Abstract
Vulnerability refers to the ability of a network to continue functioning when part of the network is either naturally damaged or targeted for attack. In this paper, the rupture degree of graphs is employed to measure the vulnerability of uniform linear hypergraphs. First, we discuss the bounds of the rupture degrees of k-uniform linear hypergraphs. Then, we give a recursive algorithm for computing the rupture degree of k-uniform hypertrees.
1. Introduction
Many complex structures resembling a network in real life are modeled as hypergraphs, which is a generalization of graphs, see [1,2,3].
Symmetry is a significant feature in hypergraph theory, especially in uniform hypergraph theory. Recent research on the open support of hypergraphs [4], the symmetric Lagrangian function of linear three-uniform hypergraphs [5], the embeddability of hypertrees and unicyclic hypergraphs [6], and the Laplacian energy of r-uniform hypergraphs [7] have been extensively studied. These results of hypergraphs are deeply dependent on the symmetric structure.
For a hypergraph , is a set of elements called vertices, and is a set of nonempty subsets of V called edges. A hypergraph with only one vertex is called a trivial hypergraph. If for , then H is called a k-uniform hypergraph. Clearly, ordinary graphs are referred to as two-uniform hypergraphs. A vertex is said to be incident to an edge if . Two vertices are said to be adjacent if they are contained in one edge, and two edges are said to be adjacent if their intersection is not empty. For a vertex , its degree is defined as . An edge is called a pendant edge of a k-uniform hypergraph if contains exactly vertices of degree one. Otherwise, it is called a nonpendant edge. A hypergraph is called a sub-hypergraph of , denoted as , if and . For , we use to denote the hypergraph induced by X, where and . is the hypergraph induced by . For , we use to denote the sub-hypergraph of H which is obtained by deleting all edges in A and keeping vertices. Given a hypergraph H, a walk W in H is a finite alternating sequence of vertices and edges of H such that: for ; for ; and for . If and , then W is called a circuit. A walk of H is called a path if no vertices and edges are repeated. A circuit W is called a cycle if no vertices and edges are repeated except . A hypergraph H is connected if for any pair of vertices , there is a path connecting u and v, otherwise H is disconnected. A component of hypergraph H is a maximal connected sub-hypergraph of H. A subset is called a cut set of H if is disconnected. A hypergraph H is a hypertree if H is connected and acyclic. A k-uniform hypergraph H is call a k-uniform linear hypergraph if every two edges have at most one common vertex in H. Clearly, a k-uniform hypertree is a k-uniform linear hypergraph. Let be an ordinary graph and be an integer. For any edge , by adding new vertices into edge e, we obtain a hypergraph in which each edge possesses k vertices, which is called a k-uniform hypergraph that underlies graph G (k-power of graph G) and denoted by . Clearly, and edge set . Clearly, is a k-uniform linear hypergraph.
In real life, we are becoming more and more dependent on networks, which makes it easy for us to fall into a crisis caused by a vulnerability of the network. For example, assume we have ten electronic components as vertices. If several electronic components work together to form an electronic module, then this electronic module is considered as a hyperedge with these electronic components as vertices. Based on their structural relationships, an integrated module network has been formed. The integrated module network can be seen as a hypergraph with vertex set V and hyperedge set E. Let be a set of electronic components, be a set of electronic modules; see Figure 1. Obviously, if one of electronic components is damaged, the electronic modules which contain would be damaged and thus affect the overall function of the whole integrated module network H. In addition, we also find that if there are different electronic components or different numbers of electronic components damaged, the damage to network H is different. For example, if only one electronic component (vertex) is damaged, it will cause damage to electronic module (hyperedge) , but the other electronic modules remain normal. If electronic component (vertex) is damaged, then electronic modules (hyperedges) and are damaged and electronic modules are normal. In order to make all the electronic modules damaged, it is easiest to understand that all the electronic components are damaged. In fact, for network H, as long as the electronic components , and are damaged, then all the electronic modules are damaged. That is, the whole network H is completely paralyzed in this case. Therefore, how and at which cost can one restructure the network such that it becomes more robust against malicious attacks? For this purpose, many network vulnerability parameters have been proposed and studied, such as toughness [8], integrity [9], tenacity [10,11,12], scattering number [13], rupture degree, etc. These parameters are composed of some or all of the following three quantities: the number of elements that are not functioning, the number of remaining connected subnetworks, and the size of the largest remaining group within which mutual communication can still occur. Indeed, the above quantities play a key role in the robustness of networks. Although a large number of significant research works have been carried out on these parameters, all of them focus on the networks modeled by ordinary graphs, and there is still a gap in the research on the vulnerability of hypernetworks.
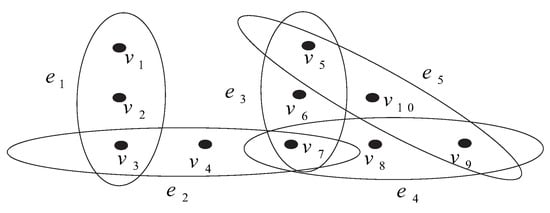
Figure 1.
The integrated module network H.
The concept of the rupture degree of a graph was introduced in [14], which has been well used to measure the vulnerability of networks (see [15,16,17,18,19]). In this paper, we employ this parameter to measure the vulnerability of hypergraph.
Let be a connected hypergraph, the rupture degree of hypergraph H is defined as
where is a cut set of H, and and denote the number of components and the order of the largest component in , respectively. The score of X is defined as . A set is called an r-set of H if .
By the definition of the rupture degree, we focus on a graph G and its four-uniform hypergraph , which is obtained by adding two vertices to each edge of G. A example is shown in Figure 2. Obviously, is an r-set of G, but not an r-set of , which has an r-set that is . This means that it is interesting and meaningful to discuss the vulnerability by determining the rupture degree of a hypergraph.
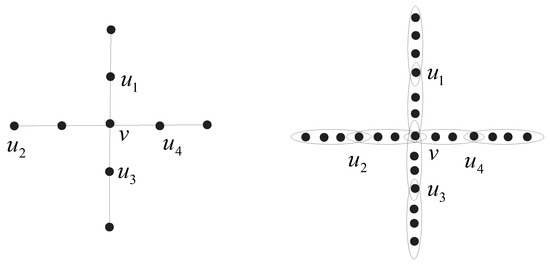
Figure 2.
Graph G and 4-uniform hypergraph that underlies graph G.
In this paper, we first give the bounds of the rupture degree of k-uniform linear hypergraph that underlies graph G in Section 2. In Section 3, we discuss the problem for computing the rupture degree of k-uniform hypertree H. In Section 4, we propose a recursive algorithm for computing the r-set of k-uniform hypertree H.
Throughout this paper, by we denote the largest integer not larger than x and by , the smallest integer not smaller than x. Any undefined terminology and notations can be found in [20,21].
2. The Rupture Degree of k-Uniform Linear Hypergraphs
In this section, we bound the rupture degree of k-uniform linear hypergraph that underlies graph G with n vertices and m edges.
Lemma 1.
Let X be an r-set of k-uniform linear hypergraph that underlies a connected graph G. Then, .
Proof.
Let X be an r-set of , we show that . If not, by the structure of , then . Suppose are components of such that . Now, let and for . Clearly, and . Consider and ; then,
This contradicts the choice of X. Thus, . □
Given a graph , an independent set of G is a subset of vertices which contains no pair of neighbors. The independence number of graph G is the size of the largest independent set in G. A set of vertices is a vertex cover of G if every edge has at least one vertex in S. The vertex cover number of G is the minimum cardinality of a vertex cover set of G, denote by .
Lemma 2.
Let X be an r-set of k-uniform linear hypergraph that underlies connected graph G. Then, .
Proof.
Let X be an r-set of k-uniform linear hypergraph that underlies a connected graph G. By Lemma 1, we obtain . This means X is a vertex cover set of graph G, and thus . Vice versa, if X is a vertex cover set of graph G, then each edge of G has at least one end vertex belonging to X. Thus, . By the definition of , consider . It follows that X is an r-set of . □
By Lemmas 1 and 2, considering , we directly obtain the rupture degree of in terms of the vertex cover number of G.
Theorem 1.
Let be a k-uniform linear hypergraph that underlies connected graph G with n vertices and m edges. Then,
Unfortunately, the problem of computing the minimum vertex cover (MVC) is NPC [22]. In [23,24], the authors gave some exact algorithms for the MVC. However, all of them took an exponential time and so were not suited for practical use in large graphs. Therefore, it is interesting to discuss the bound of the of k-uniform linear hypergraph .
In [25], Harant bounded the independence number of G with n vertices and m edges.
Proposition 1.
Let G be a connected graph on n vertices with m edges [25]. Then,
Combine the famous formula for a connected graph G with order n, we obtain the following corollary.
Corollary 1.
Let G be a connected graph on n vertices with m edges. Then,
By Theorem 1 and Corollary 1, we directly give a bound for the rupture degree of as follows.
Theorem 2.
Let be a k-uniform linear hypergraph that underlies connected graph G with n vertices and m edges. Then,
Remark 1.
The bounds in Theorem 2 are the best possible ones. The upper bound can meet at k-uniform linear hypergraph that underlies star graph . The lower bound can meet at k-uniform linear hypergraph that underlies complete graph .
Clearly, if we let in Theorem 2, then we can obtain the bounds for the rupture degree of k-uniform hypertree .
Corollary 2.
Let be a k-uniform hypertree that underlies a tree T with order n. Then,
Remark 2.
The bounds in Corollary 2 are also best possible. The upper bound can meet at k-uniform linear hypergraph that underlies star graph . The lower bound can meet at k-uniform linear hypergraph that underlies .
Notice that for any connected graph G, we also obtain the following result.
Corollary 3.
Let be a k-uniform linear hypergraph that underlies connected graph G with order n. Then,
3. The Rupture Degree of k-Uniform Hypertrees
In this section, we discuss the rupture degree of k-uniform hypertree H. For k-uniform hypertree H, if X is an r-set of H, then we easily obtain the same result as in Lemma 1.
Lemma 3.
Let be a k-uniform hypertree. If X is an r-set of H, then .
Lemma 4.
Let be a k-uniform hypertree with n vertices and m edges. Then, .
Proof.
We show how to proceed by induction on m. It is clear that the conclusion holds for . Assume the conclusion holds for . Now, we consider the case for ; suppose and are components of . By the induction hypothesis, for every component and , for , , . Thus, we have
The proof is completed. □
Lemma 5.
Let be a hypertree with [26]. Then, H has at least two pendant edges.
Theorem 3.
Let be a k-uniform hypertree and X be the r-set of H. Then, .
Proof.
Suppose X is an r-set of k-uniform hypertree H; by Lemma 3, we have . Denote and ; by the structure properties of a k-uniform hypertree, we have
Thus,
Note that , and we obtain . □
Lemma 6.
Let be a k-uniform hypertree with , and X be the r-set of H. Then,
Proof.
Let X be an r-set of k-uniform hypertree H. It is easy to know that . On the other hand, by Theorem 3, we know that . In order to let the value of be as large as possible, it suffices that the number of components of increases at most when adds one. This means . Consider ; we have
Thus,
Because is a positive integer,
The proof is completed. □
Base on Theorem 3 and Lemma 6, we give the bounds of the rupture degree of k-uniform hypertree H as follows.
Theorem 4.
Let be a k-uniform hypertree with . Then,
Remark 3.
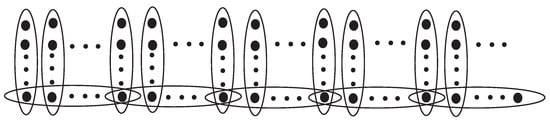
The bounds in Theorem 3 are best possible. The upper bound can meet at k-uniform linear hypertree that underlies star graph . The lower bound can meet at k-uniform linear hypertree H, which is shown in Figure 3.

Figure 3.
A k-uniform hypertree with a minimum rupture degree.
4. A Recursive Algorithm for Computing the r-Set of k-Uniform Hypertrees
Lemma 3 and Theorem 3 show that we can determine the rupture degree of k-uniform hypertree H by finding minimal cut set X to let . Here, we provide a method to obtain such vertex cut set X.
Let H be a k-uniform hypertree and be an arbitrary edge of H. By , we denote the nondecreasing degree sequence of edge e with . For convenience, is often simplified as for .
A contraction of an edge is an operation that identifies that vertices are merged into the vertex and the edges incident to these vertices are transformed into the edges incident to the vertex in H. The resulting graph is denoted as . Clearly, is also a k-uniform hypertree. Similarly, by we denote the graph obtained by contracting edges in H.
Lemma 7.
Let be pendant edges of k-uniform hypertree H such that for . Let e be an edge with such that with . Let be integer number great than 1. If X and are an r-set of k-uniform hypertree H and , respectively, then .
Proof.
Let be an r-set of and . It follows that is an r-set of H. In fact, note that is also a k-uniform hypertree. Thus, by Lemma 1, we know that . It is not difficult to check that is an r-set of H. Thus, we have . □
Lemma 8.
Let be pendant edges of k-uniform hypertree H such that for . Let e be an edge with such that with . Let be an integer number for and at least two of are great than one. If X and are r-sets of k-uniform hypertree H and , respectively, then .
Proof.
Let be an r-set of . Similar to Lemma 7, we know that is an r-set of H. Thus, we have . □
Based on Lemmas 7 and 8, we provide a recursive algorithm for computing the cardinality of an r-set of k-uniform hypertree H. Let be integer numbers for .
Recursive algorithm:
Step 1: Set .
Step 2: If H is a trivial hyperraph, go to step 10. Otherwise, go to step 3.
Step 3: For k-uniform hypertree and set
Step 4: If , then let , go to step 10. Otherwise, go to step 5.
Step 5: If , go to step 6. Otherwise, go to step 8.
Step 6: For each edge , if there exist such that and , go to step 7. Otherwise, go to step 8.
Step 7: Let and set , where denote the edge set of all edges which are incident to vertex in H; go to step 2.
Step 8: If , go to step 9. Otherwise, let , and go to step 10.
Step 9: For each edge , if there exists such that and , then let and , where denote the edge set of all edges which incident to vertex in H; go to step 2.
Step 10: Output the value of .
Example 1.
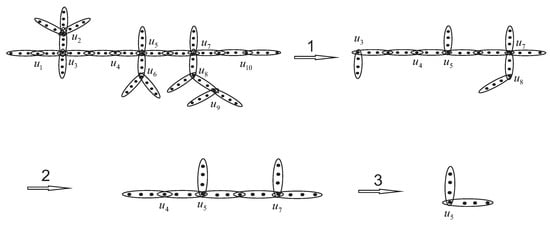
Let be a four-uniform hypertree with that underlies tree T. Using the above algorithm, we get the cardinality of the r-set X of . The details of the algorithm execution are shown in Figure 4.

Figure 4.
Computing the rupture degree of 4-uniform hypertree by our recursive algorithm.
- 1.
- 2.
- 3.
- 4.
Thus, . By Lemma 4 and Theorem 3, we obtain that the rupture degree of four-uniform hypertree is
Example 2.
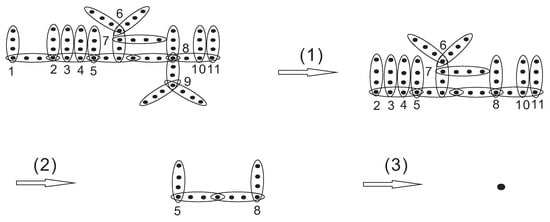
Let H be a four-uniform hypertree with . Using the above algorithm, we obtain that the cardinality of the r-set X of H. The details of the algorithm execution are shown in Figure 5.

Figure 5.
Rupture degree of 4-uniform hypertree H obtained by our recursive algorithm.
- (1)
- (2)
- (3)
Thus, we have . By Lemma 4 and Theorem 3, we obtain that the rupture degree of four-uniform hypertree H is
5. Conclusions
The rupture degree is an important parameter measuring the vulnerability of a network. However, there are few results on the vulnerability of hypernetworks. In this paper, the parameter rupture degree was used to measure the vulnerability of uniform linear hypergraphs. In fact, many parameters of vulnerability remain unexplored for hypergraphs, and they can be explored in nonuniform or nonlinear hypergraphs. Our work may stimulate more research in this field.
Author Contributions
Supervision, H.Z.; visualization, N.Z.; writing—original draft preparation, N.Z., H.Z. and Y.L.; writing—review and editing, N.Z., H.Z. and Y.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Natural Science Foundation of China (grant nos. 12261071, 11661066), by the Natural Science Foundation of Qinghai Province (grant no. 2022-ZJ-924), by the National Key Research and Development Program of China (grant no. 2020YFC1523300).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| MVC | Minimum vertex cover |
| NPC | NP-complete |
References
- Konstantinova, E.V.; Skorobogatov, V.A. Application of hypergraph theory in chemistry. Discret. Math. 2001, 235, 365–383. [Google Scholar] [CrossRef]
- Young, J.G.; Petri, G.; Peixoto, T.P. Hypergraph reconstruction from network data. Commun. Phys. 2021, 4, 135. [Google Scholar] [CrossRef]
- Wang, L.; Egorova, E.K.; Mokryakov, A.V. Development of Hypergraph Theory. J. Comput. Syst. Sci. Int. 2018, 57, 109–114. [Google Scholar] [CrossRef]
- Wu, S.; Wang, M. Open Support of Hypergraphs under Addition. Symmetry 2022, 14, 669. [Google Scholar] [CrossRef]
- Hu, S.; Wu, B. A Note on the Lagrangian of Linear 3-Uniform Hypergraphs. Symmetry 2022, 14, 1402. [Google Scholar] [CrossRef]
- Wang, G.; Chen, L.; Xiong, Z. The l1-Embeddability of Hypertrees and Unicyclic Hypergraphs. Symmetry 2022, 14, 2260. [Google Scholar] [CrossRef]
- Yalcin, N.F. On Laplacian Energy of r-Uniform Hypergraphs. Symmetry 2023, 15, 382. [Google Scholar] [CrossRef]
- Chvátal, V. Tough graphs and Hamiltonian circuits. Discret. Math. 1973, 5, 215–228. [Google Scholar] [CrossRef]
- Barefoot, C.A.; Entringer, R.; Swart, H. Vulnerability in graphs—A comparative survey. J. Comb. Math. Comb. Comput. 1987, 1, 13–21. [Google Scholar]
- Choudum, S.A.; Priya, N. Tenacity of complete graph product and grids. Networks 1999, 34, 192–196. [Google Scholar] [CrossRef]
- Piazza, B.L.; Roberts, F.S.; Stueckle, S.K. Edge tenacious networks. Networks 1995, 25, 7–17. [Google Scholar] [CrossRef]
- Cozzen, M.; Moazzami, D.; Stueckle, S. The tenacity of a graph. In Seventh International Conference on the Theory and Applications of Graphs; Wiley: New York, NY, USA, 1995; pp. 1111–1122. [Google Scholar]
- Zhang, S.G.; Wang, Z.G. Scattering number in graphs. Networks 2001, 37, 102–106. [Google Scholar] [CrossRef]
- Li, Y.K.; Zhang, S.G.; Li, X.L. Rupture degree of graphs. Int. J. Comput. Math. 2005, 82, 793–803. [Google Scholar] [CrossRef]
- Li, F.; Li, X.L. Computing the rupture degrees of graphs. ISPAN 2004, 1, 368–373. [Google Scholar]
- Li, Y.K. The rupture degree of trees. Int. J. Comput. Math. 2008, 85, 1629–1635. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, Z. Relationships between rupture degree and other parameters. Int. J. Comput. Math. 2006, 83, 793–803. [Google Scholar] [CrossRef]
- Kirlangic, A. The rupture degree and gear graphs. Bull. Malays. Math. Sci. Soc. 2009, 7, 73–80. [Google Scholar]
- Li, F.; Ye, Q.; Li, X. Tenacity and rupture degree of permutation graphs of complete bipartite graphs. Bull. Malays. Math. Sci. Soc. 2011, 2, 173–180. [Google Scholar]
- Berge, C. Graphs and Hypergraphs, 2nd ed.; North-Holland: Amsterdam, The Netherlands, 1976; Volume 6. [Google Scholar]
- Bondy, J.A.; Murty, U.S.R. Graph Theory; Springer: New York, NY, USA, 2008. [Google Scholar]
- Cook, S. The P versus NP Problem; Clay Mathematics Institute: Peterborough, NH, USA, 2000. [Google Scholar]
- Akiba, T.; Iwata, Y. Branch-and-reduce exponential/FPT algorithms in practice: A case study of vertex cover. Theor. Comput. Sci. 2016, 609, 211–225. [Google Scholar] [CrossRef]
- Delbot, F.; Laforest, C.; Phan, R. New approximation algorithms for the vertex cover problem. In International Workshop on Combinatorial Algorithms; Springer: Berlin/Heidelberg, Germany, 2013; pp. 438–442. [Google Scholar]
- Harant, J.; Schiermeyer, I. On the independence number of a graph in terms of order and size. Discrete. Math. 2001, 232, 131–138. [Google Scholar] [CrossRef]
- Mao, J.Z. On the Tree of Hypergraph: Hypertree. J. Cent. China Norm. Univ. 1982, 48–52. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).