Abstract
The Advanced Encryption Standard (AES) is widely used in different kinds of security applications. The substitution box (S-box) is the main component of many modern symmetric encryption ciphers that provides confusion between the secret key and ciphertext. The S-box component that is used in AES is fixed. If we construct this component dynamically, the encryption strength of AES would be greater than before. In this manuscript, we used chaotic logistic map, Mobius transformation and symmetric group to construct S-box for AES. The idea behind the proposed work is to make supplementary safe S-box. The presented S-box is analyzed for the following analyses: linear approximation probability (LP), nonlinearity (NL), differential approximation probability (DP), strict avalanche criterion (SAC), and bit independence criterion (BIC). The analyses show that the proposed technique is useful in generating high resistance S-box to known attacks.
1. Introduction
The concept of substitution box (S-box) was first given by Claude Shannon in 1949 [1] after that this component got the attention of many researchers. The S-box has wide usage in secure communication, and it is the core component in popular block ciphers such as data encryption standard (DES), international data encryption algorithm (IDEA) and advanced encryption standard (AES) [2] etc. Most of the time, the strength of any cryptosystem [3,4,5,6,7,8] depends on the resistance of S-boxes against known attacks, which is why, to design a robust cipher, the synthesis of strong S-boxes is required. The strength of S-box [9,10,11,12,13,14] usually depends on some algebraic and statistical criteria, such as linear and differential analyses, strict avalanche criterion (SAC) to measure maximal confusion ability between key and cipher text, bit independence criteria to know the dependency of plaintext, and ciphertext bits. Linear and differential cryptanalysis shows that it is essential to propose dominant ciphers that can resist renown attacks. The AES is largely acknowledged as a valid cryptosystem. One of the vital components of AES is its S-box, which is constructed based on the inversion of elements and an affine transformation. Due to AES popularity in the communication systems, S-box got more attention.
In the past 10 to 15 years, some cryptosystems have been constructed by chaotic maps [15,16,17,18,19,20,21] to provide more secure encryption techniques. The safety of secret data can be achieved using dynamical chaotic systems in chaos-based secure communication [22,23,24,25,26,27,28]. The inclusion of chaotic maps in vulnerable schemes can make them more secure against renowned attacks. The pseudo random number generator for symmetric key encryption ciphers and one-way functions are two basic techniques for the execution of data protection. The ability of dynamical systems to induce nonlinearity can be used to synthesize S-boxes, and the analyses of these kinds of boxes were very good against different types of attacks.
The structure of the article is as follows: Section 2 presents the preliminaries. Section 3 consists of the construction methodology for proposed S-box. In Section 4, we presented the analysis to measure the resistance of the presented box against linear and differential types of attacks. Section 5 is the conclusion.
2. Preliminaries
The proposed work is based on the action of general linear group and chaotic logistic map. There are few works on the general linear group for the construction of S-boxes in the literature. In this section, we briefly present the basics of these two modules to be used later in the section for proposed S-box generation.
2.1. General Linear Group
The group that we will use is the action of projective linear group on Galois field , and construct a nonlinear vector corresponding to a particular type of linear fractional transformation with the condition that .
where
2.2. Logistic Map
The logistic map is a model of population growth given as [29]:
where , . Furthermore, the chaotic range for logistic map lies where . p is a positive constant and is known as biotic potential, which is responsible for the chaotic behavior. While it had proposed by John Von Neumann in 1947, there are two logistic map sequences which we are using in proposed work, with initial parameters as and with and .
Chaos has several benefits when applied in secure communication. It has been shown that chaotic security algorithms have commended many advantages such as high security, speed, reasonable computational overheads, and computational power over the traditional algorithms. One of the most notable features is the sensitivity of the initial conditions. The values of the iterations are very sensitive and change significantly by a tiny change in the initial conditions of either p or y.
Figure 1 illustrates the idea of sensitivity of initial conditions. Figure 1a shows the values of the first 100 iterations against the initial parameters of and . Figure 1b shows the values of the 100 iterations generated after first 300 iterations against the initial parameters of and in red color and the values of the 100 iterations generated after first 300 iterations against the initial parameters of and in blue color. It can be seen that the two graphs are significantly different to each other despite a tiny difference in the initial condition of p. Similarly, Figure 1c shows the values of the 100 iterations generated after first 300 iterations against the initial parameters of and in red color and the values of the 100 iterations generated after first 300 iterations against the initial parameters of and in blue color. It can be seen that the two graphs are significantly different to each other despite a tiny difference in the initial condition of .
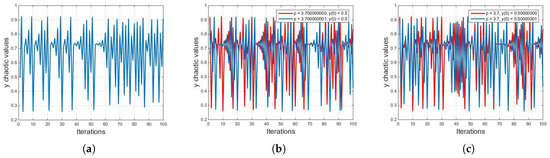
Figure 1.
Illustration of sensitivity to initial conditions of logistic map. (a) values of the first 100 iterations against the initial parameters of and , (b) comparison between the iteration values generated from two slightly different initial conditions of p, (c) comparison between the iteration values generated from two slightly different initial conditions of .
3. Propose S-Box
We have divided the proposed algorithm for the construction of S-box into three steps, we shall construct the initial row vector with the help of linear fractional group technique for the construction of nonlinear vector; this is explained earlier. In step 2, we shall construct the intermediate S-box with the help of initial vector of step 1 and chaotic logistic map of Equation (3). In step 3, we shall take the output of step 2 as a seed and will apply a particular permutation of on it to get S-box with desire properties. The illustration of the proposed generation of S-box and explanation of steps is as follows:
3.1. Step 1: Application of General Linear Group
In first step we are going to apply the action of projective linear group on Galois field as mentioned earlier. The methodology is explained in Table 1 and Galois field element representation corresponding to a particular primitive irreducible polynomial can also be shown. The output of this first step in form of 16 × 16 S-box is shown in Table 2.

Table 1.
Construction of S-box using fractional transformation.

Table 2.
Initial vector corresponding to , , and of Mobius transformation in matrix form.
The purpose of step 1 is to destroy the linear structure of Galois field , because is basically a cyclic group and it is very easy to generate all its elements with the help of root of primitive irreducible polynomial of degree 8. The process of cyclic generation of Galois field elements is a linear operation. We have made this operation nonlinear with the help of linear fractional transformation. A minimum requirement to make a linear operation into nonlinear operation is affine transformation but here we are going beyond this because affine transformation is a particular case of linear fractional transformation.
In Figure 2, we have shown the nonlinearity of the initial vector and compared it with a linear initial vector. It can be seen that red line presents a linear vector from 0 to 255 and green line shows that nonlinear vector of step 1, which we shall use for the construction of S-box. This nonlinearity of the initial vector will play an important role in improving the confusion creating capacity of the proposed S-box.
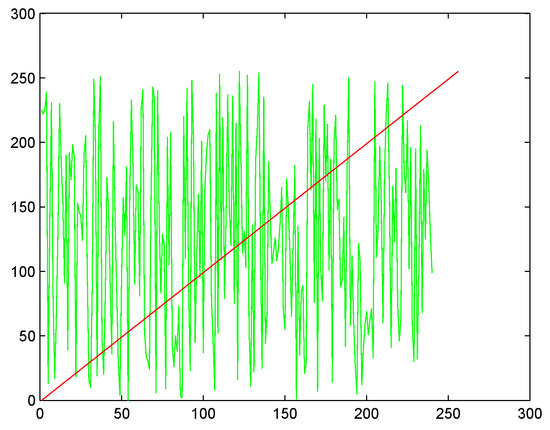
Figure 2.
Uncertainty of the initial vector.
3.2. Step 2: Applying Logistic Chaotic Map
In this step, we need the following stuff:
(a) Initial vector of step 1 as a basic seed, which is shown in Table 2. Let the initial seed be represented as K with size 1 × 256.
(b) Define the two chaotic logistic map sequences as defined in Equation (3) with appropriate initial conditions.
(c) Initial parameters for first logistic map are as follows and . The first logistic map sequence is represented as . The length of this sequence is 256.
(d) Initial parameters for second logistic map are as follows and . The second logistic map sequence is represented as y. The length of this sequence is also 256.
(e) Define , that is has a single value of second chaotic sequence which is placed at 155th position.
(f) Define a function as shown in Algorithm 1. It consists of two steps; in step 1, “ones(1,256)” will give us a row vector with 256 values, all with a value of . In step 2, the position at where the minimum difference lies will be set as an output.
(g) Use the initial seed of S-box generated with the help of general linear group shown in Table 2 and the logistic map, we will get the vector . The whole process of getting the output of this step is depicted in Algorithm 2 and the output of this step is shown in Table 3.
| Algorithm 1 To find the positions at where the minimum difference lies |
| Inputs: Two distinct logistic chaotic map sequences, , y and . Output: Position location, . 1: 2: 3: 4: 5: |
| Algorithm 2 To generate S-box with the input seeds of logistic map and general linear group |
| Inputs: Initial vector K of Table 1 (which is a substitution box), functions for logistic map and . Outputs: Substitution box, . 1: 2: while do 3: 4: 5: for do 6: if then 7: 8: end if 9: end for 10: if then 11: 12: 13: 14: 15: 16: 17: else 18: 19: 20: end if 21: end while |

Table 3.
Output of step 2.
3.3. Step 3: Application of Permutation to Get S-Box
In step 3 we shall choose a particular permutation as shown in Table 4, and then apply it on Table 3 elements as follows;
where . will change the position of elements of Table 3 in the form of proposed S-box, which is given in Table 5.

Table 4.
Particular permutation of symmetric group of permutation .

Table 5.
The proposed S-box.
4. Analyses for Evaluating the Strength of S-Box
In the analyses section we shall determine the cryptographic strength of the propose S-box with some suitable measures. To find the S-box with fitting confusion creating strength many standard evaluating analyses are presented in literature such as DP, SAC, BIC, Nonlinearity, and LP. We shall also use these criteria to test the security of proposed S-box.
4.1. Nonlinearity
Definition 1.
Letbe an n Boolean function, the nonlinearity ofcan take the form,
where,is a set of the whole linear and affine functions,denotes the Hamming distance between f and l.
The nonlinearity denoted by the Walsh spectrum can take the form,
The cyclic spectrum of the function is,
where, , and denotes the dot product of x and w. The larger the nonlinearity of the function f, the stronger the ability of its resistance to the linear attacks, and vice versa.
The results of nonlinearity of proposed algorithm are shown in Table 6, with the help of these results we can say that the nonlinearity of the nonlinear values of the substitution box created by the chaos-based scheme shaped in the reading are 112, 112, 112, 112, 112, 112, 112, 112. Nonlinearity average value, minimum value and maximum value are 112, 112, and 112, respectively.

Table 6.
Nonlinearity of proposed S-box.
4.2. Strict Avalanche Criterion
SAC describes a fact that when one bit in the input of Boolean function changes, the changing probability of every bit in its output is . In practical application, a correlation matrix, the construction method is always constructed to test the SAC property of the Boolean function. The results of SAC are shown in Table 7. In Table 7, we have shown the eight different Boolean functions corresponding to S-box. It can be observed that the values are approximately equal to 0.5, which is very good for cryptographic uncertainty. Therefore, the proposed nonlinear component satisfies this criterion with approximately optimal values.

Table 7.
SAC of proposed S-box.
4.3. Bit Independent Criterion
Given a Boolean function , is a two bits output of an S-box, if is highly nonlinear and meets the SAC, the correlation coefficient of each output bit pair may be close to 0 when one input bit is inversed. Thus, we can check the BIC of the S-box by verifying whether of any two output bits of the S-box meets the nonlinearity and SAC. According to the description of BIC, an S-box produced by our procedure is checked. The results show the exclusive-or sum of all pairs of output bits of this S-box is highly nonlinear and approximately fulfill SAC.
In Table 8, we have shown the results of bit independence criterion (BIC) for SAC. This analysis is very important to know the confusion strength of any nonlinear algorithm. The requirement of this analysis is that all values should be approximately equal to 0.5, and it can be observed that the whole table is between 0.490234 and 0.525391. It means our S-box fulfills this criterion with very close readings.

Table 8.
Bit independence criterion for SAC.
In Table 9, we presented the BIC for nonlinearity for proposed box. It can be observed that all the values are 112 which is maximum possible nonlinearity for a secure S-box.

Table 9.
Bit independence criterion for nonlinearity.
4.4. Differential Approximation Probability
The Differential approximation probability can reflect the distribution of the input and output of the Boolean function, i.e., the maximum likelihood of outputting , when the input is ,
where, X denotes a set of all possible inputs, is the number of elements in the set.
The smaller the , the stronger the ability of the S-box for fighting against differential cryptanalysis attacks, and vice versa. In Table 10, the results of differential approximation probabilities are presented. It can be observed that all the values are 0.015625 and same which is equal to AES S-box strength, this shows that our S-box is good against the differential type of attacks.

Table 10.
Differential approximation probability of proposed S-box.
4.5. Linear Approximation Probability
Given two randomly selected masks and , we used to calculate the mask of all possible values of an input x, and use to calculate the mask of the output values of the corresponding S-box. After masking the input and the output values, and the maximum number of the same results is called the maximum linear approximation that can be computed by the following equation:
where, and are the mask values of the input and output, respectively, X is a set of all possible input values of x, the elements of which is .
The smaller the LP, the stronger the ability of the S-box for fighting against linear cryptanalysis attacks, vise-versa.
5. Conclusions
In this manuscript, we have shown the usage of logistic chaotic map, symmetric group of permutation and projective general linear group action to get high-quality S-box for encryption algorithms. The method presented assurances the success of the SAC, nonlinearity, BIC with an optimal reading and at the same time guarantying an extremely good differential and linear probability. In Table 11, it can be seen that strength of proposed S-box is comparable with well-known prevailing S-boxes. So, one can use the proposed S-box for secure communication in any block cipher encryption algorithm. Moreover, the proposed method can construct 256! S-boxes based on the permutation of . The S-box which we have constructed in this paper is an example and a member of combination of eight output bits of AES S-box.

Table 11.
Comparison of the chaotic and non-chaotic S-boxes with proposed S-box.
Author Contributions
The design problem and proposed methodology were result of the contributions of all the authors. The initial draft of the manuscript was prepared by I.H. The conceptualization of the work was done by T.A.A.-M. The final draft was done by A.A and the simulations were done by M.T.M.
Funding
The publication of this article was funded by the Qatar National Library.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. The Design of RijndaeL: AES-The Advanced Encryption Standard; Springer: Berlin, Germany, 2002. [Google Scholar]
- Shukla, P.K.; Khare, A.; Rizvi, M.A.; Stalin, S.; Kumar, S. Applied Cryptography Using Chaos Function for Fast Digital Logic-Based Systems in Ubiquitous Computing. Entropy 2015, 17, 1387–1410. [Google Scholar] [CrossRef]
- T-Herrera, E.J.; Karp, J.; Távora, M.; Santos, L.F. Realistic Many-Body Quantum Systems vs. Full Random Matrices: Static and Dynamical Properties. Entropy 2016, 18, 359. [Google Scholar] [CrossRef]
- Boeing, G. Visual Analysis of Nonlinear Dynamical Systems: Chaos, Fractals, Self-Similarity and the Limits of Prediction. Systems 2016, 4, 37. [Google Scholar] [CrossRef]
- Ahmed, F.; Anees, A.; Abbas, V.U.; Siyal, M.Y. A Noisy Channel Tolerant Image Encryption Scheme. Wirel. Person. Commun. 2014, 77, 2771–2791. [Google Scholar] [CrossRef]
- Ahmed, F.; Anees, A. Hash-Based Authentication of Digital Images in Noisy Channels. In Robust Image Authentication in the Presence of Noise; Springer: Berlin, Germany, 2015; pp. 1–42. [Google Scholar] [CrossRef]
- Behnia, S.; Akhshani, A.; Mahmodi, H.; Akhavan, A. A novel algorithm for image encryption based on mixture of chaotic maps. Chaos Solitons Fractals 2015, 35, 408–419. [Google Scholar] [CrossRef]
- Anees, A.; Siddiqui, A.M.; Ahmed, F. Chaotic substitution for highly autocorrelated data in encryption algorithm. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 3106–3118. [Google Scholar] [CrossRef]
- Anees, A.; Siddiqui, A.M.; Ahmed, J.; Hussain, I. A technique for digital steganography using chaotic maps. Nonlinear Dyn. 2014, 75, 807–816. [Google Scholar] [CrossRef]
- Gondal, M.A.; Anees, A. Analysis of optimized signal processing algorithms for smart antenna system. Neural Comput. Appl. 2013, 23, 1083–1087. [Google Scholar] [CrossRef]
- Anees, A.; Khan, W.A.; Gondal, M.A.; Hussain, I. Application of Mean of Absolute Deviation Method for the Selection of Best Nonlinear Component Based on Video Encryption. Z. für Naturforsch. A 2013, 68, 479–482. [Google Scholar] [CrossRef]
- Anees, A.; Ahmed, Z. A Technique for Designing Substitution Box Based on Van der Pol Oscillator. Wirel. Person. Commun. 2015, 82, 1497–1503. [Google Scholar] [CrossRef]
- Anees, A.; Gondal, M.A. Construction of Nonlinear Component for Block Cipher Based on One-Dimensional Chaotic Map. 3D Res. 2015, 6. [Google Scholar] [CrossRef]
- Anees, A.; Siddiqui, A.M. A technique for digital watermarking in combined spatial and transform domains using chaotic maps. In Proceedings of the IEEE 2nd National Conference on Information Assurance (NCIA), Rawalpindi, Pakistan, 11–12 December 2013; pp. 119–124. [Google Scholar] [CrossRef]
- Ansari, K.J.; Ahmad, I.; Mursaleen, M.; Hussain, I. On Some Statistical Approximation by (p,q)-Bleimann, Butzer and Hahn Operators. Symmetry 2018, 10, 731. [Google Scholar] [CrossRef]
- Guzzo, M.; Lega, E. Geometric chaos indicators and computations of the spherical hypertube manifolds of the spatial circular restricted three-body problem. Phys. D 2018, 373, 38–58. [Google Scholar] [CrossRef]
- Alves, P.R.L.; Duarte, L.G.S.; da Mota, L.A.C.P. Detecting chaos and predicting in Dow Jones Index. Chaos Solitons Fractals 2018, 110, 232–238. [Google Scholar] [CrossRef]
- Cairone, F.; Anandan, P.; Bucolo, M. Nonlinear systems synchronization for modeling two-phase microfluidics flows. Nonlinear Dyn. 2018, 92, 75–84. [Google Scholar] [CrossRef]
- Lorenz, E.N. Deterministic Nonperiodic Flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef]
- Akhmet, M.U.; Fen, M.O. Entrainment by Chaos. J. Nonlinear Sci. 2014, 24, 411–439. [Google Scholar] [CrossRef]
- Kaslik, E.; Balint, Ş. Chaotic Dynamics of a Delayed Discrete Time Hopfield Network of Two Nonidentical Neurons with no Self-Connections. J. Nonlinear Sci. 2008, 18, 415–432. [Google Scholar] [CrossRef]
- Buscarino, A.; Fortuna, L.; Frasca, M. Experimental robust synchronization of hyperchaotic circuits. Phys. D 2009, 238, 1917–1922. [Google Scholar] [CrossRef]
- Hussain, I.; Anees, A.; Aslam, M.; Ahmed, R.; Siddiqui, N. A noise resistant symmetric key cryptosystem based on S8 S-boxes and chaotic maps. Eur. Phys. J. Plus 2018, 133, 1–23. [Google Scholar] [CrossRef]
- Hussain, I.; Anees, A.; AlKhaldi, A.H.; Algarni, A.; Aslamd, M. Construction of chaotic quantum magnets and matrix Lorenz systems S-boxes and their applications. Chin. J. Phys. 2018, 56, 1609–1621. [Google Scholar] [CrossRef]
- Hussain, I.; Anees, A.; Algarni, A. A novel algorithm for thermal image encryption. J. Integr. Neurosci. 2018, 17, 447–461. [Google Scholar] [CrossRef] [PubMed]
- Anees, A. An Image Encryption Scheme Based on Lorenz System for Low Profile Applications. 3D Res. 2015, 6, 1–10. [Google Scholar] [CrossRef]
- Kocarev, L. Chaos-based cryptography: A brief overview. IEEE Circuits Syst. Mag. 2001, 1, 6–21. [Google Scholar] [CrossRef]
- May, R.M. Biological populations with non overlapping generations, stable points, stable cycles, and chaos. Science 1974, 186, 645–647. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).