Seamless Vital Signs-Based Continuous Authentication Using Machine Learning
Abstract
1. Introduction
- How can vital sign data HR, HRV, Skin Temperature, , and Breathing Rate be effectively utilized for continuous, zero-effort biometric authentication?
- Which ML algorithm achieves the highest performance in accurately predicting user identity using vital signs?
- How does the framework perform under different user activities (e.g., resting, walking, running)?
- Can a vital signs-based authentication framework provide usability, reliability, and flexibility for real-world applications?
2. Related Work
3. The Proposed Framework
3.1. Real-World Application and User Interaction
3.2. The Proposed Framework Features
3.2.1. Non-Interactive
3.2.2. Continuous Authentication
3.2.3. Flexibility
3.3. Data Collection and Synthetic Data Generation
- (HRV): HRV measures the variation in time between heartbeats. The average HRV at rest ranges from 65–105 ms. During walking, it decreases to 45–60 ms, and further drops to 10–40 ms during intense physical activities such as running [21].
- Oxygen Saturation (): This measures the percentage of oxygen in the blood. At rest, levels are generally between 97–100%. During walking, they may drop to 94–96%, and during running or jogging, to 90–93% [24].
3.4. Data Acquisition Process
- User Profiles and Personalization Each user profile includes:
- -
- An activity preference, expressed as probabilities for selecting resting, walking, or running.
- -
- Personalized mean and variance values for six physiological signals: HR, HRV, skin temperature, , and breathing rate. These values vary across users and activity levels, introducing individual and contextual diversity into the data.
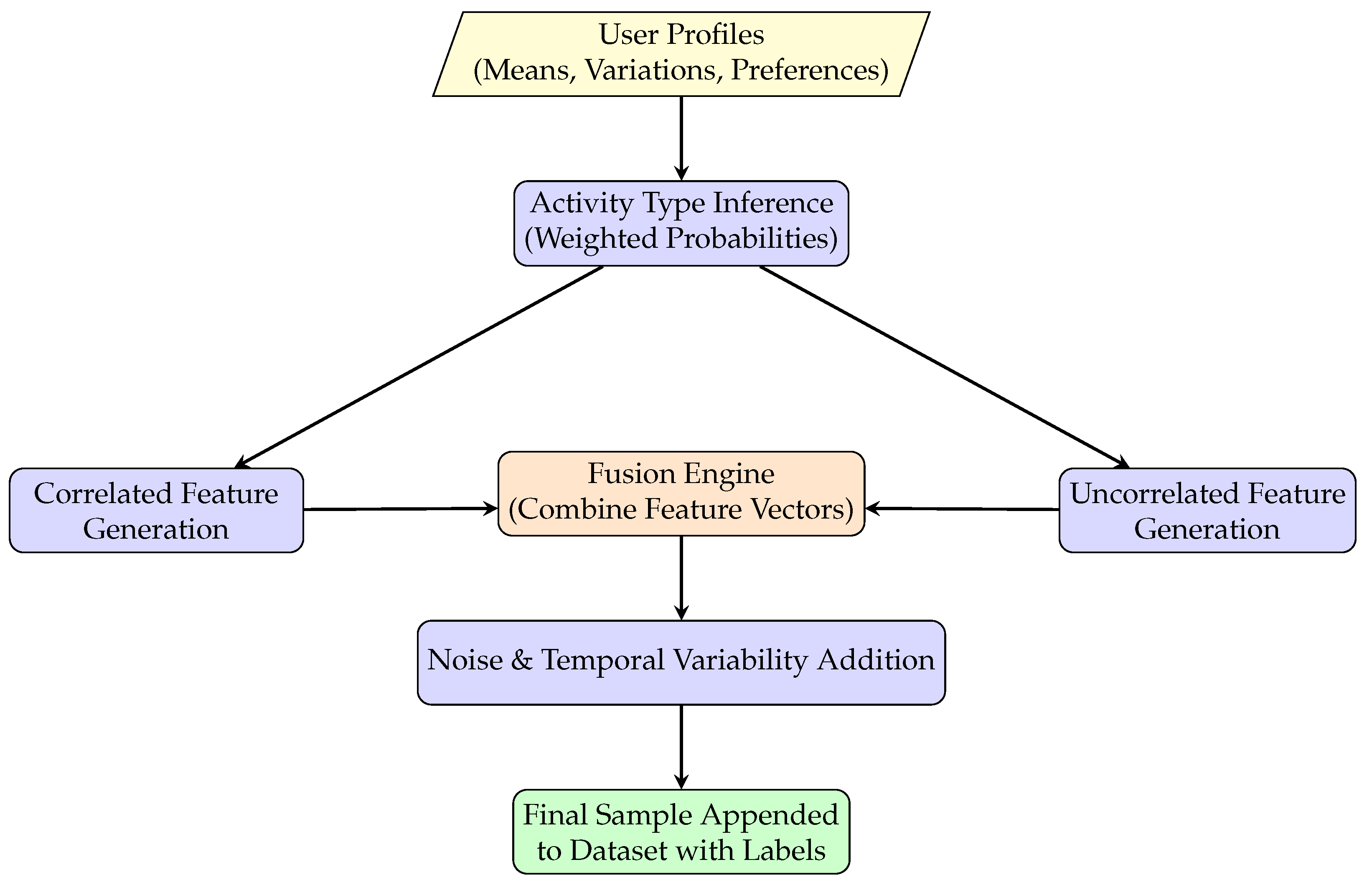
- Activity Simulation Using Probabilities:For each sample, the activity type is determined using weighted random selection based on the user’s predefined activity preference. This automated process ensures that users participate in activities at different frequencies, reflecting natural variability in daily behaviors.
- Correlated Features:HR, HRV, and Breathing Rate are tightly regulated by the autonomic nervous system (ANS) [25]. Physical activity elevates sympathetic activity, which increases HR and breathing rate, while parasympathetic withdrawal reduces HRV. To replicate these physiological relationships, a multivariate Gaussian method was applied to jointly model HR, HRV, and breathing rate using a predefined covariance matrix. These signals were modeled jointly using a predefined covariance matrix, capturing their physiological inter-dependencies across different activity levels (resting, walking, running). For example, an increase in HR during running is typically accompanied by a decrease in HRV and an elevated Breathing Rate. The covariance matrix was manually designed to reflect negative correlations between HR and HRV, and positive correlations between HR and Breathing Rate, based on general physiological trends. Activity-specific means for each user were dynamically extracted, and the synthetic samples were drawn from a multivariate normal distribution, enabling generation of coherent signal profiles that emulate real-world variability and co-variation. This data-level fusion strategy enhances the authenticity of synthetic data and provides downstream models with richer, context-aware inputs.
- Uncorrelated Features:While many physiological signals are interrelated, the degree of correlation varies significantly. HR, HRV, and Breathing Rate are directly controlled by the autonomic nervous system and tend to exhibit tight coupling, especially during changes in physical activity. In contrast, skin temperature and are influenced by a broader range of internal and external factors that do not always covary predictably with activity level or autonomic state [26,27]. Skin temperature included low-amplitude sinusoidal modulation and random environmental noise to simulate thermoregulation and external temperature effects. incorporated occasional drops (2–5%) during walking and running, occurring with low probability (2%), to reflect transient desaturation events common during exertion. Separating the correlated and uncorrelated generation methods ensures both physiological realism and computational efficiency in synthetic data creation.
- Data Post-processing and Labeling:For each user 20,000 samples were generated, totaling 80,000 rows across all users. Each row includes: User: Name (e.g., Bob, Sara), HR, Activity Level (1 = resting, 2 = walking, 3 = running), HRV, Skin Temperature, , and Breathing Rate. Figure 2 and Algorithm 1 present the full process of synthetic data generation, starting from user profile creation and extending to the finalized dataset.
- Enhanced Realism through Noise and Environmental SimulationTo better approximate real-world vital signs, controlled noise was applied to each physiological feature, capturing both natural biological variability and sensor-related imperfections. This strategy strengthens the robustness and generalizability of the authentication framework by training models on data distributions that more closely reflect real conditions. The noise models incorporated both random fluctuations and context-dependent variations, such as those induced by motion.
| Algorithm 1: Synthetic Data Generation |
 |
4. Dataset
4.1. Fusion Methods
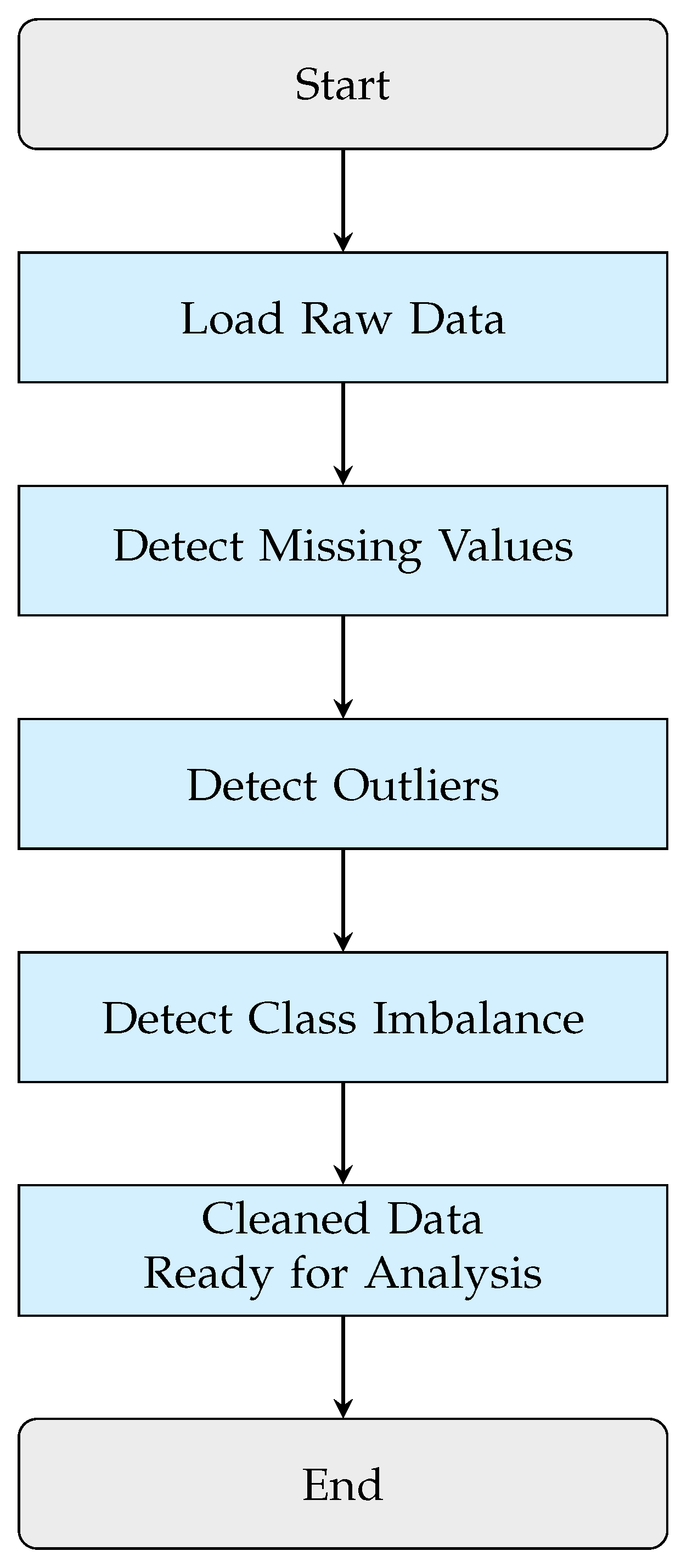
4.2. Data Preprocessing
| Algorithm 2: Data Cleaning and Preprocessing |
 |
4.2.1. Data Cleaning
4.2.2. Categorical
4.2.3. Data Balancing
4.2.4. Data Splitting
4.2.5. Feature Engineering
5. ML Framework
5.1. ML Classifiers
- Decision Tree: The Decision Tree algorithm was selected for its interpretability and simplicity. It accommodates both numerical and categorical inputs, making it well-suited for vital sign data, which combines different physiological measures. Decision Trees capture nonlinear relationships and decision boundaries between users, reflecting their unique biometric patterns. Moreover, they provide an intuitive visualization of feature contributions to classification outcomes.
- Random Forest: Random Forest, an ensemble method based on multiple Decision Trees, was chosen for its robustness and ability to mitigate overfitting through bagging. By averaging predictions across multiple models, it achieves higher accuracy and stability, particularly when handling noisy or synthetic data. Its strong performance in classification tasks makes it a reliable choice for distinguishing users based on diverse vital sign inputs.
- XGBoost Classifier: XGBoost (Extreme Gradient Boosting) XGBoost (Extreme Gradient Boosting) was included for its efficiency, scalability, and strong predictive capabilities. This boosting technique incrementally improves weak learners and handles high-dimensional data effectively. Its built-in regularization reduces the risk of overfitting, which is especially beneficial when working with synthetic datasets and vital signs that may contain noise or correlations.
- Gradient Boosting: Gradient Boosting was included for its capability to construct strong classifiers by sequentially improving multiple weak learners. It effectively captures complex interactions among features, which is particularly useful when modeling physiological signals such as HR, HRV, and . Although it can be slower than some other methods, its high accuracy and ability to distinguish subtle differences between classes make it a strong choice for biometric authentication tasks.
- K-Nearest Neighbors (KNN): KNN was selected due to its simplicity and effectiveness in pattern recognition. The algorithm classifies new samples by comparing them to labeled examples based on feature similarity, which suits vital sign data where closeness in the feature space often reflects the user’s identity. KNN makes no assumptions about data distribution, making it especially appropriate for exploratory analysis with synthetic datasets.
| Algorithm 3: Model Training and Activity-Aware Authentication |
 |
5.2. ML Metrics
5.3. Tuning Strategies
- Decision Tree: Max depth, min samples per leaf, splitting criterion (Gini/Entropy), max features.
- Random Forest: Number of trees, max depth, min samples per leaf, max features, bootstrap sampling.
- XGBoost: Learning rate (eta), max depth, number of estimators, subsample ratio, colsample_bytree, regularization parameters (lambda, alpha).
- Gradient Boosting: Learning rate, number of estimators, max depth, min samples per leaf, subsample ratio.
- K-Nearest Neighbors: Number of neighbors (k), distance metric (Euclidean, Manhattan), weighting scheme (uniform/distance), algorithm for nearest neighbor search.
5.4. ML Results
5.5. Detection and Prediction Time Evaluation
5.5.1. Training Time Evaluation
5.5.2. Prediction Time Evaluation
5.6. Real-Time Simulation
6. Discussion
6.1. Security
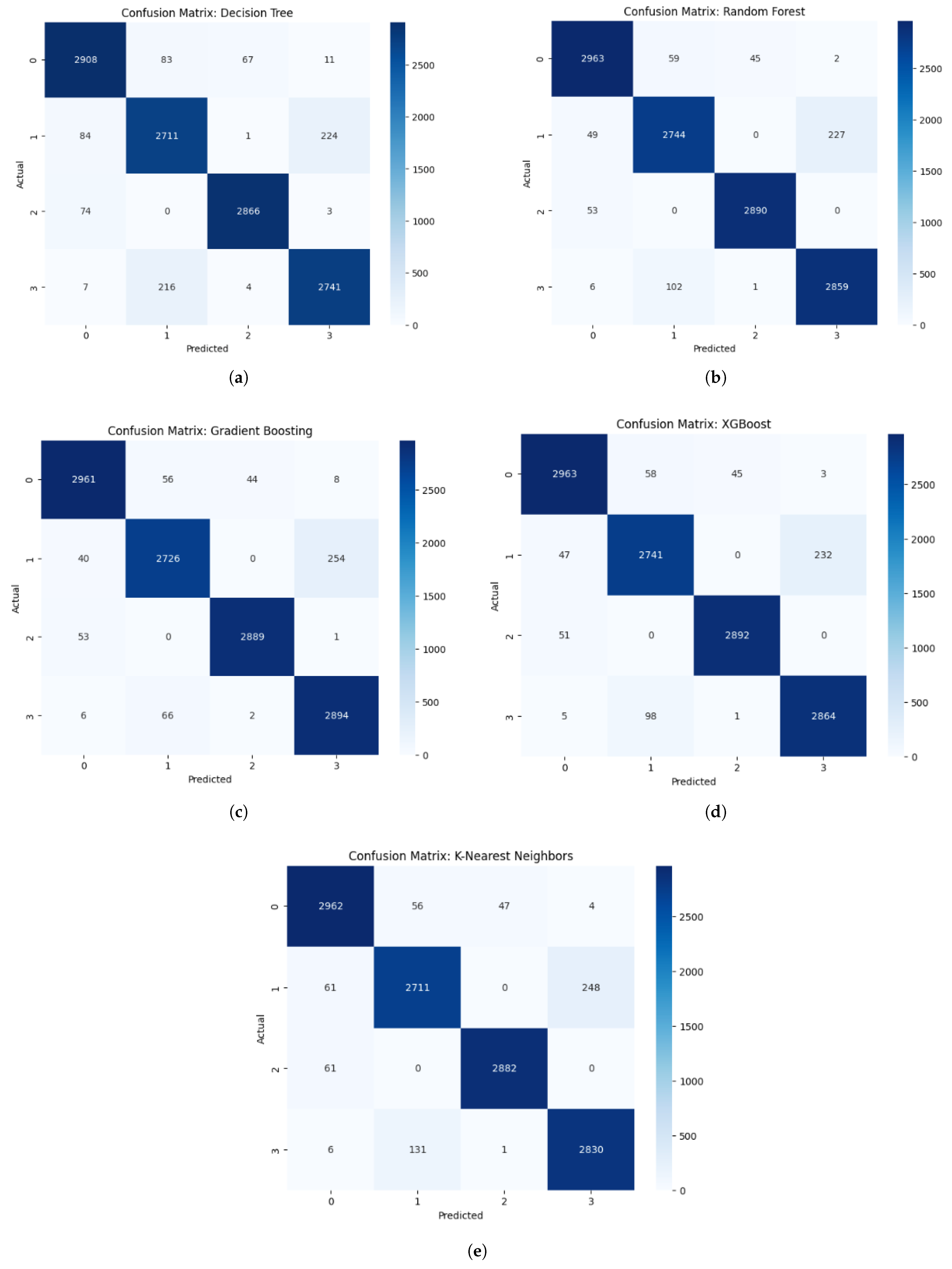
- Resistance to Impersonation Attacks (False Acceptance Control) Models with high precision minimize false positives, which correspond to unauthorized users being incorrectly accepted. XGBoost and Gradient Boosting achieved precision = 0.96, RF and KNN achieved 0.95. These values indicate a very low probability that an attacker with different physiological patterns could be falsely authenticated. The confusion-matrix plots further confirm that false-positive cells remain extremely small across all models, demonstrating strong protection against impersonation attempts.
- Protection Against Session Hijacking (Continuous Verification) Because authentication occurs continuously in the background, even if an attacker temporarily gains physical access to the device, the system continuously analyzes incoming physiological data. The high recall (0.95–0.96) ensures that the system reliably maintains the session only for the legitimate user and promptly detects deviations if the physiological patterns suddenly change (e.g., attacker replaces wearable).
- Robustness Across User Activities (Adaptive Security) Vital signs fluctuate with activity levels. If a model fails under motion, an attacker could exploit “activity windows” where the signal is degraded. The results demonstrate that the framework maintains high accuracy during resting, walking, and running, confirming that the authentication remains secure even under dynamic, real-world conditions.
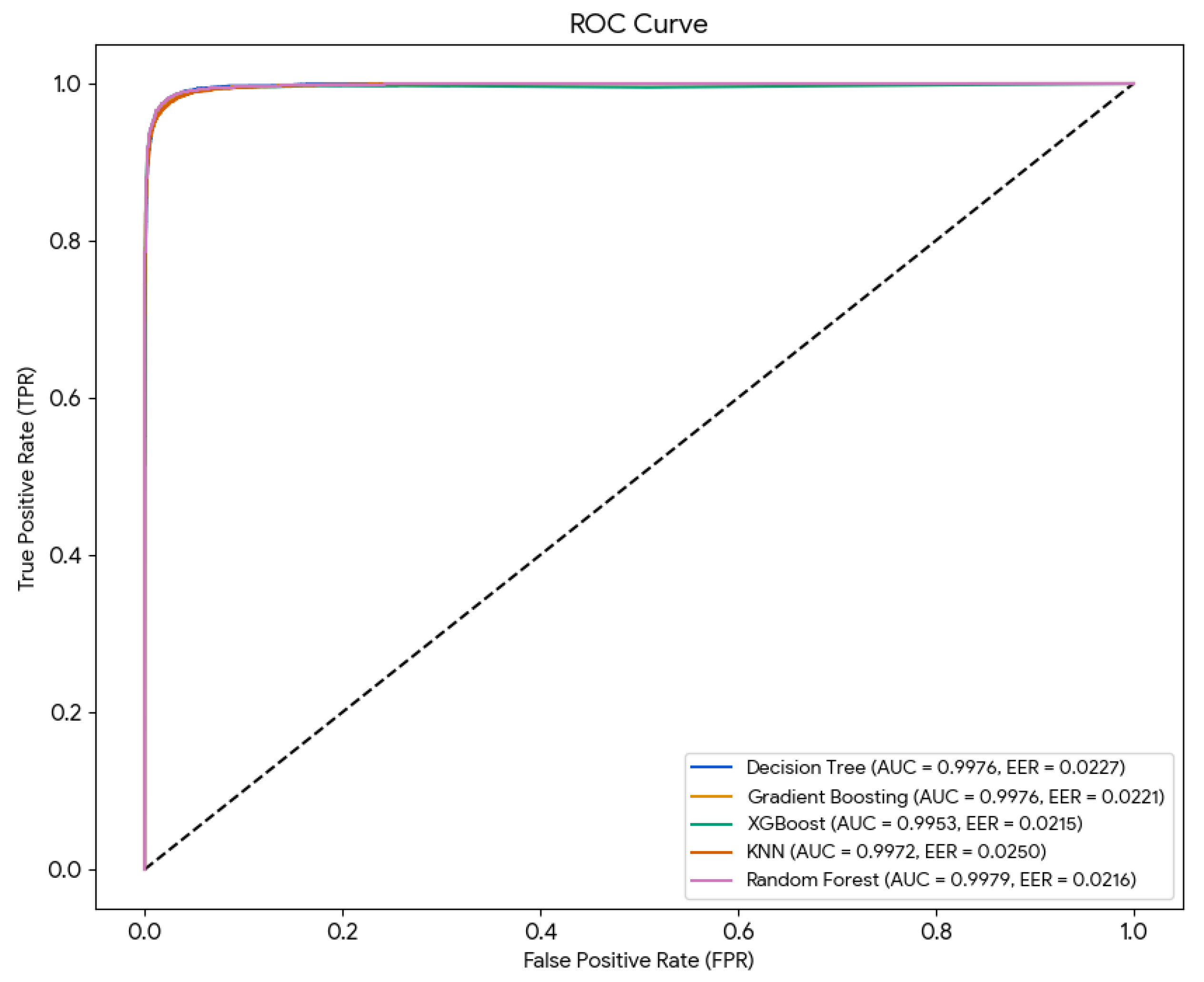
- Strong Distinguishability Between Users (High AUC Values) The ROC analysis showed AUC values of: 1.00 for three users and 0.99 for one user. These values demonstrate exceptional separability between classes, meaning the framework can effectively distinguish physiological patterns even when vital-sign ranges overlap. This is a critical property for preventing targeted spoofing attacks.
- Low Latency and Real-Time Security Enforcement Security mechanisms must not introduce delays that attackers can exploit. XGBoost delivered the best trade-off: Training time: 4.06 s and Prediction time: 0.129 s. This ensures that authentication decisions occur nearly instantly, enabling real-time continuous verification. The system can revoke access immediately when abnormal or unauthorized signals are detected.
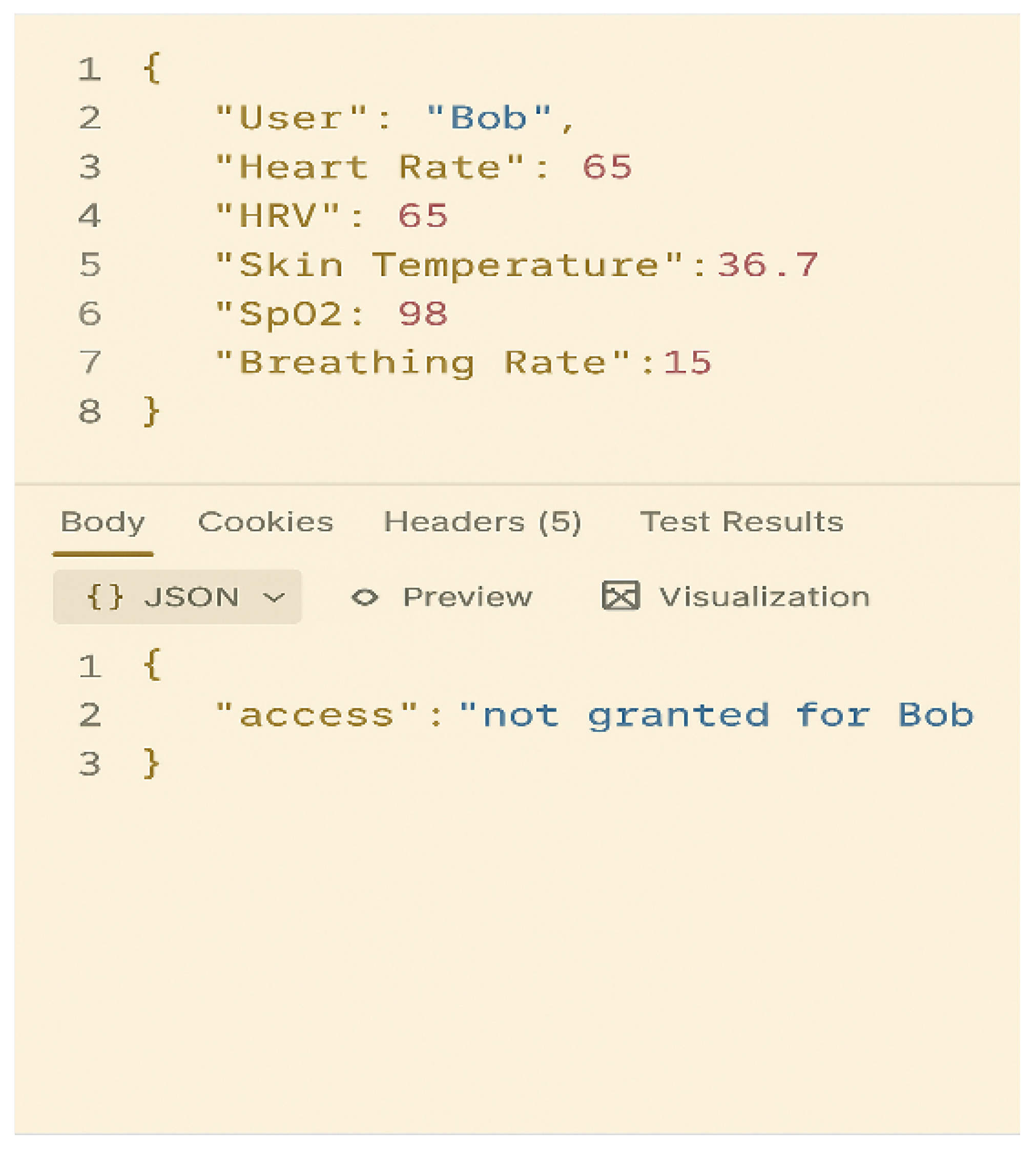
- Security Validation Through Real-Time Simulation The real-time API test using identical vital-sign values for two different individuals (“Bob” and “Charlie”) shows that the system does not rely solely on raw physiological values. Instead, authentication is based on the learned temporal and contextual biometrics, making simple spoofing or value replication ineffective.
6.2. Potential Attack Vectors
6.3. Comparison with the Discussed Related Works
6.4. Quantitative Comparison with Related Works
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Hamad, S.A.; Sheng, Q.Z.; Zhang, W.E.; Nepal, S. Realizing an Internet of Secure Things: A Survey on Issues and Enabling Technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1372–1391. [Google Scholar] [CrossRef]
- Shah, S.W.; Kanhere, S.S. Recent Trends in User Authentication—A Survey. IEEE Access 2019, 7, 112505–112519. [Google Scholar] [CrossRef]
- Xie, N.; Li, Z.; Tan, H. A Survey of Physical-Layer Authentication in Wireless Communications. IEEE Commun. Surv. Tutor. 2021, 23, 282–310. [Google Scholar] [CrossRef]
- Caballero-Hernández, H.; Gil-Antonio, L.; Lopez-Gonzalez, E.; Antonio-Velazquez, J.A. A brief review about biometrics systems in modern context. Int. J. Adv. Res. Comput. Sci. 2022, 13, 5. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Sennersten, C.; Ahmad, A. Towards Cognitive Authentication for Smart Healthcare Applications. Sensors 2022, 22, 2101. [Google Scholar] [CrossRef] [PubMed]
- Soni, P.; Pradhan, J.; Pal, A.K.; Islam, S.H. Cybersecurity Attack-resilience Authentication Mechanism for Intelligent Healthcare System. IEEE Trans. Ind. Inform. 2022, 19, 830–840. [Google Scholar] [CrossRef]
- Ammour, B.; Boubchir, L.; Bouden, T.; Ramdani, M. Face–iris multimodal biometric identification system. Electronics 2020, 9, 85. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Awad, A.I.; van de Beek, J.; Nikolakopoulos, G. Intelligent authentication of 5G healthcare devices: A survey. Internet Things 2022, 20, 100610. [Google Scholar] [CrossRef]
- Soni, M.; Singh, D.K. Privacy-preserving secure and low-cost medical data communication scheme for smart healthcare. Comput. Commun. 2022, 194, 292–300. [Google Scholar] [CrossRef]
- Wang, Y.; Gu, T.; Luan, T.H.; Lyu, M.; Li, Y. HeartPrint: Exploring a Heartbeat-Based Multiuser Authentication With Single mmWave Radar. IEEE Internet Things J. 2022, 9, 25324–25336. [Google Scholar] [CrossRef]
- Peng, J.; Hao, Z.; Zhang, Z.; Wang, R.; Li, M.; Dang, X. Utter Innocence: Contactless Authentication Method Based on Physiological Signals. IEEE Sens. J. 2024, 24, 7740–7751. [Google Scholar] [CrossRef]
- Islam, S.M.M.; Rahman, A.; Prasad, N.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication System using a Support Vector Machine (SVM) on Radar Respiration Measurements. In Proceedings of the 2019 93rd ARFTG Microwave Measurement Conference (ARFTG), Boston, MA, USA, 7 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Ning, J.; Xie, L.; Wang, C.; Bu, Y.; Xu, F.; Zhou, D.W.; Lu, S.; Ye, B. RF-Badge: Vital Sign-Based Authentication via RFID Tag Array on Badges. IEEE Trans. Mob. Comput. 2023, 22, 1170–1184. [Google Scholar] [CrossRef]
- Wang, W.; Vette, M.; Wang, Q.; Yang, J.; Zuniga, M. CamPressID: Optimizing Camera Configuration and Finger Pressure for Biometric Authentication. In Proceedings of the 2022 IEEE 19th International Conference on Mobile Ad Hoc and Smart Systems (MASS), Denver, CO, USA, 19–23 October 2022; pp. 229–235. [Google Scholar] [CrossRef]
- Wang, G.; Shanker, S.; Nag, A.; Lian, Y.; John, D. ECG biometric authentication using self-supervised learning for IoT edge sensors. IEEE J. Biomed. Health Inform. 2024, 28, 6606–6618. [Google Scholar] [CrossRef] [PubMed]
- Cheung, W.; Vhaduri, S. Continuous Authentication of Wearable Device Users from Heart Rate, Gait, and Breathing Data. In Proceedings of the 2020 8th IEEE RAS/EMBS International Conference for Biomedical Robotics and Biomechatronics (BioRob), New York, NY, USA, 29 November–1 December 2020; pp. 587–592. [Google Scholar]
- Cruz, J.C.D.; Javier, F.A.C.; Puyat, C.C.; Ibera, J.C. Non-invasive heart and respiratory rates extraction using frequency-modulated continuous-wave radar. In Proceedings of the 2021 IEEE 4th International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 13–15 August 2021; pp. 382–386. [Google Scholar]
- Romano, C.; Nicolò, A.; Innocenti, L.; Bravi, M.; Miccinilli, S.; Sterzi, S.; Sacchetti, M.; Schena, E.; Massaroni, C. Respiratory Rate Estimation during Walking and Running Using Breathing Sounds Recorded with a Microphone. Biosensors 2023, 13, 637. [Google Scholar] [CrossRef]
- Wehler, D.; Jelinek, H.F.; Gronau, A.; Wessel, N.; Kraemer, J.F.; Krones, R.; Penzel, T. Reliability of heart-rate-variability features derived from ultra-short ECG recordings and their validity in the assessment of cardiac autonomic neuropathy. Biomed. Signal Process. Control 2021, 68, 102651. [Google Scholar] [CrossRef]
- Aldumiji, N.; Khan, E. Fingerprint and location based multifactor authentication for mobile applications. Int. J. Eng. Technol. 2019, 8, 193–204. [Google Scholar]
- Abellán-Aynés, O.; López-Plaza, D.; Alacid, F.; Naranjo-Orellana, J.; Manonelles, P. Recovery of Heart Rate Variability After Exercise Under Hot Conditions: The Effect of Relative Humidity. Wilderness Environ. Med. 2019, 30, 260–267. [Google Scholar] [CrossRef]
- Sapra, A.; Malik, A.; Bhandari, P. Vital Sign Assessment; StatPearls Publishing: Treasure Island, FL, USA, 2023. [Google Scholar]
- Neves, E.B.; Cunha, R.M.; Rosa, C.; Antunes, N.S.; Felisberto, I.M.V.; Vilaça-Alves, J.; Reis, V.M. Correlation between skin temperature and heart rate during exercise and recovery, and the influence of body position in these variables in untrained women. Infrared Phys. Technol. 2016, 75, 70–76. [Google Scholar] [CrossRef]
- Lee, J.; Park, C. Remote SpO2 Estimation using End-to-End CNN Model. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Yeosu, Republic of Korea, 26–28 October 2022; pp. 1–3. [Google Scholar] [CrossRef]
- White, D.W.; Raven, P.B. Autonomic neural control of heart rate during dynamic exercise: Revisited. J. Physiol. 2014, 592, 2491–2500. [Google Scholar] [CrossRef]
- Soo, J.; Girard, O.; Ihsan, M.; Fairchild, T. The Use of the SpO2 to FiO2 Ratio to Individualize the Hypoxic Dose in Sport Science, Exercise, and Health Settings. Front. Physiol. 2020, 11, 570472. [Google Scholar] [CrossRef]
- Refinetti, R. Circadian rhythmicity of body temperature and metabolism. Temperature 2020, 7, 321–362. [Google Scholar] [CrossRef] [PubMed]



| Study | Number of Factors | Continuum | Non-Interactive | Activity Adaptive | Method |
|---|---|---|---|---|---|
| [10] | Single modality (Heartbeat motions) | ✓ | ✓ | ✗ | ML classifier on mmWave heartbeat signals |
| [11] | Dual modality (Respiration, ECG) | ✓ | ✓ | ✗ | Lightweight deep learning model–ShuffleNet V2 |
| [12] | Single modality (Respiration only) | ✓ | ✓ | ✗ | SVM (RBF kernel) on FFT features from Doppler radar |
| [13] | Dual modality (Respiration, ECG) | ✓ | ✓ | ✗ | MCNet (custom neural network) using RFID |
| [14] | Single modality (PPG only) | ✗ | ✗ | ✗ | Traditional ML-based authentication with optimized camera |
| [15] | Single modality (ECG only) | ✗ | ✓ | ✗ | ML (KNN) |
| [16] | Dual modality (HR, Breathing) | ✗ | ✓ | ✗ | CNN |
| ours | Five- modalities(HR, HRV, Skin Temperature, and Breathing Rate) | ✓ | ✓ | ✓ | ML Classifiers (DT, RF, XG Boost, Gradient Boosting, KNN) |
| No | Feature Title | Variable Data Type | Feature Categorization |
|---|---|---|---|
| 1 | HR | Continuous | Resting: 100–60; Walking: 130–110; Running: 170–140 |
| 2 | HRV | Continuous | Resting: 105–65; Walking: 60–45; Running: 40–10 |
| 3 | Skin Temperature | Continuous | Resting: 37.2–36.1; Walking: 38.5–37.5; Running: 40.0–38.7 |
| 4 | Continuous | Resting: 100–97; Walking: 96–94; Running: 93–90 | |
| 5 | Breathing Rate | Continuous | Resting: 20–12; Walking: 35–22; Running: 60–40 |
| 6 | Activity Level | Integer | 1: Resting; 2: Walking; 3: Running |
| 7 | User | Categorical | Alice; Bob; Charlie; Sara |
| Feature | Noise Type | Parameters/Function | Justification |
|---|---|---|---|
| HR | Gaussian (normal) | Simulates variability due to stress or sensor drift. | |
| HRV | Gaussian (normal) | Reflects small natural fluctuations and measurement uncertainty. | |
| Skin Temperature | Sinusoidal + Uniform | Captures small oscillations from thermoregulation and ambient temperature effects. | |
| Conditional Uniform Drop | , with 2% probability if walking/running | Simulates rare motion artifacts. | |
| Breathing Rate | Sinusoidal + Gaussian | Emulates natural rhythm of respiration. |
| Metric | Decision Tree | Random Forest | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| Accuracy | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Precision | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Recall | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| F1-score | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Metric | Decision Tree | Random Forest | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| Accuracy | 0.92 | 0.94 | 0.95 | 0.95 | 0.93 |
| Precision | 0.91 | 0.93 | 0.94 | 0.94 | 0.92 |
| Recall | 0.90 | 0.92 | 0.94 | 0.93 | 0.91 |
| F1-score | 0.90 | 0.93 | 0.94 | 0.94 | 0.92 |
| Metric | Decision Tree | Random Forest | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| Accuracy | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Precision | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Recall | 0.93 | 0.95 | 0.96 | 0.96 | 0.95 |
| F1-score | 0.94 | 0.95 | 0.96 | 0.96 | 0.95 |
| Metric | Decision Tree | Random Forest | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| Accuracy | 0.96 | 0.97 | 0.98 | 0.98 | 0.97 |
| Precision | 0.96 | 0.97 | 0.98 | 0.98 | 0.97 |
| Recall | 0.95 | 0.97 | 0.98 | 0.98 | 0.97 |
| F1-score | 0.96 | 0.97 | 0.98 | 0.98 | 0.97 |
| Metric | Decision Tree | Random Forest | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| EER | 0.0227 | 0.0216 | 0.0215 | 0.0221 | 0.0250 |
| Metric | DT | RF | XGBoost | Gradient Boosting | KNN |
|---|---|---|---|---|---|
| Training | 0.6851 | 17.6861 | 4.0650 | 90.9574 | 0.1203 |
| Prediction | 0.0043 | 0.2267 | 0.1297 | 0.1125 | 1.4079 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.
Share and Cite
Alrawili, R.; Sowells-Boone, E.; Qawasmeh, S.A.-D. Seamless Vital Signs-Based Continuous Authentication Using Machine Learning. Future Internet 2026, 18, 14. https://doi.org/10.3390/fi18010014
Alrawili R, Sowells-Boone E, Qawasmeh SA-D. Seamless Vital Signs-Based Continuous Authentication Using Machine Learning. Future Internet. 2026; 18(1):14. https://doi.org/10.3390/fi18010014
Chicago/Turabian StyleAlrawili, Reem, Evelyn Sowells-Boone, and Saif Al-Dean Qawasmeh. 2026. "Seamless Vital Signs-Based Continuous Authentication Using Machine Learning" Future Internet 18, no. 1: 14. https://doi.org/10.3390/fi18010014
APA StyleAlrawili, R., Sowells-Boone, E., & Qawasmeh, S. A.-D. (2026). Seamless Vital Signs-Based Continuous Authentication Using Machine Learning. Future Internet, 18(1), 14. https://doi.org/10.3390/fi18010014






