Abstract
In application scenarios such as cloud storage, a symmetric algorithm can be used to encrypt massive data. However, using the symmetric operation and keys in encryption and decryption, it is very difficult to realize an efficient access control system. The asymmetric encryption algorithm ciphertext-policy attribute-based encryption (CP-ABE), as a versatile one-to-many encryption algorithm, is considered an ideal access control tool to solve the user’s distrust of the service provider of cloud storage. However, in a traditional CP-ABE system, the malicious users may deliberately leak their attribute keys to others or build a decryption black box (DB) to provide illegal decryption services for benefits, while no one can determine their identities. To deal with the problems, especially the problem of tracing the DB builder, CP-ABE schemes with black-box traceability have been proposed in the past few years. But in this paper, we point out that for now, the tracing algorithms in all existing schemes actually work on an impractical assumption. That is, whenever a DB receives a decryption request, it always performs the decryption algorithm honestlycorrectly. We argue that if a DB finds the decryption request comes from the tracing algorithm, it may intentionally output incorrect decryption results to counter the tracing. Thus, we present the structural defect of the tracing algorithm applied to all known traceable CP-ABE schemes. We describe the construction of an alert decryption black box (ADB) that is capable of distinguishing a tracing ciphertext from a normal one. We also show how an ADB frustrates the tracing algorithm, and furthermore, malicious users can even apply an ADB to frame innocent users.
1. Introduction
In the case of data outsourcing such as cloud storage, a data user hosts their data in the cloud and usually uses the interface offered by the cloud service provider (CSP) to access or share their data. The data owner has to delegate access control of their data to the CSP while assuming the CSP is a fully trusted party. However, this assumption is not reasonable in many applications. It is more appropriate to consider the CSP as a semitrusted party, which means the CSP performs the operations honestly, whereas it may try to obtain the contents of the data. As one-to-many encryption cryptography, attribute-based encryption [1] (ABE), especially the ciphertext-policy attribute-based encryption (CP-ABE) variant [2], is viewed as an ideal approach to address the problem of distrust.
However, there exists a security obstacle in the practicality of the CP-ABE system, that is, how to prevent authorized users from abusing their privilege. The security problem can be summarized in two forms: (1) an authorized user may intentionally leak their attribute keys to others; and (2) the authorized users may build a decryption device/black box (DB) to provide a decryption service to others while keeping their keys hidden in it. The two cases are described in Figure 1a,b, respectively.
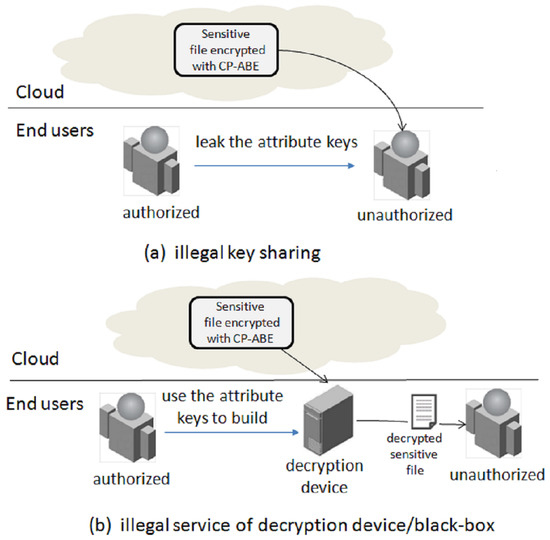
Figure 1.
Security issue of privilege abuse.
To deal with privilege abuse, Li et al. [3] firstly proposed an accountable CP-ABE scheme, which inserts some user-specific information into the user’s private key during the key generation. Hence, a malicious user, who performs illegal key sharing, can be identified with his private key. However, their scheme cannot handle case (b) in Figure 1, where the private keys of malicious users are hidden. Liu et al. [4] clarified the concept of traceability and argued that there were two levels of traceability. The first level was white-box traceability, by which given a well-formed decryption key, one can find the key owner. The second level was black-box traceability, and it means that the system can identify the malicious user who builds the decryption black box even if the decryption key and decryption algorithm are all unknown. The scheme of [3] is actually a white-box-traceable scheme, as well as the schemes of [5,6,7,8,9].
Liu et al. [4] present how a decryption black box (DB) works and categorize a DB into two types: the keylike DB and the policy-specific DB. Both kinds of DB are untraceable in a conventional CP-ABE system. Thus, for financial gain or some other motivation, malicious users may build a DB to make a profit, while there is little risk of getting caught. To deal with this security vulnerability, Liu defines the traceability against a keylike DB in [4] and the traceability against a policy-specific DB in [10]. Liu also proves that an augmented CP-ABE (AugCP-ABE) system with a message-hiding property and an index-hiding property implies the traceability against the DB. So how to design a CP-ABE scheme that has a fully collusion-resistant black-box traceability against both kinds of DB has become an important part of research about CP-ABE.
The black-box traceability (BT) implies the white-box one. To completely solve the privilege-abusing problem, a system must achieve black-box traceability. However, it is much more difficult to construct a black-box-traceable scheme. Thus, it is not until 2013 that Liu et al. [4] proposed the first black-box-traceable CP-ABE scheme. Their scheme was inspired by the approach of Boneh and Waters [11], which was an augmented broadcast encryption (AugBE) scheme that provided traceability in a broadcast encryption system. Similar to [11], they built an augmented CP-ABE to allocate each key with an index in the key generation; then, the indices of the keys could be used to identify users when tracing. The further research of Liu et al. [4,10] pointed out that there could be two types of decryption black boxes: keylike decryption black box (keylike DB) and policy-specific decryption black box (policy-specific DB). A keylike DB , which is associated with an attribute set , is able to decrypt the ciphertext whose access policy can be satisfied by . Meanwhile, a policy-specific DB can only decrypt the ciphertext with a specific access policy . Liu et al. proved that the traceability for a policy-specific DB implied the traceability for a keylike DB. Hence, their research in [10] focused on building CP-ABE schemes that were traceable against a policy-specific DB. In most application scenarios of CP-ABE, traceability for DB is necessary for security. However, the schemes with traceability against DB, including the most recent research [12,13,14,15], utilize a similar approach to AugCP-ABE. In this paper, we present a new kind of DB, the alert decryption black box (ADB), which cannot be tracked by existing tracing algorithms in AugCP-ABE systems. This means the traceability of these CP-ABE schemes is not reliable. Malicious users can build an ADB to provide illegal services, and they are still untraceable.
Currently, in existing black-box-traceable CP-ABE schemes, the tracing approach follows the same principle. Tracing algorithms generate some special ciphertext (referred to as tracing ciphertext) and send it to the DB, then identify the DB’s builder by analyzing the return decryption results from the DB. However, we have to point out that these tracing approaches actually work on the assumption that the DB always performs the decryption honestly and correctly whenever it receives a decryption request. In other words, the tracing schemes assume that the DB will not try to distinguish the tracing ciphertext from the normal ciphertext. The assumption is not that reasonable. And obviously, malicious users will endeavor to construct a DB that can differentiate between the tracing ciphertext and the normal ciphertext and take this advantage to counter the tracing.
Our contribution. (1) We reveal the security vulnerability of black-box-traceable CP-ABE schemes. Using this flaw, malicious users can collaborate to frustrate the tracing of the system, while maintaining their illegal decryption service. (2) To clarify this security problem, we analyze the structural defect of the tracing mechanisms applied to existing black-box-traceable CP-ABE schemes. We show in detail how to construct a concrete ADB that can disable tracing and even frame innocent users. (3) We also present a further discussion on how to improve the tracing algorithm.
2. Background
Before presenting how the tracing algorithm fails in tracing an ADB, we need to review the necessary notions and definitions of the black-box-traceable CP-ABE system. In this section, our discussion is mainly based on the mainstream black-box tracing mechanism that is derived from [4], because most black-box tracing CP-ABE schemes apply a similar method for tracing. Note that the subsequent black-box-traceable schemes such as [10,16,17,18,19] directly leverage the tracing algorithm of [4].
We first give the formal definition of augmented CP-ABE, which is the basis of most tracing mechanisms, then we provide the definition of the keylike decryption black box and the corresponding traceability. Finally, we give the detailed tracing algorithm of [4].
2.1. Augmented CP-ABE
As conventional CP-ABE, an augmented CP-ABE (AugCP-ABE) also includes four algorithms: Setup, KeyGen, Encryption, Decryption. However, AugCP-ABE is different in encryption, because its encryption algorithm takes an extra index , where is the number of system users.
. The algorithm takes as inputs the attribute universe U, security parameter and the number of users , then outputs a master secret key and the public parameter .
. This algorithm takes as inputs the master key , the public parameter and the user’s attribute set S. According to the attribute set S, the algorithm generates a private key assigned with a unique index .
. This algorithm encrypts a message M under an access structure and an index by using the public parameter . Note that the output ciphertext contains the access structure but does not contain the index .
. This algorithm takes as input a ciphertext , a private key and the public parameter . If the attribute set of satisfies the access structure of , it decrypts and outputs a message , or it outputs ⊥.
Correctness. For any message M, attribute , access policy over U, and , suppose , and . Only if S satisfies and does . That means if , even if S satisfies , the decryption results will be incorrect.
Security. The security of an augmented CP-ABE system is defined in the following three security games.
2.2. Traceability
A keylike decryption black ox (keylike DB) built by an adversary is a probabilistic device that inputs a ciphertext and outputs a decryption message M or ⊥. Usually, the adversary describes with a non-negligible probability value and a nonempty attribute set . If the access policy of ciphertext can be satisfied by , can decrypt the ciphertext correctly with a probability of no less than . Thus, if the probability value , the decryption ability of is equal to that of a private key associated with the attribute set . In addition, denotes the index set of the private keys which are used to build the decryption black box .
The definition of the tracing algorithm for a keylike DB is:
. Trace is an oracle algorithm that interacts with a keylike DB . By giving a public parameter , the attribute set and the probability value associated with , it runs in polynomial time in and and outputs an index set , where is the number of system users. identifies the set of malicious users who build . Note that is the security parameter of the CP-ABE scheme and must be polynomially related to .
To produce useful results, the outputs should satisfy . means that innocent users cannot be framed, and the tracing algorithm can identify at least one builder of . indicates that the Trace algorithm will identify at least one critical malicious user whose private key can provide the decryption ability according to .
To illustrate the traceability with a formal definition that implies the notion of full collusion-resistant traceability, Liu [4] provided a tracing game that was defined between a challenger and an adversary . The game was described as follows:
Setup. The challenger runs and sends to .
Key Query. For to q, adaptively makes queries according to the tuple , and the challenger responds with the private key .
Keylike decryption black-box generation. produces a decryption black box associated with a nonempty attribute set and a non-negligible probability value .
Tracing. The challenger runs the algorithm Trace and outputs an index set .
The adversary wins the game if:
- When satisfies the access policy , there is , where the probability is taken over the random choices of message M and the random coins of . It means is a useful keylike decryption black box.
- , or , or .
Definition 1.
A -user black-box-traceable CP-ABE system is traceable if the probability of any polynomial-time adversary to win the game is negligible in λ.
2.3. Tracing Algorithm
Here, we present the classic tracing approach in the work of Liu [4]. Note that the succeeding black-box-traceable schemes usually make use of the same construction or similar ones for tracing.
Suppose that is an augmented CP-ABE, Liu constructed the black-box-traceable CP-ABE system derived from , by defining . For such a CP-ABE system, given a keylike DB associated with a non-negligible probability value and a nonempty attribute set , the tracing algorithm is defined as Trace. To trace , the oracle algorithm Trace works as follows:
- For to , do the following:
- (a)
- The algorithm repeats the following steps times:
- Select a random message M from the message space.
- Let , where is the strictest access policy over .
- Query oracle with input ciphertext and compare the output of with M.
- (b)
- Let be the fraction of times that decrypted the ciphertext correctly.
- The algorithm outputs as the index set of the private decryption key of malicious users, where is the set of all for which .
Note that for an attribute set , the strictest access policy is .
3. How to Frustrate Tracing
Most black-box-traceable schemes such as [10,16,17,18,19] make use of the tracing algorithm Trace, while [20,21,22] employ other approaches for tracing. However, these tracing mechanisms in all existing traceable CP-ABE schemes follow a similar assumption that may be unreasonable.
Here, we first give a high-level analysis of the tracing mechanism in existing black-box-traceable schemes and point out the structural defect in such kinds of tracing schemes. Based on this, for the current traceable systems, we present a general approach on how to construct an untraceable keylike DB, which is referred to as an alert decryption black box (ADB) in our work. Also, we show how an ADB frustrates tracing or even frames innocent users.
3.1. Structural Defect
So far as we know, in any black-box-traceable CP-ABE scheme, the tracing algorithm needs to perform tracing for a DB by interacting with it. The tracing algorithm outputs tracing ciphertexts, which are different from the normal ciphertext, and sends them to the DB. If the DB executes decryption correctly and returns the decryption results, the tracing algorithm can analyze the results by some means and expose the private keys used in the decryption, and then find the builder of the DB. But actually, this tracing approach works on an implicit assumption that the DB must always perform the decryption honestly and correctly; only in this way can the tracing algorithm identify the malicious users who build the DB. However, if a DB can distinguish between the tracing ciphertext and the normal ciphertext, it may deliberately respond to the tracing ciphertext with incorrect decryption results or even some well-designed error message to mislead tracing. And at the same time, it keeps returning correct results for the normal ciphertext. Thus, the DB can offer its “service” as usual while countering tracing. Therefore, the traceability actually depends on whether a DB can or cannot distinguish the tracing ciphertext from the normal ones.
In fact, the decryption results of the tracing ciphertext need to differ from user to user, because if the decryption results of different users are the same, the tracing algorithm will not be able to tell who has performed the decryption. By contrast, for a normal ciphertext, the decryption results that come from the distinct authorized users, whose attributes satisfy the access policy of the ciphertext, should be the same. Since correct decryption for the normal ciphertext must recover the original plaintext, whoever performs the decryption correctly will recover the identical plaintext. We show the two decryption cases in Figure 2.
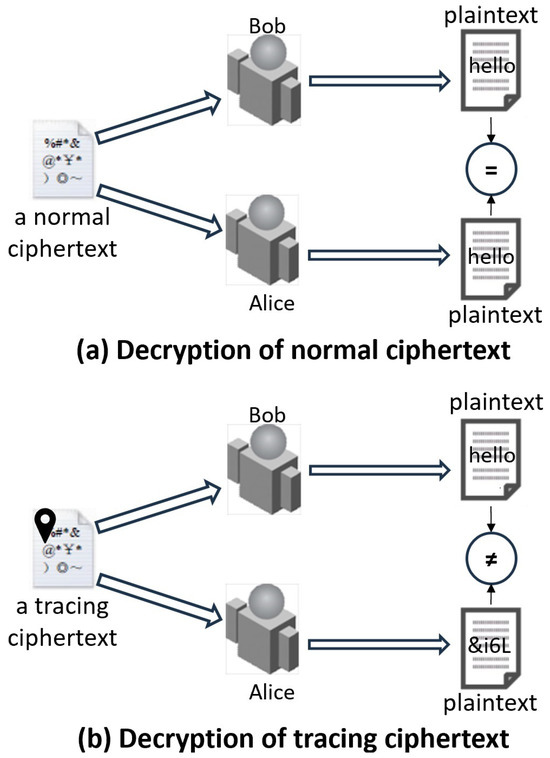
Figure 2.
Decryption situations.
Due to the nature of the tracing mechanism, there must exist some differences between the tracing ciphertext and the normal ciphertext. Malicious users can always use the difference and manage to distinguish the tracing ciphertext from the normal one, so as to counter the tracing operation.
Taking use of this structural defect, malicious users can build a DB that may be untraceable in existing CP-ABE schemes. For example, suppose that a system allocates the private key for attribute set to user A and assigns user B the private key according to attribute set . If , A and B may build a keylike DB denoted by , which is associated with a nonempty set , by generating decryption keys and both according to and embedding the keys in the DB. For each decryption request, will use and to decrypt the ciphertext, respectively. If two decryption results are identical, outputs the results as usual, otherwise, treats the sender of the ciphertext as a tracker. For the following decryption request from the tracker, can take action to counter tracing in a certain strategy, while it keeps a normal response to the normal decryption request. The operation mechanism is described in Figure 3.
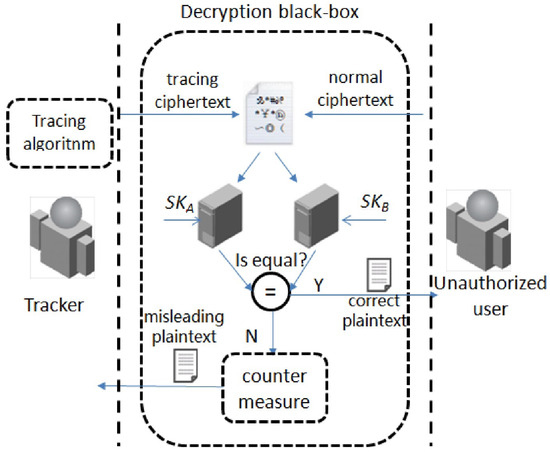
Figure 3.
Operation mechanism of an untraceable decryption black box.
3.2. Construction of Alert Decryption Black Box
In general, two or more private keys can be combined together to build a DB that may be capable of distinguishing between the tracing ciphertext and normal ciphertext, and the DB can perform further operations based on the type of ciphertext. It may intentionally output the incorrect decryption results if necessary or simply stop the service to prevent the snooping from tracing the algorithm. This kind of DB is referred to as an alert decryption black box (ADB) in this paper. To make it clear, we give the concrete construction of an ADB that is a keylike decryption black box and untraceable against the tracing algorithm . In the section, we show how fails for tracing an ADB, while the ADB can keep its illegal decryption service “valid”. Note that such an untraceable ADB can also be built in a similar way in most black-box-traceable CP-ABE schemes.
Different from the DB described in [4], which is a device owned by the buyer, in our context, the DB is considered as a server on the network owned by its builder (a more reasonable assumption for now), and it provides a decryption service for its “subscribers”.
Our fundamental idea is to build the ADB with n decryption keys where . However, to simplify the description, we take an ADB as the example, which is built with two decryption keys and , for and . is described by the attribute set and the probability value , which means provides a similar ability as a decryption key associated with the attribute set . When receives a decryption request and the access structure of cyphertext is satisfied by the attribute set , it will apply the two keys and to decrypt the message, respectively. If the decryption results are distinct, marks the message sender as a tracker. In the following interaction with this tracker, will take action to mislead it and try to frustrate its tracing, meanwhile, serves other normal subscribers as usual. We suppose that only provides service for its valid “subscribers” and will not decrypt the message when the message sender is unknown, because that is not in the interest of the ADB’s builder.
Specifically, for each subscriber (identified with ), defines three parameters , and , and initializes for each new subscriber. When receives a decryption request from any subscriber, it runs the antitracing decryption algorithm to answer it. The antitracing decryption algorithm is defined as: . This algorithm takes as inputs the public parameter , a ciphertext , the secret keys , the attribute set and the subscriber’s ID denoted by . If the attribute set cannot satisfy the access structure of , the algorithm outputs ⊥, or else, it outputs the return message . The algorithm follows the steps:
Now, we show how Algorithm 1 is applied to counter the tracing algorithm. Suppose a tracker, whose subscriber id is , applies the tracing algorithm Trace to trace a DB. Trace generates a tracing ciphertext to test the indices of the keys from 1 to one by one. For an index , Trace performs with to produce the tracing ciphertext and repeats it times in a round. Thus, in the previous rounds of the tests for the indices from 1 to , behaves as a normal DB and returns the correct decryption results, because when the index , the two decryption results are identical. However, in the th round, is marked as a “tracker” since in this round of testing. But keeps returning the correct decryption results until it comes to the ()th round. From this round on, the tracker receives the wrong messages in all following interactions, since the value of exceeds the limits (). The tracing algorithm must observe that ; then, is identified as the index of the private keys that belongs to the users who build . Therefore, the tracker fails to capture the real builder, and remains untraceable.
| Algorithm 1 |
|
To illustrate the mechanism of , consider the following example. Assume the two private keys and are used to build the decryption black box , where and . The attribute set is . Suppose that a system manager runs the tracing algorithm and sends , the tracing ciphertext, which is encrypted under the policy “ AND ”. In the first 9 rounds, decrypts the ciphertext correctly since the decryption results over the two keys and are equal for each ciphertext. After that, finds that the decryption results under the two keys are different (). Thus, marks the system manager as a “tracker” and sets as a random value from the range 10 to 102. Here, we assume that is randomly set to 29. Thus, in the next 20 rounds, counts the decryption requests from this tracker and keeps returning the correct messages produced by the key until it comes to the 30th round. From this round on, returns a random message as the response to the request of the tracker. This causes the index 29 to be identified as the key of the malicious user because . As a result, the tracing algorithm is misled; meanwhile, ’s illegal service is not affected by the antitracing procedure.
Thus, the ADB can be untraceable for the tracker while useful for other subscribers. Similar constructions can be applied to build such kinds of untraceable ADBs in most traceable CP-ABE systems.
3.3. Discussion
If an ADB is built by two keys with indices and , the ADB can be used to frame any user with a key index between and . Suppose that an ADB tries to frame the user who owns a key index , where . It simply sets instead of a random value when it performs step 6 of the algorithm . In the following interaction with the ADB, the tracing algorithm detects that and identifies as the key index of the ADB builder. The failure of Trace can be ascribed to its deterministic testing of key indices, which strictly adheres to a sequential order ranging from 1 to . Thus, the ADB can determine the testing index of the key by counting the tracing cyphertext.
3.3.1. Improvement of Tracing Algorithm
The failure of the tracing algorithm is because it generates and sends the tracing ciphertext in a fixed sequence. Thus, it is easy for an ADB to find out the key index embedded in the tracing ciphertext. Therefore, a simple conclusion is that if a tracing algorithm tests the keys according to a certain fixed mode, the mode needs to be kept secret. Otherwise, an ADB can always use the mode to guess the test key index and take some strategies to mislead the tracing algorithm. To avoid keeping the test mode a secret, it is reasonable that the tracing algorithm tests the key indices in random order. We suggest a new tracing algorithm Trace working as follows:
- Generate a sequence of integers . It is a random permutation of the numbers 1 to , where , and for .
- For to , do the following:
- (a)
- The algorithm repeats the following steps times:
- Select a random message M from the message space.
- Let , where is the strictest access policy over .
- Query oracle with input ciphertext and compare the output of with M.
- (b)
- Let be the fraction of times that decrypted the ciphertext correctly.
- The algorithm outputs as the index set of the private decryption key of malicious users, where is the set of all for which .
Note that to keep the random permutation secure, the first step of Trace must equally likely produce each permutation of the numbers 1 to , and such an algorithm to generate the permutation can be found in [23]. Since the algorithm sends the tracing ciphertext with random key indices, the ADB is not able to determine the key index of the tracing ciphertext, so it fails to frame the particular users.
3.3.2. Analysis of Traceability
In this section, we analyze the probability of identifying the malicious users who build the ADB, if the algorithm is applied to track them. Assuming that malicious users build the ADB with their decryption keys and , for and , and a tracker performs to interact with the ADB. To simplify the problem, we focus on the probability of identifying the key index of . Obviously, can identify index in the following two cases.
- Index is tested before the tracker has been marked, and index is tested when . Therefore, the ADB returns the correct decryption for the testing of index , and the incorrect decryption results for the testing of index . The probability of this case is:
- Index undergoes testing after the tracker has been marked, and this testing occurs when . And index undergoes an evaluation during , leading to a distinct decryption operation for the two indices. The probability of this case is
The total probability of identifying index of the malicious user is
By setting , we demonstrate the probability of identifying index belonging to the malicious user in Figure 4. This probability decreases with an increase in and increases with . For , the probabilities in all three cases are less than 0.008. As a result, if ADB builders select a small value of , the probability of detecting the malicious user is only slightly better than a random guess.
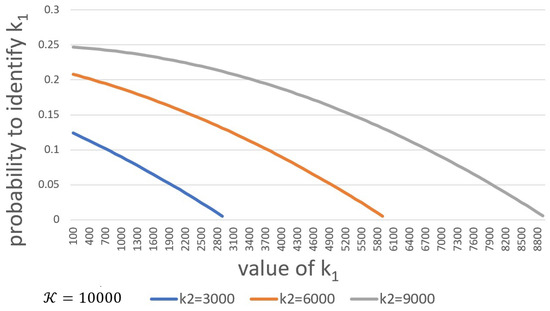
Figure 4.
Probability to identify .
However, an ADB may choose to adopt an alternative strategy whereby it discontinues the decryption service provided to a “subscriber” once it has been flagged as a tracker by . In such cases, the tracker must assume a new subscriber identity to resume service from the ADB. The number of subscriber accounts required by the tracker to accomplish tracing is determined by a specific function, denoted as . In most scenarios, the cost of tracing is prohibitively high, particularly in large-scale systems with a substantial user base. In fact, based on the ability to distinguish the tracing ciphertext from the normal ciphertext, other kinds of complicated DB can also be designed. For example, AI technologies can be applied to design a smart DB, which can even take an adaptive strategy to counter the tracing algorithm.
4. Conclusions
Currently, in black-box-traceable CP-ABE schemes, the DB built by malicious users is assumed to be a device that always performs the decryption honestly and correctly. That is, a DB executes the decryption operation correctly even if it receives a tracing cyphertext. We point out the assumption about the DB is too simple and idealistic. Malicious users who build decryption black boxes must try to get benefits while keeping themselves secure against tracking. The DB they build may choose to output incorrect decryption results to mislead the tracker when it detects tracing cyphertext sent by the tracker. Thus, we analyzed the structural defect of the tracing mechanism in most black-box-traceable systems. It means that the decryption result of the tracing cyphertext varies from user to user, but for a normal cyphertext, different users obtain the same decryption results. Making use of the structural defect, two or more malicious users may collaborate together to build a DB. This kind of DB can distinguish the tracing cyphertext from the normal cyphertext; then, it can take certain strategies to counter tracing. Based on that, we presented an example of an ADB that can mislead the tracing algorithm of AugCP-ABE systems. Similar constructions can also be applied to disable the tracking of most black-box-traceable CP-ABE schemes. Finally, we discussed the improvement of the tracing algorithm and proposed the algorithm. But we proved that the new algorithm could only prevent innocent users from being framed, and it is still difficult to identify the malicious users who build ADBs, which means ADBs are still untraceable for now. To achieve traceability against ADBs, we believe that future research should focus on modifying the tracing mechanism so that a DB cannot distinguish the tracing ciphertext from the normal ciphertext.
Author Contributions
Conceptualization, H.Q.; methodology, H.Q.; software, H.Q. and J.R.; validation, Z.W.; writing—original draft preparation, H.Q.; writing—review and editing, H.Q., Y.H. and J.R.; supervision, Z.W. All authors have read and agreed to the published version of the manuscript.
Funding
The research is funded in part by the National Natural Science Foundation of China, under grant no. 61303191 and no. 61402508. It is also supported by the Research Foundation of the Education Bureau of Hunan Province, China (grant no. 20A112 and no. 22B0735) and the Natural Science Foundation of Hunan Province, China (grant no. 2022JJ30197 and no. 2022JJ50120).
Data Availability Statement
Data is contained within the article.
Acknowledgments
We would like to thank the anonymous reviewers for their insightful suggestions on improving this paper.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| CP-ABE | Ciphertext-policy attribute-based encryption |
| AugCP-ABE | Augmented ciphertext-policy attribute-based encryption |
| CSP | Cloud service provider |
| DB | Decryption device/black box |
| ADB | Alert decryption device/black box |
References
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology—EUROCRYPT 2005; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3494, pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Li, J.; Ren, K.; Kim, K. A2BE: Accountable Attribute-Based Encryption for Abuse Free Access Control. IACR Cryptol. Eprint Arch. 2009, 1–16. [Google Scholar]
- Liu, Z.; Cao, Z.; Wong, D.S. Blackbox traceable CP-ABE: How to catch people leaking their keys by selling decryption devices on eBay. In Proceedings of the ACM Conference on Computer and Communications Security, Berlin, Germany, 4–8 November 2013; pp. 475–486. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Lin, X. TR-MABE: White-box traceable and revocable multi-authority attribute-based encryption and its applications to multi-level privacy-preserving e-healthcare cloud computing systems. In Proceedings of the IEEE INFOCOM, Hong Kong, China, 26 April–1 May 2015; Volume 26, pp. 2398–2406. [Google Scholar] [CrossRef]
- Zhang, K.; Li, H.; Ma, J.; Liu, X. Efficient large-universe multi-authority ciphertext-policy attribute-based encryption with white-box traceability. Sci. China Inf. Sci. 2018, 61, 032102. [Google Scholar] [CrossRef]
- Ning, J.; Dong, X.; Cao, Z.; Wei, L.; Lin, X. White-box traceable ciphertext-policy attribute-based encryption supporting flexible attributes. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1274–1288. [Google Scholar] [CrossRef]
- Ning, J.; Cao, Z.; Dong, X.; Wei, L.; Lin, X. Large universe ciphertext-policy attribute-based encryption with white-box traceability. In Computer Security—ESORICS 2014; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2014; Volume 8713, pp. 55–72. [Google Scholar] [CrossRef]
- Liu, Z.; Cao, Z.; Wong, D.S. White-box traceable ciphertext-policy attribute-based encryption supporting any monotone access structures. IEEE Trans. Inf. Forensics Secur. 2013, 8, 76–88. [Google Scholar] [CrossRef]
- Liu, Z.; Cao, Z.; Wong, D.S. Traceable CP-ABE: How to trace decryption devices found in the wild. IEEE Trans. Inf. Forensics Secur. 2015, 10, 55–68. [Google Scholar] [CrossRef]
- Boneh, D.; Waters, B. A fully collusion resistant broadcast, trace, and revoke system. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 211–220. [Google Scholar] [CrossRef]
- He, X.; Li, L.; Peng, H. An enhanced traceable CP-ABE scheme against various types of privilege leakage in cloud storage. J. Syst. Archit. 2023, 136, 102833. [Google Scholar] [CrossRef]
- Zhenhua, L.; Yingying, D.; Ming, Y.; Baocang, W. Black-Box Accountable Authority CP-ABE Scheme for Cloud-Assisted E-Health System. IEEE Syst. J. 2022, 17, 756–767. [Google Scholar]
- Yuchen, Y.; Qingqing, G.; Cong, Z.; Ning, L.; Changji, W.; Yuning, J. A Revocable Outsourced Data Accessing Control Scheme with Black-Box Traceability. In Information Security Practice and Experience, Proceedings of the ISPEC 2023, Copenhagen, Denmark, 24–25 August 2023; Lecture Notes in Computer Science; Springer: Singapore, 2023; pp. 380–398. [Google Scholar]
- Qianqian, Z.; Gaofei, W.; Hua, M.; Yuqing, Z.; He, W. Black-Box and Public Traceability in Multi-authority Attribute Based Encryption. Chin. J. Electron. 2020, 29, 106–113. [Google Scholar]
- Ning, J.; Cao, Z.; Dong, X.; Gong, J.; Chen, J. Traceable CP-ABE with short ciphertexts: How to catch people selling decryption devices on ebay efficiently. In Computer Security—ESORICS 2016; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2016; Volume 9879, pp. 551–569. [Google Scholar] [CrossRef]
- Liu, Z.; Wong, D.S. Practical attribute-based encryption: Traitor tracing, revocation and large universe. Comput. J. 2016, 59, 983–1004. [Google Scholar] [CrossRef]
- Liu, Z.; Wong, D.S. Traceable CP-ABE on prime order groups: Fully secure and fully collusion-resistant blackbox traceable. In Information and Communications Security—ICICS 2015; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2016; Volume 9543, pp. 109–124. [Google Scholar] [CrossRef]
- Li, X.; Liang, K.; Liu, Z.; Wong, D. Attribute based encryption: Traitor tracing, revocation fully security on prime order groups. In Proceedings of the 7th International Conference on Cloud Computing and Services Science (CLOSER 2017), Porto, Portugal, 24–26 April 2017; pp. 281–292. [Google Scholar]
- Qiao, H.; Ren, J.; Wang, Z.; Ba, H.; Zhou, H. Compulsory traceable ciphertext-policy attribute-based encryption against privilege abuse in fog computing. Future Gener. Comput. Syst. 2018, 88, 107–116. [Google Scholar] [CrossRef]
- Qiao, H.; Ren, J.; Wang, Z.; Ba, H.; Zhou, H.; Hu, Y. Practical, Provably Secure, and Black-Box Traceable CP-ABE for Cryptographic Cloud Storage. Symmetry 2018, 10, 482. [Google Scholar] [CrossRef]
- Wu, S.; Zhang, Y. Secure cloud storage using anonymous and blackbox traceable data access control. Secur. Commun. Netw. 2015, 8, 4308–4318. [Google Scholar] [CrossRef]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 3rd ed.; The MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).