Abstract
Quantum computing allows the implementation of powerful algorithms with enormous computing capabilities and promises a secure quantum Internet. Despite the advantages brought by quantum communication, certain communication paradigms are impossible or cannot be completely implemented due to the no-cloning theorem. Qubit retransmission for reliable communications and point-to-multipoint quantum communication (QP2MP) are among them. In this paper, we investigate whether a Universal Quantum Copying Machine (UQCM) generating imperfect copies of qubits can help. Specifically, we propose the Quantum Automatic Repeat Request (QARQ) protocol, which is based on its classical variant, as well as to perform QP2MP communication using imperfect clones. Note that the availability of these protocols might foster the development of new distributed quantum computing applications. As current quantum devices are noisy and they decohere qubits, we analyze these two protocols under the presence of various sources of noise. Three major quantum technologies are studied for these protocols: direct transmission (DT), teleportation (TP), and telecloning (TC). The Nitrogen-Vacancy (NV) center platform is used to create simulation models. Results show that TC outperforms TP and DT in terms of fidelity in both QARQ and QP2MP, although it is the most complex one in terms of quantum cost. A numerical study shows that the QARQ protocol significantly improves qubit recovery and that creating more clones does not always improve qubit recovery.
1. Introduction
Quantum computing is a promising solution for the next generation of advanced computing with enormous capabilities. Technology is developing rapidly, and soon quantum computers will exchange quantum messages among themselves, enabling distributed quantum computing. Such quantum computers, connected by the quantum Internet, can be used for various applications ranging from quantum key distribution (QKD) [] to specialized quantum computing tasks [], while guaranteeing information-theoretic security governed by the laws of quantum mechanics, i.e., perfect security as compared to classical approaches []. However, there is a fundamental barrier to the development of distributed quantum computing: the no-cloning theorem [], which makes perfect quantum bit (qubit)—the fundamental unit of quantum information—duplication impossible. This renders some quantum communication paradigms impossible, such as qubit retransmission and point-to-multipoint (P2MP) [].
Currently, quantum computers belong to the Noisy Intermediate Scale Qubits (NISQ) era [], only being capable of working with a small set of noisy qubits. Noisy operations limit the functionality of quantum devices and lead to a great challenge in near-term quantum networks: the loss of the qubit. Several effects can contribute to the loss of qubits: (i) the generation of imperfect entanglement pairs, as entanglement is fundamental for transporting qubits; entanglement describes the phenomenon where two particles can be created in such a way that they are correlated no matter how far apart they are; (ii) imperfect quantum memories and gate operations; and (iii) lossy quantum channels.
A possible solution to recover a qubit loss might be to use error-correcting codes [,,], but these cannot recover information if errors are beyond the error-correcting capability. The authors in [] explored new protocols for communication in a quantum network, specifically addressing the issue of packet loss during transmission. The proposed solution involves a quantum retransmission protocol that utilizes a recursive quantum secret sharing scheme. However, such a solution is suitable for packet quantum networks only when there are low transmission errors.
In classical packet networks, the Transmission Control Protocol (TCP) implements an error-control mechanism based on a variant of the Automatic Repeat Request (ARQ) protocol, which stores and retransmits packets, i.e., bits. One could expect the development of similar protocols based on storing and retransmitting qubits to guarantee quantum messages’ reliability. However, such an approach is impossible in quantum networks due to the no-cloning theorem. Additionally, quantum networks have been mainly studied for point-to-point communications (P2P), whereas P2MP communication is far less explored. For instance, the authors of [] proposed applications of P2MP for continuous variable (CV) quantum access networks, where a single-photon detector was deployed at a node to be shared by up to 64 users for secret key exchange, thus reducing hardware requirements. This innovation overcomes a major limitation, enabling multiuser QKD networks with resource efficiency. In this paper, however, we target discrete variable (DV) systems. The difference between these two lies in the dimensionality of the state space. The DV is finite-dimensional while the CV is infinite-dimensional. While security for DVs has been perfectly proven against an eavesdropper, security proofs are still less advanced for CVs []. Like qubit retransmission, the limiting factor to implement P2MP communications in DV systems is the no-cloning theorem, since each single qubit needs to be delivered to multiple destinations.
An alternative to implement reliability and P2MP in quantum communications consists of making clones of qubits. Although perfect cloning is impossible, imperfect clones of qubits can be made using quantum cloning machines. In this regard, fidelity is the measure of how similar to the initial quantum state the best possible quantum clone can be made. Since perfect cloning has a fidelity of 1, the fidelity of imperfect cloning should be as close as possible to that value, since a value equal to or below 0.5 means that the clone is no longer usable. In fact, the maximum theoretical fidelity is bounded, and its value depends on the number of states to clone and the number of clones to be made []. Different types of quantum cloning machines have been proposed in the literature (see, e.g., [,,,,,]). For our study, we consider the Universal Quantum Copying Machine (UQCM) [], which creates imperfect optimal clones of the original qubits, i.e., it achieves the theoretical maximum, and it can be used to generate multiple qubit copies. The UQCM provides equal fidelities of all the states. However, the maximum theoretical fidelity of a two-state input qubit is bounded to 0.833, 0.77, and 0.75 for two, three, and four clones, respectively.
In this paper, we extend our works in [,] and propose taking advantage of the UQCM for reliable and P2MP quantum communications. Specifically, the contributions of this work are the following:
- The Quantum Automatic Repeat Request (QARQ) protocol, which combines classical and quantum channels to provide reliable transmission. Here, clones can be created and stored in quantum memories ready to be used in case of qubit loss;
- Enabling Quantum P2MP (QP2MP) communications, where the transmitter generates multiple clones of each incoming qubit and sends them to a set of destinations.
We have developed a simulation platform using NetSquid [] to evaluate the feasibility of the QARQ protocol and QP2MP communications in the presence of various noise sources. These protocols are studied for three different quantum technologies: (i) direct transmission (DT), which uses a quantum channel for qubit transmission; (ii) teleportation (TP) [], which uses entanglement for transporting qubits; and (iii) telecloning (TC) [], which uses teleportation and cloning natively in the protocol. We use fidelity as a metric to evaluate the performance of the proposed protocols for the three quantum technologies studied.
The rest of the paper is organized as follows. Section 2 gives the needed background on quantum communications, shows how QARQ and QP2MP can be enabled, and presents the sources contributing to qubit decoherence (the gradual degradation of qubit coherence over time). Section 3 focuses on the implementation of QARQ and QP2MP. Section 4 evaluates the feasibility of QARQ and QP2MP for short- and long-distance quantum communication and determines which method is best suited to achieve the best quality of qubit state. Complexity analysis is carried out for each case. Finally, Section 5 draws the main conclusions of this work.
2. Quantum Bit Retransmission and Quantum Point-to-Multipoint Communications
This section introduces quantum communication and aims to provide the required background to understand the core concepts described in this paper. Then, the basics on how a quantum communication channel is established using QARQ or QP2MP is described, and the sources of decoherence present in QARQ and QP2MP for DT, TP, and TC are demonstrated.
2.1. Background on Quantum Communication
Quantum communication involves moving away from classical forms of communication to instead take advantage of the laws of quantum physics. Classical computers send data as classical bits of either 0 or 1, whereas quantum computers communicate via the transmission of quantum states. The latter relies on qubits, where, when only two states are considered, data are sent as superpositions of 0 and 1. Like classical logic gates, quantum computers use quantum gates to perform quantum operations that change the qubit’s state to a desired one [].
Various platforms are available for quantum computing: superconducting qubits [], trapped ions [], and Nitrogen-Vacancy (NV) centers in diamond [], to name a few. Each platform possesses its own pros and cons. Superconducting quantum computing implements quantum computing with superconducting electronic circuits. Superconducting qubits have fast decoherence times and gate operation, but they must also be kept in the extreme cold, which is costly and troublesome. Trapped ion computers—charged atomic particles confined and suspended in free space—have longer decoherence times compared to superconducting quantum computers. While a trapped ion computer can run at room temperature, the ions must be cooled for optimal performance, and they are slower than a superconducting qubit. Finally, the NV center platform uses an electron spin inside an NV center in a diamond lattice. It has a long coherence period and high gate decoherence, but it can be operated at room temperature. All three platforms tend to face qubit decoherence, which is the main limitation in quantum communication and needs to be carefully addressed. In this paper, we use the NV center platform for analysis and simulation since it makes it possible to send quantum states far away to connect and entangle NV centers over distance, thus making quantum Internet possible. Furthermore, diamond spin qubits [] enable quickly establishing robust entanglement links, which is one of the primary requirements of quantum networks.
In contrast to classical networks, where data must be delivered error-free, quantum applications can operate with imperfect quantum states as long as fidelity is greater than an application-specific threshold. For instance, the threshold fidelity for basic QKD is about 0.8 [], i.e., very close to the fidelity of optimal cloning. Importantly, fidelity and decoherence are interdependent; reduction in fidelity occurs as we lose qubit coherence, which makes decoherence one of the critical challenges in quantum networks. In particular, the loss of quantum state fidelity in a quantum network occurs in several ways:
- Qubits interact with the environment, mainly when traversing a quantum transmission channel, which is particularly relevant in the DT case and limits the distance that a qubit can traverse. However, this can be avoided by using entanglement distribution networks [] that allow the qubit to be transported without traversing the channel.
- Imperfect entanglement reduces fidelity in entanglement distribution networks. Therefore, we can receive benefits from entanglement distribution networks only when they outperform the fidelity degradation caused by using the quantum channel.
- Coherence degrades a quantum state’s fidelity while the qubits are stored in a quantum memory, and it puts highly stringent requirements on how long qubits can be held in memory. Although lab tests have shown memory lifetimes of up to one minute, experiments with network-connected devices showed memory times reduced to just a few milliseconds []. Different platforms have different methods of implementing quantum memories. In the case of the NV center platform, the electronic spin of NV centers and the neighboring nuclei enable NV-based interaction with individual nuclear spins, possessing remarkably long-lived quantum states and providing supplementary states for quantum memory [].
- Imperfect implementations of quantum gates reduce fidelity whenever any qubit is processed.
This paper considers all the above loss of quantum state fidelity to evaluate the proposed QARQ and QP2MP.
2.2. Quantum Communications Enabling QARQ and Sources of Decoherence
Figure 1 describes the QARQ protocol, where we consider a quantum communication system consisting of two quantum nodes, namely Alice (A) and Bob (B). The quantum channels (solid lines) are used to transmit qubits from A to B by means of DT, TP, or TC, while the classical channels (dashed lines) are used to exchange classical messages between them. As in classical ARQ, QARQ uses acknowledgements (ACKs) and timeout messages to achieve reliable quantum communication over an unreliable quantum system. Alice may send the quantum data with error detection codes, e.g., repetition codes to check whether the quantum data are received correctly. If no error is detected, B notifies A using a positive ACK (PACK) via the classical channel and the quantum memory is flushed (Figure 1a). Conversely, if an error is detected and it cannot be recovered, B discards the quantum data and sends back a negative ACK (NACK) (Figure 1b). When A receives the NACK, the cloned quantum data stored in the quantum memory are sent to B. Additional retransmissions can be performed if more clones are generated but at the expense of the degradation of qubit fidelity, as previously introduced. Moreover, QARQ sets timeouts for retransmission, where A uses the stored qubits if no ACK is received after a specified time period (Figure 1c).
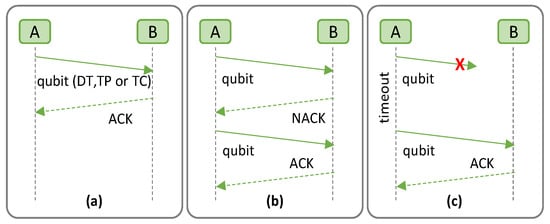
Figure 1.
The QARQ protocol; Qubit received correctly (a); Qubit received with uncorrectable errors (b); Qubit lost, and timeout initiated (c). (X indicates qubit is lost).
Let us now describe the procedure to set up a quantum communication channel enabling QARQ. Figure 2 shows the basic principle of QARQ. The UQCM can create multiple clones for retransmission, where the number of clones to be generated highly depends on the quantum application. In addition, we examine specific factors contributing to qubit decoherence in each of the three quantum technologies studied. This provides insight into a received qubit’s fidelity.
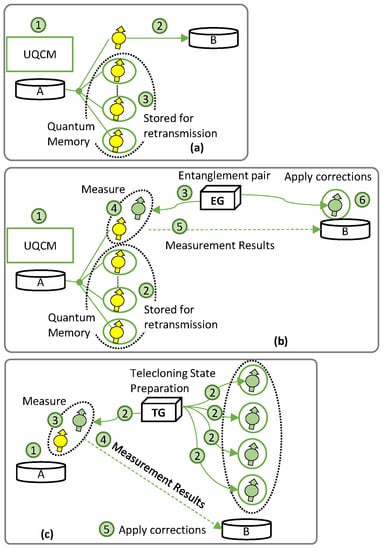
Figure 2.
QARQ for (a) DT, (b) TP, and (c) TC.
Figure 2a represents QARQ implemented on DT (QARQ-DT), where incoming qubits go into the UQCM for cloning before transmission (not shown in the figure); for each received qubit, one of the clones is sent to B using the quantum channel and the others are stored in quantum memories. In QARQ-DT, A generates optimal clones before transmission to B (labeled 1 in Figure 2a); this introduces decoherence due to the delay in gate operation. One of the clones is sent through the quantum channel in DT (2), which causes transmission channel decoherence. The remaining clones are stored in quantum memories, where they decohere until utilized.
Figure 2b shows the implementation of QARQ using TP (QARQ-TP). TP allows the qubit to be transported to the destination by making use of quantum entanglement and classical measurement, i.e., without traversing the quantum channel. In this case, predistributed entanglement pairs are provided to A and B by an entanglement pair generator (EG), which EG can be located at any intermediate point between A and B. Alice uses the UQCM to generate clones of the incoming qubits (1 in Figure 2b); one is used for transportation and the rest of the clones are stored in the quantum memory (2). The EG (3) generates entangled pairs for A–B. We assume entanglement pairs for all the clones are generated at the beginning of the session. The fidelity of the teleported qubit degrades if the entanglement generation is not perfect. Next, bell measurements between clones and entangled qubits are performed at A (4) and the results are sent to B via the classical channel (5). Due to this, the entangled qubit at B must wait in the quantum memory, where decoherence also occurs. After that corrections are applied (6). If retransmission is needed, it will occur by utilizing the decohered entanglement pairs and clones waiting in the quantum memories.
Finally, Figure 2c represents QARQ exploiting TC (QARQ-TC). TC requires the preparation of telecloning states by a telecloning state generator (TG) and a measurement to create and send all the clones together. A holds a qubit (1 in Figure 2c) and the TG prepares the TC states and distributes them between A and B (2). Note that all clones are sent directly to B, which uses the first one and stores the rest in its quantum memory. If the fidelity of the TC state is imperfect, it impacts the fidelity of the transported qubit. Meanwhile, A performs measurement between the source qubit and the TC one (3). Measurement results are sent to B via classical channel (4), where corrections are applied (5). Due to (3) and (4), the TC qubit at B must wait in a quantum memory, where it experiences decoherence (5).
2.3. Quantum Communications Enabling QP2MP and Sources of Decoherence
Figure 3 shows the setup for QP2MP communications, where A holds a qubit and wishes to send it to several recipients (B, Charlie (C), etc.). The best A can do is to realize optimal copies of the quantum states and send them to the desired destinations. For the sake of simplicity, only two destinations are considered. As in the previous subsection, we examine specific factors contributing to qubit decoherence in each of the three quantum technologies studied.
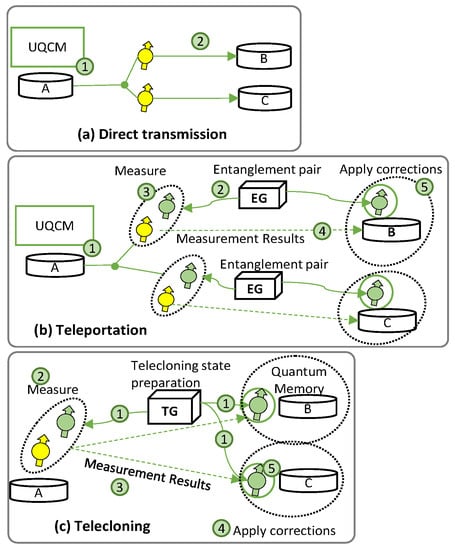
Figure 3.
Example of QP2MP using DT (a), TP (b), and TC (c).
Figure 3a represents the QP2MP implementation for DT (QP2MP-DT). Here, quantum clones are sent to multiple destinations (to B and C in Figure 3a). Alice generates optimal clones before transmission to destinations B and C (1 in Figure 3a), which introduces decoherence due to the delay in gate operation. Clones are sent through the quantum channel in DT (2), which brings transmission channel decoherence.
Figure 3b represents the implementation for TP (QP2MP-TP), where all clones are sent to multiple destinations by using the predistributed entanglement pairs. We assume that the EG is at some intermediate location between A, B, and C. As in DT, A generates optimal clones for B and C (1 in Figure 3b). However, in this case, the qubits are transported using quantum entanglement and classical measurement without traversing the quantum channel. The EG generates entangled pairs for A–B and A–C (2), which degrades the fidelity of the teleported qubit if the entanglement generation is not perfect. Next, bell measurements between clones and entangled qubits are performed at A (3), and the results are sent to B and C via the classical channel (4). Due to (3) and (4), the entangled qubits at B and C must wait in the quantum memory, where decoherence occurs, before applying corrections (5).
Finally, Figure 3c depicts QP2MP using TC (QP2MP-TC), where all the clones are received by all the destinations and utilized for processing. QP2MP-TC also needs a TG at some intermediate location. The TG prepares the TC state and distributes it among A, B, and C (1 in Figure 3c). If the fidelity of the TC state is imperfect, it impacts the fidelity of the transported qubit. Meanwhile, A performs measurements between the source qubit and a TC qubit (2). Measurement results are sent to B and C via the classical channel (3), where corrections are applied (4). Then, the TC qubits at B and C must wait in a quantum memory, where they experience decoherence (5).
3. Implementation and Quantum Hardware Design of QARQ and QP2MP
This section is devoted to the implementation of QARQ and QP2MP. First, it details the phases of QARQ and QP2MP, and then, it presents the quantum circuit design for DT, TP, and TC used in QARQ and QP2MP.
3.1. Phases of QARQ and QP2MP
Let us now describe the specifics of QARQ and QP2MP. In the first case, the QARQ-DT, QARQ-TP, and QARQ-TC methods consist of three main phases: (i) initialization; (ii) transmission; and (iii) QARQ. The initialization and transmission phases are jointly executed by both the sender and the receiver, while the QARQ protocol is introduced after transmission begins, with sender and receiver listening to each other. The initialization and transmission phases are different in each of the quantum technologies, while the QARQ phase is similar for DT and TP, but different for TC.
- In the initialization phase in DT and TP, clones using the UQCM are created. In DT, the initialization phase stops here, whereas in TP, M entanglement pairs are also requested and distributed in parallel to nodes A and B to be used during the teleportation phase. In TC, however, a qubit is prepared and a TC state is requested.
- During the transmission phase in DT, clones are sent to B via the quantum channel, whereas in TP and TC, clones are sent by the TP and TC protocols (see Section 2).
- During the QARQ phase, in the case of DT and TP, the receiver waits for the successful recovery of the transmitted clone and sends PACK if the reception is successful and NACK otherwise. The sender waits for the response from the receiver, and if NACK is received or a time limit is exceeded, it retransmits stored clones via DT or TP. The cycle repeats until either PACK is received by the sender or there are no clones left. For TC, all clones are at the side of B, which sends PACK if one of the clones is successfully received and sends NACK if none of the clones is useful, and transmission begins again.
Table 1 shows two types of probabilities of the successful transmission of a qubit with QARQ as a function of the number of generated clones r: (i) pqr(p), where p is the probability of successful transmission without QARQ; and (ii) pqfr(p,fr), where fr is the fidelity of the transported qubit.

Table 1.
Probability of successful transmission.
Note that pqr(·) increases with the number of clones. However, cloning in the UQCM reduces fr, which reduces the probability of successful recovery given by pqfr(·). For instance, let us take the case of two clones, with values p = 0.5 and fr=2 = 0.8. When the clones are produced, the value of pqr=2 increases to 0.75. However, due to the fr=2 value, the combined probability of recovery pqfr=2 is reduced to 0.6. This leads to an overall enhancement of 0.1 in qubit recovery. As a consequence, the optimal number of clones needs to be investigated to maximize pqfr(·).
As for QP2MP, only the initialization and transmission phases are present, which are identical to those in QARQ except that the clones are sent directly to the destinations and not stored in the quantum memory. Also, entanglements are directly utilized for transporting qubits instead of waiting to be used when retransmission is requested, as in QARQ.
3.2. Quantum Circuits Design for QARQ and QP2MP
This section analyses the quantum hardware on the gate level when using DT, TP, and TC to realize QARQ and QP2MP. Table 2 summarizes the used notation.

Table 2.
Notation.
Figure 4 shows a case where the UQCM generates two clones’ states |Ψ*⟩q0 and |Ψ*⟩q1 of a qubit q0. These are prepared in a random state |Ψ⟩ (|Ψ⟩q0). These clones can be used either for DT or TP in QARQ or QP2MP. The following gates are used:
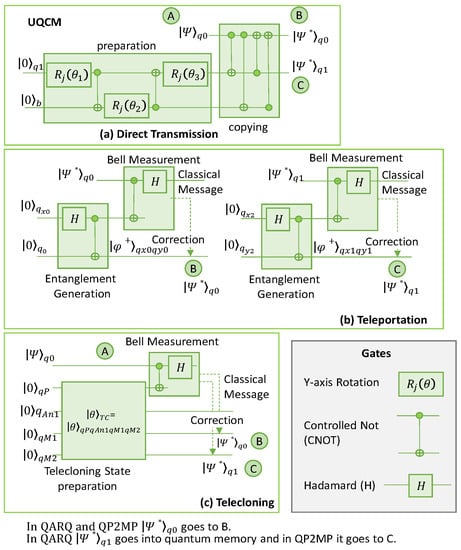
Figure 4.
Quantum circuit for QARQ and QP2MP. DT (a), TP (b), and TC (c).
- The Y-rotation gate performs qubit rotation around the y-axis of the Bloch sphere.
- The Controlled NOT (CNOT) gate acts on two qubits, with one as ‘control’ and the other as ‘target’. It performs a NOT operation on the target if the control is active.
- The Hadamard gate (H) rotates the quantum state by 180 degrees around the vector on the Bloch sphere vector pointing halfway between the x-axis and the z-axis.
3.2.1. Direct Transmission
Let us describe how |Ψ*⟩q0 and |Ψ*⟩q1 are generated by the UQCM in Figure 4a. The cloning at the UQCM can be subdivided into a preparation phase and copying phase. Input q1 represents a blank paper on which information is copied and b is a photocopier machine that aids in the creation of copies but does not include any information of the input qubit; both are initialized to state |0⟩. Before interacting with the original qubit state |Ψ⟩q0, the quantum copier is set in a specified state generated by the preparation block during the preparation state. In the preparation block, three rotations (R(ϴj)) are performed by three Y-rotation gates and two CNOT gates to impose the desired state []. After preparing the qubit states of the quantum copier, four CNOT gates can be utilized sequentially in the copying network to obtain a copy of the initial state.
To help to visualize how the UQCM changes the state of a qubit, Figure 5 shows the Bloch sphere representation of its output in ideal operating conditions. |Ψ⟩q0 is initialized randomly and the two clones (|Ψ*⟩q0 and |Ψ*⟩q1) are created with 83.33% fidelity, showing the difference between cloned states and |Ψ⟩q0. We observe that the cloned state vector maintains its original direction, although its magnitude diminishes.
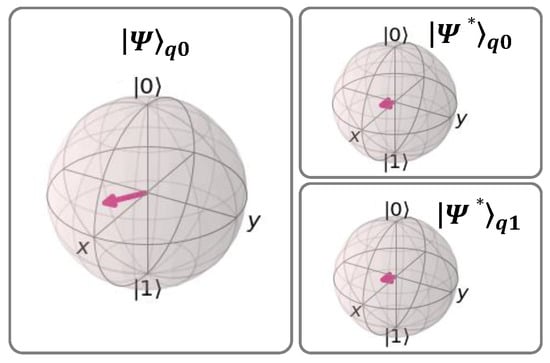
Figure 5.
Bloch sphere representation of UQCM output. The arrow represents the state vector of the qubit.
DT is shown in Figure 4a; for QARQ, |Ψ*⟩q0 is sent to B and |Ψ*⟩q1 is stored in the quantum memory, whereas for QP2MP, |Ψ*⟩q0 is sent to B and |Ψ*⟩q1 is sent to C.
3.2.2. Teleportation
Figure 4b shows the quantum circuit for TP. The first step is to create maximally entangled states (|φ+⟩qxiqyi), all between A and B for QARQ or among multiple parties for QP2MP. In Figure 4b, two entanglement pairs are generated in the states |φ+⟩qx0qy0 and |φ+⟩qx1qy1. To generate the entanglement pairs, qubits qx0 (at A), qy0 (at B), qx1 (at A), and qy1 (at B) are prepared in state |0⟩. The Hadamard gate (H) followed by a CNOT gate are used to generate the entangled state. Then, A performs a bell measurement on |Ψ*⟩q0 and |Ψ⟩qx0, which is performed by applying a CNOT gate followed by an H gate. This provides measurement bits mz and mx, which are sent to B as a classical message which applies correction in terms of Pauli gates (the quantum gates) []. Gate I is applied when both mz and mx are 0, gate X is applied if mx = 1, and gate Z is applied if mz = 1 (gate ZX is applied if both mx and mz are 1). After corrections, the state of qy0 becomes equal to |Ψ*⟩q0. For QARQ, |Ψ*⟩q1 is stored in the quantum memory and teleported later to B, if needed, using |φ+⟩qx1qy1, whereas for QP2MP, |Ψ*⟩q1 is teleported to C immediately using |φ+⟩qx1qy1.
3.2.3. Telecloning
Figure 4c represents the quantum circuit for telecloning. The circuit requires preparing the TC state. This is achieved with one port qubit (qP), with potentially M − 1 ancilla qubits (qAni) and M qubits to be used for making clones (qMi). The TC state is represented by θ⟩TCM = |θ⟩qPqAniqMi []. qP is at the sender side (A), qMi at the receiver side (B and/or C), and qAni can be anywhere. Figure 4c shows the circuit for two clones.
To prepare |θ⟩TC, qP, qAn1, qM1, and qM2 are first set to |0⟩. Then, |θ⟩TC2, representing the telecloning state for two clones, is obtained as defined in Equation (1), by applying gate operations (see [] for details). Note that the state vector is essential to generate the gate-level circuit of this state.
In Figure 4c, A performs a bell measurement on its qubit q0 with qP of |θ⟩TC2 the same as TP and sends the measurement results to B in the case of QARQ, and to B and C in the case of QP2MP, where corrections are applied similarly to TP to convert the states of qM1 and qM2 into |Ψ*⟩q0 and |Ψ*⟩q1.
4. Illustrative Results
In this section, we focus on the evaluation of the performance of QARQ and QP2MP. To that end, we used NetSquid [], a simulator designed specifically for modeling quantum networks that allows for the precise modeling of quantum physical devices. The gates used in the simulations are based on the parameters given in Table 3 [], which indicate NV center implementation and are modeled as depolarizing noise. For a fair comparison, we assume that the depolarization probability (dp) of all gates is equal to 0.01. The depolarization probability per km of the fiber is examined also for channel decoherence. The T1T2 noise model is used for quantum memory, with T1 = 10 h and T2 = 1 s, where T1 and T2 are the decay and decoherence time constants for the NV center platform [,]. For the sake of simplicity, entanglement is generated for each clone at the start of the protocol. Then, each clone has an entanglement pair ready before transmission.

Table 3.
Time duration of operations.
4.1. QARQ
Let us first focus on the performance of quantum technologies for QARQ. Figure 6 compares the performance of QARQ-DT and QARQ-TP for two clones in terms of the fidelity of the received qubit. This can be used later to analyze the significance of implementing QARQ in quantum communication.
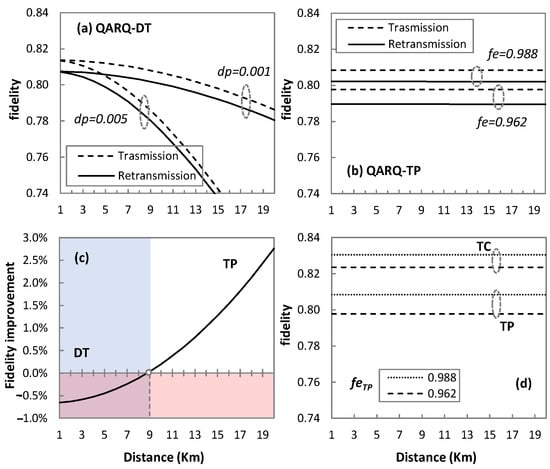
Figure 6.
QARQ quantum technologies performance comparison; Performance of QARQ-DT (a); Performance of QARQ-TP (b); Fidelity improvement in QARQ-TP against QARQ-DT (c); Performance comparison of QARQ-TC and QARQ-TP (d).
In Figure 6a for QARQ-DT, we observe the fidelity of the transmitted and retransmitted qubit. The fidelity of the qubit in DT highly depends on the length of the quantum channel and degrades faster as dp increases (from 0.001 to 0.005 in Figure 6a). This leaves the QARQ-DT protocol as an unsuitable candidate for long-distance transmission as QARQ performance depends on fr (see Table 1). The degrading effect of distance is not observed in Figure 6b, when teleportation is used, since fr mainly depends on the entanglement fidelity (feTP) of entanglement pairs and not on the distance. feTP represents the end-to-end fidelity of the pair once desired ends are reached. However, feTP depends on the distance traversed by entanglement pairs during distribution. To cater this effect, we consider imperfect feTP (0.988 and 0.962 in the case of Figure 6b). Remember that entanglement distillation can be performed to achieve the desired entanglement [], which is out of the scope of this paper. This suggests that QARQ-TP might be a better solution for longer distances. Comparing both solutions, we observe in Figure 6c that DT provides better fidelity in short distances (up to 9 km, shown by coloured regions in Figure 6c), whereas QARQ-TP is superior for longer distances.
QARQ-DT and QARQ-TP depend upon creating clones by the UQCM before sending the qubits to destinations and the UQCM degrades the fidelity of qubit. In the case of QARQ-TC, a special entangled-state TC is used to perform cloning and teleportation, so fidelity mainly depends on the fidelity of the entangled state (feTC). Figure 6d compares the performance of QARQ-TP and QARQ-TC, and it demonstrates that if we consider feTC equal to feTP (0.988 and 0.962), QARQ-TC can provide better fidelity than QARQ-TP (only the transmission case is plotted here). Specifically, we found that the improvement in the fidelity of the received qubit is 2.73% and 3.24% for feTC = 0.988 and feTC = 0.962, respectively.
Let us now perform a quantitative analysis of QARQ by comparing the probability of successful transmission with QARQ (pqfr) and without QARQ (p) (Figure 7). The impact of fidelity degradation in the protocol due to various sources of decoherences is considered.
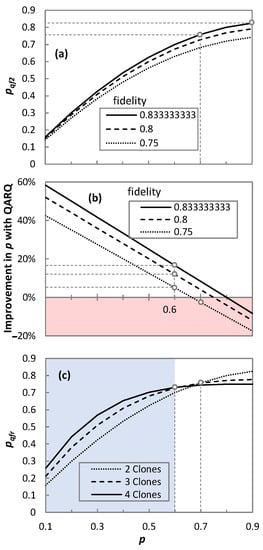
Figure 7.
Probability of successful transmission with and without QARQ; pqfr curve at different fidelities of qubit (a); Improvement in p with QARQ at different fidelities of qubit (b); pqfr curve for different no. of clones (c).
Figure 7a describes the cases where the QARQ protocol could provide better qubit recovery, assuming two clones. Three fidelity values are studied: 0.75, 0.8, and 0.833. When p = 0.7, pqf2 rises to 0.76 for fidelity 0.833. However, when p increases to 0.9, pqf2 is only 0.825 as it can never exceed the maximum theoretical value of 0.833. This means that the protocol can only offer better pqfr when p is lower than the fidelity of the UQCM. Figure 7b shows the improvement of QARQ in the probability of successful transmission for two clones. In the case of p = 0.6, improvements of 16.67%, 12%, and 5% are observed for fidelity values of 0.833, 0.8, and 0.75, respectively. However, for p = 0.7, QARQ fails to provide improvement for a fidelity value of 0.75. Finally, Figure 7c analyzes the QARQ performance for two, three, and four clones (results consider maximum theoretical fidelity) and provides insight about the cases where increasing the number of clones can help. With four clones and p ≤ 0.6, we observe better pqf4 than with only three (pqf3). The same effect can be observed with three clones, which provides better pqf3 than with only two (pqf2). However, for p = 0.7 and three or four clones, QARQ provides improvement in qubit recovery, but two clones seems a better solution in this case due to the large impact of fidelity on QARQ performance. As a conclusion, QARQ-TC provides better fidelity than QARQ-TP, whereas the latter provides better fidelity than QARQ-DT. All these quantum technologies can significantly improve the probability of the successful transmission of qubits. In addition, increasing the number of clones does not always increase the probability of the successful transmission of qubits.
4.2. QP2MP
Let us first study the fidelity of the three quantum technologies applied to QP2MP (Figure 8). We assume a fidelity threshold equal to 0.8, as in QKD [], represented by red line in Figure 8.
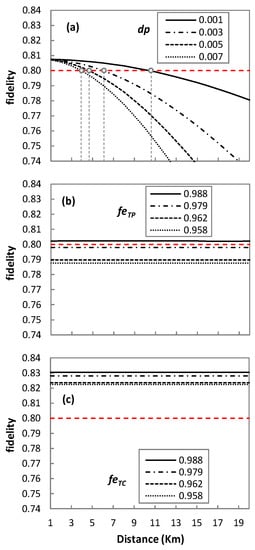
Figure 8.
QP2MP quantum technologies performance comparison; Performance of QP2MP-DT (a); Performance of QP2MP-TP (b); Performance of QP2MP-TC (c).
In the case of DT (Figure 8a), the fidelity of the received qubit highly depends on channel depolarization and degrades drastically as the distance increases. For this reason, results are shown for different values of dp, which reveal that DT may not be the best solution for longer distances. For dp = 0.001, fidelity below 0.8 starts to be observed after 10 km. Similarly, for dp = 0.003, 0.005, and 0.007, fidelity remains above the threshold until 6, 4, and 3 km, respectively. As for TP (Figure 8b) and TC (Figure 8c), the fidelity of the qubit is highly dependent on the fidelity of the entanglement pair (feTP) and the fidelity of the telecloning state (feTC), respectively. We observe that when feTP in Figure 8b and feTC in Figure 8c decrease, the fidelity of the teleported and telecloned qubit also decreases. For TP, the fidelity threshold is met only for feTP = 0.988. However, for TC, all the feTC values provide fidelity above the desired threshold.
TP and TC protocols tend to have no significant effect on fidelity in terms of the transmission distance, but they provide a major degradation of fidelity if entanglement is not perfect. For example, from feTP = 0.988 to 0.979 (Figure 8b) and at 1 km, the fidelity of the teleported qubit drops from 0.802 to 0.798. Similarly, for the telecloned qubit from feTC = 0.988 to 0.979 (Figure 8c) at 1 km, the fidelity drops from 0.830 to 0.828. This could suggest that if entanglement is not perfect, then DT may provide better results for short distances than TP or TC. To illustrate this better, Figure 9 represents the improvement in fidelity by using TP and TC over DT. For feTP = feTC = 0.988 and dp = 0.001, DT outperforms TP for a distance of up to 9 km. However, TC performs better than DT and TP for the same case scenario, and improvement increases with transmission distance. In particular, the improvement in the fidelity of TC is around 3.5% with respect to TP, which increases to 3.77% for feTP = feTC = 0.979.
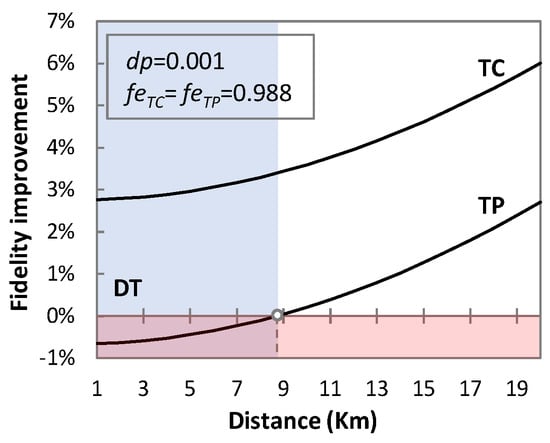
Figure 9.
Fidelity improvement.
The results highlight that TC performs better than TP, whereas TP outperforms DT for longer distances. However, the implementation of TC and TP entails higher complexity. In order to estimate complexity, we compute quantum cost and quantum bits. Quantum cost is computed as the number of 1 × 1 and 2 × 2 quantum gates required in the circuit, i.e., we assume that the quantum cost of all 1 × 1 and 2 × 2 quantum circuits is the same []. For finding the quantum cost of TC, the TC state is prepared using state vector notation and then decomposing it into quantum circuits by using Qiskit []. Quantum bits represent the total number of bits required to create each protocol. Table 4 summarizes the complexity of each protocol, clearly indicating that TC is the most complex protocol in terms of quantum cost, whereas TP is the most complex in terms of qubits (which is not significant for small-scale quantum systems). Therefore, it can be concluded that the optimal protocol depends on the desired fidelity requirement, distance between the nodes, and complexity of each protocol.

Table 4.
Complexity of quantum technologies.
5. Concluding Remarks
In quantum communication, perfect qubit retransmission and P2MP communication are not possible due to the no-cloning theorem. To mitigate such fact, a UQCM has been proposed to create imperfect qubit copies, while sacrificing fidelity. The QARQ protocol has been proposed for qubit retransmission and the QP2MP one has been proposed for P2MP communication. To implement both QARQ and QP2MP, three quantum technologies have been investigated, as they use different means for transporting qubits: DT, TP, and TC.
The performance of the QARQ and QP2MP was studied through simulation. It was shown that the performance of QARQ highly depends on the fidelity of the received qubit and QARQ-TC provides the highest fidelity of the three QARQ protocols. The probability of successful qubit transmission was investigated, and it was shown that increasing the number of clones does not always increase such probability. Regarding QP2MP, results showed that TP and TC provide better fidelity, with TC outperforming TP for longer distances. However, the fidelity of entangled pairs and telecloning states is critical in these two quantum technologies, which is a major research challenge. Finally, analysis of the complexity of DT, TP, and TC revealed that TC is the most complex protocol in terms of quantum cost. A summary of the analysis is presented in Table 5.

Table 5.
Summary of QARQ and QP2MP protocols.
Author Contributions
Conceptualization, L.V. and M.I.; methodology, L.V. and M.I.; investigation, L.V. and M.I.; data curation, L.V. and M.I.; writing—original draft, L.V. and M.I.; writing—review and editing, M.R., N.C., A.N. and J.P.; supervision, M.R., N.C., A.N., J.P. and L.V. All authors have read and agreed to the published version of the manuscript.
Funding
This work has received funding from the European Union’s Horizon Europe research and innovation programme under grant agreement no. 101070009 (ALLEGRO Project), from the AEI IBON (PID2020-114135RB-I00) project, and from the ICREA Institution.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ahmadian, M.; Ruiz, M.; Comellas, J.; Velasco, L. Cost-effective Ml-powered polarization-encoded quantum key distribution. IEEE/OPTICA J. Light. Technol. JLT 2022, 40, 4119–4128. [Google Scholar] [CrossRef]
- Wehner, S.; Elkouss, D.; Hanson, R. Quantum internet: A vision for the road ahead. Science 2018, 362, eaam9288. [Google Scholar] [CrossRef] [PubMed]
- Iqbal, M.; Velasco, L.; Costa, N.; Napoli, A.; Pedro, J.; Ruiz, M. LPsec: A fast and secure cryptographic system for optical connections. IEEE/OPTICA J. Opt. Commun. Netw. JOCN 2022, 14, 278–288. [Google Scholar] [CrossRef]
- Wootters, W.; Zurek, W. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Ruiz, M.; Velasco, L. Performance Evaluation of Light-tree Schemes in Flexgrid Optical Networks. IEEE Commun. Lett. 2014, 18, 1731–1734. [Google Scholar] [CrossRef]
- Preskill, J. Quantum computing in the NISQ era and beyond. Quantum 2018, 2, 79. [Google Scholar] [CrossRef]
- Shor, P. Scheme for reducing decoherence in quantum computer memory. Phys. Rev. A 1995, 52, 2493–2496. [Google Scholar] [CrossRef]
- Wilde, M. Quantum Error Correction; Cambridge University Press: Cambridge, UK, 2013; pp. 553–582. [Google Scholar]
- Roffe, J. Quantum error correction: An introductory guide. Contemp. Phys. 2019, 60, 226–245. [Google Scholar] [CrossRef]
- Yu, N.; Lai, C.; Zhou, L. Protocols for packet quantum network intercommunication. IEEE Trans. Quantum Eng. 2021, 2, 1–9. [Google Scholar] [CrossRef]
- Fröhlich, B.; Dynes, J.; Lucamarini, M.; Sharpe, A.; Yuan, Z.; Shields, A. A quantum access network. Nature 2013, 501, 69–72. [Google Scholar] [CrossRef]
- Laudenbach, F.; Pacher, C.; Fung, C.; Poppe, A.; Peev, M.; Schrenk, B.; Hentschel, M.; Walther, P.; Hübel, H. Continuous-variable quantum key distribution with gaussian—The theory of practical implementations. Adv. Quantum Technol. 2017, 1, 1870011. [Google Scholar] [CrossRef]
- Navez, P.; Cerf, N. Cloning a real d-dimensional quantum state on the edge of the no-signaling condition. Phys. Rev. A 2003, 68, 032313. [Google Scholar] [CrossRef]
- Woodhead, E. Quantum cloning bound and application to quantum key distribution. Phys. Rev. A 2013, 88, 012331. [Google Scholar] [CrossRef]
- Buzek, V.; Hillery, M. Universal optimal cloning of qubits and quantum registers. Quantum Comput. Quantum Commun. 1998, 1509, 235–246. [Google Scholar]
- Iblisdir, S.; Acín, A.; Cerf, N.; Filip, R.; Fiurášek, J.; Gisin, N. Multipartite asymmetric quantum cloning. Phys. Rev. A 2005, 72, 042328. [Google Scholar] [CrossRef]
- Scarani, V.; Iblisdir, S.; Gisin, N.; Acin, A. Quantum cloning. Rev. Mod. Phys. 2005, 77, 1225. [Google Scholar] [CrossRef]
- Shi, P.; Li, N.; Wang, S.; Liu, Z.; Ren, M.; Ma, H. Quantum Multi-User Broadcast Protocol for the Platform as a Service Model. Sensors 2019, 19, 5257. [Google Scholar] [CrossRef]
- Fan, H.; Wang, Y.; Jing, L.; Yue, J.; Shio, H.; Zhang, Y.; Mu, L. Quantum Cloning Machines and the Applications. Phys. Rep. 2013, 10, 544. [Google Scholar] [CrossRef]
- Iqbal, M.; Velasco, L.; Ruiz, M.; Napoli, A.; Pedro, J.; Costa, N. Quantum bit retransmission using universal quantum copying machine. In Proceedings of the 2022 International Conference on Optical Network Design and Modeling (ONDM), Warsaw, Poland, 16–19 May 2022. [Google Scholar]
- Iqbal, M.; Ruiz, M.; Costa, N.; Napoli, A.; Pedro, J.; Velasco, L. Dynamic and efficient point-to-point and point-to-multipoint communications by slicing the optical constellation. In Proceedings of the 2022 Optical Fiber Communications Conference and Exhibition (OFC), San Diego, CA, USA, 6–10 March 2022. [Google Scholar]
- Coopmans, T.; Knegjens, R.; Dahlberg, A.; Maier, D.; Nijsten, L.; Filho, J.; Papendrecht, M.; Rabbie, J.; Rozpędek, F.; Skrzypczyk, M.; et al. NetSquid, a network simulator for quantum information using discrete events. Commun. Phys. 2021, 4, 164. [Google Scholar] [CrossRef]
- Rota, M.; Basset, F.; Tedeschi, D.; Trotta, R. Entanglement teleportation with photons from quantum dots: Toward a solid-state based quantum network. IEEE J. Sel. Top. Quantum Electron. 2020, 26, 6400416. [Google Scholar] [CrossRef]
- Pelofske, E.; Bartschi, A.; Garcia, B.; Kiefer, B.; Eidenbenz, S. Quantum telecloning on NISQ computers. In Proceedings of the 2022 IEEE International Conference on Quantum Computing and Engineering (QCE), Broomfield, CO, USA, 18–23 September 2022. [Google Scholar]
- Bernhardt, C. Quantum Computing for Everyone; The MIT Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Riel, H. Quantum computing technology and roadmap. In Proceedings of the ESSDERC 2022—IEEE 52nd European Solid-State Device Research Conference (ESSDERC), Milan, Italy, 19–22 September 2022. [Google Scholar]
- Png, W.H.; Hsu, T.; Liu, T.-W.; Lin, G.-D.; Chang, M.-S. Quantum computing with trapped ions: An overview. IEEE Nanotechnol. Mag. 2022, 16, 30–36. [Google Scholar] [CrossRef]
- Liu, Y.; Dzeng, Y.; Ting, C. Nitrogen vacancy-centered diamond qubit: The fabrication, design, and application in quantum computing. IEEE Nanotechnol. Mag. 2022, 16, 37–43. [Google Scholar] [CrossRef]
- Humphreys, P.; Kalb, N.; Morits, J.; Schouten, R.; Vermeulen, R.; Twitchen, D.; Markham, M.; Hanson, R. Deterministic delivery of remote entanglement on a quantum network. Nature 2018, 558, 268–273. [Google Scholar] [CrossRef] [PubMed]
- Kozlowski, W.; Wehner, A.D.S. Designing a quantum network protocol. In Proceedings of the CoNEXT’20: Proceedings of the 16th International Conference on Emerging Networking EXperiments and Technologies, Barcelona, Spain, 1–4 December 2020. [Google Scholar]
- Wang, Y.; Yu, X.; Zhao, Y.; Nag, A.; Zhang, J. Pre-established entanglement distribution algorithm in quantum networks. J. Opt. Commun. Netw. 2022, 14, 1020–1033. [Google Scholar] [CrossRef]
- Childress, L.; Hanson, R. Diamond NV centers for quantum computing and quantum networks. MRS Bull. 2013, 38, 134–138. [Google Scholar] [CrossRef]
- Murao, M.; Jonathan, D.; Plenio, M.; Vedral, V. Quantum telecloning and multiparticle entanglement. Phys. Rev. A 1999, 59, 156–161. [Google Scholar] [CrossRef]
- Liao, C.; Bahrani, S.; Silva, F.; Kashefi, E. Benchmarking of quantum protocols. Sci. Rep. 2022, 12, 5298. [Google Scholar] [CrossRef] [PubMed]
- Germain, J.; Dantu, R.; Thompson, M.; Dockendorf, M. Quantum networks: Reset-and-reuse can be a game-changer for entanglement via distillation. In Proceedings of the 2022 IEEE International Conference on Quantum Computing and Engineering (QCE), Broomfield, CO, USA, 18–23 September 2022. [Google Scholar]
- Mamun, M.; Menville, D. Quantum cost optimization for reversible sequential circuit. Int. J. Adv. Comput. Sci. Appl. 2014, 4, 15–21. [Google Scholar]
- Qiskit.org. Available online: https://qiskit.org/ (accessed on 1 August 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).