Abstract
With the development of the Internet of Things, smart grids have become indispensable in our daily life and can provide people with reliable electricity generation, transmission, distribution and control. Therefore, how to design a privacy-preserving data aggregation protocol has been a research hot-spot in smart grid technology. However, these proposed protocols often contain some complex cryptographic operations, which are not suitable for resource-constrained smart meter devices. In this paper, we combine data aggregation and the outsourcing of computations to design two privacy-preserving outsourcing algorithms for the modular exponentiation operations involved in the multi-dimensional data aggregation, which can allow these smart meter devices to delegate complex computation tasks to nearby servers for computing. By utilizing our proposed outsourcing algorithms, the computational overhead of resource-constrained smart meter devices can be greatly reduced in the process of data encryption and aggregation. In addition, the proposed algorithms can protect the input’s privacy of smart meter devices and ensure that the smart meter devices can verify the correctness of results from the server with a very small computational cost. From three aspects, including security, verifiability and efficiency, we give a detailed analysis about our proposed algorithms. Finally, through carrying out some experiments, we prove that our algorithms can improve the efficiency of performing the data encryption and aggregation on the smart meter device side.
1. Introduction
Smart grids [1] play an important role in promoting social stability and the economic development, as they can utilize the information and communication technologies [2] to stably and efficiently generate and distribute electricity. The grid providers can formulate a more reasonable and reliable distribution strategy of electricity by the real-time collection and analysis of the situation of electric generation, transmission and demand/consumption [3]. However, the information exchange between the end user and the grid providers may face some security issues and threats [4,5,6].
The first issue is how to distinguish and authenticate the identity of a new smart meter (SM) or gateway (GW) when it wants to connect to the smart grid system [7,8]. Another issue is how to ensure the privacy and integrity of the collected data from a SM [9,10]. Integrity means to ensure that the exchanged data between the various parts of smart grid will not be modified or deleted. Privacy means to ensure that the collected data will not be leaked to the adversary. The electricity consumption data often contains the user’s confidential information. Once this confidential information is leaked or distorted, it may cause serious harm to the consumers or the grid system [11]. For example, the adversary can analyze the electricity consumption in different time periods to determine whether the owner is at home.
Recently, a number of researchers have designed many multidimensional data encryption and aggregation protocols [12,13,14] to solve the above issues. Although these protocols continually strive to improve the efficiency and enhance the protection of users’ data, these protocols often contain some complex cryptographic operations, such as modular exponentiation operation. In practical application, for the resource-constrained SM, there may be no insufficient computation resources and storage resources to carry out the modular exponentiation operation. The resource-constrained SM may take a long time to execute the designed protocol, which may not meet the requirements for real-time processing grid data. How to improve the execution efficiency of data encryption and aggregation has become an urgent problem to be solved.
Outsourcing computation [15,16] can allow the resource-constrained SM to outsource complex computation tasks to the server (may be another GW) with sufficient computation resources, which is suitable for SMs. However, there are three security challenges [17] for outsourcing computation. Trusted computing [18] may solve these challenges, but it needs corresponding hardware devices. Therefore, it has become more and more popular to design some secure outsourcing algorithms to solve these challenges. The specific challenges are described below. At first, the server is not completely trusted by the user. The outsourced data often contains the confidential data, such as the plaintext of the collected data and the user’s private key in smart grid, which cannot be disclosed to the server. The first challenge is how to protect the privacy of the user’s data in the process of outsourcing computation. Due to the various subjective factors including saving computation resources and objective factors, such as existing system bugs, attacked by hackers, the server may be curious [19,20], lazy and malicious, and thus may try to steal users’ confidential data and return random or computationally indistinguishable results to cheat users. The second challenge is to ensure that the user has the capability to verify the correctness of the returned results. The third challenge is efficiency. The time cost of the secure outsourcing algorithm on the local user side must be lower than that of solving this task by itself. Otherwise, it will be meaningless for the user to execute an outsourcing algorithm. Generally speaking, an outsourcing algorithm must be privacy-preserving, verifiable and efficient.
In this paper, we combine outsourcing computation with data encryption and aggregation to reduce the computational overhead on the SM side and improve the execution efficiency of SMs. Specifically, we explore how to outsource the modular exponentiation operation involved in these data encryption and aggregation protocols to a powerful server. In the designed outsourcing algorithms, SMs can protect the confidentiality and privacy of data by utilizing random splitting technology. In addition, a SM can verify the correctness of results from an untrusted server with a high probability and low computational overhead. We can summarize the contributions of this paper into the following aspects:
- For the different forms of modular exponentiation operation in some data encryption and aggregation protocols, we respectively propose two different outsourcing algorithms. The first outsourcing algorithm can solve modular exponentiation with a fixed base and a variable exponent. The second outsourcing algorithm can solve modular exponentiation with a variable base and exponent. Both of these two outsourcing algorithms can protect the privacy of user’s data by logic division and the Euler theorem;
- The two outsourcing algorithms ensure that a SM can verify the correctness of the returned results. In the first algorithm, an SM can detect a server’s malicious behavior with a probability of 19/20. In the second algorithm, incorrect results from a malicious server can be detected by an SM with a probability of 59/60;
- The two outsourcing algorithms only need one round of communication between the server and SM. Through systematic analysis, we can prove that the proposed algorithms satisfy all security requirements including privacy, verifiability, and efficiency. In addition, we carry out a comprehensive experiment to demonstrate that the proposed algorithms are efficient.
We organize the rest of our paper as follows: in Section 2, we review the related work. We introduce the system model and the threat model and give some formal definitions of secure outsourcing computation in Section 3. In Section 4, we briefly describe a specific data encryption and aggregation protocol and give a detailed description of the proposed outsourcing algorithms. The security and complexity analysis are given in Section 5. In Section 6, we evaluate the proposed algorithms through experiments. After that, we conclude this paper in Section 7.
2. Related Work
In this section, we will introduce some privacy-preserving algorithms for smart grids and review some related works about securely outsourcing modular exponentiation to a malicious server. Table 1 shows the difference between our algorithms and the previous algorithms.

Table 1.
Comparison of algorithms.
2.1. Privacy-Preserving Algorithms for Smart Gird
Saxena et al. [23] proposed a secure and efficient mutual authentication and authorization algorithm in smart grids with an advanced metering infrastructure (AMI). The authors used an attribute-based access control to mitigate outsider and insider threats in smart grids. Their algorithm was suitable for the different user-roles scenario. However, their proposed algorithm could not consider the error detection and the fault tolerance. For secure smart grid communications, Sun et al. [24] put forward an efficient aggregation algorithm (APED) with error detection by employing a pairwise private stream aggregation method. In order to improve the APED algorithm, Shi et al. [25] proposed a diverse grouping-based algorithm (DG-APED) for data aggregation with error detection. The authors applied the differential privacy technique into the grouping-based private stream aggregation and formulated the lifetime of a SM as an exponential distribution to achieve the data aggregation and perform error detection in a malfunctioning SM. In their algorithm, a control center (CC) could only obtain the aggregated results but not the individual data. Bao et al. [26] put forward a new differentially private data aggregation algorithm with fault tolerance named DPAFT. Their algorithm could handle fault tolerance in smart metering by applying a novel key management technique and constructing an artful constraint relation. Based on an improved Boneh–Goh–Nissim cryptosystem, their algorithm could protect the privacy of the user’s data under the honest-but-curious model. Guo et al. [27] put forward a lightweight privacy-preserving data aggregation algorithm by utilizing a novel symmetric homomorphic encryption scheme. In addition, the authors also proposed an authentication agreement algorithm based on the password authenticated key exchange protocol. In order to satisfy the requirement of the fine-grained demands from CC, Li et al. [21] designed a privacy-preserving multisubset data aggregation algorithm named PPMA. Their algorithm could not only aggregate the user’s electricity consumption data of the different ranges, but also protect the privacy of user’s electricity consumption data from being disclosed to a strong adversary. Ge et al. [28] put forward a consortium blockchain-oriented approach to solve the issue of user’s privacy in energy trading in smart grids. The authors designed an account mapping technique to avoid directly exposing user’s data to attackers. Gough et al. [29] designed an innovative differential privacy-compliant algorithm to protect the data from SMs. Their algorithm ensured that the extra costs are divided among the participants by a fair, efficient and equitable manner based on the cooperative game theory.
2.2. Outsourcing Algorithms for Modular Exponentiation
The research on the outsourcing modular exponentiation algorithm [30,31,32,33,34,35,36] mainly focuses on two aspects: two servers and a single server. Under the two-servers model, the user can verify the correctness of the returned result by comparing the results returned from the two servers. Hohenberger et al. [30] gave a formal security definition for securely outsourcing cryptographic computation. The authors also proposed two practical and secure outsourcing algorithms for the Cramer–Shoup cryptosystem and the Schnorr signature. However, the probability that the user could detect malicious behavior from the servers was only 1/2. In order to improve efficiency and verifiability on the user side, Chen et al. [31] put forward new algorithms for the secure outsourcing of modular exponentiation. The verifiability in their algorithms was improved to 2/3. In addition, the authors also designed a secure outsourcing algorithm for simultaneous modular exponentiation. Ye et al. [32] explored how to securely outsource modular exponentiation to malicious servers by utilizing a new logical division method. The user could verify the validity of the returned results with the probability of 19/20. There are also a number of studies that concentrate on designing secure outsourcing algorithms for modular exponentiation under a single server. Wang et al. [33] firstly explored how to securely outsource modular exponentiation to a malicious server. However, the user needed to perform a time-consuming modular exponentiation operation locally once. The verifiability in their algorithm was only 1/2. Based on the Euler theorem, Ren et al. [34] presented an outsourcing algorithm for modular exponentiation under a single server. While improving efficiency, the user could check the failure with a probability of 1. However, their algorithm required the user to pre-compute some random tuples. Zhou et al. [35] put forward a secure outsourcing algorithm for modular exponentiation without pre-computation. The authors designed this new method to protect the privacy of the base, exponentiation and modular exponentiation. The user could detect malicious behavior of the server with a probability of approximately 1.
3. System Model and Definition
In this section, we will give a brief description about the system model and the threat model. Then, we introduce the general framework and some security requirements of the secure outsourcing computation.
3.1. System Model and Threat Model
As shown in Figure 1, the system architecture of a secure outsourcing computation model in a smart grid mainly consists of four entities: smart meters (SM), gateways (GW), control centers (CC) and a malicious server (MS). A detailed description of the functions of these entities is as follows:
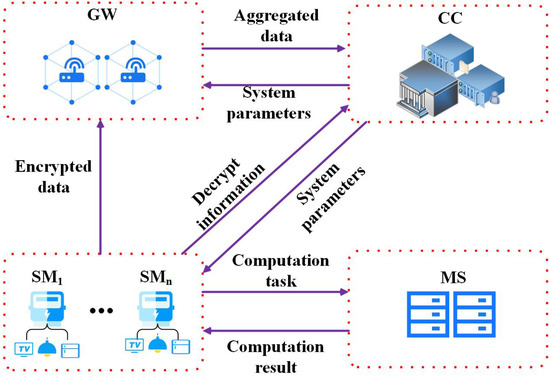
Figure 1.
System model.
- SM: The main function of SMs is to continuously collect various electricity consumption information and other identity information of users, such as the user’s name and location. The SM periodically encrypts the collected data by the modular exponentiation operations and sends it to the GW;
- GW: The main function of a GW is to verify the legitimacy of the received messages and aggregate data reported by multiple SMs. Then, the GW sends the results after aggregation to the CC;
- CC: The main function of a CC is to generate system parameters. When a new device (SM or GW) is connected to the grid network, it will be authenticated by a CC. In addition, a CC can verify the legitimacy of the received messages from SMs and GWs.
- MS: The main function of a MS is to help a SM complete the corresponding complex computation tasks. The SM sends the time-consuming computation tasks to the MS, and the MS returns a correct result to the SM. The MS only communicates with the SM. There is no communication channel between the MS and the GW (or CC).
In our system architecture, we define a SM as an honest entity. The SM will carry out the corresponding operations according to protocol. However, the SM does not have sufficient computation resources and storage resources to complete complex computations. The GW and CC are honest but curious. They will execute protocol honestly, but they try to get the user’s private data during the execution of the protocol. The MS is regarded to be a malicious entity with sufficient computation resources. The MS not only wants to steal the user’s confidential data, but also returns computationally indistinguishable results to deceive the user. This threat model is called the “full-malicious” model [37] and is used in this paper. Therefore, the SM should encrypt the inputs x and outputs y of a computation task F before sending it to the MS and should have capability to verify the correctness of the returned results from the MS.
3.2. Rand Algorithm
The Rand algorithm [38] is used to generate a series of blinded pairs, shaped like . The specific process of the algorithm is as follows:
is a multiplicative group of order M, and is its generator. The user firstly generates n random integers and computes . Then, the user stores and in a table. When the user needs a blinded pair, the user will select k numbers from as S. For each , the user selects a random integer , where , and computes:
The user finally obtains a blinded pair . For a l-bit exponent, for each invoke, the computational complexity of Rand algorithm is .
3.3. General Framework
The general framework of our proposed outsourcing algorithms contains the following sub-algorithms:
- Pre-computation: The SM computes some static parameters in advance to speed up the execution efficiency of algorithms;
- Problem transformation: At the stage of problem transformation, the SM encrypts the computation input x into a public value and stores a secret value locally, which can be used for decryption and verification of the results. Then, the SM sends the computation task F and the public value to the MS;
- Server computation: Based on the received computation task and the value , the MS solves the transformed problem and returns the corresponding result to the SM;
- Result verification: At the stage of result verification, the SM verifies the validity the result based on the stored ;
- Result recovery: If the result successfully passes the verification, the SM decrypts and obtains the real result y.
3.4. Security Requirements
We follow the security definition introduced in [30], which has been widely employed in many previous outsourcing algorithms. A cryptographic algorithm can be divided into two parts: a trusted component T and an untrusted component U. T has access to make queries to U. The adversary A also can be divided into two parts: the adversarial environment E and a malicious component that operates in place of U. E can submit the adversarial input to and can record all information during the execution of . We consider that is an outsource-secure implementation of if (1) T and U implement , i.e., , and (2) a malicious cannot learn anything about the inputs and outputs during the execution of . Furthermore, we formally define the security of the outsourcing computation for the cryptographic algorithm.
Definition 1 (Algorithm with Outsource-IO).
An algorithmobeys outsource input/output specification if it takes in five inputsand generates three outputs. The first three inputs are generated by T and the last two inputs are adversarially submitted by E. The classification of these five inputs depends on howhas knowledge about them. In particular,
Inputs:
- is the honest and secret input, which is only known to T;
- is the honest and protected input, which is known to T and E, but not to ;
- is the honest and unprotected input, which is known to T, E and ;
- is the adversarial and protected input, which is known to T and E, but not to ;
- is the adversarial and unprotected input, which is known to T, E and .
Outputs:
- is the secret output, which is only known to T;
- is the protected output, which is known to T and E, but not to ;
- is the unprotected output, which is known to T, E and .
Definition 2 (Outsource-Security).
Let be an algorithm with outsource-IO. A pair of algorithms can be considered to be an outsource-secure implementation of if:
Correctness: is a correct implementation of .
Security: For anyone probabilistic polynomial-time adversary , there exists the probabilistic expected polynomial-time simulators such that the following pairs of random variables are computationally indistinguishable.
(1) Pair One: .
If the random variables of pair one are computationally indistinguishable, this means the adversarial environment E cannot learn any useful information.
We can formally define the view obtained by the adversarial environment E in the real processing process as follows:
The real process proceeds in rounds. There is an honest and stateful process I, which the environment E does not have access to. In round i, I can pick the honest (secret, protected and unprotected) inputs.
Then, E can choose some parameter values according to its view from the last round. The value of is a way of remembering what it does next time when it is invoked. is the index of inputs (E can only specify the index, but cannot specify their values of these inputs). E can choose the adversarial and protected input and the adversarial and unprotected input . is the Boolean variable, which determines whether the round i is the last round in the process.
Based on the inputs , the algorithm begins to run, where is previously saved by T and generates a new state for T. In addition, produces the secret output , the protected output and the unprotected output . The oracle is given its previously saved state , as input, and the current state of is saved in the variable . E can obtain the final view in the real process, which is just its view in the last round.
The ideal process also proceeds in rounds. In the ideal process, there is a stateful simulator , which can obtain the view when shielded from the secret input . In round i, based on the non-secret outputs that generates, can decide to either output the values generated by or replace them with some other values . Whether will be replaced with depends on the value of , which is a bit. In doing this, is allowed to query the oracle ; additionally, saves its state as in the real experiment.
(2) Pair Two: .
If the random variables of pair two are computationally indistinguishable, this means the malicious software cannot learn any useful information.
The view that the untrusted software can obtain in the real process is the same as that described in pair one. .
In the ideal process, there is a stateful simulator , which can only know the unprotected input and has the access to query . As before, may maintain its state.
Definition 3 (-Efficient [39]).
A pair of algorithms can be considered to be an α-efficient implementation of an algorithm if (1) is an outsource-secure implementation of , and (2) for any inputs x, we suppose that the time cost for a task F to be solved locally by T is and the time cost for a task F to be solved locally by a secure outsourcing algorithm is , which satisfies .
Definition 4 (-Verifiable [39]).
A pair of algorithms can be considered to be a β-verifiable implementation of an algorithm if (1) is an outsource-secure implementation of , and (2) for any inputs x, if there exists the malicious behavior from , the probability that T can detect the error is not less than β.
Remark 1.
In this paper, we do not adopt a method [40] to show the security of our proposed algorithms in a real environment. We only prove that our proposed algorithms meet our proposed security definition through detailed theoretical analysis. In the future research, we will explore how to prove the security in a real environment according to the method proposed in [40].
4. Algorithm
Recently, Zuo et al. [12] put forward a privacy-preserving aggregation algorithm for multidimensional data in a smart grid without a trusted authority. Their algorithm is based on the ElGamal cryptosystem, which can support distributed decryption. This algorithm needs the SM to encrypt the collected data periodically by the ElGamal encryption in the data encryption stage. We will use Zuo’s algorithm as an example to describe our algorithm.
In this section, we will briefly describe Zuo’s algorithm. Then, for the modular exponentiation operation in Zuo’s algorithm, we give a detailed description of our proposed secure outsourcing algorithms.
4.1. Overview of Zuo’s Algorithm
In Zuo’s algorithm, there are six parts in total. We assume that the number of SM is n.
- System Initialization: CC firstly generates a series of system parameters , where G and are the multiplicative cyclic group of a large secure prime p, g is a generator of G, e is a bilinear map: , H is a one-way hash function: , is the public key of CC, and are the superincreasing sequences, and are the k range values of power consumption.
- Registration: All and GW register with CC. chooses a random number and computes the public key and the signature , where is the identity of the user and is the current timestamp. Then, sends to the CC. The CC verifies if holds. Once the equation is established, it means that the registration is successful. The registration progress of the GW is similar. The GW randomly chooses a number and computes the public key .
- Generation of Common Public Key: Each broadcasts its public key and verifies the validity of other public keys from other SMs. Then, computes the common public key as follows:
- Encryption of User Data: Each collects w dimensions of power consumption . is the total power consumption data of each user. If , chooses a random number and computes the corresponding ciphertext based on the common public key and , where and .computes its own signature as follows:sends to the GW.
- Data Aggregation: The GW firstly checks the timestamp and verifies the validity of n signatures. After successful verification, the GW computes the aggregated ciphertext and its own signature . The GW sends , to the CC.
- Decryption of aggregation Data: The CC firstly checks the timestamp and verifies the signature. Each is required to provide and signature to the CC.where is the current timestamp. sends to the CC. The CC recovers the aggregated data.
From the above description, we can know that there are many complex and time-consuming cryptography operations in Zuo’s algorithm, including the modular exponentiation operation and the bilinear pairing operation. For the GW and CC, there are sufficient computation resources and storage resources to carry out these complex operations. However, for an SM, as a kind of resource-constrained device, there are not enough computation resources and storage resources to deal with the time-consuming modular exponentiation operation, or it needs a lot of time to complete these operations. In Zuo’s algorithm, there are three parts involving modular exponentiation operations: registration, encryption and decryption. In the registration process, each SM only performs a modular exponentiation operation. Even if it takes a longer time, it has little effect on the efficiency of the protocol. We mainly solve the modular exponentiation operation in encryption and decryption because the SM constantly performs modular exponentiation. This situation is not suitable for the CC to process power consumption data in real time. Therefore, we design secure outsourcing algorithms to improve the efficiency of the SM’s execution of modular exponentiation.
4.2. Description of Outsourcing Algorithms
In Zuo’s algorithm, every time the SM sends power consumption data, the SM needs to perform the modular exponentiation operation five times. The SM needs to compute , , , and . When calculating and , the base of modular exponentiation is fixed and secret, and the exponent is variable and secret. When calculating , and , the base and exponent of modular exponentiation are variable and secret. For these two different cases of modular exponentiation operations, we design two different secure outsourcing algorithms.
We use u to represent the base of modular exponentiation and a to represent the exponent of modular exponentiation. p is the modulus. The SM sends u, a and p to the MS, and the MS returns to the SM. In the process of computing and , g is the generator of a group and is the common public key. g and are the fixed parameters. When designing an outsourcing algorithm for and , the SM needs to protect the privacy of u, a and p.
In Algorithm 1, u and p are secret and fixed, and a is secret and variable. Because u is fixed, the SM can compute two blinding pairs, and , in advance. In order to keep the information of a private from the MS, the SM can use and to blind the exponent a. Based on the discrete logarithm problem, the MS cannot obtain the base u from and . Based on the big integer factorization problem, the MS cannot obtain the base modular p from . In order to ensure the verifiability of the returned results, the SM needs to randomly choose a number r. The SM not only needs to send the blinding original computation to the MS, but also needs to send the blinding-related computation to the MS. When it is necessary to verify the correctness of the result returned from the MS, the SM only needs to verify whether the equation holds. When the verification is successful, the SM can use the locally stored p to recovery the real result .
Now, we utilize an example to illustrate our proposed Algorithm 1.
Example 1.
The SM wants to compute , where is a prime, and . The SM can compute as follows:
- 1.
- Pre-computation: The SM chooses and . Then, The SM computes and .
- 2.
- Problem transformation: The SM chooses and . Then, the SM computes and . The SM computes and .
- 3.
- Server computation: The MS computes and .
- 4.
- Result verification: The SM can verify the following equation:
- 5.
- Result recovery: The SM can recover the real result .
In process of computing , and , the exponent is the user’s private key, and the base is the message summary or the aggregated ciphertext , which cannot be disclosed to MS. Once leaked, it will have a serious impact on the security of the entire algorithm. Therefore, when designing an outsourcing algorithm for , and , the SM needs to protect the privacy of the base and the exponent, that is, the privacy of u and a.
Before introducing Algorithm 2, we firstly introduce a theorem. Let N be a positive integer, and let u be an integer which satisfies ; then we have .
Theorem 1.
For , where are distinct prime numbers, we have
whereis the Euler’s function and γ is a random integer.
| Algorithm 1 Secure Outsourcing of Modular Exponentiation with Public Base and Secret Exponent (Fixed Base) |
|
In Algorithm 2, and . u and a are secret and variable. In order to keep the information of u private from the MS, the SM firstly runs the Rand algorithm to generate four blinding pairs and compute two blinding pairs to blind the base u. The original base u can be transformed into . Because the MS does not know any knowledge about , the MS cannot obtain the base u from . By utilizing Theorem 1, the SM can protect the information of a from being disclosed to the MS.The original exponent a can be transformed into , where is a random integer. Similar to Algorithm 1, the SM chooses a random integer r and compares the two returned results to ensure the verifiability of the results. When the verification is successful, the SM can use the locally stored and p to recover the real result .
Now, we utilize an example to illustrate our proposed Algorithm 2.
Example 2.
The SM wants to compute , where is a prime, , and . The SM can compute as follows:
- 1.
- Pre-computation: The SM chooses , , , , , . Then, SM computes , , , , , .
- 2.
- Problem transformation: The SM chooses , and . Then, the SM computes and . The SM computes , , and .
- 3.
- Server computation: The MS computes , , and .
- 4.
- Result verification: The SM can verify the following equation:
- 5.
- Result recovery: The SM can recover the real result .
| Algorithm 2 Secure Outsourcing of Modular Exponentiation with Secret Base and Exponent (Variable Base) |
|
5. Security and Complexity Analysis
In this section, we firstly analyze the correctness and the security of the proposed algorithms. Then, we give a detailed description about the verifiability of the returned results. Finally, we analyze the computational complexity of the proposed algorithms.
5.1. Security Analysis
Theorem 2.
In the malicious model, the algorithm is an outsource-secure implementation of Algorithms 1 and 2, where the input may be honest, secret; or honest, protected; or adversarial, protected.
Proof.
The correctness of these two algorithms is obvious and straightforward. We mainly focus on security. is a PPT adversary that interacts with a PPT algorithm T in the malicious model. We need to prove that pair one and pair two are computationally indistinguishable. □
Pair One: If the input is anything other than honest and secret, the same way that the simulator behaves as in the real execution. Under an honest and secret input , will behave as follows: once the information is received in the ith round, neglects it and correspondingly makes two random queries of the form to . randomly tests one output from the program (i.e., . Once it detects an error, saves the states of itself and , and outputs . If no error is detected, outputs ; otherwise, randomly chooses an element R and outputs . In either case, also stores the appropriate states. In the real and ideal experiment, the input distributions to are computationally indistinguishable. The inputs in the ideal experiment are chosen uniformly at random. Each part of all two queries that T makes is re-randomized and computationally indistinguishable. If behaves honestly in the ith round, we have . If behaves dishonestly in the ith round, both T and detect malicious behavior with a high probability and output “error”. In the real experiment, the two outputs generated by are blinded by a random value. Therefore, we have . In summary, we can get no matter whether is honest or malicious.
Pair Two: The way that the simulator behaves is as follows: Once the information is received in the ith round, neglects it and correspondingly makes two random queries of the form to . Then, saves the states of itself and . These real and ideal experiments can be easily distinguished by E because the outputs in the ideal experiment are never corrupted. Because there is no channel between E and , E cannot transmit any messages to . In the ith round of the real experiment, T re-randomizes its inputs to . generates the random and independent queries to in the ideal experiment. We can know . In summary, we can get .
5.2. Verifiability Analysis
Theorem 3.
In the malicious model, the proposed Algorithm 1 is a 19/20-verifiable secure outsourcing algorithm and the proposed Algorithm 2 is a 59/60-verifiable secure outsourcing algorithm.
Proof.
At first, we prove that Algorithm 1 is a 19/20-verifiable secure outsourcing algorithm. If the MS wants to cheat the SM, the MS may make some guesses about the value and r. In order to verify the correctness of the results, the SM needs to check the equation:
In order to cheat the SM, the MS needs to randomly choose a integer C and constructs the following equation:
In order to make the above equation hold, the MS needs to guess the value of r and distinguish from and . Because the random number r is chosen from the set , the probability that the MS can accurately guess the value of r is 1/10. The probability that the MS can accurately distinguish from and is 1/2. Therefore, the probability that the MS can cheat the SM is 1/20. Algorithm 1 is a 19/20 (0.95)-verifiable secure outsourcing algorithm. □
Then, we prove that Algorithm 2 is a 59/60-verifiable secure outsourcing algorithm. Similar to Algorithm 1, in order to cheat the SM, the MS needs to randomly choose a integer C and construct the following equation:
On the one hand, the MS needs to guess the value of r. On the other hand, the MS needs to distinguish and from , , and and separately compute and . The probability that the MS can accurately guess the value of r is 1/10. The probability that the MS can accurately distinguish and from , , and is 1/6. Therefore, the probability that the MS can cheat the SM is 1/60. Algorithm 2 is a 59/60 (0.983)-verifiable secure outsourcing algorithm.
Then, we compare the security, verifiability and efficiency of Algorithm 2 with some previous algorithms. As shown in Table 2, there is the comparison of security, verifiability and efficiency for the user in these outsourcing algorithms. In order for all outsourced algorithms to have the same level of security, we set and . All random numbers and are larger than . From Table 2, we can find that Algorithm 2 is superior to [33,41] in both efficiency and security. Compared to [42], although Algorithm 2 does less , it needs to do one more and one . However, Algorithm 2 has higher verifiability. In addition, compared with the previous three algorithms, our algorithm has higher security that can protect the modulus of modular exponentiation.

Table 2.
Comparison of algorithms.
5.3. Complexity Analysis
Theorem 4.
In the malicious model, the proposed Algorithm 1 is a ((1.5log r + 3)* + 2*)/*-efficient secure outsourcing algorithm, and the proposed Algorithm 2 is a ((1.5log r + 15)* + 2*)/*-efficient secure outsourcing algorithm.
Proof.
We denote as a once modular multiplication operation and as a once modular inverse operation. For a l-bit exponent, the SM needs to be times to compute by the square-and-multiply method. The bit length of and p is l. □
In Algorithm 1, the process of problem transformation needs three times (we omit ) and twice . The process of result verification needs log r times . We omit other operations such as modular additions. Thus, the proposed Algorithm 1 is a ((1.5log r + 3)* + 2*)/*-efficient secure outsourcing algorithm.
In Algorithm 2, the process of problem transformation needs nine times and twice . The process of result verification and recovery needs log r times . Thus, the proposed Algorithm 2 is a ((1.5log r + 15)* + 2*)/*-efficient secure outsourcing algorithm.
6. Evaluation
6.1. Numeric Analysis
In this section, we will give an analysis of communication overhead and storage space overhead.
At first, we give an analysis of communication overhead. The bit length of is L. In Algorithm 1, the SM needs to send , , , and to the MS. The size of these parameters is bits. The MS needs to return and to the SM. The size of these parameters is bits. To sum up, the communication overhead of Algorithm 1 is bits. Similar to Algorithm 1, in Algorithm 2, the SM needs to send , , , and to the MS. The size of these parameters is bits. The MS needs to return and to the SM. The size of these parameters is bits. To sum up, the communication overhead of Algorithm 2 is bits.
Then, we give a analysis of storage space overhead. The storage space that the SM requires contains two parts: an online phase and offline phase. In the offline phase of Algorithm 1, the SM needs to store the two pre-computed pairs and the parameters , which needs bits storage space. In the online phase of Algorithm 1, the SM firstly needs l bit of storage space to store a. Then, the SM needs bits storage space during the problem transformation stage, which contains the parameters . We assume that s and p have the same bit length l and omit the bit length of r. The client needs bits storage space during the result verification and recovery, which contains the parameters . To sum up, the storage space overhead of Algorithm 1 is bits.
We can analyze Algorithm 2 in a similar way. The SM needs to bits storage space to store six blinding pairs and p in the offline phase of Algorithm 2. In the online phase of Algorithm 2, the SM firstly needs bits storage space to store a and u. Then, the SM needs bits storage space during the problem transformation stage, which contains the parameters . We omit the bit length of r, and . The SM needs bits of storage space during the result verification and recovery, which contains the parameters . To sum up, the storage space overhead of Algorithm 2 is bits.
Table 3 shows the communication overhead and storage space overhead.

Table 3.
Communication overhead and storage space overhead.
6.2. Performance Evaluation
In this section, in order to show that our proposed algorithms are efficient, we carried out some experiment evaluations. We implemented our algorithms by using the C++ programming language with the GMP library, which is specially designed to handle some large integer operations. We used a software named Sublime Text3 to write the programs. In the program, all variables were first defined as the types defined in GMP. Then, we wrote code step-by-step according to the algorithms. We need edto define many variables to receive the intermediate data. We usee the system’s own time function to compute the time cost of the two algorithms. SM was simulated by a computer with a Linux Ubuntu 20.04.2 LTS operating system and Intel Core i5 processors (2.4 GMz and 2 G memory). MS was simulated by a computer with a Linux Ubuntu 20.04.2 LTS operating system and Intel Core i5 processors (2.6 GMz and 8 G memory). In our experiment, the bit length of p ranged from 256 bits to 2048 bits. As shown in Table 4, there are some simulation parameters when the bit length of p is 256 bits and 512 bits.

Table 4.
Some simulation parameters.
Figure 2a compares the time cost of not outsourcing with our proposed Algorithm 1 on the SM side. Figure 3a compares the time cost of not outsourcing with our proposed Algorithm 2 on the SM side. As shown in Figure 2a and Figure 3a, the time cost of Algorithms 1 and 2 are much smaller than that of direct computation. Note that the time cost of Algorithms 1 and 2 on the SM side dose not include the pre-computation process. The pre-computation process can be done off-line. In Algorithms 1 and 2, the time cost on the SM side concentrates on these three processes: transformation, verification and recovery.
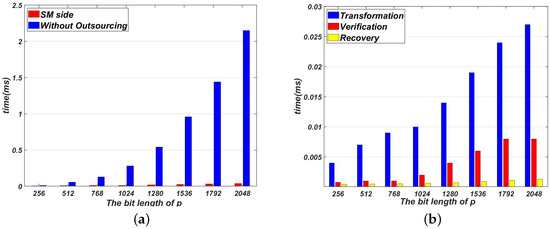
Figure 2.
Evaluation results for Algorithm 1. (a) The time cost of Algorithm 1 without outsourcing on the SM side; (b) The time cost comparison among phases in Algorithm 1.
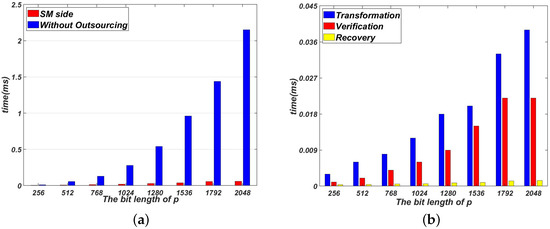
Figure 3.
Evaluation results for Algorithm 2. (a) The time cost of Algorithm 2 without outsourcing on the SM side; (b) The time cost comparison among phases in Algorithm 2.
Figure 2b and Figure 3b show the time cost of transformation, verification and recovery in Algorithms 1 and 2. As shown in Figure 2b and Figure 3b, the process of transformation needs to take more time than two other processes. This is because the process of transformation contains two modular inverse operations. Generally speaking, it takes more time to complete a modular inversion operation than a modular multiplication operation. Because only one modular operation is performed in the process of recovery, the time cost of recovery is the smallest.
Figure 4 shows that the ratio between the time cost of our proposed algorithms and direct computation. From Figure 4, we can see that Algorithms 1 and 2 can significantly improve the efficiency of the SM. In addition, as the bit length of p increases, the improvement becomes more and more significant.
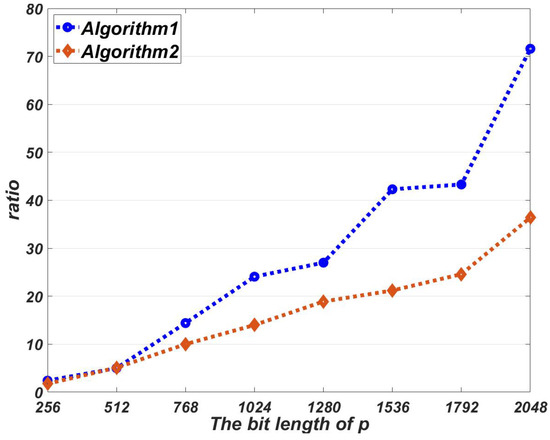
Figure 4.
The ratio between the time cost of our proposed algorithms and direct computation.
7. Conclusions
In this paper, for the complex modular exponentiation operations involved in Zuo’s privacy-preserving data aggregation protocol, we designed two secure and efficient outsourcing algorithms for resource-constrained SMs. The proposed algorithms not only can protect SMs’ confidential data from being leaked to an untrusted server, but can also ensure the correctness of the returned results from the server. In addition, we provided an analysis of the security, verifiability and efficiency and proved that the SM can detect error with a probability of 19/20 in Algorithm 1 and with a probability of 59/60 in Algorithm 2. Finally, through experimental evaluation, we proved that our proposed algorithms are well suitable for data encryption and aggregation in smart grids. In the future, on the one hand, we will investigate more outsourcing algorithms, including bilinear pairing and scalar multiplication on elliptic curves, which are applicable to other data encryption and aggregation protocols. On the other hand, we will explore how to combine outsourcing computation with distributed computation to reduce the computational overhead on the server side.
Author Contributions
Conceptualization, F.Z. and T.Y.; methodology, F.Z. and T.Y.; software, F.Z. and B.Z.; validation, F.Z., T.Y., B.Z. and H.C.; formal analysis, F.Z.; investigation, F.Z.; resources, F.Z.; data curation, F.Z.; writing—original draft preparation, F.Z.; writing—review and editing, F.Z.; visualization, F.Z.; supervision, F.Z.; project administration, F.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Key Research and Development Program of China (2017YFE0132100) and the National Natural Science Foundation of China (61971305).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart Grid—The New and Improved Power Grid: A Survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart Grid Technologies: Communication Technologies and Standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef] [Green Version]
- Yu, L.; Jiang, T.; Zou, Y. Distributed Online Energy Management for Data Centers and Electric Vehicles in Smart Grid. IEEE Internet Things J. 2016, 3, 1373–1384. [Google Scholar] [CrossRef]
- Iyer, S. Cyber security for smart grid, cryptography, and privacy. Int. J. Digit. Multimed. Broadcast. 2011, 2011, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Dwivedi, A.D.; Singh, R.; Ghosh, U.; Mukkamala, R.R.; Tolba, A.; Said, O. Privacy preserving authentication system based on non-interactive zero knowledge proof suitable for Internet of Things. J. Ambient. Intell. Humaniz. Comput. 2021, 1–11. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Hajjej, F.; Ali, A.; Pasha, M.F.; Almomani, O. A Novel Hybrid Trustworthy Decentralized Authentication and Data Preservation Model for Digital Healthcare IoT Based CPS. Sensors 2022, 22, 1448. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Privacy-Aware Authenticated Key Agreement Scheme for Secure Smart Grid Communication. IEEE Trans. Smart Grid 2019, 10, 3953–3962. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. Secure Three-Factor User Authentication Scheme for Renewable-Energy-Based Smart Grid Environment. IEEE Trans. Ind. Inform. 2017, 13, 3144–3153. [Google Scholar] [CrossRef]
- Ding, Y.; Wang, B.; Wang, Y.; Zhang, K.; Wang, H. Secure Metering Data Aggregation With Batch Verification in Industrial Smart Grid. IEEE Trans. Ind. Inform. 2020, 16, 6607–6616. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and Privacy-Preserving Data Aggregation Scheme for Smart Grid Against Internal Adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2419. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A Survey on Cyber Security for Smart Grid Communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef] [Green Version]
- Zuo, X.; Li, L.; Peng, H.; Luo, S.; Yang, Y. Privacy-Preserving Multidimensional Data Aggregation Scheme Without Trusted Authority in Smart Grid. IEEE Syst. J. 2020, 15, 395–406. [Google Scholar] [CrossRef]
- Peng, C.; Luo, M.; Wang, H.; Khan, M.K.; He, D. An Efficient Privacy-Preserving Aggregation Scheme for Multidimensional Data in IoT. IEEE Internet Things J. 2021, 9, 589–600. [Google Scholar] [CrossRef]
- Boudia, O.R.M.; Senouci, S.M.; Feham, M. Elliptic curve-based secure multidimensional aggregation for smart grid communications. IEEE Sens. J. 2017, 17, 7750–7757. [Google Scholar] [CrossRef]
- Atallah, M.J.; Frikken, K.B. Securely Outsourcing Linear Algebra Computations. In Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, ASIACCS ’10, Beijing, China, 13–16 April 2010; pp. 48–59. [Google Scholar]
- Li, H.; Yu, J.; Yang, M.; Kong, F. Secure Outsourcing of Large-Scale Convex Optimization Problem in Internet of Things. IEEE Internet Things J. 2022, 9, 8737–8748. [Google Scholar] [CrossRef]
- Ren, K.; Wang, C.; Wang, Q. Security Challenges for the Public Cloud. IEEE Internet Comput. 2012, 16, 69–73. [Google Scholar] [CrossRef]
- Munoz, A.; Mafia, A. Software and hardware certification techniques in a combined certification model. In Proceedings of the 2014 11th International Conference on Security and Cryptography (SECRYPT), Vienna, Austria, 28–30 August 2014; pp. 1–6. [Google Scholar]
- Gao, X.; Yu, J.; Chang, Y.; Wang, H.; Fan, J. Checking Only When It Is Necessary: Enabling Integrity Auditing Based on the Keyword with Sensitive Information Privacy for Encrypted Cloud Data. IEEE Trans. Dependable Secur. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Ge, X.; Yu, J.; Zhang, H.; Bai, J.; Fan, J.; Xiong, N.N. SPPS: A Search Pattern Privacy System for Approximate Shortest Distance Query of Encrypted Graphs in IIoT. IEEE Trans. Syst. Man, Cybern. Syst. 2022, 52, 136–150. [Google Scholar] [CrossRef]
- Li, S.; Xue, K.; Yang, Q.; Hong, P. PPMA: Privacy-preserving multisubset data aggregation in smart grid. IEEE Trans. Ind. Inform. 2017, 14, 462–471. [Google Scholar] [CrossRef]
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An efficient and privacy-preserving aggregation scheme for secure smart grid communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]
- Saxena, N.; Choi, B.; Lu, R. Authentication and Authorization Scheme for Various User Roles and Devices in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2016, 11, 907–921. [Google Scholar] [CrossRef] [Green Version]
- Sun, R.; Shi, Z.; Lu, R.; Lu, M.; Shen, X.S. APED: An efficient aggregation protocol with error detection for smart grid communications. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 432–437. [Google Scholar]
- Shi, Z.; Sun, R.; Lu, R.; Chen, L.; Chen, J.; Shen, X.S. Diverse Grouping-Based Aggregation Protocol With Error Detection for Smart Grid Communications. IEEE Trans. Smart Grid 2015, 6, 2856–2868. [Google Scholar] [CrossRef]
- Bao, H.; Lu, R. A New Differentially Private Data Aggregation With Fault Tolerance for Smart Grid Communications. IEEE Internet Things J. 2015, 2, 248–258. [Google Scholar] [CrossRef]
- Guo, C.; Jiang, X.; Choo, K.; Tang, X.; Zhang, J. Lightweight privacy preserving data aggregation with batch verification for smart grid. Future Gener. Comput. Syst. 2020, 112, 512–523. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M.S. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Gough, M.; Santos, S.; Alskaif, T.; Javadi, M.; Castro, R.; Catalao, J.P.S. Preserving Privacy of Smart Meter Data in a Smart Grid Environment. IEEE Trans. Ind. Inform. 2022, 18, 707–718. [Google Scholar] [CrossRef]
- Hohenberger, S.; Lysyanskaya, A. How to Securely Outsource Cryptographic Computations. In Proceedings of the International Conference on Theory of Cryptography, Cambridge, MA, USA, 10–12 February 2005; pp. 264–282. [Google Scholar]
- Chen, X.; Li, J.; Ma, J.; Tang, Q.; Lou, W. New Algorithms for Secure Outsourcing of Modular Exponentiations. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 2386–2396. [Google Scholar] [CrossRef] [Green Version]
- Ye, J.; Chen, X.; Ma, J. An Improved Algorithm for Secure Outsourcing of Modular Exponentiations. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangiu, Korea, 24–27 March 2015; pp. 73–76. [Google Scholar]
- Wang, Y.; Wu, Q.; Wong, D.S.; Qin, B.; Chow, S.S.M.; Liu, Z.; Tan, X. Securely Outsourcing Exponentiations with Single Untrusted Program for Cloud Storage. In Proceedings of the European Symposium on Research in Computer Security, Wroclaw, Poland, 7–11 September 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 326–343. [Google Scholar]
- Ren, Y.; Dong, M.; Qian, Z.; Zhang, X.; Feng, G. Efficient Algorithm for Secure Outsourcing of Modular Exponentiation with Single Server. IEEE Trans. Cloud Comput. 2021, 9, 145–154. [Google Scholar] [CrossRef]
- Zhou, K.; Afifi, M.H.; Ren, J. ExpSOS: Secure and Verifiable Outsourcing of Exponentiation Operations for Mobile Cloud Computing. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2518–2531. [Google Scholar] [CrossRef]
- Li, H.; Yu, J.; Zhang, H.; Yang, M.; Wang, H. Privacy-Preserving and Distributed Algorithms for Modular Exponentiation in IoT With Edge Computing Assistance. IEEE Internet Things J. 2020, 7, 8769–8779. [Google Scholar] [CrossRef]
- Chen, X.; Huang, X.; Li, J.; Ma, J.; Lou, W.; Wong, D.S. New Algorithms for Secure Outsourcing of Large-Scale Systems of Linear Equations. IEEE Trans. Inf. Forensics Secur. 2015, 10, 69–78. [Google Scholar] [CrossRef]
- Nguyen, P.Q.; Shparlinski, I.E.; Stern, J. Distribution of Modular Sums and the Security of the Server Aided Exponentiation. In Cryptography and Computational Number Theory; Birkhäuser: Basel, Switzerland, 2001; pp. 331–342. [Google Scholar]
- Gennaro, R.; Gentry, C.; Parno, B. Non-interactive Verifiable Computing: Outsourcing Computation to Untrusted Workers. In Advances in Cryptology—CRYPTO 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 465–482. [Google Scholar]
- Muñoz, A.; Maña, A.; Serrano, D. AVISPA in the validation of ambient intelligence scenarios. In Proceedings of the 2009 International Conference on Availability, Reliability and Security, Jukuoka, Japan, 16–19 March 2009; pp. 420–426. [Google Scholar]
- Ye, J.; Wang, J. Secure outsourcing of modular exponentiation with single untrusted server. In Proceedings of the 2015 18th International Conference on Network-Based Information Systems, Taipei, Taiwan, 2–4 September 2015; pp. 643–645. [Google Scholar]
- Kiraz, M.S.; Uzunkol, O. Efficient and verifiable algorithms for secure outsourcing of cryptographic computations. Int. J. Inf. Secur. 2016, 15, 519–537. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).