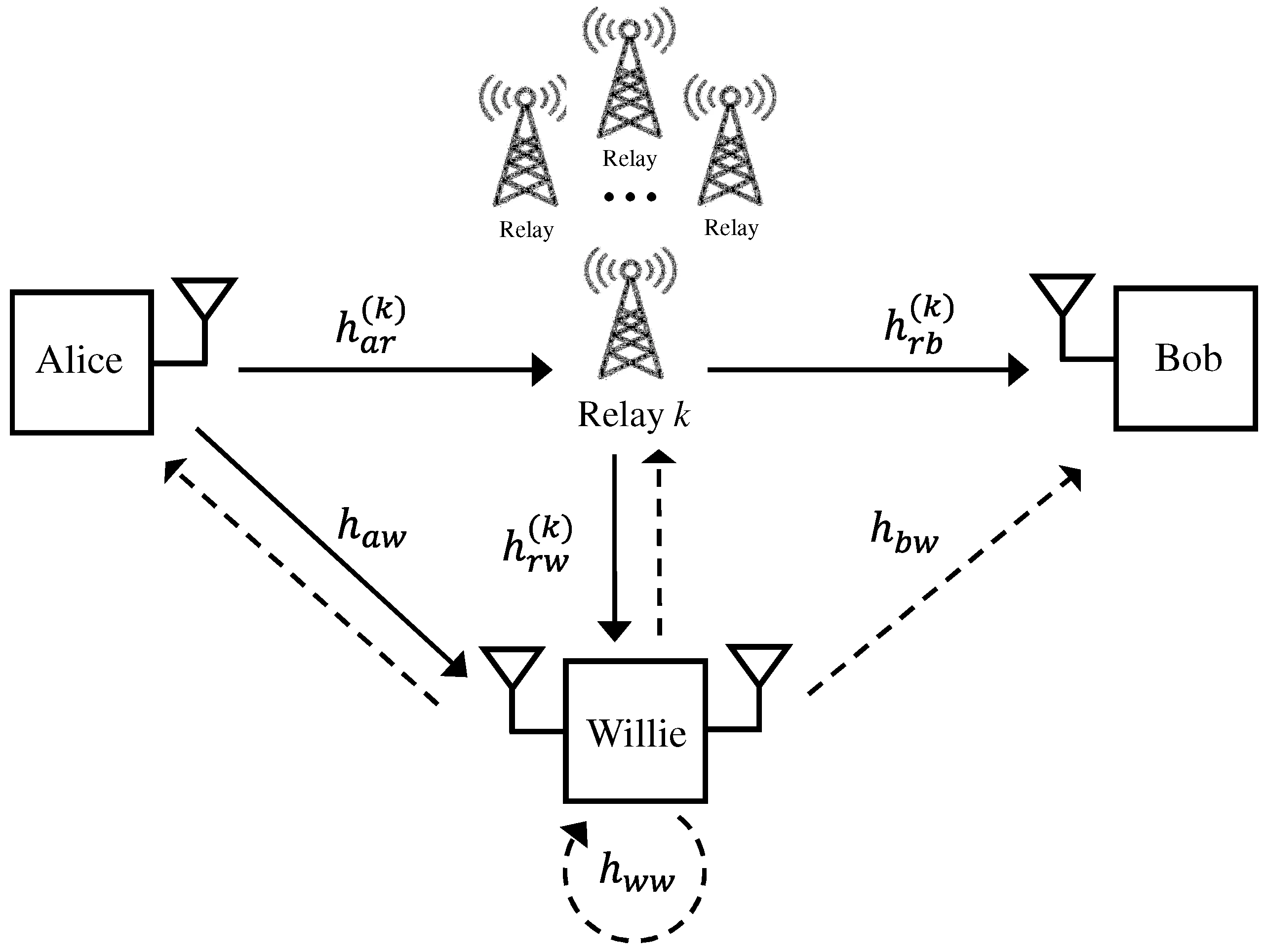
1. Introduction
Recently, as the importance of privacy and information security has grown significantly, interest in security technology has also increased substantially. The traditional approach to information security relies on cryptographic techniques at the upper layers of communication systems. However, advances in devices with powerful computational capabilities have placed cryptographic technology under increasing threat. As a result, physical layer security technology was introduced to enhance security across all communication layers [
1]. The goal of physical layer security technology is to prevent information eavesdropping by unauthorized eavesdroppers by exploiting the properties of the wireless channel, such as fading and noise. Pioneering researchers have demonstrated that a positive information-theoretic secrecy capacity can be achieved for various channel models [
2,
3,
4]. Building on the knowledge of information-theoretic capacity, efficient transmission strategies have been proposed and analyzed for physical layer security. However, as the demand for strong security on the physical layer has increased, there has been a growing need for more robust security techniques that could conceal the existence of the transmission. To address this demand for stronger security, covert communications have been introduced as a key security technology for future communication networks [
5,
6] such as industrial Internet of Things (IoT), autonomous robotic systems, and UAV swarms, where communication often takes place in adversarial or sensitive environments. In such scenarios, undetectable data exchange is essential to ensure mission integrity and prevent interception or jamming. The goal of covert communication techniques is to prevent the exposure of the transmission’s presence itself to wardens. As a result, covert communications provide stronger security compared to conventional physical layer security techniques, where messages may be received by eavesdroppers but remain undecodable.
Various communication strategies have been investigated to increase the covert rate for covert communication [
7,
8,
9,
10]. Channel inversion power control for covert communication was proposed in [
7], and it was shown that a positive covert rate can be achieved with the aid of a full-duplex receiver. A stochastic geometric approach to analyzing covert communication networks was presented in [
8]. For a random network where wardens and friendly jammers are located randomly, the authors maximized the covert rate through transmit power and rate control. In [
9], an opportunistic jammer selection strategy was proposed for covert communication with multiple friendly jammers. The authors first analyzed the detection error and outage probabilities and then obtained the optimal threshold for jammer selection based on analytical results. For multiple-antenna covert communication systems, efficient beamforming techniques were proposed in [
10]. The zero-forcing beamformer and the robust beamformer were designed for perfect channel state information (CSI) and imperfect CSI scenarios, respectively.
As a promising technique to achieve covertness, relay-assisted transmission has also been intensively studied [
11,
12,
13,
14]. In covert communication systems, relays can be utilized both as jammers to confuse the warden’s detection and as helpers to forward the covert message from the transmitter. The square root law was demonstrated in relay-assisted covert communications [
11]. In [
11], it was shown that the square root law can be achieved with the help of a full-duplex amplify-and-forward (AF) relay and channel uncertainty. Covert rate maximization was considered for covert communication with full-duplex and half-duplex AF relays in [
12]. The authors determined the optimal transmit power at the relay to maximize the covert rate while satisfying the covertness constraint. In [
13], the authors considered beamformer design for decode-and-forward (DF) relay-assisted covert communication. In the presence of both direct and relay links, they provided an algorithm to jointly design the beamformers at the transmitter and the relay. A covert communication system in which relays and friendly jammers coexist was introduced in [
14]. A relay selection strategy and power control were proposed, along with corresponding cooperative jamming. In these works, the focus was mainly on passive wardens who attempt to detect the covert transmission without taking active actions.
In recent works, the active warden, who poses a greater threat, has been considered in covert communication systems [
15,
16,
17,
18,
19,
20,
21,
22]. Contrary to the passive warden, who only attempts to detect the covert transmission, the active warden can not only detect the covert transmission but also transmit jamming signals to disrupt the reception of the covert message at the receivers [
15]. In [
16], the authors investigated the performance of covert communication from the perspective of the active warden under channel uncertainty. The active warden was assumed to eavesdrop on the transmitter and simultaneously generate artificial noise toward the receiver in full-duplex mode. They showed that the active warden was able to inject artificial noise covertly with perfect CSI of the jamming link, regardless of CSI uncertainties at the transmitter and receiver. Depending on the availability of CSI at the transmitter, the performance of covert communication was analyzed in terms of the covertness outage probability [
17]. To counter the threat posed by the active warden, efficient transmission strategies have been proposed for various covert communication systems, such as multi-channel communication [
18], UAV-assisted communication [
19], and short-packet communication [
20]. For relay-assisted covert communications, transmission strategies against the active warden have been proposed, and their performance has been analyzed [
21,
22]. A power threshold game for covert communication with a single relay was presented in [
21]. The authors proved that
bits can be transmitted covertly in the proposed system, and the Nash equilibrium was obtained. In [
22], the authors analyzed the performance of relay selection schemes in covert communication with multiple relays and an active warden. Specifically, they considered random relay selection and maximum channel relay selection schemes, which were originally developed for conventional relay systems without an active warden. The paper investigates the performance of these conventional schemes when applied to covert communication scenarios involving an active warden in terms of the detection error probability of the warden and the outage probability. The relay schemes in existing works were primarily designed for conventional communication systems, where the active warden is absent. Therefore, these schemes cannot efficiently counter the detection threats and jamming attacks posed by the active warden.
In this paper, we consider a two-phase DF relaying system, where the transmitter sends the covert message in the first phase, and the relay forwards it to the receiver in the second phase. From the active warden’s perspective, it is most effective to be located near the relay during both phases. In the first phase, the active warden can significantly disrupt covert message reception at the relay, and in the second phase, it can easily detect covert message transmission from the relay. In other words, to achieve covert communication with a high covert rate, it becomes critically threatening when the channel between the relay and the active warden is strong. Therefore, in covert communication with multiple relays, we consider a relay selection strategy to minimize the threat posed by the active warden. In our proposed relay selection scheme, we choose the relay with the lowest channel gain from the relay to the warden. For the proposed scheme, we analyze the theoretical performance and demonstrate performance improvements based on analytical results, specifically in terms of the warden’s detection error probability, the average received signal-to-interference plus noise ratio (SINR), and the outage probability. We then formulate a power allocation problem at the transmitter and the relay to maximize the covert rate. The numerical results validate our theoretical analysis, and we evaluate the performance of the proposed scheme in comparison to reference schemes.
The rest of this paper is organized as follows. In
Section 2, we present the system configuration, signal model, and the proposed relay selection scheme. In
Section 3, we analyze the theoretical performance, including the detection probability of the warden, the average received SINR, and the outage probability for the proposed scheme. We also formulate the power allocation problem to maximize the covert rate in this section. In
Section 4, we validate our analytical analysis and evaluate the performance of the proposed scheme. Finally, the conclusion of this paper is provided in
Section 5.
4. Numerical Results
In this section, we verify our analytical analysis via simulations and evaluate the performance of the proposed relay selection by comparing it with the reference schemes (since there are few existing relay selection schemes specifically designed for the environments with the active warden, which is the main focus of this study, we used the random relay selection and maximum relay channel selection schemes as references to clearly demonstrate the advantages of our proposed method that considers the channel between the relay and Willie). As mentioned in
Section 2.3, for reference schemes, we consider the random relay selection and maximum relay channel selection [
22]. In our simulations, we assume that the average channel gains from Alice to the relays are equal and set to
. The average channel gains from the relays to Bob are also assumed to be equal to
. The average channel gains of Alice-to-Willie and Willie-to-Bob are set to
, and the average channel gain of the self-interference at Willie is set to
. We consider equal average channel gains from the relays to Willie that aer set to
, unless otherwise specified. The noise powers at all nodes are set equal to
. The maximum transmit power budgets of Alice and the relays are assumed to be equal, and thus their transmit SNR becomes
. The transmit SNR of Willie is defined by
. We also assume that the target SINR for the outage event is set to
, and the covertness constraint is set to
.
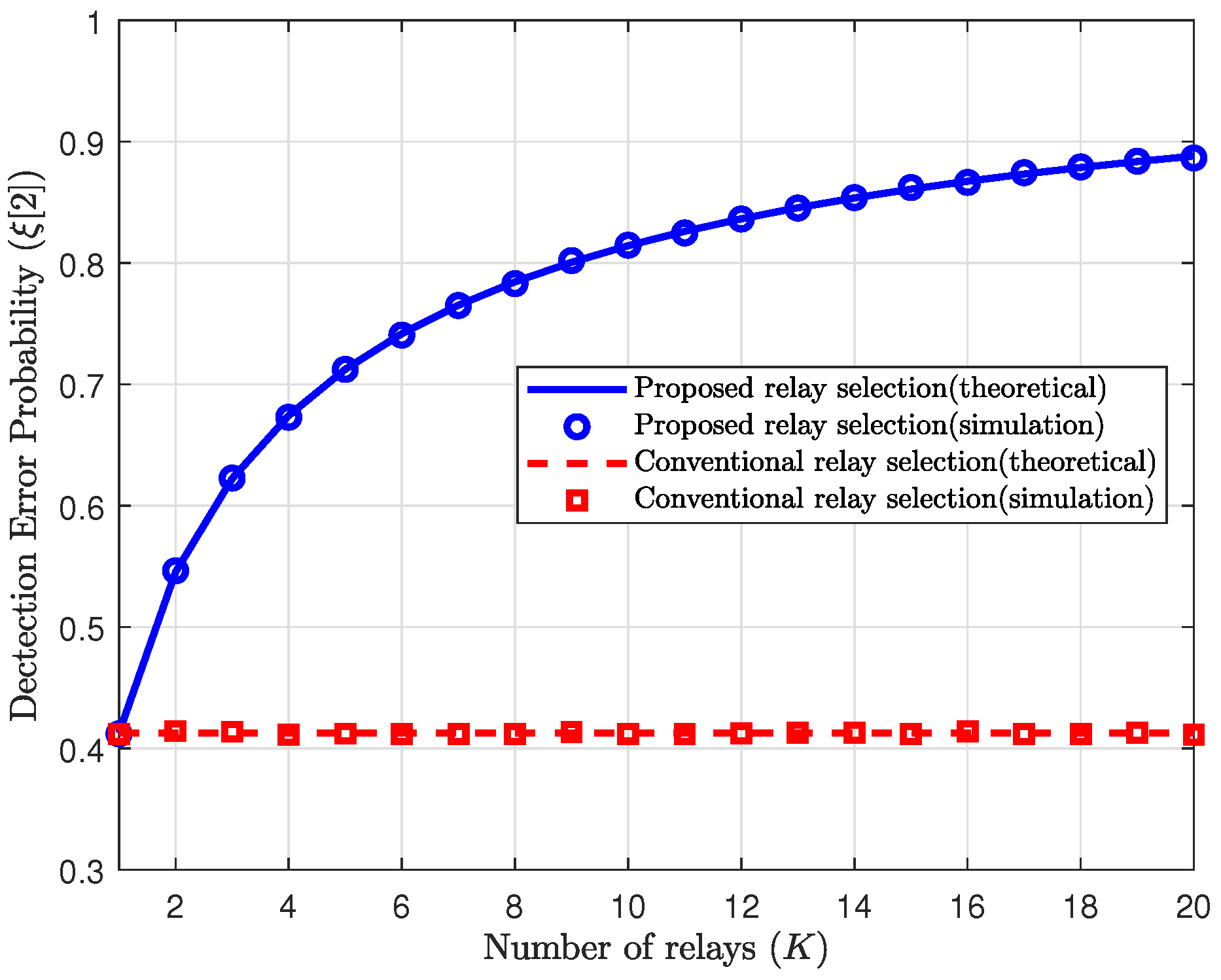
We first evaluate the performance of the proposed scheme in terms of the detection error probability of Willie in the second phase. In
Figure 2 and
Figure 3, the detection error probabilities of Willie in the second phase are plotted with respect to the number of the relay, i.e.,
K, for the proposed and reference schemes. The theoretical detection error probability for the proposed scheme is given in (
21), and the detection error probability for the reference scheme is obtained by replacing
with
in (
21). To ensure the verification of the theoretical results, all channels are generated more than
times for the simulation. In this figure, we assume that the relay uses full power with the maximum power budget
.
In
Figure 2, the transmit SNRs of the relay and Willie are set to
and
, respectively. The conventional relay selection refers to both the random relay selection and the maximum channel relay selection, since Willie’s detection error probabilities for both schemes are identical. From
Figure 2, we first observe that our theoretical results closely match with the simulations. As mentioned in
Section 3.1, in the reference schemes, the relay is chosen regardless of the channels to Willie, and thus the detection error probability is not affected by
K. However, the proposed scheme selects the relay with the minimum channel gain to Willie, thereby minimizing the signal leakage to Willie. Thus, the proposed scheme increases the detection error probability of Willie with
K in the second phase, as shown in (
24). Furthermore, we can check that the proposed scheme effectively increases the detection error probability of Willie even for a small or moderate number of relays, e.g.,
K such that
.
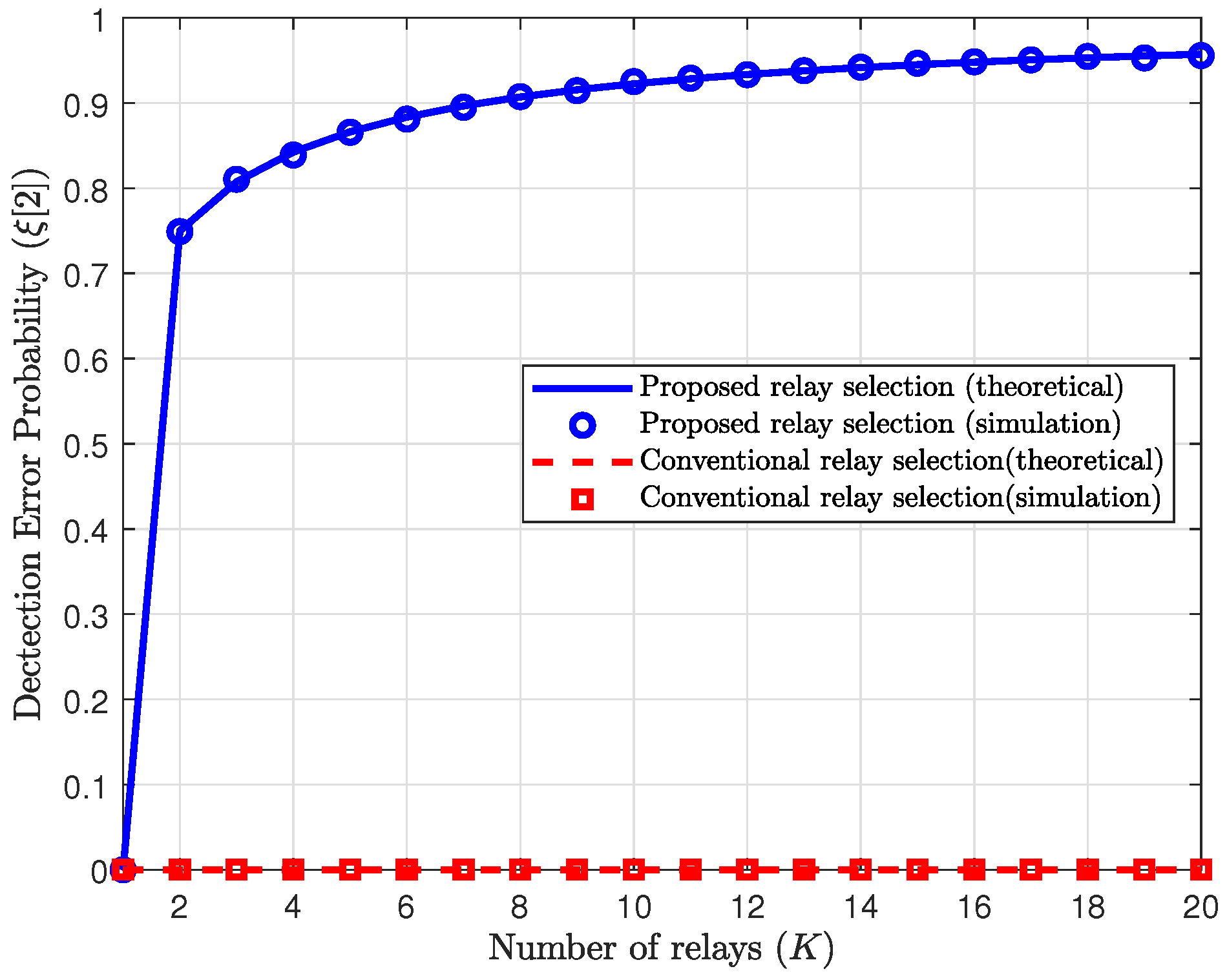
Figure 3 shows the detection error probabilities of Willie with
, where
. As mentioned in
Section 3.1, the detection error probabilities of the reference schemes become 0 in this special case. Therefore, in the reference schemes, the relay must significantly reduce its transmit power to satisfy the covertness constraint. In this case, for the proposed scheme, the detection error probability of Willie is given by (
26), and it increases as
K increases. From
Figure 3, we can observe that the effect of the proposed scheme is significant even for a small number of relays, e.g.,
K such that
. Therefore, the relay in the proposed scheme can use significantly more power for covert message transmission while satisfying the covertness constraint, as compared to the reference schemes.
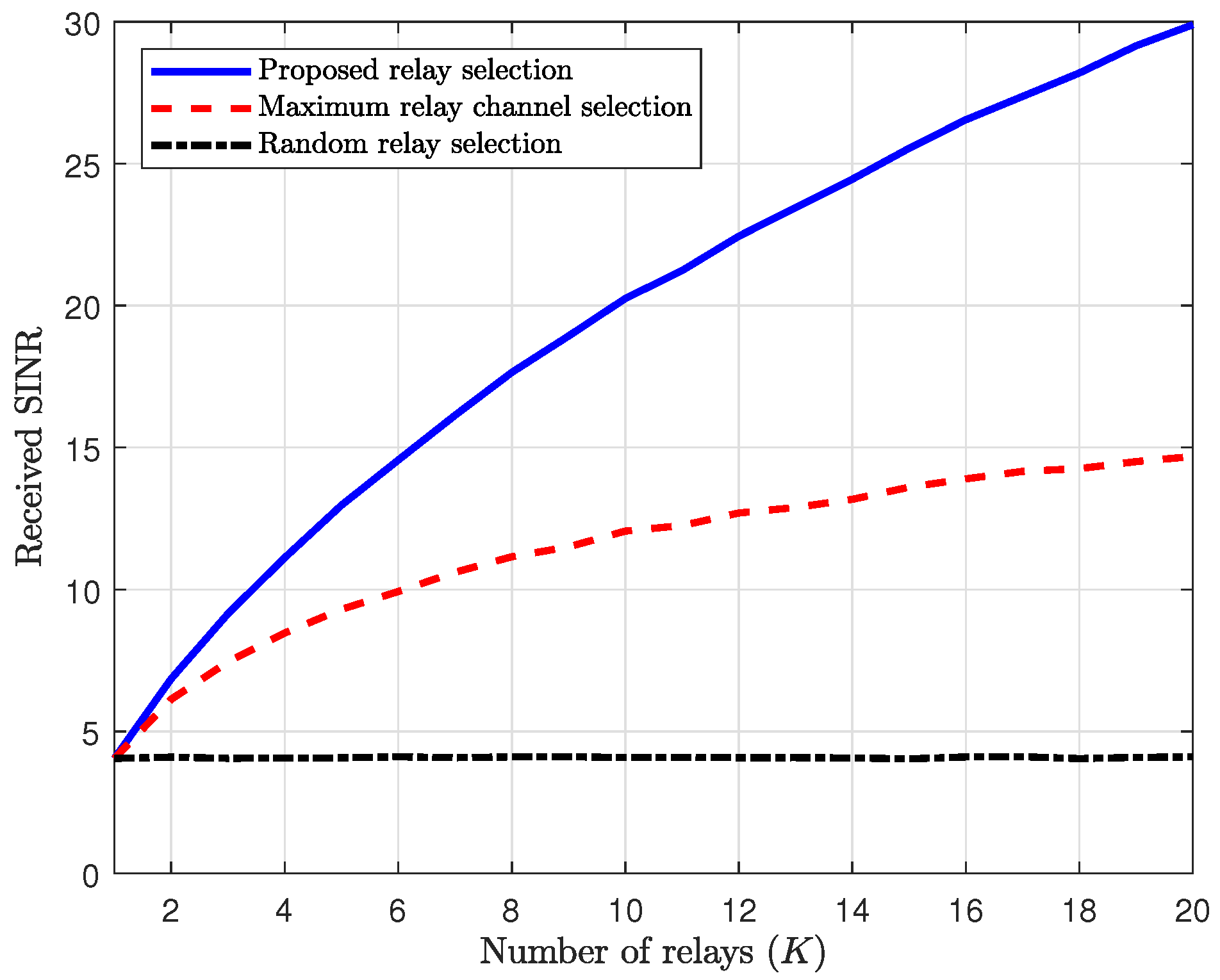
Figure 4 illustrates the received SINRs at the relay as a function of the number of relays,
K. In this figure, since we aim to observe the asymptotic behavior of the received SINR at the relay in the high-SNR regime, we set the transmit SNRs of the relay and Willie to
. Also, we assume that Alice uses full power with the maximum power budget
. As shown in (
31), we first observe that the random relay selection cannot achieve the diversity gain of
K relays. In contrast, both the proposed and the maximum relay channel selection schemes can achieve the diversity gain of
K relays, as shown in (
39) and (
35), respectively. The received SINR of the relay in the proposed scheme linearly increases according to the number of relays, while in the maximum relay channel selection scheme, it asymptotically increases with the
K-th harmonic number,
(where
).
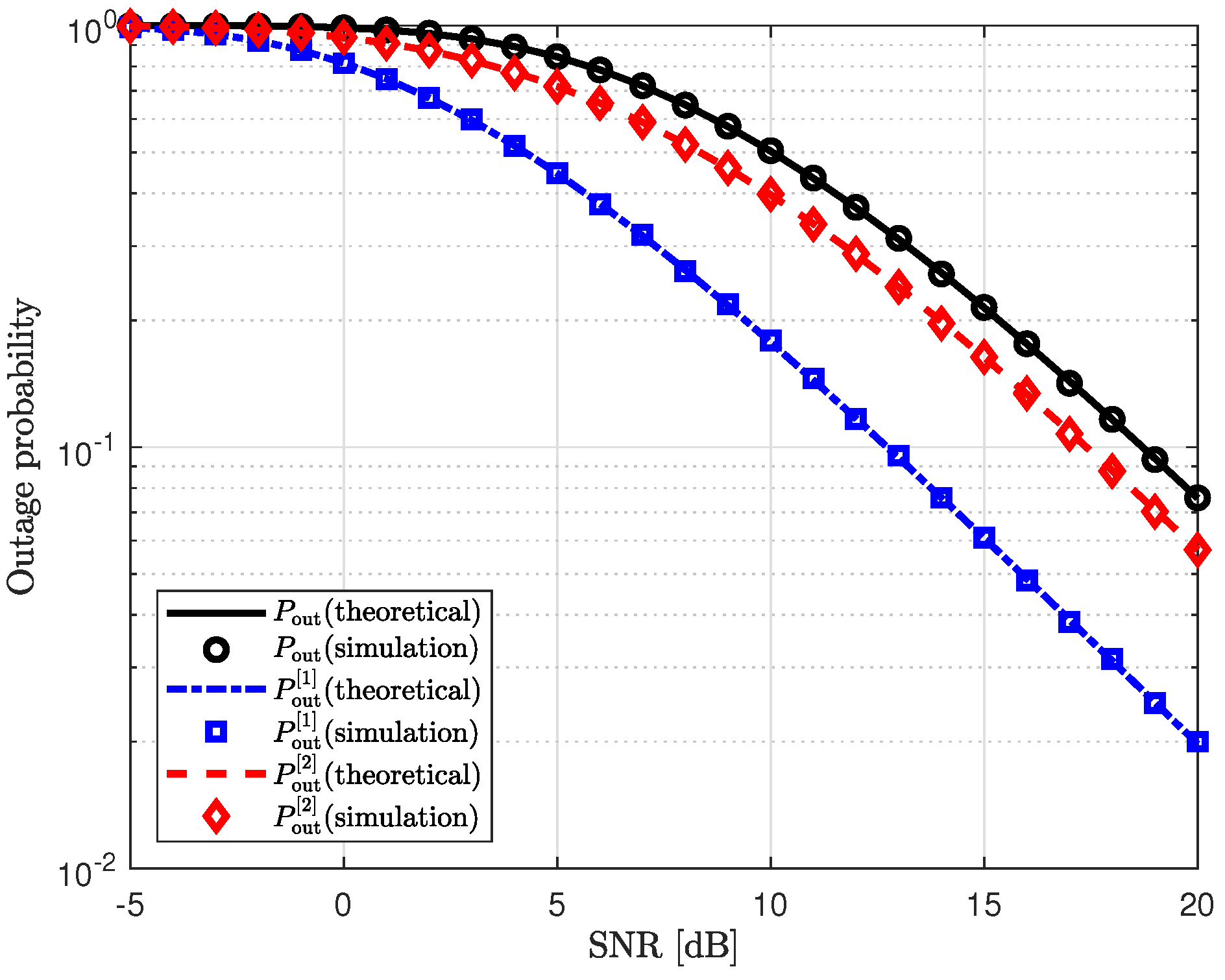
We verify our theoretical results for the outage probability through simulations in
Figure 5.
Figure 5 shows the outage probability of the proposed scheme as a function of the transmit SNR, along with the outage probabilities in the first and second phases. The theoretical outage probability of the proposed scheme is given in (
42). The outage probabilities in the first and second phases are provided in (
40) and (
41), respectively. For the simulation results, the channels are generated over
iterations. The transmit SNR of Willie is set to
. In this figure, we can see that our theoretical results for the outage probability are closely aligned with the simulation results. Compared to the outage probability in the second phase, the proposed scheme significantly reduces the outage probability in the first phase by effectively mitigating the interference from Willie.
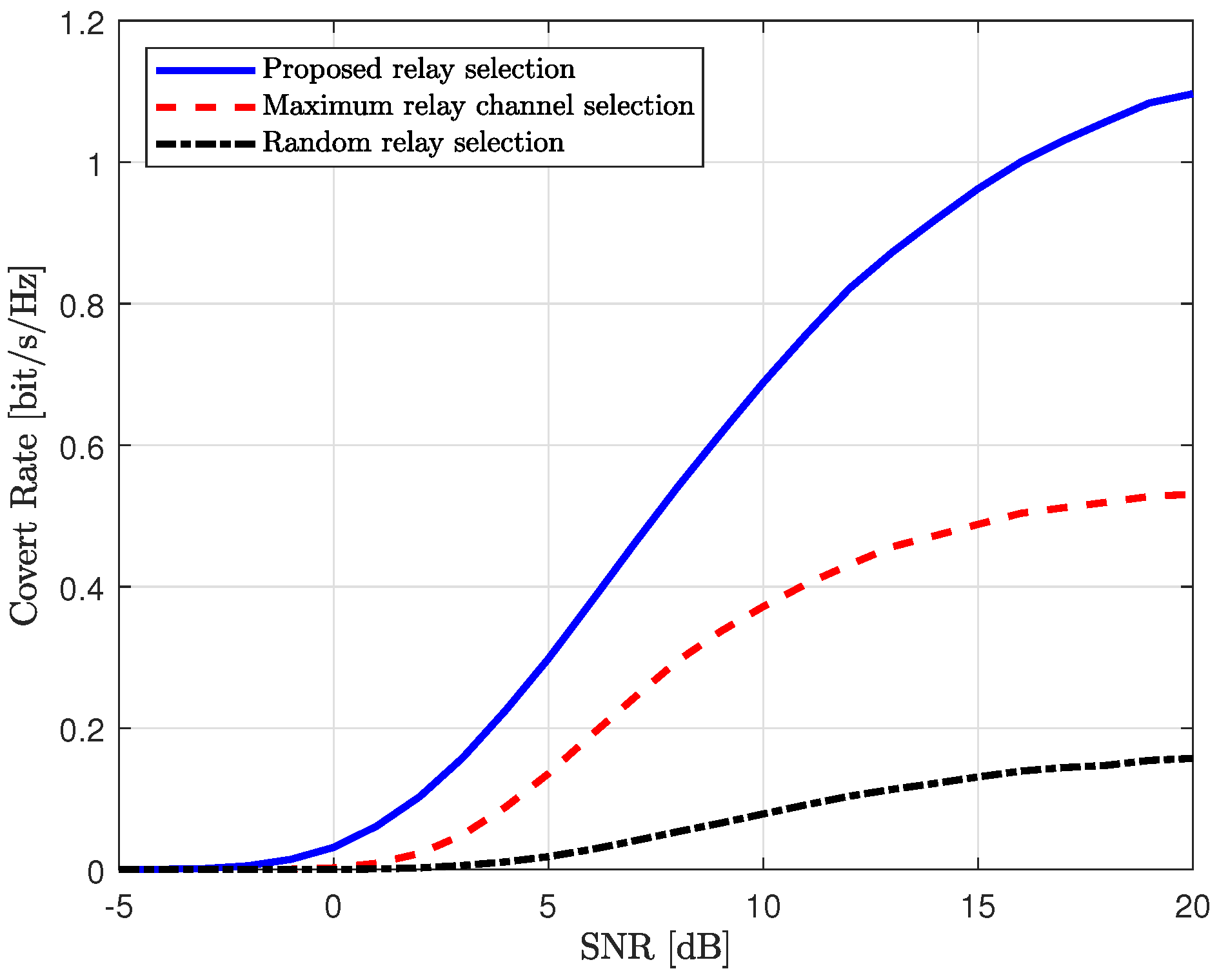
We evaluate the performance of the proposed scheme with the reference schemes in terms of the covert rate in
Figure 6 and
Figure 7. The achievable covert rate of the proposed scheme is defined in (
57), where the transmit powers at Alice and the relay are optimized to maximize the covert rate while satisfying the covertness constraint. For reference schemes, the transmit powers at Alice and the relay are also optimized to maximize their cover rates. The transmit SNRs at Alice, the relay, and Willie are set equal to
.
In
Figure 6, the covert rates of the proposed scheme and the reference schemes are plotted in accordance with the transmit SNR. As mentioned previously, the average channel gain from the relay to Willie and the covertness constraint are set to
and
, respectively. In this figure, the proposed scheme outperforms the reference schemes, with the performance gap increasing in the high-SNR regime. For the configuration with a relatively strong channel from Willie, the performance of the reference schemes can degrade significantly due to the strong interference from Willie. Additionally, as shown in
Figure 2 and
Figure 3, the relay must reduce the transmit power for the covert message in order to satisfy the covertness constraint. However, the proposed scheme effectively reduces interference from Willie by selecting the relay with minimum channel gain from Willie. Furthermore, the proposed scheme allows the relay to use more power to forward the covert message while satisfying the covertness constraint, as shown in
Figure 2 and
Figure 3.
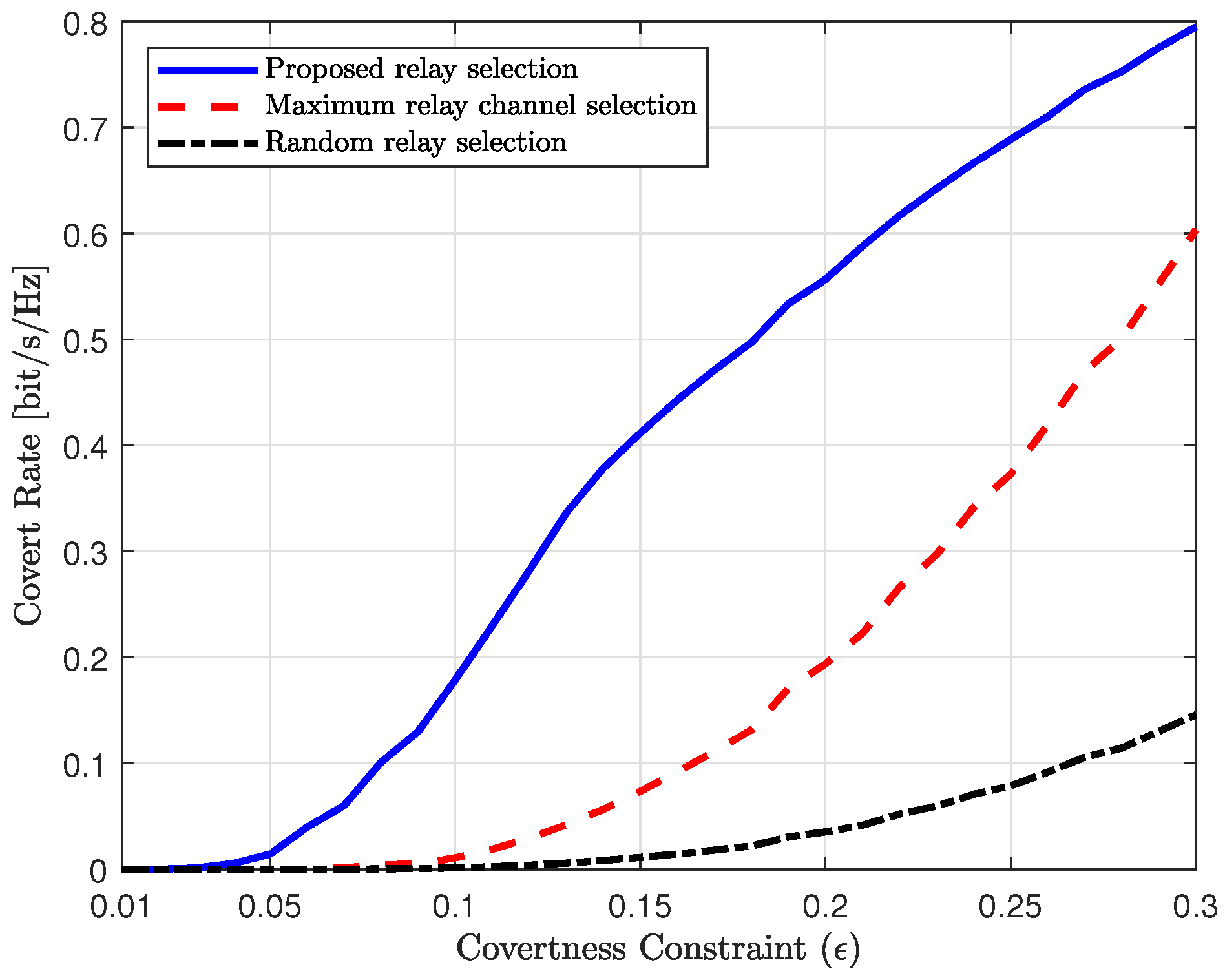
Figure 8 shows the covert rate of the proposed and reference schemes as a function of the covertness constraint. The transmit SNR is set to 10 dB, i.e.,
. It can be observed that the covert rate increases for all schemes as the covertness constraint becomes more relaxed. However, the proposed scheme and the maximum relay channel selection scheme exhibit a steeper increase in covert rate compared to the random relay selection scheme. In the regime of tight covertness constraints (e.g.,
), the performance of the conventional schemes is highly limited, whereas the proposed scheme achieves significantly higher covert rates. This is because the conventional schemes consider only the strength of the transmission channels, while the proposed scheme minimizes the signal leakage from the relay to Willie. As the covertness constraint becomes more relaxed, the performance of the maximum channel relay selection scheme approaches that of the proposed scheme, since under loose constraints, the channel strength to Bob becomes more dominant than minimizing the leakage to Willie. Consequently, the proposed scheme significantly outperforms the conventional schemes in scenarios requiring high covertness.
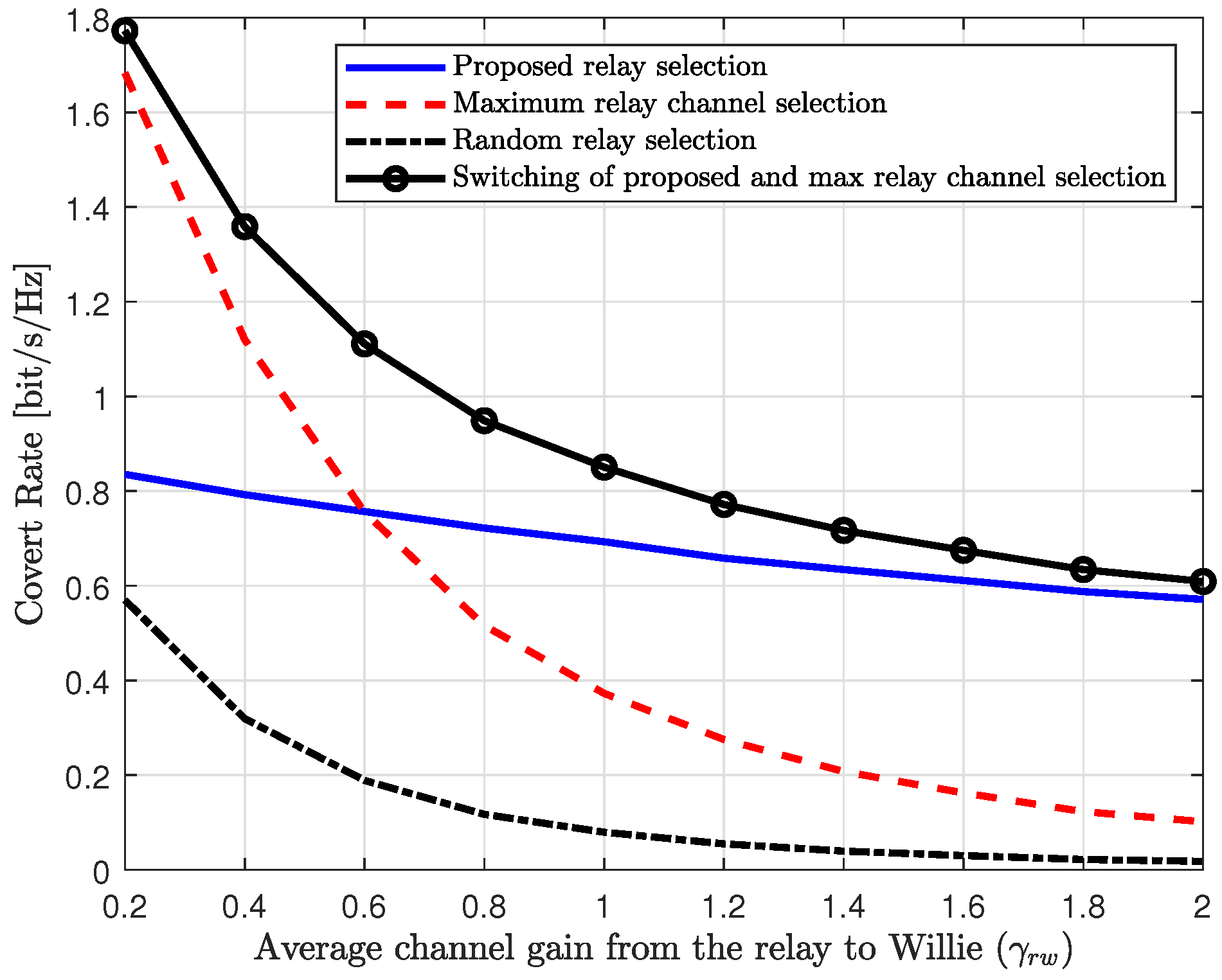
Figure 7 illustrates the effect of the average channel gain between the relay and Willie on the performance of the relay selection schemes. In
Figure 7, the covert rates of the proposed and reference schemes are shown as a function of the average channel gain from the relay to Willie,
. In this figure, we can observe that the covert rates of the random relay selection and the maximum relay channel selection scheme decrease significantly as the average channel gain to Willie increases. Specifically, since the maximum relay channel selection scheme is optimal for the DF relaying without Willie, it outperforms the proposed scheme when the average channel gain to Willie is weak (e.g.,
). However, it experiences significant performance degradation when Willie’s channel is strong (e.g.,
). In contrast, the proposed scheme provides robust performance, with performance degradation due to the increase in Willie’s channel gain being marginal. Therefore, for the moderate or strong channels to Willie (e.g.,
), the proposed scheme outperforms the reference schemes. To account for a general channel configuration, we plot a switching scheme between the proposed scheme and the maximum relay channel selection scheme. In the switching scheme, the relay selection scheme that provides the higher covert rate for a given channel configuration is chosen. In
Figure 7, we can observe that the switching scheme provides higher performance compared to the other schemes by selecting the optimal strategy for the given channel configuration. However, the switching scheme requires the CSIs of all channels in the system and involves solving the power optimization for all relays to be implemented, which increases implementation complexity. Therefore, developing a simple and efficient algorithm that offers robust performance under general channel configurations remains an ongoing research topic.