Abstract
In literature, there are a number of cryptographic algorithms (RSA, ElGamal, NTRU, etc.) that require multiple computations of modulo multiplicative inverses. In this paper, we describe the modulo operation and we recollect the main approaches to computing the modulus. Then, given a and n positive integers, we present the sequence , where , and . Regarding the above sequence, we show that it is bounded and admits a simple explicit, periodic solution. The main result is that the inverse of a modulo n is given by with . The computational cost of such an index i is , which is less than of the Euler’s phi function. Furthermore, we suggest an algorithm for the computation of using plain multiplications instead of modular multiplications. The latter, still, has complexity versus complexity (naive algorithm) or complexity (extended Euclidean algorithm). Therefore, the above procedure is more convenient when (e.g., ).
Keywords:
extended-Euclid algorithm; RSA algorithm; modular multiplicative inverse; public-key cryptography MSC:
11T71; 11Y16; 11Y05
1. Introduction
The modulo operation returns the remainder of a division, after one number is divided by another number called “modulus”. In other terms, given two positive numbers a and n, is the remainder of the Euclidean division of the dividend a by the divisor n.
A modular multiplicative inverse of an integer a is an integer x such that the product is congruent to 1 with respect to the modulus n, and it is denoted as
Modulo n is an equivalence relation. The equivalence class of the integer a, denoted by , is the set . This set, consisting of all the integers congruent to a modulo n, is called congruence class or residue class of the integer a modulo n.
If a has an inverse modulo n, then there are an infinite number of solutions that belong to the congruence class with respect to the said modulus. In addition, any integer that is congruent to a will have any element of x’s congruence class as a modular multiplicative inverse. In other terms, denoted with the symbol , the multiplication of equivalence classes modulo n, the modulo multiplicative inverse of the congruence class is the congruence class such that:
This multiplication is the analogue of the multiplicative inverse in the set of real numbers where numbers are replaced by congruence classes. Therefore, a fundamental use of this operation is to solve (whenever possible) linear congruences of the form
The solution of Equation (1) has practical applications in the field of public-key cryptography and, in particular, in the Rivest–Shamir–Adleman (RSA) algorithm [1] where encryption and decryption are performed by using a pair of large prime numbers that are multiplicative inverses with respect to a selected modulus.
When invented, RSA was considered one of the most effective algorithms because there was no key exchange in the encryption and decryption processes. In the RSA algorithm, the strength depends on the factorization problem that is NP complete [2] and the key length was the only way to protect systems. However, the RSA key is broken from time to time due to the development of both software and computer speed. To counter that, developers have increased key length from one time to another to maintain a high security and privacy to systems that are protected by the RSA. Other countermeasures vary from using multiple public and private keys [3] to enhance and secure the RSA public key cryptosystem (ESRPKC) algorithm using the Chinese remainder theorem [4], from the use of a pair of random numbers and their modular multiplicative inverse [5] to the Cuckoo Search Optimization (CSA) algorithm for securing data integrity in the cloud [6]. For a survey, see Mumtaz et al. [7].
As mentioned, cryptographic algorithms rely on multiple computations of modulo multiplicative inverses. Examples are the RSA cryptographic algorithm by [8,9], RSA with digital signature [10], ElGamal cryptocol [11]; encryption and decryption schemes based on extraction of square roots [12], NTRU cryptosystem [13], modular multiplicative inverse (MMI) for cryptanalysis of public-key cryptographic protocols [14], etc. Recently, Boolean functions have gained attraction because of some interesting properties from a cryptographic point of view such as “nonlinearity, propagation criterion, resiliency, and balance” [15]. However, following similar research on RSA cryptographic algorithms, we focused on the problem of encrypting/decoding information based on the use of the vector-modular methods. For example, Yakymenko et al. [16] suggest a modular exponential to “replace the complex operation of modular multiplication with the addition operation, which increases the speed of the RSA cryptosystem”. In our case, instead, we investigate the properties of the sequence in Definition 1, which we show to be useful for computing the inverse modulo. In particular, for the above sequence, we show that it is bounded and admits a simple explicit, periodic solution. Next, we illustrate that the inverse of a modulo n is given by with . The advantage is that the computational cost of such an index i is versus of the Euler’s phi function. Finally, we suggest an algorithm for calculating using plain multiplications instead of modular multiplications. The latter, again, has complexity versus complexity of the extended Euclidean algorithm. Therefore, the above procedure is more convenient when (e.g., ). Those results are new in literature.
2. Main Approaches to the Computation of Modulus
In the following, we describe the most common methods to compute the inverse modulo n.
2.1. Naive Method (Recursive Multiplications)
This is the simplest way to compute the inverse of a positive integer a, modulo n, with and greatest common divisor . We have to multiply a by all the elements of and the first of them which gives a product equal to 1 (modulo n) will be the inverse of a. The complexity in this case is .
Example 1.
To find the inverse of modulo , we have to multiply a by every element of , i.e.,
Therefore, modulo 7.
2.2. Euler’s Phi Function
The following approach was introduced in modern terms by Gauss with reference to Euler (even though the method has been reported before [17]). Given a positive integer n, the Euler’s phi function (or Euler’s totient function) counts the number of primes, up to n, which are relatively prime to n. It can be expressed as
with ’s being the primes dividing n. Given a positive integer a, with and , one has
due to the well-known Fermat’s little theorem. The above relation provides an explicit formula for the inverse of a modulo n that is
However, the calculation of is equivalent to doing the prime factorization of n, hence the complexity of Formula (2) is . Thus, despite (2) giving a closed formula, it is less convenient than a recursive algorithm (like those of Section 2.1 and Section 2.3).
Example 2.
2.3. Extended Euclidean Algorithm
One of the ancient methods to compute the GCD between two integers , with , is given by the Euclidean algorithm. It is based on the following property: if both a and b divide a same integer c, then also their difference divides c. The algorithm states that if the difference is equal to b; otherwise, are replaced by and , respectively, and the previous procedure is repeated by computing the new difference d. Table 1 describes the pseudocode of the algorithm.

Table 1.
Pseudocode of the Euclidean algorithm (repeated differences).
An interesting extension of such method works with repeated divisions instead of the repeated differences. By computing the following quotients and remainders ,
it is possible to say that is the last non-zero remainder . The complexity of this method is . The pseudocode of this procedure is reported in Table 2.

Table 2.
Pseudocode of the Euclidean algorithm (repeated divisions).
The above method allows us to compute the inverse modulo n through the so-called Bézouts’s identity which states that there exist two integer such that
The numbers can be computed from the quotients (), by reversing the order of the equations in the Euclidean algorithm (with repeated divisions). Beginning with the last non-zero remainder , we can write
The quantity may be likewise expressed in terms of their quotients and preceding remainders, i.e.,
Substituting these formulas into the first equation yields as a linear sum of . The process of substituting remainders by formulas involving their predecessors can be continued until a and b are reached, as follows:
After all the remainders () have been replaced, the final equation expresses as the linear combination .
In the special case that , then t is the multiplicative inverse of b, modulo a, or, equivalently, s is the multiplicative inverse of a, modulo b.
The pseudocode of this method is shown in Table 3.

Table 3.
Pseudocode of the inverse modulo n (through the extended Euclidean algorithm).
Example 3.
Consider and . Obviously, . The extended Euclidean algorithm gives
By rewriting the next steps backward, we obtain
where . Hence, we can conclude that .
3. The Sequence : Definition and Properties
In this section, given a and n positive integers, we define the sequence , where , and . For the said sequence, we illustrate some properties and results useful to the computation of the inverse modulo.
3.1. Definitions and Main Results
Definition 1.
Given two positive integers with and , define the sequence as follows:
starting from , with
with M being the ceiling part of .
Observe that ’s represent the (ceiling) difference between n and relative to a.
Next, the Proposition gives an explicit expression for the sequence .
Proposition 1.
The explicit form of the sequence defined in (3) is given by
Proof.
□
The following Proposition gives an explicit, and more convenient, expression for the sequence .
Proposition 2.
Proof.
□
Corollary 1.
Now, we are able to state the main results of this section.
Theorem 1.
Proof.
Since , from the Bézouts’s identity, there exists an index such that . Indeed, without loss of generality, there exist a pair of positive integers such that
Fixing i, from the above equation, we obtain
where we denote by
the fractional part function of . In particular, the last equality of (10) holds true because both g and are positive integers. Thus, as and belong to we can say that must be equal to 1. Hence,
and, more specifically,
which implies
where the last equality comes from Proposition 2. Finally, notice that (see Corollary 2) and this concludes the proof. □
3.2. Properties of the Sequence
To better understand the nature of the sequence , we illustrate the following properties.
Proposition 3.
The sequence defined in (3) is periodic with a period equal to a.
Proof.
For any , we have to prove that . Let us proceed by induction on j. If ,
□
Corollary 2.
Proof.
From Proposition 3, we have to prove that for any . For this purpose, distinguish the following three cases:
- (i)
- The is trivial.
- (ii)
- If , we have
- (iii)
- The case may be proved analogously to ii).
Finally, it is clear that the modular inverse defined in (9), i.e., , is less than n since . □
To see what was observed up to now, we shall consider a numerical example.
Example 4.
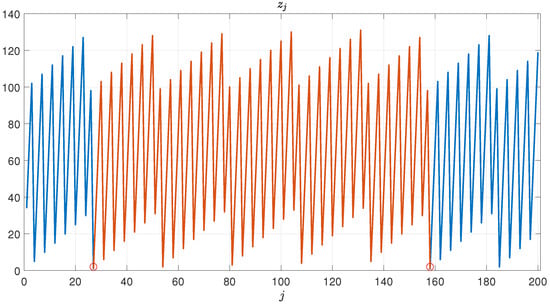
Choose and . Obviously, that guarantees the existence of . It is obtained by and
modulo 621. Figure 1 shows the behavior of the sequence . In particular, the blue line denotes the series when , while those colored in red represent the entire sequence from two consecutive unitary ’s (circled in red), i.e., and . As proved, the series is periodic with a period equal to 131 and any value less than 621.

Figure 1.
Sequence when and . The red line highlights the entire sequence between two consecutive unitary ’s (red circles).
3.3. Limitations and Future Challenges
A limitation of the proposed approach is that we have left the problem of determining the index i unsolved. In fact, by virtue of Theorem 1, we need to compute , such that
Observe that , where is defined by (11), and can be easily computed, as follows.
Proposition 4.
Let i be the solution of Equation (12); then, one has
Example 5.
With reference to Example 4, we have and . By computing directly from i, we obtain the value , which coincides with that given by the a priori Formula (13).
The knowledge of jointly with the periodicity information given by Proposition 4 suggests to solve the problem (12) by the simple algorithm described in Table 4.

Table 4.
Pseudocode of a simple algorithm to solve (12).
Notice that the complexity of the algorithm just shown in Table 4 is . Therefore, the above procedure is more convenient when (e.g., ). In addition, when a is close to n, the algorithm in Table 4 is still better compared to the naive algorithm in Table 1 (since it involves simple multiplications instead of modular multiplications). Furthermore, Equation (9) represents a closed formula for the modular inverse, as does Equation (2), where the computational cost of the index i is . This is less than of the Euler’s phi function. These features are a clear advantage when n is large.
4. Conclusions
In this article, we have introduced the modulo operation and described the most common methods for computing the inverse modulo n. Hence, we have shown that, to solve the problem in Equation (12) through a closed formula, we need to investigate the properties of the sequence . The fact that the sequence admits a simple explicit form which is periodic (for ) helps us in understanding the features of . In particular, we have shown that the computational cost is versus of Euler’s phi function. In terms of implementation, we suggest an algorithm for calculating using plain multiplications instead of modular multiplications. From a practical point of view, this approach is quite convenient because it has complexity compared to of the extended Euclidean algorithm. This result is related to the characteristics of i, and, consequently, of . Next, research will focus on the determination of the index i such that .
Author Contributions
Conceptualization, M.B.; methodology, M.B. and D.B.; software, D.B.; validation, G.O., M.B. and D.B., formal analysis, M.B. and D.B.; investigation, G.O., M.B. and D.B.; resources, M.B. and D.B.; data curation, M.B. and D.B.; writing—original draft preparation, M.B.; writing—review and editing, G.O. and M.B.; visualization, G.O. and M.B.; supervision, G.O. and M.B.; project administration, G.O. and M.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
No applicable.
Informed Consent Statement
No applicable.
Data Availability Statement
No applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Rivest, R.L.; Shamir, A.; Adleman, L.M. Cryptographic Communications System and Method. U.S. Patent 4,405,829, 20 September 1983. [Google Scholar]
- Somani, U.; Lakhani, K.; Mundra, M. Implementing digital signature with RSA encryption algorithm to enhance the Data Security of cloud in Cloud Computing. In Proceedings of the 2010 First International Conference On Parallel, Distributed and Grid Computing (PDGC 2010), Solan, India, 28–30 October 2010; pp. 211–216. [Google Scholar]
- Mezher, A.E. Enhanced RSA cryptosystem based on multiplicity of public and private keys. Int. J. Electr. Comput. Eng. 2018, 8, 3949. [Google Scholar] [CrossRef][Green Version]
- Kumar, V.; Kumar, R.; Pandey, S. An enhanced and secured RSA public key cryptosystem algorithm using Chinese remainder theorem. In Proceedings of the International Conference on Next, Generation Computing Technologies, Dehradun, India, 30–31 October 217; Springer: Berlin/Heidelberg, Germany, 2017; pp. 543–554. [Google Scholar]
- Islam, M.A.; Islam, M.A.; Islam, N.; Shabnam, B. A modified and secured RSA public key cryptosystem based on “n” prime numbers. J. Comput. Commun. 2018, 6, 78. [Google Scholar] [CrossRef]
- Raja shree, S.; Chilambu Chelvan, A.; Rajesh, M. An efficient RSA cryptosystem by applying cuckoo search optimization algorithm. Concurr. Comput. Pract. Exp. 2019, 31, e4845. [Google Scholar] [CrossRef]
- Mumtaz, M.; Ping, L. Forty years of attacks on the RSA cryptosystem: A brief survey. J. Discret. Math. Sci. Cryptogr. 2019, 22, 9–29. [Google Scholar] [CrossRef]
- Crandall, R.; Pomerance, C.B. Prime Numbers: A Computational Perspective; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006; Volume 182. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Verkhovsky, B. Overpass-Crossing Scheme for Digital Signature. In Proceedings of the International Conference on System Research, Informatics and Cybernetics, Baden-Baden, Germany, 30 July–4 August 2001; Volume 30. [Google Scholar]
- ElGamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Rabin, M.O. Digitalized Signatures and Public-Key Functions as Intractable as Factorization; Technical Report; Massachusetts Inst of Tech Cambridge Lab for Computer Science: Cambridge, MA, USA, 1979. [Google Scholar]
- Hoffstein, J.; Pipher, J.; Silverman, J.H.; Silverman, J.H. An Introduction to Mathematical Cryptography; Springer: Berlin/Heidelberg, Germany, 2008; Volume 1. [Google Scholar]
- Verkhovsky, B. Enhanced Euclid Algorithm for Modular Multiplicative Inverse and Its Application in Cryptographic Protocols. IJCNS 2010, 3, 901–906. [Google Scholar] [CrossRef]
- Sosa-Gómez, G.; Paez-Osuna, O.; Rojas, O.; Madarro-Capó, E.J. A New Family of Boolean Functions with Good Cryptographic Properties. Axioms 2021, 10, 42. [Google Scholar] [CrossRef]
- Yakymenko, I.; Kasianchuk, M.; Ivasiev, S.; Melnyk, A.; Nykolaichuk, Y.M. Realization of RSA cryptographic algorithm based on vector-module method of modular exponention. In Proceedings of the 2018 14th International Conference on Advanced Trends in Radioelecrtronics, Telecommunications and Computer Engineering (TCSET), Lviv-Slavske, Ukraine, 20–24 February 2018; pp. 550–554. [Google Scholar]
- Ore, O. Number Theory and Its History; Dover Books on Mathematics Series; Dover: Mineola, New York, USA, 1988; ISBN 9780486656205. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).