Cross-Network Information Dissemination in Vehicular Ad hoc Networks (VANETs): Experimental Results from a Smartphone-Based Testbed
Abstract
:1. Introduction
- to provide an in-deep description of the X-NETAD architecture and its implementation on a VANET formed by an Android smartphone;
- to present the experimental results, obtained by implementing X-NETAD on a testbed of commercial off-the-shelf (COTS) Android smartphones, with no high-end requirements, shedding light on the strengths and weaknesses of the proposed architecture.
2. Related Works
3. X-NETAD: The Idea
3.1. The Big Picture
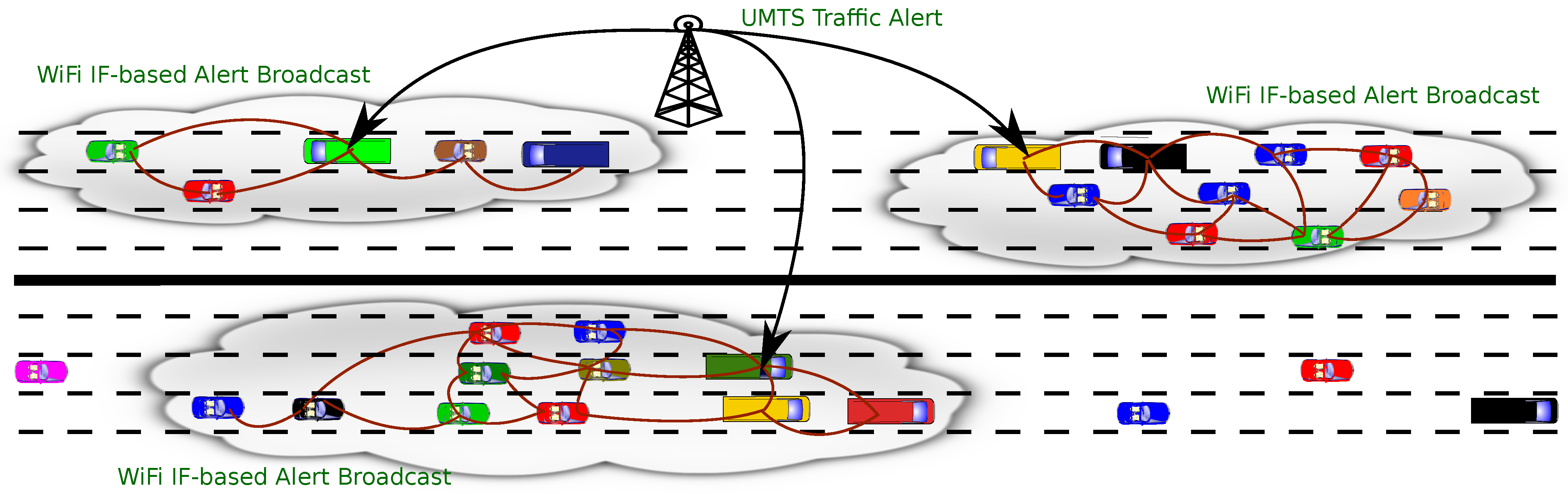
- to provide suitable access interfaces on the Internet;
- to provide a secure communication channel with the PUs;
- to possess authentication, authorization and accounting capabilities;
- to support a basic set of operations to allow the PUs to register to the service and to obtain localized traffic information (of a given geographical area or route) according to a pull-based distribution model.
3.2. A Push/Pull Dissemination Approach
- The communications between AS and PUs are unicast, since (i) 3G networks do not allow broadcast communications and (ii) each PU should receive different information according to its position.
- The information distributed in X-NETAD are not time-critical, and thus, there is no need to use a push-based approach in order to minimize the delay.
- The energy consumption is one of the main concerns with mobile applications, and it is well known that a 3G connection has a high energy consumption. By adopting a pull-based approach, the mobile application can schedule the request for traffic updates without the need of keeping a 3G connection active all the time. Moreover, the application can adapt the intervals between consecutive queries according to the behavior of the vehicles. For example, if the vehicle is not moving, there is no need to look for traffic updates. Similarly, if the battery of the smartphone is depleting, the application can decide to reduce the update frequency.
- A pull-based approach significantly increases the complexity of the server, since it has to cope with a potentially large number of concurrent requests—current techniques, however, should not make this aspect a limitation.
3.3. The Irresponsible Forwarding (IF) Protocol
3.3.1. Reference Scenario
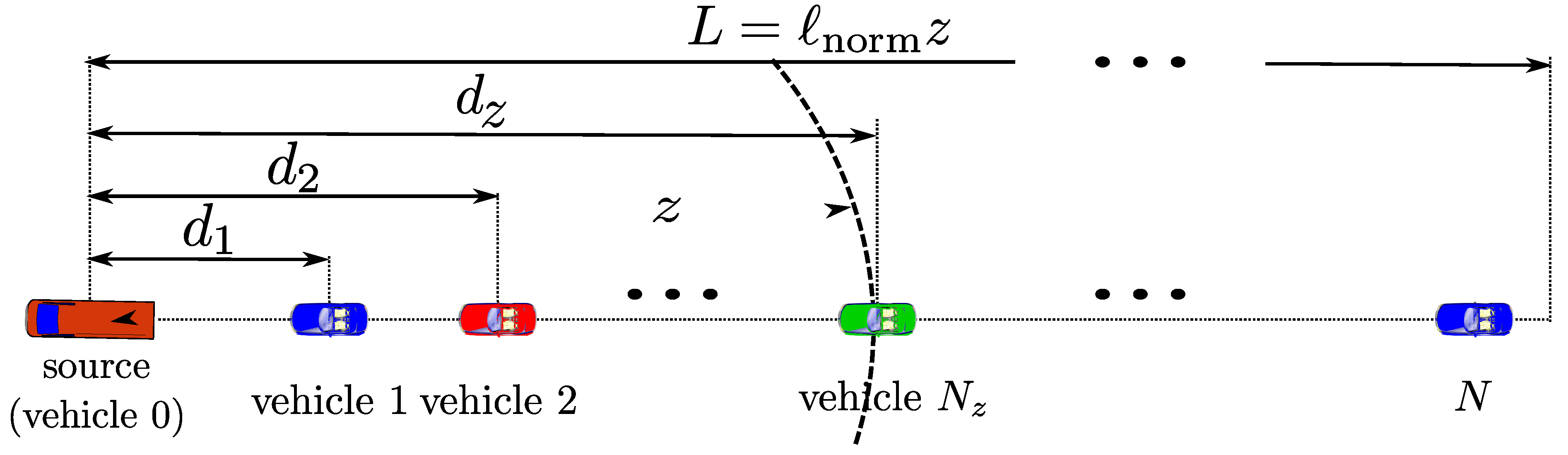
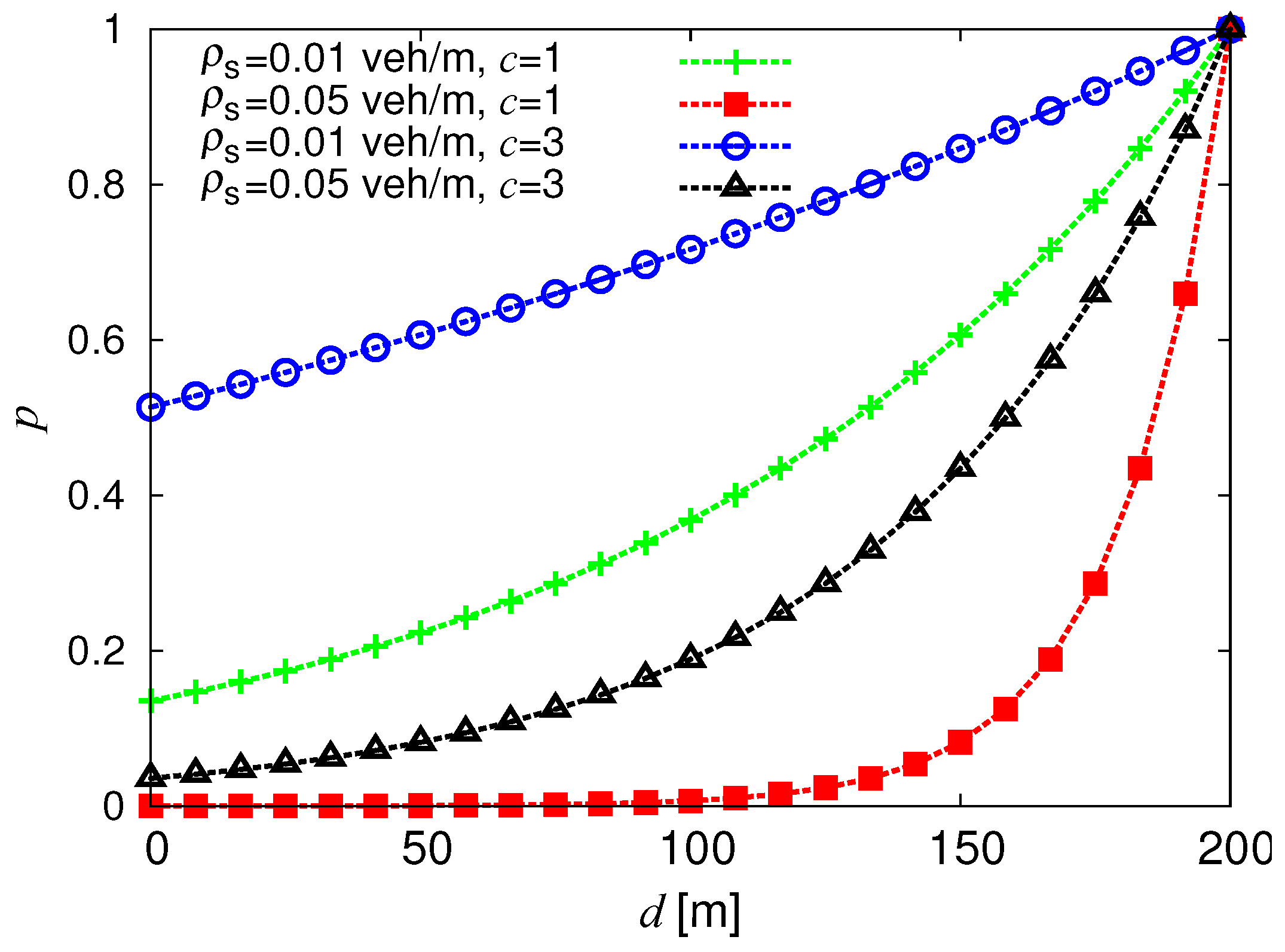
3.3.2. Probability Assignment Function
3.3.3. IF in IEEE 802.11 Networks
4. Application Design and Implementation
4.1. System Overview and Challenges
4.2. Message Structure and Dissemination Protocol
4.2.1. Cellular Domain
4.2.2. Ad Hoc Domain
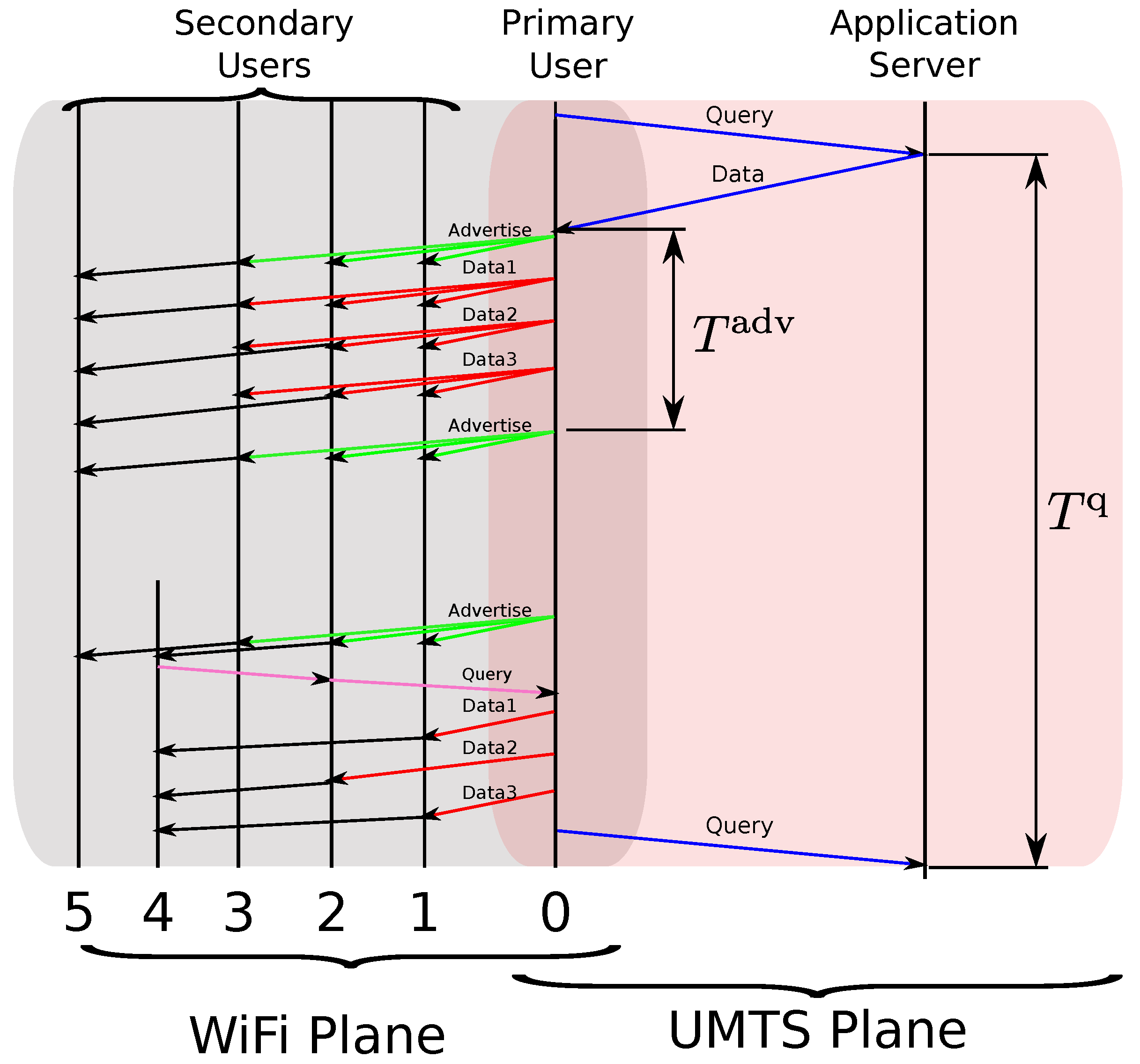
4.3. System Architecture
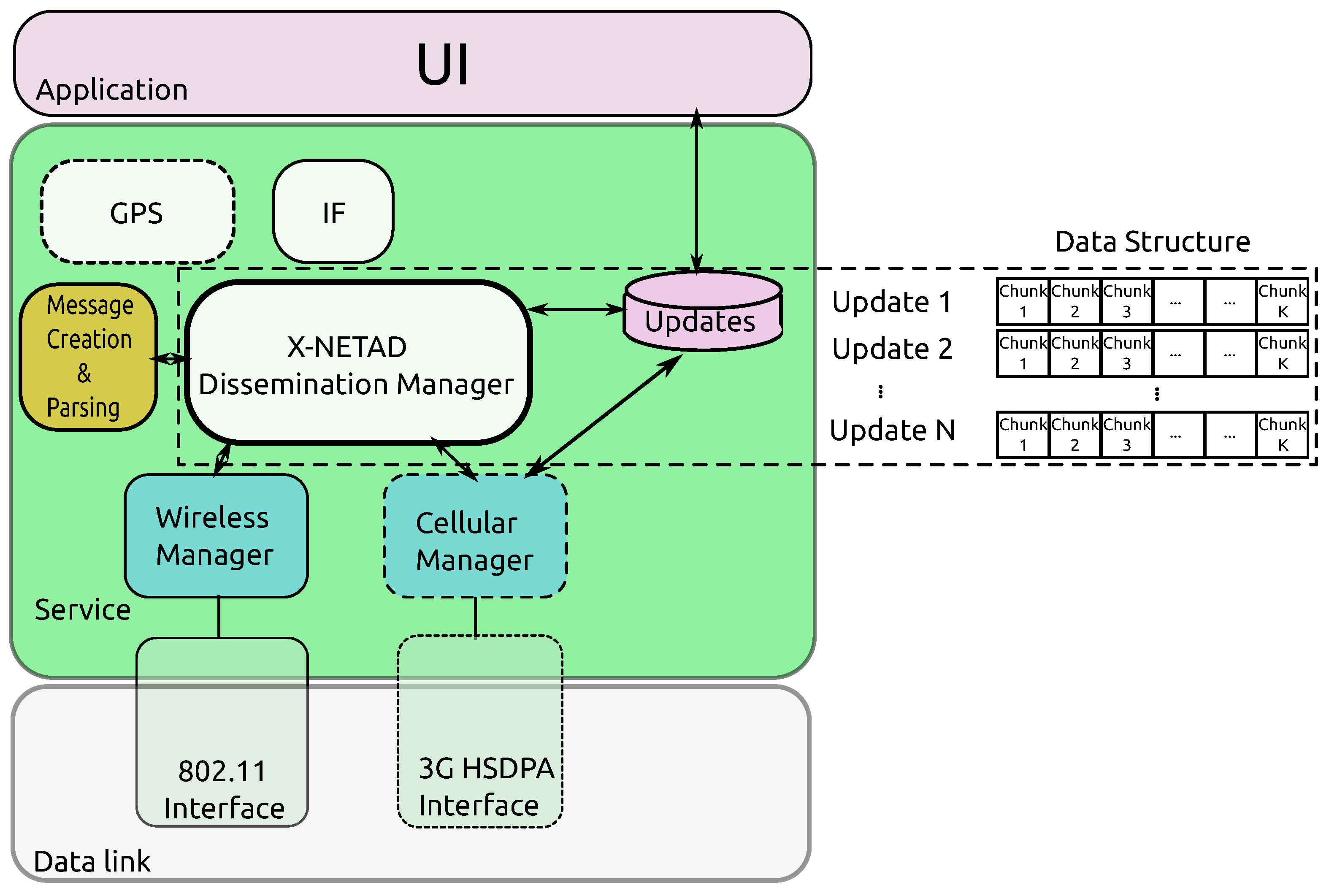
5. Experimental Results
5.1. Metrics of Interest
- The number of DATA messages retransmitted at each SU—the ratio between this quantity and the total number of transmitted packets is correlated to the Probability Assignment Function (PAF) of the IF protocol defined in Equation (1).
- The PMF of the hop index at which the DATA messages are received. This indicator is strictly related to the distance between a PU and an SU.
- The number of missing DATA messages, before the first REQUEST message. This metric is a coarse indicator of the wireless channel quality. In ideal conditions, the PMF should concentrate only at zero. However, in realistic conditions, this statement is not valid, due to radio channel interference and fading.
- The number of DATA messages requested when receiving a REQUEST message. This metric is representative of the “attitude” of a node to receive requests for missing chunks from surrounding nodes.
- The PMF of the archive reception time. This metric indicates the amount of time it takes to a node to receive all the chunks of the archive sent by the PU.
- The CDF of the number of DATA messages received before each REQUEST message. This metric is an indicator of the reception status of the traffic update before each round of REQUEST messages.
5.2. Preliminary Results
5.2.1. PER as a Function of the Data Rate
| Data rate (Mb/s) | Scheme | Modulation | RX Sensitivity (dBm) |
|---|---|---|---|
| 1 | DSSS | BPSK | |
| 6 | OFDM | BPSK | |
| 9 | OFDM | BPSK | |
| 12 | OFDM | QPSK | |
| 18 | OFDM | QPSK | |
| 24 | OFDM | 16-QAM | |
| 36 | OFDM | 16-QAM | |
| 48 | OFDM | 64-QAM | |
| 54 | OFDM | 64-QAM |
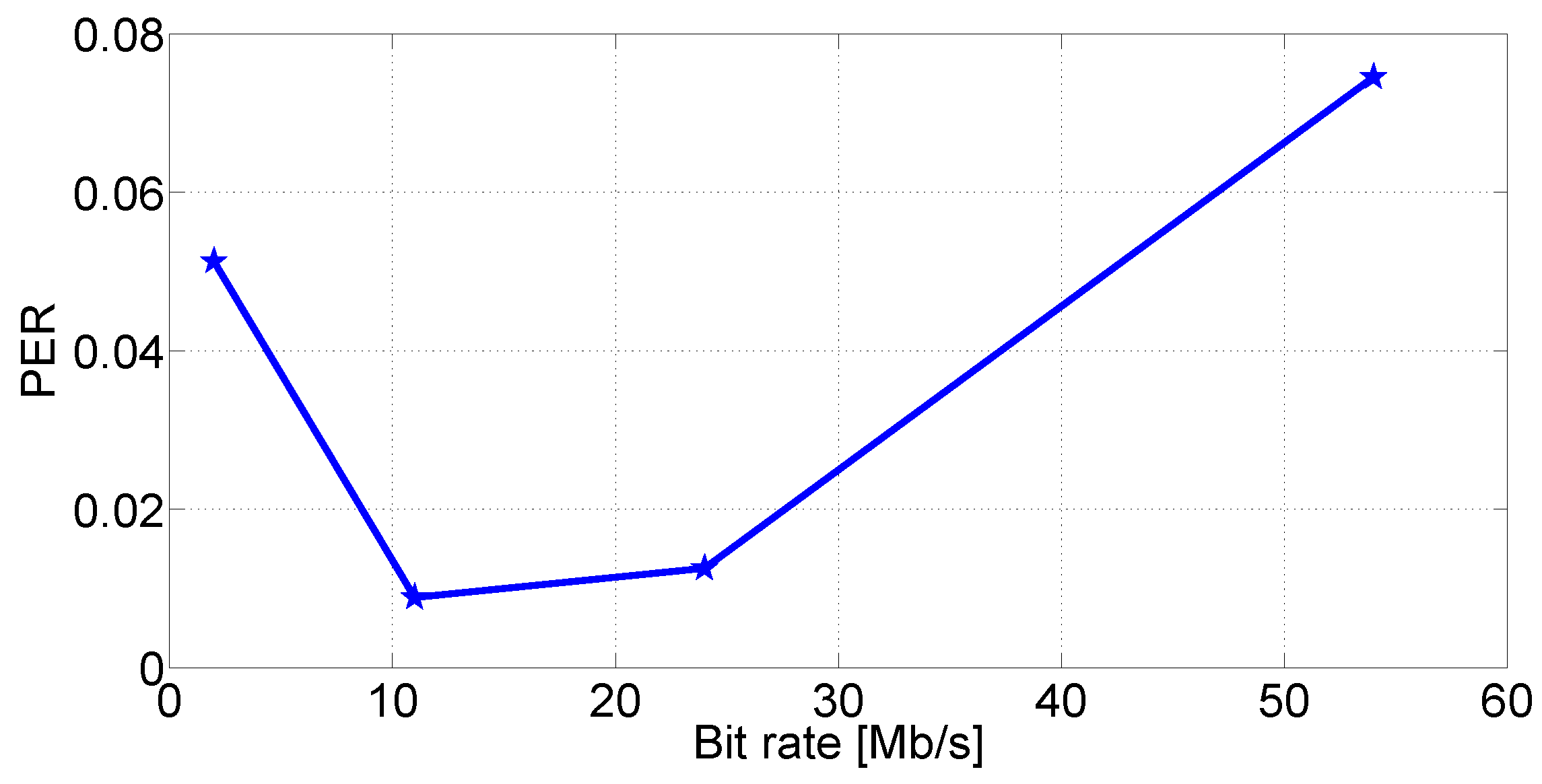
5.2.2. PER as a Function of the Distance
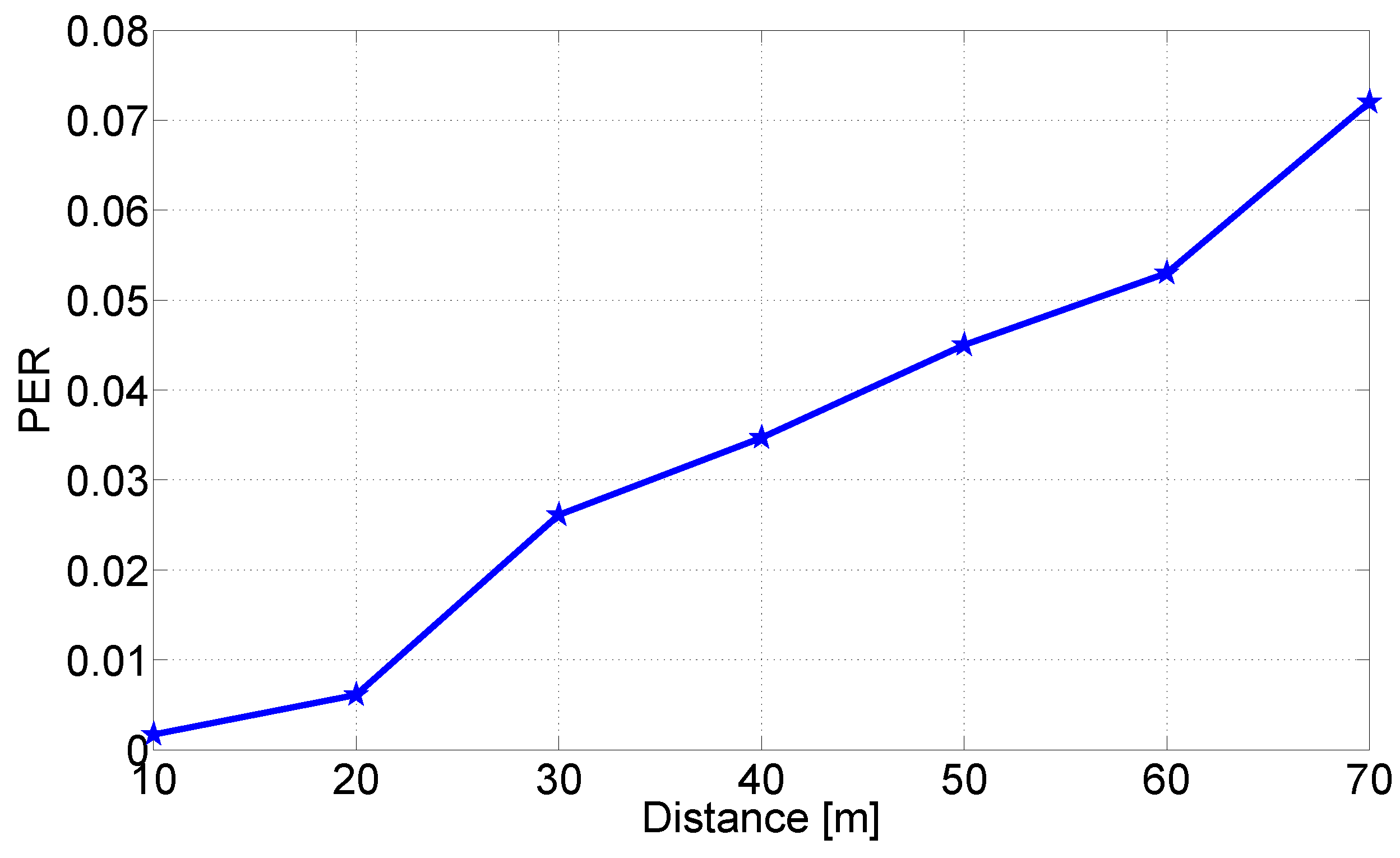
5.3. Tests in Ideal Static Scenarios
5.3.1. Experimental Setup and Results
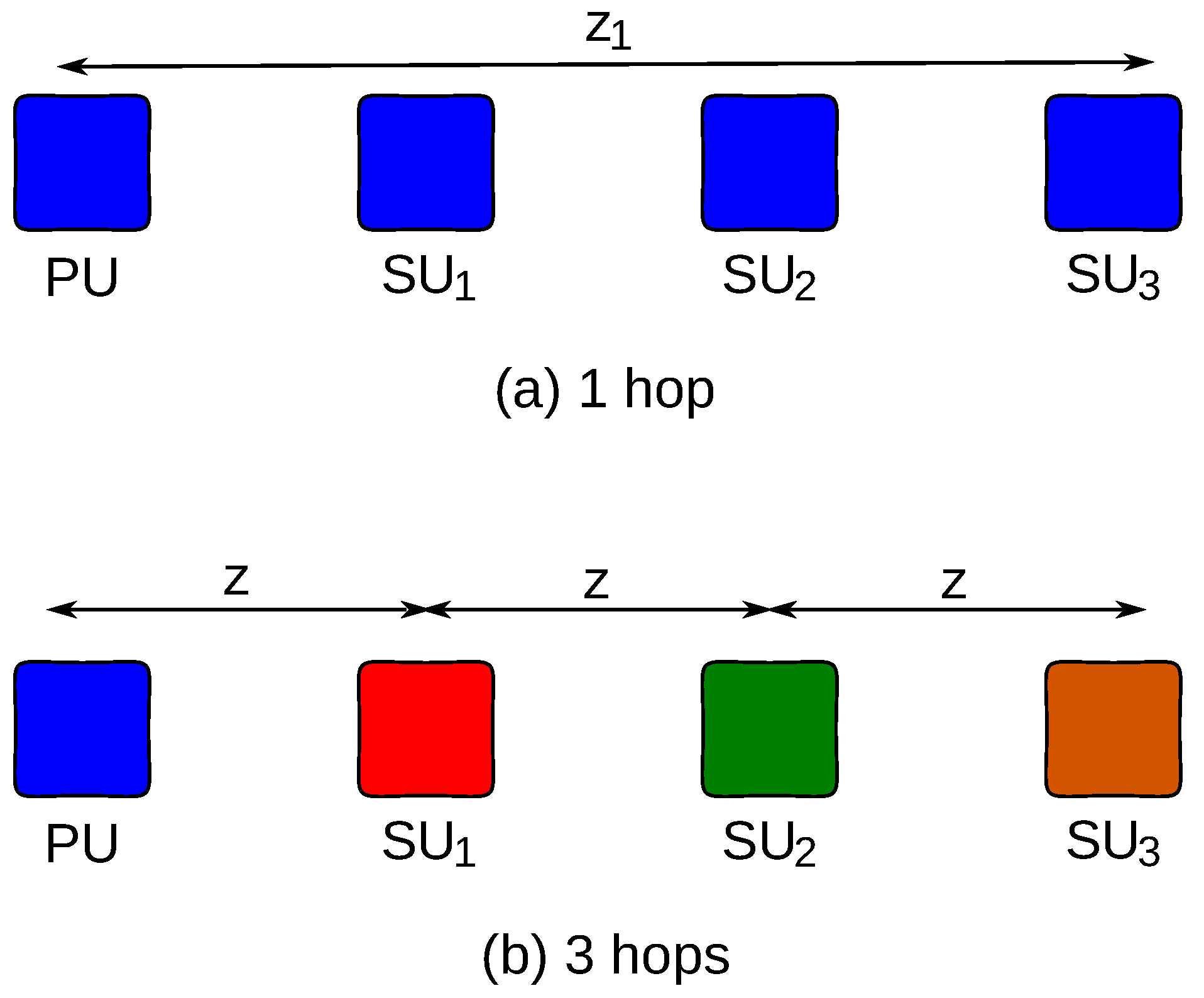
5.3.2. Scenario 1
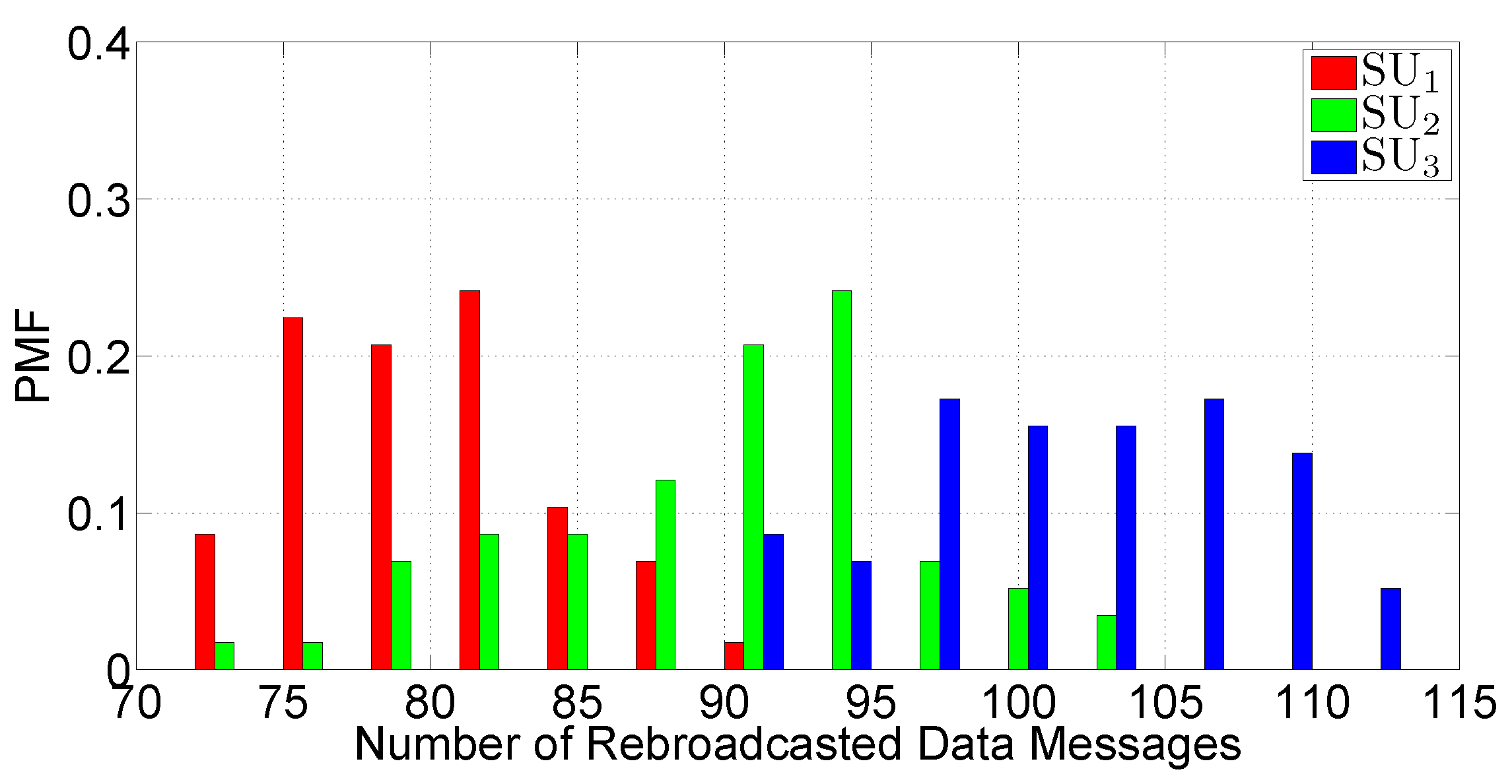
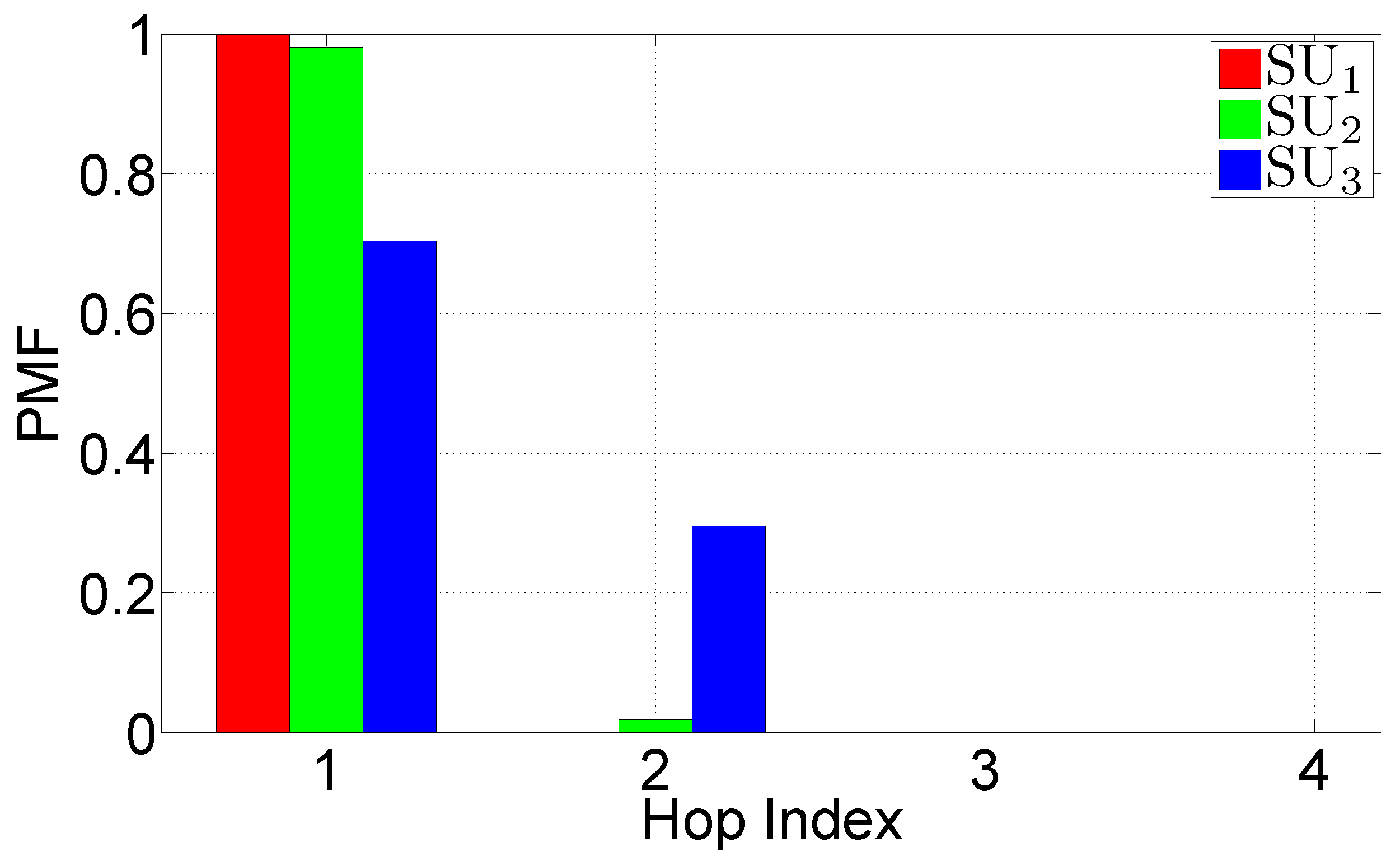
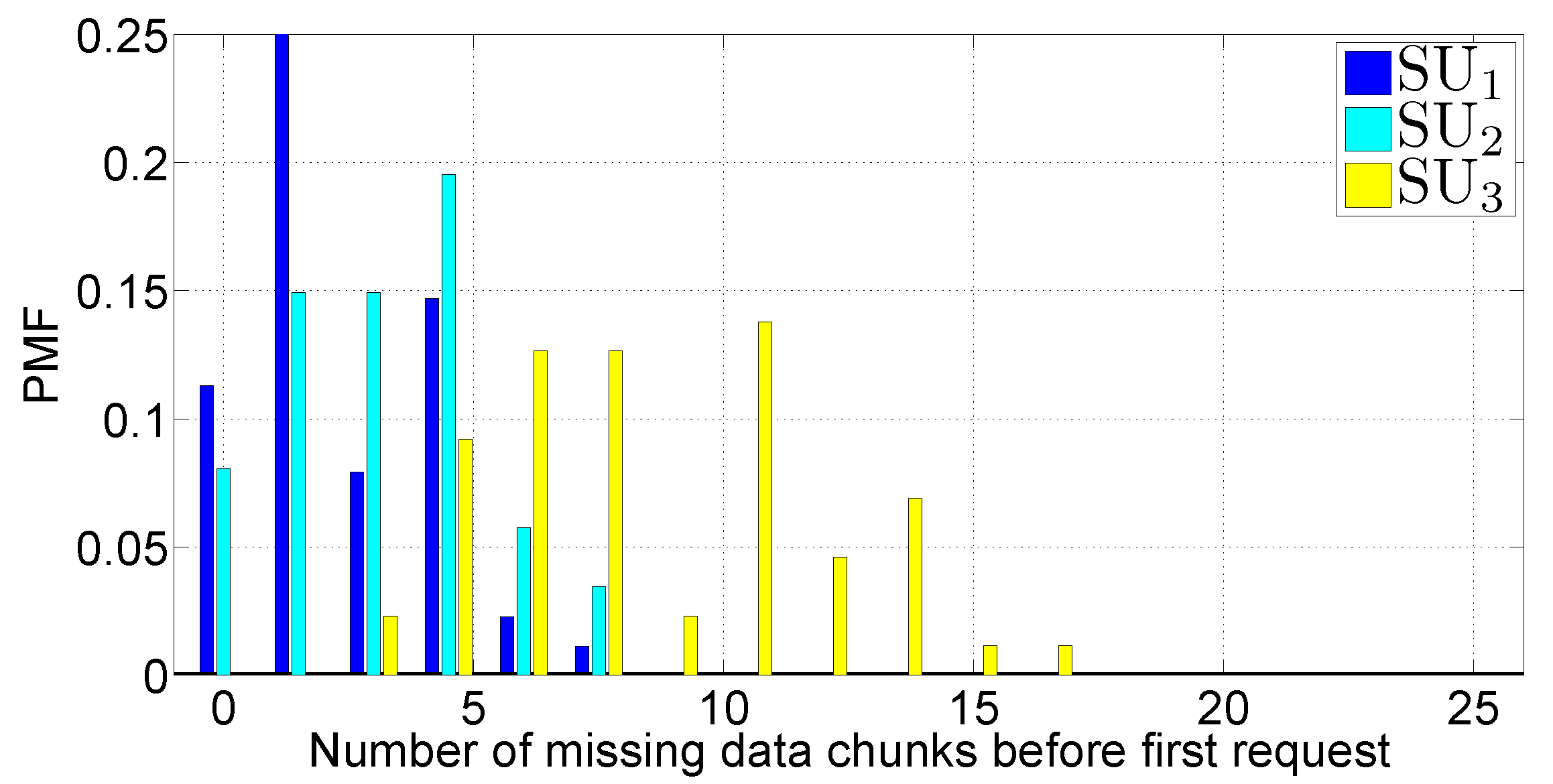
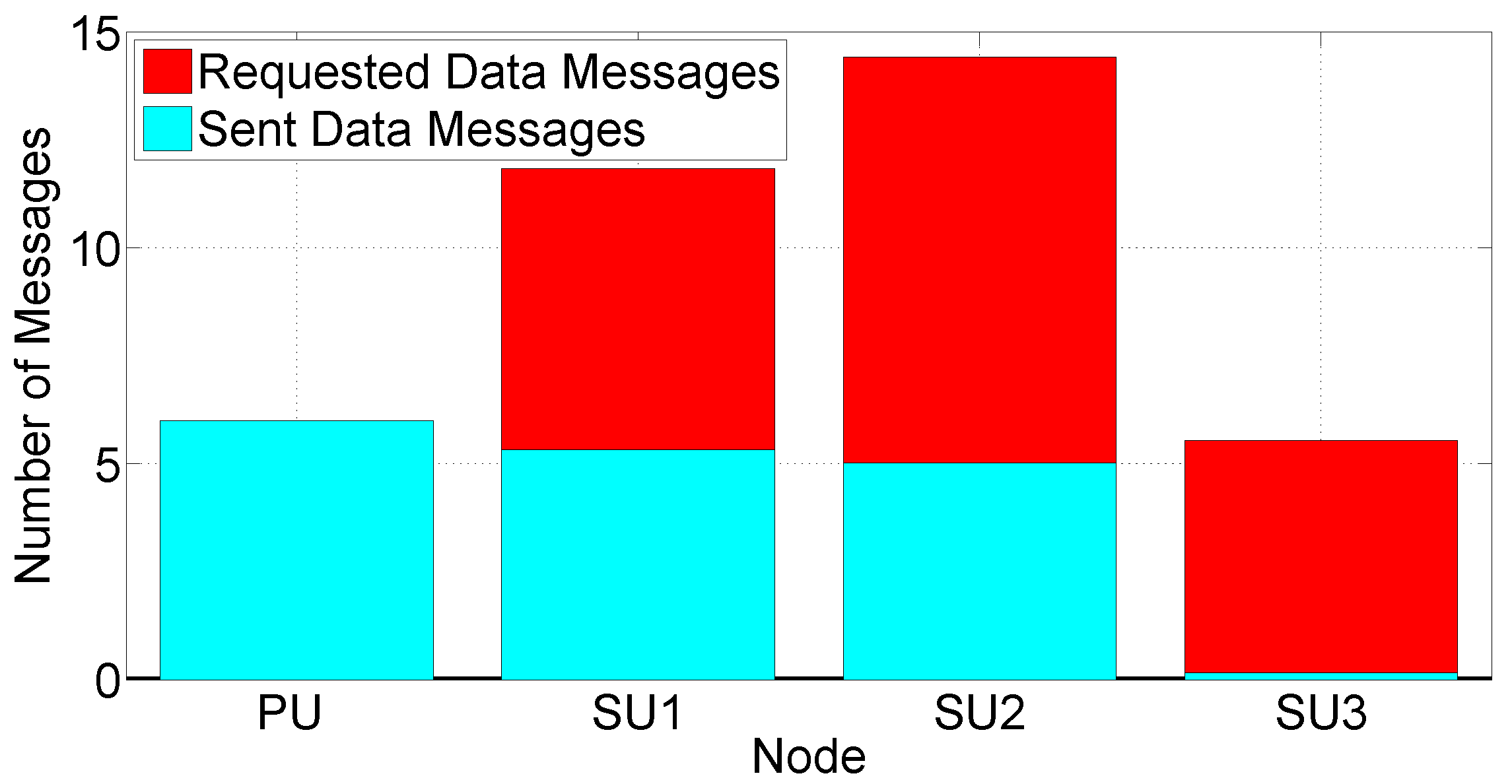
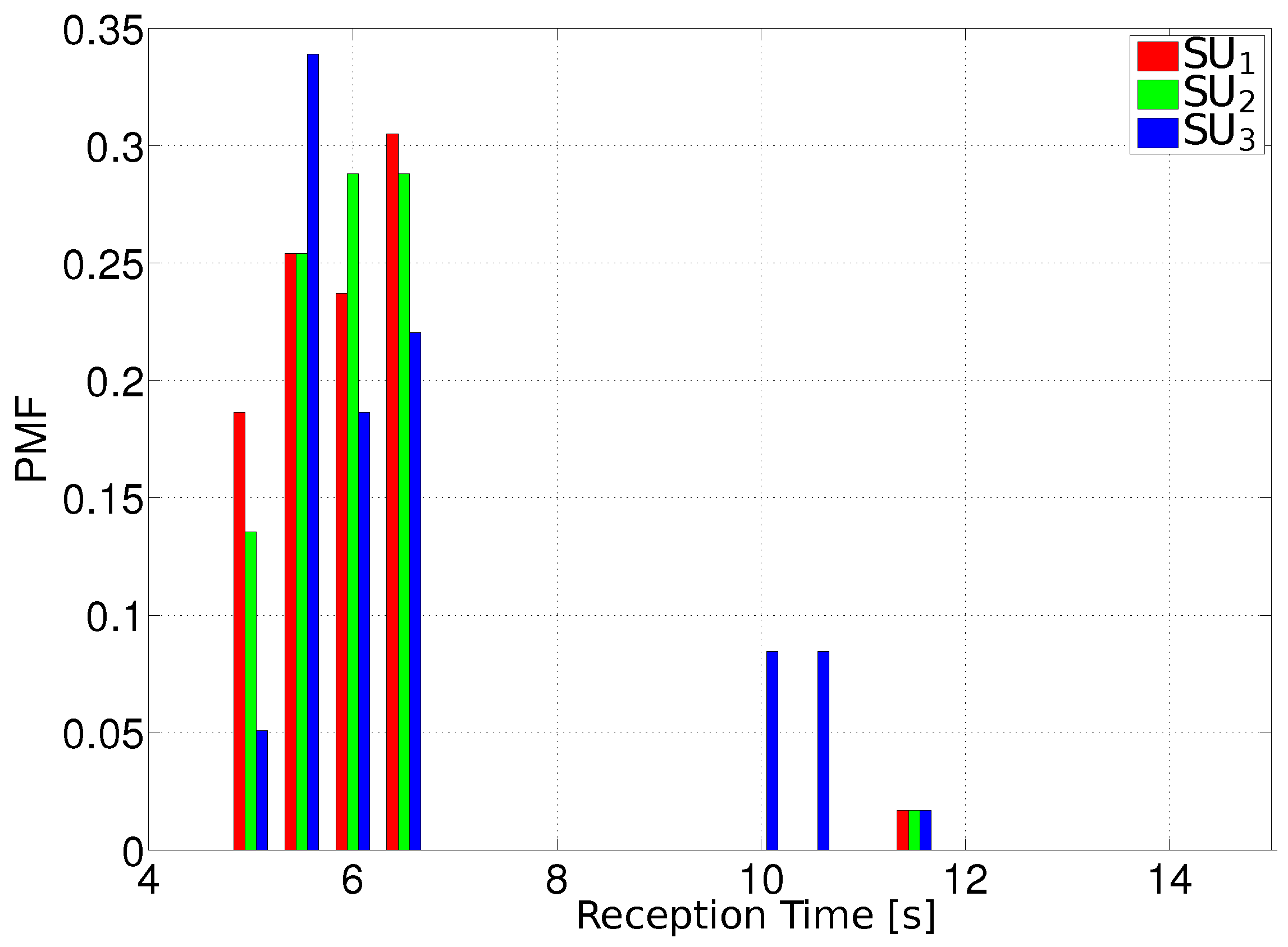
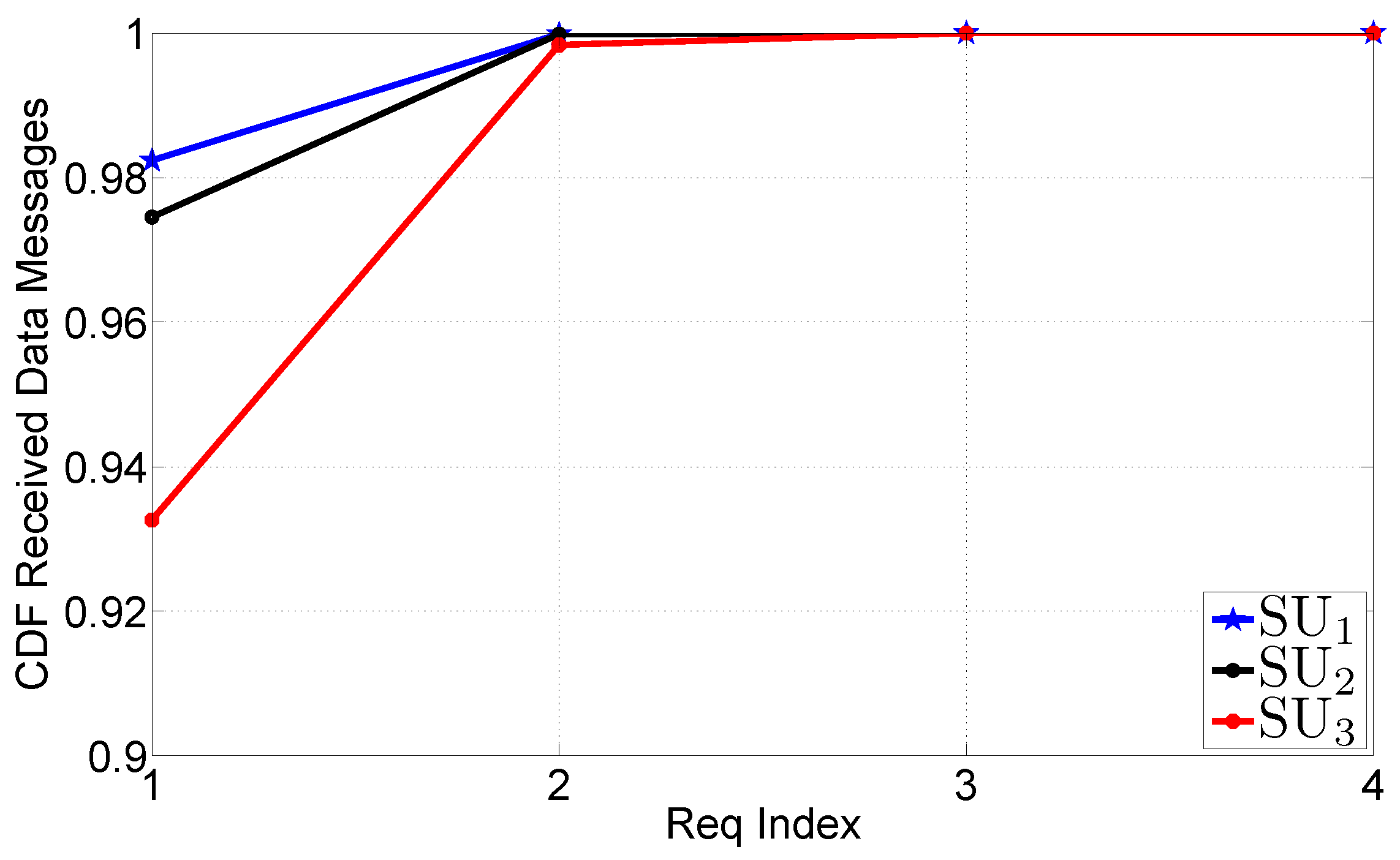
5.3.3. Scenario 2
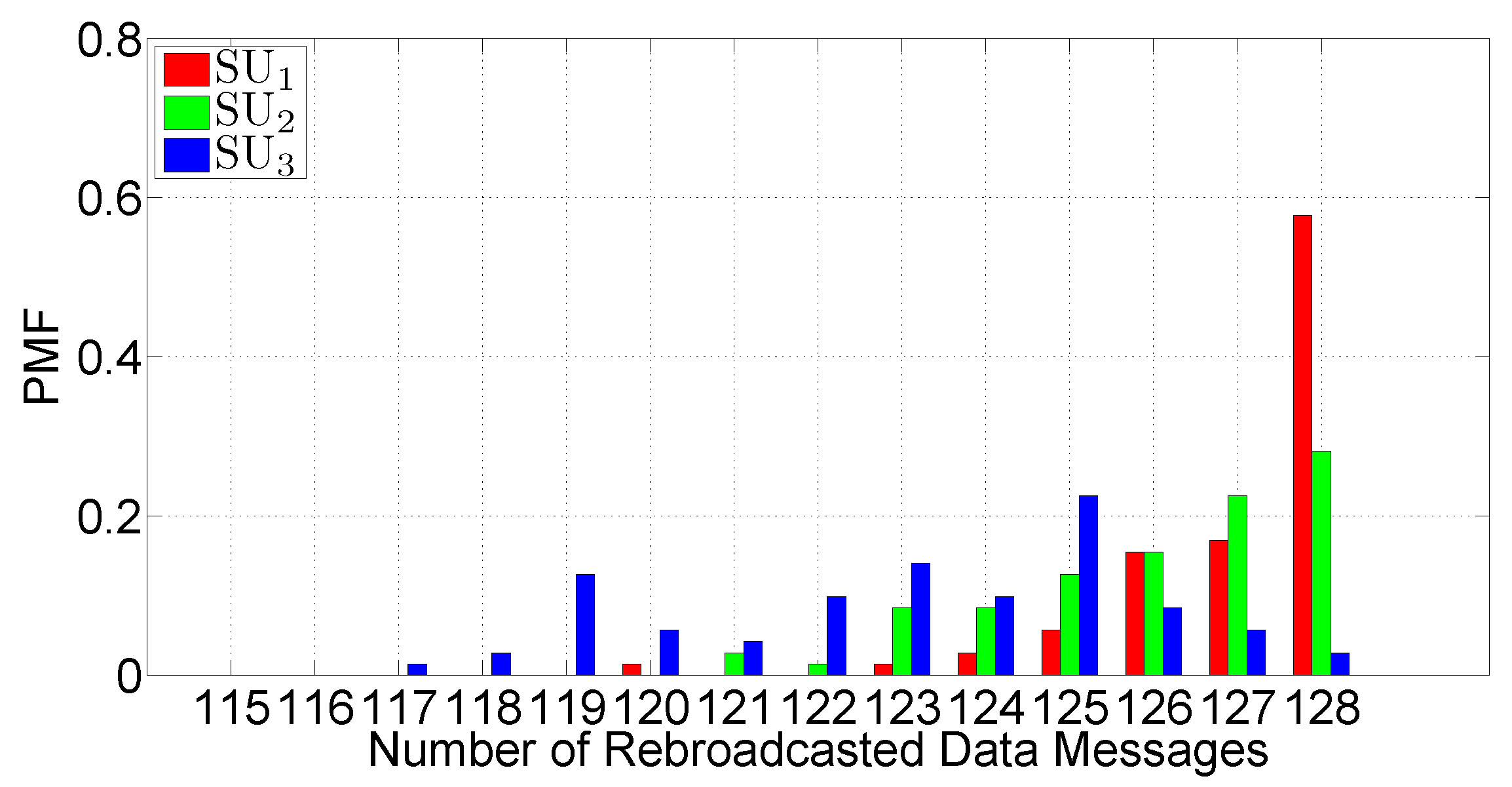
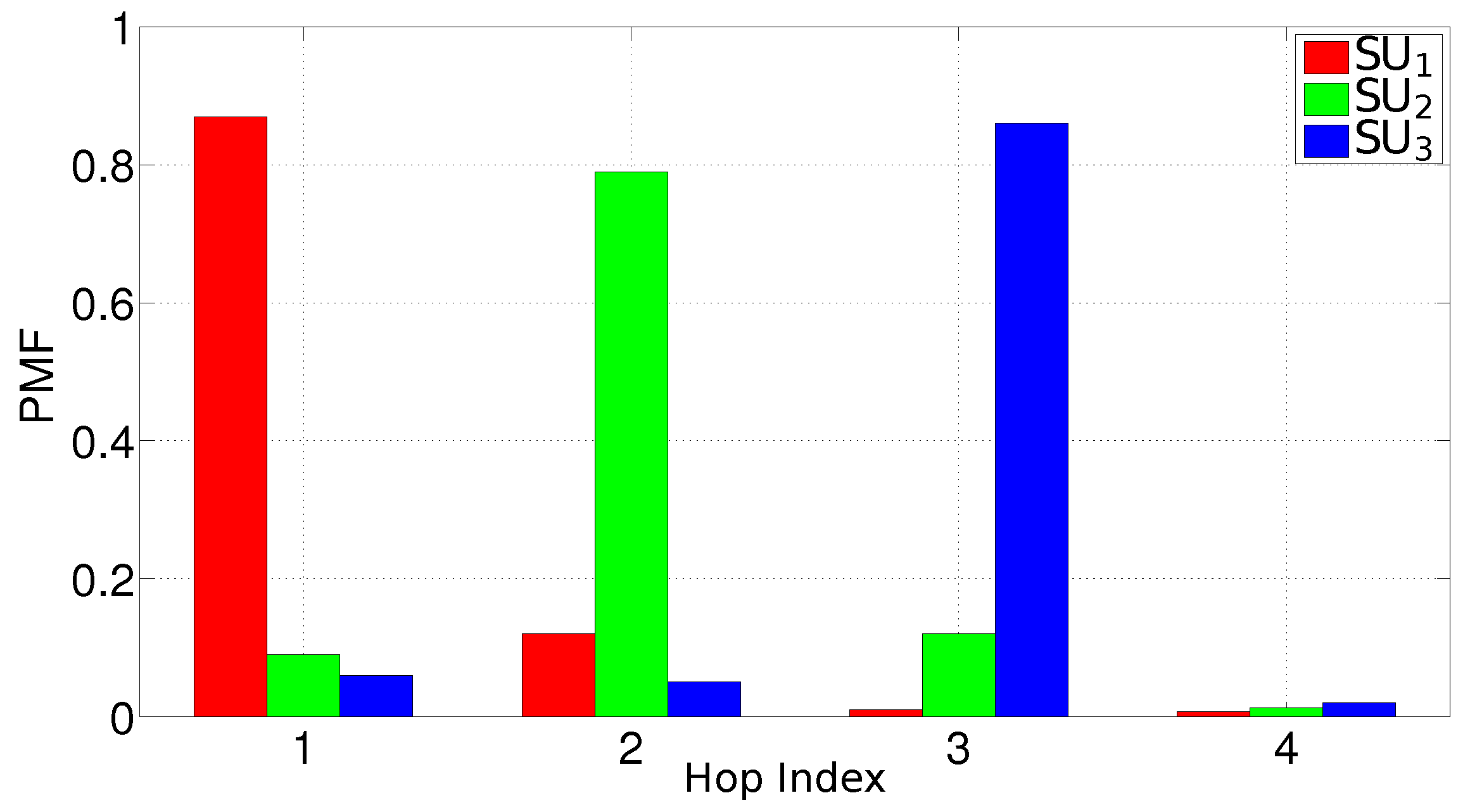
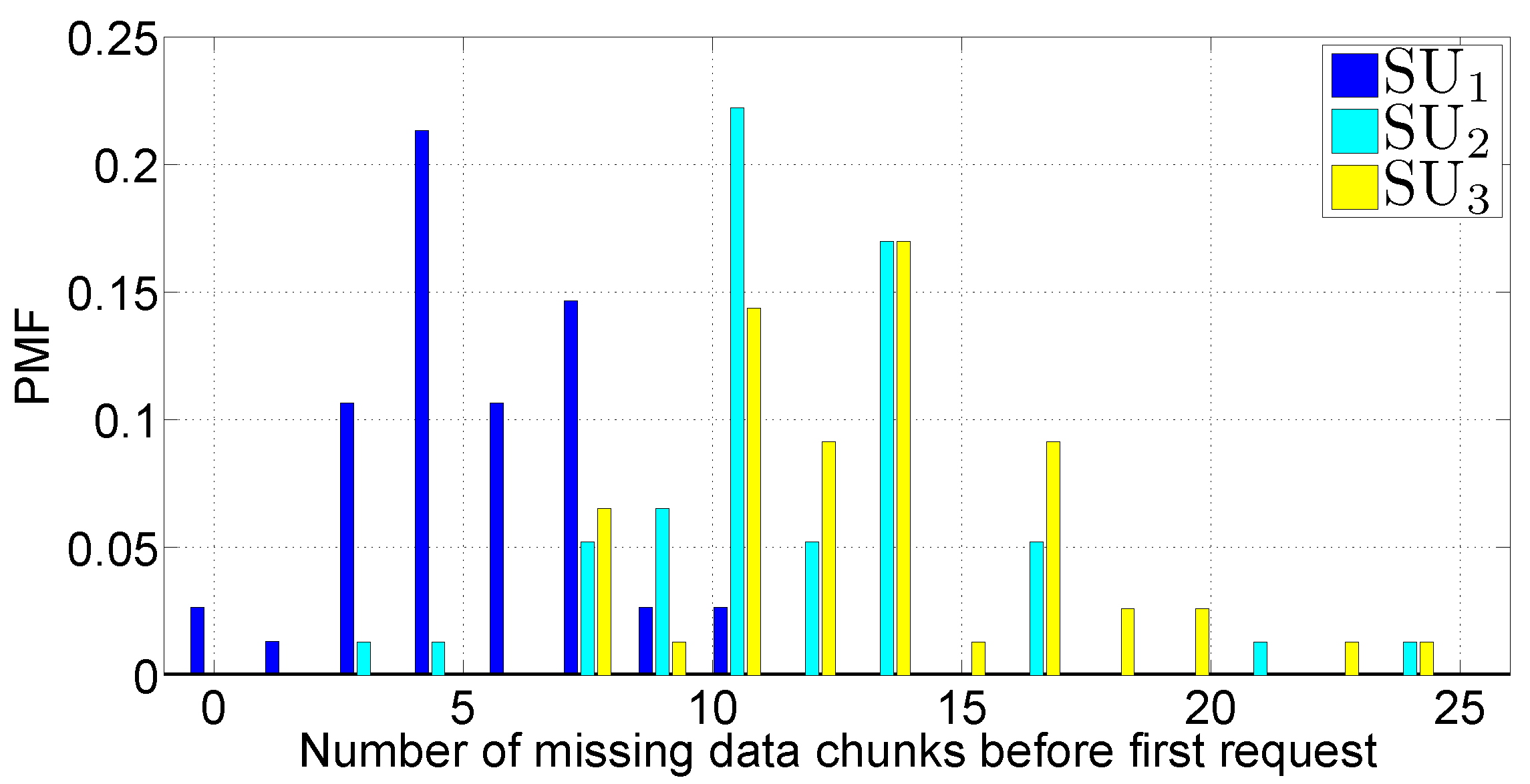
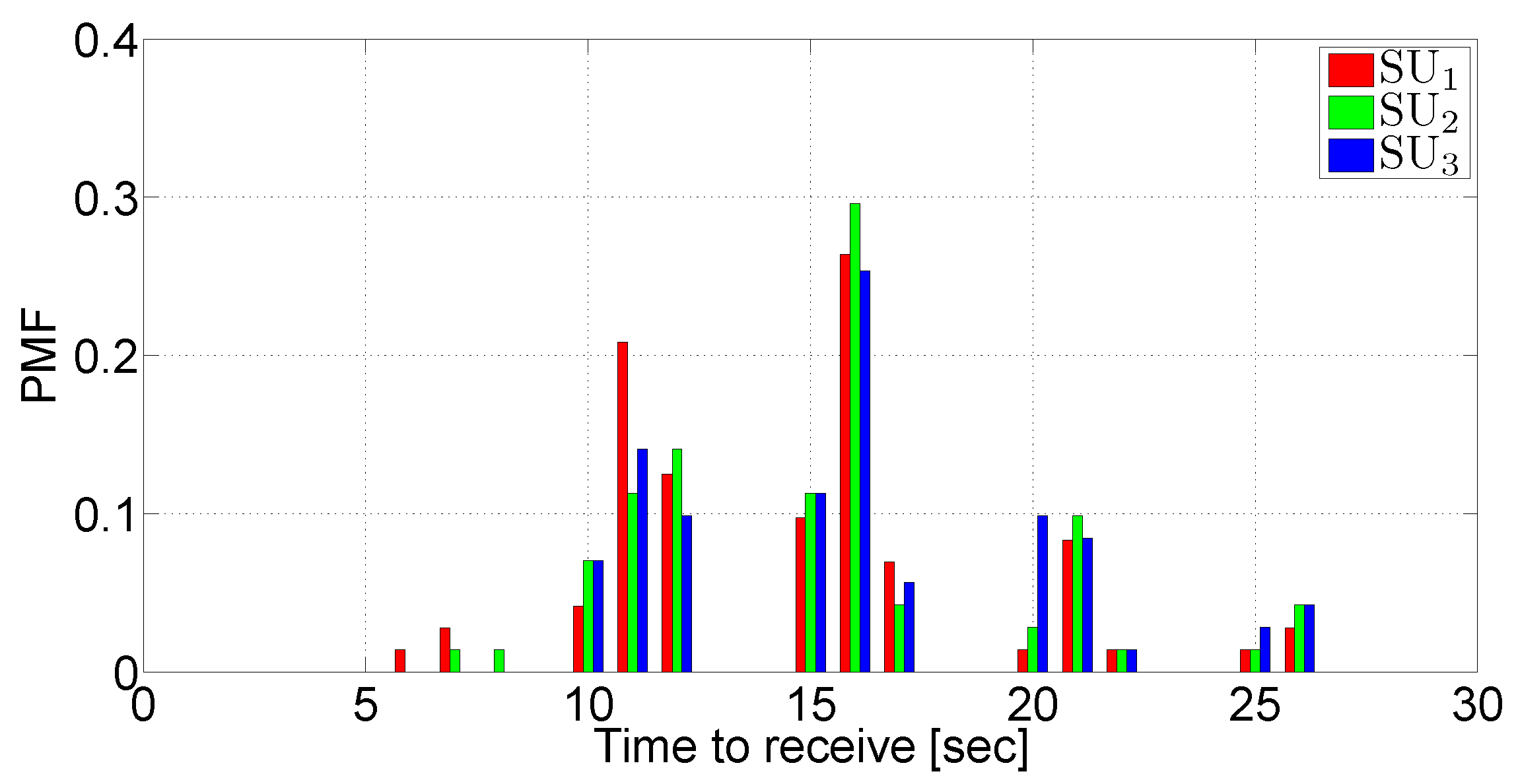
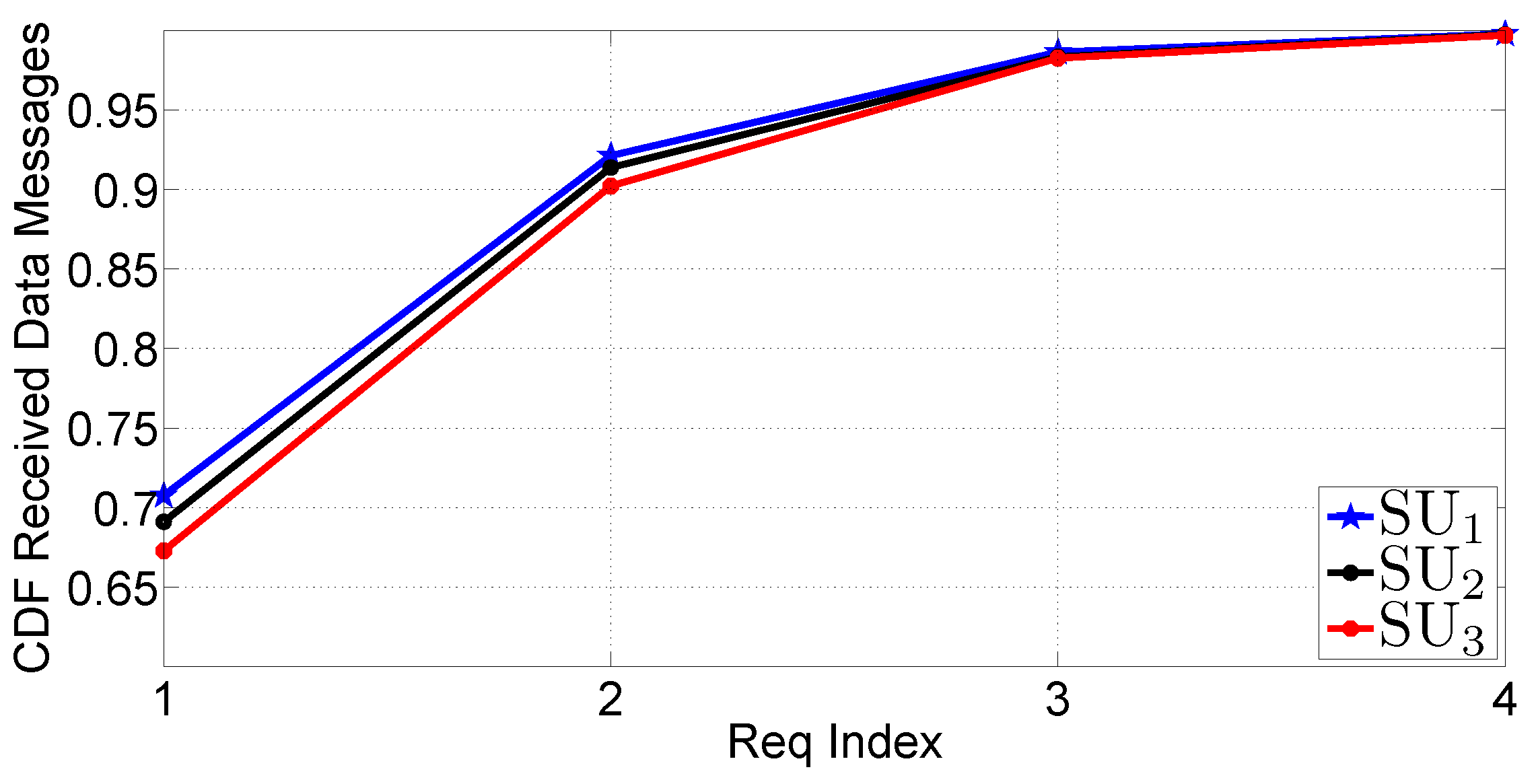
5.4. Tests in a Mobile Scenario
5.4.1. Scenario Description
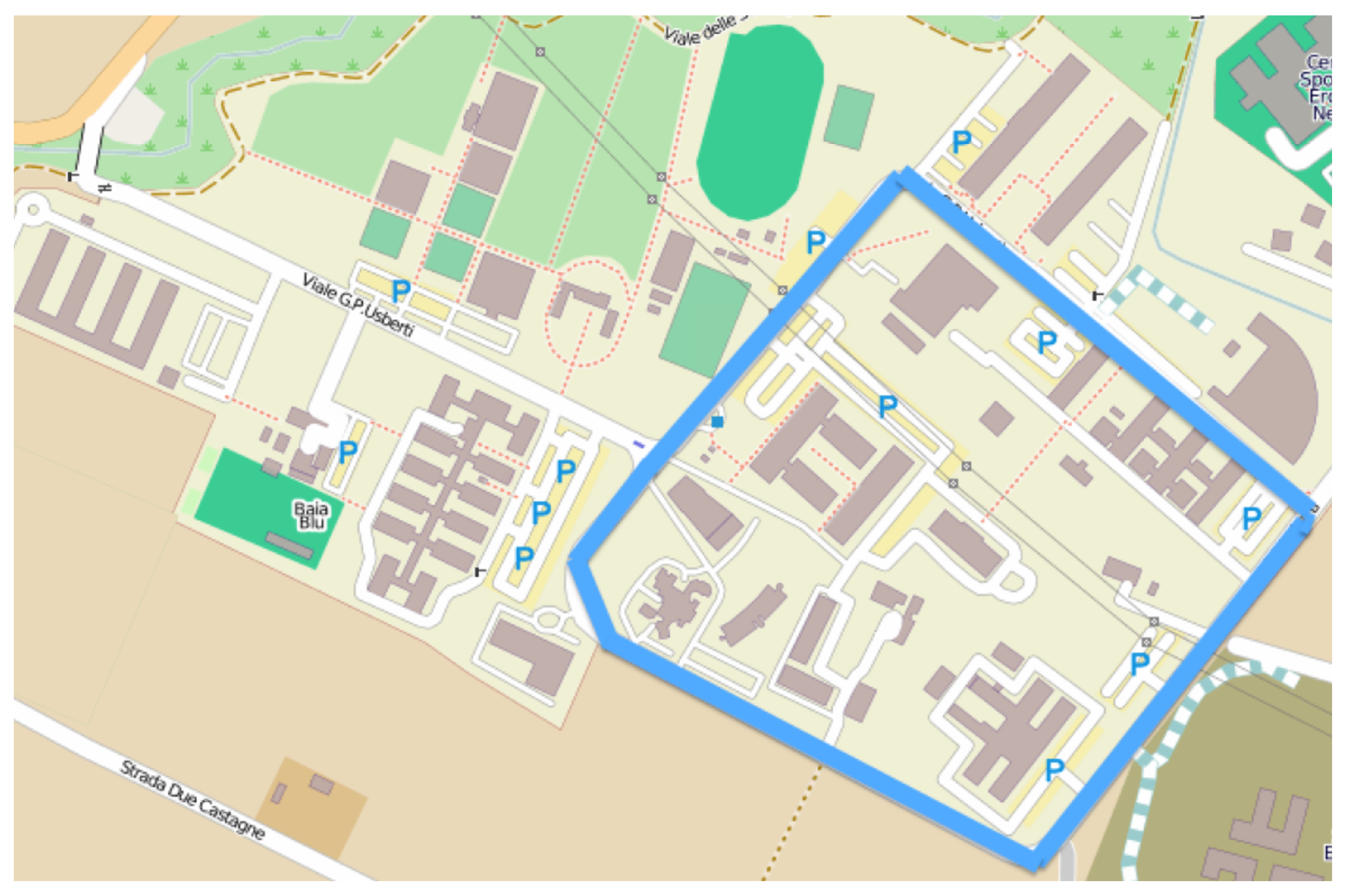
5.4.2. Experimental Results
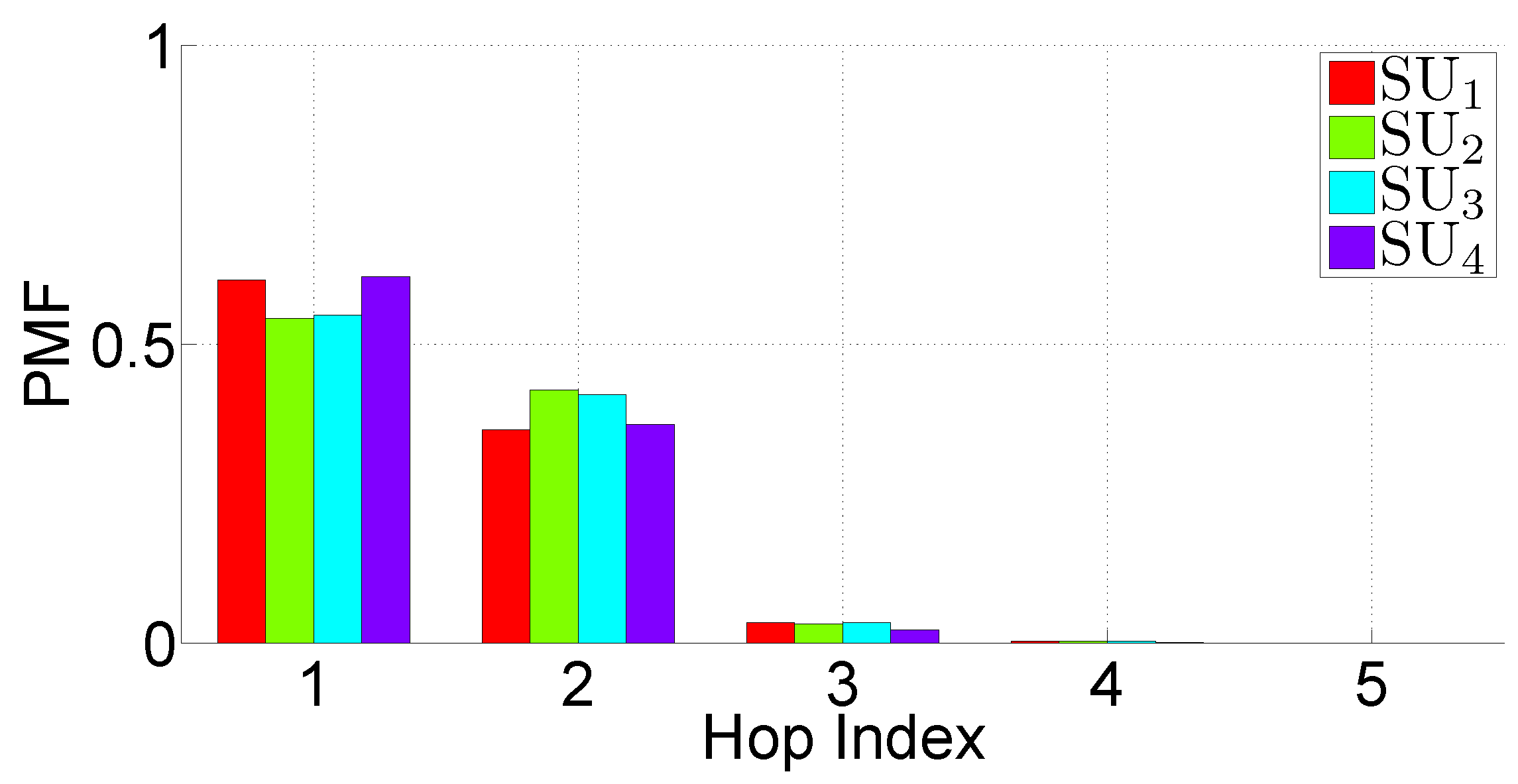
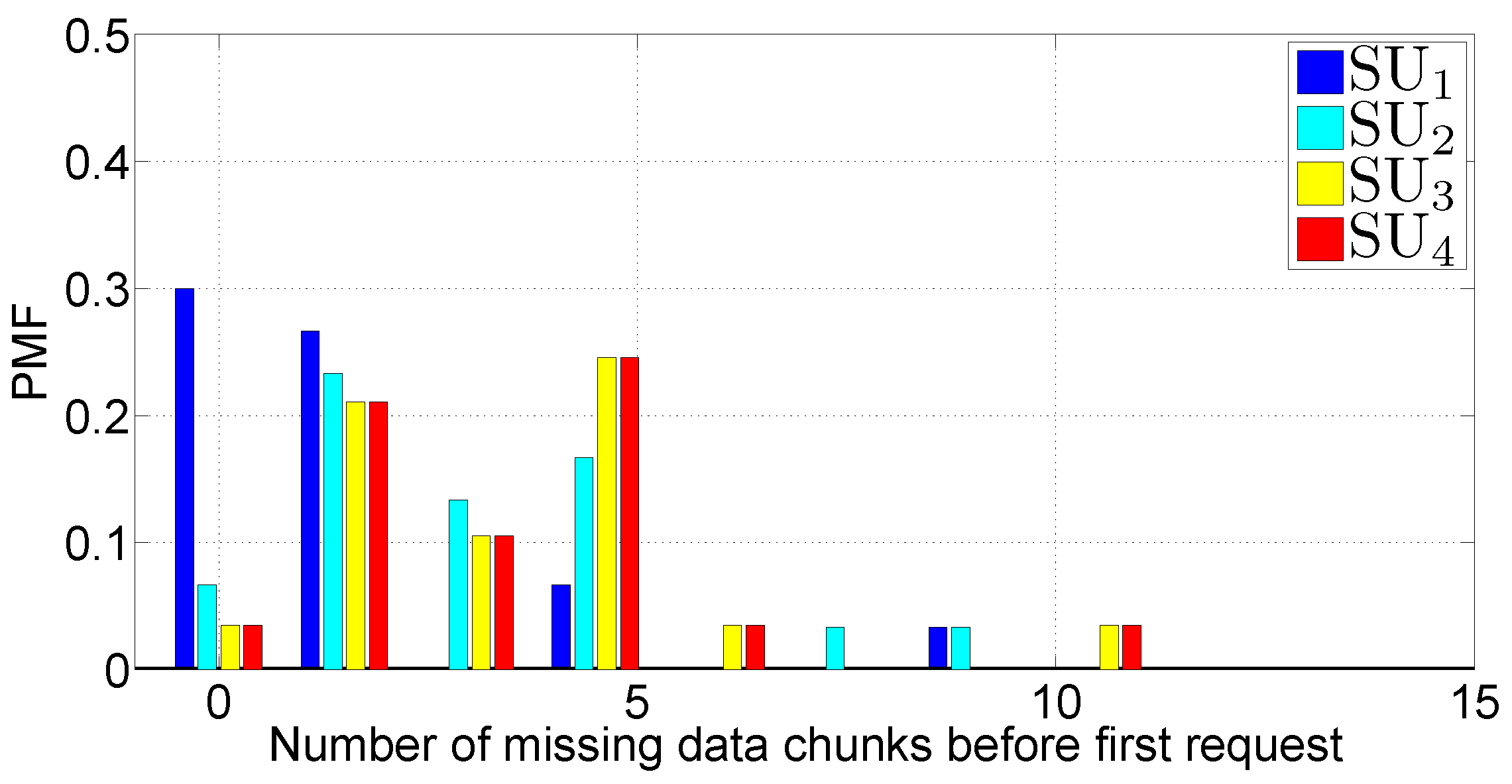
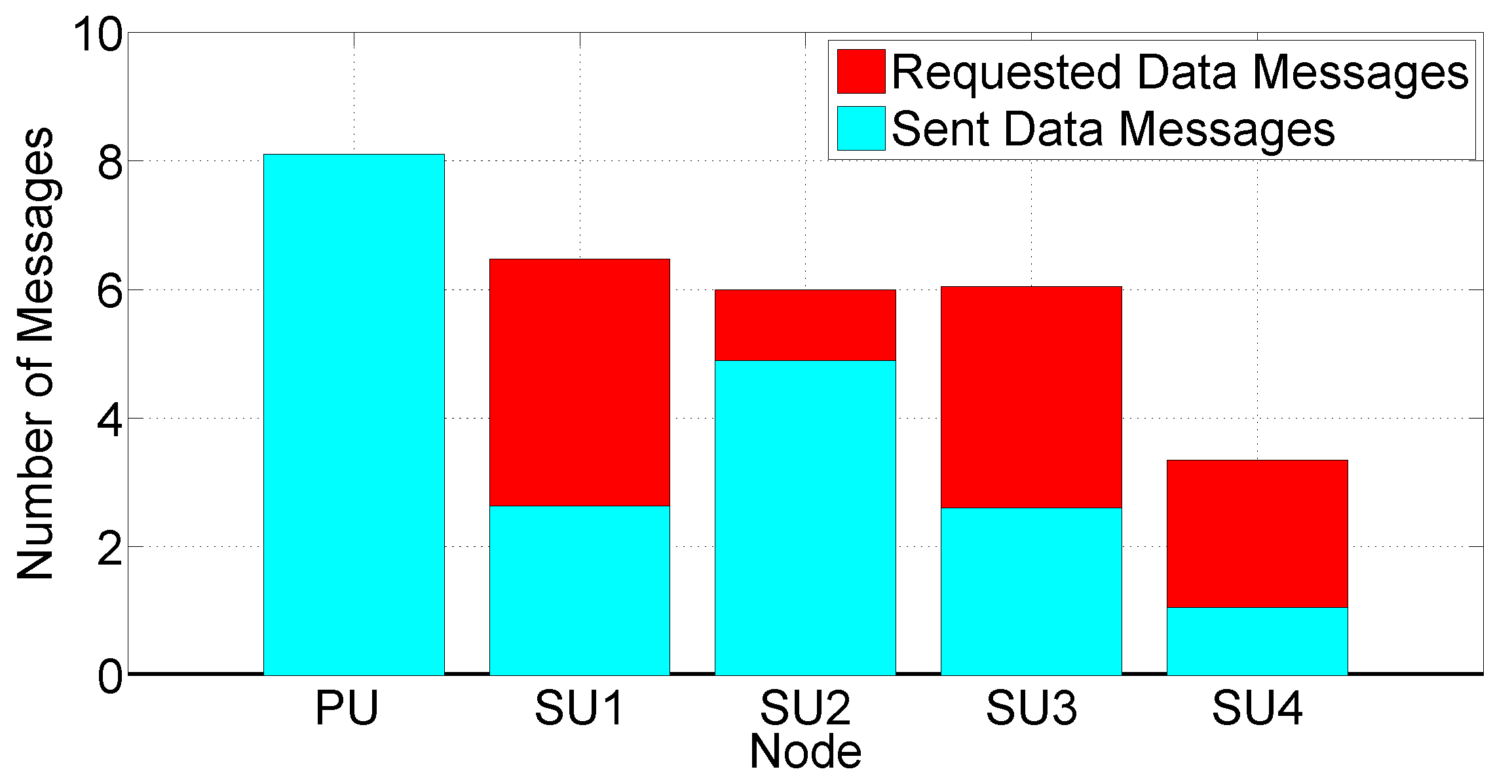
- the archive is received in a very short time (after 1 or 2 REQUEST message rounds)—this happens when the network conditions are good and stationary;
- the archive is received after a large number of rounds (5 or 6)—this happens when the network homogeneity disappears because of phenomena that break the network topology, such as the presence of other vehicles fragmenting the platoon or an excessive inter-vehicle distance.
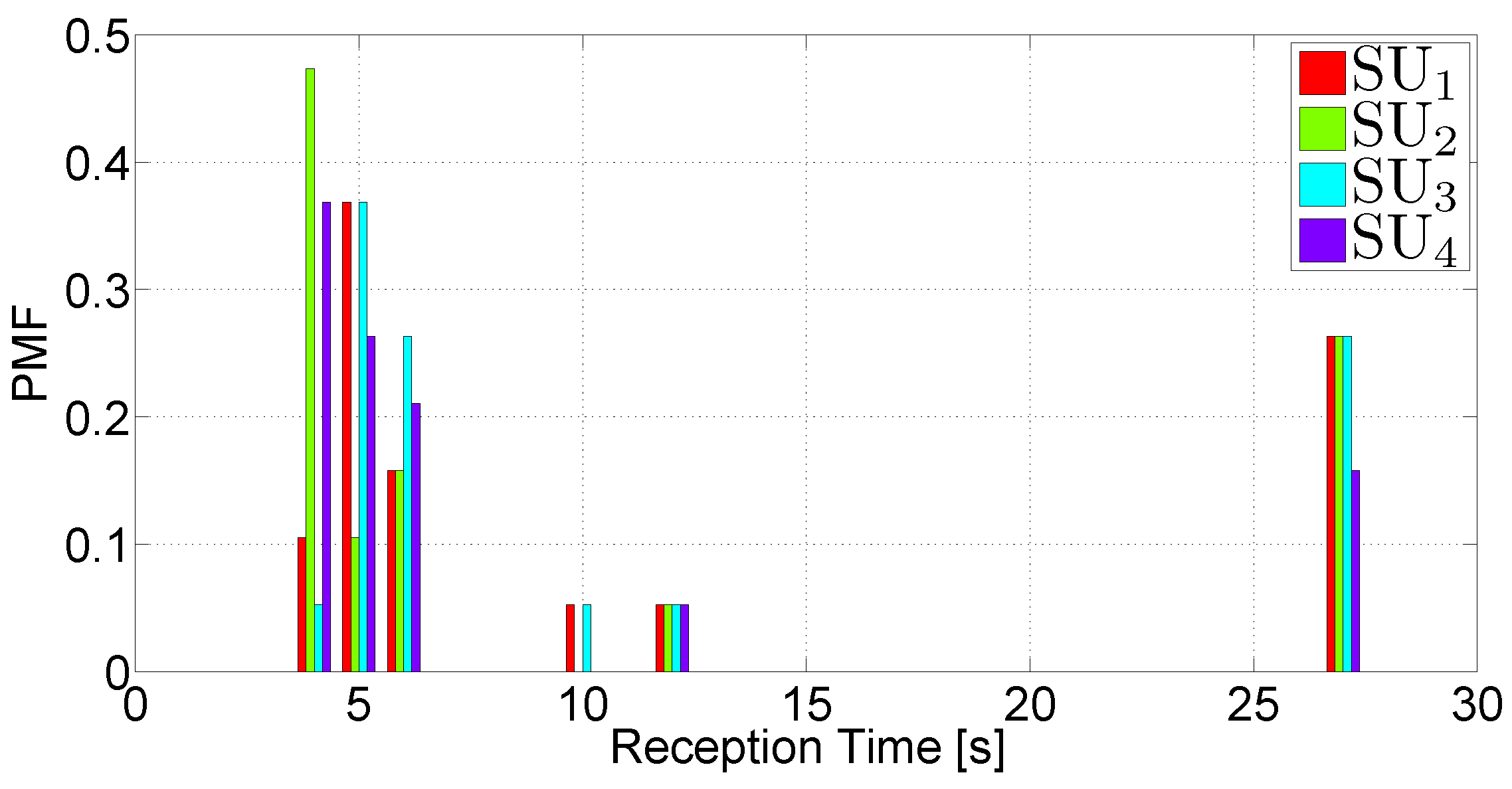
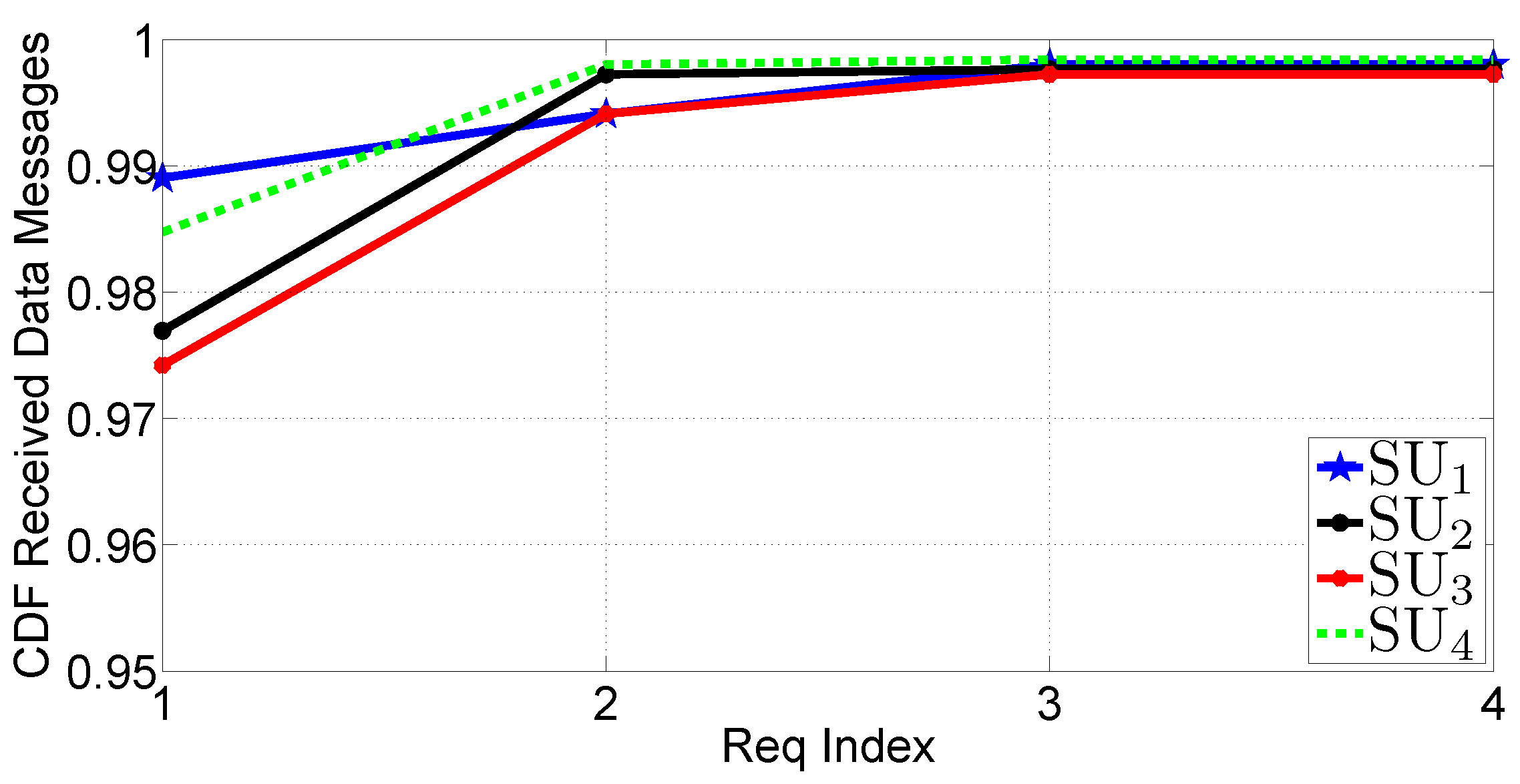
5.5. Discussion
6. Conclusions
Acknowledgments
Conflict of Interest
References
- Hartenstein, H.; Laberteaux, K. VANET Vehicular Applications and Inter-Networking Technologies; John Wiley & Sons: Chichester, UK, 2010. [Google Scholar]
- Insitute of Electrical and Electronics Engineers. IEEE Standard for Information technology—Telecommunications and Information Exchange between Systems—Local and Metropolitan Area Networks–Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments; IEEE Standard 802.11p-2010 (Amendment to IEEE Std 802.11-2007); IEEE: Washington, DC, USA, 2010; pp. 1–51. [Google Scholar]
- European Profile Standard for the Physical and Medium Access Control Layer of Intelligent Transport Systems Operating in the 5 GHz Frequency Band; ETSI ES 202 663 V1.1.0; ETSI: Sophia-Antipolis, France, 2010; pp. 1–27.
- Araniti, G.; Campolo, C.; Condoluci, M.; Iera, A.; Molinaro, A. LTE for vehicular networking: A survey. IEEE Commun. Mag. 2013, 51, 148–157. [Google Scholar] [CrossRef]
- Nye, S. Connected Vehicle Survey. Technical Report for Informa Telecoms&Media: London, UK, 2012. Available online: http://connectedcarsworld.com/wp-content/uploads/connectedcw13/2013/02/Informa Connected Vehicle Survey interim results.pdf (accessed on 22 July 2013).
- Vinel, A. 3GPP LTE versus IEEE 802.11p/WAVE: Which technology is able to support cooperative vehicular safety applications? IEEE Wirel. Commun. Lett. 2012, 1, 125–128. [Google Scholar] [CrossRef]
- Intelligent Transport Systems (ITS). Framework for Public Mobile Networks in Cooperative. ITS (C-ITS); ETSI: Sophia-Antipolis, France, 2012. [Google Scholar]
- Vandenberghe, W.; Moerman, I.; Demeester, P. On the Feasibility of Utilizing Smartphones for Vehicular Ad Hoc Networking. In Proceedings of the ITS Telecommunications (ITST), 2011 11th International Conference on IEEE, Saint-Petersburg, Russia, 28–30 August 2011; pp. 246–251.
- Baiocchi, A.; Cuomo, F. Infotainment services based on push-mode dissemination in an integrated VANET and 3G architecture. J. Commun. Netw. 2013, 15, 179–190. [Google Scholar] [CrossRef]
- Ferrari, G.; Busanelli, S.; Iotti, N.; Kaplan, Y. Cross-network Information Dissemination in VANETs. In Proceedings of the 11th International Conference on Telecommunications for Intelligent Transport Systems (ITST-2011), IEEE, Saint-Petersburg, Russia, 28–30 August 2011; pp. 351–356.
- Eureka Project 6252 X-NETAD. Available online: http://www.eurekanetwork.org/project/-/id/6252 (accessed on 22 July 2013).
- Avni, O. Performance and Limitations of Cellular-based Traffic Monitoring Technologies: Based on Case Study of Benchmarking Cellint’s TrafficSense with Road Sensors. In Proceedings of the Institute of Transportation Engineers (ITE) Technical Conference and Exhibit, San Diego, CA, USA, 25–28 March 2007.
- Calabrese, F.; Colonna, M.; Lovisolo, P.; Parata, D.; Ratti, C. Real-time urban monitoring using cell phones: A case study in Rome. Intell. Transp. Syst. IEEE Trans. 2011, 12, 141–151. [Google Scholar] [CrossRef]
- Rybicki, J.; Scheuermann, B.; Kiess, W.; Lochert, C.; Fallahi, P.; Mauve, M. Challenge: Peers on Wheels-a Road to New Traffic Information Systems. In Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking, Montréal, QC, Canada, 9–14 September 2007; pp. 215–221.
- Rybicki, J.; Scheuermann, B.; Koegel, M.; Mauve, M. PeerTIS: A Peer-to-peer Traffic Information System. In Proceedings of the Sixth ACM International Workshop on VehiculAr InterNETworking, Beijing, China, 15–16 September 2009; pp. 23–32.
- Picone, M.; Amoretti, M.; Zanichelli, F. Proactive neighbor localization based on distributed geographic table. Int. J. Pervasive Comput. Commun. 2011, 7, 240–263. [Google Scholar] [CrossRef]
- Picone, M.; Amoretti, M.; Zanichelli, F. A Decentralized Smartphone Based Traffic Information System. In Proceedings of the Intelligent Vehicles Symposium (IV), 2012 IEEE, Alcalá de Henares, Spain, 3–7 June 2012; pp. 523–528.
- Ni, S.; Tseng, Y.; Chen, Y.; Sheu, J. The Broadcast Storm Problem in a Mobile Ad Hoc Network. In Proceedings of the ACM Conference on Mobile Computing and Networking (MOBICOM), Seattle, WA, USA, 15–19 August 1999; pp. 151–162.
- Khabbazian, M.; Bhargava, V.K. Efficient broadcasting in mobile ad hoc networks. IEEE Trans. Mob. Comput. 2009, 8, 231–245. [Google Scholar] [CrossRef]
- Kihl, M.; Sichitiu, M.; Joshi, H.P. Design and evaluation of two geocast protocols for vehicular ad-hoc networks. J. Int. Eng. Klidarithmos Press 2008, 2, 127–135. [Google Scholar]
- Torrent-Moreno, M.; Mittag, J.; Santi, P.; Hartenstein, H. Vehicle-to-vehicle communication: Fair transmit power control for safety-critical information. IEEE Trans. Veh. Technol. 2009, 58, 3684–3707. [Google Scholar] [CrossRef]
- Korkmaz, G.; Ekici, E.; Ozguner, F. Black-burst-based multihop broadcast protocols for vehicular networks. IEEE Trans. Veh. Technol. 2007, 56, 3159–3167. [Google Scholar] [CrossRef]
- Fasolo, E.; Zanella, A.; Zorzi, M. An Effective Broadcast Scheme for Alert Message Propagation in Vehicular Ad hoc Networks. In Proceedings of the IEEE International Conference on Communication (ICC), Istanbul, Turkey, 11–15 June 2006; Volume 9, pp. 3960–3965.
- Sahoo, J.; Wu, E.; Sahu, P.; Gerla, M. BPAB: Binary Partition Assisted Emergency Broadcast Protocol For Vehicular Ad Hoc Networks. In Proceedings of the IEEE International Conference on Computer Communicaition and Networks (ICCCN), San Francisco, CA, USA, 3–6 August 2009; pp. 1–6.
- Busanelli, S.; Martalò, M.; Ferrari, G. Clustered Vehicular Networks: Decentralized Detection “on the move”. In Proceedings of the ITS Telecommunications (ITST), 2011 11th International Conference on, IEEE, Saint-Petersburg, Russia, 23–25 August 2011; pp. 744–749.
- Busanelli, S.; Ferrari, G.; Panichpapiboon, S. Efficient Broadcasting in IEEE 802.11 Networks through Irresponsible Forwarding. In Proceedings of the IEEE Global Telecommunication Conference (GLOBECOM), Honolulu, HA, USA, 30 November–4 December 2009.
- Busanelli, S.; Ferrari, G.; Gruppini, R. Recursive analytical performance evaluation of broadcast protocols with silencing: Application to VANETs. EURASIP J. Wirel. Commun. Netw. 2012, 2012, 1–21. [Google Scholar] [CrossRef]
- Car-to-Car Communication Consortium. Available online: http://www.car-2-car.org (accessed on 22 July 2013).
- Final GeoNet Specification, GeoNet Deliverable D2.2, 2010. Available online: http://www.geonet-project.eu/ (accessed on 21 July 2013).
- Wisitpongphan, N.; Bai, F.; Mudalige, P.; Sadekar, V.; Tonguz, O.K. Routing in sparse vehicular ad hoc wireless networks. IEEE J. Sel. Areas Commun. 2007, 25, 1538–1556. [Google Scholar] [CrossRef]
- Insitute of Electrical and Electronics Engineers. IEEE Std 802.11TM-2007. Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications; IEEE: Washington, DC, USA, 2007. [Google Scholar]
- Rappaport, T.S. Wireless Communications. Principles & Practice, 2nd ed.; Prentice-Hall: Upper Saddle River, NJ, USA, 2002. [Google Scholar]
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Busanelli, S.; Rebecchi, F.; Picone, M.; Iotti, N.; Ferrari, G. Cross-Network Information Dissemination in Vehicular Ad hoc Networks (VANETs): Experimental Results from a Smartphone-Based Testbed. Future Internet 2013, 5, 398-428. https://doi.org/10.3390/fi5030398
Busanelli S, Rebecchi F, Picone M, Iotti N, Ferrari G. Cross-Network Information Dissemination in Vehicular Ad hoc Networks (VANETs): Experimental Results from a Smartphone-Based Testbed. Future Internet. 2013; 5(3):398-428. https://doi.org/10.3390/fi5030398
Chicago/Turabian StyleBusanelli, Stefano, Filippo Rebecchi, Marco Picone, Nicola Iotti, and Gianluigi Ferrari. 2013. "Cross-Network Information Dissemination in Vehicular Ad hoc Networks (VANETs): Experimental Results from a Smartphone-Based Testbed" Future Internet 5, no. 3: 398-428. https://doi.org/10.3390/fi5030398
APA StyleBusanelli, S., Rebecchi, F., Picone, M., Iotti, N., & Ferrari, G. (2013). Cross-Network Information Dissemination in Vehicular Ad hoc Networks (VANETs): Experimental Results from a Smartphone-Based Testbed. Future Internet, 5(3), 398-428. https://doi.org/10.3390/fi5030398






