Abstract
Users encounter various threats, such as cross-site scripting attacks and session hijacking, when they perform login operations in the browser. These attacks pose significant risks to the integrity and confidentiality of personal data. The browser fingerprint, as an authentication technique, can effectively enhance user security. However, attackers can bypass browser fingerprint authentication through phishing attacks and other methods, leading to unauthorized logins. To address these issues, we propose a secure browser fingerprint authentication scheme that integrates the data of the browser cache side-channel into the traditional browser fingerprint. Consequently, it enhances the dynamics and non-determinism of the browser fingerprint and improves the anti-attack capabilities of the authentication process. Experimental results demonstrate that this scheme can effectively mitigate phishing attacks and man-in-the-middle attacks, achieving a 95.33% recognition rate for attackers and a 96.17% recall rate for authorized users.
1. Introduction
The advent of the Internet has fundamentally transformed the way we interact with information, communicate with others, and conduct business [1]. Central to this digital revolution is the browser, a software application that enables users to access and navigate the vast expanse of the World Wide Web [2]. Today, the technologies to enrich the user experience are evolving at an amazing pace [3]. Browsers have become indispensable tools for virtually every aspect of modern life, facilitating everything from online shopping and social networking to research and entertainment [4].
Browser authentication is crucial for maintaining data privacy, preventing identity theft, and enforcing secure access controls in the online environment. Most sites rely on relatively weak forms of authentication [5], and passwords are the default solution [6]. However, the widespread reliance on username-password-based authentication poses significant challenges [7,8]. As early as 2016, research indicated that over 3.3 billion credentials had been compromised through this approach alone. Meanwhile, phishing attacks significantly increase the risk of account hijacking [9]. While multi-factor authentication (MFA) [10,11] can enhance user security, the introduction of additional authentication factors increases the complexity and time cost of the user login process.
Browser fingerprint, as a stateless technique [12], harnesses user device data (e.g., browser type, operating system, installed plugins, etc.) collected by the browser to construct a distinct device identifier [13]. Browser fingerprinting for authentication is a way to put browser fingerprints in the service of benign purposes [14]. Unlike traditional username-password authentication methods, browser fingerprint authentication is considerably more resistant to cracking, thus enhancing user security, which is a promising additional web authentication factor [15].
However, current browser fingerprint authentication technology faces two significant challenges. First, the weak stability of browser fingerprints contradicts the need for a relatively stable credential for authentication. Since browser fingerprints directly reflect users’ devices and their environment, any modifications or updates to device parameters can easily alter the browser fingerprint [16]. Second, browser fingerprints are vulnerable to illegitimate theft by attackers through techniques such as cross-site scripting (XSS) and cross-site request forgery (CSRF). Additionally, they are susceptible to phishing attacks [17] and man-in-the-middle attacks [18]. Specifically, malicious websites can collect users’ fingerprints and use them to mimic their devices, therefore bypassing authentication mechanisms. Simultaneously, attackers can intercept users’ login information and tamper with users’ identities to achieve authentication. These vulnerabilities undermine the reliability and security of browser fingerprint authentication, necessitating further advancements to address these concerns and enhance the overall robustness of the authentication process.
To tackle these challenges, we propose a browser fingerprint authentication scheme based on browser cache side-channel technology [19]. First, we utilize Fast Fourier Transform (FFT) to map browser cache side-channel data into a unique browser fingerprint attribute. Since browser cache side-channel data are closely tied to the hardware information of user devices, this approach significantly improves stability compared to traditional browser fingerprint authentication methods. Furthermore, due to the diversity of hardware devices, attackers are unable to replicate user devices, therefore thwarting phishing attacks. Second, we introduce the concept of timestamps. By recording the time when fingerprint collection is completed and analyzing the duration of fingerprint collection, we can detect man-in-the-middle attacks. This dual-pronged approach aims to enhance the security and reliability of browser identity authentication, mitigating the vulnerabilities associated with traditional methods and bolstering overall protection against malicious activities in the online environment.
In summary, the main contributions of this paper are summarized below:
- We propose a more stable and secure browser fingerprint authentication scheme that integrates browser cache side-channel technology, therefore mitigating phishing attacks.
- We introduce the timestamp to identify man-in-the-middle (MITM) attacks by analyzing the duration of fingerprint collection.
- We test and analyze the uniqueness and stability of browser cache side-channel data across 11 different computer devices. Furthermore, the accuracy of the proposed authentication scheme is tested, with experimental results indicating a recall rate of 96.17% even in the presence of man-in-the-middle and phishing attacks.
The remaining sections of the paper are structured as follows. We review the state-of-the-art in Section 2, including browser cache side-channel technology and browser fingerprint authentication technology. Section 3 introduces the system model, the threat model, and the design goals of the proposed scheme, followed by its detailed design in Section 4. We analyze the security and privacy of the scheme regarding resistance against man-in-the-middle attacks and phishing attacks in Section 5. Section 6 conducts experiments to evaluate the uniqueness, stability, and accuracy of the scheme. Finally, we draw a conclusion in the Section 7.
2. Background and Related Work
In this section, we critically examine the current state-of-the-art literature on browser cache side-channel technology and browser fingerprint authentication. We also identify and discuss the limitations of existing methodologies.
2.1. Browser Cache Side-Channel Technology
The browser cache side-channel technology is a type of microarchitecture attack [20,21] in which sensitive information can be recovered by analyzing the physical phenomena of the device during operation [22]. Since the mid-1990s, side-channel technology has received increasing attention from researchers [23]. Among the different types of side-channel attacks, cache side-channel attacks can leak large amounts of information [24]. The Prime and Probe technique was initially proposed by Osvik et al. in 2006 [25], which, as shown in Figure 1, typically involves three main phases:
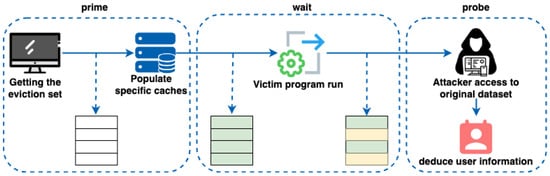
Figure 1.
The General Flow of the Prime and Probe Technique.
- Prime Phase: the attacker fills the CPU cache with specific data carefully selected to impact the cache’s behavior in subsequent operations.
- Wait Phase: victims execute operations that may replace the data previously loaded by attackers in the cache.
- Probe Phase: the attacker performs memory access operations and observes the timing or latency of these operations. By carefully timing memory accesses, the attacker can infer information about the cache state and potentially recover sensitive data.
In 2020, Shusterman et al. explored the application of cache side-channel techniques in a networked environment [26]. Cronin et al. present a new GPU side-channel attack in 2021 by targeting different levels of caching in devices [27]. In 2022, Mojtaba et al. [19] proposed a cash occupancy attack through browser cache side-channel data based on the Prime and Probe technique. It exploits the variations in cache occupancy to infer sensitive information or monitor user behavior in computing systems. In this attack, adversaries analyze the occupancy patterns of cache memory to deduce details about the system’s operations or the data being processed.
2.2. Browser Fingerprint Authentication Technology
In 2009, Mayer conducted an investigation into the potential exploitation of browser environment variations by remote attackers for user identification purposes [2]. In this study [28], experiments were conducted to collect data on browsers, screen characteristics, and browser plugins. The findings, derived from a sample of 1328 users, demonstrated that 1278 users (96.23%) could be identified.
Andriamilanto et al. conducted extensive research on the browser fingerprint, rigorously assessing its necessity as a factor in browser identity authentication [28]. Their work has gradually raised awareness of the crucial role that browser fingerprints play in the authentication process. In 2013, Nikiforakis et al. launched an in-depth study on the variability of browser fingerprints [29].
However, issues such as weak uniqueness and stability have long constrained the development of browser fingerprint authentication. To address these challenges, Queiroz et al. recognized a device’s web browser fingerprint by studying the use of the Web Audio API [30]. Karami et al. introduced behavioral fingerprints in the authentication process in 2020 [31]. In 2022, ref. [32] conducted a comparative analysis of single-peak and multi-peak behavioral biometric features obtained from various activities such as typing, scrolling, drawing numbers, and screen tapping on smartphones. The introduction of behavioral fingerprints significantly raised the difficulty for attackers to simulate fingerprints, therefore enhancing the uniqueness of browser fingerprints and reducing the risk of credential theft. However, users’ behaviors may vary over time [33], influenced by factors such as emotions, health conditions, etc., leading to subsequent authentication failures.
In the same year, Andriamilanto et al. utilized machine-learning techniques to propose a dynamic fingerprint updating scheme, ensuring the uniqueness of fingerprints [34]. However, this scheme requires re-authentication of users every time fingerprint updating is conducted, which demands substantial data for training and incurs high maintenance costs.
As shown in Figure 2, Xu et al. [35] proposed a type of phishing attack on the process of browser fingerprint authentication in 2022. Initially, attackers extract fingerprinting code from susceptible websites and incorporate it into their phishing sites. Subsequently, it automatically replicates the fingerprinting process of target websites to ensure that collected fingerprints match the expected ones. Finally, various fingerprinting functions are included on the phishing page to gather fingerprints, enabling exploitation across multiple websites simultaneously.
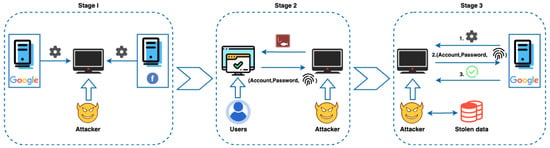
Figure 2.
The General Flow of the Phishing Attack.
In response to the aforementioned challenges and attacks, our scheme innovatively integrates cache side-channel data with browser fingerprints, which ensures stability and uniqueness and improves the ability to defend against phishing attacks.
3. Problem Statement
In this section, we illustrate the system model, the threat model, and the design goals of this scheme and describe the notation involved in the scheme, as shown in Table 1.

Table 1.
The Explanation of Notations.
3.1. System Models
The system model of this scheme is shown in Figure 3, which contains two main entities: the server and clients.
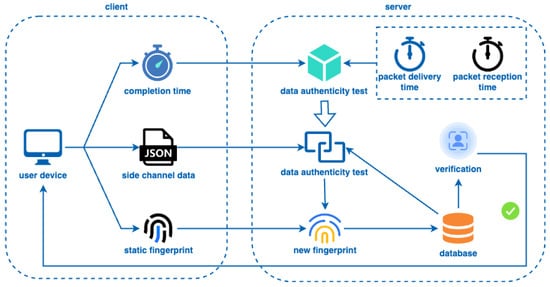
Figure 3.
System Model.
Clients: Clients mainly refer to the user devices, which are mainly responsible for collecting the browser cache side-channel data and the timestamp of the data collection completion.
Server: The server authenticates clients based on received data. Initially, it converts browser cache side-channel data into browser fingerprints to perform identity authentication. Subsequently, it utilizes the timestamp to determine whether the data sent by the client has been maliciously altered, therefore preventing man-in-the-middle attacks. In this paper, we assume that the server is a trusted entity.
3.2. Threat Models
The browser fingerprint authentication process is threatened by two main types of attacks: phishing attacks and man-in-the-middle attacks.
3.2.1. Phishing Attacks
Phishing attacks trick users into divulging their browser fingerprint data to malicious attackers under the guise of a legitimate entity or service [36,37,38]. By designing an official-looking website with the capability of browser fingerprint collection, the attacker induces the victim to log in and perform authentication operations. In this way, the attacker illegally obtains the victim’s login credentials and realizes authentication.
3.2.2. Man-in-the-Middle Attack
A man-in-the-middle (MITM) attack is a type of cyberattack where a malicious attacker intercepts communication between two parties without their knowledge [39,40]. Attackers position themselves between the server and clients, allowing them to eavesdrop on the communication, manipulate the data being transmitted, and, in some cases, inject their own malicious content into the conversation.
3.3. Design Goals
We intend to design a secure browser fingerprint authentication scheme based on the browser cache side-channel technology, supporting uniqueness, stability, phishing attack resistance, and man-in-the-middle attack resistance.
- Uniqueness: A secure browser fingerprint authentication scheme demonstrates uniqueness if the cache side-channel data from different devices exhibit distinct characteristics from each other.
- Stability: A secure browser fingerprint authentication scheme holds stability if the cache side-channel data from one device remains highly consistent over time.
- Phishing attack resistance: A secure browser fingerprint authentication scheme exhibits resistance to phishing attacks if it can identify an attacker who fraudulently obtains users’ browser fingerprint data under the guise of a legitimate entity or service.
- Man-in-the-middle attack resistance: A secure browser fingerprint authentication scheme demonstrates resistance to man-in-the-middle attacks if it can detect an attacker who intercepts communication between two parties without their knowledge.
4. Scheme Design
Our scheme contains four steps: data collection, data processing, browser fingerprint generation, and timestamp analysis. Clients initially collect browser cache side-channel data and subsequently transmit it to the server. Upon receiving the data, the server conducts a Fast Fourier Transform (FFT), therefore mapping the data to a browser fingerprint and proceeding with authentication. Furthermore, based on the timestamp, the server assesses whether the data sent by the client has been maliciously altered to prevent man-in-the-middle attacks.
Next, we describe the scheme in detail according to these four steps.
4.1. Data Collection
We collect the browser cache side-channel data based on the Prime and Probe technique proposed by Mojtaba et al. [19]. The data are represented by a matrix X with N rows and M columns, as referenced in Equation (1). Each row in the matrix represents a set of time-domain eigenvalue sequences extracted by performing a browser cache side-channel operation, where N indicates the number of executions.
For clarity and differentiation, data collected during user registration are denoted as matrices and , where serves as the baseline value. Subsequently, data collected during logins is represented using matrix B.
4.2. Data Processing
Upon receiving the browser cache side-channel data B sent by the client during logins, the server processes it according to the procedure outlined in Figure 4. Initially, the server calculates the average values of each column of the array and transforms them into a non-periodic curve. Subsequently, all elements of the array are normalized and converted into complex numbers, with their length extended to the nearest power of two. The FFT algorithm is then applied to the array with the butterfly operation to reduce the overall computational effort. Finally, authentication is performed by calculating the correlation between two different sets of data using the Inverse FFT (IFFT) algorithm and the K-Nearest Neighbors (KNN) algorithm. The specific process is described as follows:
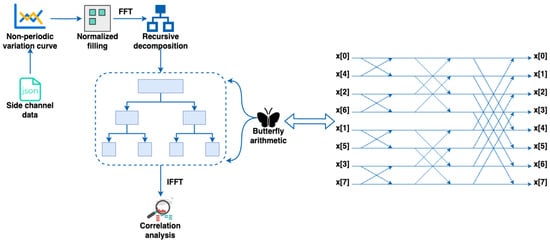
Figure 4.
The process of cache side-channel data processing.
- Mean ComputationWe convert the cache side-channel data , , and B into one-dimensional vectors , , and according to the following equation:
- Complex FormulationSubsequently, we apply Equation (3) to convert the elements within the vectors , , and into complex numbers, and pad their length to the smallest power of 2.
- Fast Fourier TransformFFT is an efficient algorithm to execute the Discrete Fourier Transform (DFT). It is a mathematical operation that transforms data from the time domain into a representation in the frequency domain. It can effectively analyze the frequency domain features of the data and help identify the similarity between two sets of data. We apply the FFT algorithm, as shown in Algorithm 1, to convert the vector to a vector F representing data in the frequency domain. Initially, the elements in the vector are divided into two parts: elements with even indexes and elements with odd indexes. Subsequently, F is computed by recursively performing the Fourier transform based on these two parts. During this process, the butterfly operation is employed to reduce the overall computational effort by combining smaller Fourier transforms into larger ones through recursion.
Algorithm 1 FFT - 1:
- Input:
- 2:
- Output: F
- 3:
- 4:
- if then
- 5:
- return
- 6:
- end if
- 7:
- ▹ elements of with even indexes
- 8:
- ▹ elements of with odd indexes
- 9:
- for k from 1 to do ▹ Perform the butterfly operation
- 10:
- ▹ Calculate the rotation factor
- 11:
- 12:
- 13:
- end for
- 14:
- return
- Correlation analysisAccording to Equation (4), we utilize the convolution theorem in the frequency domain to compute the correlation between data and , and between data and B, respectively. FFT*() denotes the covariance result after the Fast Fourier Transform, and IFFT() denotes the Inverse Fast Fourier Transform.The IFFT algorithm is the inverse operation of the Fast Fourier Transform. As shown in Algorithm 2, it transforms the product of browser cache side-channel data and in the frequency domain (denoted by and , respectively) to a vector R representing a list of correlations between and . The process begins by determining the length of the arrays. Each element of is then multiplied by the conjugate of the corresponding element in , with the results stored in a temporary array . This temporary array is subsequently conjugated and transformed using the FFT algorithm. The resulting array, , is again conjugated, and both its real and imaginary parts are normalized by dividing by the array length. The final result, R, represents the correlations between the original data sets in the time domain.
Algorithm 2 IFFT - 1:
- Input:
- 2:
- Output: R
- 3:
- 4:
- for j from 1 to l do ▹ Multiply each element of by the conjugate
- 5:
- of the corresponding element
- 6:
- ▹ Conjugate operation
- 7:
- 8:
- end for
- 9:
- for j from 1 to l do
- 10:
- 11:
- end for
- 12:
- 13:
- for j from 1 to l do
- 14:
- 15:
- ▹ the real part of
- 16:
- ▹ the imaginary part of
- 17:
- end for
- 18:
- return
4.3. Browser Fingerprint Generation
We apply the browser fingerprint generation (BFG) algorithm based on Manhattan distance and the KNN algorithm to transform data correlation into browser fingerprints for authentication. The KNN algorithm, as shown in Algorithm 3, is a distance-based machine-learning classification method that predicts the category of a new value based on the categories of the k nearest data points. Its theoretical maturity and lack of an extensive training process make it well-suited for enhancing real-time fingerprint identification. We collect n sets of baseline value data for each user during the registration phase, where and K is the number of nearest neighbors applied in the KNN algorithm. We use the symbol D to denote the correlation generated in the registration phase by all users. For m users, , where and . The Manhattan distance between the correlation and is calculated according to Equation (5) when a user logs in.
The results are sorted in ascending order, and the first K Manhattan distances are selected as the nearest neighbors. Subsequently, the user’s identity of data B denoted by is determined based on the principle of majority voting.
| Algorithm 3 BFG |
|
4.4. Timestamp Analysis
However, in the above process, an attacker can launch man-in-the-middle attacks to indirectly bypass the authentication mechanism. Malware in the middle of communication can monitor and alter confidential information [41]. To prevent this attack, we introduce the concept of timestamp. Specifically, we assume that the server notifies a client at time and subsequently receives data from the client at time . Upon completing the browser cache side-channel data collection, the client records the time as and transmits both the data and the timestamp to the server. We assume that the network remains stable for a brief period. In this scenario, the duration of data collection can be expressed as Equation (6).
We set a threshold . When , it is inferred that no man-in-the-middle attack has occurred. Conversely, if , it is deduced that a man-in-the-middle attack has transpired. Even in the presence of network delays, as illustrated in Figure 5, the duration for data collection remains consistent, expressed as , where and denote the completion time of data collection and the time of receiving data in the delayed environment, respectively. Through this analysis, we ascertain that our scheme remains unaffected by network delays.
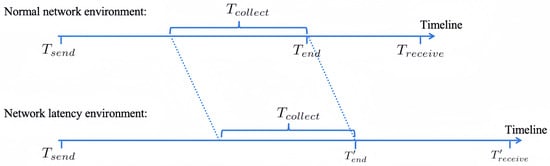
Figure 5.
Comparison of Authentication Duration in a Normal Environment and Delay Environment.
5. Security and Privacy Analysis
This section analyzes how this scheme can successfully protect user privacy and resist both man-in-the-middle attacks and phishing attacks.
5.1. Security Analysis
5.1.1. Resistance to Man-in-the-Middle Attacks
This scheme can resist man-in-the-middle attacks against IP redirection and timestamp modification.
- IP redirectionThe attacker attempts to achieve unauthorized login by altering the IP address upon receiving data from victims. In this case, the duration of fingerprint collection is represented as , where denotes the time of receiving data when encountering man-in-the-middle attacks. As shown in Figure 6, the process by which attackers alter IP addresses extends the duration of fingerprint collection, ultimately falling outside the normal range.
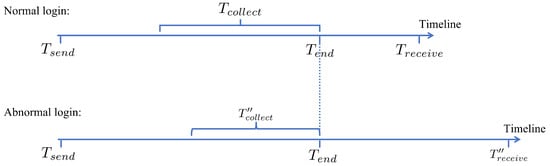 Figure 6. Comparison of Authentication Duration between Normal Login and IP Redirection.
Figure 6. Comparison of Authentication Duration between Normal Login and IP Redirection. - Timestamp ModificationAdditionally, the attacker may attempt to manipulate the completion time of the browser cache side-channel data collection () to ensure that the overall duration of data collection appears normal. As shown in Figure 7, according to Equation (7), executing this attack requires the attacker to simultaneously know the start time of data collection (), , and . However, and are collected only on the server side, which is a trusted entity. Additionally, is not collected during the entire communication process. Therefore, this scheme effectively mitigates man-in-the-middle attacks involving timestamp modification.
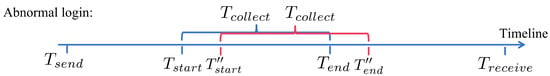 Figure 7. Timeline when Timestamp Modification.
Figure 7. Timeline when Timestamp Modification.
In summary, this scheme can effectively resist man-in-the-middle attacks.
5.1.2. Resistance to Phishing Attacks
Browser cache side-channel data are tightly bound to users’ devices. For device fingerprinting [42], even if these data are obtained illicitly by an attacker through phishing attacks, it is challenging for the attacker to simulate it on their device without access to detailed parameters of the victim’s device. Moreover, the diversity of devices further decreases the likelihood of collision. Consequently, our scheme effectively resists phishing attacks.
5.2. Privacy Analysis
On one hand, the browser cache side-channel data are a mapping of hardware devices and external resources. Without knowledge of the external resources, an attacker cannot infer the hardware device parameters through the browser cache side-channel data. On the other hand, hardware device parameters do not contain the personal identity information of the user. Even if an attacker illegally obtains hardware device parameters, it is impossible to obtain any information related to the user’s identity. Therefore, the browser cache side-channel data do not pose a threat to user privacy.
6. Evaluation
In this section, we first analyze the computation complexity of algorithms proposed in Section 4. Subsequently, we verify the uniqueness and stability of the browser cache side-channel data. Finally, we test the accuracy of our browser fingerprint authentication scheme.
6.1. Computation Overhead
We analyze the computation complexity of three algorithms, FFT, IFFT, and BFG, as shown in Table 2:

Table 2.
Algorithmic Computation Complexity.
The FFT and IFFT algorithms both exhibit a complexity of , where l represents the length of the input. These two algorithms are independent of the number of users, making them highly suitable for a wide range of applications. The BFG algorithm, with a complexity of , where m and n denote the number of users and baseline values, respectively, scales sub-exponentially with the number of users. It is relatively more computationally intensive. However, for moderate problem sizes, this overhead remains manageable. To improve scalability, we can further enhance the computation efficiency by employing optimization strategies such as multi-threading, multiple servers, or high-performance server configurations.
6.2. Uniqueness Test
We initially tested uniqueness by comparing the correlation of browser cache side-channel data from 11 different devices. The configurations of these devices are detailed in Table 3.

Table 3.
Device Configuration.
All devices’ browsers execute the registration operation with the same baseline value. Subsequently, each device performs 300 login operations to collect browser cache side-channel data, followed by correlation calculations with the baseline value. As depicted in Figure 8, it is evident that browser cache side-channel data from different devices exhibit high uniqueness after FFT operations and correlation calculations.
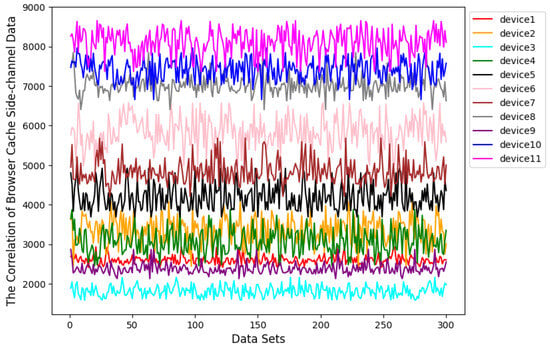
Figure 8.
Browser Cache Side-channel Data Correlation Results from Different Devices.
6.3. Stability Test
We test the stability of browser cache side-channel data by comparing its correlation across time. Our scheme is implemented on a desktop running the Windows 10 operating system, equipped with an Intel Core i7 CPU and 32 GB of RAM.
We perform login operations every three months, collecting 50 sets of browser cache side-channel data each time. Subsequently, we calculate their correlation with the baseline value. As illustrated in Figure 9, the correlation results of the browser cache side-channel data from the same device remain highly similar after two months, indicating a high degree of stability of the browser cache side-channel data.
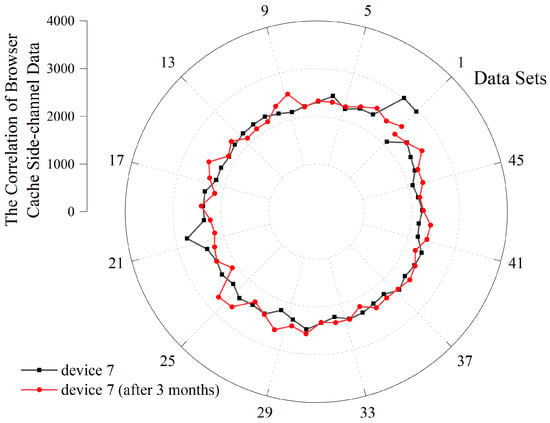
Figure 9.
Browser Cache Side-channel Data Correlation Results of Different Time.
6.4. Accuracy Test
We evaluate the accuracy of our browser fingerprint authentication using the following metrics:
- Recall Rate (): The proportion of legitimate users judged to be legitimate users.
- False Acceptance Rate (): The proportion of illegal users judged to be legitimate users.
- False Rejection Rate (): The proportion of legitimate users judged to be illegitimate users.
These metrics are calculated based on the following equations:
Among them, true positive () denotes the number of legitimate users judged to be legitimate users, false negative () denotes the number of legitimate users judged to be illegal users, false positive () denotes the number of illegal users judged to be legitimate users, and true negative () denotes the number of illegal users judged to be illegal users.
We designate 15 groups of devices, with configurations selected from Table 3, to act as attackers and victims, respectively. In this setup, attackers attempt to obtain the victim’s account, password, and other information through phishing attacks, simulating the victim’s login. This experiment collects 300 pieces of browser cache side-channel data to generate browser fingerprints. The fingerprints provided by the attacker and the victim are mixed before being sent to the server for verification.
We first test the effect of different values of K on the . As presented in Figure 10, is highly sensitive to noise when because only 1 nearest neighbor is considered, resulting in lower accuracy. The highest , at 96.17%, is achieved when . The shows a gradual decrease as the value of K increases beyond 3.
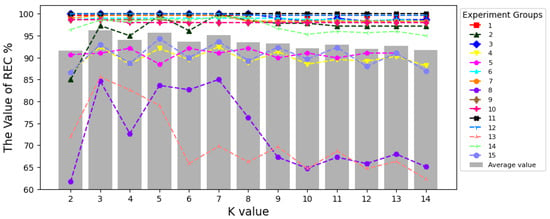
Figure 10.
The Effect of Different K Values on Recall Rate.
Then, we test the effect of different values of K on the . As shown in Figure 11, the lowest FAR, at 0, is achieved when . The increases when , and becomes stable when .
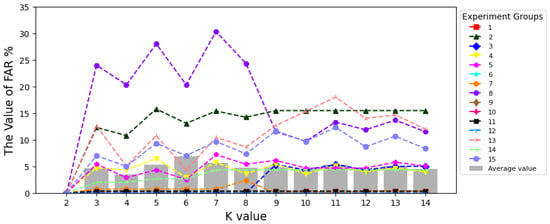
Figure 11.
The Effect of Different K Values on False Acceptance Rate.
Finally, we test the effect of different values of K on the . As shown in Figure 12, the reaches its minimum at 3.83% when . Beyond this point, the exhibits an upward trend as the value of K continues to increase.
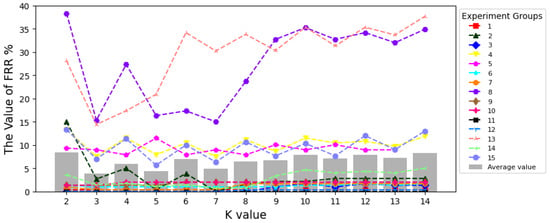
Figure 12.
The Effect of Different K Values on False Rejection Rate.
The verification results for and are summarized in Table 4. In summary, the values of and are optimized at 96.17% and 3.83%, respectively, when K = 3, with at 4.67%. When , reaches its minimum at 0%, while and are 91.58% and 8.42%, respectively. These values demonstrate that our scheme exhibits strong resistance to phishing attacks [35].

Table 4.
The Accuracy of Our Browser Fingerprint Authentication Scheme when K = 2 and K = 3.
The (Cross-)Browser Fingerprinting scheme [43] achieved authentication by extracting and combining stable features of the operating system and hardware across different browsers on the same device to create unique user fingerprints, yielding a of 90.84% and a of 9.16%. As shown in Table 5, our scheme significantly improves the compared to this method. Additionally, the FP-Inspector scheme [44] realized authentication by combining static and dynamic analysis of illegal behaviors through a machine-learning approach. It detects browser fingerprinting through machine-learning classifiers that extract features from script contents and execution traces. This scheme has a of 6.2%, which is higher than that of our scheme.

Table 5.
Performance Comparison.
7. Conclusions
We proposed a browser fingerprint authentication scheme in this paper, which integrates browser cache side-channel technology. It offers a promising solution to enhance user security during online authentication processes. By leveraging the stability and uniqueness of browser cache side-channel data, this scheme effectively mitigates phishing attacks and man-in-the-middle attacks, achieving high recognition and recall rates for both attackers and authorized users. The experimental results demonstrate the scheme’s ability to resist malicious activities and maintain a high level of authentication accuracy even in the presence of sophisticated attacks. Overall, this innovative approach contributes to strengthening browser identity authentication, addressing the limitations of traditional methods, and bolstering overall protection in the online environment.
This scheme relies on the assumption that the server is fully trusted and secure, making it vulnerable to attacks targeting the server in reality. If an attacker gains control of the server, authentication anomalies and potential breaches could occur. Additionally, this scheme, like many security solutions, faces significant challenges in defending against zero-day attacks. These sophisticated attacks exploit previously unknown vulnerabilities, making detection and mitigation difficult with existing measures. To enhance security, we could deploy a Trusted Execution Environment (TEE) within the server in future work. A TEE can provide a secure, isolated area to perform sensitive operations, protecting the server from external attacks. Moreover, future work could incorporate machine-learning models for anomaly detection to improve the scheme’s ability to identify zero-day attacks. These models can analyze patterns in browser cache side-channel data and user behavior to detect deviations that might indicate an exploit. Additionally, regular security audits and penetration testing should be conducted to identify and address potential vulnerabilities proactively. Combining these strategies can significantly fortify the scheme against zero-day attacks, enhancing overall system resilience.
Author Contributions
Conceptualization, Y.Y.; methodology, Y.Y.; software, Y.Y.; validation, Y.Y.; formal analysis, Y.Y. and H.Q.; investigation, Y.Y.; resources, Y.Y.; data curation, Y.Y.; writing—original draft preparation, Y.Y. and H.Z.; writing—review and editing, Y.Y., H.Z. and H.Q. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the Undergraduate Teaching Reform Research Program of Shandong Province (No. M2023218).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Rock, L.Y.; Tajudeen, F.P.; Chung, Y.W. Usage and impact of the internet-of-things-based smart home technology: A quality-of-life perspective. Univers. Access Inf. Soc. 2024, 23, 345–364. [Google Scholar] [CrossRef] [PubMed]
- Laperdrix, P.; Bielova, N.; Baudry, B.; Avoine, G. Browser fingerprinting: A survey. ACM Trans. Web (TWEB) 2020, 14, 1–33. [Google Scholar] [CrossRef]
- Laperdrix, P.; Rudametkin, W.; Baudry, B. Beauty and the beast: Diverting modern web browsers to build unique browser fingerprints. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 878–894. [Google Scholar]
- DiMaggio, P.; Hargittai, E.; Neuman, W.R.; Robinson, J.P. Social implications of the Internet. Annu. Rev. Sociol. 2001, 27, 307–336. [Google Scholar] [CrossRef]
- Ross, B.; Jackson, C.; Miyake, N.; Boneh, D.; Mitchell, J.C. Stronger Password Authentication Using Browser Extensions. In Proceedings of the USENIX Security Symposium, Baltimore, MD, USA, 31 July–5 August 2005; Volume 17, p. 32. [Google Scholar]
- Laperdrix, P.; Avoine, G.; Baudry, B.; Nikiforakis, N. Morellian analysis for browsers: Making web authentication stronger with canvas fingerprinting. In Proceedings of the Detection of Intrusions and Malware, and Vulnerability Assessment: 16th International Conference, DIMVA 2019, Gothenburg, Sweden, 19–20 June 2019; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2019; pp. 43–66. [Google Scholar]
- Al Kabir, M.A.; Elmedany, W. Adaptive Risk-Based Passwordless Authentication: A Fido2 Integrated Approach for Enhanced Security and Usability. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4795401 (accessed on 9 July 2024).
- Tyagi, V.; Saraswat, A.; Bansal, S. An Analysis of Securing Internet of Things (IoT) Devices from Man-in-the-Middle (MIMA) and Denial of Service (DoS). In Smart Cities; CRC Press: Boca Raton, FL, USA, 2023; pp. 337–357. [Google Scholar]
- Andriamilanto, N.; Allard, T.; Le Guelvouit, G. FPSelect: Low-cost browser fingerprints for mitigating dictionary attacks against web authentication mechanisms. In Proceedings of the 36th Annual Computer Security Applications Conference, Virtual, 7–11 December 2020; pp. 627–642. [Google Scholar]
- Otta, S.P.; Panda, S.; Gupta, M.; Hota, C. A systematic survey of multi-factor authentication for cloud infrastructure. Future Internet 2023, 15, 146. [Google Scholar] [CrossRef]
- Mohammed, A.H.Y.; Dziyauddin, R.A.; Latiff, L.A. Current multi-factor of authentication: Approaches, requirements, attacks and challenges. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 166–177. [Google Scholar] [CrossRef]
- Gómez-Boix, A.; Laperdrix, P.; Baudry, B. Hiding in the crowd: An analysis of the effectiveness of browser fingerprinting at large scale. In Proceedings of the 2018 World Wide Web Conference, Lyon, France, 23–27 April 2018; pp. 309–318. [Google Scholar]
- Upathilake, R.; Li, Y.; Matrawy, A. A classification of web browser fingerprinting techniques. In Proceedings of the 2015 7th International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 27–29 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–5. [Google Scholar]
- Durey, A.; Laperdrix, P.; Rudametkin, W.; Rouvoy, R. FP-Redemption: Studying browser fingerprinting adoption for the sake of web security. In Proceedings of the Detection of Intrusions and Malware, and Vulnerability Assessment: 18th International Conference, DIMVA 2021, Virtual Event, 14–16 July 2021; Proceedings 18. Springer: Berlin/Heidelberg, Germany, 2021; pp. 237–257. [Google Scholar]
- Andriamilanto, N.; Allard, T.; Guelvouit, G.L. “Guess Who?” Large-scale data-centric study of the adequacy of browser fingerprints for web authentication. In Proceedings of the Innovative Mobile and Internet Services in Ubiquitous Computing: Proceedings of the 14th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS-2020), Lodz, Poland, 1–3 July 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 161–172. [Google Scholar]
- Eckersley, P. How unique is your web browser? In Proceedings of the Privacy Enhancing Technologies: 10th International Symposium, PETS 2010, Berlin, Germany, 21–23 July 2010; Proceedings 10. Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–18. [Google Scholar]
- Bursztein, E.; Benko, B.; Margolis, D.; Pietraszek, T.; Archer, A.; Aquino, A.; Pitsillidis, A.; Savage, S. Handcrafted fraud and extortion: Manual account hijacking in the wild. In Proceedings of the 2014 Conference on Internet Measurement Conference, Vancouver, BC, Canada, 5–7 November 2014; pp. 347–358. [Google Scholar]
- Sanchez-Rola, I.; Bilge, L.; Balzarotti, D.; Buescher, A.; Efstathopoulos, P. Rods with laser beams: Understanding browser fingerprinting on phishing pages. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 4157–4173. [Google Scholar]
- Zaheri, M.; Oren, Y.; Curtmola, R. Targeted deanonymization via the cache side channel: Attacks and defenses. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 1505–1523. [Google Scholar]
- Ge, Q.; Yarom, Y.; Cock, D.; Heiser, G. A survey of microarchitectural timing attacks and countermeasures on contemporary hardware. J. Cryptogr. Eng. 2018, 8, 1–27. [Google Scholar] [CrossRef]
- Bazm, M.M.; Sautereau, T.; Lacoste, M.; Sudholt, M.; Menaud, J.M. Cache-based side-channel attacks detection through intel cache monitoring technology and hardware performance counters. In Proceedings of the 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 7–12. [Google Scholar]
- Randolph, M.; Diehl, W. Power side-channel attack analysis: A review of 20 years of study for the layman. Cryptography 2020, 4, 15. [Google Scholar] [CrossRef]
- Standaert, F.X. Introduction to side-channel attacks. In Secure Integrated Circuits and Systems; Springer: Berlin/Heidelberg, Germany, 2010; pp. 27–42. [Google Scholar]
- Gruss, D.; Maurice, C.; Wagner, K.; Mangard, S. Flush+ Flush: A fast and stealthy cache attack. In Proceedings of the Detection of Intrusions and Malware, and Vulnerability Assessment: 13th International Conference, DIMVA 2016, San Sebastián, Spain, 7–8 July 2016; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2016; pp. 279–299. [Google Scholar]
- Osvik, D.A.; Shamir, A.; Tromer, E. Cache attacks and countermeasures: The case of AES. In Proceedings of the Topics in Cryptology—CT-RSA 2006: The Cryptographers’ Track at the RSA Conference 2006, San Jose, CA, USA, 13–17 February 2005; Proceedings. Springer: Berlin/Heidelberg, Germany, 2006; pp. 1–20. [Google Scholar]
- Shusterman, A.; Avraham, Z.; Croitoru, E.; Haskal, Y.; Kang, L.; Levi, D.; Meltser, Y.; Mittal, P.; Oren, Y.; Yarom, Y. Website fingerprinting through the cache occupancy channel and its real world practicality. IEEE Trans. Dependable Secur. Comput. 2020, 18, 2042–2060. [Google Scholar] [CrossRef]
- Cronin, P.; Gao, X.; Wang, H.; Cotton, C. An exploration of ARM system-level cache and GPU side channels. In Proceedings of the 37th Annual Computer Security Applications Conference, Virtual Conference, 6–10 December 2021; pp. 784–795. [Google Scholar]
- Andriamilanto, N.; Allard, T.; Le Guelvouit, G.; Garel, A. A large-scale empirical analysis of browser fingerprints properties for web authentication. ACM Trans. Web (TWEB) 2021, 16, 1–62. [Google Scholar] [CrossRef]
- Nikiforakis, N.; Kapravelos, A.; Joosen, W.; Kruegel, C.; Piessens, F.; Vigna, G. Cookieless monster: Exploring the ecosystem of web-based device fingerprinting. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 541–555. [Google Scholar]
- Queiroz, J.S.; Feitosa, E.L. A web browser fingerprinting method based on the web audio API. Comput. J. 2019, 62, 1106–1120. [Google Scholar] [CrossRef]
- Karami, S.; Ilia, P.; Solomos, K.; Polakis, J. Carnus: Exploring the Privacy Threats of Browser Extension Fingerprinting. In Proceedings of the 27th Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 23–26 February 2020. [Google Scholar]
- Stragapede, G.; Vera-Rodriguez, R.; Tolosana, R.; Morales, A.; Acien, A.; Le Lan, G. Mobile behavioral biometrics for passive authentication. Pattern Recognit. Lett. 2022, 157, 35–41. [Google Scholar] [CrossRef]
- Sánchez, P.M.S.; Valero, J.M.J.; Celdrán, A.H.; Bovet, G.; Pérez, M.G.; Pérez, G.M. A survey on device behavior fingerprinting: Data sources, techniques, application scenarios, and datasets. IEEE Commun. Surv. Tutor. 2021, 23, 1048–1077. [Google Scholar] [CrossRef]
- Andriamilanto, N.; Allard, T. Brfast: A tool to select browser fingerprinting attributes for web authentication according to a usability-security trade-off. In Proceedings of the Companion Proceedings of the Web Conference 2021, Ljubljana, Slovenia, 19–23 April 2021; pp. 701–704. [Google Scholar]
- Lin, X.; Ilia, P.; Solanki, S.; Polakis, J. Phish in sheep’s clothing: Exploring the authentication pitfalls of browser fingerprinting. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 1651–1668. [Google Scholar]
- Alkhalil, Z.; Hewage, C.; Nawaf, L.; Khan, I. Phishing attacks: A recent comprehensive study and a new anatomy. Front. Comput. Sci. 2021, 3, 563060. [Google Scholar] [CrossRef]
- Alabdan, R. Phishing attacks survey: Types, vectors, and technical approaches. Future Internet 2020, 12, 168. [Google Scholar] [CrossRef]
- Gupta, B.B.; Tewari, A.; Jain, A.K.; Agrawal, D.P. Fighting against phishing attacks: State of the art and future challenges. Neural Comput. Appl. 2017, 28, 3629–3654. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Callegati, F.; Cerroni, W.; Ramilli, M. Man-in-the-Middle Attack to the HTTPS Protocol. IEEE Secur. Priv. 2009, 7, 78–81. [Google Scholar] [CrossRef]
- Mallik, A. Man-in-the-middle-attack: Understanding in simple words. Cyberspace J. Pendidik. Teknol. Inf. 2019, 2, 109–134. [Google Scholar] [CrossRef]
- Alaca, F.; Van Oorschot, P.C. Device fingerprinting for augmenting web authentication: Classification and analysis of methods. In Proceedings of the 32nd Annual Conference on Computer Security Applications, Los Angeles, CA, USA, 5–9 December 2016; pp. 289–301. [Google Scholar]
- Cao, Y.; Li, S.; Wijmans, E. (Cross-) browser fingerprinting via OS and hardware level features. In Proceedings of the Proceedings 2017 Network and Distributed System Security Symposium. Internet Society, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Iqbal, U.; Englehardt, S.; Shafiq, Z. Fingerprinting the fingerprinters: Learning to detect browser fingerprinting behaviors. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2020; IEEE: Piscataway, NJ, USA, 2021; pp. 1143–1161. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).