Abstract
Most current access control models are rigid, as they are designed using static policies that always give the same outcome in different circumstances. In addition, they cannot adapt to environmental changes and unpredicted situations. With dynamic systems such as the Internet of Things (IoT) with billions of things that are distributed everywhere, these access control models are obsolete. Hence, dynamic access control models are required. These models utilize not only access policies but also contextual and real-time information to determine the access decision. One of these dynamic models is the risk-based access control model. This model estimates the security risk value related to the access request dynamically to determine the access decision. Recently, the risk-based access control model has attracted the attention of several organizations and researchers to provide more flexibility in accessing system resources. Therefore, this paper provides a systematic review and examination of the state-of-the-art of the risk-based access control model to provide a detailed understanding of the topic. Based on the selected search strategy, 44 articles (of 1044 articles) were chosen for a closer examination. Out of these articles, the contributions of the selected articles were summarized. In addition, the risk factors used to build the risk-based access control model were extracted and analyzed. Besides, the risk estimation techniques used to evaluate the risks of access control operations were identified.
1. Introduction
Security is the nightmare for almost all new technologies. Providing a secure system is not an easy task. One of the significant components to resolve security challenges is to build an efficient and effective access control model. This model is utilized to manage access to system resources by allowing only authorized users who have been authenticated successfully. An access control model comprises three main items: subject, target and rules. Subjects are system users who make the access request to access system resources (targets). Rules are utilized to make the access decision, whether granting or denying access [1,2]. The main purpose of the access control is to decline unauthorized users and reduce the tasks of authorized users on a certain device. In addition, it prevents the action that could trigger a security violation [3].
There are two classes of access control approaches: traditional and dynamic. Traditional access control approaches utilize rigid and predetermined policies to determine the access decision. These static policies provide the same decision in different circumstances. Therefore, this inflexible approach cannot provide a robust security method for various dynamic and distributed systems such as the Internet of Things (IoT) and cloud computing [4]. Alternatively, dynamic access control methods employ not only static policies but also dynamic and real-time features to make access decisions. These dynamic features can involve context, trust, history events, location, time, and security risk [5].
Risk-based access control model is one of the dynamic methods that utilize the security risk value related to each access request as a criterion to determine access decisions [1]. A risk-based access control model provides several benefits over current access models. For example, it delivers more flexibility and resilience while accessing system resources by utilizing dynamic and contextual features to determine the access decision. In addition, it considers the exceptional and unpredicted access requests that are essential for some applications such as healthcare and the military, where granting access can literally save thousands of lives [6]. The ultimate goal of the risk-based access control model is to produce a scheme that promotes information sharing to increase the organization’s benefit and at the same time keeps users responsible for their activities and stops the anticipated damage due to sensitive information disclosure [4].
The objective of the paper is to present a systematic literature review and investigate the state-of-the-art of the risk-based access control model, which is one of the pillars toward designing a dynamic and adaptive access control model for distributed systems. Based on the selected search plan, 44 articles (of 1044 articles) were chosen for closer investigation. Out of the retrieved and analyzed articles, the risk factors utilized to design the risk-based access control model were extracted and analyzed. Besides, the risk estimation techniques used to evaluate security risks were identified. In addition, the contributions of the selected articles were summarized. As compared to other surveys, to the best of the authors’ knowledge, this is the first paper that provides a systematic literature review for the risk-based access control model.
The contribution of this paper can be summarized as follows:
- Reviewing recent studies of risk-based access control models by providing a summary of the contributions of each study.
- Identifying and analyzing various risk factors used in recent risk-based access control models.
- Determining and investigating different risk estimation techniques utilized in recent risk-based access control models.
The rest of this paper is structured as follows. Section 2 gives an overview of access control approaches; Section 3 introduces the risk-based access control model and its main components; Section 4 provides the research methodology; Section 5 presents the analysis of results; Section 6 presents a discussion to show how this systematic review answered proposed research questions, and Section 7 is the conclusion.
2. An Overview of Access Control
The key objective of the access control is to limit operations performed by authorized users. In addition, it prohibits any action that could trigger a security violation [1]. An effective access control model should fulfill the security demands of confidentiality, integrity, and availability [3]. It is essential to make a reasonable distinction between authentication, authorization, and access control. Authentication is the process of verifying the identity of a user [7], while allowing or denying access to an authenticated user to carry out particular tasks on particular resources is called authorization. Access control is the process of enforcing authorization policies. Once a user is authenticated and the authorization level is identified, access control is used to enforce user permissions to prevent the user/subject from accessing anything that he/she should not be able to [3].
The history of the phrase “Access Control” has started in transportation in the first half of the 20th century. The concept of the limited-access road was suggested in 1907 to control fast-growing motor traffic. Although early cars were not as fast as today’s standard, car drivers were enforced to control their speed on highways. They were enforced to enter and exit via one-way ramps to control the access to highways, which led to a reduction in the probability of cross-traffic accidents and increases the speed of traffic flows [8].
Currently, access control is applied at diverse levels in several domains such as database management systems and operating systems to control resources and allow only legal users/subjects to use system resources in an authorized way. An access control model comprises of five core elements: subjects, actions, objects, privileges, and access policies [9].
- Subjects: represents various entities that can be user, agents, or processes that make an access request to access system resources (objects).
- Objects: describes system resources encompassing data or information that needed to be accessed by subjects/users.
- Actions: represents various types of actions or activities that subjects can perform on a particular object such as read, write, execute, etc.
- Privileges: These are the permissions that are granted to subjects to be able to carry out a particular action on a particular object.
- Access policies: These are a group of rules or procedures that specify the criteria needed to determine the access decision whether granting or denying access for each access request.
The flow of an access control process can be shown in Figure 1. The flow begins when a subject/user sends an access request to the access control manager to access a particular object. Then, the access control manager compares the subject’s credentials against access policies to decide whether granting or denying access. If the access is granted, the access control manager will allow the user to access the object. While if the access is denied, the access control manager will send a warning message due to insufficient credentials and ask the subject to use sufficient credentials to be able to access the requested object [9].
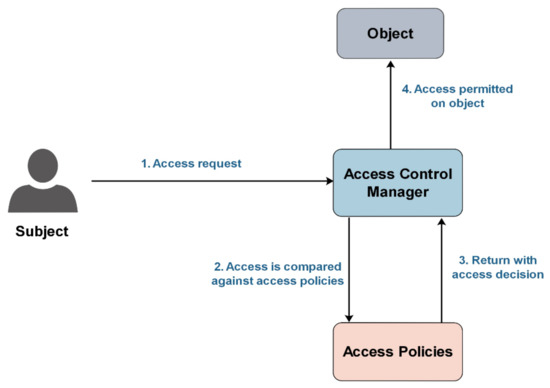
Figure 1.
Flow of an access control operation.
There are many access control approaches, which can be categorized into two main groups: traditional and dynamic access control approaches.
2.1. Traditional Access Control Models
Traditional access control (also called classical or static) approaches utilize rigid and predetermined policies to determine the access decision. These static and rigid policies provide the same decision in different circumstances. Although traditional access control approaches were successfully applied in different environments to solve various problems, these approaches are designed to provide a relationship between information associated with an access control rule logic and a resource for which access is requested. The implementation of an access control approach is subject to manipulation, which can range from an unexpected situation, including poorly written access policies to several malicious entities acquiring access to a set of existing accounts. Therefore, traditional access control approaches provide a set of advantages, but they also have drawbacks. One of these drawbacks is that it cannot handle unpredicted situations as they are based on static and predefined policies [10]. This inflexible approach cannot provide a robust security method for various dynamic and distributed systems such as IoT and Cloud Computing, which need more flexibility in accessing system resources. Instead, this static approach can be the best solution in situations where there is no way to collect a contextual feature/attribute while making the access request, for example the operating system.
There are various traditional access control approaches including Access Control List (ACL), Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-Based Access Control (RBAC). ACL is a list of specific objects that involve lawful users together with their access permissions. ACLs are utilized in various systems, for example, UNIX systems. Although ACL is an efficient and effective model, it is not scalable, in which it cannot cope with a huge list of objects and subjects. For DAC, it is mainly built for multi-user databases and systems with few previously known users. Granting access in DAC is mainly based on the subject identity and authorization that are determined using open policies. This enables the object’s owner to allow access to this object to any subject. For MAC, the level of sensitivity of objects is used to categorize objects into several sensitivity levels—for example, sensitive, not sensitive, confidential, etc. Each object has a label that specifies the sensitivity level of that object. In addition, each subject has a label that specifies the object the subject can access [11,12]. For RBAC, it involves three main components: users or subjects, roles (collections of permissions), and actions (activities performed on target resources) [13]. The basis of RBAC depends on roles, in which each role is accompanied by a set of access permissions. Each organization has several roles—for example, client, employee, manager, administrator, etc. A user can be a member of one or more roles, and a role can involve one or more users [14].
2.2. Dynamic Access Control Models
The core principle of dynamic access control models is that they consider not only access policies but also dynamic and contextual features that are collected at the time of the access request to make access decisions [15]. This provides more flexibility and can adjust to various situations and circumstances while making the access decision.
The need to adopt dynamic access control approaches should be one of the essential priorities to provide efficient and flexible access control model. However, most existing access methods are relying on static and rigid access policies and manual processes. These approaches are unable to provide a roadmap to improve automation significantly. This absence of automation results in a heavy involvement of human analysis that is error-prone and susceptible to various types of attacks based on social engineering. Additionally, current classical approaches have issues with resolving risks and threats in real time, especially when handling a previously unidentified threat. This is because these approaches make their access decision based on a set of policies built by a security analyst, who cannot resolve different access control situations in real time but can deal only with problems that were recognized before [16].
Instead of static policies, dynamic access methods use dynamic and real-time features to provide access decisions. These dynamic features can include trust, context, history, risk and operational need. Besides, these dynamic methods can adapt to different situations and circumstances at the time of deciding access decisions [5,17]. This dynamic access control approach can be valuable for several applications such as healthcare and the military, where considering exceptional access requests to provide the access can literally save thousands of lives. Table 1 provides a comparison between traditional and dynamic access control approaches.

Table 1.
Comparison between traditional and dynamic access control approaches. ACL: Access Control List, DAC: Discretionary Access Control, IoT: Internet of Things, MAC: Mandatory Access Control, and RBAC: Role-Based Access Control.
The security risk is one of the dynamic features that is used to build a risk-based access control model. The next section provides an overview of the risk-based access control model.
3. Risk-Based Access Control Model
Commonly, the risk is the possibility of loss or injury. It is about some incident that may arise in the future and cause losses. According to Elky [18], the risk is defined as “the possible damage that may arise from the existing operation or from some upcoming incident”. The risk is found in numerous domains of our life. From the information technology security perspective, the security risk is defined as the damage that undesirably affects operation and its related information, while the process of understanding and mitigating against issues that may result in a breach of confidentiality, integrity, or availability of an information system is called risk management [18].
Security risk in the access control context can be defined as the possibility of information leakage and the value of this information that may occur from accessing system resources [1]. Risk-based access control model utilizes the security risk as a criterion to make the access decision for each access request. This model is based on estimating the security risk value associated with each access request dynamically, and it then uses the estimated risk value to decide whether granting or denying access [4]. Mathematically, the most popular formula to represent the risk in a quantitative form is the likelihood/ probability of an incident to occur multiplied by the impact regarding that incident [19].
There are several methods to build a risk-based access control model. These methods have certain common features from different models. The main elements of a risk-based access control model are shown in Figure 2. The risk-based access control model comprises three key modules. The risk estimation is the main module, which gets access requests from users, analyzes them, collects the required information of risk factors, and estimates the security risk value related to each access request. Then, the estimated risk value is compared against access policies to decide the access decision whether granting or denying the access [20].
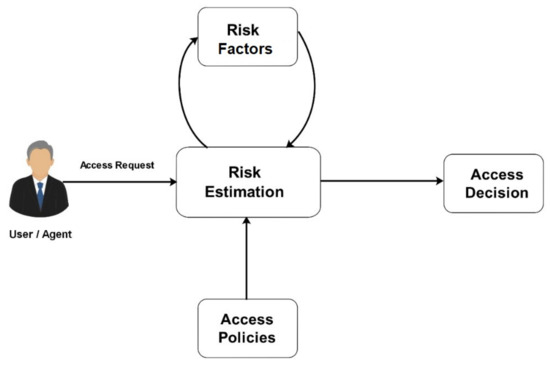
Figure 2.
Main elements of a risk-based access control model.
4. Methodology
The risk-based access control model has several advantages in terms of flexibility and ability to provide an effective security model for dynamic systems. This systematic literature review is conducted to examine and investigate current research regarding risk-based access control models and explain the findings of the conducted review. A systematic literature review is mainly conducted as a way to specify, evaluate, and interpret all available research related to specific research questions, certain subjects, or phenomenon of interest [21].
Conducting a systematic literature review passed through five stages, as depicted in Figure 3. The first stage aims to formulate the research questions that the current review paper attempts to answer and then decide the criteria to include or exclude articles in the second stage to make sure that the selected articles are the best and most appropriate regarding the review objectives. The third stage is the main stage that discusses at length which different databases will be searched to locate relevant articles. The fourth stage analyzes the results and then in the fifth stage, the results of each research question will be discussed.
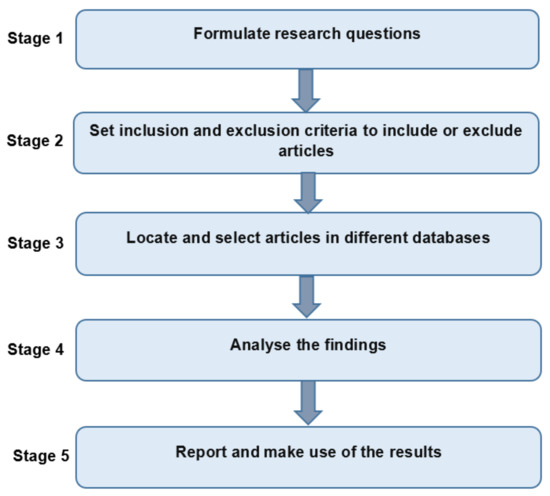
Figure 3.
Stages of the current systematic literature review.
This approach/methodology was adopted to make the reader fully aware of the stages of conducting this systematic literature review. The methodology was started by defining the research questions to have a specific target while reviewing multiple publications. Then, inclusion and exclusion criteria were presented to show how the retrieved publication are filtered to reach the target of the study. Data sources where publications were retrieved are also presented to show the digital libraries utilized to collect these publications. In addition, the selection of relevant articles is discussed. The adopted methodology has several advantages in which it aims to describe the full process utilized to reach the target of the study to make the reader fully aware of all the procedures conducted by the researcher. In addition, this approach was adopted in several previous systematic literature reviews. On the other hand, this approach produces some drawbacks in which it limits the scope of the review/study, which may not give all the information about a certain topic to the reader.
4.1. Research Questions
The current study/paper aims to answer the subsequent research questions:
- RQ1: What are recent and peer-reviewed literature regarding risk-based access control models?
- RQ2: What are the risk factors used to build risk-based access control models?
- RQ3: What are risk estimation techniques employed in risk-based access control models?
4.2. Inclusion and Exclusion Criteria
Inclusion and exclusion criteria for selecting the appropriate research were employed. These criteria are mainly aimed to answer research questions and ensure designing efficient literature review. Inclusion criteria were:
- Scientific and peer-reviewed articles
- Topic is mainly risk-based access control model
- Relevant to research questions
- Articles written in English
- Published any time (year of publication is open and is not limited to a specific period)
Exclusion criteria were:
- Articles concerning risk estimation techniques that are not in the context of risk-based access control models
- Articles concerning risk factors that are not in the context of risk-based access control models
- Unpublished articles, non-peer-reviewed articles, and editorial articles
- Articles that are not fully available
- Non-English articles
- Duplicates of already included articles
4.3. Data Sources
Searches were carried out via digital libraries. This systematic review involved the following electronic databases:
- IEEE Xplore
- PubMed
- Elsevier ScienceDirect
- Google Scholar
- ACM Digital Library
- SpringerLink.
A keyword-based search was employed to collect the articles that relevant to the topic and research questions. The main keywords that were utilized involve:
- Risk-Based Access Control
- Risk Estimation
- Risk estimation Technique
- Risk Factors
- Security Risk.
4.4. Selection of Relevant Articles
Selecting relevant and recent studies with respect to the risk-based access control model started with 1044 articles collected from various online digital libraries that were decided in the previous section. The selection process on the collected publications was divided into three phases:
- Phase 1: The results of the search and collected publications were filtered depending on the inclusion and exclusion criteria that were discussed in Section 4.2. The search conducted was not bounded by a specific range of years to be able to collect all relevant publications regarding risk-based access control models.
- Phase 2: The publications collected from various online digital libraries were assessed depending on the relevance of the publication to the topic and research questions by examining only the title and abstract.
- Phase 3: The main purpose of this phase was to remove the duplicates of the collected publications from six different online digital libraries.
5. Analysis of Results
The inclusion and exclusion criteria were applied on the collected publications through three phases, as depicted in Figure 4. Based on the assessment through reading only the title and the abstract and its relevance to the research questions, 986 publications were excluded. In addition, the duplicates between different online digital databases were excluded, in which 32 duplicate publications were excluded.
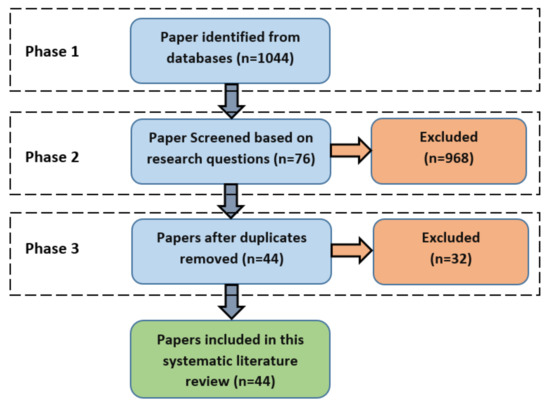
Figure 4.
Flow diagram of the search.
The search that was executed in six different well-known online databases enables us to collect, as much as possible, most of the publications that are relevant to risk-based access control models. The result of the collected publications from each online database and the resultant number of publications after applying the three selection phases can be shown in Table 2. The results show that Google Scholar was the richest data source of publications related to risk-based access control models.

Table 2.
The number of search result per database after applying three phases of the selection process.
In addition, Figure 5 illustrates the number of articles published per year. The results show that the risk-based access control model started to attract the attention of the researcher after 2010. However, it is still an undiscovered area for multiple researchers. Given the steady number of publications in 2011, 2012, and 2013, we can see that the number of publications started to decrease, which reaches only one in 2019.
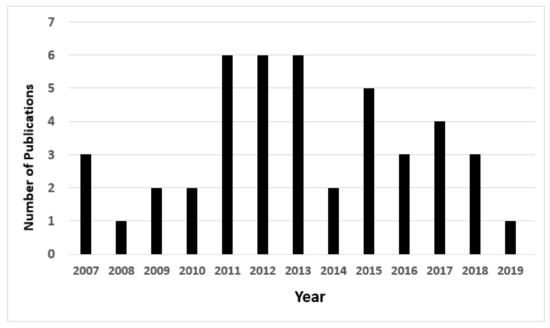
Figure 5.
Number of selected articles published per year.
In addition, Figure 6 categorizes retrieved publications regarding risk-based access control models into either journal or conference publication per year. The results show that most publications that match our research questions were conference publications. In addition, Table 3 contains basic information about the analyzed and selected publications, which involve a publication’s ID, publication citation, publication type, and year of publication. All selected/retrieved articles were published in peer-reviewed journals and conference proceedings. Besides, the selected publications contain only 3 book chapters, which are also peer-reviewed.
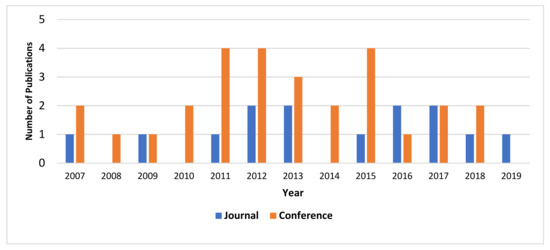
Figure 6.
Number of journal and conference publications per year.

Table 3.
Retrieved publications that are related to research questions.
6. Discussion
The risk-based access control model is one of the hot topics that many scholars are investigating to provide flexible, dynamic, and operative access control approach in distributed and dynamic systems. This paper can be a good starting point for such researchers to understand this model and review existing work related to proposed research questions. In this section, a discussion of the retrieved/analyzed publications was presented to show how the retrieved publications answered the proposed research questions.
RQ1: What are recent and peer-reviewed literature regarding risk-based access control models?
To answer this research question, retrieved/analyzed publications that are related to risk-based access control models will be discussed. Recent and peer-review publication outlined risk-based access control models are discussed. Table 4 summarizes the contributions of each publication.

Table 4.
Summary of recent studies outlined risk-based access control models.
RQ2: What are the risk factors used to build risk-based access control models?
One of the essential parts of a risk-based access control model is to choose the effective risk factors that determine access decisions efficiently. Many risk factors can be used to estimate the risk value associated with the access request to make the access decision dynamically and efficiently. To answer this research question, risk factors utilized in recent risk-based access control models were reviewed. Then, a brief overview of these risk factors is provided. This is followed by showing the risk factors extracted from retrieved/analyzed publications, as depicted in Table 5.

Table 5.
Risk factors used in retrieved/analyzed publications of risk-based access control models.
- Subject Clearance (Role): It represents the subject security level acquired from the system administrator. The most popular clearances in the military are Top Secret, Secret, Confidential, and no clearance. Different access permissions are granted according to the subject role in the organization. Each role is associated with certain permissions [58]. The higher the clearance granted, the lower the associated risk value.
- Resource Sensitivity: It describes the sensitivity level of resources the user wants to access. Different sensitivity levels have different risk values. The higher the resource sensitivity, the higher the risk value if the access is granted to this resource [24].
- Action Severity: It characterizes the cost of a particular action on a particular resource in terms of confidentiality, integrity, and availability. So, different actions have different consequences and so have different risk values.
- Risk History: It represents user previous risk values on a certain resource. It can be used to detect the future behavior of the user toward a certain resource.
- Trust: It is similar to the risk history. It represents the subject/user trust toward a certain resource. Trust is classified into two categories: identity and behavioral trust. Identity trust is concerned with validating the authenticity of an object and focuses on objective credentials. While behavioral trust works with the entity’s trustworthiness, which depends on certain contexts [59]. In risk-based access control models, only behavioral trust is used.
- Benefits of User: It describes any sort of advantages/privileges the user will get when the access is granted. It also represents what will be the damage that will happen for the user if the access was denied [4].
- Outcomes of Actions: The access control system has inputs, consisting of the action and list of consequence outcomes of the action. Each outcome may occur in some specific contexts, consisting of principle context, environment context, and resource context. The outcome of actions estimates the risk of each of these contexts [20].
- Context: It signifies the real-time and environmental information that can be collected while making the access request. Contexts features are utilized to specify the security risk value related to each access request. Location and time are the most popular contexts [41].
- Access Policies: They are primarily utilized by the access control manager (risk estimation module in the risk-based access control model) to specify access decisions. These policies are designed by the resource owner or security system administrator to classify terms and situations of granting or denying access to a particular resource. In the risk-based control model, the estimated risk value resulted from the risk estimation module is compared against risk policies to decide whether granting or denying access [41].
The results show that risk factors used to implement risk-based access control models are significantly based on the context where the risk-based access control model will be deployed. However, several risk factors can be applied in various contexts. Reviewing risk factors used in risk-based access control models of retrieved publications reveal that “Risk History” was the dominant risk factor in most risk-based access control models in which it was adopted in 18 publications, as depicted in Figure 7. This should be normal or expected, as any risk model would or should use their previous risk values given to a user/subject to assess their current and future access. In addition, the context was one of the significant risk factors used in 14 publications. Using the context as a risk factor in risk-based access control models customizes the risk model to a specific application and adds the flexibility needed for these access control models to be able to adapt to their environment. Resource sensitivity and trust were adopted in 12 and 11 risk-based models, respectively. As a conclusion, determining the appropriate risk factors for building a risk-based access control model is significantly based on the application and environment where this model will be deployed. It also depends on the availability of data for such a risk factor to be able to use it to calculate the overall security risk value associated with the access request to determine the access decision.
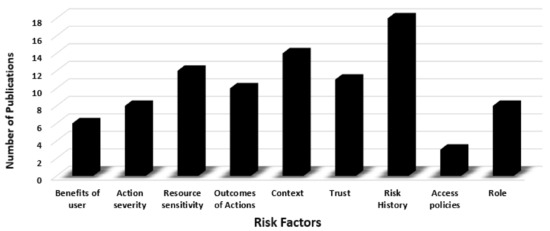
Figure 7.
Risk factors used to build risk-based access control models that are discussed in retrieved publications.
RQ3: What are risk estimation techniques employed in risk-based access control models?
The vital stage of implementing a risk-based access control model is the risk estimation process. This process is based on estimating the likelihood of information leakage and the value of that information. The main purpose of the risk estimation process is to build a method to arrange risks based on their priorities and use risk values to make access decisions following a specific context.
There are several challenges associated with the risk estimation process. For example, the key purpose of the risk estimation process is to forecast the future likelihood of information leakage and the impact of such leakage on system resources. Defining such a likelihood is not an easy job [60]. Moreover, if the risk estimation process is based on imprecise or incomplete information, it will result in complications and problems to identify the value of information [31].
Determining the suitable risk estimation technique for building a risk-based access control models is not an easy task, as there are many things that should be taken into consideration: for instance, the availability of data that describe the risk likelihood and its impact. In addition, in the access control context, the security risk value will be used to determine the access decision whether granting or denying access, which requires having a precise and accurate quantitative/numeric risk value.
This section answers the third research question by investigating and reviewing various risk estimation techniques utilized in risk-based access control models of retrieved/analyzed publications, as shown in Table 6.

Table 6.
Risk estimation techniques used in retrieved/analyzed publications of risk-based access control models.
As discussed earlier, one of the challenges of implementing a reliable and effective risk-based access control model is to determine the risk estimation technique that produces accurate and precise risk values to determine the access decision. However, due to the unavailability of datasets that describe risk likelihood and its impact, most publications did not discuss a clear method to assess the security risks of each access request. This reflected on having 18 publications from retrieved papers without a risk estimation process.
On the other hand, there are 8 publications that proposed a mathematical equation based on relationships between input and output variables to estimate the risk. However, these mathematical equations are variable dependent and cannot be adopted in different environments. In the same way, there are 7 publications that proposed the fuzzy logic system for the risk estimation process. However, the major issue in that method is the subjectivity and the need for domain experts to define fuzzy variables and build fuzzy rules. In addition, there are 7 publications that utilized the risk assessment to determine risks and assign them priorities. However, the risk assessment itself cannot provide a numeric risk value that can be used to make the access decision. For the machine learning and game theory as risk estimation methods, there are a few publications that discussed these methods. This is due to the lack of datasets that are required for training and testing phases in machine learning and for building appropriate strategies in game theory.
As discussed, providing a dataset that describe risk likelihood and its impact on a specific context is one of the key issues of implementing risk-based access control models. We encourage various researchers to build and share different datasets regarding risk-based access control models that can improve the performance and add learning ability to current risk-based access control models. Having datasets that consider different risk factors in different domains can help researchers improve and optimize their current risk-based models. There are no specific criteria for a dataset for the risk-based access control model except it should provide quantitative values of risk likelihood and its impact for a set of access control scenarios in a specific context with the specifying risk factors adopted.
7. Conclusions
Current access control models provide a static way to provide access decisions for various applications. However, an access control model for a dynamic and distributed system should rely on contextual and real-time data. With billions of sensors and devices in our environment, contextual information can be collected and utilized in the access control process, which can provide what is called dynamic access control models. One of these dynamic models is the risk-based access control model. This model is capable of providing the access decision dynamically by estimating the security risk value associated with the access request. The risk-based access control model can provide several benefits for several trending technologies such as IoT, cloud computing, etc. This paper presented a systematic literature review and analysis of the state-of-the-art of the risk-based access control model to provide a detailed understanding of the topic. Based on the selected search strategy, 44 articles (of 1044 articles) were chosen for a closer examination in terms of recent risk-based models, risk factors, and risk estimation techniques. The results provided a summarized version of selected articles to give the reader a basic view of different risk-based access control models from the perspective of various researchers. Although there are several risk factors that can be applied in various contexts—for example, risk history, which was adopted in 18 publications—the results show that risk factors used to implement risk-based access control models are significantly based on the context/domain. In addition, the results demonstrated that providing an efficient and accurate risk estimation technique that can be applied in different domains is one of the major issues of implementing risk-based access control models. Although some risk estimation approaches can work well such as decision tree, the lack of a dataset to represent the likelihood and impact of each risk scenario in a specific context is the key problem.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Dos Santos, D.R.; Westphall, C.M.; Westphall, C.B. A dynamic risk-based access control architecture for cloud computing. In Proceedings of the IEEE/IFIP NOMS 2014—IEEE/IFIP Network Operation and Managment Symposioum, Krakow, Poland, 5–9 May 2014; pp. 1–9. [Google Scholar]
- Liu, J.K.; Au, M.H.; Huang, X.; Lu, R.; Li, J. Fine-Grained Two-Factor Access Control for Web-Based Cloud Computing Services. IEEE Trans. Inf. Forensics Secur. 2016, 11, 484–497. [Google Scholar] [CrossRef]
- Suhendra, V. A Survey on Access Control Deployment. In Communications in Computer and Information Science; Kim, T., Adeli, H., Fang, W., Villalba, J.G., Arnett, K.P., Khan, M.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 259, pp. 11–20. [Google Scholar]
- Chen, P.; Pankaj, C.; Karger, P.A.; Wagner, G.M.; Schuett, A. Fuzzy Multi—Level Security: An Experiment on Quantified Risk—Adaptive Access Control. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Ouckland, CA, USA, 20–23 May 2007; pp. 222–227. [Google Scholar]
- Shaikh, R.A.; Adi, K.; Logrippo, L. Dynamic risk-based decision methods for access control systems. Comput. Secur. 2012, 31, 447–464. [Google Scholar] [CrossRef]
- Khambhammettu, H.; Boulares, S.; Adi, K.; Logrippo, L. A framework for risk assessment in access control systems. Comput. Secur. 2013, 39, 86–103. [Google Scholar] [CrossRef]
- Hulsebosch, R.J.; Bargh, M.S.; Lenzini, G.; Ebben, P.W.G.; Iacob, S.M. Context Sensitive Adaptive Authentication; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Houlis, P. The History and Future of Access Control Credentials 2018. Available online: https://www.ifsecglobal.com/global/history-future-access-control-credentials/ (accessed on 9 March 2019).
- Atlam, H.F.; Alassafi, M.O.; Alenezi, A.; Walters, R.J.; Wills, G.B. XACML for Building Access Control Policies in Internet of Things. In Proceedings of the 3rd International Conference on Internet of Things, Big Data and Security (IoTBDS 2018), Madeira, Portugal, 19–21 May 2018. [Google Scholar]
- Metoui, N. Privacy-Aware Risk-Based Access Control Systems. Ph.D. Thesis, University of Trento, Trento, Italy, May 2018. [Google Scholar]
- Bugiel, S.; Heuser, S.; Sadeghi, A.-R. Flexible and fine-grained mandatory access control on Android for diverse security and privacy policies. In Proceedings of the 22nd USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 131–146. [Google Scholar]
- Hulsebosch, R.J.; Salden, A.H.; Bargh, M.S.; Ebben, P.W.G.; Reitsma, J. Context sensitive access control. In Proceedings of the Tenth ACM Symposium on Access Control Models and Technologies, Stockholm, Sweden, 1–3 June 2005; pp. 111–119. [Google Scholar]
- Bijon, K.Z.; Krishnan, R.; Sandhu, R. A framework for risk-aware role based access control. In Proceedings of the IEEE Conference on Communications and Network Security, National Harbor, MD, USA, 14–16 October 2013; pp. 462–469. [Google Scholar]
- Kumar, A.; Karnik, N.M.; Chafle, G. Context sensitivity in role-based access control. Oper. Syst. Rev. 2002, 36, 53–66. [Google Scholar] [CrossRef]
- Wang, Q.; Jin, H. Quantified risk-adaptive access control for patient privacy protection in health information systems. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security—ASIACCS ’11, Hong Kong, China, 22–24 March 2011; pp. 406–410. [Google Scholar]
- Brooks, T.; Caicedo, C.; Park, J.S. Security Vulnerability Analysis in Virtualized Computing Environments. Int. J. Intell. Comput. Res. 2012, 3, 263–277. [Google Scholar] [CrossRef]
- Li, Y.; Sun, H.; Chen, Z.; Ren, J.; Luo, H. Using Trust and Risk in Access Control for Grid Environment. In Proceedings of the Security Technology, Hainan Island, China, 13–15 December 2008; pp. 13–16. [Google Scholar]
- Elky, S. An Introduction to Information System Risk Management; Sans Institute: Bethesda, MD, USA, 2006. [Google Scholar]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cogn. Comput. 2018, 2, 1–18. [Google Scholar]
- Diep, N.N.; Hung, L.X.; Zhung, Y.; Lee, S.; Lee, Y.; Lee, H. Enforcing Access Control Using Risk Assessment. In Proceedings of the Fourth European Conference on Universal Multiservice Networks, Toulouse, France, 14–16 February 2007; pp. 419–424. [Google Scholar]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; University of Durham: Durham, UK, 2007. [Google Scholar]
- Ricardo, D.; Marinho, R.; Schmitt, G.R.; Westphall, C.M.; Westphall, C.B. A Framework and Risk Assessment Approaches for Risk-based Access Control in the Cloud. J. Netw. Comput. Appl. 2016, 74, 1–27. [Google Scholar]
- Choi, D.; Kim, D.; Park, S. A Framework for Context Sensitive Risk-Based Access Control in Medical Information Systems. Comput. Math. Methods Med. 2015, 2015, 265132. [Google Scholar] [CrossRef] [PubMed]
- Li, J.; Bai, Y.; Zaman, N. A fuzzy modeling approach for risk-based access control in eHealth cloud. In Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 17–23. [Google Scholar]
- Arias-Cabarcos, P.; Rez-Mendoza, F.A.; Marín-López, A.; Díaz-Sánchez, D.; Sánchez-Guerrero, R. A metric-based approach to assess risk for ‘On cloud’ federated identity management. J. Netw. Syst. Manag. 2012, 20, 513–533. [Google Scholar] [CrossRef]
- Baracaldo, N.; Joshi, J. An adaptive risk management and access control framework to mitigate insider threats. Comput. Secur. 2013, 39, 237–254. [Google Scholar] [CrossRef]
- Kandala, S.; Sandhu, R.; Bhamidipati, V. An Attribute Based Framework for Risk-Adaptive Access Control Models. In Proceedings of the Sixth International Conference on Availability, Reliability and Security, Vienna, Austria, 22–26 August 2011; pp. 236–241. [Google Scholar]
- Lee, S.; Lee, Y.W.; Diep, N.N.; Lee, S.; Lee, Y.; Lee, H. Contextual Risk-based access control. Secur. Manag. 2007, 2007, 406–412. [Google Scholar]
- Atlam, H.F.; Wills, G.B. An efficient security risk estimation technique for Risk-based access control model for IoT. Internet Things 2019, 6, 1–20. [Google Scholar] [CrossRef]
- Diaz-Lopez, D.; Dolera-Tormo, G.; Gomez-Marmol, F.; Martinez-Perez, G. Dynamic counter-measures for risk-based access control systems: An evolutive approach. Futur. Gener. Comput. Syst. 2016, 55, 321–335. [Google Scholar] [CrossRef]
- Namitha, S.; Gopalan, S.; Sanjay, H.N.; Chandrashekaran, K. Risk Based Access Control In Cloud Computing. In Proceedings of the International Conference on Green Computing and Internet of Things (ICGCloT), Delhi, India, 8–10 October 2015; pp. 1502–1505. [Google Scholar]
- McGraw, R. Risk-Adaptable Access Control (RAdAC); National Security Agency: Fort Meade, MD, USA, 2009.
- Molloy, I.; Dickens, L.; Morisset, C.; Cheng, P.; Lobo, J.; Russo, A. IBM Research Report Risk-Based Access Control Decisions under Uncertainty; IBM: Armonk, NY, USA, 2011; Volume 25121. [Google Scholar]
- Ni, Q.; Bertino, E.; Lobo, J. Risk-based access control systems built on fuzzy inferences. In Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, Beijing, China, 13 April 2010; pp. 250–260. [Google Scholar]
- Abie, H.; Balasingham, I. Risk-Based Adaptive Security for Smart IoT in eHealth. In Proceedings of the 7th International Conference on Body Area Networks, Oslo, Norway, 24–26 September 2012; pp. 269–275. [Google Scholar]
- Shaikh, R.A.; Adi, K.; Logrippo, L.; Mankovski, S. Risk-based decision method for access control systems. In Proceedings of the PST 2011: 9th International Conference on Privacy, Security and Trust, Montreal, QC, Canada, 19–21 July 2011; pp. 189–192. [Google Scholar]
- Ricardo dos Santos, D.; Westphall, C.M.; Westphall, C.B. Risk-based Dynamic Access Control for a Highly Scalable Cloud Federation. In Proceedings of the Seventh International Conference on Emerging Security Information, Systems and Technologies (SECUREWARE 2013), Barcelona, Spain, 25–31 August 2013; pp. 8–13. [Google Scholar]
- Molloy, I.; Dickens, L.; Lobo, J.; Morisset, C.; Russo, A. Risk-Based Security Decisions Under Uncertainty Categories and Subject Descriptors. Data Appl. Secur. Priv. 2012, 157–168. [Google Scholar] [CrossRef]
- Rajbhandari, L.; Snekkenes, E.A. Using game theory to analyze risk to privacy: An initial insight. In Privacy and Identity Management for Life; Springer: Berlin/Heidelberg, Germany, 2011; pp. 41–51. [Google Scholar]
- Sharma, M.; Bai, Y.; Chung, S.; Dai, L. Using risk in access control for cloud-assisted ehealth. In Proceedings of the 2012 IEEE 14th International Conference on High Performance Computing and Communication & 2012 IEEE 9th International Conference on Embedded Software and Systems, Liverpool, UK, 25–27 June 2012; pp. 1047–1052. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B.; Daniel, J. Developing an adaptive Risk-based access control model for the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; pp. 655–661. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Hussein, R.K.; Wills, G.B. Validation of an Adaptive Risk-based Access Control Model for the Internet of Things. Int. J. Comput. Netw. Inf. Secur. 2018, 10, 26–35. [Google Scholar] [CrossRef]
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B. An overview of risk estimation techniques in risk-based access control for the internet of things. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017. [Google Scholar]
- Molloy, I.; Cheng, P.C.; Rohatgi, P. Trading in risk: Using markets to improve access control. In Proceedings of the New Security Paradigms Workshop, Oxford, UK, 8–11 September 2009; pp. 107–125. [Google Scholar]
- Babu, B.M.; Bhanu, M.S. Prevention of Insider Attacks by Integrating Behavior Analysis with Risk based Access Control Model to Protect Cloud. Procedia Comput. Sci. 2015, 54, 157–166. [Google Scholar] [CrossRef]
- Clark, J.A.; Tapiador, J.E.; McDermid, J.; Cheng, P.-C.; Agrawal, D.; Ivanic, N.; Slogget, D. Risk based access control with uncertain and time-dependent sensitivity. In Proceedings of the 2010 International Conference on Security and Cryptography (SECRYPT), Athens, Greece, 26–28 July 2010. [Google Scholar]
- Helil, N.; Kim, M.; Han, S. Trust and risk based access control and access control constraints. KSII Trans. Internet Inf. Syst. 2011, 5, 2254–2271. [Google Scholar] [CrossRef]
- Badar, N.; Vaidya, J.; Atluri, V.; Shafiq, B. Risk based access control using classification. In Automated Security Management; Springer International Publishing: Cham, Switzerland, 2013; pp. 79–95. [Google Scholar]
- Metoui, N.; Bezzi, M.; Armando, A. Trust and risk-based access control for privacy preserving threat detection systems. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2016; Volume 10018 LNCS, pp. 285–304. [Google Scholar]
- Chun, S.A.; Atluri, V. Risk-Based Access Control for Personal Data Services. In Algorithms, Architectures and Information Systems Security; World Scientific: Sinagapore, 2008; pp. 263–283. [Google Scholar]
- Rahmati, A.; Fernandes, E.; Eykholt, K.; Prakash, A. Tyche: A risk-based permission model for smart homes. In Proceedings of the 2018 IEEE Cybersecurity Development Conference, SecDev 2018, Cambridge, MA, USA, 30 September–2 October 2018; pp. 29–36. [Google Scholar]
- Metoui, N.; Bezzi, M.; Armando, A. Risk-based privacy-aware access control for threat detection systems. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2017; Volume 10720 LNCS, pp. 1–30. [Google Scholar]
- Burnett, C.; Chen, L.; Edwards, P.; Norman, T.J. TRAAC: Trust and risk aware access control. In Proceedings of the 2014 Twelfth Annual International Conference on Privacy, Security and Trust, Toronto, ON, Canada, 23–24 July 2014; pp. 371–378. [Google Scholar]
- Dankar, F.K.; Badji, R. A risk-based framework for biomedical data sharing. J. Biomed. Inform. 2017, 66, 231–240. [Google Scholar] [CrossRef]
- Abomhara, M.; Koien, G.; Oleschchuk, V.; Hamid, M. Towards Risk-aware Access Control Framework for Healthcare Information Sharing. In Proceedings of the 4th International Conference on Information Systems Security and Privacy, Funchal, Madeira, Portugal, 22–24 January 2018; pp. 312–321. [Google Scholar]
- Armando, A.; Bezzi, M.; Di Cerbo, F.; Metoui, N. Balancing trust and risk in access control. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2015; Volume 9415, pp. 660–676. [Google Scholar]
- Chen, L.; Crampton, J. Risk-aware role-based access control. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2012; Volume 7170 LNCS, pp. 140–156. [Google Scholar]
- Atlam, H.F.; Walters, R.J.; Wills, G.B.; Daniel, J. Fuzzy Logic with Expert Judgment to Implement an Adaptive Risk-Based Access Control Model for IoT. Mob. Netw. Appl. 2019, 1–13. [Google Scholar] [CrossRef]
- Luo, J.; Ni, X.; Yong, J. A trust degree based access control in grid environments. Inf. Sci. N. Y. 2009, 179, 2618–2628. [Google Scholar] [CrossRef]
- Habib, K.; Leister, W. Context-Aware Authentication for the Internet of Things. In Proceedings of the Eleventh International Conference on Autonomic and Autonomous Systems Fined, Rome, Italy, 24–29 May 2015; pp. 134–139. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).