Abstract
As advancements in autonomous underwater vehicle (AUV) technology unfold, the role of underwater wireless sensor networks (UWSNs) is becoming increasingly pivotal. However, the high energy consumption in these networks can significantly reduce their operational lifespan, while latency issues can impair overall network performance. To address these challenges, a novel mixed packet forwarding strategy is developed, which incorporates a wakeup threshold and a dynamically adjusted access probability for the cluster head (CH). This approach aims to conserve energy while maintaining acceptable network latency levels. The wakeup threshold restricts the frequency of state switching for the CH, thereby reducing energy consumption. Meanwhile, the dynamic access probability regulates the influx of packets to mitigate system congestion based on current network conditions. Furthermore, to accommodate the network’s varied transmission demands, packets generated by sensor nodes (SNs) are categorized into two types according to their sensitivity to latency. A discrete−time queueing model with preemptive priority is then established to evaluate the performance of different packets and the CH. Numerical results show how different parameters affect network performance and demonstrate that the proposed mixed packet forwarding mechanism can effectively manage the trade−off between latency and energy consumption, outperforming the traditional mechanism within a specific range of parameters.
1. Introduction
Underwater wireless sensor networks (UWSNs) are network systems that deploy sensor nodes (SNs) in underwater environments and achieve data collection and transmission through acoustic communication, which hold broad application prospects in various fields such as ocean monitoring, resource exploration, environmental research, submarine pipeline monitoring, disaster warning, and military applications [1,2,3]. With the increasing emphasis on marine resources, the research and application of UWSNs are receiving more and more attention.
For the current research, there are mainly three structures: two−dimensional static UWSNs, three−dimensional static UWSNs, and three−dimensional UWSNs integrated with autonomous underwater vehicles (AUVs) [4]. The two−dimensional UWSN is limited to collecting data from a specific area of the seafloor. In contrast, the three−dimensional UWSN allows for the modulation of sensor node depths to gather oceanic data across various depths. The structure of the three−dimensional static UWSN is similar to that of the three−dimensional UWSNs equipped with AUVs, with the key difference being the substitution of stationary sensor nodes with mobile AUVs in the latter. This three−dimensional UWSN, enhanced by AUVs, represents an advancement over static networks, potentially boosting the communication capabilities of UWSNs. However, deploying these three−dimensional UWSN structures is challenging, and they are susceptible to damage due to the unique characteristics of underwater environments. Therefore, existing research mostly focuses on the two−dimensional static UWSN structure.
Energy consumption optimization is a core and urgent issue that needs to be addressed in UWSNs. Because SNs are typically deployed in environments that are difficult to access physically, such as deep−sea or remote water areas, the initial configuration of batteries often limits the energy supply of these nodes, and it is difficult to carry out subsequent energy replenishment or replacement [5,6,7]. Therefore, the energy consumption of SNs directly determines the lifecycle and stability of the network, and the development of energy−saving technologies is particularly crucial. Cluster structure is the most efficient energy−saving method in UWSNs, whose core principle is to organize a large number of SNs into clusters [8]. Each cluster is led by a cluster head (CH), responsible for coordinating and managing the data collection, processing, and transmission of nodes within the cluster [9].
In actual underwater network environments, data sensitivity to transmission latency often varies [10]. Sudden events in environmental monitoring (such as ocean pollution spills, early warning of natural disasters, etc.) usually require more rapid forwarding. In contrast, information with lower time sensitivity (such as long−term climate trend analysis and monitoring of periodic changes in ecosystems) can tolerate a certain degree of latency. Therefore, designing a reasonable data classification mechanism can more intelligently allocate limited resources and improve the network’s overall performance.
Congestion control is particularly important and regarded as one of the most significant challenges [11,12]. Congestion not only reduces network throughput but may also lead to packet loss, affecting the reliability and stability of the network. Frequent retransmissions consume valuable energy from nodes, accelerating their energy depletion and shortening the network’s lifespan. Therefore, it is necessary to introduce reasonable congestion control mechanisms, dynamically adjust data transmission, balance network loads, and avoid or reduce congestion.
This paper proposes a mixed packet forwarding mechanism with a priority schedule based on dynamic access probability and wakeup threshold. The wakeup threshold controls the system’s state switching and saves system energy consumption. The dynamic access probability controls packet access based on the system’s implementation status, reducing system congestion. The following are the primary contributions of this paper.
- 1.
- A mixed packet forwarding mechanism is suggested to satisfy the diversity needs of data transmission while balancing average latency and network energy consumption.
- 2.
- A three−dimensional Markov−chain (3DMC) model with preemptive priority is established to evaluate the performance of the proposed mechanism.
- 3.
- Numerical results show how various parameters affect system performance and how effective the proposed method is.
The remainder of the paper is structured as below. In Section 2, we review the relevant literature. We provide a mechanism description and modeling analysis of the forwarding mechanism with priority scheduling based on dynamic access probability and wakeup threshold in Section 3. The performance expressions for two different priority packets and the CH are given in Section 4. In Section 5, we analyze how various parameters affect system performance through numerical results and evaluate the effectiveness of the proposed mechanism in balancing average latency and energy consumption. In Section 6, we summarize our work. The complementary probability event is expressed using the overbar mark, and Table 1 displays the symbols used in this paper along with their meanings.

Table 1.
Symbols and corresponding meanings.
2. Related Works
In UWSNs, queueing theory is widely used to analyze network performance and optimize network topology [13,14,15]. In [13], a data acquisition method was proposed based on the queueing model and the genetic algorithm for underwater acoustic collaborative sensor networks. This method modeled the process of each SN sending packets to the CH as a single service station hybrid M/M/1/K queueing model. The results demonstrated that this method could effectively reduce packet loss rate. In [14], a latency−sensitive underwater wireless optical network was analyzed. An M/G/1 queueing model was constructed to quantify the system performance, and the end−to−end latency and blocking rate were evaluated in different scenarios through the numerical results. In [15], a number of charging strategies were suggested for three−dimensional charging UWSNs. An M/G/1 queueing model was used to simulate the energy mule charging process. The proposed scheme was verified through simulation experiments to be energy−saving and time−saving and to guarantee the efficient use of resources. The above literature adopted the continuous−time queueing theory for modeling. However, we observe that the digital features of contemporary network communication are better suited to the discrete−time queueing theory [16].
Sleep/wakeup mode is an effective energy−saving strategy to improve network lifetime. Due to the limited energy of underwater SNs, the network’s lifespan can be extended significantly by reasonably arranging the wakeup and sleep states of nodes. In [17], an adaptive sleep/wakeup scheduling method was proposed. The timeline was divided into multiple time slots, and each node was allowed to autonomously decide whether to sleep, listen, or send in one−time slot. In [18], a three−dimensional space−moving target tracking method based on the Kalman filter was proposed, and the sleep/wakeup strategy was used to save the system’s energy consumption. In this method, only part of the nodes closer to the target path would be woken up and participate in the tracking. The simulation results demonstrated that the average energy consumption could be reduced effectively. These studies designed different sleep/wake modes for application scenarios to balance energy consumption and performance, but they did not limit the switching between the two states. We note that switching between the sleep and wakeup states also takes a lot of energy and time, so this paper introduces a wakeup threshold to reduce the frequency of state switching [19]. In the wakeup threshold mechanism, wakeup is performed after a certain amount of information has been accumulated, which will also increase the average latency to a certain extent. Therefore, it is necessary to introduce a reasonable access control mechanism to mitigate this adverse effect.
The tail−drop method is the default congestion management technique for wireless networks, which adopts the principle of first−come−first−serve. When the cache is full, newly arrived packets will be dropped directly [20]. This method can only react when congestion occurs in the system, and cannot prevent congestion from occurring. Random early detection (RED) is a widely used method of queue management that can effectively prevent system congestion [21,22]. In [23], a variety of queueing models were established and analyzed according to whether there were RED and tail−drop mechanisms or priority packets. Numerical results showed that dividing packets into multiple priorities could improve the quality of service of the network, and the introduction of RED and tail−drop mechanisms could effectively alleviate congestion. However, this RED method required two thresholds (minimum and maximum thresholds) and a maximum probability for joint regulation, which is more complex to implement. In [24], considering the ignorance of queue information, a probabilistic access method for wireless sensor networks was proposed to control system congestion. When a sensor was in the sleep state, it received newly arrived packets with probability p; when it was in the wakeup state, it received the newly arrived packets with probability q. Based on this strategy, a Markov−chain model was constructed, and numerical results verified its effectiveness. However, this method of using a fixed value as the access probability was difficult to adapt to the changing network environment. In [25], an access control strategy with a dynamic access threshold was proposed. A reasonable dynamic access threshold was set according to different packet arrival rates to constrain the access behavior of packets. Numerical experiments verified the effectiveness of the strategy in energy saving. This method was similar to the wakeup threshold used in this paper; however, if congestion is to be effectively avoided, other mechanisms need to be introduced to regulate it. Therefore, we propose a dynamic access probability mechanism that will reduce access probability when many packets are retained in the system based on the influence of real−time queue length rather than the packet arrival rate. Compared with the RED method used in literature [23], the dynamic access probability mechanism used in this paper requires fewer control parameters and is simpler to implement. Compared with the fixed access probability method in [24], the dynamic access probability mechanism is more suitable for dynamically changing network environments. Compared with the method in [25], our method can alleviate congestion further.
In summary, this paper studies the packet forwarding mechanism of the CH in UWSNs with different latency sensitivities. Taking into account the trade−off between latency and energy consumption, wakeup threshold and dynamic access probability are introduced to control the CH’s state switching and packet access behavior, respectively. By constructing a discrete−time queueing model, we provide a performance analysis and energy consumption evaluation method to effectively balance energy consumption and latency. The novelty of this paper is summarized as follows:
- 1.
- A packet grading mechanism with preemptive priority is proposed to satisfy the diversified latency tolerance of packets.
- 2.
- A hybrid packet forwarding mechanism is proposed to effectively balance latency and energy consumption.
- 3.
- A new performance quantitative analysis method using discrete−time queueing theory is provided.
3. System Model
3.1. Mechanism Description
Figure 1 shows the architecture of the UWSN considered in this paper.

Figure 1.
The UWSN architecture we considered in this paper [26].
As shown in Figure 1, we consider a homogeneous UWSN consisting of three types of nodes: the base station (BS), SNs, and CHs. Each SN or CH has the same physical characteristics and operating mode. SNs are cheaper and have less energy than CHs, which cannot directly communicate with the BS. CHs have more energy and gather packets sent by SNs and forward them to the BS.
SNs can generate two types of packets based on different perceived environmental content: emergency packets and non−emergency packets. The information carried by emergency packets is highly urgent and requires timely transmission to the BS. Non−emergency packets have lower real−time transmission requirements and can tolerate significant queueing delays. Therefore, emergency packets are given higher priority and can preempt non−emergency packets’ cluster head forwarding rights. Considering that the packets generated by each SN arrive at each CH without discrimination, we mainly focus on analyzing a single CH system to evaluate the overall performance of this architecture.
Figure 2 describes the packet forwarding mechanism in the system.

Figure 2.
The packet forwarding mechanism.
In Figure 2, considering the high sensitivity of emergency packets to latency and the high throughput requirements of non−emergency packets, a cache with capacity is set for only non−emergency packets. However, suppose many non−emergency packets are stuck in the system. In that case, it may reduce the forwarding performance and make the waiting packets lose their timeliness. Therefore, an access control mechanism is introduced to determine whether non−emergency packets can enter the cache. Non−emergency packets will dynamically change their access probability based on the amount of packets. The more packets there are, the less likely the incoming non−emergency packets can access the system. The access probability f is expressed as follows.
where N is the amount of packets, is the minimum value of f, and K is the cache size. Due to the fact that the cache can hold up to K packets and the CH can hold one packet, N will not exceed .
For the sake of simplicity, let and refer to as the adjustment factor of f. Therefore, the access probability f can be succinctly expressed as follows.
We define the packet forwarding process by the CH as the working state; otherwise, it is defined as the sleep state. When the CH is in sleep state, it can be regarded as a cache space that can only hold one packet rather than forward it. Considering that the transition of the CH from the sleep state to working state requires a significant amount of energy consumption, a wakeup control mechanism controlled by a wakeup threshold is introduced to reduce the state switching frequency of the CH. The setting of H cannot exceed the cache size K, so that the system can accumulate H non−emergency packets before being awakened, thereby reducing the frequency of state switching. Only when the CH is in the working state or the amount of non−emergency packets in the cache reaches H will the CH forward the non−emergency packets in the cache. On the contrary, once emergency packets arrive at the CH, the CH will forward them directly. Based on the wakeup control mechanism, the state swtching process of the CH can be described in Figure 3.

Figure 3.
The state switching mechanism of the CH.
Combining Figure 2 and Figure 3, we can summarize the access and forwarding behavior of two kinds of packets in each time slot as Figure 4.

Figure 4.
The access and forwarding behavior of two kinds of packets in each time slot.
As shown in Figure 4, when there is an incoming emergency packet, if the CH is in the sleep state at this time, this emergency packet will directly access the CH for data forwarding and the CH will enter working state (if the CH stores a non-emergency packet at this time, this non-emergency will be preempted). If the CH is in the working state and the forwarded packet is a non−emergency packet at this time, this incoming emergency packet will preempt the forwarding priority of the non−emergency packet, and the interrupted non−emergency packet returns to the start of the cache to wait for further forwarding when there is a space in the cache; if the CH is in the working state at this time and the forwarded packet is an emergency packet, the incoming emergency packet will be blocked and discarded. To sum up, as long as there is an emergency packet in the system, the CH will enter the working state.
When there is an incoming non−emergency packet in the system, this non−emergency packet will access the end of the cache with access probability f to wait for data forwarding if there is a space in the cache. Otherwise, it will be discarded. Moreover, if other packets do not occupy the CH, the non−emergency packet at the start of the cache will access the CH (if the CH is still in sleep mode at this time, it only temporarily stores the non−emergency packet without forwarding; if the CH is in working state, the non−emergency packet in the CH will be forwarded directly). If the CH is in the sleep state and the amount N of packets in the cache reaches H, the CH will switch to the working state and begin to forward this packet; otherwise, the non−emergency packets in the system will wait for next forwarding chance. To sum up, the access probability f only controls the possibility of non−emergency packets accessing the system. Whether the CH can switch from the sleep state to the working state depends on whether the number N of non−emergency packets in the system exceeds the wakeup threshold H.
3.2. Model Building
In UWSNs, random events (such as temperature change, humidity change, object movement, etc.) perceived by SNs occur randomly. The occurrence of these events can be regarded as a random process, and its probability distribution can be used to describe the frequency of occurrence of events. When these events are perceived by the SNs and packets are generated, the arrival of packets is also random. Therefore, we assume that the arrival process of packets is a Bernoulli process. Specifically, the Bernoulli process is a simple stochastic process in which the occurrence or absence of events within each time interval is independent, and the probability of events occurring within each time interval is constant. In this way, we can more accurately analyze and optimize the performance of UWSNs, ensuring that the network can efficiently process and transmit the perceived event information.
We divide the time axis into infinite time slots with the same interval, expressed as . We assume that arrival intervals of emergency and non−emergency packets follow the geometric distribution, and the arrival rates are and , respectively. The forwarding time of the CH for emergency and non−emergency packets follows geometric distribution, and the service rates are and . Based on the regulation of the Early Arrival System, the packet arrival event and departure occur at the start and end of each time slot, respectively [27]. Let , and , where i, j, and k are three state−variables, represents the amount of total packets in the system at time , represents the amount of emergency packets in the system at time , and represents the state of the CH at time . When , it indicates that the CH is in the sleep state; otherwise, when , it indicates that the CH is in the working state. Then constitutes a 3DMC with state space , and is expressed as follows.
According to the structure of the state space , we can obtain that there are states in the system. We mark as the one−step transition probability matrix of the 3DMC, and can be expressed by block matrices as follows based on the change of the amount of total packets in the one−step transition.
We will give each block matrix in detail, where m and n represent the amount of total packets before and after the one−step transition.
- 1.
- When , it indicates that the amount of packets is zero before the one−step transition, and the transition submatrices are given as follows.
- 2.
- When and , due to the special dimension of the submatrix, its form is given as follows.
- 3.
- When and , is expressed as follows.
- 4.
- When and , is expressed as follows.
- 5.
- When and , is expressed as follows.
- 6.
- When and , is expressed as follows.
- 7.
- When and , is expressed as follows.
- 8.
- When and , is expressed as follows.
- 9.
- When , is expressed as follows.
All submatrices have been discussed, and the transition probability matrix can be further obtained. We define as the steady−state probability distribution of the 3DMC, and is expressed as follows.
We can further define the steady−state vector as follows.
According to the structure of the matrix , the 3DMC is irreducible, aperiodic, and normally recurrent. Based on the equilibrium equation and normalization condition [28], we can obtain the following equations.
where is a column vector with all 1 s. A numerical calculation method [29] for calculating the equations above is provided in Table 2.

Table 2.
The procedures for solving .
4. Performance Metrics
4.1. Performance Metrics for Emergency Packets
4.1.1. Emergency Packets’ Blocking Rate
When an emergency packet arrives, if other emergency packets occupy the CH at this time, the incoming emergency packet will be blocked. Emergency packets’ blocking rate is expressed as follows.
4.1.2. Emergency Packets’ Throughput
Emergency packets’ throughput is the amount of emergency packets forwarded completely in a unit time slot, expressed as follows.
4.2. Performance Metrics for Non−Emergency Packets
When an incoming non−emergency packet voluntarily leaves the system with probability or requests access with probability f while the system has no vacancies, this incoming non−emergency packet will be blocked. Non−emergency packets’ blocking rate is expressed as following two situations.
- 1.
- If , is expressed as follows.
- 2.
- If , is expressed as follows.
When a non−emergency packet is interrupted, the interrupted packet will be discarded if there are no available spaces in the cache. Non−emergency packets’ outage and loss rate is expressed as follows.
Non−emergency packets’ throughput is the amount of emergency packets forwarded completely in a unit time slot, expressed as follows.
Non−emergency packets’ average latency refers to the time interval between non−emergency packets entering and leaving the system. According to Little’s formula [28], is expressed as following two situations.
- 1.
- If , is expressed as follows.
- 2.
- If , is expressed as follows.
4.3. Performance Metrics for State Switching and Energy Consumption
The state switching rate is the amount of times the CH state switches in a unit time slot, expressed as following two situations.
- 1.
- If , is expressed as follows.
- 2.
- If , is expressed as follows.
The definition of energy consumption E is the energy consumed by the CH per unit time slot. Considering that the state switching of the CH requires a certain amount of energy to complete, the energy consumption E of the CH is expressed in the following two situations.
- 1.
- If , is expressed as follows.
- 2.
- If , is expressed as follows.
where is the energy consumption in a unit time slot for keeping the CH in the sleep state; is the energy consumption for changing the CH from the sleep state to working state; is the energy consumption for changing the CH from the working state to sleep state; and is the energy consumption for keeping the CH in the working state.
5. Numerical Results
5.1. Performance Analysis
To evaluate how various parameters affect the system’s performance, numerical experiments are conducted to obtain various performance index figures. In the numerical experiments, the fixed parameters are displayed in Table 3. Other dynamic parameters are displayed in the legends, while the wakeup threshold H is set as the horizontal axis parameter.

Table 3.
The fixed parameters of the experiments for performance analysis.
5.1.1. Performance Analysis for Emergency Packets
Figure 5 and Figure 6 show the changing trends in emergency packets’ blocking rate and throughput under the proposed mixed mechanism.
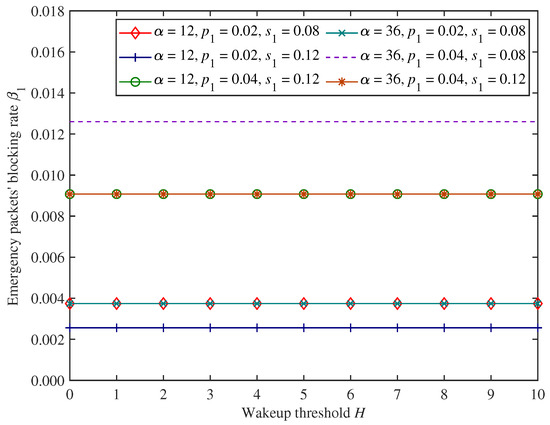
Figure 5.
The changing trends in emergency packets’ blocking rate.

Figure 6.
The changing trends in emergency packets’ throughput.
As shown in Figure 5 and Figure 6, when the wakeup threshold H and adjustment factor change, emergency packets’ blocking rate and throughput remain unchanged. This is because the wakeup threshold and dynamic access probability control the access and forwarding process for only non−emergency packets, and the system behaviour of non−emergency packets cannot affect emergency packets, which have preemptive priority. It also indicates that the proposed mixed mechanism can ensure the comprehensive forwarding performance of emergency packets.
In Figure 5 and Figure 6, we can find that as emergency packets’ arrival rate increases, emergency packets’ blocking rate and throughput also increase under the parameter settings of this experiment. This is because the CH can forward a greater number of emergency packets if the arrival rate of emergency packets is higher, and emergency packets’ throughput will be larger. However, the forwarding efficiency of the CH is constant, and there will also be more incoming emergency packets that cannot access the CH.
Moreover, in Figure 5 and Figure 6, when emergency packets’ service rate increases, emergency packets’ blocking rate decreases, and the throughput increases under the parameter settings of this experiment. This is because the higher the emergency packets’ service rate, the more emergency packets can be forwarded completely by the CH per unit of time, and the corresponding number of non−emergency packets that the CH can forward increases, so emergency packets’ throughput will increase. This also provides more opportunities for emergency packets to access CH for data forwarding and reduces their blocking rate.
5.1.2. Performance Analysis for Non−Emergency Packets
Figure 7, Figure 8 and Figure 9 show the change trends in non−emergency packets’ blocking rate , throughput , and average latency under the proposed mixed mechanism.

Figure 7.
The changing trends in non−emergency packets’ blocking rate.

Figure 8.
The changing trends in non−emergency packets’ throughput.

Figure 9.
The changing trends in non−emergency packets’ average latency.
In Figure 7, Figure 8 and Figure 9, as the wakeup threshold H increases, non−emergency packets’ blocking rate and average latency show an upward trend. In contrast, the throughput shows a downward trend under the parameter settings of this experiment. This is because as the wakeup threshold increases, the CH will start forwarding non−emergency packets only when the amount of non−emergency packets stuck in the system increases. The number of successfully forwarded non−emergency packets per unit time decreases, resulting in a decrease in throughput. At the same time, more non−emergency packets are stuck in the cache, and the possibility of the cache being full is also higher, so the blocking rate and average latency both increase.
Moreover, in Figure 7, Figure 8 and Figure 9, when the adjustment factor increases, non−emergency packets’ blocking rate decreases, while throughput and average latency increase under the parameter settings of this experiment. This has to do with the fact that dynamic access probability f is the probability of allowing non−emergency packets to access the system dynamically based on the load, and the larger the adjustment factor , the higher the dynamic access probability. Therefore, the amount of non−emergency packets that voluntarily abandon access to the system for forwarding decreases, resulting in a corresponding decrease in blocking rate and an increase in throughput. At the same time, a large number of non−emergency packets are stuck in the cache after accessing the system, increasing average latency.
In addition, from Figure 7, Figure 8 and Figure 9, when emergency packets’ arrival rate increases, non−emergency packets’ blocking rate and average latency also increase under the parameter settings of this experiment and throughput decreases. This is because, in this situation, the CH is more likely to be occupied by emergency packets, while a large number of non−emergency packets are stuck in the cache waiting to be forwarded, resulting in an increase in blocking rate and average latency and a decrease in throughput. Similarly, emergency packets’ service rate has an opposite impact on the forwarding performance of non−emergency packets compared with the arrival rate.
5.1.3. Performance Analysis for State Switching and Energy Consumption
Figure 10 and Figure 11 show the change trends in the state switching rate and energy consumption E under the proposed mixed mechanism.

Figure 10.
The changing trends in state switching rate of the CH.

Figure 11.
The changing trends in energy consumption of the CH.
In Figure 10 and Figure 11, we can find that as the wakeup threshold H increases, the state switching rate and energy consumption E of the CH show decreasing trends under the parameter settings of this experiment. This is because the wakeup threshold constrains the conditions for the CH to switch from sleep state to working state. The larger the wakeup threshold, the more time the CH will remain in the sleep state, resulting in a lower state switching rate and energy consumption.
Moreover, in Figure 10 and Figure 11, under the parameter settings of this experiment, increasing the adjustment factor will reduce the state switching rate while increasing energy consumption instead. According to the definition of access probability, the larger the adjustment factor, the greater the possibility of allowing non−emergency packets to access the CH. At this time, the CH remains in the working state for a longer period of time, reducing the possibility of switching to the sleep state, thereby reducing the state switching rate and increasing energy consumption. Similarly, increasing emergency packets’ arrival rate or decreasing service rate shows the same trends on state switching rate and energy consumption.
5.2. Performance Comparison
To evaluate the effectiveness of the proposed mixed mechanism, a performance comparison experiment is conducted between the proposed mixed mechanism and existing mechanisms using numerical results. We compare non−emergency packets’ average latency, state switching rate, and energy consumption with respect to whether to use the wakeup threshold mechanism [19] or the dynamic access probability mechanism (which can be regarded as a variation of the RED [23] method where the minimum threshold is 0 and maximum threshold is equal to the cache size K). Due to the adjustability of the proposed mixed mechanism, the existing mechanisms for comparison can be obtained by changing the values of the adjustment factor and wakeup threshold H. The differences between contrast mechanisms are shown in Table 4. The parameter settings of different mechanisms are shown in Table 5, and other fixed parameters are shown in Table 6.

Table 4.
Differences between contrast mechanisms.

Table 5.
The values of adjustment factor and wakeup threshold under different mechanisms.

Table 6.
The fixed parameters of the experiment for performance comparison.
Figure 12, Figure 13 and Figure 14 show the performance comparison of non−emergency packets’ average latency , state switching rate , and energy consumption E of the CH under different mechanisms.

Figure 12.
Comparison for non−emergency packets’ average latency.

Figure 13.
Comparison for switching rate of the CH.

Figure 14.
Comparison energy consumption of the CH.
From Figure 12 and Figure 13, compared with the traditional mechanism, introducing an access probability mechanism can effectively reduce the non−emergency packets’ average latency, but this will also increase the state switching rate of the CH accordingly. On the contrary, introducing a wakeup threshold mechanism can reduce the state switching rate of the CH but also increase non−emergency packets’ average latency. Therefore, introducing a single mechanism cannot effectively balance these two performance indexes.
Moreover, in Figure 12, Figure 13 and Figure 14, under the parameter settings of this experiment, the performance of the traditional mechanism of the CH shows a polarized trend when the non−emergency packets arrival rate is at a low level and high level. With the increase in non−emergency packets’ arrival rate, the state switching rate of the CH shows a drastic change. The mixed mechanism proposed in this paper has relatively smooth trends for these two performance indexes and is more stable under different packet loads. (We use range to express the difference between the maximum value and the minimum value. The range of under the traditional mechanism is approximately 92.630, while the range of under the proposed mechanism is approximately 26.706; the range of under traditional mechanism is approximately 0.058, while the range of under the proposed mechanism is approximately 0.041). In addition, within a certain range (for example, when ), non−emergency packets’ average latency and state switching rate of the CH under the mixed mechanism are both lower than those under the traditional mechanism.
In Figure 14, we can see that both the access probability mechanism and the wakeup threshold mechanism can save system energy, and the energy consumption of the proposed mechanism, which introduces both mechanisms, is the lowest. This also demonstrates the effectiveness of the mixed mechanism proposed in this paper for energy conservation.
In summary, compared to using only the access probability mechanism or wakeup threshold mechanism, the mixed mechanism proposed in this paper can effectively balance non−emergency packets’ latency and state switching rate of the CH. Compared with the traditional mechanism, the mixed mechanism proposed in this paper has stronger stability in performance under different packet loads. Within a certain load range, the proposed mixed mechanism outperforms traditional mechanisms in both latency and state switching rate.
6. Conclusions
To effectively balance the latency and energy consumption performance while meeting the diverse transmission needs of data in UWSNs, we proposed a mixed packet forwarding strategy based on wakeup threshold and dynamic access probability with priority scheduling for CHs. We derived a series of system performance index expressions by constructing a discrete−time queueing model with preemptive priority. We provided numerical results and analyzed how various parameters affected network performance. By comparing with the traditional mechanism, access probability mechanism, and wakeup threshold mechanism, we objectively analyzed the superiority of the proposed mixed mechanism. The numerical results indicated that compared with the traditional mechanism, the mixed mechanism proposed in this paper was less affected by network load in terms of latency and energy consumption (for example, the range of under traditional mechanism is approximately 92.630, while the range of under the proposed mechanism is approximately 26.706; the range of under traditional mechanism is approximately 0.058, while the range of under the proposed mechanism is approximately 0.041), and performs better than traditional mechanisms within a specific parameter range (for example, when ). Compared with the single access probability mechanism and wakeup threshold mechanism, the mixed mechanism could effectively balance latency and energy consumption performance.
In this paper, we assume that the arrival process of packets is a single−input process that obeys the geometric distribution, and in future work, we can further construct a parallel−input queueing model to analyze the network performance with multiple sensor nodes, so as to improve the accuracy of the model. In addition, in this paper, our numerical results are derived from the ideal environment. In future work, we will consider non−ideal conditions such as forwarding failures or mistakes, and further build a queueing model that is more in line with the actual network environment. Moreover, this paper only divides the CH into two states (sleep/working mode). In future research, we will consider further dividing it into multi−state mode (such as sleep/idle/working mode [30]) according to the actual environment to improve the accuracy of our model.
Author Contributions
Conceptualization, N.L.; Methodology, Z.X.; Validation, J.L.; Formal analysis, Z.G.; Resources, L.F.; Project administration, H.G.; Funding acquisition, L.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Independent Project deployed by Innovative Academy of Marine Information Technology, Chinese Academy of Sciences (No. CXBS202102).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All relevant data are within the paper.
Conflicts of Interest
The authors declare that there are no conflicts of interest regarding the publication of this manuscript.
References
- Khan, M.U.; Otero, P.; Aamir, M. Underwater Acoustic Sensor Networks (UASN): Energy Efficiency Perspective of Cluster-Based Routing Protocols. In Proceedings of the 2022 Global Conference on Wireless and Optical Technologies (GCWOT), Malaga, Spain, 14–17 February 2022; pp. 1–6. [Google Scholar]
- Tian, W.; Zhao, Y.; Hou, R.; Dong, M.; Ota, K.; Zeng, D.; Zhang, J. A centralized control-based clustering scheme for energy efficiency in underwater acoustic sensor networks. IEEE Trans. Green Commun. Netw. 2023, 7, 668–679. [Google Scholar] [CrossRef]
- Khalid, M.; Ullah, Z.; Ahmad, N.; Arshad, M.; Jan, B.; Cao, Y.; Adnan, A. A survey of routing issues and associated protocols in underwater wireless sensor networks. J. Sens. 2017, 2017, 7539751. [Google Scholar] [CrossRef]
- Luo, J.; Chen, Y.; Wu, M.; Yang, Y. A survey of routing protocols for underwater wireless sensor networks. IEEE Commun. Surv. Tutorials 2021, 23, 137–160. [Google Scholar] [CrossRef]
- Murgod, T.R.; Sundaram, S.M.; Manchaiah, S.; Kumar, S. Priority based energy efficient hybrid cluster routing protocol for underwater wireless sensor network. Int. J. Electr. Comput. Eng. (IJECE) 2023, 13, 3161–3169. [Google Scholar] [CrossRef]
- Sun, Y.; Zheng, M.; Han, X.; Li, S.; Yin, J. Adaptive clustering routing protocol for underwater sensor networks. Ad Hoc Netw. 2022, 136, 102953. [Google Scholar] [CrossRef]
- Liu, G.; Yan, S.; Mao, L. Receiver-Only-Based Time Synchronization Under Exponential Delays in Underwater Wireless Sensor Networks. IEEE Internet Things J. 2020, 7, 9995–10009. [Google Scholar] [CrossRef]
- Gomathi, R.; Manickam, J.M.L.; Sivasangari, A.; Ajitha, P. Energy efficient dynamic clustering routing protocol in underwater wireless sensor networks. Int. J. Netw. Virtual Organ. 2020, 22, 415–432. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An efficient metaheuristic-based clustering with routing protocol for underwater wireless sensor networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef] [PubMed]
- Raina, V.; Jha, M.K.; Bhattacharya, P.P. The Alive-in-Range Medium Access Control Protocol to Optimize Queue Performance in Underwater Wireless Sensor Networks. J. Telecommun. Inf. Technol. 2017, 4, 31–46. [Google Scholar] [CrossRef]
- Domingo, M.C. Marine communities based congestion control in underwater wireless sensor networks. Inf. Sci. 2013, 228, 203–221. [Google Scholar] [CrossRef]
- Goyal, N.; Dave, M.; Verma, A.K. Congestion control and load balancing for cluster based underwater wireless sensor networks. In Proceedings of the 2016 Fourth International Conference on Parallel, Distributed and Grid Computing (PDGC), Waknaghat, India, 22–24 December 2016; IEEE: New York, NY, USA, 2016; pp. 462–467. [Google Scholar]
- Luo, Y.; Dong, Y.; Zhu, X.; Chen, Y.; Wu, J. AUV-Assisted Data Collection Based on Queuing Theory and Genetic Algorithm for Underwater Acoustic Cooperative Sensor Networks. In Proceedings of the 2023 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Zhengzhou, China, 14–17 November 2023; IEEE: New York, NY, USA, 2023; pp. 1–5. [Google Scholar]
- Al-Halafi, A.; Alghadhban, A.; Shihada, B. Queuing Delay Model for Video Transmission Over Multi-Channel Underwater Wireless Optical Networks. IEEE Access 2019, 7, 10515–10522. [Google Scholar] [CrossRef]
- Lin, C.; Wang, K.; Chu, Z.; Wang, K.; Deng, J.; Obaidat, M.S.; Wu, G. Hybrid charging scheduling schemes for three-dimensional underwater wireless rechargeable sensor networks. J. Syst. Softw. 2018, 146, 42–58. [Google Scholar] [CrossRef]
- Alfa, A.S. Queueing Theory for Telecommunications: Discrete Time Modelling of a Single Node System; Springer: New York, NY, USA, 2010. [Google Scholar]
- Ye, D.; Zhang, M. A Self-Adaptive Sleep/Wake-Up Scheduling Approach for Wireless Sensor Networks. IEEE Trans. Cybern. 2018, 48, 979–992. [Google Scholar] [CrossRef] [PubMed]
- Poostpasand, M.; Javidan, R. An adaptive target tracking method for 3D underwater wireless sensor networks. Wirel. Netw. 2018, 24, 2797–2810. [Google Scholar] [CrossRef]
- Zhang, C.; Yang, J.; Wang, N. An active queue management for wireless sensor networks with priority scheduling strategy. J. Parallel Distrib. Comput. 2024, 187, 104848. [Google Scholar] [CrossRef]
- Abualhaj, M.M.; Abu-Shareha, A.A.; Al-Tahrawi, M.M. FLRED: An efficient fuzzy logic based network congestion control method. Neural Comput. Appl. 2018, 30, 925–935. [Google Scholar] [CrossRef]
- Karmeshu; Patel, S.; Bhatnagar, S. Adaptive mean queue size and its rate of change: Queue management with random dropping. Telecommun. Syst. 2017, 65, 281–295. [Google Scholar] [CrossRef]
- Feng, C.W.; Huang, L.F.; Xu, C.; Chang, Y.C. Congestion control scheme performance analysis based on nonlinear RED. IEEE Syst. J. 2015, 11, 2247–2254. [Google Scholar] [CrossRef]
- Xu, Y.; Qi, H.; Xu, T.; Hua, Q.; Yin, H.; Hua, G. Queue models for wireless sensor networks based on random early detection. Peer-Netw. Appl. 2019, 12, 1539–1549. [Google Scholar] [CrossRef]
- Zhang, X.; Li, D.; Zhang, Y. Maximum throughput under admission control with unknown queue-length in wireless sensor networks. IEEE Sens. J. 2020, 20, 11387–11399. [Google Scholar] [CrossRef]
- Huang, D.C.; Lee, J.H. A dynamic N threshold prolong lifetime method for wireless sensor nodes. Math. Comput. Model. 2013, 57, 2731–2741. [Google Scholar] [CrossRef]
- Keshtgary, M.; Mohammadi, R.; Mahmoudi, M.; Mansouri, M.R. Energy consumption estimation in cluster based underwater wireless sensor networks using m/m/1 queuing model. Int. J. Comput. Appl. 2012, 43, 6–10. [Google Scholar]
- Zhao, Y.; Li, H.; Liu, J. Performance analysis and optimization of CRNs based on fixed feedback probability mechanism with two classes of secondary users. Math. Probl. Eng. 2019, 2019, 9385693. [Google Scholar] [CrossRef]
- Tian, N.; Zhang, Z.G. Vacation Queueing Models: Theory and Applications; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006; Volume 93. [Google Scholar]
- Zhao, Y.; Xiang, Z.; Lu, Q. Performance evaluation for secondary users in finite-source cognitive radio networks with dynamic preemption limit. AEU-Int. J. Electron. Commun. 2022, 149, 154183. [Google Scholar] [CrossRef]
- You, S.; Eshraghian, J.K.; Iu, H.C.; Cho, K. Low-power wireless sensor network using fine-grain control of sensor module power mode. Sensors 2021, 21, 3198. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).