Abstract
In the contemporary era, Vehicular Ad Hoc Networks (VANETs) have emerged as a vital technology in intelligent transportation systems, substantially enhancing the overall travel experience by providing advanced services to vehicles while ensuring driver safety. Despite the notable improvements, the inherent complexity of VANETs presents persistent security challenges, encompassing issues such as privacy preservation for vehicles, message authentication, and constraints in computational power and network bandwidth. Various authentication protocols have been designed for VANETs. However, many of these protocols exhibit significant vulnerabilities, rendering them insecure and unreliable in the face of diverse security threats, such as denial of service, replay, forgery, and impersonation attacks. Moreover, some existing schemes encounter limitations, including high computational complexity and the introduction of additional communication overhead and computational costs. To tackle these concerns, we designed a lightweight and secure identity authentication protocol based on elliptic curve cryptography with the objective of furnishing an effective and secure data transmission mechanism across a public communication channel for the Internet of Vehicles. In addition, we introduce Physically Unclonable Functions (PUFs) to ensure physical layer security during the communication process. A detailed security analysis demonstrates that the proposed protocol is resilient against various attacks. Through a comparative analysis with existing relevant protocols, in scenarios with a high density of vehicles, the algorithm demonstrates significantly lower computational costs and communication overhead than the related protocols, indicating that the proposed protocol is lightweight and efficient. Consequently, the empirical findings indicate that our protocol surpasses others in terms of reliability, user convenience, and practicality for ensuring secure data transmission within VANETs.
1. Introduction
With the rapid development of technology, Vehicular Ad Hoc Network (VANET) technology has emerged as a revolutionary advancement in the modern automotive industry. By closely integrating vehicles with the internet, VANETs provide drivers with unparalleled experiences of intelligence, convenience, and safety. Obviously, with the increasing number of vehicles in urban areas [1,2], intelligent transportation systems have been playing a crucial role in urban traffic management, to the extent that support from VANETs has become a vital pillar in ensuring road safety [3]. Hence, VANETs have garnered significant attention from both industry and academia [4].
In Vehicular Ad Hoc Networks (VANETs), the On-Board Units (OBUs) serve as a tamper-resistant device installed in vehicles, capable of storing critical vehicle information such as identity and certain cryptographic computations. Additionally, the system involves a Trusted Authority (TA) and numerous Road Side Units (RSUs). RSUs are positioned along the roadside, serving as communication bridges between the TA and vehicles. The TA is tasked with registering both RSUs and vehicles, as well as providing necessary communication assistance. Within VANETs, two communication modes exist: Vehicle-to-Vehicle (V2V), where vehicles in motion can communicate with each other, and Vehicle-to-Infrastructure (V2I), enabling communication between moving vehicles and roadside infrastructure. Both of these modes can utilize the Dedicated Short-Range Communication (DSRC) standard [5,6], operating over open wireless communication channels. Due to the fact that V2V and V2I communications take place over open wireless communication channels, they are vulnerable to a variety of attacks, including interference, eavesdropping, and spoofing [7]. This reality not only exposes potential threats to information exchange between vehicles but also underscores the urgency of identity authentication in VANETs. Additionally, by employing side-channel attacks [8], partial information stored in the On-Board Units can be obtained, leading to privacy leakage in vehicles.
In this era of information, vehicles are no longer standalone entities but are interconnected within the expansive realm of cyberspace. This integration renders VANET security highly susceptible to network threats like identity theft, unauthorized access, and malicious attacks, all of which can severely impact its safety. Therefore, ensuring the security of both vehicles and their user identities is of paramount importance. As a crucial component in ensuring the security of VANET systems, the identity authentication mechanism enables the straightforward identification of all authenticated vehicles [9,10]. Simultaneously, the identity authentication mechanism must strike a delicate balance between convenience and security to ensure the protection of users’ privacy rights.
The central research contributions of this paper are delineated as follows:
- We propose an improved, lightweight identity authentication protocol with conditional privacy protection suitable for VANETs. Leveraging elliptic curve cryptography, the protocol ensures a balance between lightweight characteristics, security, and privacy through lightweight encryption operations such as hash functions, concatenation, XOR, and PUF technology.
- We conducted in-depth formal and informal analyses of the security attributes of the proposed protocol. Formal verification was achieved through Burrows-Abadi-Needham (BAN) logic proof and the Real-Or-Random (ROR) model to demonstrate the protocol’s resistance to security threats. Additionally, we showcased the security resilience of the proposed protocol against relevant attacks.
- We conducted a performance analysis of existing authentication schemes [11,12,13,14,15], demonstrating that the proposed scheme outperforms others in various aspects, such as communication cost and computational cost, in most cases.
- We conducted simulation and emulation of the proposed protocol using discrete event simulators OMNeT++ 5.6.2 and Simulation of Urban Mobility 1.8.0 (SUMO), an open-source traffic simulation software, to illustrate its practical feasibility in real-world scenarios.
The remaining sections of this paper are structured as follows. Section 2 presents relevant research on VANET identity authentication. Section 3 introduces some fundamental knowledge related to the proposed protocol. The specific protocol process is outlined in Section 4. Section 5 showcases the security analysis and protective mechanisms of the proposed protocol, while Section 6 analyzes and verifies the performance of the scheme through simulation. Finally, conclusions are drawn in Section 7, along with prospects for future research in VANET security.
2. Related Studies
In this section, we will discuss the existing authentication schemes for VANETs. Each authentication approach utilizes distinct communication modes and cryptographic principles, resulting in varying degrees of security and performance. In 2008, Lu et al. [16] introduced the concept of conditional privacy security, aiming to protect the privacy of OBUs from attackers while preventing malicious OBUs from interfering with normal communication. The general public cannot track OBUs, but the Trusted Authority (TA) has the capability to identify the real identities of exposed OBUs. In the same year, Zhang et al. [17] proposed an identity-based authentication method with conditional privacy, which eliminates the requirement for certificates between RSUs and vehicles. The following year, Zhang et al. [18] designed a novel key management protocol aimed at ensuring the security of VANET communications. Nevertheless, Lee et al. [19] later found that the scheme proposed by Zhang et al. [18] was vulnerable to threats like denial-of-service and replay attacks. Additionally, Lee et al. [19] proposed a more secure and scalable protocol based on bilinear pairing. In 2015, He et al. [20] proposed an identity-based authentication method for VANETs, eliminating the need for bilinear pairing and thereby reducing processing costs. Following He et al.’s approach [20], subsequent modifications [21,22] were proposed to further enhance performance. Lo and Tsai [23] introduced a pairing-free authentication method in 2016 to maintain computational complexity. Dua et al. [24] introduced a two-tier identity authentication protocol utilizing elliptic curve cryptography (ECC), aiming at safeguarding the security of vehicle communication in intelligent transportation systems. However, it is unable to defend against cluster head impersonation attacks, where any registered yet dishonest cluster head can manipulate regular vehicles. Li et al. [25] introduced an identity authentication scheme for UAV networks based on elliptic curve cryptography. Their design encompasses three stages: ECC certificate generation, identity authentication, and key compatibility verification. However, their scheme led to substantial computational costs. Bagga et al. [26] proposed a novel bidirectional identity authentication and key agreement protocol aimed at enhancing the security, anonymity, and resilience of VANETs within intelligent transportation systems. The proposed method achieves low communication and computational overhead, along with higher security. Additionally, due to its lower throughput, it is suitable for networks in sparsely populated areas. Yang et al. [27] devised a certificateless key establishment protocol based on elliptic curve cryptography to address the key escrow problem in traditional identity-based cryptography (IBC) protocols. However, their protocol is susceptible to physical/cloning attacks. In 2020, Li et al. [28] introduced a lightweight key agreement scheme based on hashing. However, Shamshad et al. [29] conducted an evaluation of their study, uncovering that the scheme [28] lacks guarantees of untraceability and anonymity and is vulnerable to threats like impersonation and RSU key leakage attacks. In the same year, Alshudukhi et al. [30] developed an identity verification technique that supports privacy factors, countering potential side-channel attacks by regularly updating the Tamper-proof Device (TPD). Similarly, Cui et al. [31] also opted for regularly updating information to resist side-channel attacks, ensuring vehicles complete identity authentication securely. Aman et al. [32] introduced a VANET authentication scheme based on physical unclonable functions to minimize costs and network traffic while protecting the network against clone attacks. In order to minimize authentication overhead and improve network throughput, the network is organized into three tiers: roadside units, roadside unit gateways, and trusted authorities. Simulation results demonstrate a significant reduction in MAC/PHY overhead and enhanced security against various attacks. While the scheme achieves lower throughput and bandwidth requirements, it may not be suitable for densely populated areas. Gope et al. [33] introduced a lightweight, privacy-preserving dual-factor authentication scheme for IoT devices utilizing physical unclonable functions. However, due to their oversight of message loss during transmission, their scheme is susceptible to desynchronization attacks [34]. Kudva et al. [35] introduced an approach to enhance VANET security during vehicle-to-vehicle and vehicle-to-infrastructure communication. They implemented a secure AODV protocol to safeguard the network against black hole attacks in the event of network failures. Additionally, the scheme employs cryptographic function-based encryption and decryption methods to achieve better performance. This approach has demonstrated improved performance in terms of packet delivery ratio, packet loss rate, latency, and overhead, but it has not achieved high throughput. Son et al. [36] proposed a blockchain-based authentication framework considering handover for V2I communication. However, the paper lacks a clear explanation regarding the storage or calculation of certain parameters, and the method may be susceptible to smart contract capture and dictionary attacks if vehicle verification can be bypassed to initiate authentication. Feng et al. [37] introduced an efficient privacy-preserving authentication model leveraging blockchain technology. They extended its architecture to safeguard and streamline authentication processes within vehicular ad hoc networks. This model supports member identity verification and optimizes time utilization by circumventing verification through certificate revocation lists. Ahmed et al. [38] also proposed a blockchain-based authentication protocol for VANET. This protocol is adept at mitigating diverse attacks while concurrently reducing the computational overhead and storage footprint associated with authentication messages. Tandon et al. [39] introduced a decentralized architecture based on dual blockchains for vehicle authentication and secure, efficient communication within the network. This approach employs separate blockchains for identity verification, message sharing, and enhancing network efficiency, responsiveness, and security.
3. Preliminary
3.1. VANET Architecture
Vehicular Ad Hoc Network (VANET) is a special form of Mobile Ad Hoc Network (MANET), involving communication between vehicles and between vehicles and roadside infrastructure. The architecture of VANETs (as illustrated in Figure 1) typically consists of several key components:
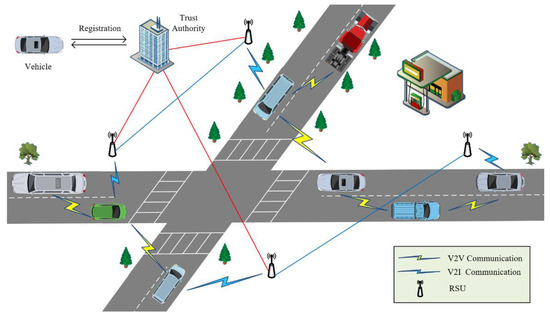
Figure 1.
The system structure of the VANET.
On-Board Units (OBUs): On-Board Units are integral components of vehicular ad hoc networks (VANETs). They are dedicated communication devices installed in vehicles to facilitate communication between vehicles and between vehicles and roadside infrastructure. Numerous OBUs employ DSRC technology, functioning within the 5.9 GHz frequency band. Furthermore, certain OBUs may utilize cellular networks like 4G and 5G for communication. Typically, OBUs integrate sensors like GPS, accelerometers, and gyroscopes to furnish vehicle-related data. It is important to highlight that OBUs play a vital role in ensuring the security and privacy of communication within VANETs. They are responsible for implementing encryption and authentication mechanisms to prevent unauthorized access and malicious activities.
Road Side Units (RSUs): Roadside Units are infrastructure components within VANETs, typically strategically deployed along roadways, intersections, and other locations to provide optimal communication coverage. RSUs are outfitted with network equipment utilizing short-range wireless communication standards like IEEE 802.11p [40]. This enables them to establish wireless connections with OBUs installed in vehicles. RSUs efficiently gather and distribute real-time information regarding traffic conditions, road hazards, and other pertinent data to vehicles. This facilitates the enhancement of traffic signal timing, traffic flow management, and the alleviation of roadway congestion.
Trusted Authority (TA): In the context of vehicular ad hoc network communication systems, the Trusted Authority is the entity responsible for managing and implementing network security, often regarded as the highest authority within VANETs. Its role is vital in ensuring the authenticity, integrity, and confidentiality of communication between vehicles and between vehicles and infrastructure components. Furthermore, the TA can engage in partnerships with other stakeholders, such as government bodies, industry institutions, and network operators, to foster a secure and reliable environment for VANET communication. The TA is generally regarded as entirely trustworthy and impervious to attacks.
3.2. Threat Models
Threat modeling, as a crucial process for identifying and analyzing potential security risks and vulnerabilities, holds unparalleled significance in the development of open network protocols like VANETs. By conducting threat modeling, effective planning and implementation of corresponding security controls and strategies can be achieved, ensuring the resilience and reliability of VANET systems. In this paper, we will employ commonly used threat models, such as the Dolev-Yao (DY) threat model [41] and the Canetti-Krawczyk (CK) adversarial model [42], to describe the capabilities of adversaries. The DY model offers a simplified and abstract framework for assessing the security of encryption protocols, delineating adversaries’ capabilities in accessing communication channels. The CK model introduces a more realistic and computationally feasible adversary model, taking into account attackers’ polynomial-time computational constraints. This makes it more suitable for analyzing practical systems and key exchange protocols. Hence, we assume that adversary possesses the following capabilities:
- Adversary is capable of freely accessing any message transmitted over the public communication channel and can modify, delete, intercept, and replay messages at will.
- is cognizant of the public identities of all protocol participants, and the identity of TA is publicly known.
- can be either an insider or an outsider. Any registered or unregistered vehicle could potentially be adversary .
- During the session key establishment process, adversary can steal and compromise session states for partial secret information stored in insecure storage within OBUs.
- has sufficient computational power to conduct exhaustive guessing attacks within polynomial time.
3.3. System Network Model and Assumptions
In this section, we present the fundamental network model and assumptions of the proposed protocol. The VANET network model utilized in this paper is depicted in Figure 2. The Trusted Authority (TA) is deemed entirely reliable, boasting ample computational capabilities and storage capacity. Vehicles are outfitted with tamper-resistant On-Board Units (OBUs) designed to store sensitive data and conduct associated computations. However, compared to TA, their computational power and storage space are extremely limited. In this network model, the protocol operates at two communication levels: one at the server level and the other at the vehicle level. At the server level, which operates within a secure channel, the Trusted Authority (TA) resides. It stores detailed information about registered vehicles and partial credentials. Additionally, it performs initialization and registration operations for vehicles, allowing them to obtain relevant authentication parameters. The TA supports elements at the vehicle level and assists authenticated vehicles in identifying the legitimate identities of other vehicles during the authentication process. At the vehicle level, communication between vehicles occurs using DSRC for information exchange and authentication processes. This layer operates within a non-secure public channel. In the event of an OBU malfunction in a vehicle, rendering it unable to broadcast evacuation information, other vehicles can serve as relay nodes to ensure uninterrupted communication. This means that the malfunction or evacuation of a single vehicle does not disrupt communication across the entire network, thereby guaranteeing the stability of authentication communication at the vehicle level.
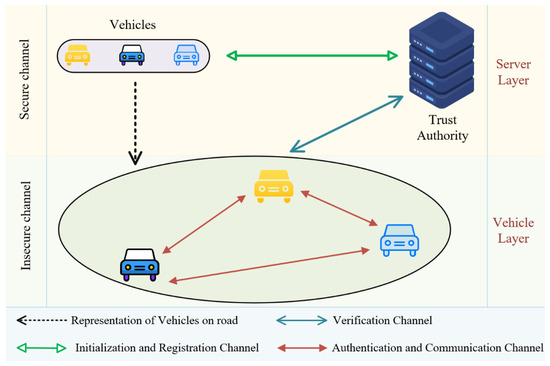
Figure 2.
Network model.
3.4. Physical Unclonable Function
The Physical Unclonable Function (PUF) is a hardware-based security technology that relies on the microscopic irregularities and physical characteristics of hardware devices to generate unique identifiers. PUF generally functions using a challenge–response mechanism. When presented with a challenge , the PUF generates a distinct response based on its physical traits. This response serves as a unique identifier for the device. Due to the inherent irregularities in the hardware manufacturing process, even devices of the same model exhibit slight variations in their physical characteristics. This uniqueness makes PUF responses unclonable, meaning identical hardware models cannot generate the same response. As a result, the security of the system is enhanced. An ideal PUF would provide various features, such as reliability, unpredictability, and uniqueness, effectively safeguarding sensing devices against side-channel attacks [43], cloning attempts, and tampering threats [11]. PUF systems typically exhibit the ability to handle diversity in challenging situations. Even if the same challenge is issued multiple times, variations in environmental conditions or device noise cause the PUF-generated responses to differ. If the following conditions are met, a PUF can be considered -secure [44]:
- For any two Physical Unclonable Functions, and , and for any input , holds, where represents the Hamming distance.
- For any and any input , holds.
- For any and any input , holds. This condition states that when multiple inputs are used to evaluate different PUFs, the minimum entropy of the PUF outputs must be greater than with high probability [45]. Here, represents the error rate, represents the message length, and represents two different challenge messages.
3.5. Notation Table
The notations used in this paper and their corresponding explanations are shown in Notation table in Abbreviations section below.
4. Discussion
In this section, we will provide a detailed explanation of the proposed identity authentication protocol, which involves two entities: vehicles and the trusted authority. The protocol is divided into four main phases: initialization, registration, authentication, and communication. In the initialization and registration phases, communication between entities occurs via dedicated channels, while in the authentication phase, communication takes place over non-secure channels. Descriptions of each phase will be provided in subsequent sections.
4.1. Initialization Phase
During this phase, relevant parameters will be generated and sent to the vehicles, laying the foundation for subsequent authentication communications in the protocol. Communication during the initialization setup process will be carried out over a secure channel. The steps in this phase are as follows:
First, selects an elliptic curve over a finite field and determines a suitably sized prime number and generator . selects a random number () over the chosen finite field . This random number will serve as the server’s private key. Then, performs scalar multiplication on the random number and the generator point over the elliptic curve , denoting the result as , which serves as the server’s public key, namely, . selects two one-way hash functions, denoted as , where and . Additionally, elects a secure symmetric encryption algorithm such as the AES algorithm. Finally, stores its own public–private key pair and distributes to all participating vehicles in the protocol.
4.2. Registration Phase
During this phase, all vehicles participating in the protocol need to undergo initial registration at the TA. Over a secure channel, communication for the entire registration process will be conducted, as this phase involves handling sensitive information that will be utilized for authentication purposes in the future. The registration process details are depicted in Figure 3.
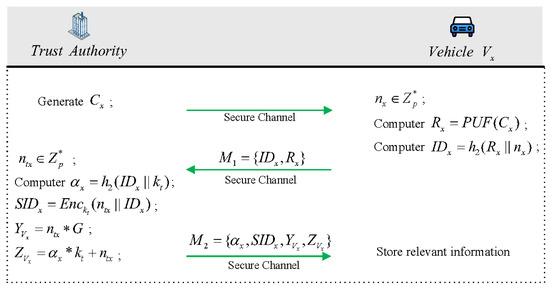
Figure 3.
Registration phase.
After receiving the challenge message from the TA, vehicle computes to generate the response message, which is embedded in the of vehicle . Following this, vehicle proceeds by selecting a random number and subsequently storing it within . The vehicle’s identity is derived by calculating the hash value of the concatenation of the response and the random number. Afterward, the vehicle transmits message to the TA. Upon reception of message , the TA saves the challenge–response pair associated with vehicle into the database and, subsequently, elects another random number to function as a temporary key. Afterwards, computations are executed to derive and , which will be used for the subsequent authentication and serve as pseudo-identity for vehicle , respectively. The pseudo-identity will be stored in the TA’s database. Then, the TA will calculate and for constructing the session key. Ultimately, the pertinent information is encapsulated within message and dispatched to vehicle , whereupon it is stored after receipt.
4.3. Authentication Phase
During this phase, vehicles authenticate each other to ensure secure communication for subsequent exchanges. During the authentication phase, vehicles can verify each other’s identities using both insecure and secure channels. Secure channel communication is exclusively utilized when vehicles verify each other’s identities with the TA, while other communications can occur over insecure channels, enabling V2V communication by DSRC mode over the public channel. Figure 4 provides a detailed illustration of this phase.
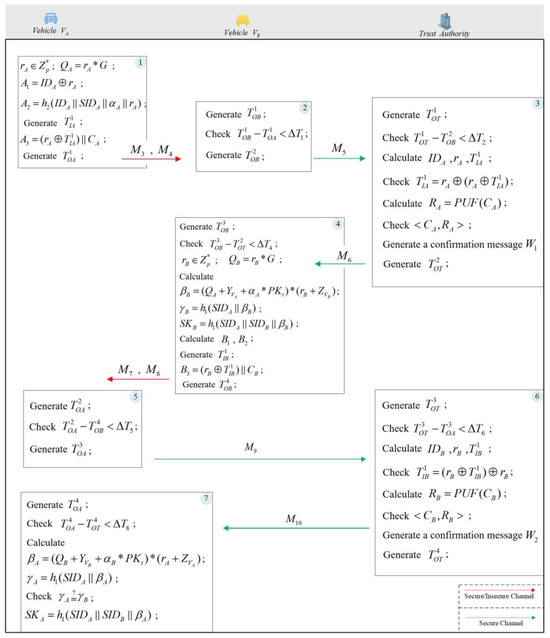
Figure 4.
Authentication phase.
- The vehicle selects a random integer and calculates the following values , , and . Then obtain the current timestamp and calculate . Finally, obtain the current timestamp again and send the messages and to vehicle .
- Vehicle , upon receiving messages and , obtains the current timestamp and retrieves the timestamp from the messages. Then, it calculates and verifies if the inequality holds. If the inequality is not satisfied, terminates the authentication process. Otherwise, if the inequality holds, obtains the current timestamp and sends message to TA.
- TA verifies the freshness of the message, after receiving message , by selecting the current timestamp and checking whether the inequality holds true. If the inequality does not hold true, the authentication process is terminated. Otherwise, the TA proceeds to compute to get the value of . Compute to get the value of . Then, by calculating , we can get the . After that, check if the inequality holds true. It is worth noting that the time threshold is slightly different from the previously used threshold . The former is used to determine and ensure that messages from vehicle have not been intercepted or spoofed. If vehicle receives a message from vehicle that is forged or replayed, the internally calculated time threshold will exceed the specified range. Since this timestamp cannot be known by a third party, forging this timestamp is impossible. If the inequality is not satisfied, the authentication process is terminated. However, if the inequality holds, TA retrieves the challenge of vehicle from , calculates its response , and verifies it against the corresponding challenge–response pair stored in the database. After successful validation, a confirmation message is generated, and then a timestamp is acquired. Subsequently, message is transmitted to vehicle .
- After receiving message , vehicle retrieves the current timestamp and verifies whether the condition holds true. If the inequality holds true, accepts and confirms that vehicle is legitimate. Afterward, vehicle selects a random integer ( ) and calculates . Then, it computes the values and to generate the session key . Afterward, similar to vehicle , vehicle computes for the verification from vehicle . The values of are as follows: , , . In which, the in is the current timestamp obtained by vehicle after computing . Finally, vehicle obtains the current timestamp and sends messages and to vehicle .
- Vehicle , upon receiving messages , selects the current timestamp and retrieves the timestamp from the received messages. Then, it evaluates whether the inequality holds true. If the inequality does not hold true, the authentication process is terminated. If the inequality holds true, vehicle obtains the current timestamp and sends the message to TA.
- Upon receiving the message , TA first verifies its freshness by selecting the current timestamp and calculating whether the inequality holds true. If the inequality does not hold true, the authentication process is terminated. If the inequality holds true, TA calculates to obtain the value of . Calculate to obtain the value of , then calculate and determine if the inequality is satisfied. If the inequality does not hold true, the authentication process is terminated. If the inequality holds true, obtain the challenge from , compute response , and compare it with the corresponding challenge–response pair stored in the database, , for validation. After successful validation, a confirmation message is generated, and then a timestamp is acquired. Subsequently, message is transmitted to vehicle .
- After receiving message , vehicle retrieves the current timestamp and verifies whether the condition holds true. If the inequality holds true, accepts and confirms that vehicle is legitimate. Otherwise, terminate the authentication process. Then, vehicle calculates the values of and and verifies . If true, compute the session key .
Considering that , substituting the following equations , , into yields . Also, since the equation , can be transformed into . At this point, it can be observed that by substituting the equation and simplifies to . At this moment, it is worth noting that by substituting , , and , we obtain , namely, . Now, we have , it can be inferred that and . Thus, . Also, since and , it follows that .
4.4. Communication Phase
In this phase, the vehicles have mutually authenticated each other and can communicate using the agreed-upon session key established earlier. An important point to highlight is that identity authentication among vehicles occurs solely during the initial communication exchange. Subsequent communication instances do not necessitate reauthentication. Moreover, it is noteworthy that information exchange between vehicles during the communication phase will transpire over an insecure communication channel. The detailed elucidation of the communication steps will be delineated in the subsequent section (Figure 5).
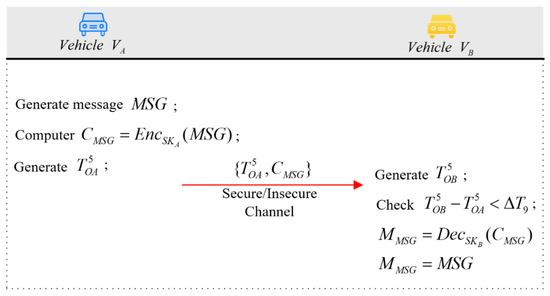
Figure 5.
Communication phase.
Let represent the message to be transmitted from vehicle to vehicle . Employing the session key , previously negotiated with vehicle , vehicle encrypts message using symmetric encryption, yielding ciphertext . Vehicle selects the current timestamp and combines it with the ciphertext, sending this amalgamation as the message to vehicle . Upon receiving the message, vehicle first generates the current timestamp and checks if to ensure the legality of the message. Should the inequality prove valid, vehicle proceeds to decrypt the ciphertext using to get , as the session key shared between vehicle and vehicle ensures mutual decryption capability, namely, .
4.5. Information Update
The subsequent process allows vehicles to update their relevant information, such as identities, passwords, or characteristic data, due to various reasons. In this step, vehicles connect to the TA via a secure channel, and the values requiring updates are registered directly with the server. The detailed process (Figure 6) will be explained below.
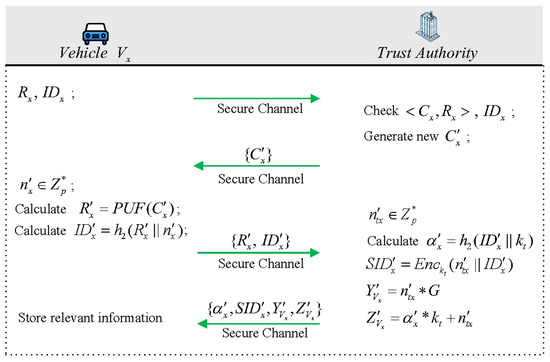
Figure 6.
Vehicle password update phase.
Vehicle sends its response and identity to the TA. The TA compares the received challenge–response pair with its stored one and verifies the identity of the vehicle . Upon successful verification, it generates a new challenge and sends it to vehicle . After receiving the challenge message, the vehicle recalculates the response , selects a new random number , and computes the . Subsequently, it sends the new response and identity to the TA. Upon receiving the information from the vehicle, TA stores the new challenge–response pair and the vehicle’s identity in the database. It then selects another new random number and recalculates the following values: , , and . Afterwards, using the new random number and identity, the TA computes the new pseudonym for vehicle . Finally, the calculated values are sent to vehicle , which stores the new values after receiving the message.
5. Security Analysis
This section provides a detailed analysis of the security of the proposed protocol. Specific details will be elaborated on in the subsequent subsections.
5.1. Informal Security Analysis
In this section, we provide an informal security proof for the VANET authentication scheme, demonstrating its security and its ability to mitigate significant security threats as per the security objectives of the vehicular ad hoc network authentication scheme.
Vehicle Anonymity: During the authentication procedure, a vehicle employs a pseudonymous identity on the public channel to obscure its actual identity . It should be emphasized that the pseudonymous identity of the vehicle, denoted as , is produced by through encryption using its private key . Furthermore, apart from , no third party will know the value of . Therefore, besides the vehicle itself, only can access the true identity of the vehicle, while only can determine the pseudonymous identity of vehicle . Additionally, the pseudonymous identity used by a vehicle may vary for the same vehicle under different circumstances. As a result, attacker cannot identify or track vehicle by intercepting the information transmitted by on the public channel, ensuring the anonymity of the vehicle.
Resistance to Replay Attack: In this protocol, timestamps are employed in communications between entities to ensure the freshness and integrity of messages. As each message is received, a check is performed against the current timestamp, for example, . If an adversary attempts to eavesdrop on and impersonate any message in transit, it will fail to meet the time constraints specified in equations similar to the one above. Consequently, this protocol is resilient against replay attacks.
Mutual Authentication: The authentication between vehicles and is accomplished by computing a session key through negotiation. In the protocol, each communicating party computes their corresponding value using self-selected random numbers and various parameters obtained during the registration stage. It is important to highlight that and never exchange temporary keys throughout this process. Instead, they calculate their respective values using known parameters and parameters extracted from messages and . Subsequently, one of the entities involved in communication, vehicle , needs to calculate the value of and send it to . On the other hand, also needs to compute its own value of and verify to ensure the security of the mutual authentication process.
Resistance to Physical Attack: Ensuring the security of the is crucial for the entire authentication protocol, considering it is a device highly susceptible to access and tampering by attackers like . In this protocol, every is equipped with a to enhance the physical layer security of the authentication process. As this paper focuses on the design of authentication protocols, it does not impose constraints on PUFs. To resist side-channel attacks, improvements to PUFs can be made, such as adopting low-power RO PUFs [46] or Subthreshold Current Array (SCA) PUFs [47]. (Interested readers can refer to [46,47] for more information.) Besides, any attempt to tamper with the during the authentication process will cause fluctuations in the , rendering it unable to generate accurate outputs. Additionally, the can easily identify such tampering attempts. Since the attacker cannot reconstruct the in subsequent attacks, the protocol can resist physical layer attacks such as cloning/tampering during the authentication process.
Vehicle Traceability: Traceability is essential for the to detect any unusual activities by vehicles and to enable authorized vehicles to reclaim their true identities. This protocol ensures that attacker cannot obtain the true identity of vehicle , thereby preserving the anonymity of the vehicles. However, the true identity of vehicle is only accessible to through the calculation of during the authentication process, aside from the vehicle itself. Thus, this protocol only allows to trace vehicle .
Resistance to Vehicle Impersonation Attack: If attacker intends to conduct a vehicle masquerading attack on this protocol, they must forge relevant request information, such as and . However, for to successfully forge the corresponding data, they would need to know some secret credentials of , such as , which are not accessible to attacker . Meanwhile, during vehicle authentication, submits the verification of the counterpart vehicle to . At this point, since the database of does not contain any forged messages by attacker , this will directly expose the deception attempted by . Therefore, due to the absence of relevant parameters and ’s verification mechanism, it is impractical for attacker to disguise as a vehicle.
Forward Secrecy: Using the CK adversarial model, forward secrecy can be achieved when attacker has complete access to communication information and knowledge of secret credentials. Even if the session state and secret credentials are compromised, attacker remains unable to access/generate the temporary key for vehicle , thus rendering them incapable of computing the secret key . Hence, in the CK adversarial model, this protocol guarantees forward secrecy.
5.2. Formal Security Proof Based on the ROR Model
In this section, we will provide a security proof of the proposed scheme using the ROR model [48]. In the ROR model, all legitimate participants involved in session key negotiation share a dictionary of size N. The ROR model enables participants to transform low-entropy passwords, randomly chosen from the dictionary, into high-entropy shared session keys through negotiation among themselves. Here are the different terms and definitions in the ROR model.
Participants: Vehicles , , and the Trusted Authority are three distinct independent participants in the protocol, with representing instances of participants , respectively. These instances are referred to as random oracle machines, and the random oracle machines will be involved in the execution of the 3PAKE protocol.
Partnering: Partnering is based on session identifier (SID) and partner identification (PID). Here, SID can be viewed as the variable of all protocol messages exchanged by instances and , while PID is an instance used to establish shared keys. Two instances are considered to be partnering when they satisfy the following conditions:
- Both instances and accept.
- Instances and share the same SID.
- The PID of both and is the same.
- No instance except for and will accept a PID equal to that of and .
Freshess: When the adversary fails to discover the session key between and by Reveal (), then or is considered fresh.
Random oracle: Both participant and adversary have access to a one-way hash function h, also known as a hash oracle.
Adversary: The adversary has the capability to eavesdrop on and control the entire communication network, employing a polynomial number of oracle queries to simulate realistic attacks, thereby intercepting all communication messages between the participants. The queries are formulated as follows:
Execute query : The adversary executes this query to intercept/eavesdrop on all instances of communication exchanged between and .
Send query : The adversary executes this query to conduct an active attack, sending a message m to the instance . Upon receiving m, will compute some relevant information of the proposed protocol and send them back to adversary .
Reveal query : Adversary can obtain the current session key between and its partner through this query. If adversary requests to send a reveal query to , then will output as follows:
- and its partner mutually authenticate, enter an accept state, and compute the session key . Then sends the session key to adversary .
- Otherwise, returns an empty value as output.
Test query : This query is used to demonstrate the semantic security of the session key . If and its partner have computed the session key, it returns ; otherwise, it returns a null value. So, is allowed to perform the Test query to only once. When receives , it tosses an unbiased coin c, and if the result is 1, it outputs the session key ; if the result is 0, it returns a randomly generated key of the same length as the session key; otherwise, it returns a null value .
Now, we can define as the advantage of adversary breaking the semantic security of the proposed protocol p, and W as the event of breaking the semantic security of the proposed protocol p. Thus, holds. This means that if , then p is secure, where is an arbitrarily small positive value.
Theorem 1.
Suppose that the adversary attempts to break the semantic security of protocol p between and within polynomial time t.
Then, the advantage of in breaking the semantic security of p is denoted by:
where represents the number of hash queries, the range space of the hash function, and the advantage of in breaking the proposed protocol , respectively.
Proof.
The proof process is based on the following four games, denoted as . Where simulates a real attack on protocol p, and illustrates the minimum advantage of in breaking in the protocol. For each , we define an event as the event where succeeds in guessing c in . Considering , then we have:
Game : In this game, selects c and starts attacking p. This attack models the hash function as a random oracle, yielding:
Game : In this game, obtains all the information exchanged between during the authentication and communication phases through the Execute query. Upon receiving the messages, can execute the Test query to verify whether the output is the session key or a random key. Since and are the session keys for and , respectively, and , and we cannot obtain the values of and through eavesdropping, the chances of winning the game are not increased in this case. Therefore, we have:
Game : In this game, attacks by using hash queries to distinguish between the session key and the random key. can utilize the previously eavesdropped information, and , to perform hash queries. But requires relevant information to compute the session key, which cannot be obtained through eavesdropping or querying. Because the hash digest ensures that messages do not collide, must find a hash collision in polynomial time to win the game, as inferred from the birthday paradox [49]:
Game : In this game, attempts to eavesdrop to obtain the real session key . However, cannot obtain the key to compute , nor can obtain from . Therefore, we have:
At this point, if guesses correctly for c, can win the game. So:
From (3), (4), and (7) we get:
From (5)–(7), and the triangle inequality, we get:
From (8) and (9), we obtain the desired result, namely (1):
5.3. Formal Security Proof Based on BAN Logic
BAN Logic [50] is a logical system used for analyzing the security of protocols, commonly employed to prove or analyze the correctness and security of cryptographic protocols. BAN Logic typically involves a set of formal rules and inference mechanisms used to prove the goals of authentication protocols. By employing BAN Logic, users can ultimately ascertain the reliability of transmitted data and prevent eavesdropping and tampering. Here is the security analysis of the proposed protocol using BAN Logic.
The logical assumptions or rules of BAN Logic that will be used in the analysis process are as follows:
The message meaning rule : .
The freshness rule : .
The nonce-verification rule :
The jurisdiction rule :
The corresponding objectives to be proven for the proposed protocol are as follows:
The idealized form of the messages transmitted between vehicles , and between and in the proposed protocol is as follows:
Message :
Message :
Message :
According to the proposed protocol, the following basic assumptions are made:
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
Assumption :
The proposed protocol aims to demonstrate its objectives based on rules, idealizations, and assumptions. The specific proofs are as follows:
From Message , get :
From , and rule , get :
From , and rules , , get : [ proved]
From , and rule , get : [ proved]
From Message , get :
From , and rule , get :
From , and rules , get : [ proved]
From , and rule , get : [ proved]
From Message , get :
From , and rule , get :
From , and rules , get : [ Proved]
From , and rule , get : [ Proved]
6. Performance Analysis
This section will delve into the performance evaluation of the proposed protocol, juxtaposed with comparative analyses against other protocols [11,12,13,14,15]. This comparison is based on two key metrics: computational expenditure and communication overhead. Considering that initialization setup and registration phases occur only once, performance analysis primarily focuses on the authentication and communication phases. The experiments were executed on a 64-bit Ubuntu (18.04.6) system, powered by a 12th Gen Intel(R) Core(TM) i5 3.5 GHz processor and 32 GB of memory. To enhance the accuracy of the experimental findings, each operation underwent rigorous testing 50 times, and the resultant average value was considered the definitive outcome. Detailed analysis will be elaborated in the subsequent sections.
6.1. Computation Cost
The computational expense of the authentication algorithm is contingent upon the computation method utilized. Table 1 provides a breakdown of the computational time required for each computational method. In the proposed phase, PUF is embedded into the OBU of the vehicle, and the BCH code offset mechanism [51] is utilized to minimize the impact of environmental factors on the output. Table 2 delineates the computational costs associated with accessing individual and multiple devices in both the existing solutions and our proposed approach. In the proposed protocol, the authentication and communication stages involve a total of six hash operations. Additionally, symmetric encryption and decryption operations occur twice in both the authentication and communication stages. Furthermore, there are four elliptic curve point addition operations, four elliptic curve scalar multiplication operations, and two PUF operations. Therefore, the overall computational expenditure amounts to:

Table 1.
Running time of the cryptographic operations.

Table 2.
Computation cost in the mathematical equation.
Other relevant protocols [11,12,13,14,15] can also employ the same methodology to obtain their computational costs, as depicted in Figure 7. In terms of computational costs, there is little difference between the proposed protocol and the protocols by Wu et al. [13] and Umar et al. [15] when the number of vehicles is small or even exceeds them in some cases. As the number of participating vehicles increases, the proposed protocol exhibits a slower growth rate in computational costs compared to other relevant protocols, thereby making it better suited for scenarios involving a larger number of vehicles.
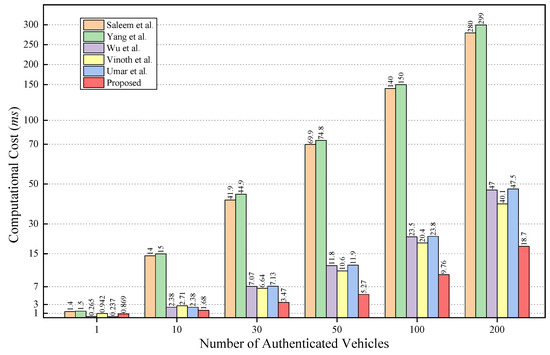
Figure 7.
Computation cost comparison [11,12,13,14,15].
6.2. Communication Cost
Communication overhead refers to the number of bits required to transmit messages between participants in the authentication protocol. This section presents a quantitative analysis of the communication costs of the proposed protocol compared to previous relevant protocols. Table 3 presents the communication costs of the proposed protocol and related protocols in scenarios involving single and multiple participants.

Table 3.
Comparison of the communication costs.
During the identity authentication phase, vehicle sends information packet to vehicle , resulting in a total cost of 256 + 256 + 384 + 128 + 256 + 192 + 192 + 256 = 1920 bits within the proposed protocol. Subsequently, vehicle requests authentication from TA, and upon receiving the verification message, both operations incur costs, denoted as 256 + 256 + 384 + 128 + 256 = 1280 bits and 256 + 8 = 264 bits, respectively. After receiving the verification feedback message, vehicle promptly sends a message to vehicle , which includes the following content: .
The total cost of this part is 256 + 256 + 384 + 128 + 256 + 192 + 192 + 256 + 256 = 2176 bits. Vehicle , similar to vehicle ’s action, requests authentication from TA. The communication overhead for this operation is 1280 bits, while the feedback message returned is 264 bits. The overall cost incurred during communication between vehicles is denoted as 128 + 256 = 384 bits. The total overhead for authentication and communication processes is represented by 1920 + 1280 + 264 + 2176 + 1280 + 264 + 384n = 7184 + 384n. In a similar manner, the communication expenses for related protocols [11,12,13,14,15] can be calculated, as shown in Figure 8. It can be observed from the figure that, the proposed protocol does not demonstrate significant superiority over other related protocols and, in some cases, even incurs higher costs when the number of vehicles is small. However, with the growth in the number of vehicles, the overall overhead increases at a noticeably slower rate compared to other relevant schemes, indicating superior adaptability for multivehicle scenarios. In summary, the proposed protocol stands out as lightweight and highly efficient compared to related protocols.
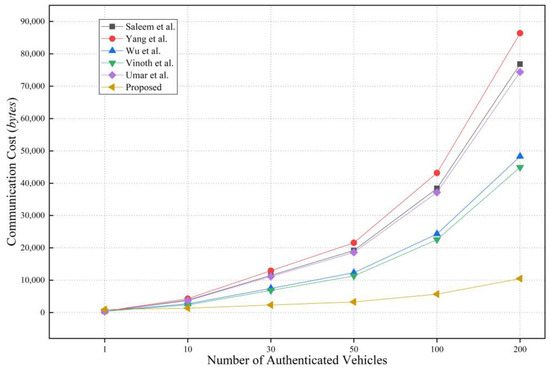
Figure 8.
Communication cost comparison.
6.3. Simulation
To test the feasibility of the proposed protocol, simulations were conducted using the network simulation systems OMNeT++ 5.6.2 and SUMO 1.8.0. OMNeT++ is responsible for detailed packet-level simulation of source, destination, data traffic transmission, reception, background load, routing, links, and channels. SUMO is used to create traffic simulations, generate the required road networks for the simulation, and represent traffic demand. The specifications of the simulation experiment environment are shown in Table 4. We selected a 1600 m2 area from the OpenStreetMap as the simulation area and included different types of vehicles, such as cars, buses, and trucks. Since SUMO requires the road network to be in its own format, the first step is to configure the desired road network on the OpenStreetMap webpage and export it as a .osm file. After that, the .osm file needs to be converted into a .net.xml file format that SUMO can accept. Using the randomTrips.py tool provided in SUMO, a route file .rou.xml can be generated, and then the simulation is configured using the .sumocfg file (as shown in Figure 9b). Finally, the simulation is conducted in OMNeT++, where vehicle movement and information exchange are simulated. Figure 9a illustrates the transmission of messages during the simulation process, validating the practicality of the proposed protocol.

Table 4.
Simulation parameters.
Figure 9.
(a) A glimpse of message transfer. (b) SUMO configuration file.
7. Conclusions
In this paper, we propose an efficient, lightweight identity authentication protocol tailored for VANETs, based on elliptic curve cryptography with conditional privacy protection. Additionally, the proposed protocol effectively balances security with lightweight characteristics. Formal and informal evaluations of the protocol’s security reveal its effectiveness in defending against physical attacks on vehicles, as well as thwarting vehicle impersonation and replay attacks. Additionally, the protocol ensures vehicle anonymity and untraceability while satisfying forward secrecy requirements. Performance evaluations focusing on computational costs and communication overhead demonstrate that our protocol outperforms recent relevant protocols, particularly in scenarios with a higher number of vehicles. Given that the authentication process of this protocol still involves communication between vehicles and TA, it is more suitable for urban areas with a higher density of vehicles and well-established infrastructure. However, for environments lacking infrastructure, such as rural areas, there are still certain challenges to overcome. Our future study will focus on addressing the issue of vehicles’ excessive dependence on infrastructure to ensure applicability in different network environments, such as urban and rural areas. Additionally, we can choose to integrate blockchain technology, leveraging its distributed framework, to store and transmit application data information between vehicles more efficiently and securely. At this point, introducing an efficient and scalable consensus mechanism would be an open research challenge. Our next research focus will be on efficiently achieving vehicle-to-vehicle authentication and malicious node exclusion through rapid and lightweight consensus methods.
Author Contributions
Methodology, Z.F. and S.W.; software, Z.F., B.Z. and Z.L.; validation, S.W., Z.F. and Y.D.; analysis, Z.F., B.Z. and Y.D.; investigation, Z.F. and Y.S.; writing—original draft, Z.F. and Y.S.; writing—review and editing, Z.F., S.W. and Y.D.; supervision, S.W. and Y.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Natural Science Foundation of Jilin Province (20240101343JC), Department of Science and Technology of Jilin Province (20220201154GX).
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
Notation Table.
| Symbol | Description |
| TA | Trusted Authority |
| PUF | Physical Unclonable Function |
| E | Elliptic Curve |
| Finite Field | |
| G | Generator |
| Vehicle | |
| TA’s private key | |
| TA’s public key | |
| Challenge–response pair | |
| Vehicle identity | |
| Pseudonym of the vehicle | |
| Timestamp | |
| Data involved in the authentication process | |
| Vehicle session key | |
| XOR operation | |
| Concatenation operation | |
| One-way hash function | |
| Prescribed time threshold |
References
- Tang, Q.; Xie, M.; Yang, K.; Luo, Y.; Zhou, D.; Song, Y. A decision function based smart charging and discharging strategy for electric vehicle in smart grid. Mob. Netw. Appl. 2019, 24, 1722–1731. [Google Scholar] [CrossRef]
- Xia, Z.; Hu, Z.; Luo, J. UPTP vehicle trajectory prediction based on user preference under complexity environment. Wirel. Pers. Commun. 2017, 97, 4651–4665. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A security and privacy review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996. [Google Scholar] [CrossRef]
- Sun, X.; Lin, X.; Ho, P.H. Secure vehicular communications based on group signature and ID-based signature scheme. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 24–28 June 2007; pp. 1539–1545. [Google Scholar]
- Cheng, X.; Yang, L.; Shen, X. D2D for intelligent transportation systems: A feasibility study. IEEE Trans. Intell. Transp. Syst. 2015, 16, 1784–1793. [Google Scholar] [CrossRef]
- Dak, A.Y.; Yahya, S.; Kassim, M. A literature survey on security challenges in VANETs. Int. J. Comput. Theory Eng. 2012, 4, 1007. [Google Scholar] [CrossRef]
- Standaert, F.X. Introduction to side-channel attacks. Secur. Integr. Circuits Syst. 2010, 27–42. [Google Scholar] [CrossRef]
- Huang, J.L.; Yeh, L.Y.; Chien, H.Y. ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2010, 60, 248–262. [Google Scholar] [CrossRef]
- Hao, Y.; Cheng, Y.; Zhou, C.; Song, W. A distributed key management framework with cooperative message authentication in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 616–629. [Google Scholar] [CrossRef]
- Saleem, M.A.; Li, X.; Ayub, M.F.; Shamshad, S.; Wu, F.; Abbas, H. An Efficient and Physically Secure Privacy-Preserving Key-Agreement Protocol for Vehicular Ad-Hoc Network. IEEE Trans. Intell. Transp. Syst. 2023, 24, 9940–9951. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, X.; Wang, X.; Fu, J.; Zheng, J.; Liu, Y. A novel authentication and key agreement scheme for Internet of Vehicles. Future Gener. Comput. Syst. 2023, 145, 415–428. [Google Scholar] [CrossRef]
- Wu, L.; Sun, Q.; Wang, X.; Wang, J.; Yu, S.; Zou, Y.; Zhu, Z. An efficient privacy-preserving mutual authentication scheme for secure V2V communication in vehicular ad hoc network. IEEE Access 2019, 7, 55050–55063. [Google Scholar] [CrossRef]
- Vinoth, R.; Deborah, L.J.; Vijayakumar, P.; Kumar, N. Secure multifactor authenticated key agreement scheme for industrial IoT. IEEE Internet Things J. 2020, 8, 3801–3811. [Google Scholar] [CrossRef]
- Umar, M.; Islam, S.H.; Mahmood, K.; Ahmed, S.; Ghaffar, Z.; Saleem, M.A. Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans. Veh. Technol. 2021, 70, 12158–12167. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications. In Proceedings of the IEEE INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1229–1237. [Google Scholar]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.H.; Shen, X. An efficient identity-based batch verification scheme for vehicular sensor networks. In Proceedings of the IEEE INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 246–250. [Google Scholar]
- Zhang, L.; Wu, Q.; Solanas, A.; Domingo-Ferrer, J. A scalable robust authentication protocol for secure vehicular communications. IEEE Trans. Veh. Technol. 2009, 59, 1606–1617. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M. Toward a secure batch verification with group testing for VANET. Wirel. Netw. 2013, 19, 1441–1449. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Zhong, H.; Wen, J.; Cui, J.; Zhang, S. Efficient conditional privacy-preserving and authentication scheme for secure service provision in VANET. Tsinghua Sci. Technol. 2016, 21, 620–629. [Google Scholar] [CrossRef]
- Gayathri, N.B.; Thumbur, G.; Reddy, P.V.; Rahman MZ, U. Efficient pairing-free certificateless authentication scheme with batch verification for vehicular ad-hoc networks. IEEE Access 2018, 6, 31808–31819. [Google Scholar] [CrossRef]
- Lo, N.W.; Tsai, J.L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transp. Syst. 2015, 17, 1319–1328. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure message communication protocol among vehicles in smart city. IEEE Trans. Veh. Technol. 2017, 67, 4359–4373. [Google Scholar] [CrossRef]
- Teng, L.; Jianfeng, M.; Pengbin, F.; Yue, M.; Xindi, M.; Jiawei, Z.; Gao, C.; Di, L. Lightweight security authentication mechanism towards UAV networks. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu City, Republic of Korea, 10–13 October 2019; pp. 379–384. [Google Scholar]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.; Choo, K.K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Ming, Y.; Cheng, H. Efficient certificateless conditional privacy-preserving authentication scheme in VANETs. Mob. Inf. Syst. 2019, 2019, 7593138. [Google Scholar] [CrossRef]
- Li, X.; Liu, T.; Obaidat, M.S.; Wu, F.; Vijayakumar, P.; Kumar, N. A lightweight privacy-preserving authentication protocol for VANETs. IEEE Syst. J. 2020, 14, 3547–3557. [Google Scholar] [CrossRef]
- Shamshad, S.; Saleem, M.A.; Obaidat, M.S.; Shamshad, U.; Mahmood, K.; Ayub, M.F. On the security of a lightweight privacy-preserving authentication protocol for VANETs. In Proceedings of the 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS), Coimbatore, India, 25–27 March 2021; pp. 1766–1770. [Google Scholar]
- Alshudukhi, J.S.; Mohammed, B.A.; Al-Mekhlafi, Z.G. An efficient conditional privacy-preserving authentication scheme for the prevention of side-channel attacks in vehicular ad hoc networks. IEEE Access 2020, 8, 226624–226636. [Google Scholar] [CrossRef]
- Cui, J.; Xu, W.; Han, Y.; Zhang, J.; Zhong, H. Secure mutual authentication with privacy preservation in vehicular ad hoc networks. Veh. Commun. 2020, 21, 100200. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, X.; Zhang, N.; Tian, Y.; Ma, X.; Ma, J. Two-factor authentication protocol using physical unclonable function for IoV. In Proceedings of the 2019 IEEE/CIC International Conference on Communications in China (ICCC), Changchun, China, 11–13 August 2019; pp. 195–200. [Google Scholar]
- Kudva, S.; Badsha, S.; Sengupta, S.; La, H.; Khalil, I.; Atiquzzaman, M. A scalable blockchain based trust management in VANET routing protocol. J. Parallel Distrib. Comput. 2021, 152, 144–156. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Feng, X.; Shi, Q.; Xie, Q.; Liu, L. An efficient privacy-preserving authentication model based on blockchain for VANETs. J. Syst. Archit. 2021, 117, 102158. [Google Scholar] [CrossRef]
- Ahmed, M.; Moustafa, N.; Akhter, A.S.; Razzak, I.; Surid, E.; Anwar, A.; Zengin, A. A blockchain-based emergency message transmission protocol for cooperative VANET. IEEE Trans. Intell. Transp. Syst. 2021, 23, 19624–19633. [Google Scholar] [CrossRef]
- Tandon, R.; Verma, A.; Gupta, P.K. D-BLAC: A dual blockchain-based decentralized architecture for authentication and communication in VANET. Expert Syst. Appl. 2024, 237, 121461. [Google Scholar] [CrossRef]
- Jiang, D.; Delgrossi, L. IEEE 802.11 p: Towards an international standard for wireless access in vehicular environments. In Proceedings of the VTC Spring 2008-IEEE Vehicular Technology Conference, Marina Bay, Singapore, 11-14 May 2008; pp. 2036–2040. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 453–474. [Google Scholar]
- Crocetti, L.; Baldanzi, L.; Bertolucci, M.; Sarti, L.; Carnevale, B.; Fanucci, L. A simulated approach to evaluate side-channel attack countermeasures for the Advanced Encryption Standard. Integration 2019, 68, 80–86. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Armknecht, F.; Moriyama, D.; Sadeghi, A.R.; Yung, M. Towards a unified security model for physically unclonable functions. In Topics in Cryptology-CT-RSA 2016: The Cryptographers’ Track at the RSA Conference 2016, San Francisco, CA, USA, 29 February–4 March 2016, Proceedings; Springer International Publishing: Berlin/Heidelberg, Germany, 2016; pp. 271–287. [Google Scholar]
- Cao, Y.; Zhao, X.; Ye, W.; Han, Q.; Pan, X. A compact and low power RO PUF with high resilience to the EM side-channel attack and the SVM modelling attack of wireless sensor networks. Sensors 2018, 18, 322. [Google Scholar] [CrossRef] [PubMed]
- Xi, X.; Aysu, A.; Orshansky, M. Fresh re-keying with strong PUFs: A new approach to side-channel security. In Proceedings of the 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018; pp. 118–125. [Google Scholar]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Public Key Cryptography-PKC 2005: 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Proceedings 8; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Advances in Cryptology—EUROCRYPT 2000: International Conference on the Theory and Application of Cryptographic Techniques Bruges, Belgium, 14–18 May 2000; Proceedings 19; Springer: Berlin/Heidelberg, Germany, 2000; pp. 156–171. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. (TOCS) 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Advances in Cryptology-EUROCRYPT 2004: International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Proceedings 23; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).