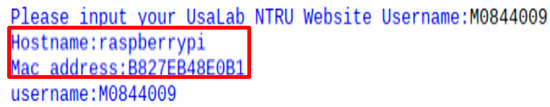
Figure 6.
Raspberry Pi’s registration request.
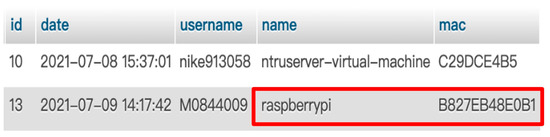
Figure 7.
Server storing information on Raspberry Pi in database.
After gathering data from DHT11, Raspberry Pi transformed data into binary (Figure 8), encrypted binary data (Figure 9), and signed binary data (Figure 10) using the scheme proposed above, and then Raspberry Pi transmitted data to the gateway through wireless communication.
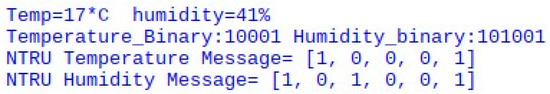
Figure 8.
Raspberry Pi transformed data to binary.
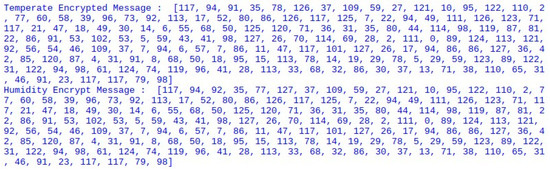
Figure 9.
Raspberry Pi encrypted data.
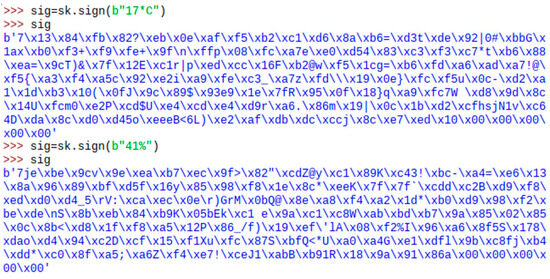
Figure 10.
Raspberry Pi signed data.
After receiving data, as shown in Figure 11 and Figure 12, the gateway verified the signature and decrypted data using the private key in the smart token, as shown in Figure 13. As a result, the gateway verified the signature successfully and showed that the signature was correct in Figure 14; the gateway also decrypted data successfully, as shown in Figure 15, which shows the same results as those in Figure 8.
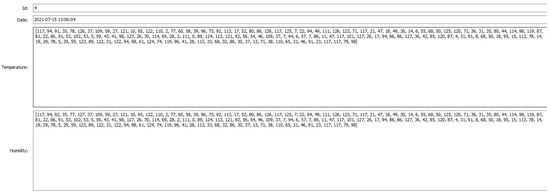
Figure 11.
Gateway receiving encrypted data.
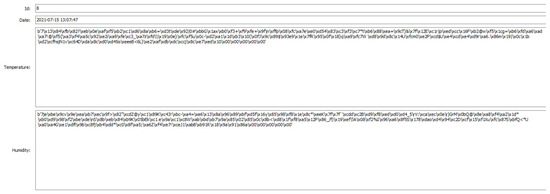
Figure 12.
Gateway receiving signed data.
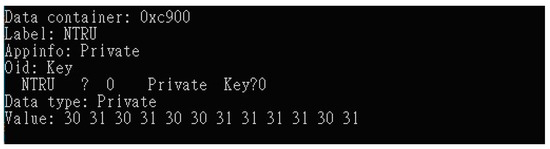
Figure 13.
Private key in smart token.
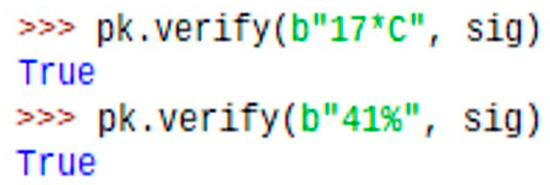
Figure 14.
Gateway verifying signature.
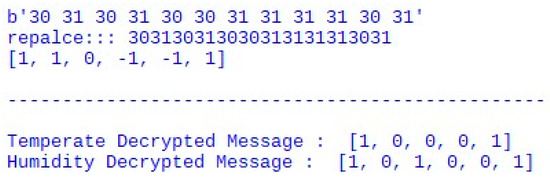
Figure 15.
Gateway decrypting data.
The gateway encrypted and signed the data using the private key in the smart token, as shown in Figure 16 and Figure 17, and the gateway sent the data to the server, as shown in Figure 18 and Figure 19.

Figure 16.
Gateway encrypting data.
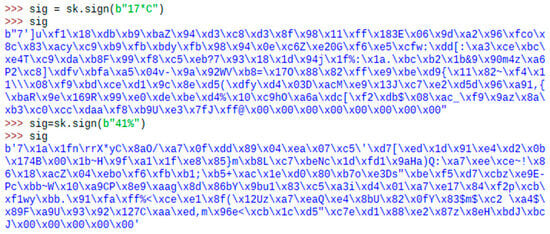
Figure 17.
Gateway signing data.
Figure 18.
Encrypted data being stored in server.
Figure 19.
Signed data being stored in server.
7. Result and Discussions
We present a discussion on the research results and limitations of this research.
We proposed a device authentication and secure communication system for AIoT environments using NTRU [9] and Falcon signature mechanisms [10]. NTRU and Falcon signature mechanisms have been proven to be quantum-resistant public key cryptosystems [9,10,20]. Although the NTRU cannot be used in post-quantum cryptography standardization, it is still applied widely because of its advantages over other lattice-based schemes [9,20,21]. Moreover, the Falcon signature mechanism [10] is a lattice-based compact signature with advantages over the NTRU, so the NTRU [9] and Falcon signature mechanisms [10] can be integrated. Because of reasons above, we could design a scheme that allows the execution of encryption, authentication, and signature mechanisms at once. However, since the NTRU [9] fell short among the candidates of post-quantum cryptography standardization, other lattice-based schemes can be discussed in the future, such as CRYTSTAL-Kyber [31] or CRYSTALS-Dilithium digital signature algorithms [32].
This research has limitations. Although the proposed scheme was able to achieve security features, such as quantum resistance, it did not seem ideal in terms of execution time. The results will limit the implementation possibilities of AIoT environments. We take smart medical or telemedicine systems with AIoT as examples. Biodata are measured by wearable devices and transmitted through gateways to a server, and the server can analyze and predict each patient’s health condition or possible disease using AI algorithms. Biodata may not be transmitted every second, so the proposed scheme can be applied in this scenario. If data have to be transmitted every second, the proposed scheme is not suitable unless a redeployment of end devices better than that provided by the Raspberry Pi 3B module is carried out in the system implementation of the proposed scheme. With the rapid development of PQC, hardware circuit and system design has been discussed. For example, Xie et al. proposed a tutorial for PQC and introduced related techniques [33].
8. Conclusions
The ability to collect data in real time through sensors and analyze data using machine learning algorithms is enabling AIoT to expand its possibilities and applications into many sectors. AIoT creates value for sustainable industries by combining artificial intelligence, the Internet of Things, and big data analysis. Nevertheless, AIoT requires security measures suitable for the environment in which it operates because of its reliance on networks that are exposed to adversaries from any internet location. Due to the limited resources of devices in AIoT systems, which can lead to a loss of attractive features, traditional security measures may not be an appropriate solution. We designed and evaluated a device authentication and secure communication system with PQC for AIoT environments that utilized PQC to provide a lightweight security scheme while resisting attacks from quantum computers. We chose NTRU and Falcon signature mechanisms to design and implement secure algorithms. We analyzed the security and performance of the proposed scheme and proved that it can achieve confidentiality, integrity, and non-repudiation meanwhile also achieving efficiency.
Author Contributions
Conceptualization, Y.-J.C., C.-L.H., and T.-W.L.; methodology, Y.-J.C. and C.-L.H.; software, Y.-J.C.; validation, Y.-J.C. and T.-W.L.; formal analysis, Y.-J.C.; writing—original draft preparation, Y.-J.C.; writing—review and editing, T.-W.L., C.-L.H., and J.-S.L.; visualization, Y.-J.C. and T.-W.L.; supervision, C.-L.H. and J.-S.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Murphy, K.; Di Ruggiero, E.; Upshur, R.; Willison, D.J.; Malhotra, N.; Cai, J.C.; Malhotra, N.; Lui, V.; Gibson, J. Artificial intelligence for good health: A scoping review of the ethics literature. BMC Med. Ethics 2021, 22, 14. [Google Scholar] [CrossRef] [PubMed]
- Lin, T.-W.; Hsu, C.-L. Privacy-Preserved Hierarchical Authentication and Key Agreement for AI-Enabled Telemedicine Systems. In Proceedings of the 2021 International Conference on Security and Information Technologies with AI, Internet Computing and Big-Data Applications, Taichung City, Taiwan, 18–20 November 2021; pp. 134–142. [Google Scholar]
- Li, S.; Xu, L.D.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Wong, A.M.; Hsu, C.-L.; Le, T.-V.; Hsieh, M.-C.; Lin, T.-W. Three-Factor Fast Authentication Scheme with Time Bound and User Anonymity for Multi-Server E-Health Systems in 5G-Based Wireless Sensor Networks. Sensors 2020, 20, 2511. [Google Scholar] [CrossRef] [PubMed]
- Cheng, S.M.; Hong, B.K.; Hung, C.F. Attack Detection and Mitigation in MEC-Enabled 5G Networks for AIoT. IEEE Internet Things Mag. 2022, 5, 76–81. [Google Scholar] [CrossRef]
- Nozari, H.; Szmelter-Jarosz, A.; Ghahremani-Nahr, J. Analysis of the Challenges of Artificial Intelligence of Things (AIoT) for the Smart Supply Chain (Case Study: FMCG Industries). Sensors 2022, 22, 2931. [Google Scholar] [CrossRef] [PubMed]
- Dyakonov, M. When will useful quantum computers be constructed? Not in the foreseeable future, this physicist argues. Here’s why: The case against: Quantum computing. IEEE Spectr. 2019, 56, 24–29. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Hoffstein, J.; Pipher, J.; Silverman, J.H. NTRU: A ring-based public key cryptosystem. In Proceedings of the Algorithmic Number Theory, Third International Symposium, ANTS-III, Portland, OR, USA, 21–25 June 1998; pp. 267–288. [Google Scholar]
- Fouque, P.-A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon: Fast-Fourier Lattice-Based Compact Signatures over NTRU. Available online: https://falcon-sign.info/falcon.pdf (accessed on 22 December 2023).
- Lei, X.; Liao, X. NTRU-KE: A Lattice-based Public Key Exchange Protocol. IACR Cryptol. ePrint Arch. 2013, 2013, 718. [Google Scholar]
- Rong, G.; Xu, Y.; Tong, X.; Fan, H. An edge-cloud collaborative computing platform for building AIoT applications efficiently. J. Cloud Comput. 2021, 10, 36. [Google Scholar] [CrossRef]
- Ricquebourg, V.; Menga, D.; Durand, D.; Marhic, B.; Delahoche, L.; Loge, C. The Smart Home Concept: Our immediate future. In Proceedings of the 2006 1ST IEEE International Conference on e-Learning in Industrial Electronics, Hammamet, Tunisia, 18–20 December 2006; pp. 23–28. [Google Scholar]
- Lucke, D.; Constantinescu, C.; Westkämper, E. Smart Factory—A Step towards the Next Generation of Manufacturing. In Proceedings of the Manufacturing Systems and Technologies for the New Frontier: The 41st CIRP Conference on Manufacturing Systems, Tokyo, Japan, 26–28 May 2008; pp. 115–118. [Google Scholar]
- Schaffers, H.; Komninos, N.; Pallot, M.; Trousse, B.; Nilsson, M.; Oliveira, A. Smart Cities and the Future Internet: Towards Cooperation Frameworks for Open Innovation. In The Future Internet: Future Internet Assembly 2011: Achievements and Technological Promises; Springer: Berlin/Heidelberg, Germany, 2011; pp. 431–446. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; De, D. Edge computing for Internet of Things: A survey, e-healthcare case study and future direction. J. Netw. Comput. Appl. 2019, 140, 1–22. [Google Scholar] [CrossRef]
- Post-Quantum Cryptography. Available online: https://csrc.nist.gov/Projects/Post-Quantum-Cryptography (accessed on 18 March 2024).
- Kim, J.; Park, J.H. NTRU+: Compact Construction of NTRU Using Simple Encoding Method. IEEE Trans. Inf. Forensics Secur. 2023, 18, 4760–4774. [Google Scholar] [CrossRef]
- Perlner, R.A.; Cooper, D.A. Quantum resistant public key cryptography: A survey. In Proceedings of the 8th Symposium on Identity and Trust on the Internet, Gaithersburg, MD, USA, 14–16 April 2009; pp. 85–93. [Google Scholar]
- Mailloux, L.O.; Lewis, C.D., II; Riggs, C.; Grimaila, M.R. Post-Quantum Cryptography: What Advancements in Quantum Computing Mean for IT Professionals. IT Prof. 2016, 18, 42–47. [Google Scholar] [CrossRef]
- Bi, J.; Han, L. Lattice Attacks on NTRU Revisited. IEEE Access 2021, 9, 66218–66222. [Google Scholar] [CrossRef]
- Ahmed Othman, K.; Shaimaa Khudhair, S.; Hind Jumaa, S.; Zainab Khyioon, A. Subject Review: Comparison between RSA, ECC & NTRU Algorithms. Int. J. Eng. Res. Adv. Technol. 2019, 5, 11–15. [Google Scholar] [CrossRef]
- Loriya, H.T.; Kulshreshta, A.; Keraliya, D.R. Security analysis of various public key cryptosystems for authentication and key agreement in wireless communication network. Int. J. Adv. Res. Comput. Commun. Eng. 2017, 6, 267–274. [Google Scholar]
- Singh, G. NTRU-Python3. Available online: https://github.com/topShotZexN/NTRU-Python3 (accessed on 22 December 2023).
- Prest, T. falcon.py. Available online: https://github.com/tprest/falcon.py (accessed on 22 December 2023).
- Shang, Z.; Ma, M.; Li, X. A Secure Group-Oriented Device-to-Device Authentication Protocol for 5G Wireless Networks. IEEE Trans. Wirel. Commun. 2020, 19, 7021–7032. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, B.; Wu, J.; Liu, B.; Chen, R.; Chang, J. Efficient and Privacy-Preserving Blockchain-Based Multifactor Device Authentication Protocol for Cross-Domain IIoT. IEEE Internet Things J. 2022, 9, 22501–22515. [Google Scholar] [CrossRef]
- Schwabe, P.; Avanzi, R.; Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Seiler, G.; Stehle, D. CRYSTALS-Kyber Algorithm Specifications and Supporting Documentation (Version 3.02). 2021. Available online: https://www.pq-crystals.org/kyber/data/kyber-specification-round3-20210804.pdf (accessed on 1 February 2024).
- Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Dilithium: A Lattice-Based Digital Signature Scheme. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 238–268. [Google Scholar] [CrossRef]
- Xie, J.; Zhao, W.; Lee, H.; Roy, D.B.; Zhang, X. Hardware Circuits and Systems Design for Post-Quantum Cryptography—A Tutorial Brief. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 1670–1676. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).