Abstract
Biometric authentication is widely regarded as more secure and reliable than conventional approaches like passwords and PINs. Nonetheless, many current systems rely on active user participation, such as fingerprint scanning or facial recognition, which can disrupt tasks, increase the likelihood of errors, and raise privacy concerns. To address these challenges, this study introduces a continuous, seamless authentication framework that utilizes vital signs for passive identity verification across various activities, including resting, walking, and running. The framework analyzes physiological indicators such as Heart Rate (HR), Heart Rate Variability (HRV), Skin Temperature, Peripheral Oxygen Saturation (), and Breathing Rate to provide zero-effort authentication without requiring user intervention. Multiple machine learning algorithms, including Decision Tree, Random Forest, XGBoost, Gradient Boosting, and K-Nearest Neighbors, were implemented and compared to identify the most effective predictive model. The methodology involved data collection, preprocessing, model construction, evaluation, and comparison. Experimental results revealed that the XGBoost Classifier achieved the highest accuracy at 96%. Overall, the proposed framework demonstrates strong reliability, scalability, adaptability, and flexibility, making it suitable for practical deployment. By continuously verifying identity without interrupting user activity, it improves both security and usability, offering a modern and convenient alternative to traditional authentication methods.
1. Introduction
Security is a critical concern in cyberspace applications and services, and user authentication is a crucial step in ensuring the protection of information systems and networks from unauthorized access [1]. As the first line of defense in cyberspace security [2], user authentication verifies the identity of a user to an authentication entity. Due to the open nature of cyberspace, which exposes the network to a higher risk of security vulnerabilities [3], user authentication is even more important. Among different approaches, biometrics have emerged as particularly effective because they rely on inherent human traits rather than knowledge or possessions [4,5,6,7,8,9]. Unlike passwords or tokens that can be lost, shared, or stolen, biometric features are inseparable from the individual and therefore provide stronger resistance to impersonation. Beyond convenience, they also contribute to privacy protection and robust security design. However, many biometric systems still impose usability challenges. They often require users to pause their activity to provide a sample, such as pressing a finger, looking into a camera, or positioning the eye for scanning. These interactions disrupt the user experience and make it difficult to maintain authentication continuously, especially in situations involving movement or multitasking. To address these challenges, this research proposes a continuous, zero-effort authentication framework that leverages vital signs for passive identity verification during various activities, including resting, walking, and running. By employing machine learning algorithms to analyze physiological signals, the framework aims to enhance security while minimizing user inconvenience. This study further evaluates multiple classification models to identify the most effective predictive approach and demonstrate the feasibility, scalability, and adaptability of vital signs-based authentication in real-world applications.
This research seeks to answer the following questions:
- How can vital sign data HR, HRV, Skin Temperature, , and Breathing Rate be effectively utilized for continuous, zero-effort biometric authentication?
- Which ML algorithm achieves the highest performance in accurately predicting user identity using vital signs?
- How does the framework perform under different user activities (e.g., resting, walking, running)?
- Can a vital signs-based authentication framework provide usability, reliability, and flexibility for real-world applications?
The remainder of this paper is structured as follows: Section 2 describes the background and rationale of the study; Section 3 provides an overview of the proposed tool; Section 4 explains the steps taken to acquire, clean, and visualize the data; Section 5 presents the findings of the study; Section 6 presents a comparative summary of the proposed framework and several existing studies; finally, Section 7 concludes with a summary of the proposed tool and our findings.
2. Related Work
Vital signs-based authentication introduces an innovative method for verifying identity by using physiological characteristics such as HR, Breathing Rate, skin Temperature, and other related metrics. Unlike traditional approaches like passwords, this biometric technique is inherently tied to the user and can be continuously monitored. However, as promising as this method is, it is not without its drawbacks, particularly regarding user interruption and inconvenience. Traditional user authentication methods such as passwords or two-factor authentication typically demand active user participation, which can interrupt daily activities. These methods can prove especially impractical in scenarios requiring hands-free interaction or constant mobility. To date, only a limited number of studies have explored the use of vital signs for authentication purposes. One notable study [10] introduced HeartPrint, which applies mmWave radar to capture heartbeat motion patterns as a biometric signature. While the system achieved strong recognition in controlled, stationary conditions, its accuracy decreased significantly once subjects were in motion, limiting its utility for continuous mobile authentication. However, the system lacks adaptability when users are in motion or engaged in physical activity. Another approach [11], presented Utter Innocence, a contactless approach that verifies users through physiological signals. Although the model achieved promising accuracy, its performance was sensitive to factors such as body posture and overall physical condition, restricting consistency in everyday usage. Many conventional methods of authentication using vital signs rely on one or two metrics, such as HR or HRV, which limits robustness by narrowing the biometric scope. While these metrics can provide some indication of a user’s unique biological profile, relying on only a single or dual-factor approach has notable limitations. In [12], developed an identity verification method using Doppler radar to capture respiratory signals, which were classified with an SVM (RBF kernel). Although the system reported near-perfect accuracy, it relied solely on respiration and required fixed placement, reducing its feasibility in dynamic or mobile scenarios. Another recent work [13] incorporated two biometric features, the respiratory movement effect and internal organ reflections (notably from the heart). Although effective in controlled experiments, it still faces limitations due to reliance on just two features and difficulties with continuous real-world deployment. Furthermore, a study [14] proposed CamPressID, which utilizes smartphone cameras to extract fingertip PPG signals. Although the system matched the performance of dedicated PPG sensors with 90% BAC, it required precise fingertip pressure and careful positioning, reducing its practicality outside controlled settings. Another study [15] built an ECG-based authentication framework, enhanced by convolutional neural networks and contrastive self-supervised learning. While the system excelled in accuracy and showed potential for IoT integration, it lacked flexibility and robustness compared to multi-signal, activity-aware approaches. Similarly, another study [16] proposes an implicit, context-dependent authentication system using soft biometric signals specifically, heart rate, gait, and breathing audio on wearable devices. Although this approach is lightweight and user-friendly, it suffers from several drawbacks. Its reliance on a narrow set of features may weaken accuracy and resilience under real-world variability. Additionally, signals such as gait and breathing audio are highly sensitive to environmental conditions, background noise, and recording quality, which may compromise reliability. The absence of explicit activity-level modeling further limits the system, as it does not adapt authentication logic to different physical states (e.g., resting, walking, or running), which is critical for maintaining accuracy during dynamic daily activities. Furthermore, although evaluated with leave-one-out validation, the study does not demonstrate real-time or continuous authentication, raising concerns about its practical deployment.
To synthesize the existing literature, Table 1 compares previous approaches across key dimensions, including interactivity, support for continuous authentication, flexibility, and whether they employ single or multiple biometric characteristics. After conducting a comprehensive literature review of the most commonly used biometric traits and vital signs in user authentication, it is clear that there is a lack of prior research directly addressing vital signs–based user authentication while the user is in motion. This dearth of previous work emphasizes the significance of our research, as it seeks to fill the gap in the existing knowledge. In this research, we present the user authentication mechanism based on five vital signs while the user is active, such as HR, HRV, Skin Temperature, , and Breathing Rate that can be measured continuously. This diverse set of vital signs ensures a thorough representation of the physiological characteristics necessary for accurate authentication across various user activities. By leveraging ML algorithms to analyze these vital signs in real-time, we aim to develop an authentication system that is convenient for users, without user interruption.

Table 1.
Comparison with the related works, where ✓: Feature Supported, and ✗: Not supported.
One key advantage of using vital signs for authentication is that these signals are continuously generated by the body and can be monitored frequently. The framework could continuously monitor the user’s vital signs, matching them against stored profiles to verify identity without requiring any conscious interaction from the user. This continuous authentication method offers significant benefits: It reduces the need for reauthentication or session-based identity checks, providing a more seamless user experience. Moreover, because the authentication process occurs passively in the background, users experience no interruptions. Vital signs-based authentication could also adapt to different physical states, such as resting, walking, and running. This adaptive nature enhances the robustness and reliability of the authentication process, making it suitable for dynamic environments where the user’s state is constantly changing. This innovative approach of user authentication offers a dynamic and practical solution, aligning with the modern users’ need for mobility and security.
3. The Proposed Framework
3.1. Real-World Application and User Interaction
In a real-world deployment, the proposed authentication framework operates silently in the background using wearable devices such as smartwatches, wristbands, or fitness sensors already used in daily life. After an initial enrollment phase, during which the system records the user’s baseline vital signs (HR, HRV, Skin Temperature, , and Breathing Rate) under multiple conditions such as rest, walking, and light activity, the authentication mechanism becomes fully passive. During normal use, the wearable continuously streams the user’s physiological signals to a mobile device or local processing module, where the trained machine learning model evaluates whether the incoming pattern matches the legitimate user. If the identity is verified, the system maintains uninterrupted access to the protected service (e.g., smartphone unlock, app login, secure workstation session, or IoT device control) without requiring the user to perform any explicit action. If the authentication probability drops below a threshold, the system triggers a lightweight secondary check such as a fingerprint or PIN request. This architecture ensures a seamless user experience by reducing the frequency of manual authentication events while also strengthening security through continuous monitoring. By leveraging sensors that users already wear throughout their day, the framework offers a scalable, low-friction approach suitable for healthcare devices, enterprise environments, mobile applications, and smart-home systems.
3.2. The Proposed Framework Features
3.2.1. Non-Interactive
The proposed framework is designed as a zero-effort, non-interactive authentication system, greatly improving user convenience by removing the need for conscious actions such as typing passwords, scanning fingerprints, or using facial recognition. Once activated, authentication occurs automatically in the background through physiological signals, enabling users to carry out daily activities, such as working, walking, or exercising, without interruptions. This passive approach not only enhances usability but also minimizes risks related to human error and forgotten credentials.
3.2.2. Continuous Authentication
Unlike conventional one-time authentication methods, the framework provides continuous verification by constantly monitoring user vital signs (e.g., HR, HRV, skin temperature, , and breathing rate) in different physical states, including resting, walking and running. This ongoing real-time process ensures that the identity is seamlessly validated as users transition between activities. By continuously authenticating, the system strengthens security, quickly identifying unauthorized access or anomalies, and reducing the risk of intrusions. Moreover, it is well suited for dynamic and mobile environments where users frequently move or multitask, making it ideal for integration with wearable, mobile devices and smart technologies.
3.2.3. Flexibility
A major advantage of the framework is its adaptability to diverse user activities and real-world scenarios; the framework is capable of authenticating users across various physical states without requiring behavior-specific calibration. This physiological-based approach is inclusive, maintaining high accuracy whether the user is at rest, walking, or engaged in vigorous activity. Such flexibility ensures reliable performance across varied contexts, making the framework suitable for applications that demand secure, seamless, and adaptive authentication.
At its core, the framework leverages machine learning to identify users based on their unique physiological traits. By collecting and analyzing HR, HRV, Skin Temperature, in real time, it builds a comprehensive representation of the user’s physiological profile. This allows for continuous, unobtrusive authentication that strengthens security while maintaining a seamless user experience across different activities.
Figure 1 provides a high-level overview of the proposed process. The authentication workflow begins with the collection of vital signs, which are synthetically generated during the system’s development and training stages. These signals are then analyzed using advanced machine learning algorithms that continuously validate the user’s identity. To strengthen reliability and accuracy, the ML models are trained on synthetic datasets that closely replicate real-world conditions, including variability and noise.
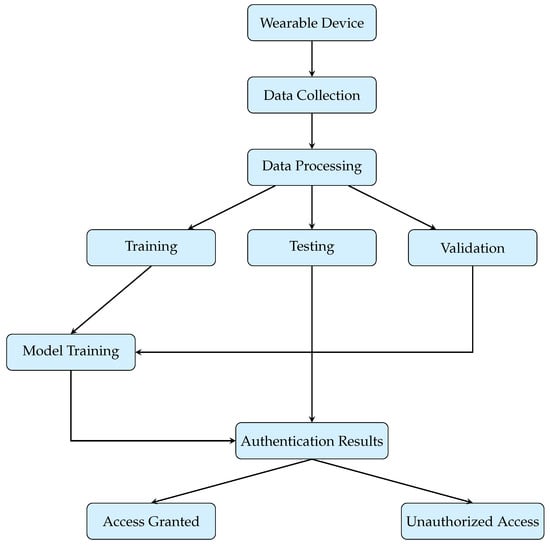
Figure 1.
High-level overview of the authentication process.
3.3. Data Collection and Synthetic Data Generation
The proposed framework relies on synthetic data for development and initial validation due to the challenges associated with obtaining real-world physiological datasets, which are often restricted by privacy, ethical, and access constraints. Synthetic data allows us to model vital signs under multiple conditions and generate sufficiently large datasets for algorithm training, feature combination, and system tuning. We acknowledge, however, that synthetic data cannot fully capture the complex, non-stationary dynamics of real bio-signals, including motion artifacts, individual variability, and sensor calibration issues. As such, the results obtained on synthetic data serve as a preliminary assessment, and validation on real-world data is necessary to fully evaluate the framework’s robustness and applicability.
The goal of the data collection phase is to create synthetic data to train the proposed framework’s ML module to determine a user’s identity based on their vital signs. To support identity verification across multiple activity levels, resting, walking, and running, we created synthetic vital sign data that serve as the foundation for robust authentication. The dataset is generated to include key physiological indicators such as HR, HRV, Skin Temperature, , and Breathing Rate. This diverse set of features ensures a comprehensive representation of the physiological characteristics required for accurate authentication across different user activity levels.
To simulate real-world conditions, Python-based algorithms were developed to generate synthetic data reflecting the natural patterns of and variability in vital sign measurements. These algorithms capture physiological parameters, individual differences, and activity-related fluctuations. To further enhance realism, noise was deliberately introduced into the generated signals, modeling real-world imperfections such as sensor inaccuracies. This addition of noise improves the robustness of training and validation by exposing the ML models to greater variability, thereby strengthening their generalization and resilience. Prior to introducing noise, the physiological basis of each vital sign was carefully studied using established research and scientific literature. For instance, resting heart rate was modeled between 60 and 100 beats per minute, while running heart rate ranged from 140 to 170 beats per minute.
The final dataset contains 80,000 rows and six feature attributes, with the first six variables used to predict the seventh target variable. A detailed summary of the dataset is provided in Table 2. Below is a summary of the vital sign ranges used during synthetic data generation.

Table 2.
Details of the Dataset.
- Breathing Rate: This feature measures the respiratory rate. At rest, it typically ranges from 12–20 breaths per minute. During walking, it increases to 22–35 breaths per minute, and during running, it rises to 40–60 breaths per minute [17,18].
- (HR): This measures the number of heartbeats per minute. At rest, the average HR is between 60–100 bpm, increasing to 110–130 bpm while walking, and 140–170 bpm while running [19,20].
- (HRV): HRV measures the variation in time between heartbeats. The average HRV at rest ranges from 65–105 ms. During walking, it decreases to 45–60 ms, and further drops to 10–40 ms during intense physical activities such as running [21].
- Skin Temperature: This refers to the temperature of the body’s outer surface. At rest, skin temperature typically ranges between 36.1–37.2 °C [22]. It increases to 37.5–38.5 °C during walking and reaches 38.7–40 °C during running [23].
- Oxygen Saturation (): This measures the percentage of oxygen in the blood. At rest, levels are generally between 97–100%. During walking, they may drop to 94–96%, and during running or jogging, to 90–93% [24].
3.4. Data Acquisition Process
To simulate realistic vital signs data for user authentication, synthetic data generation was performed using Python’s scikit-learn 1.7 library. Specifically, scikit-learn data generation utilities were employed to introduce controlled randomness and variability into the dataset, ensuring that the simulated signals reflected natural fluctuations observed in real-world measurements. The process involves creating personalized physiological profiles for four users: Charlie, Alice, Sara, and Bob, and simulating their vital signs on three levels of activity: resting, walking, and running. The primary goal was to emulate real-world variability while maintaining user-specific biometric patterns.
- User Profiles and Personalization Each user profile includes:
- -
- An activity preference, expressed as probabilities for selecting resting, walking, or running.
- -
- Personalized mean and variance values for six physiological signals: HR, HRV, skin temperature, , and breathing rate. These values vary across users and activity levels, introducing individual and contextual diversity into the data.
- Activity Simulation Using Probabilities:For each sample, the activity type is determined using weighted random selection based on the user’s predefined activity preference. This automated process ensures that users participate in activities at different frequencies, reflecting natural variability in daily behaviors.
- Correlated Features:HR, HRV, and Breathing Rate are tightly regulated by the autonomic nervous system (ANS) [25]. Physical activity elevates sympathetic activity, which increases HR and breathing rate, while parasympathetic withdrawal reduces HRV. To replicate these physiological relationships, a multivariate Gaussian method was applied to jointly model HR, HRV, and breathing rate using a predefined covariance matrix. These signals were modeled jointly using a predefined covariance matrix, capturing their physiological inter-dependencies across different activity levels (resting, walking, running). For example, an increase in HR during running is typically accompanied by a decrease in HRV and an elevated Breathing Rate. The covariance matrix was manually designed to reflect negative correlations between HR and HRV, and positive correlations between HR and Breathing Rate, based on general physiological trends. Activity-specific means for each user were dynamically extracted, and the synthetic samples were drawn from a multivariate normal distribution, enabling generation of coherent signal profiles that emulate real-world variability and co-variation. This data-level fusion strategy enhances the authenticity of synthetic data and provides downstream models with richer, context-aware inputs.
- Uncorrelated Features:While many physiological signals are interrelated, the degree of correlation varies significantly. HR, HRV, and Breathing Rate are directly controlled by the autonomic nervous system and tend to exhibit tight coupling, especially during changes in physical activity. In contrast, skin temperature and are influenced by a broader range of internal and external factors that do not always covary predictably with activity level or autonomic state [26,27]. Skin temperature included low-amplitude sinusoidal modulation and random environmental noise to simulate thermoregulation and external temperature effects. incorporated occasional drops (2–5%) during walking and running, occurring with low probability (2%), to reflect transient desaturation events common during exertion. Separating the correlated and uncorrelated generation methods ensures both physiological realism and computational efficiency in synthetic data creation.
- Data Post-processing and Labeling:For each user 20,000 samples were generated, totaling 80,000 rows across all users. Each row includes: User: Name (e.g., Bob, Sara), HR, Activity Level (1 = resting, 2 = walking, 3 = running), HRV, Skin Temperature, , and Breathing Rate. Figure 2 and Algorithm 1 present the full process of synthetic data generation, starting from user profile creation and extending to the finalized dataset.
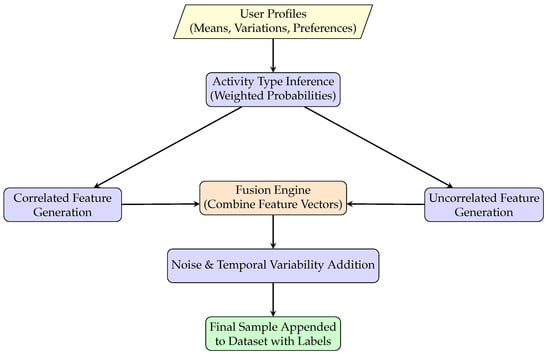 Figure 2. Data Acquisition Workflow.
Figure 2. Data Acquisition Workflow. - Enhanced Realism through Noise and Environmental SimulationTo better approximate real-world vital signs, controlled noise was applied to each physiological feature, capturing both natural biological variability and sensor-related imperfections. This strategy strengthens the robustness and generalizability of the authentication framework by training models on data distributions that more closely reflect real conditions. The noise models incorporated both random fluctuations and context-dependent variations, such as those induced by motion.
| Algorithm 1: Synthetic Data Generation |
 |
Table 3 summarizes the noise injection techniques applied to each physiological feature to replicate realistic variability and sensor-related artifacts. For heart rate (HR), Gaussian noise with a standard deviation of 3 was introduced to emulate short-term fluctuations that naturally occur due to stress, emotions, or environmental changes. HRV was perturbed using smaller Gaussian noise, reflecting the subtle fluctuations and measurement uncertainty inherent in HRV signals. Skin Temperature was modeled with a combination of sinusoidal and uniform noise, capturing both the rhythmic oscillations associated with thermoregulation and the random effects of ambient temperature changes. For , a conditional uniform drop was applied with a low probability during walking or running, simulating rare but realistic motion artifacts or brief deoxygenation events that occur during physical activity. Finally, breathing rate was perturbed using a sinusoidal function combined with Gaussian noise, which reproduced the natural rhythm of respiration alongside irregular variations from users and sensors. Collectively, these noise models were chosen to capture biological and environmental influences on vital signs, embedding controlled variability into the dataset to enhance both realism and the robustness of the authentication framework.

Table 3.
Summary of Noise Introduced to Simulate Physiological Signal Variability.
4. Dataset
4.1. Fusion Methods
In this study, an early fusion strategy was employed to integrate multiple physiological signals specifically HR, HRV, Skin Temperature, , Breathing Rate, and Activity Level. These features were merged at the feature level and represented as a single input vector for training the ML models.
Additionally, data-level fusion was incorporated during synthetic data generation. A multivariate normal distribution was applied to simulate the correlations among HR, HRV, and Breathing Rate, reflecting the natural physiological interdependence of these signals across different activity states (resting, walking, running). This correlation structure enabled the creation of more realistic and context-aware samples. These fusion strategies enhance authentication performance by capturing cross-feature interactions and providing a holistic representation of the user’s physiological profile. Late fusion or decision-level fusion techniques were not employed in this research.
4.2. Data Preprocessing
This section describes the preprocessing methods applied to prepare the dataset for analysis and ML tasks. Since raw data can contain issues such as missing values, inconsistencies, or unsuitable formats for modeling, preprocessing is an essential step to enhance data quality and model performance. The following techniques were implemented: data cleaning to resolve errors and fill in missing values, encoding of categorical variables to convert them into numerical format, and class balancing to address any skewed distributions in the target labels. These procedures ensure the dataset is clean, structured, and well-suited for effective and reliable modeling. The data preprocessing steps are illustrated in Figure 3 and Algorithm 2.
| Algorithm 2: Data Cleaning and Preprocessing |
 |
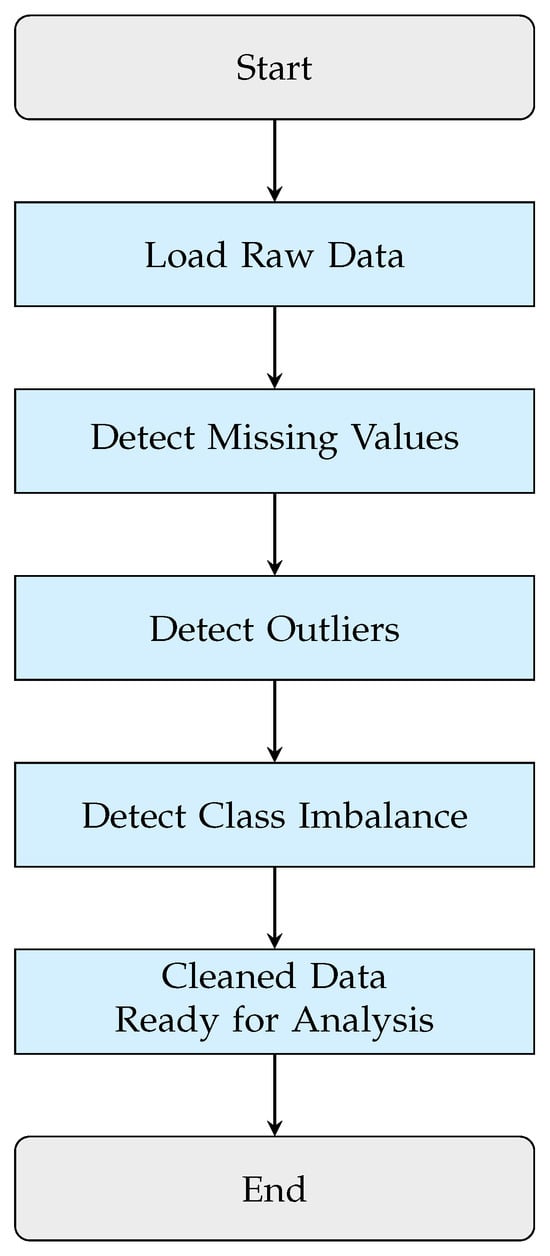
Figure 3.
Data Cleaning and Preprocessing Workflow.
4.2.1. Data Cleaning
Given that the dataset was synthetically generated, it inherently contained no missing values.To maintain uniformity across features and prepare the data for machine learning models, normalization was performed as an essential preprocessing step. All numerical variables, including HR, HRV, Breathing Rate, Skin Temperature, and , were scaled using MinMaxScaler to map their values within the range of 0 to 1. This scaling minimizes the influence of features with larger numerical ranges, supports faster model convergence, and enhances overall performance. Applying this transformation consistently across all features ensured that the dataset was cleaner, standardized, and more suitable for analysis and classification tasks.
4.2.2. Categorical
During preprocessing, categorical features were transformed into numerical values to ensure compatibility with machine learning algorithms, which generally require numerical inputs. The UserID, which represents individual users in the data set, was encoded in numeric labels so the models could effectively process identity information. Similarly, the Activity Level variable categorizing each instance as resting, walking, or running was encoded with integers (1 for resting, 2 for walking, and 3 for running). This conversion streamlined activity classification and facilitated efficient learning during both training and evaluation.
4.2.3. Data Balancing
The dataset maintained a realistic yet balanced distribution of activity types: walking comprised 30% of the data, resting 28%, and running 22%. These variations were deliberately introduced to mirror natural behavioral tendencies, where some individuals walk more often, while others rest or run more frequently. This variability strengthens the robustness of the model by exposing it to diverse activity patterns. To further ensure fair training across all users, balancing techniques were applied to mitigate differences in class distributions. Since unequal sample sizes per user could bias predictions toward majority groups, an equal number of synthetic samples was generated for each user across all activities. This approach guaranteed consistent representation, improved generalization, reduced overfitting, and ultimately enhanced both the fairness and accuracy of the authentication framework.
4.2.4. Data Splitting
To ensure robust model training and evaluation, the data set was divided into three distinct subsets: training (70%), validation (15%), and testing (15%). This method allows us to build effective models while reducing the likelihood of overfitting. The training set was used to fit the ML models and capture the underlying patterns in users’ vital signs across different activities. The validation set was employed to fine-tune model hyperparameters and guide model selection, helping to optimize performance without biasing the final evaluation. Finally, the testing set, which remained unseen during training and validation, was used to assess the model’s generalization capability. This three-way split provides a realistic assessment of model performance, closely simulating real-world deployment scenarios.
4.2.5. Feature Engineering
To enhance the accuracy of the authentication framework, an “Activity Level” feature was introduced during feature engineering. This feature assigns each record to the user’s current physical activity, allowing the model to adjust to natural variations in vital signs across different states. The activity levels were categorized as follows: 1 for resting, 2 for walking, and 3 for running. Incorporating this variable enabled the model to more effectively recognize the distinct vital sign patterns associated with each activity, thereby improving authentication performance across varied scenarios.
5. ML Framework
The following section outlines the rationale behind the selected ML models, presents the metrics used to evaluate their effectiveness, and reports the results obtained from the proposed framework.
5.1. ML Classifiers
In this study, the Scikit-learn (Sklearn) library was employed to implement a range of machine learning classifiers. Sklearn is a versatile Python library that supports tasks such as classification, clustering, and model selection. When selecting algorithms for user authentication based on vital signs, it is crucial to focus on models suited for classification tasks, capable of handling both continuous and categorical inputs, and effective in dealing with multi-dimensional features such as physiological signals. Guided by these considerations, several classifiers were selected to predict user identity from vital signs: Decision Tree, Random Forest, XGBoost Classifier, Gradient Boosting, and K-Nearest Neighbors (KNN), as shown in Algorithm 3.
- Decision Tree: The Decision Tree algorithm was selected for its interpretability and simplicity. It accommodates both numerical and categorical inputs, making it well-suited for vital sign data, which combines different physiological measures. Decision Trees capture nonlinear relationships and decision boundaries between users, reflecting their unique biometric patterns. Moreover, they provide an intuitive visualization of feature contributions to classification outcomes.
- Random Forest: Random Forest, an ensemble method based on multiple Decision Trees, was chosen for its robustness and ability to mitigate overfitting through bagging. By averaging predictions across multiple models, it achieves higher accuracy and stability, particularly when handling noisy or synthetic data. Its strong performance in classification tasks makes it a reliable choice for distinguishing users based on diverse vital sign inputs.
- XGBoost Classifier: XGBoost (Extreme Gradient Boosting) XGBoost (Extreme Gradient Boosting) was included for its efficiency, scalability, and strong predictive capabilities. This boosting technique incrementally improves weak learners and handles high-dimensional data effectively. Its built-in regularization reduces the risk of overfitting, which is especially beneficial when working with synthetic datasets and vital signs that may contain noise or correlations.
- Gradient Boosting: Gradient Boosting was included for its capability to construct strong classifiers by sequentially improving multiple weak learners. It effectively captures complex interactions among features, which is particularly useful when modeling physiological signals such as HR, HRV, and . Although it can be slower than some other methods, its high accuracy and ability to distinguish subtle differences between classes make it a strong choice for biometric authentication tasks.
- K-Nearest Neighbors (KNN): KNN was selected due to its simplicity and effectiveness in pattern recognition. The algorithm classifies new samples by comparing them to labeled examples based on feature similarity, which suits vital sign data where closeness in the feature space often reflects the user’s identity. KNN makes no assumptions about data distribution, making it especially appropriate for exploratory analysis with synthetic datasets.
| Algorithm 3: Model Training and Activity-Aware Authentication |
 |
5.2. ML Metrics
The performance of the machine learning models was assessed using several standard evaluation metrics, including accuracy, precision, recall, F1-score, Equal Error Rate (ERR), and the confusion matrix. These metrics were also examined across the three activity states, resting, walking, and running, to evaluate robustness under varying physiological conditions. Additionally, prediction and detection times were recorded to assess computational efficiency, an important factor for real-world deployment.
Accuracy serves as an overall indicator of a model’s classification capability. It is calculated as the ratio of correctly predicted instances (both true positives and true negatives) to the total number of predictions. Formally, accuracy can be expressed as:
where TP denotes true positives, TN denotes true negatives, FP denotes false positives, and FN denotes false negatives.
Precision quantifies the number of correctly predicted positive observations relative to the total predicted positives:
Recall (also known as sensitivity) measures the ability of the model to identify all relevant instances:
The F1-Score provides a balance between precision and recall, especially useful in imbalanced datasets, and is calculated as:
The Equal Error Rate (EER) is a critical metric used in classification and verification systems, such as biometrics. It represents the specific classification threshold at which the False Acceptance Rate (FAR) becomes exactly equal to the False Rejection Rate (FRR). The FAR measures the rate of non-target items incorrectly accepted (FPs), while the FRR measures the rate of target items incorrectly rejected (FNs). This balance point provides a single, robust measure of the system’s overall classification performance, where a lower EER reflects better distinguishing capabilities.
These metrics provide a comprehensive understanding of how well the model distinguishes between users and helps compare the performance of different classifiers in the context of vital signs–based authentication.
5.3. Tuning Strategies
To ensure clarity on model configuration, we briefly summarize common hyperparameter tuning strategies for the classifiers used in this study. While each algorithm allows for extensive tuning to optimize performance, the following parameters are typically adjusted during model development:”
- Decision Tree: Max depth, min samples per leaf, splitting criterion (Gini/Entropy), max features.
- Random Forest: Number of trees, max depth, min samples per leaf, max features, bootstrap sampling.
- XGBoost: Learning rate (eta), max depth, number of estimators, subsample ratio, colsample_bytree, regularization parameters (lambda, alpha).
- Gradient Boosting: Learning rate, number of estimators, max depth, min samples per leaf, subsample ratio.
- K-Nearest Neighbors: Number of neighbors (k), distance metric (Euclidean, Manhattan), weighting scheme (uniform/distance), algorithm for nearest neighbor search.
While these models support a range of hyperparameter tuning strategies to potentially improve performance, in this study we used the default parameters provided by standard libraries. This choice was made to maintain a consistent baseline for comparison across classifiers and because the primary goal was to evaluate the proposed framework using synthetic data rather than to optimize individual models. The default settings provide reasonable performance for exploratory analysis and initial validation of the framework.
5.4. ML Results
For robust evaluation and to prevent overfitting, the dataset was divided into training, validation, and test sets. The training set, comprising 70% of the data, was used to fit the machine learning models. The validation set, accounting for 15% of the data, was utilized to fine-tune hyperparameters and select the best-performing model during training. The remaining 15%, reserved as the test set, was employed to evaluate model performance on unseen data, providing a reliable measure of generalization. This separation ensures accurate assessment and supports the development of a dependable predictive tool.
Five ML models were evaluated: Decision Tree (DT), Random Forest (RF), XGBoost, Gradient Boosting, and K-Nearest Neighbors (KNN) using key metrics: accuracy, precision, recall, and F1 score. The average detection performance on the testing data is summarized in Table 4, and Figure 4. The precision, which indicates the proportion of true positives among all positive predictions, remained consistently high across all models. XGBoost and Gradient Boosting achieved a precision of 0.96, followed closely by RF and KNN with 0.95, and DT with 0.94. These results demonstrate the effectiveness of the models in minimizing false positives.

Table 4.
Models’ Performance on Testing Data.
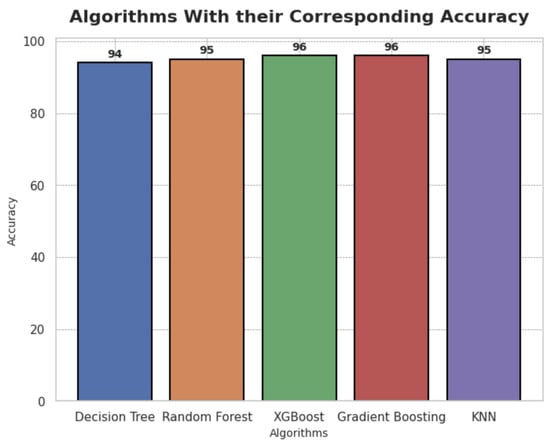
Figure 4.
Algorithms with their Corresponding Accuracy.
Recall, reflecting the models’ ability to correctly identify all true positives, showed a similar trend. XGBoost and Gradient Boosting reached 0.96, while RF and KNN scored 0.95. This indicates that the models were effective at reducing false negatives.
The F1 scores, which balance precision and recall, further highlight the robust performance of the models. XGBoost and Gradient Boosting achieved 0.96, while RF and KNN obtained 0.95, indicating slightly lower but still strong performance.
Overall accuracy was high for all models, with XGBoost and Gradient Boosting reaching 96%. These findings confirm that all evaluated models are highly effective at predicting user identity based on vital signs.
Performance was also evaluated separately for different user activities: walking, running, and resting. As shown in Table 5, Table 6 and Table 7, the models maintained consistently high performance across all activities. Accuracy, precision, recall, and F1-score remained above 0.93 for walking, slightly higher for running, and reached up to 0.98 for resting. XGBoost and Gradient Boosting consistently achieved the best results across activities, demonstrating their robustness in predicting user identity regardless of activity type.

Table 5.
Models’ Performance for Running Activity.

Table 6.
Models’ Performance for Walking Activity.

Table 7.
Models’ Performance for Resting Activity.
During the evaluation phase, confusion matrices were generated for each model. As shown in Figure 5, these matrices confirm the findings from the classification reports. In particular, XGBoost and Gradient Boosting demonstrated strong performance, exhibiting very low rates of both false positives and false negatives.
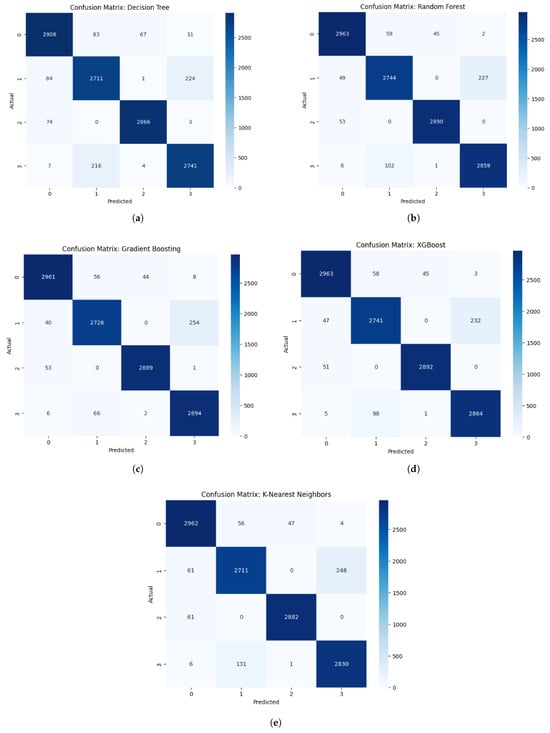
Figure 5.
Confusion matrices for the different models: (a) Decision Tree. (b) Random Forest, (c) Gradient Boosting, (d) XGBoost, (e) K-Nearest Neighbors.
The Receiver Operating Characteristic (ROC) curves for each user class indicate highly effective model performance as indicated in Figure 6. The Area Under the Curve (AUC) scores for the five models ranged from 0.995 to 0.998, demonstrating the model’s strong ability to accurately differentiate between individuals based on their vital signs. Furthermore, the Equal Error Rates (EERs) were very low, between 0.0215 and 0.0250 as indicated in Table 8. These results confirm the robustness and reliability of the proposed authentication framework across multiple user identities.
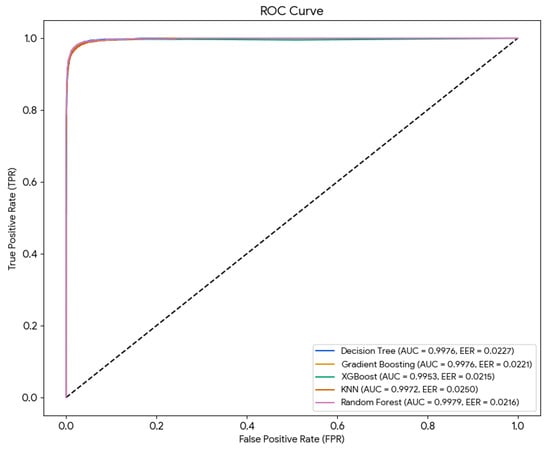
Figure 6.
Receiver Operating Characteristic (ROC).

Table 8.
Equal Error Rate for different Machine Learning Models.
Finally, we evaluated the effect of different types and levels of noise injection on model performance. Across all scenarios, the performance remained largely stable, indicating minimal sensitivity to the injected noise. This behavior likely reflects the limited complexity of the synthetic dataset, which does not fully capture the variability and challenges present in real-world physiological signals.
5.5. Detection and Prediction Time Evaluation
5.5.1. Training Time Evaluation
Training time refers to the duration required for the framework to collect and process physiological signals, such as HR, HRV, Skin Temperature, , and Breathing Rate, to confirm that a user is present and the data is ready for classification. Measuring training time is essential for evaluating the framework’s responsiveness and its feasibility for real-time authentication.
5.5.2. Prediction Time Evaluation
Prediction time represents the time taken by a trained ML model to analyze the extracted features and correctly identify the user. It spans from receiving the processed input to generating the predicted identity and serves as a measure of the model’s computational efficiency and scalability.
As shown in Table 9, the results indicate that XGBoost was the most efficient model in terms of both training and prediction times, highlighting its suitability for real-time authentication applications.

Table 9.
Average Training and Prediction Time (in seconds).
Among the five classifiers evaluated, Decision Tree, Random Forest, XGBoost, Gradient Boosting, and K-Nearest Neighbors, XGBoost proved to be the most well-rounded and efficient model for user authentication based on vital signs. It achieved a high classification accuracy of 96%, with consistently strong precision, recall, and F1-scores across all user classes. In addition to its robust predictive performance, XGBoost demonstrated low computational overhead, with a training time of 4.07 s and a prediction time of 0.13 s, making it highly suitable for real-time authentication scenarios.
While Random Forest delivered comparable accuracy and classification metrics, its training time was considerably longer (17.69 s), potentially limiting scalability. Gradient Boosting, despite high accuracy, required an even longer training duration (90.96 s), which may be impractical for dynamic or real-time systems. Decision Tree and KNN offered faster training or simpler implementation, but this came at the cost of lower accuracy or slower prediction. Therefore, XGBoost was selected as the optimal classifier, striking a balance between high performance and computational efficiency, making it ideal for continuous, real-time authentication.
5.6. Real-Time Simulation
To assess the framework’s ability to authenticate users using real-time physiological data, even when multiple individuals exhibit similar or identical vital sign values, two API requests were submitted, one for “Bob” and another for “Charlie”with identical inputs: HR, HRV, Skin Temperature, , and Breathing Rate. The objective was to determine whether the model could distinguish users based on the unique physiological patterns learned during training. The contrasting outcomes, access denied for Bob and granted for Charlie, demonstrate that the model relies on user-specific physiological signatures rather than just raw vital sign values.
Figure 7 and Figure 8 illustrate functional examples of a vital signs–based user identification framework using physiological data inputs. In Figure 7, a user’s five vital signs were tested and access was granted. In contrast, Figure 8 shows a case in which access was denied because the user’s vital signs did not match the authenticated profile. This evaluation confirms that the authentication framework performs contextual biometric recognition, which is essential for ensuring both high security and accuracy in real-world applications.
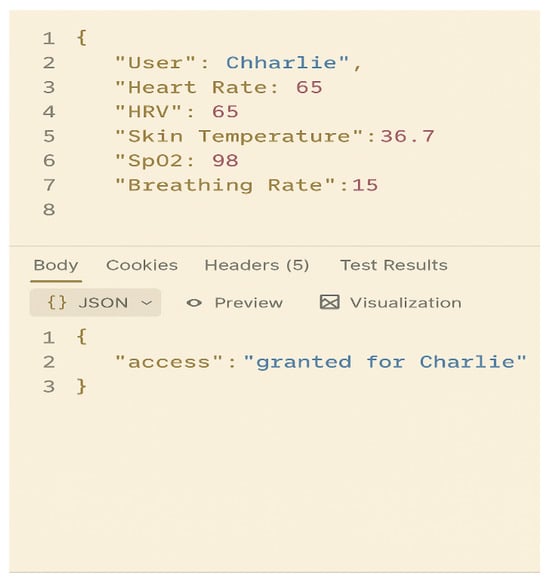
Figure 7.
Real-Time API Authentication Result (Access Granted).
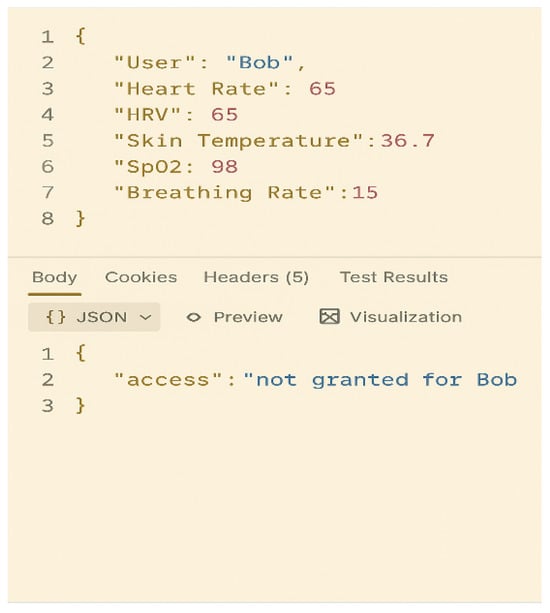
Figure 8.
Real-Time API Authentication Result (Access Denied).
6. Discussion
6.1. Security
Although the previous subsections focused on ML performance, these results directly translate into the security strength of the proposed continuous authentication framework. In biometric authentication systems, security depends on the ability of the classifier to correctly recognize legitimate users and reliably reject impostors. The experimental results demonstrate that the proposed ML-driven vital-signs authentication mechanism provides strong security guarantees across multiple dimensions.
- Resistance to Impersonation Attacks (False Acceptance Control) Models with high precision minimize false positives, which correspond to unauthorized users being incorrectly accepted. XGBoost and Gradient Boosting achieved precision = 0.96, RF and KNN achieved 0.95. These values indicate a very low probability that an attacker with different physiological patterns could be falsely authenticated. The confusion-matrix plots further confirm that false-positive cells remain extremely small across all models, demonstrating strong protection against impersonation attempts.
- Protection Against Session Hijacking (Continuous Verification) Because authentication occurs continuously in the background, even if an attacker temporarily gains physical access to the device, the system continuously analyzes incoming physiological data. The high recall (0.95–0.96) ensures that the system reliably maintains the session only for the legitimate user and promptly detects deviations if the physiological patterns suddenly change (e.g., attacker replaces wearable).
- Robustness Across User Activities (Adaptive Security) Vital signs fluctuate with activity levels. If a model fails under motion, an attacker could exploit “activity windows” where the signal is degraded. The results demonstrate that the framework maintains high accuracy during resting, walking, and running, confirming that the authentication remains secure even under dynamic, real-world conditions.
- Strong Distinguishability Between Users (High AUC Values) The ROC analysis showed AUC values of: 1.00 for three users and 0.99 for one user. These values demonstrate exceptional separability between classes, meaning the framework can effectively distinguish physiological patterns even when vital-sign ranges overlap. This is a critical property for preventing targeted spoofing attacks.
- Low Latency and Real-Time Security Enforcement Security mechanisms must not introduce delays that attackers can exploit. XGBoost delivered the best trade-off: Training time: 4.06 s and Prediction time: 0.129 s. This ensures that authentication decisions occur nearly instantly, enabling real-time continuous verification. The system can revoke access immediately when abnormal or unauthorized signals are detected.
- Security Validation Through Real-Time Simulation The real-time API test using identical vital-sign values for two different individuals (“Bob” and “Charlie”) shows that the system does not rely solely on raw physiological values. Instead, authentication is based on the learned temporal and contextual biometrics, making simple spoofing or value replication ineffective.
The combined findings indicate that the proposed framework: Minimizes impersonation risks through extremely low false acceptance rates, maintains identity verification even during physical activity, responds in real time to potential intrusion, provides biometric separation strong enough to resist targeted spoofing, and ensures stable performance across multiple conditions. These characteristics collectively demonstrate that the vital-signs–based continuous authentication mechanism provides strong, practical, and scalable security suitable for real-world deployment.
6.2. Potential Attack Vectors
Although the proposed framework demonstrates strong performance in continuous authentication using physiological signals, it is important to consider potential security threats. Attack vectors such as spoofing, replay attacks, or sensor manipulation could compromise system integrity if an adversary attempts to imitate or replay a user’s physiological patterns. For instance, spoofing may involve generating signals that mimic the user’s baseline vital signs, while replay attacks could reuse previously recorded data. To mitigate these risks, multiple strategies can be employed. Liveness detection and temporal consistency checks can help ensure that the signals are coming from a live user in real time. Multi-modal verification, which leverages several physiological signals simultaneously, increases robustness since an attacker would need to replicate all signals accurately. Additionally, anomaly detection mechanisms can identify unusual patterns or abrupt deviations from the user’s typical physiological behavior. Combining these techniques can significantly strengthen the security of the authentication system, making it more resilient to potential attacks while maintaining seamless and continuous monitoring.
6.3. Comparison with the Discussed Related Works
Table 10 provides a comparative evaluation of our proposed authentication framework against existing frameworks, focusing specifically on three essential features: non-interactive operation, continuous verification, and flexibility across different user activities. While studies such as [10,11,12,13,15] successfully provide non-interactive authentication, they lack flexibility, limiting their ability to adapt to varying physical states or dynamic real-world conditions. Similarly, although many of these works implement continuous authentication [10,11,12,13]), they often neglect the need for flexibility. On the other hand, studies like [14,16] lack both non-interactivity and flexibility, offering only partial solutions. Notably, none of the compared studies manage to incorporate all three essential criteria simultaneously. In contrast, our proposed framework successfully integrates non-interactive, continuous, and flexible authentication, setting a new benchmark for usability and robustness. This comprehensive approach ensures secure and seamless user verification across different activities (resting, walking, and running), without requiring manual user interaction or compromising adaptability, highlighting a significant advancement in the field of motion-based user authentication.

Table 10.
Comparison with the discussed works, where ✓: Feature Supported, and ✗: Not Supported.
6.4. Quantitative Comparison with Related Works
Table 11 presents a detailed quantitative comparison of our proposed framework with several existing studies, focusing on three key metrics: the number of authentication factors used, authentication type, and accuracy.

Table 11.
Comparative Quantitative Analysis.
Most prior works focus primarily on accuracy, often at the expense of flexibility and seamless real-time integration. For instance, study [12] achieves perfect accuracy (100%) but relies on only one factor, which limits its robustness and adaptability. Similarly, refs. [10,15] reach high accuracy levels of 99.15% and 95% respectively, yet each uses only one factor, indicating limited depth in authentication criteria. Studies [11,13] use two factors and demonstrate decent accuracy (93.7% and 97.1%), which illustrates a trade-off between complexity and performance. Nevertheless, these approaches still fail to fully address the challenges of real-time flexibility across different user activities. Studies [14,16] both employ non-continuous authentication, with [14] showing the lowest accuracy (90.6%), highlighting the limitations of discontinuous verification methods.
In contrast, the proposed framework utilizes five key authentication factors derived from vital signs, the highest among the compared studies, while achieving a competitive accuracy of 96%. It also provides continuous, seamless authentication across various activities, including resting, walking, and running, thereby enhancing both security and user convenience. This approach demonstrates a balanced and holistic strategy, addressing not only accuracy but also real-world adaptability, usability, and robustness, which are essential for modern biometric systems.
7. Conclusions
This research introduces a zero-effort user authentication framework that continuously and passively verifies identity through vital signs during motion. The framework addresses a critical challenge in modern authentication: ensuring strong security while preserving a seamless user experience. By leveraging physiological signals, Heart Rate HR, Heart Rate Variability HRV, Skin Temperature, , and Breathing Rate, the system provides a non-intrusive method capable of functioning effectively across daily activities such as resting, walking, and running.
A key contribution of this study is the demonstration that vital signs, when processed through machine learning ML algorithms, can serve as reliable biometric identifiers. The framework achieved high accuracy rates, 96% with XGBoost and Gradient Boosting, 95% with Random Forest and K-Nearest Neighbors (KNNs), and 94% with Decision Tree algorithms. These results highlight its ability to accurately recognize users across different physical states, confirming that individual physiological patterns remain sufficiently distinct even under varying activity levels. The framework’s defining feature is its zero-effort design; users are not required to perform explicit actions such as entering passwords, using PINs, or presenting biometric scans. Instead, authentication occurs continuously and passively, reducing the risk of human error, improving usability, and strengthening security. Another important aspect of this research is the use of synthetic data generation to simulate physiological variability under different activity conditions. By incorporating controlled noise and variability, the synthetic dataset closely reflected real-world dynamics, allowing the models to achieve robust and generalizable performance in simulated scenarios. This approach ensured adaptability while laying the groundwork for future real-world applications. Overall, the findings suggest that vital sign-based authentication offers a secure, flexible, and practical alternative to traditional static methods. Its ability to adapt to users’ physical states makes it well-suited for domains where continuous and unobtrusive verification is critical.
While the study’s objectives have largely been met, several opportunities remain for future enhancement. Integrating real-world physiological data is an essential next step to validate the framework’s practical effectiveness and refine model generalization. Additionally, exploring deep learning, such as through recurrent neural networks (RNNs), convolutional neural networks (CNNs), and attention-based architectures, may further improve performance by capturing temporal dependencies and complex signal patterns, particularly for long-term authentication and anomaly detection. In conclusion, this work advances the field of user authentication by introducing a continuous, zero-effort framework based on vital signs that demonstrates both accuracy and adaptability. With continued progress, especially through the incorporation of real-world data and the application of advanced modeling techniques, this approach holds strong potential to evolve into a widely adopted solution for secure and seamless identity verification.
Author Contributions
Conceptualization, R.A. and E.S.-B.; methodology, R.A. and E.S.-B.; software, S.A.-D.Q.; validation, R.A., E.S.-B. and S.A.-D.Q.; formal analysis, R.A. and S.A.-D.Q.; investigation, R.A.; resources, R.A.; data curation, S.A.-D.Q.; writing—original draft preparation, R.A. and E.S.-B.; writing—review and editing, R.A., E.S.-B. and S.A.-D.Q.; visualization, R.A. and S.A.-D.Q.; supervision, E.S.-B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The dataset presented in this study is available on request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Hamad, S.A.; Sheng, Q.Z.; Zhang, W.E.; Nepal, S. Realizing an Internet of Secure Things: A Survey on Issues and Enabling Technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1372–1391. [Google Scholar] [CrossRef]
- Shah, S.W.; Kanhere, S.S. Recent Trends in User Authentication—A Survey. IEEE Access 2019, 7, 112505–112519. [Google Scholar] [CrossRef]
- Xie, N.; Li, Z.; Tan, H. A Survey of Physical-Layer Authentication in Wireless Communications. IEEE Commun. Surv. Tutor. 2021, 23, 282–310. [Google Scholar] [CrossRef]
- Caballero-Hernández, H.; Gil-Antonio, L.; Lopez-Gonzalez, E.; Antonio-Velazquez, J.A. A brief review about biometrics systems in modern context. Int. J. Adv. Res. Comput. Sci. 2022, 13, 5. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Sennersten, C.; Ahmad, A. Towards Cognitive Authentication for Smart Healthcare Applications. Sensors 2022, 22, 2101. [Google Scholar] [CrossRef] [PubMed]
- Soni, P.; Pradhan, J.; Pal, A.K.; Islam, S.H. Cybersecurity Attack-resilience Authentication Mechanism for Intelligent Healthcare System. IEEE Trans. Ind. Inform. 2022, 19, 830–840. [Google Scholar] [CrossRef]
- Ammour, B.; Boubchir, L.; Bouden, T.; Ramdani, M. Face–iris multimodal biometric identification system. Electronics 2020, 9, 85. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Awad, A.I.; van de Beek, J.; Nikolakopoulos, G. Intelligent authentication of 5G healthcare devices: A survey. Internet Things 2022, 20, 100610. [Google Scholar] [CrossRef]
- Soni, M.; Singh, D.K. Privacy-preserving secure and low-cost medical data communication scheme for smart healthcare. Comput. Commun. 2022, 194, 292–300. [Google Scholar] [CrossRef]
- Wang, Y.; Gu, T.; Luan, T.H.; Lyu, M.; Li, Y. HeartPrint: Exploring a Heartbeat-Based Multiuser Authentication With Single mmWave Radar. IEEE Internet Things J. 2022, 9, 25324–25336. [Google Scholar] [CrossRef]
- Peng, J.; Hao, Z.; Zhang, Z.; Wang, R.; Li, M.; Dang, X. Utter Innocence: Contactless Authentication Method Based on Physiological Signals. IEEE Sens. J. 2024, 24, 7740–7751. [Google Scholar] [CrossRef]
- Islam, S.M.M.; Rahman, A.; Prasad, N.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication System using a Support Vector Machine (SVM) on Radar Respiration Measurements. In Proceedings of the 2019 93rd ARFTG Microwave Measurement Conference (ARFTG), Boston, MA, USA, 7 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Ning, J.; Xie, L.; Wang, C.; Bu, Y.; Xu, F.; Zhou, D.W.; Lu, S.; Ye, B. RF-Badge: Vital Sign-Based Authentication via RFID Tag Array on Badges. IEEE Trans. Mob. Comput. 2023, 22, 1170–1184. [Google Scholar] [CrossRef]
- Wang, W.; Vette, M.; Wang, Q.; Yang, J.; Zuniga, M. CamPressID: Optimizing Camera Configuration and Finger Pressure for Biometric Authentication. In Proceedings of the 2022 IEEE 19th International Conference on Mobile Ad Hoc and Smart Systems (MASS), Denver, CO, USA, 19–23 October 2022; pp. 229–235. [Google Scholar] [CrossRef]
- Wang, G.; Shanker, S.; Nag, A.; Lian, Y.; John, D. ECG biometric authentication using self-supervised learning for IoT edge sensors. IEEE J. Biomed. Health Inform. 2024, 28, 6606–6618. [Google Scholar] [CrossRef] [PubMed]
- Cheung, W.; Vhaduri, S. Continuous Authentication of Wearable Device Users from Heart Rate, Gait, and Breathing Data. In Proceedings of the 2020 8th IEEE RAS/EMBS International Conference for Biomedical Robotics and Biomechatronics (BioRob), New York, NY, USA, 29 November–1 December 2020; pp. 587–592. [Google Scholar]
- Cruz, J.C.D.; Javier, F.A.C.; Puyat, C.C.; Ibera, J.C. Non-invasive heart and respiratory rates extraction using frequency-modulated continuous-wave radar. In Proceedings of the 2021 IEEE 4th International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 13–15 August 2021; pp. 382–386. [Google Scholar]
- Romano, C.; Nicolò, A.; Innocenti, L.; Bravi, M.; Miccinilli, S.; Sterzi, S.; Sacchetti, M.; Schena, E.; Massaroni, C. Respiratory Rate Estimation during Walking and Running Using Breathing Sounds Recorded with a Microphone. Biosensors 2023, 13, 637. [Google Scholar] [CrossRef]
- Wehler, D.; Jelinek, H.F.; Gronau, A.; Wessel, N.; Kraemer, J.F.; Krones, R.; Penzel, T. Reliability of heart-rate-variability features derived from ultra-short ECG recordings and their validity in the assessment of cardiac autonomic neuropathy. Biomed. Signal Process. Control 2021, 68, 102651. [Google Scholar] [CrossRef]
- Aldumiji, N.; Khan, E. Fingerprint and location based multifactor authentication for mobile applications. Int. J. Eng. Technol. 2019, 8, 193–204. [Google Scholar]
- Abellán-Aynés, O.; López-Plaza, D.; Alacid, F.; Naranjo-Orellana, J.; Manonelles, P. Recovery of Heart Rate Variability After Exercise Under Hot Conditions: The Effect of Relative Humidity. Wilderness Environ. Med. 2019, 30, 260–267. [Google Scholar] [CrossRef]
- Sapra, A.; Malik, A.; Bhandari, P. Vital Sign Assessment; StatPearls Publishing: Treasure Island, FL, USA, 2023. [Google Scholar]
- Neves, E.B.; Cunha, R.M.; Rosa, C.; Antunes, N.S.; Felisberto, I.M.V.; Vilaça-Alves, J.; Reis, V.M. Correlation between skin temperature and heart rate during exercise and recovery, and the influence of body position in these variables in untrained women. Infrared Phys. Technol. 2016, 75, 70–76. [Google Scholar] [CrossRef]
- Lee, J.; Park, C. Remote SpO2 Estimation using End-to-End CNN Model. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Yeosu, Republic of Korea, 26–28 October 2022; pp. 1–3. [Google Scholar] [CrossRef]
- White, D.W.; Raven, P.B. Autonomic neural control of heart rate during dynamic exercise: Revisited. J. Physiol. 2014, 592, 2491–2500. [Google Scholar] [CrossRef]
- Soo, J.; Girard, O.; Ihsan, M.; Fairchild, T. The Use of the SpO2 to FiO2 Ratio to Individualize the Hypoxic Dose in Sport Science, Exercise, and Health Settings. Front. Physiol. 2020, 11, 570472. [Google Scholar] [CrossRef]
- Refinetti, R. Circadian rhythmicity of body temperature and metabolism. Temperature 2020, 7, 321–362. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.