Abstract
In this paper, we investigate a scenario in which protected and unprotected services coexist in an elastic optical network under dynamic traffic. In the investigated scenario, unprotected services can reuse the reserved idle bandwidth to provide protection to the protected services. Under this scenario, we propose a new heuristic algorithm that enables such reuse as well as define and introduce a new assignment problem in elastic optical networks, named a Transmission Spectrum Assignment (T-SA) problem. In this paper, we consider a scenario in which services may be routed using the multipath routing approach. Additionally, protection using bandwidth squeezing is also considered. We assess our proposal through simulations on three different network topologies and compare our proposal against the classical protection approach, in which bandwidth reuse is not allowed. For the simulated range of network loads, the maximum (minimum) blocking probability reduction obtained by our proposal is approximately 48% (10%) in the European topology, 46% (7%) in the NSFNET topology, and 32% (6%) in the German topology.
1. Introduction
Compared to Wavelength Division Multiplexing (WDM) optical networks, Elastic Optical Networks (EONs) were conceived as a more effective optical network infrastructure, as their spectral resource is divided into finer bandwidth entities (slots), and these may be provided in numbers that exactly fit the demanded traffic, instead of a rigid (single) spectrum portion as in WDM. In order to implement the service requests made to EONs, it is necessary to solve the fundamental problem of routing and spectrum assignment (RSA) [1,2,3], which consists of finding a path with a sufficiently large number of available slots that are continuous (with the same indices along the route links) and contiguous (with adjacent indices). The need to observe these two constraints might lead to a situation of misalignment between available spectral bands along the network links, which is known in the literature as spectral fragmentation (SF). SF has a deleterious effect on network performance [3,4,5,6].
During optical network operations, due to the large amount of traffic supported by an optical fiber, a link failure event would imply traffic disruption to millions of users, leading to important economic losses. Therefore, resiliency, which is the network’s ability to continue in operation when failure occurs, becomes an essential requirement to be employed in optical networks [7]. This is commonly performed by a strategy known in the literature as traffic protection [5,6,8,9], which consists of allocating, in the network, not only enough transmission capacity to meet a given service request () but also an extra capacity () that can be used in the event of failures. An alternative strategy explored in the literature for the same purpose is restoration, which differs from protection as it does not reserve resources beforehand; rather, it seeks resources only upon the occurrence of a failure. Restoration tends to consume fewer spectral resources compared to protection, but it lacks assurance for service restoration in case of failure. Additionally, successful restoration takes longer to restore the affected services compared to protection [10,11,12]. We investigate, in this paper, the utilization of a protection strategy to provide network resilience.
The classic strategy to provide protection against single-link failure is to use two link-disjoint paths with enough individual capacity to attend to the demanded request. Since the same transmission rate is allocated on both paths, it is necessary to double the total allocated capacity, i.e., . These paths are conventionally referred to as working (or principal) and backup (or secondary) paths. This is the well-known Dedicated Path Protection (DPP) technique, which can be directly employed in WDM or Elastic Optical Networks. The application of protection strategies can lead to excessive consumption of a network’s spectral resources (ECSRs) [5,8,9]. Therefore, enhancements to DPP have been investigated, remarkably for EONs, since the capability of allocating resources with variable granularity allows the employment of more efficient protection mechanisms [5,8,13].
An approach partially similar to DPP is Shared Backup Path Protection (SBPP), for which a working (primary) lightpath and a backup (secondary) lightpath are also pre-calculated, and their required bandwidths are reserved for each connection demand [14]. However, SBPP differs from DPP in the fact that, while in DPP backup lightpaths have their own dedicated spectrum resources, in SBPP, the resources of the backup lightpath of different demands may be shared under the condition that these resources can be used only by one demand under failure condition.
One of the key concerns of a Network Carrier (NC) is how to effectively utilize the deployed network capacity, which is related to utilizing the minimum resources to attend to new services and doing it in a coordinated way to avoid future service rejection. A form to mitigate both SF and ECSR is the use of a multipath routing strategy (MPR), which consists of spreading the total necessary transmission rate () to implement a protected service over multiple paths in the network [15,16]. If these paths are link-disjoint, the strategy is named as link-disjoint MPR (LD-MPR) [5,6,9]. When applying the LD-MPR scheme, there is no difference between working and backup paths: is divided among P () link-disjoint paths so that if a single-link failure occurs in one of the P paths, the remaining are capable of transmitting at least [8,9]. This convenient traffic partitioning not only reduces the total bandwidth required to allocate but also allows to be allocated using narrow spectral bands over multiple different paths, which enables the twofold benefit of a more effective traffic distribution among network links as well as a better fit in the existing spectral gaps and a consequent SF reduction [8,9]. There are two potential drawbacks in applying the MPR strategy: the need to allocate guard bands on each path and the differential propagation delay between these paths [15]. Another form to further mitigate ECSR is the application of bandwidth squeezing protection (BSP) [8,9]. Under a BSP regime, it is allowed that the service requested bit rate, , may be reduced by, at most, a certain squeezing factor () under a failure in one of the links used by the service.
All the survivability mechanisms described in the references so far are designed to provide efficient reliability mechanisms for protected traffic only. However, network carriers must be prepared to attend to two kinds of customers: those who demand services that must remain active even upon failure occurrences in a network’s links and those who do not [12]. To cope with this situation, NCs may offer to their customers either a protected service (PS) or an unprotected service (US). Few works in the literature have investigated such multi-service scenarios [11,12,17]. However, none of them discuss the possibility of how unprotected connections can effectively use the spare capacity provided by protected connections when both protected and unprotected services coexist in the same network, except for the work by Lopes et al. [17] (this work is further detailed in Section 2), which addresses the opposite scenario: allowing protected services of a certain type to calculate their backup route on the same route and spectrum already used by unprotected services. In addition, the proposal by Lopes et al. cannot be applied in a multipath routing scenario because, in their work, they assume a clear distinction between the primary and backup paths, which, as discussed before, cannot be assumed in a multipath routing network.
Under the non-failure condition of an MPR protection scheme, part of the frequency slots allocated in P paths to cope with is being effectively used to transmit information (Tx-SLOTs), whereas another part is reserved but idle (Id-SLOTs). The Id-SLOTs are only effectively used for transmission in the case of a link failure. Any kind of spare capacity usage has a financial impact on NCs, as more services can be attended to for the same network capacity. Therefore, in order to improve the effectiveness of MPR protection mechanisms under a multi-service scenario, it is vital to discuss the possibility of how unprotected connections can effectively use the spare capacity provided by protected connections when both protected and unprotected services coexist in the same network.
In this paper, we investigate the scenario in which PS and US coexist in the network and, in addition, US can be established in the network by reusing the Id-SLOTs allocated for PSs. We use the acronym SHLRRS (services with heterogeneous levels of resilience and the reuse of idle slots) to identify this scenario. We also consider LD-MPR and BSP to deal with PSs and both single paths and LD-MPR to USs. The main contributions of this paper are the analysis of an expected practical scenario where protected and unprotected services coexist in the same network; the introduction of the problem of how spare capacity from protected services can effectively be reused by unprotected services; the definition of a new assignment problem, named Transmission Spectrum Assignment (T-SA), that arises in EONs under SHLRRS; and the proposal of a new heuristic that enables USs to reuse Id-SLOTs left by PSs. This paper introduces the problem of implementing capacity reuse by unprotected services in the spare capacity of established protected services under multipath-routed EONs assuming bandwidth squeezing capability.
2. Related Works
Recent studies have addressed resilience in Elastic Optical Networks by considering protection strategies through Multipath Provisioning with or without bandwidth squeezing. Takeda et al. [13] proposed a scheme to minimize the required spectrum resources necessary to provide protection in elastic optical networks. The scheme enables the allocation of different numbers of spectrum slots to each path, effectively reducing the total required spectrum resources. Using a similar approach, Assis et al. [8] proposed a mixed-integer linear programming (MILP) formulation to optimize the unequal partitioning of connections’ transmission rates among multiple link-disjoint paths to reduce total spectral usage. The authors apply the protection scheme to implement a resilient network against single-link failures and demonstrate the effectiveness of the proposed OPDPP formulation in reducing spectrum usage. Halder et al. [5] introduced the E-S-RSM-RSA scheme, optimizing spectrum and energy efficiency in regenerator-aware EONs. The proposed RSA applies the protection scheme to deal with the survivability of EONs under static traffic. Dinarte et al. [18] proposed a scheme that uses a genetic algorithm to optimize RSA ordering selection for each source–destination node pair. They introduced the Hybrid Partitioning Dedicated Path Protection (HPDPP) algorithm for resilient connection establishment with optimized R-SA or SA-R policy selection. Liu et al. [19] proposed a survivable multipath fragmentation-sensitive and fragmentation-aware routing strategy to simultaneously enhance the survivability and spectrum fragmentation of space-division multiplexing (SDM) EONs, leading to improved network blocking probability and spectrum utilization.
In terms of the coexistence of different service classes in the network, there are also recent works investigating the theme. Dixit et al. [20] and Batham et al. [21] consider three distinct classes of service (CoSs) coexisting in the network: CoS1 for real-time traffic (e.g., online audio–video traffic), CoS2 for nonreal-time traffic (e.g., compressed video and transactional data traffic), and CoS3 for delay-tolerant traffic (such as store-and-forward bulk data file transfer between various data centers). Liu et al. [22] investigate the coexistence of services with different levels of priorities, and they assumed that the priority levels can be arbitrarily defined by the network provider and its users via service level agreement (SLA). Note that in these previous three works, the assumed classes of services are differentiated either in terms of constraints regarding the delay experienced by the services or in the level of call priorities, not in terms of the level of resilience offered to each service. On the other hand, the present paper deals with different services coexisting in the network, but each service requires a different level of resilience. Hereafter, we discuss works that investigate this latter type of service differentiation.
Hai [12] analyzes the current real traffic worldwide and concludes that premium traffic (requiring protection) accounts for a portion of the total traffic, with the remaining being best-effort traffic (not requiring protection). Observing this fact, the author identifies an opportunity to optimize spectrum allocation and presents a novel integer linear programming (ILP) approach to address this scenario. To illustrate the author’s idea, let us assume a demand from node A to node B with aggregated traffic of X Gb/s, half composed by premium service, and the remaining being best effort. The article proposes that protection is not required for the entire X Gb/s flow but only for half relative to the premium service, and the author claims to address this scenario for the first time. In order to adequately address this scenario wherein service differentiation exists, the paper redesigns dedicated path protection in Elastic Optical Networks to minimize spectrum usage of resilient services.
Xiong et al. [23] and Shakouri et al. [10] investigate scenarios in which services with different resilience levels coexist in the network. Both works consider the approach known as proactive restoration, which consists of a restoration scheme that precomputes the backup path before the failure event. The frequency slots assigned to these precomputed restoration paths are “marked” but not reserved in the network. The authors assume two service classes with different resilience levels: high and low priority. Services in the high-priority class use the strategy of having precomputed restoration paths, whereas the restoration paths for low-priority class services are only computed upon the failure occurrence. It is worth noting that by using this strategy, the precomputed restoration paths may be occupied by other working paths from the high-priority class at any time, once no resources for these restoration paths are reserved as they are only marked. Each time this situation occurs, a new restoration path is calculated by the control plane to restore the restoration path that is no longer available. Additionally, the restoration paths of high-priority connections may be calculated using the resources allocated for low-priority connections. In this case, there is an optimization in the use of network slots because the same resources are being used both as working paths for low-priority services and as restoration routes for high-priority services. Upon the occurrence of a failure, the marked resources are allocated to the restoration paths of the high-priority connections, and low-priority connections, whose resources have been taken, require a restoration procedure. Notice that a new restoration path of a high-priority service is recalculated when the marked resources of its current restoration path are occupied by another working path or when one link of its current restoration path fails. The above strategy optimizes the use of resources in the network, but there is no guarantee that in the event of a failure, restoration paths will be available in the network to serve high-priority services. Note that, different from our work, which employs protection as a strategy to provide resilience to the network, Xiong et al. and Shakouri et al. employ the restoration strategy.
Lopes et al. [17] present an algorithm designed to support differentiated resilience services in SDM-EONs. The authors introduce the term quality of protection (QoP) to represent the coexistence of classes of service (CoS) with varying levels of protection guarantees. The CoS definitions are based on their QoP requirements: CoS1 exhibits high preemption and QoP (dedicated protection), CoS2 demonstrates medium preemption and QoP (shared protection), and CoS3 features no protection and no preemption (low-priority traffic). Preemption, as defined by the authors, allows for the interruption of lower-priority services in favor of higher-priority ones during the path and spectrum calculations. The algorithm proposed by the authors assumes that CoS2 services can share backup routes with other services of the same type. Additionally, the backup routes of CoS2 services may be found among the routes and spectra already allocated to CoS3 (unprotected) services without resulting in the tearing down of the active CoS3 service in the network. Lopes et al. [11] further investigated the scenario they study in [17] and proposed a new algorithm, which provides routing, resource allocation, and protection in SDM-EONs. Nevertheless, they assumed, in [11], only CoS1- and CoS3-type services, and for this reason, there is no possibility for the backup paths to reuse the spectrum already allocated for unprotected services, only preemption is allowed.
Summarizing the reviewed articles, none of them address slot reuse in an elastic optical network that employs multipath protection.In our understanding, the work closest to ours is the work by Lopes et al. [17], but as discussed at the end of Section 1 and delineated in the present section, the proposal is not applicable when considering LD-MPR under SHLRRS. Table 1 summarizes the main characteristics exhibited by each reviewed work. Additionally, we did not find any algorithm (similar to ours) in the literature that can be directly applied in the multipath-routed network and, therefore, could be used as a basis for comparison with our proposal.

Table 1.
Main characteristics exhibited by the related works found in the literature.
3. Transmission Spectrum Assignment Problem
In this section, we introduce and discuss the Transmission Spectrum Assignment problem by means of an illustrative example. We begin by stating the mathematical notation. Consider a service that requires a transmission rate (in Gb/s) to be established between nodes i and j in the network using a certain type of resilience mechanism . We denote this service by . In this paper, we consider . Note that P disjoint routes () are required to establish a service of type PS, as well as frequency slots in each of the P routes. We define , where and , as the frequency index used by the s-th slot assigned on route p to a service . The set of all associated with a service can be written using the matrix . Notice that some of the slots allocated to a PS are actually used for data transmission (Tx-SLOTs), while others are allocated/reserved (Id-SLOTs) on the network but used for a service’s data transmission only in the case of link failure. To mathematically express the assignment of these two types of slots, we use the matrix , in which if the service uses the frequency index in route p as Tx-SLOT and if the frequency index is defined as Id-SLOT.
Suppose the establishment of two protected services, and , in the network, as shown in Figure 1. Figure 1 shows three possible link-disjoint routes to establish and , as well as the current spectral occupation of each route (white and gray squares are free and occupied slots, respectively). To simplify the analysis, we assume that all three routes allow a spectral efficiency of 4 (bits/s)/Hz, and the frequency slots are 12.5 GHz wide. Thus, four slots are required to transmit 200 Gb/s. By adopting the classic 1:1 protection scheme, may be established using the routes and . This choice is mathematically described by
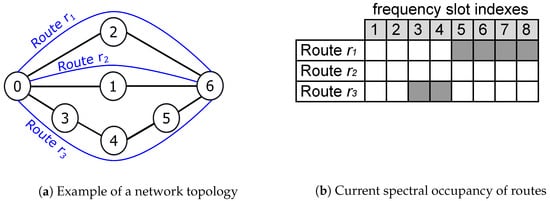
Figure 1.
Example of a network topology with 3 link-disjoint routes (a) and the spectral occupancy of these routes (b).
Similarly, may be established using and as and . Both allocations are shown in case A of Figure 2. Figure 2 shows some examples (cases A to F) of allocations that are discussed in this section. Tx-SLOTs are marked with 1 and Id-SLOTs with 0. Note that there is an alternative form to allocate Id-SLOTs and Tx-SLOTs of by calculating , which is shown in case B.
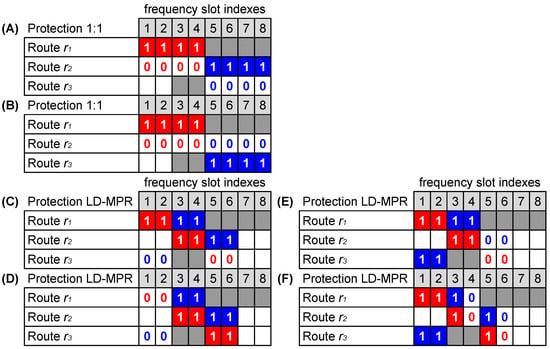
Figure 2.
Some possibilities of solutions to the T-SA problem considering the same RSA solution and the following protection scheme: 1:1 (cases (A,B)) and LD-MPR (cases (C–F)).
If Id-SLOTs cannot be reused by the USs, the allocations shown in cases A and B in Figure 2 are equivalent because both RSA solutions occupy the very same routes and slot indices. However, the purpose of this paper is to investigate the SHLRRS scenario, in which USs are allowed to reuse Id-SLOTs. Under SHLRRS, for instance, in case A, it is possible to establish upcoming USs with up to four slots on and (by reusing Id-SLOTs) and with up to two slots on (using free slots), whereas in case B, it is possible to establish upcoming USs with up to eight slots on (reusing Id-SLOTs) and with up to two slots on (using free slots). Clearly, under SHLRRS, in addition to solving the RSA problem for PSs, it is also necessary to solve the T-SA. Once the routes and slots to allocate a PS are found (by RSA), the T-SA problem can be solved by assigning each of these found slots to either Tx-SLOT or Id-SLOT. In other words, while matrix A represents the solution of the RSA problem, matrix B represents the result of the solution to the T-SA problem over matrix A.
We may also analyze the allocation of and in the same scenario, but now assuming both multipath (LD-MPR) and squeezing (BSP). In this case, is equally divided among the P link-disjoint routes, and the bit-rate allocated for each route p () is given by [8,9]
in which is the squeezing factor. For the sake of this example, we assume and . For requests of Gb/s, we obtain Gb/s, which means that two slots per route are required to establish and . A possible RSA solution for and , under the same route states shown in Figure 1b, is and , which is shown in Figure 2 by means of the cases C, D, E, and F. These four cases illustrate the same RSA solution but stand for different T-SA solutions. Therefore, they lead to different spectral occupations by Id-SLOTs, and as a consequence, they affect the capacity of the network differently to accommodate future USs in Id-SLOTs. This simple example shows the importance of an adequate solution for T-SA under SHLRRS.
In this article, the T-SA problem is solved using the First-Fit approach, that is, the lines of matrix B are successively filled with 1 s, from left to right in each line, until completing the number of 1 s necessary to establish the service.
4. Proposed Routing and Spectrum Assignment for Protected and Unprotected Services
In this section, we describe the proposed RSA algorithms to perform the establishment of both PSs and USs. The proposed algorithm for establishing USs enables the reuse of Id-SLOTs of PSs. Let us start by defining the mathematical notation and functions used in the routing procedures. We assume there is available an ordered set of K pre-computed candidate groups of P link-disjoint paths between each source and destination node pairs , defined as , in which is composed of an ordered set of P link-disjoint routes in the network topology, i.e., , where and are link-disjoint routes for , . The manner in which the set is generated is described in [9]. The function (B,r) performs the spectrum assignment, and it returns true if it is possible to find Id-SLOTs in route r capable of transmitting the bit-rate B. Otherwise, it returns false. Similarly, (B,g) performs the spectrum assignment on the routes of group g, and it returns true if it is possible to find free slots (Fr-SLOT) capable of transmitting the bit-rate B in each route that belongs to group g. Otherwise, it returns false. In both cases, the First-Fit algorithm is assumed to perform the spectral assignment.
Algorithm 1 is executed upon each new service request to the network. Initially, it identifies if the service is either PS or US (lines 1 and 7, respectively). If the service is US, an attempt is made to establish it using a single route by executing the function SinglePath (Algorithm 2), which tries to reuse the available Id-SLOTs. If this attempt is not successful, a new attempt is made (but now using two paths and no reuse) by executing the function MultiPath (Algorithm 3) on line 5. On the other hand, if the service is PS, we try to establish it directly using multiple paths by executing the function MultiPath (Algorithm 3) on line 8.
| Algorithm 1 Main(,P,K,i,j,) |
|
| Algorithm 2SinglePath(,P,K,i,j) |
|
| Algorithm 3MultiPath(,P,K,i,j,) |
|
The function SinglePath (Algorithm 2) searches only for Id-SLOTs to establish the current service. The search is conducted by successively testing if spectrum reuse can be accomplished in the last route (loop in line 3) of each pre-computed group of P link-disjoint routes, , starting from groups with P link-disjoint routes to those with two routes (loop in line 1). The first route with successful spectrum reuse (function in line 4) is returned as the solution to the SinglePath function. If none of the searched routes has enough available Id-SLOTs, the algorithm is finalized with an unsuccessful return message (“blocked” return, as shown in line 9).
The function MultiPath (Algorithm 3) is called either the first option of PS or for US whenever the SinglePath function does not succeed on its spectrum reuse exploration in the routes of the pre-computed candidate groups. MultiPath searches only for free slots (Fr-SLOT) to establish the current service. Loop in line 1 considers, successively, splitting the service bit-rate among P, , two paths. For each possibility, its K pre-computed groups are acquired (line 2) and tested (loop in line 8). The bit-rate to be allocated on each of the p routes is calculated according to the type of current service, either PS or US (lines 4 to 6). If the service is PS, Equation (3) is employed (line 4), as stated for LD-MPR protection assignment. In case the service is US, since it does not demand traffic protection, its entire rate, , is merely split among the P provided routes in the evaluated group (line 6). All K groups of link-disjoint routes are tested successively (loop in line 8) for the feasibility, or not, of allocating the current service using the k-th group. The tests are conducted using the function (line 9). In line 11, if the allocation of the service of type PS is successful, the problem of T-SA is also solved (as described in Section 3).
In a given instant of time, an Id-SLOT can be reused by only a single US. The tearing down process of a US that is reusing one or more Id-SLOTs from a PS makes these specific Id-SLOTs again available for reusing. On the other hand, the tearing down process of a PS that has active USs reusing its Id-SLOTs does not deactivate these USs, which makes them remain active in the network. In the case of a link failure, the Id-SLOTs from the PSs affected by the failure are reclaimed and the USs that were using these reclaimed slots are disconnected. Note that a link failure in an optical network is expected to be a rare event.
5. Simulation Setup
An elastic optical network simulator derived from SimEON [24] is used to carry out simulation results. SimEON is an open-source simulator capable of simulating the required EON characteristics relevant to the present study. SimEON and its extensions have been used and validated as a simulation engine in many works in the literature [18,25,26]. Call requests are established through a unidirectional circuit-switched lightpath. Poisson’s traffic model is assumed. The simulator generates a large number of services in each simulation. We assumed the following set up for the services: are randomly generated considering Gbits/s (uniform), (70% of PS and 30% of US), and node pair (uniform). The simulator simulates the process of setting up and tearing down services in a real network, and by doing so, it can evaluate the probability that enough resources are not available in the network to accommodate the service at its arrival time, which is referred to as the network blocking probability (BP). BP is evaluated by
in which and stands for the number of accepted and blocked services, respectively, during the simulation. The network blocking probability under this dynamic traffic is used as the performance metric. We assume , , , and 320 frequency slots (each 12.5 GHz wide) available per optical fiber. We run simulations in three different network topologies: European [3], Nsfnet [5], and German [27]. We consider the 4-QAM modulation format.
6. Results
To study the network blocking probability reduction achieved by the proposed heuristic, we executed two different versions of it. The first, named “With Reuse”, enables USs to reuse Id-SLOTs left by PSs. The RSA problem is then solved using Algorithm 1. The second, named “No Reuse”, disables reuse capability, which is achieved using a version of Algorithm 1 obtained after the removal of lines 2, 3, 4, and 6.
Figure 3 shows the BP as a function of the network load for both investigated strategies “With Reuse” and “No Reuse” in the considered topologies: European (Figure 3a), Nsfnet (Figure 3b), and German (Figure 3c). The symbols plotted in the graphs stand for the mean value obtained for the BP, whereas the error bars stand for the confidence interval of 95%. We can observe that in all investigated cases, the “With Reuse” strategy achieves lower values of BP than the “No Reuse” strategy. Moreover, we observe no overlapping of the obtained confidence intervals (with the exception of 320 erlangs in the German topology), which corroborates the statistical significance of the results. For the simulated range of network loads, the maximum (minimum) BP reductions obtained by the “With Reuse” strategy in comparison to “No Reuse” are approximately 48% (10%) in the European topology, 46% (7%) in the Nsfnet topology, and 32% (6%) in the German topology.
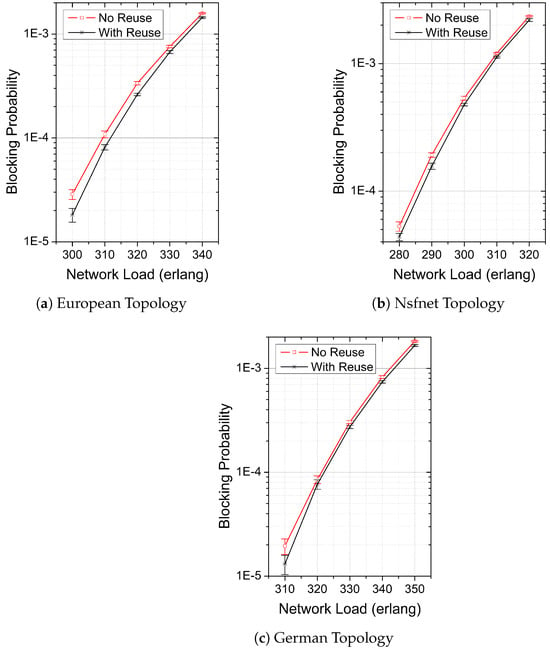
Figure 3.
Mean values and 95% confidence intervals of blocking probabilities obtained by the “With Reuse” and “No Reuse” strategies as a function of network-offered loads in the network topologies (a) European, (b) Nsfnet, and (c) German.
7. Conclusions
In this paper, we investigated resilient Elastic Optical Networks that employ protection mechanisms under multipath routing and bandwidth squeezing in a scenario where protected and unprotected services coexist. Differently from conventional protection mechanisms, where both transmission slots and idle slots remain dedicated to the connection, we propose that unprotected services may reuse those idle slots of protected services. We identified and described, for the first time, the necessity of solving the T-SA problem in resilient networks with multipath routing where the proposed reuse is permitted.
To enable our proposal, new straightforward heuristic algorithms are presented. They deal with the spectrum reuse capability and solve the introduced Transmission Spectrum Assignment problem with the aim of properly assigning unprotected services over idle slots of protected services, mitigating the network path request blocking probability.
We examined three conventional network topologies, where we could observe that our proposal could effectively assign unprotected services to Id-SLOTs, which enabled additional traffic to be carried by the network when compared to its equivalent protection strategy without slot reuse. In the blocking probability range of approximately to , our proposal achieved blocking probability reductions between 10% and 48% for the European topology, between 7% and 46% for the Nsfnet topology, and between 6% and 32% for the Germany topology.
By defining the efficiency of a network as the total amount of traffic capacity it can handle relative to its telecommunications infrastructure, we can state that the spectrum reuse proposal presented in this article can enhance the efficiency of a resilient EON. This is because the proposal enables unprotected services to use the Id-SLOTs, allowing more total traffic to be carried by the network. This conclusion is evidenced by the reduction in blocking probability achieved by our proposal.
We believe that more sophisticated algorithms to solve the addressed problems can lead to further reductions in the network path request blocking probability. In the case of T-SA, one way we envision achieving this reduction is by solving it in an optimized manner, using, for example, a computational intelligence algorithm. We also believe that there is still room for optimization in the routing mechanism itself, by using, for example, an adaptive routing procedure that finds the shortest path considering only the links with available Id-SLOTs.
Author Contributions
M.M.L.C. contributes on coding an simulation results. G.W.T., H.A.D., R.C.A.J. and D.A.R.C. contribute for conceptualization and manuscript draft, R.B. contributes for manuscript draft. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Council for Scientific and Technological Development (CNPq).
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors give thanks to the University of Pernambuco, the Federal University of Pernambuco, the University of Waterloo, and the National Council for Scientific and Technological Development (CNPq).
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Tang, B.; Huang, Y.C.; Xue, Y.; Zhou, W. Heuristic Reward Design for Deep Reinforcement Learning-Based Routing, Modulation and Spectrum Assignment of Elastic Optical Networks. IEEE Commun. Lett. 2022, 26, 2675–2679. [Google Scholar] [CrossRef]
- Cavalcante, M.; Pereira, H.; Chaves, D.; Almeida, R. Optimizing the cost function of power series routing algorithm for transparent elastic optical networks. Opt. Switch. Netw. 2018, 29, 57–64. [Google Scholar] [CrossRef]
- Dinarte, H.A.; Correia, B.V.; Chaves, D.A.; Almeida, R.C. Routing and spectrum assignment: A metaheuristic for hybrid ordering selection in elastic optical networks. Comput. Netw. 2021, 197, 108287. [Google Scholar] [CrossRef]
- Ujjwal; Thangaraj, J.; Kumar, R. Multi-path provisioning in elastic optical network with dynamic on-request optimal defragmentation strategy. Opt. Switch. Netw. 2021, 41, 100607. [Google Scholar] [CrossRef]
- Halder, J.; Acharya, T.; Chatterjee, M.; Bhattacharya, U. E-S-RSM-RSA: A Novel Energy and Spectrum Efficient Regenerator Aware Multipath Based Survivable RSA in Offline EON. IEEE Trans. Green Commun. Netw. 2021, 5, 1451–1466. [Google Scholar] [CrossRef]
- Paira, S.; Halder, J.; Chatterjee, M.; Bhattacharya, U. On energy efficient survivable multipath based approaches in space division multiplexing elastic optical network: Crosstalk-aware and fragmentation-aware. IEEE Access 2020, 8, 47344–47356. [Google Scholar] [CrossRef]
- Da S. Oliveira, H.M.N.; Da Fonseca, N.L.S. Backup, Routing, Modulation, Spectrum and Core Allocation in SDM-EON for Efficient Spectrum Utilization. In Proceedings of the 2022 IEEE Latin-American Conference on Communications (LATINCOM), Rio de Janeiro, Brazil, 30 November–2 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Assis, K.D.R.; Almeida, R.C.; Reed, M.J.; Santos, A.F.; Dinarte, H.; Chaves, D.A.R.; Li, H.; Yan, S.; Nejabati, R.; Simeonidou, D. Protection by diversity in elastic optical networks subject to single link failure. Opt. Fiber Technol. 2023, 75, 103208. [Google Scholar] [CrossRef]
- Dinarte, H.A.; Almeida, R.C.; Assis, K.D.R.; Chaves, D.A.R. Multi-objective Optimization of Asymmetric Bit Rate Partitioning for Multipath Protection in Elastic Optical Networks. TechRxiv 2023. [Google Scholar] [CrossRef]
- Shakouri, S.; Ghaffarpour Rahbar, A. Proactive restoration with low re-provisioning in Elastic Optical Networks. Comput. Netw. 2021, 197, 108284. [Google Scholar] [CrossRef]
- Lopes, R.; Rosário, D.; Cerqueira, E.; Oliveira, H.; Zeadally, S. Priority-aware traffic routing and resource allocation mechanism for space-division multiplexing elastic optical networks. Comput. Netw. 2022, 218, 109389. [Google Scholar] [CrossRef]
- Hai, D.T. On the spectrum-efficiency of QoS-aware protection in elastic optical networks. Optik 2020, 202, 163563. [Google Scholar] [CrossRef]
- Takeda, K.; Sato, T.; Shinkuma, R.; Oki, E. Multipath provisioning scheme for fault tolerance to minimize required spectrum resources in elastic optical networks. Comput. Netw. 2021, 188, 107895. [Google Scholar] [CrossRef]
- Tomassilli, A.; Jaumard, B.; Giroire, F. Path protection in optical flexible networks with distance-adaptive modulation formats. In Proceedings of the 2018 International Conference on Optical Network Design and Modeling (ONDM), Dublin, Ireland, 14–17 May 2018; pp. 30–35. [Google Scholar] [CrossRef]
- Ruiz, L.; Durán Barroso, R.J.; De Miguel, I.; Merayo, N.; Aguado, J.C.; Abril, E.J. Routing, Modulation and Spectrum Assignment Algorithm Using Multi-Path Routing and Best-Fit. IEEE Access 2021, 9, 111633–111650. [Google Scholar] [CrossRef]
- Moura, P.M.; da Fonseca, N.L.S. Multipath Routing in Elastic Optical Networks with Space-Division Multiplexing. IEEE Commun. Mag. 2021, 59, 64–69. [Google Scholar] [CrossRef]
- Lopes, R.S.; Oliveira, H.M.N.D.S.; Da Fonseca, N.L.S. Differentiated Resource Allocation in Resilient SDM-EON. In Proceedings of the 2021 IEEE Latin-American Conference on Communications (LATINCOM), Santo Domingo, Dominican Republic, 17–19 November 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Dinarte, H.A.; Teixeira, G.W.; Almeida, R.C.; Assis, K.D.R.; Waldman, H.; Chaves, D.A.R. Multipath provisioning for survivable elastic optical networks with optimized RSA ordering selection. In Proceedings of the 2023 23rd International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 2–6 July 2023; pp. 1–4. [Google Scholar] [CrossRef]
- Liu, H.; Tang, C.; Chen, Y.; Tan, M.; Qiu, Y.; Chen, H.; Hu, J. A survivable multipath resource allocation strategy based on fragmentation-sensitive fragmentation-aware in space division multiplexing elastic optical networks. Comput. Commun. 2023, 204, 78–88. [Google Scholar] [CrossRef]
- Dixit, S.; Batham, D.; Narwaria, R.P. Cost function-based class of service provisioning strategy in elastic optical networks. Int. J. Commun. Syst. 2020, 33, e4634. [Google Scholar] [CrossRef]
- Batham, D.; Thakare, V.V. An improved cost function-based class of service provisioning scheme for elastic optical networks. Comput. Netw. 2024, 243, 110283. [Google Scholar] [CrossRef]
- Liu, C.; Wang, K.; Zhan, W.; Wang, Y.; Xiao, B.; Gao, W. Multi-path routing spectrum allocation algorithm based on fragment sensing and energy saving. In Proceedings of the 5th International Conference on High Performance Compilation, Computing and Communications, HP3C’21, Guangzhou, China, 18–20 June 2021; pp. 50–54. [Google Scholar] [CrossRef]
- Xiong, Y.; Li, Y.; Zhou, B.; Wang, R.; Rouskas, G.N. SDN enabled restoration with triggered precomputation in elastic optical inter-datacenter networks. J. Opt. Commun. Netw. 2018, 10, 24–34. [Google Scholar] [CrossRef]
- Cavalcante, M.A.; Pereira, H.A.; Almeida, R.C. SimEON: An open-source elastic optical network simulator for academic and industrial purposes. Photonic Netw. Commun. 2017, 34, 193–201. [Google Scholar] [CrossRef]
- Hu, B.; Majid, M.J.; Ramamurthy, B. Dynamic network simulation using DeepRMSA in Elastic Optical Networks. In Proceedings of the 2022 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Gandhinagar, Gujarat, India, 18–21 December 2022; pp. 287–292. [Google Scholar] [CrossRef]
- Boyang Hu, M.J.M.; Ramamurthy, B. Integrating SimEON with DeepRMSA for Dynamic Network Simulation of Elastic Optical Networks. Res. Sq. 2023. [Google Scholar] [CrossRef]
- Ferrari, A.; Filer, M.; Le Rouzic, E.; Kundrát, J.; Correia, B.; Balasubramanian, K.; Yin, Y.; Grammel, G.; Galimberti, G.; Curri, V. GNPy: An open source planning tool for open optical networks. In Proceedings of the 2020 International Conference on Optical Network Design and Modeling (ONDM), Barcelona, Spain, 18–21 May 2020; pp. 1–6. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).