Abstract
Internet of Drones (IoD), designed to coordinate the access of unmanned aerial vehicles (UAVs), is a specific application of the Internet of Things (IoT). Drones are used to control airspace and offer services such as rescue, traffic surveillance, environmental monitoring, delivery and so on. However, IoD continues to suffer from privacy and security issues. Firstly, messages are transmitted over public channels in IoD environments, which compromises data security. Further, sensitive data can also be extracted from stolen mobile devices of remote users. Moreover, drones are susceptible to physical capture and manipulation by adversaries, which are called drone capture attacks. Thus, the development of a secure and lightweight authentication scheme is essential to overcoming these security vulnerabilities, even on resource-constrained drones. In 2021, Akram et al. proposed a secure and lightweight user–drone authentication scheme for drone networks. However, we discovered that Akram et al.’s scheme is susceptible to user and drone impersonation, verification table leakage, and denial of service (DoS) attacks. Furthermore, their scheme cannot provide perfect forward secrecy. To overcome the aforementioned security vulnerabilities, we propose a secure mutual authentication and key agreement scheme between user and drone pairs. The proposed scheme utilizes physical unclonable function (PUF) to give drones uniqueness and resistance against drone stolen attacks. Moreover, the proposed scheme uses a fuzzy extractor to utilize the biometrics of users as secret parameters. We analyze the security of the proposed scheme using informal security analysis, Burrows–Abadi–Needham (BAN) logic, a Real-or-Random (RoR) model, and Automated Verification of Internet Security Protocols and Applications (AVISPA) simulation. We also compared the security features and performance of the proposed scheme and the existing related schemes. Therefore, we demonstrate that the proposed scheme is suitable for IoD environments that can provide users with secure and convenient wireless communications.
1. Introduction
Internet of Drones (IoD) [1], which is often referred to as an unmanned aerial vehicles (UAVs) network, is a layered network control architecture designed to coordinate the access of drones. Drones in IoD environments can perform various flight tasks by embedding various sensors, actuators, recorders, batteries, computations, and communication modules. Figure 1 shows the basic structure of a drone in IoD environments. With these modules, drones are used to control the airspace and offer services such as rescue, healthcare, traffic surveillance, environmental monitoring, delivery, and search to users [2]. The IoD architecture generally comprises remote users, a control server, and drones. Remote users query the information of drones to receive useful services. The control server is centrally located in the wireless communication flow, mediating and providing a seamless data exchange process between remote users and drones. Drones, located in their own flying zone, collect surrounding environment information and send it to users through the control center.
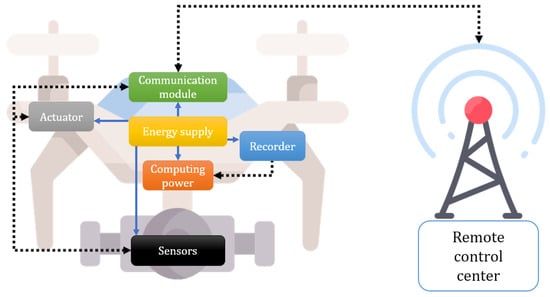
Figure 1.
Basic structure of the drone in IoD environments.
Although IoD environments offer useful services to users, they can suffer from several privacy and security issues [3]. Firstly, IoD environments can be vulnerable to various security attacks, such as eavesdropping, deleting, and intercepting, because all messages are transmitted via a public channel. Moreover, the mobile devices of remote users can be stolen/lost, and the sensitive stored data of these devices can threaten the whole IoD environment. Additionally, drones can be physically captured by malicious adversaries who can try to impersonate them using secret information extracted from drones using power analysis attacks. Finally, drones in IoD environments are designed to use restricted power, computation, and storage sources because the entire energy source is preferentially devoted to flying tasks. Thus, a secure and lightweight authentication scheme is necessary, considering the above security vulnerabilities and specific features of IoD environments.
In 2021, Akram et al. [4] proposed a user–drone access scheme designed to be secure and lightweight for drone networks. The authors claimed that the scheme resists user, control center, and drone impersonation attacks and provides anonymity and untraceability. However, we find that Akram et al.’s scheme is vulnerable to drone impersonation, verification table leakage, and denial of service (DoS) attacks. In addition, their scheme cannot ensure perfect forward secrecy and fails to guarantee correctness. To improve these vulnerabilities, we propose a mutual authentication and key agreement (MAKA) scheme that can provide convenient services to users with high security and efficiency for IoD environments. In the proposed scheme, we utilize biometrics [5] to resist various security attacks, such as offline guessing attacks on user devices. Moreover, we apply physical unclonable function (PUF) [6] technology to prevent cloning and physical attacks of drones using power analysis attacks. Considering real-time communication in IoD environments and the limited computation resources of user devices and drones, we only utilize hash functions and exclusive-OR operators, which are reliable in terms of computation and communication overheads.
1.1. Research Contributions
- We review and perform a security analysis of Akram et al.’s scheme. Then, we propose a MAKA scheme designed to ensure high security using biometrics and PUF. Hash functions and exclusive-OR operations are used for lightweight architecture, making the proposed scheme suitable for drone networks. Moreover, a fuzzy extractor and PUF are applied in the proposed scheme to enhance the security level.
- We prove the security robustness of the proposed scheme using the Automated Verification of Internet Security Protocols and Applications (AVISPA) simulation tool [7,8], Real-or-Random (RoR) model [9], and Burrows–Abadi–Needham (BAN) logic [10].
- We perform an informal analysis to ensure that the proposed scheme can provide security against various attacks, including offline password guessing, session key disclosure, verification table leakage, impersonation, and DoS attacks. Additionally, we show that the proposed scheme can achieve mutual authentication, perfect forward secrecy, untraceability, and anonymity.
- We evaluate and compare the security features, communication, and computation costs of the proposed scheme with existing authentication schemes, including Akram et al.’s scheme.
1.2. Organization
In Section 2, we introduce existing studies on IoD environments. We provide a system model as well as an adversary model, fuzzy extractor, and PUF used in the proposed scheme in Section 3. Then, we show Akram et al.’s scheme in Section 4. Section 5 describes security vulnerabilities discovered in Akram et al.’s scheme. The proposed scheme is introduced in Section 6. Security analyses, i.e., BAN logic, RoR model, AVISPA, are shown in Section 7, and performance analyses, i.e., security features, communication, computation costs, are shown in Section 8. In Section 9, we conclude our paper and describe future works.
2. Related Works
Since the basic concept of IoD environments was introduced by Gharibi et al. [1], various authentication schemes have been proposed over the past few years. In 2018, Wazid et al. [11] proposed an authentication scheme to provide remote users with drone services based on three-factor technology. To apply lightweight communication services, Wazid et al. utilize hash function and exclusive-OR operators. However, their scheme cannot prevent privileged insider and impersonation attacks. In 2019, Teng et al. [12] analyzed security vulnerabilities, named “attacker mode”, which can happen in IoD environments. Thus, they proposed an authentication scheme utilizing the elliptic curve digital signature algorithm (ECDSA) to verify the legitimacy of identity signatures on drones. However, Teng et al.’s scheme was designed as an authentication scheme involving two-way authentication between drones based on ECC, which incurs a large computational overhead. Srinivas et al. [13] proposed a temporal credential-based authentication for IoD networks. Srinivas et al. argued that security and efficiency are the main requirements for the IoD environment, and a lightweight authentication protocol is essential to satisfy these requirements. In their scheme, the authors claimed that it can resist various security attacks such as a stolen mobile device, replay, MITM, ephemeral secret leakage (ESL), impersonation, password and/or biometric update, and remote drone capture attacks. In 2020, Ali et al. [14] pointed out that Srinivas et al.’s scheme [13] does not provide untraceability and resists stolen verifier attacks. To overcome that, Ali et al. suggested a lightweight authentication scheme for drones using symmetric key primitives and temporal credentials. Ever [15] suggested a framework for mobile sinks used in drones using bilinear pairing and ECC, which has a large computational cost. However, Ever’s protocol cannot provide user anonymity and untraceability [16]. In 2022, Wu et al. [17] proposed a drone communication scheme for 5G networks. They argued that several existing IoD protocols have high computation overheads because of using a public key infrastructure (PKI) mechanism. Therefore, they only utilized hash functions and exclusive-OR operators. In the same year, Tanveer et al. [18] proposed an authentication mechanism for IoD environments. They used an AES-CBC-256 cipher and ECC to ensure the anonymity of users. Although the above schemes [11,12,13,14,15,17,18] provide useful services such as healthcare, rescue, and traffic surveillance, they can suffer from physical attacks because each drone cannot protect security parameters from power analysis attacks.
To strengthen the authentication process and access control of drones, various PUF-based authentication schemes have been proposed. Alladi et al. [19] proposed a two-stage authentication protocol that divided drone hierarchies for smart drone networks. In Alladi et al.’s scheme, each drone equipped with PUF communicates with a ground station through a leader drone, reducing network overhead. Thus, the authors claimed their scheme does not require the storage of secret keys in drones, protecting it from impersonation, drone tampering, and MITM attacks. In the same years, Pu et al. [20] proposed an authentication protocol for drone environments using PUF and chaotic systems. The authors used the challenge–response pair of the PUF as the seed value of the chaotic system to jumble the message randomly. In 2021, Zhang et al. [21] suggested a three-party authentication scheme for IoD environments. In Zhang et al.’s scheme, the head drone manages member drones and mediates the communication between the ground station and member drones. The entire process of their scheme only uses hash functions and XOR operations. Moreover, the authors introduced PUF systems to prevent physical capture attacks.
In 2021, Akram et al. [4] suggested a scheme for secure and efficient drone access in IoD networks. The authors demonstrated that various security attacks, e.g., user, control center, and drone impersonation attacks, can be prevented in their scheme. However, our security analysis indicates that their scheme is vulnerable to DoS, session key disclosure, stolen-verifier, and drone impersonation attacks and cannot provide perfect forward secrecy.
We summarize the cryptographic techniques and the advantages and limitations of the existing related schemes [4,11,12,13,14,15,17,18,19,20,21] in Table 1. Although previous authentication schemes can provide convenient services to users, they still have high computational and communication overhead and security drawback problems. Therefore, we propose a secure drone-access scheme to improve these security flaws considering lightweight communication characteristics of IoD environments. The proposed scheme can provide stolen mobile device and drone impersonation attacks using biometric and PUF technologies, respectively. Moreover, the proposed scheme can support efficient communications using only hash functions and exclusive-OR operators.

Table 1.
Cryptographic technologies and properties of the related schemes for IoD environments.
3. Preliminaries
We present the system model and adversary model for IoD environments. Moreover, we introduce some relevant preliminaries to understand this paper.
3.1. System Model
As shown in Figure 2, IoD environments consist of a control center, users and drones. According to the IoD environment model, various drones collect the data in their particular zones in a target field and transmit the data to the server. External users are required to connect to the server to obtain data from the deployed drones. For access, secure authentication is necessary between the user and drone via the control center. Subsequently, the user and drone pair share a session key and begin communication. The details of this process are as follows.
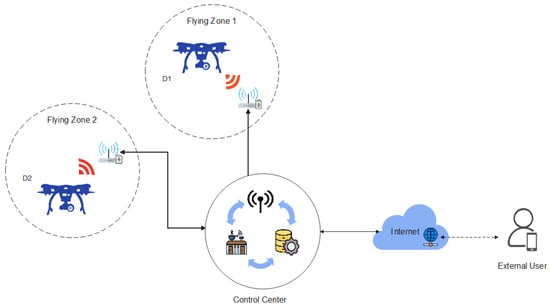
Figure 2.
The general system model of IoD environments.
- Remote user (): A remote user owns a mobile device to receive IoD services. To communicate with a drone , must register with the control center. utilizes biometric technology in addition to identity and password to store sensitive information safely.
- Control center: The control center is a trusted third party with enough computation and storage capacities. Therefore, the control center perform a role as the system manager of IoD environments. Furthermore, the control center authenticates with both and information and helps to access the . The control center generates secret keys for and against their identities.
- Drone (): A drone collects the data in their particular flying zone and must be registered by the control center to communicate with . Then, sends the data to = through the control center. Moreover, has restricted computation and storage capacities.
3.2. Adversary Model
We follow the widely used adversary model, named the “Dolev–Yao (DY) adversary model” [22,23]. Under the DY model, the entities involved in the IoD environments, i.e., and , are not assumed to be trustworthy, and the communication of the channel is insecure. Therefore, an adversary can modify or delete the transmitted messages and also can eavesdrop on the exchanged messages. Furthermore, drones move around in unattended hostile areas with collected sensor data. Thus, they are vulnerable to physical capture attacks [11,24], and the sensitive data stored in the drone can be extracted using the power analysis attacks.
3.3. Fuzzy Extractor
The fuzzy extractor [25] is widely accepted to verify the biometric authentication. A biometric key can be generated with a biometric template such as fingerprints, faces and irises. The fuzzy extractor is defined with the following two algorithms:
- : It is a probabilistic algorithm to generate a secret key . The user inputs biometric , the output of this function is the secret parameter , and the public reproduction parameter .
- : It is a deterministic algorithm to recreate the original . The function accepts a noisy user biometric and controls the noise using the public reproduction parameter . Then, this algorithm reproduces the original biometric secret key .
3.4. Physical Unclonable Function
PUF is a physical circuit that maps a bit-string pair called “challenge–response pair” [6]. When an input challenge value is entered into the PUF circuit, it produces a value that isan arbitrary string of bits. In this paper, we use PUF to generate secret values instead of stringing them in the memory of the drone and obtain a stable response good enough for security using fuzzy extractors. The property of PUF is as below.
- The PUF is a physical microstructure of the device.
- It is extremely difficult or impossible to clone the PUF circuit.
- An unpredictable response value must be output.
- It is possible to evaluate and implement a PUF circuit easily.
4. Revisit of Akram et al.’s Scheme
Akram et al. [4] suggested a drone-access authentication protocol for surveillance tasks in a smart city. Akram et al.’s scheme is composed of the following phases: (1) user registration; (2) drone registration; (3) authentication and key agreement (AKA) phases. Table 2 shows the whole notation and description in their scheme.

Table 2.
Notations and descriptions.
4.1. Registration Phase
4.1.1. Remote User Registration Phase
- Step 1:
- The user inputs their own , and imprints . Then, calculates and sends to the control center.
- Step 2:
- The control center calculates , and generates a random number . After that, the control center computes and sends to .
- Step 3:
- computes , . Then, stores .
4.1.2. Drone Registration Phase
- Step 1:
- selects and sends it to the control center.
- Step 2:
- The control center computes , and stores in its database. Then, the control center sends to .
- Step 3:
- When receives , saves them in the memory.
4.2. AKA Phase
- Step 1:
- inputs , and also imprints . Then, computes , , . Afterward, generates and computes , and . Finally, sends to the control center.
- Step 2:
- The control center retrieves . Then, the control center computes , and , and verifies against . Then, the control center computes and checks . The control center generates , and computes , , and . Finally, the control center sends , to the drone .
- Step 3:
- computes , and . Then, checks and generates . After that, computes , , and . Finally, sends , to .
- Step 4:
- The computes , and . Then, it validates and computes .
5. Cryptanalysis of Akram et al.’s Scheme
According to Section 3.2, an adversary can obtain a from legitimate user’s mobile device. Moreover, can obtain from a captured drone using a power analysis attack. With this information, various security attacks, i.e., session key disclosure, drone impersonation, stolen-verifier, DoS attacks, and perfect forward secrecy, can be executed by . The details are shown below.
5.1. Session Key Disclosure Attack
For to generate a session key , has to obtain and . The procedures are as follows.
- Step 1:
- computes , , and .
- Step 2:
- calculates .
Thus, Akram et al.’s scheme is insecure against session key disclosure attacks.
5.2. Drone Impersonation Attack
In this attack, we assume that can capture drones physically and obtain the value stored in the memory of . In order to be able to forward message on behalf of legal , then has to calculate the value of , can compute the and through the following below:
- Step 1:
- The adversary first intercepts transmitted by the public channel.
- Step 2:
- can obtain , by computing .
- Step 3:
- can compute through .
- Step 4:
- generates random and computes .
- Step 5:
- can successfully compute , .
Therefore, Akram et al.’s scheme cannot resist drone impersonation attacks.
5.3. Stolen-Verifier Attack
When obtains the table information of the control center, can calculate . The steps are the same as Section 5.1. Therefore, Akram et al.’s scheme is vulnerable to stolen-verifier attacks.
5.4. Perfect Forward Secrecy
Let us suppose that the control center’s long-term secret key MSK is compromised by the adversary , and has captured all the previously transmitted messages and through the public channel. can retrieve through , compute , , , and . Furthermore, can retrieve and through and compute . Finally, computes the session key . Thus, Akram et al.’s scheme does not provide perfect forward secrecy.
5.5. DoS Attack
In the AKA phase, the login process is not executed normally in the remote user () side. Afterward, the inputs , , and , compute , , and . Then, immediately generates a random nonce and computes an authentication request message . Therefore, the adversary can send unlimited amounts of login authentication request messages to the control center if obtains a stolen/lost mobile device of and inputs a randomly selected identity, password, and biometrics. These messages can threaten the load on the control center. Thus, Akram et al.’s scheme is vulnerable to DoS attacks.
5.6. Correctness
In the user registration phase, the control center calculates the value of . After that, the is not transmitted to , and cannot compute it because the is masked with MSK, which is the control center’s secret key. However, in the AKA phase, sends the to the control center as the first transmitted message. Thus, Akram et al.’s scheme has a correctness problem.
6. Proposed Scheme
The proposed scheme consists of the following phases: (1) initialization; (2) user registration; (3) drone registration; (4) MAKA. We show the flowchart of the proposed scheme in Figure 3. The proposed scheme is lightweight as it uses only the cryptographic one-way hash function and exclusive-OR operations, apart from the fuzzy extractor and PUF technique that is needed for verification at the user side and drone side, respectively.
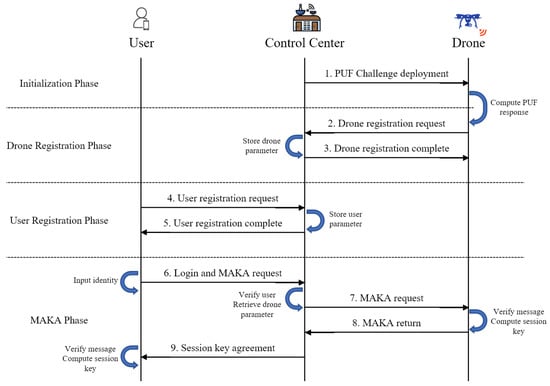
Figure 3.
The overall flowchart of the proposed scheme.
6.1. Initialization Phase
This phase describes that the control center selects an identity and a challenge for the drone before the registration phase. Detailed steps are illustrated in Figure 4. Additionally, this phase is performed via a secure channel.
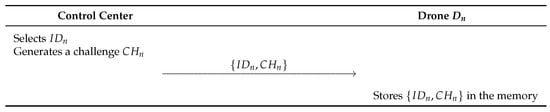
Figure 4.
Initialization phase of the proposed scheme.
- Step 1:
- The control center selects an identity and a challenge and sends to the drone .
- Step 2:
- The drone stores in the memory.
6.2. Drone Registration Phase
In this phase, a drone is registered at the control center to its deployment in the IoD environments through a secure channel. Detailed steps are illustrated in Figure 5.
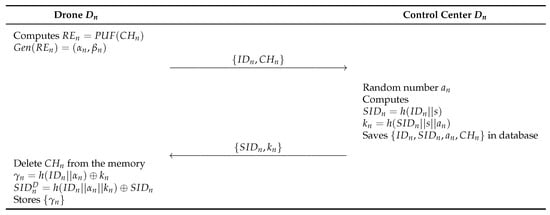
Figure 5.
Drone registration phase of the proposed scheme.
- Step 1:
- The drone retrieves the challenge stored in the memory and computes , and . After that, the sends to the control center.
- Step 2:
- The control center generates a random number and computes , , and saves in the database. Then, the control center sends to the .
- Step 3:
- Finally, the deletes the and computes , , and stores in its memory.
6.3. User Registration Phase
In the user registration phase, a remote user has to register at the control center to access the real-time information from an accessed drone in IoD environments. This procure performs via a secure channel with the following steps. Figure 6 shows the details.
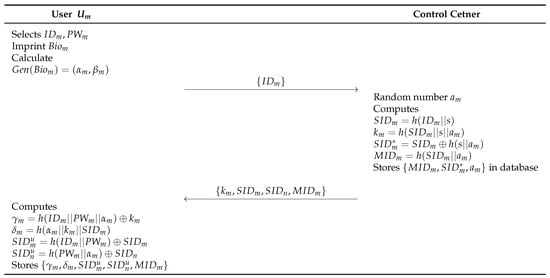
Figure 6.
User registration phase of the proposed scheme.
- Step 1:
- The user selects an identity , a password , and a biometric template . After that, the mobile device calculates . The sends to the control center.
- Step 2:
- The control center generates random number and computes , , and . Then, the control center stores in the database, and sends , to the .
- Step 3:
- The computes , , , and , and stores in the memory.
6.4. MAKA Phase
The following steps are performed among the , the control center, and an accessed drone through a public channel. To establish a session key for secure communication among them, they need to perform the MAKA processes. Details are illustrated in Figure 7.

Figure 7.
MAKA phase of the proposed scheme.
- Step 1:
- The inputs and , and imprints . After that, computes , , , , and , and checks . Then, the generates a random nonce and calculates , , and . The sends to the control center.
- Step 2:
- The control center checks whether or . If then, retrieves against , and if , retrieves against . After that, the control center computes , , , , and . If is correct, the control center computes and updates . Then, the control center checks for against from its database and computes . The control center calculates , , , and and sends to the drone.
- Step 3:
- The drone computes , , , , , , , and . If is correct, the generates a random nonce , and calculates , , , and . Then, the sends to the .
- Step 4:
- The computes , , , and and checks . Then, the updates .
7. Security Analysis
To prove the security robustness of the proposed scheme, BAN logic, RoR model, and AVISPA simulation are used in this section. Using informal security analysis, we analyze the theoretical security of the proposed scheme.
7.1. BAN Logic
BAN logic [10] is a widely known formal proof used by many researchers to show mutual authentication of protocols [26,27,28]. Therefore, we apply the proposed scheme to BAN logic proof and verify mutual authentication. We introduce notations and descriptions for BAN logic in Table 3.

Table 3.
Basic notations in BAN logic.
7.1.1. Rules
In BAN logic, there are five logical rules: message meaning rule (MMR), nonce verification rule (NVR), jurisdiction rule (JR), belief rule (BR), and freshness rule (FR). Details are as follows.
- 1.
- MMR:
- 2.
- NVR:
- 3.
- JR:
- 4.
- BR:
- 5.
- FR:
7.1.2. Goals
In the proposed scheme, there are four goals for the BAN logic. Let the user, control center, and drone be , , and , respectively.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
7.1.3. Idealized Forms
Three messages, i.e., , , and , are transmitted via open channels in the proposed scheme. These messages are converted to idealized forms in BAN logic as below.
- :
- :
- :
7.1.4. Assumptions
We show the assumptions using in BAN logic as follows.
- :
- :
- :
- :
- :
- :
- :
- :
7.1.5. BAN Logic Proof
- Step 1:
- We can obtain from the message .
- Step 2:
- We can obtain from the rule MMR using and .
- Step 3:
- We can obtain from the rule FR using and .
- Step 4:
- We can obtain from the rule NVR using and .
- Step 5:
- We can obtain from the message .
- Step 6:
- We can obtain from the MMR using and .
- Step 7:
- We can obtain from the FR using and .
- Step 8:
- We can obtain from the NVR using and .
- Step 9:
- We can obtain from the message .
- Step 10:
- We can obtain from the MMR using and .
- Step 11:
- We can obtain from the NVR using and .
- Step 12:
- We can obtain and from and . Therefore, and can compute the session key , where .
- Step 13:
- We can obtain and from the jurisdiction rule using and , and and , respectively.
7.2. RoR Model
The Real-or-Random model [9] is a formal proof analysis that proves the session key security of the protocol. Thus, we establish a premise for applying the proposed scheme to the RoR model. There are participants, adversaries and queries in our scheme. Participants are the entities that communicate with each other in the proposed scheme. Therefore, participants are as follows: , , and , where i, j, and k are the instances of user, control center, and drone, respectively. The adversary in RoR model can modify, delete, and eavesdrop the exchanged messages. With this ability, the adversary can perform various queries such as , , , and . We describe the details of these queries as below.
- : In this query, the adversary eavesdrop messages are transmitted via an open channel. Therefore, the adversary can obtain messages generated from , , and . This query is a passive attack.
- : In this query, the adversary can obtain secret parameters from using a power analysis attack. Therefore, the query CorruptDevice is an active attack.
- : In this query, the adversary can send messages to all participants , , and . Furthermore, the adversary can obtain returned messages from these participants. Thus, this query is an active attack
- : Before starting the game, an unbiased coin is flipped in this query. The adversary obtains when the session key is fresh. The adversary can also obtain when the session key of the proposed scheme cannot guarantee freshness. If not, the adversary obtains a “null value” ⊥. To achieve a secure session key agreement, the adversary cannot discriminate between the session key and the random number.
Security Proof
Theorem 1.
The adversary attempts to compute the session key in polynomial time. Therefore, we define the possibility that breaks the security of the session key as . Moreover, we define that and are the range space of the function and , respectively. The number of , , and queries are , , and , respectively. We define the secret biometric bits as . At last, we define the Zipf’s parameter [29] as and .
Proof.
The security proof in the proposed scheme is composed of five games . Before starting the game, we define as the probability that wins the game and as the advantage of . We follow the security proof according to [30,31,32].
- :
- In , the adversary selects a random bit r. Thus, we obtain the following equation.
- :
- In , the adversary eavesdrops messages , , and using query. Then, the adversary performs the query to obtain the session key . To compute , the adversary must obtain the random nonces , , and . Moreover, is composed of , , and , where is the secret parameter of user. Therefore, the adversary cannot calculate . Therefore, we can obtain the following equation.
- :
- In , the adversary utilizes and to attack the network. However, all of the parameters are masked in a cryptographic hash function that can prevent the hash collision problem. For this reason, the adversary cannot obtain the session key . According to the birthday paradox [33], we can obtain the following inequation.
- :
- Similar to , the adversary utilizes queries and in this game. According to Section 3.4, the PUF is extremely difficult or impossible to clone. This means the adversary has no advantage in .
- :
- This game is the final game in which the adversary extracts secret parameters from the device of the user using the query . The adversary attempts to calculate from these parameters. However, each parameter consists of a password and the biometrics of a user, and this means that the adversary must guess the password and biometrics at the same time. Since this task is computationally infeasible, the adversary cannot compute . Therefore, we can obtain the following inequation using Zipf’s law [29].
After the game, the adversary guesses the result bits r, and we can make the following equation.
We can calculate and obtain Equation (7) using (1) and (2).
Then, we can calculate and obtain Equation (8) from (6) and (7).
The result (9) can be obtained using the triangular inequality.
After multiplying (9) by 2, we can obtain the required result inequation.
Therefore, we can demonstrate that the proposed scheme can ensure the session key security by proving the Theorem 1. □
7.3. AVISPA Simulation
AVISPA [7,8] is a simulation tool that proves the security robustness of the proposed scheme against replay and MITM attacks. Therefore, various security protocols [23,34,35] are proved by using AVISPA. In this section, we explain the main data flow of AVISPA and show the simulation result.
Firstly, we need to write the proposed scheme as a programming language named “High-Level Protocol Specification Language (HLPSL)” in AVISPA. After writing in HLPSL code, the proposed scheme is converted to “Intermediate Format (IF)”. Then, the translator in AVISPA starts analyzing the IF through the four backends: “On-the-Fly Model Checker (OFMC)”, “Three Automata based on Automatic Approximations for Analysis of Security Protocol (TA4SP)”, “SAT-based Model Checker (SATMC)”, and “Constraint Logic-based Attack Searcher (CL-AtSe)”. Because OFMC and CL-AtSe only support an exclusive-OR operator, the proposed scheme is executed in these backends. The analyzed result is recorded and summarized in the “Output Format (OF)”. If there is a result of “SAFE” in OF, we can demonstrate that the proposed scheme can prevent replay and MITM attacks.
In AVISPA, we define roles to be suitable for the proposed scheme. Therefore, there are three roles in the proposed scheme: the user , control center , and drone . Moreover, we show the session and environment roles in Figure 8.
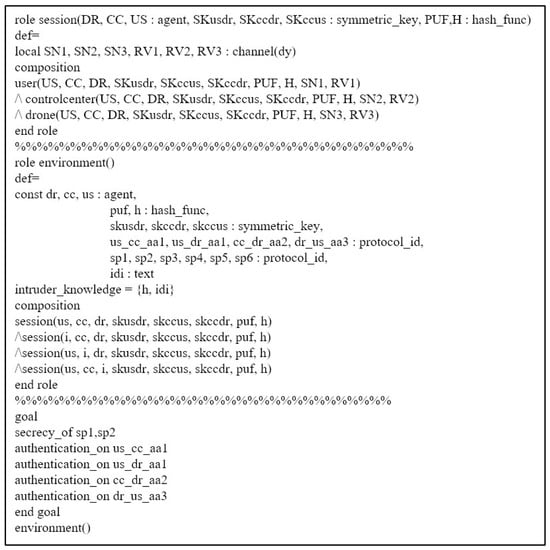
Figure 8.
Session and environment roles written in HLPSL.
Figure 9 shows the role of user written in HLPSL code. State 1 is the user registration phase that sends to the through a secure channel. After receiving return message from , computes and stores , , , and in state 2. Then, computes a login request message to the . Note that and are functions to prove the freshness of random nonce . Finally, receives from and computes the session key . The code means the acceptance of freshness for .

Figure 9.
User role written in HLPSL.
The AVISPA result is shown in Figure 10. As we mentioned before, we execute the proposed scheme in OFMC and CL-AtSe backends, and the summary of the result is “SAFE”. Therefore, we prove that the proposed scheme can prevent replay and MITM attacks.
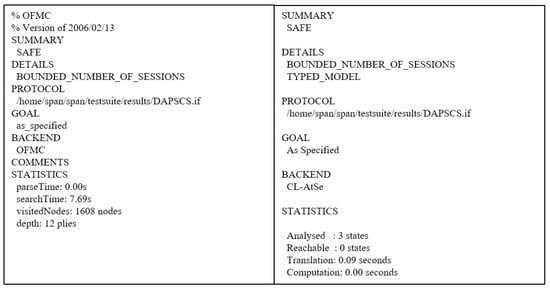
Figure 10.
AVISPA result.
7.4. Informal Security Analysis
We conduct an informal analysis of the proposed scheme to demonstrate the theoretical security robustness. Details are as below.
7.4.1. Stolen/lost Mobile Device Attack
If an adversary obtains a lost mobile device of , it can extract secret parameters using power analysis attacks. However, all of secret parameters are masked in the identity , password , and biometrics information. Therefore, must guess , , and at the same time and this process is not practical. Thus, the proposed scheme is secure against stolen/lost mobile device attacks.
7.4.2. Offline Password-Guessing Attack
An adversary can attempt an offline guessing attack using , , and , and the extracted values , from mobile device and drone, respectively. Using a password dictionary, can guess . However, cannot know that is valid or not. It is because is masked with biometric secret key . Therefore, the proposed scheme prevents offline password-guessing attacks.
7.4.3. Impersonation Attack
- (1)
- User impersonation attack: In this attack, an adversary tries to disguise a legitimate user . has to make a valid login request message . can obtain from the mobile device. However, without having the credentials , and , it is a difficult task for to calculate . Thus, cannot generate a valid login request message on behalf of . Hence, the proposed scheme provides protection against user impersonation attacks.
- (2)
- Control center impersonation attack: For this attack, let us suppose that tries to send the message to the on behalf of the CC. However, without having the credentials , and random nonce , it is computationally hard for to make a valid message. Therefore, the proposed scheme is resilient against the CC impersonation attack.
- (3)
- Drone impersonation attack: This attack is a disguise attack in which a malicious adversary conceals its identity information and attempts to behave as . To do this, computes . Since is a physical unclonable circuit, cannot compute . Therefore, it is impossible to compute , , , to calculate . Thus, the proposed scheme can prevent drone impersonation attacks.
7.4.4. Replay and MITM Attacks
In the proposed scheme, all messages are masked in random nonce , , and to maintain the freshness. Moreover, each participant, e.g., remote user, control center, drone, checks the validity of the message by calculating and checking , , and . Therefore, the proposed scheme can prevent replay and MITM attacks.
7.4.5. Physical and Cloning Attacks
For this attack, an adversary intercepts a drone and extracts the secret parameters from the memory. However, cannot compute the session key because each parameter in the message is masked in the PUF technology, which has an unclonable property. Thus, cannot obtain any advantages from , and this means that the proposed scheme is secure against physical or cloning attacks.
7.4.6. Privileged Insider Attack
In this attack, an adversary is a privileged insider of the proposed system. Thus, can obtain the registration request message and secret parameters from the remote user . However, without having and biometric secret key of , deriving secret credentials and is computationally infeasible. Thus, the proposed scheme prevents privileged insider attacks.
7.4.7. Ephemeral Security Leakage Attack
To prevent this security attack, the proposed scheme must maintain security even if random numbers are leaked. Thus, obtains , which are used during the AKA phase. However, cannot calculate , and without knowing the secret key s to the control center. Additionally, cannot obtain any advantages to impersonate as a legitimate user . Thus, the proposed scheme prevents ephemeral secret leakage (ESL) attacks.
7.4.8. Stolen-Verifier Attack
We can assume that an adversary obtains table data and from the database of the control center and attempts to calculate the session key or impersonate the control center. However, cannot calculate the secret parameter and without the secret keys of the control center and also cannot obtain random number . Thus, cannot compute or impersonate the control center. This means that the proposed scheme is resilient to stolen-verifier attacks.
7.4.9. User Anonymity and Untraceability
An adversary cannot reveal the real identity of a legitimate user because of a cryptographic one-way hash function masks with the secret key of the control center. Therefore, the proposed scheme provides the user’s anonymity.
7.4.10. Perfect Forward Secrecy
If the master key s of the control center is leaked to an adversary , it can attempt to compute to attack the previous session. However, cannot obtain the because does not include s. Moreover, if master secret key s of the control center is compromised, cannot obtain because cannot compute without the real identity of the and without the secret key . Therefore, does not obtain any advantages over . This means that the proposed scheme guarantees perfect forward secrecy.
7.4.11. Mutual Authentication
In the MAKA phase, there are three messages , , transmitted via public channels. Thus, each participant checks the legitimacy of the other participants and messages using , , and in the proposed scheme. If this process is successful, we can ensure authentication. Thus, the proposed scheme guarantees mutual authentication.
7.4.12. DoS Attack
If an adversary tries to transmit to the control center as a replay message, has to pass the login phase by verifying the values of . However, cannot construct a valid because cannot obtain . Therefore, the replay message would not be sent to the control center. Thus, this proposed scheme can resist DoS attacks.
7.4.13. Drone Capture Attack
If an adversary captures a drone and obtains , can try to threaten another legitimate drone . However, all of the drones are secure in PUF technology according to Section 7.4.5, and is an independent parameter. Therefore, the proposed scheme can prevent drone capture attacks.
7.4.14. Session Key Disclosure Attack
To compute the session key , an adversary has to obtain and . However, cannot obtain any of these values because and are masked with secret key s and and are random numbers that are temporarily used in a session. Therefore, the proposed scheme is secure against session key disclosure attacks.
8. Performance Analysis
We demonstrate the security features of the proposed scheme with a related sch- eme [4,14,18,21,24] in terms of “security functionalities”, “communication costs”, and “computation costs”.
8.1. Security Features Comparison
In order to provide visualized information, we offer comprehensive security properties of the proposed scheme and related schemes [4,14,17,18,21,24] in a table. As shown in Table 4, we consider various security functionalities and attacks, including “stolen smart card/mobile device”, “offline password guessing ”, “impersonation”, “replay”, “privileged-insider”, “physical and cloning”, “ESL”, “verification table leakage”, “user anonymity”, “perfect forward secrecy”, “mutual authentication”, “DoS”, “untraceability”, “device/drone capture”, and “correctness”. Thus, our scheme offers secure and functional features as compared to the related schemes [4,14,18,21,24].

Table 4.
Security and functionality features (SFF) comparison.
8.2. Communication Costs Comparison
We demonstrate the comparison analysis for communication costs of the proposed scheme with the other related schemes [4,14,17,18,21,24]. We refer to [4] and assume that the bit lengths for the hash function, random number, identity, PUF challenge, ECC point, and enc-decryption are 256, random, 160, 32, 160, and 128 bits, respectively. Thus, during the MAKA process of our scheme, the exchanged messages require ( bits), the message requires ( bits), and the message requires ( bits), respectively. Table 5 shows the total communication costs of the proposed scheme and the related schemes.

Table 5.
Comparison study of communication costs.
Although our scheme has slightly higher communication costs than Akram et al.’s scheme [4], we offer better security functionalities and efficient computation costs compared to the related schemes [14,17,18,21,24]. Figure 11 illustrates the total communication costs of the proposed scheme and the related schemes.
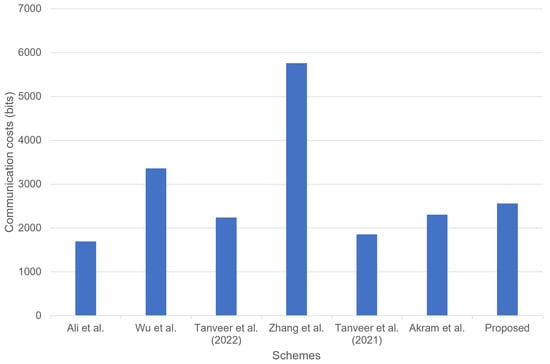
Figure 11.
Communication costs comparison [4,14,17,18,21,24].
8.3. Computation Costs Comparison
We estimate the computation costs of the proposed scheme and [4,14,17,18,21,24] in the AKA phase. Referring to [18,21,24], we define that , , , , , , , and denote the hash function(≈0.029 ms), ECC multiplication(≈0.605 ms), enc-decryption time(≈0.036 ms), fuzzy extractor(≈0.605 ms), AEGIS(≈0.07 ms), FourQ point multiplication(≈1.199 ms), HMAC(≈0.053 ms), and BPV-online function(≈2.117 ms), respectively. Table 6 shows the total computation costs of the proposed scheme and the related schemes.

Table 6.
Comparison study of computation costs.
Compared with the proposed scheme and Akram et al.’s scheme, the proposed scheme consumes more computation costs. However, the proposed scheme utilizes the fuzzy extractor and PUF technologies and, therefore, provides much higher security to the entire IoD network systems than [4]. Figure 12 illustrates that the computational cost (delay) increases at the control center with an increasing number of users.
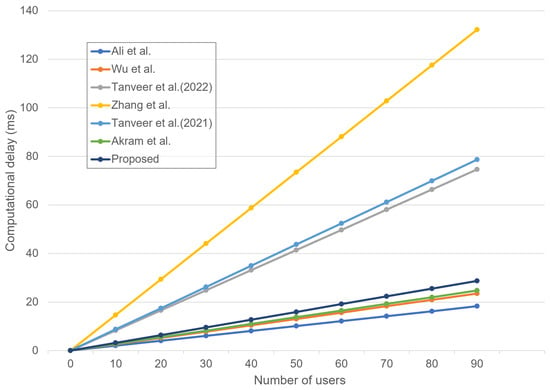
Figure 12.
Computational delay at the control center with increasing the AKA requests [4,14,17,18,21,24].
9. Conclusions
In this study, we reviewed Akram et al.’s scheme, which was proposed for secure authentication between users and drones in IoD networks. In Akram et al.’s scheme, there are several security vulnerabilities, such as session key disclosure, drone impersonation, and stolen-verifier attacks. In addition, their scheme cannot ensure perfect forward secrecy and has correctness problems. To overcome the security flaws of their scheme and provide various functional features, we proposed a secure MAKA scheme using biometrics and PUF technologies. The proposed scheme can provide robustness to withstand various attacks, including session key disclosure, verification table leakage, impersonation, ESL, and privileged insider attacks. Moreover, the proposed scheme can achieve mutual authentication, perfect forward secrecy, and anonymity. To prove the session key security and mutual authentication, we analyzed the proposed scheme using an RoR model and BAN logic, respectively. Furthermore, we simulated the proposed scheme using AVISPA and showed that the proposed scheme is resilient against replay and MITM attacks. A comparative study of functionality features, efficiency, and security shows the effectiveness of the proposed scheme. Therefore, we can demonstrate that the proposed scheme has security robustness compared to existing user authentication protocols for IoD environments with reasonable computation and communication overheads. These characteristics show that the proposed scheme can provide users with high security reliability and high-speed communication in IoD environments. In future work, we intend to implement the proposed scheme in real environments using the mobile device as a user, a desktop as a server, and Raspberry PI 4 as a drone.
Author Contributions
Conceptualization, Y.P. (Yohan Park) and D.R.; Formal analysis, D.R. and D.K.; Methodology, Y.P. (Yohan Park) and D.K.; Software, D.K.; Validation, Y.P. (Yohan Park) and Y.P. (Youngho Park); Formal Proof, D.K.; Writing—original draft, and Y.P. (Yohan Park) and D.R.; Writing—review and editing, Y.P. (Yohan Park) and D.K.; Supervision, Y.P. (Yohan Park). All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Bisa Research Grant of Keimyung University in 2019.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar] [CrossRef]
- Abualigah, L.; Diabat, A.; Sumari, P.; Gandomi, A.H. Applications, deployments, and integration of internet of drones (iod): A review. IEEE Sens. J. 2021, 21, 25532–25546. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.K.R.; Vinel, A.; Huang, X. Security and privacy for the internet of drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Akram, M.W.; Bashir, A.K.; Shamshad, S.; Saleem, M.A.; AlZubi, A.A.; Chaudhry, S.A.; Alzahrani, B.A.; Zikria, Y.B. A secure and lightweight drones-access protocol for smart city surveillance. IEEE Trans. Intell. Transp. Syst. 2021, 23, 19634–19643. [Google Scholar] [CrossRef]
- Umar, M.; Islam, S.H.; Mahmood, K.; Ahmed, S.; Ghaffar, Z.; Saleem, M.A. Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans. Veh. Technol. 2021, 70, 12158–12167. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- AVISPA, T. Automated Validation of Internet Security Protocols and Applications. 2015. Available online: https://www.avispa-project.org/ (accessed on 6 February 2023).
- Glouche, Y.; Genet, T.; Heen, O.; Courtay, O. A security protocol animator tool for AVISPA. In Proceedings of the ARTIST2 Workshop on Security Specification and Verification of Embedded Systems, Pisa, Italy, 18–20 May 2006; pp. 1–7. [Google Scholar]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. (TOCS) 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Design and analysis of secure lightweight remote user authentication and key agreement scheme in Internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Teng, L.; Jianfeng, M.; Pengbin, F.; Yue, M.; Xindi, M.; Jiawei, Z.; Gao, C.; Di, L. Lightweight security authentication mechanism towards UAV networks. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu City, Republic of Korea, 10–13 October 2019; pp. 379–384. [Google Scholar]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. TCALAS: Temporal credential-based anonymous lightweight authentication scheme for Internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Ali, Z.; Chaudhry, S.A.; Ramzan, M.S.; Al-Turjman, F. Securing smart city surveillance: A lightweight authentication mechanism for unmanned vehicles. IEEE Access 2020, 8, 43711–43724. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the internet of drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Deebak, B.D.; AI-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]
- Wu, T.; Guo, X.; Chen, Y.; Kumari, S.; Chen, C. Amassing the security: An enhanced authentication protocol for drone communications over 5G networks. Drones 2022, 6, 10–29. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Naushad, A.; Kumar, N.; Alharbi, A.G. RUAM-IoD: A Robust User Authentication Mechanism for the Internet of Drones. IEEE Access 2022, 10, 19836–19851. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Kumar, N. PARTH: A two-stage lightweight mutual authentication protocol for UAV surveillance networks. Comput. Commun. 2020, 160, 81–90. [Google Scholar] [CrossRef]
- Pu, C.; Li, Y. Lightweight authentication protocol for unmanned aerial vehicles using physical unclonable function and chaotic system. In Proceedings of the 2020 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Orlando, FL, USA, 13–15 July 2020; pp. 1–6. [Google Scholar]
- Zhang, N.; Jiang, Q.; Li, L.; Ma, X.; Ma, J. An efficient three-factor remote user authentication protocol based on BPV-FourQ for internet of drones. Peer-to-Peer Netw. Appl. 2021, 14, 3319–3332. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Chattaraj, D.; Bera, B.; Das, A.K.; Rodrigues, J.J.; Park, Y. Designing Fine-Grained Access Control for Software-Defined Networks Using Private Blockchain. IEEE Internet Things J. 2021, 9, 1542–1559. [Google Scholar] [CrossRef]
- Tanveer, M.; Kumar, N.; Hassan, M.M. RAMP-IoD: A robust authenticated key management protocol for the Internet of Drones. IEEE Internet Things J. 2021, 9, 1339–1353. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Kim, M.; Lee, J.; Park, K.; Park, Y.; Park, K.H.; Park, Y. Design of secure decentralized car-sharing system using blockchain. IEEE Access 2021, 9, 54796–54810. [Google Scholar] [CrossRef]
- Kwon, D.K.; Yu, S.J.; Lee, J.Y.; Son, S.H.; Park, Y.H. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef]
- Shashidhara, R.; Nayak, S.K.; Das, A.K.; Park, Y. On the design of lightweight and secure mutual authentication system for global roaming in resource-limited mobility networks. IEEE Access 2021, 9, 12879–12895. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.; Choo, K.K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 156–171. [Google Scholar]
- Kwon, D.; Son, S.; Park, Y.; Kim, H.; Park, Y.; Lee, S.; Jeon, Y. Design of Secure Handover Authentication Scheme for Urban Air Mobility Environments. IEEE Access 2022, 10, 42529–42541. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-based three-factor mutual authentication protocol for telecare medical information system. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).