Abstract
The need for continuous monitoring of physiological information of critical organs of the human body, combined with the ever-growing field of electronics and sensor technologies and the vast opportunities brought by 5G connectivity, have made implantable medical devices (IMDs) the most necessitated devices in the health arena. IMDs are very sensitive since they are implanted in the human body, and the patients depend on them for the proper functioning of their vital organs. Simultaneously, they are intrinsically vulnerable to several attacks mainly due to their resource limitations and the wireless channel utilized for data transmission. Hence, failing to secure them would put the patient’s life in jeopardy and damage the reputations of the manufacturers. To date, various researchers have proposed different countermeasures to keep the confidentiality, integrity, and availability of IMD systems with privacy and safety specifications. Despite the appreciated efforts made by the research community, there are issues with these proposed solutions. Principally, there are at least three critical problems. (1) Inadequate essential capabilities (such as emergency authentication, key update mechanism, anonymity, and adaptability); (2) heavy computational and communication overheads; and (3) lack of rigorous formal security verification. Motivated by this, we have thoroughly analyzed the current IMD authentication protocols by utilizing two formal approaches: the Burrows–Abadi–Needham logic (BAN logic) and the Automated Validation of Internet Security Protocols and Applications (AVISPA). In addition, we compared these schemes against their security strengths, computational overheads, latency, and other vital features, such as emergency authentications, key update mechanisms, and adaptabilities.
1. Introduction
The need for continuous monitoring of physiological information of critical organs of the human body, combined with the ever-growing field of electronics and sensor technologies, and the colossal opportunities brought by 5G connectivity, have made implantable medical devices (IMDs) the most necessitated devices in the health arena. This is clearly shown by the global IMD market share, which was worth USD 96.6 billion in 2018 [1] and grew to around USD 103.3 Billion in 2019, and will likely rise to USD 148.8 Billion in 2024 [2].
IMDs possess several applications to help manage numerous health conditions. These include controlling the heart rhythm using cardiac pacemakers, heart support using ventricular assist devices, and chronic spinal pain reliefs using spinal cord stimulators [3]. Furthermore, they extend their applications by enabling wireless communication technologies that help manage the interaction between IMDs and external devices in wireless body area networks (WBANs) [4,5]. IMDs functioning in WBANs have made a significant contribution in resolving several challenges in both medical and non-medical fields, yet they have their hurdles.
Despite their critical roles in improving human health conditions, IMDs have various challenges, among which, limitations of resource (power, storage, computation, etc.) and security concerns are the most serious. The former challenge is directly related to their small size and inflexibility since they are implanted in the human body. Concerning the latter, IMDs are susceptible to many security and privacy threats that put a patient’s life in danger [6]. Some of the most common security problems that IMDs face are impersonation, requesting confidential information, causing a shock to the patient, reprogramming of IMD, etc. Moreover, security assaults (e.g., side-channel attacks) targeting a wide range of internet of things (IoT) processors, such as the Cortex-A platform, also threaten the wellbeing of IMDs [7].
To date, many countermeasures have been taken to keep the confidentiality, integrity, and availability of IoT systems, along with different privacy and safety mechanisms [8,9,10,11,12]. In particular, to IMDs, different researchers have proposed several solutions that can be categorized into three main groups: cryptographic, access control, and misbehavior detection. The first group of solutions utilizes cryptographic rudiments (including public-key encryption, symmetric-key encryption, cryptographic hash functions, etc.) [13,14]. Access control mechanisms [15,16,17], on the other hand, protect IMDs from unauthorized access by employing different techniques, such as certificates and lists, designation-based, juxtaposition-based, and biometric-based [6]. The last type of method involves malicious behavior detection to shield IMDs from a range of attacks that may not be easily addressed by the former two solutions [18,19].
IMDs are very sensitive as they are implanted in the human body, and the patients depend on them for the proper functioning of their vital organs. Moreover, due to their resource limitations and the open channel utilized for data transmission, they are intrinsically vulnerable to several attacks, such as distributed denial of service with different attacker intentions [20]. Hence, failing to secure them would put the life of the patient in jeopardy, and damage the reputations of the manufacturer. Consequently, it is imperative to carefully examine the security of the IMD authentication protocols for any vulnerabilities. To do so, we followed two methods. First, we conducted an extensive literature review to understand the operations, architectural perspectives, critical security, and privacy requirements and proposed solutions. We also leveraged empirical data that approximated delays introduced by cryptographic operations for comparative analysis of the authentication protocols. Next, we used two well-known security verification approaches, BAN logic [21] and AVISPA [22], to formally analyze the authentication protocols. Unfortunately, many security protocols designed for IMDs are not formally verified, or they use only one verification method [23,24,25,26,27,28,29,30].
The main contributions of this research work can be summarized as follows:
- We examined various security and privacy requirements along with numerous threats that surround IMDs.
- We performed formal security validation of the contemporary authentication schemes based on BAN logic and AVISPA against several security goals.
- We compared these schemes concerning security strength, computational overhead, latency, and additional features, such as emergency authentication, adaptiveness, and key update mechanisms.
The rest of the paper continues as follows. Section 2 describes the components of a typical IMD system architecture. Section 3 outlines various security and privacy requirements, issues, and proposed solutions. Section 4 presents the formal security analysis of different IMD authentication protocols using BAN logic and AVISPA. Section 5 puts forward the discussion of the results found in Section 4. Section 6 describes the comparative analysis of the authentication protocols concerning functionality, computational overhead, and communication latency. Finally, Section 7 concludes the paper.
2. Typical IMD System Architecture
IMDs play a critical role in sensing vital physiological information, which is then sent out to an external device via the wireless medium for different actions, such as remote monitoring and drug delivery. Typically, such systems are assembled from various components, as shown in Figure 1, among which the following are the main ones.
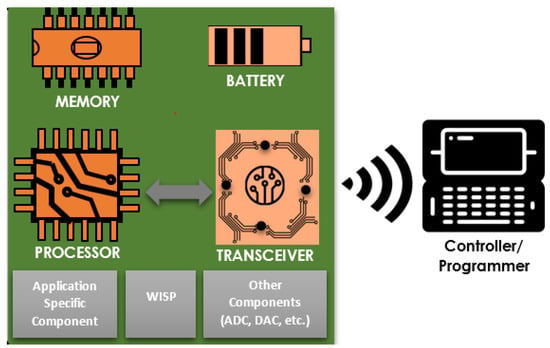
Figure 1.
A typical IMD system architecture.
- Sensor devices. These are small, in-body implanted, battery-powered, and wireless communication enabled sensors to sense, collect, and send patient information to a controller. In general, there are three categories (based on the data measured/collected) of such sensors: those that measure vital physiological information (such as glucose level, EEG, ECG, etc.), those that gather main environmental parameters, such as humidity, temperature, and pressure, and those that measure signals related to the human body movements [31].
- Battery. Implanted sensors need the power to sense information on the body and produce an output. The source of energy for active implants comes from batteries. These batteries can be chargeable or non-chargeable, depending on the sensor type [32], and external or through independent power sources [33]. While the former approach uses optical charging, ultrasonic transducer, and inductive coupling, the latter uses the body environment energy to generate electrical energy for IMDs. Either way, efficient power management is a must since it is difficult (or not desirable) to change batteries now and then. Hence, batteries fixed with these implants should serve for a prolonged period.
- Memory. Memory is vital for the proper functioning of IMDs. It enables implants to store sensed data, configurations, and other important information (such as security keys). The device memory is generally non-volatile (read-only memory (ROM)), retaining its contents regardless of the power supply. In addition, the electrically erasable programmable ROM (EEPROM) and flash memories can be good candidates [32].
- Processing unit. The processing unit is the brain of the entire IMD system, which processes instructions and control signals. The processing unit actively directs the communication between IMDs and external devices, efficient power and transceiver management, and is responsible for other essential tasks, such as sensing and processing data [32].
- Transceiver. To communicate different sensed data to the external devices (such as a programmer) and receive other information from the external devices, IMDs need to establish a wireless medium. An electronic device, known as a transceiver (transmitter and receiver), assists this exchange of information. A specifically designed transceiver called the Medical Implant Communication System (MICS) is available for medical implants with low-power, short-range, and high data rate features [34].
- Application-Specific Components. These components are optional, meaning they may not appear in all implanted devices. One good illustration is the Smart Implant Security Core (SISC) [35]. Communication between IMD and a programmer via wireless medium passes through this device. It runs an energy-efficient security protocol by using energy harvesting when it performs authentication with the programmer. Apart from that, SISC helps defend against denial-of-service attacks, particularly resource exhaustion attacks.
- Wireless Identification and Sensing Platform (WISP). One of the significant constraints of implanted devices is related to power. These devices reside in the human body, making them challenging to recharge or frequently change. Hence, a device called WISP is proposed [32]. Using WISP, therefore, it is possible to conserve the battery of an IMD, especially during an authentication process, as it harvests energy from the reader via radiofrequency.
- Programmer/Controller. Sensing or measuring vital physiological states is only half of the primary goal of using implants. The sensors should also convey the sensed information to an external device (a specially designed controller or a smartphone) near the IMDs. Apart from collecting sensed information from the implants, programmers/controllers assist in configuration setup and regulation of therapy, among others.
3. Security and Privacy Requirements, Threats, and Proposed Solutions
IMDs encounter several challenges, from their conception through their operation. These devices are implanted and severely limited in terms of power, storage, and computing capabilities, making it challenging to build effective communication technologies and security mechanisms. In this regard, IMDs must satisfy various security requirements to withstand the ever-increasing attacks that target them.
The privacy of patients is of paramount importance. Two critical issues in this regard are user anonymity and non-traceability [6,36]. The former refers to a strong requirement that it should be impossible (or difficult enough) for the attacker to intercept the patient’s identity from the messages exchanged. Often, this is the first step towards an impersonation attack in which an adversary identifies the user’s real identity to fool the other party. Non-traceability, on the other hand, protects the IMD by making it difficult for an attack to know where the patient is or from where he is communicating. As a result, the locations of patients remain confidential, and any acts they conduct cannot be traced back to them by an unauthorized entity.
3.1. Security and Privacy Requirements
Here, we describe nine essential security requirements relevant to the IMDs:
- Confidentiality: the physiological information collected by IMDs is often sent out to a reader via a wireless medium, which both authorized and malicious users can observe. Accordingly, it is essential to encrypt this information to protect the data transmitted from exploitation by the adversaries sitting between the IMD and the reader.
- Integrity: protecting the integrity of the information transmitted via the wireless link in IMD reader communication defends against unauthorized modification. In addition, when illegitimate users tamper with the data, it should be known by the authorized users that the data is modified.
- Availability: this is one of the three security triads (confidentiality, integrity, and availability) that has the objective of making the IMD-enabled system accessible to authorized users despite the presence of adversaries.
- Mutual authentication: unless authorized access is in place, an adversary can impersonate the IMD or the reader to fool the other. Hence, communicating parties need to make sure whom they are talking to before disclosing important information.
- Authorization: once the confidentiality, integrity, and availability of IMDs are guaranteed, and the users (a human user or a device such as a reader) are authenticated, proper authorization to identify the privileges of these users’ proceeds. For instance, a doctor who may issue commands to the IMD should be distinct from a nurse who may only read information to monitor the patient.
- Non-repudiation: there are cases in which one party’s actions (knowingly or not) bring unwanted consequences. For instance, in an IMD-enabled health care system, there can be many participants in the process of diagnosing, monitoring, and treating patients. These professionals should not be able to repudiate the actions they took during the process so that, if anything terrible happened next, it is possible to know who did what.
- Session key agreement: communicating entities need to agree on a session key and use that key to encrypt the exchanged information. Session keys are symmetric keys that are primarily derived from another key (called a master key) to restrict ciphertexts and minimize the exposure of an attack. Furthermore, using session keys improves communication performance since these keys do not need to be stored and searched. Moreover, symmetric key encryption is faster.
- Perfect forward secrecy: satisfying this security requirement means the past sessions will not be compromised even if a master key is compromised. In the context of IMDs, if the long-term key is stolen, and if this is known, the key can be updated, and only minimal information would be disclosed while all past communications can be kept safe from future compromises.
- Emergency authentication: if we deal with patients with implanted devices, there can always be emergencies requiring human intervention. Emergency authentication is one of the paradox requirements since unauthorized users need to access the implants to override the authorization and authentication properties, which calls for a clear definition of an emergency.
Concerning privacy, there are at least five privacy requirements [12,37] that should be satisfied:
- Device-existence privacy: this privacy requirement challenges the protocol designers to conceal the device’s information of an IMD-enabled system and prohibit an adversary from learning its existence.
- Device-type privacy: in the cases where the presence of a device cannot be wholly concealed or its privacy cannot be maintained, the type of the device should stay anonymous. By doing so, it is possible to protect the patient from device-type specific attacks.
- Specific-device ID privacy: the unique ID (or serial number) of an IMD should not be disclosed to unauthorized users. Doing so protects the patients by prohibiting attackers from tracking down their locations.
- Measurement and log privacy: the information measured, collected, and analyzed in either IMD or the reader should be kept private. Keeping the privacy of logs enables the investigation and trace actions taken during the communication.
- Bearer privacy: these are often related to information such as patients’ names, record history, tests, IMD characteristics, etc., which should be kept private.
3.2. Security Issues and Proposed Solutions
Threats are only dangerous because of adversaries, malicious entities that usually have access to the communication media and are placed between the authorized entities to violate confidentiality (and privacy), integrity, and availability. These adversaries can be passive or active, internal or external, computationally restrained or unrestrained, and single individual vs. group [6].
In regard to IMD security, we can broadly classify adversaries based on their capabilities as passive eavesdroppers and active attackers [37,38,39]. The first class of adversaries can only eavesdrop on the radio communication between the legitimate entities to discover unencrypted messages. Sometimes, even if the messages are encrypted, passive adversaries may observe patterns to violate the privacy of communicating parties, such as learning the existence of IMD.
On the other hand, active attackers can replay, modify, or delete messages in addition to possessing all of the capabilities of passive adversaries. These are the most dangerous types of adversaries that can bring life-threatening attacks to IMD-enabled systems. Adversaries in this category can execute replay attacks by forwarding exchanged messages later, changing critical settings of the implants by producing new commands, and exhausting the battery life of IMDs.
Different researchers have studied various security and privacy issues that challenge the normal operations of IMDs along with various proposed solutions that can be generally categorized as auditing-alone solutions, cryptographic solutions, and access control schemes [6]. The first category refers to solutions that solely depend on the access logs for the IMD. However, such techniques may not be suitable, as they cannot withstand active attacks if not used with other techniques such as access control mechanisms. The second measure utilizes cryptographic rudiments such as asymmetric-key cryptography, symmetric-key cryptography, and cryptographic hash functions. Three problems have been identified concerning the cryptographic solutions for IMDs [40]—the difficulty of implementation as most of the IMDs are already implanted in the human body, challenging to authenticate doctors during emergencies in which the patient is unconscious, and difficulty in maintaining the hardware and software of the implanted devices. The third solution refers to schemes that make use of access control help to protect IMDs from unauthorized access. The noticeable weakness in this solution is the difficulty of access during an emergency [6].
4. Formal Security Verification
Checking the safety of security protocols via a formal approach boosts users’ confidence, giving more convincing proof than its informal counterpart. When it comes to security protocols, such techniques may be divided into three categories: modal logic, model checkers, and theorem provers. This section will use one from the variants of modal logic (BAN logic) and another from model checking (AVISPA) to perform formal security verification for the authentication schemes proposed to safeguard IMDs. It is worth mentioning that the last two IMD authentication protocols (shown in Section 4.3.6 and Section 4.3.7) have also been analyzed, in [41,42], by the same authors.
4.1. BAN Logic Based Formal Security Verification
BAN logic uses logic of beliefs to analyze authentication protocols by following its own rules. First, the messages exchanged between the participants of the protocol are idealized. Then, reasonable assumptions will be formulated, and the objectives that the protocol intends to meet are defined. Finally, a derivation step follows where the BAN logic rules are used together with the assumptions and the intermediate results to reach the goals. Figure 2 shows a typical procedure of carrying out formal analysis using BAN logic. The BAN logic symbols and rules are shown in Table 1 and Table 2, respectively.
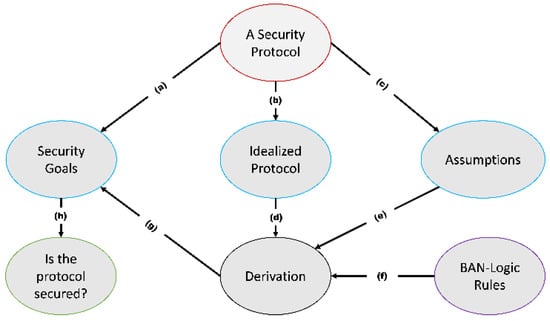
Figure 2.
A typical BAN logic formal analysis procedure. (a) Security goals are extracted from the protocol’s security requirements. (b) The security protocol is put in idealized form. (c) Realistic assumptions about the protocol is made. (d–f) Derivation uses these inputs to derive the stated goals. (g) The security goals are checked if the derivation satisfies them. (h) Based on the results of (g), the protocol is validated as safe or not.

Table 1.
BAN logic notations.

Table 2.
BAN logic rules.
4.2. AVISPA Based Formal Security Analysis
The previous section shows that BAN logic has been extensively used to verify authentication protocols by transforming them into a particular format and validating them through different logical rules. Unfortunately, BAN logic has limitations in accurately specifying a protocol in the idealization phase [21,43]. For that reason, most authentication protocols use automated formal security verification tools alongside BAN logic.
AVISPA provides a language called the high-level protocol specification language (HLPSL) [44] for describing security protocols and specifying their intended security properties, as well as a set of tools to validate them formally. An hlpsl2if translates the HLPSL specification into the Intermediate Format (IF). IF is a lower-level language that is read directly by the back-ends of the AVISPA Tool. The IF specification of a protocol is then input to the back-ends of the AVISPA Tool to analyze the stated security goals. Figure 3 shows this process.
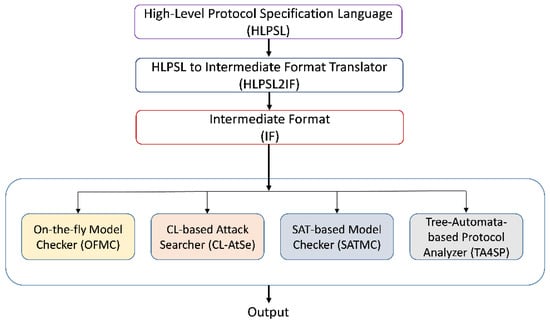
Figure 3.
AVISPA system structure.
The HLPSL specification is consists of basic roles, transitions, and composed roles used in three modules: role, session, and environment. Basic role refers to the specification of each of the modeled protocol participants and the initially known information as a parameter. These roles are then called to specify how the resulting participants interact by connecting various basic roles into a composed role. The transition part of an HLPSL specification encompasses a set of transitions between different roles. Each transition symbolizes the acceptance of a message and the sending of a response message.
4.3. Formal Security Analysis of IMD Authentication Protocols
4.3.1. Khan et al.’s Protocol
The protocol proposed by Khan et al. [23] is a privacy-preserving key agreement protocol for WBANs. The protocol has four main participants: the system administrator (SA), the hub node (HN), the intermediary nodes (IN), and the normal nodes (N). HN is often considered a trusted high-end server that does not have computing resource constraints. The Ns are implanted sensors with computational limitations. The intermediary nodes have better processing, battery, and storage than Ns, and they are placed between HN and Ns to relay traffic. Furthermore, the protocol is executed in three main phases: initialization, registration, and authentication. Figure 4 shows the final phase of the protocol. Figure 5 presents the OFMC and CL-AtSe back-end results of the protocol.
- BAN logic based Formal Security Analysis
● Idealization (I1) (I2) ● Assumption (A1) (A2) (A3) (A4) (A5) (A6) (A7) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) 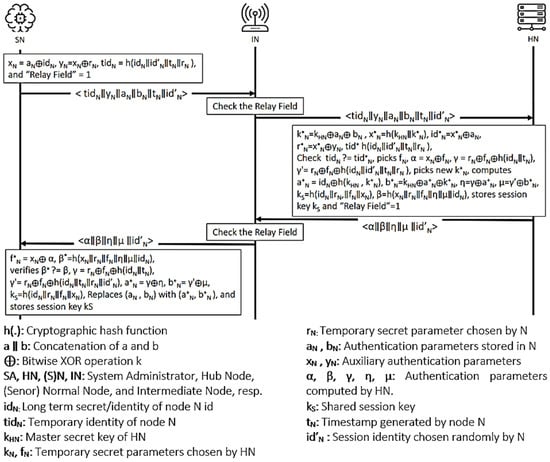 Figure 4. Khan et al.’s protocol.
Figure 4. Khan et al.’s protocol.● Derivations (D1) (D2) (D3) (D4) (D5) . (D6) (D7) (D8) (D9) (D10) (D11) (D12) (D13) - AVISPA based Formal Security Analysis Result
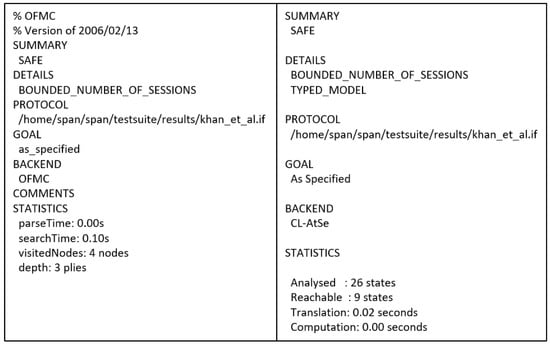 Figure 5. AVISPA result of Khan et al.’s protocol.
Figure 5. AVISPA result of Khan et al.’s protocol.
4.3.2. Wu et al.’s Protocol
This protocol [24] is a proxy-based access control protocol that uses attribute-based encryption, particularly the ciphertext policy attribute-based encryption (CP-ABE). The protocol is executed by three participants—IMD, operator, and proxy. The IMDs have unique identifications IDi and a master key KiM, which is only used for the initial pairing process with the proxy. All operators with the public parameters PK used in CP-ABE, unique identifications IDo, a public and private key pair (PUOP and PROP, respectively), and a certificate Cert must first be registered at a Central Health Authority (CHA). The CHA will then generate the secret key SK. The operator uses a programmer to communicate with the IMD and proxy after it obtains the required information by manual inputting or reading in from a smart card. With the identification of IDp and connection with an IMD programmer through an audio cable, the proxy device performs the access control for the IMD. Figure 6 shows the flow of messages in the protocol. Figure 7 illustrates the OFMC and CL-AtSe back-end results of the protocol.
- BAN logic-based formal security analysis.
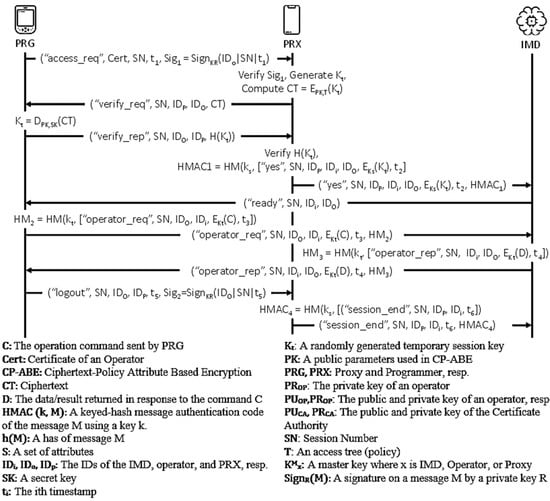 Figure 6. Wu et al.’s protocol.
Figure 6. Wu et al.’s protocol.● Idealization (I1) (I2) (I3) , (I4) , (I5) , ● Assumption (A1) (A2) (A3) (A4) (A5) (A6) (A7) (A8) (A9) (A10) (A11) (A12) (A13) (A14) (A15) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) (G8) (G9) (G10) ● Derivations (D1) (D2) (D3) (D4) (D5) (D6) (D7) (D8) (D9) (D10) (I3) (D11) (D12) (D13) (D14) (D15) (D16) (D17) (D18) (D19) (D20) (D21) (D22) (D23) (D24) (D25) (D26) (D27) (D28) (D29) By (D28),(I15), JR - AVISPA-based formal security analysis result.
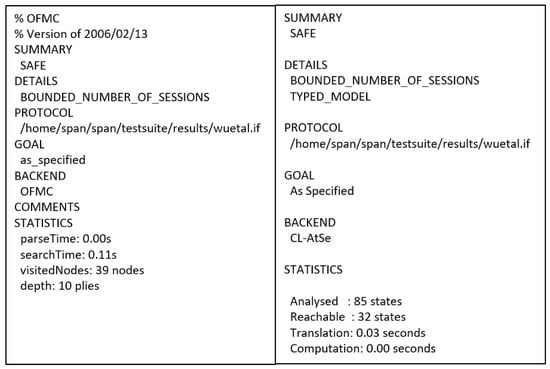 Figure 7. AVISPA result of Wu et al.’s protocol.
Figure 7. AVISPA result of Wu et al.’s protocol.
4.3.3. Chi et al.’s Protocol
This protocol [25] uses a compressing-based encryption mechanism and public key infrastructure, and other cryptographic protocols, such as RSA, AES, and HMAC. The protocol comprises three participants—IMD, smartphone, and programmer. The IMD communicates with the patient’s smartphone via Bluetooth, and it interacts with the doctor’s programmer through the wireless medium. The smartphone refers to both the patient and doctor smartphones, in which the patient’s smartphone links with the IMD utilizing Bluetooth and connects with a programmer wirelessly. The protocol involves four stages—initialization, pairing, authentication, and authorization, as shown in Figure 8 and Figure 9 presents the OFMC and CL-AtSe back-end results of the protocol.
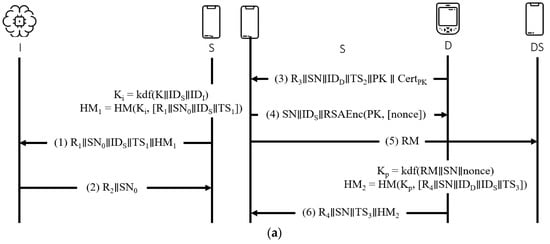
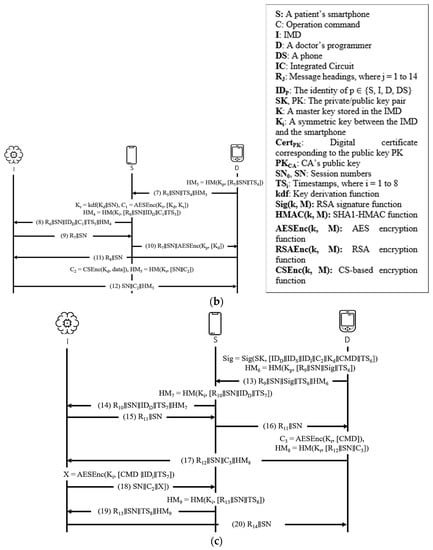
Figure 8.
Chi et al.’s protocol. (a) Initialization phase. (b) Pairing phase. (c) Authentication and authorization phase.
- BAN logic-based formal security analysis.
● Idealization (I1) (I2) (I3) (I4) (I5) (I6) (I7) (I8) ● Assumption (A1) (A2) (A3) (A4) (A5) (A6) (A7) (A8) (A9) (A10) (A11) (A12) (A13) (A14) (A15) (A16) (A17) (A18) (A19) (A20) (A21) (A22) (A23) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) (G8) (G9) (G10) (G11) (G12) (G13) (G14) (G15) (G16) (G17) ● Derivations By (I2) By (I3) (I4) By (I5) (I6) (I7) - AVISPA-based formal security analysis result.
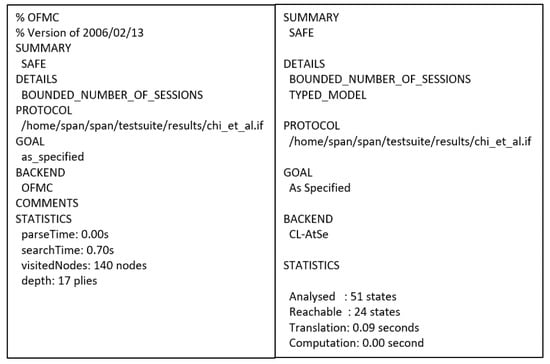 Figure 9. AVISPA result of Chi et al.’s protocol.
Figure 9. AVISPA result of Chi et al.’s protocol.
4.3.4. Parvez et al.’s Protocol
The proposed authentication scheme [26] extended the protocol in [45] that comprises of sensors, which are resource-constrained devices that are implanted in (or wearable on) human body; mobile devices, which are small handheld devices to collect the data sent by the sensors; gateway, which is a trusted server that is used to register sensors, mobile devices and medical experts, and generates different keys for secure communication; and medical experts refers to medical professionals, such as doctors or nurses who analyze and take action with the collected information. The proposed protocol is executed in two phases—registration and authentication—as shown in Figure 10 and Figure 11 illustrates the OFMC and CL-AtSe back-end results of the protocol.
- BAN logic-based formal security analysis.
● Idealization (I1) (I2) (I3) (I4) 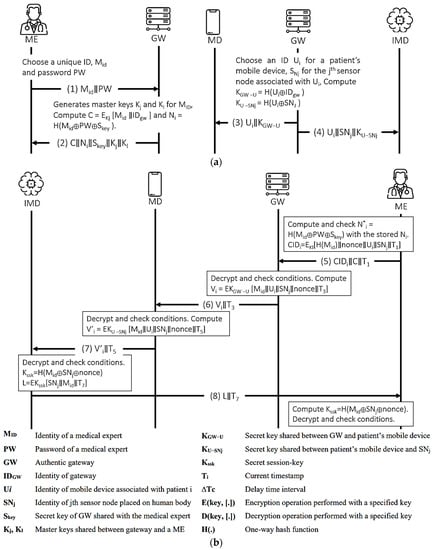 Figure 10. Parvez et al.’s protocol. (a) Registration procedure. (b) Authentication Procedure.
Figure 10. Parvez et al.’s protocol. (a) Registration procedure. (b) Authentication Procedure.● Assumption (A1) (A2) (A3) (A4) (A5) (A6) (A7) (A8) (A9) (A10) (A11) (A12) (A13) (A14) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) ● Derivations (D1) (D2) (D3) (D4) (D5) (D6) (I2) (D7) (D8) (D9) (D10) (D11) (D12) (D13) . (D14) (D15) (D16) (D17) (D18) (D19) (D20) (D21) (D22) - AVISPA-based formal security analysis result.
 Figure 11. AVISPA result of Parvez et al.’s protocol.
Figure 11. AVISPA result of Parvez et al.’s protocol.
4.3.5. Iqbal et al.’s Protocol
The proposed protocol [27] works between the sensor nodes (SN), controller (BS), and a medical server (MS). The SNs are (implanted) medical devices that sense vital physiological information. In this protocol, a BS is only used to assist the authentication process so that the SN directly communicates with the MS after successful authentication is achieved. The protocol is executed in three stages: deployment, authentication, and data communication, as shown in Figure 12 and Figure 13 presents the OFMC and CL-AtSe back-end results of the protocol.
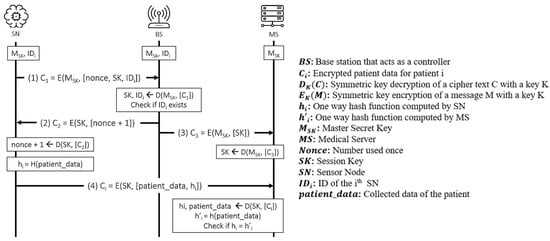
Figure 12.
Iqbal et al.’s protocol.
- BAN logic-based formal security analysis
● Idealization (I1) (I2) (I3) (I4) ● Assumption (A1) (A2) (A3) (A4) (A5) (A6) ● Hypotheses (H1) (H2) ● Goals (G1) (G2) (G3) (G4) (G5) ● Derivations (D1) (D2) (D3) (D4) (D5) (D6) (I2) (D7) (D8) , FR, BC (D9) (D10) (D11) , FR (D12) By (D10), (H2), JR - AVISPA-based formal security analysis result.
 Figure 13. AVISPA result of Iqbal et al.’s protocol.
Figure 13. AVISPA result of Iqbal et al.’s protocol.
4.3.6. He and Zeadally’s Protocol
He and Zeadally’s authentication protocol [28] comprises a programmer/controller, the AAL server, and a user. The controller is responsible for communicating with the IMDs and receiving collected physiological information. Once such information is collected, it can be accessed by a remote user after the AAL server authenticates the user. Furthermore, the controller may communicate with different devices, such as home robots for immediate nearby assistance, located in the patient’s premises. The protocol is also executed in two stages: registration and authentication, as shown in Figure 14 and Figure 15 illustrates the OFMC and CL-AtSe back-end results of the protocol.
- BAN logic-based formal security analysis.
● Idealization (I1) (I2) (I3) (I4) ● Assumption (A1) (A2) (A3) (A4) (A5) (A6) (A7) (A8) (A9) (A10) (A11) 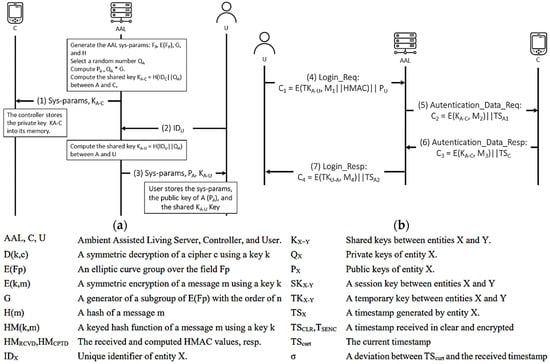 Figure 14. He and Zeadally’s protocol. (a) Registration phase. (b) Authentication phase.
Figure 14. He and Zeadally’s protocol. (a) Registration phase. (b) Authentication phase.● Hypotheses (H1) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) (G8) (G9) (G10) (G11) (G12) ● Derivations (D1) , (D2) (D3) (D4) (D5) (D6) (D7) (D8) (D9) (D10) (D11) (D12) (D13) (D14) (D15) (D16) By (D13), BC, (A6), DH (D17) (D18) (D19) (D20) (D21) (D22) (D23) (D24) (D25) (D26) (D27) (D28) - AVISPA-based formal security analysis result.
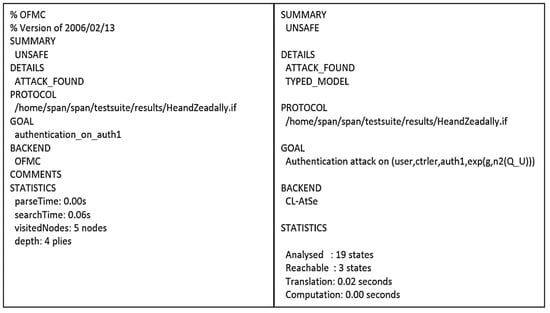 Figure 15. AVISPA result of He and Zeadally’s protocol.
Figure 15. AVISPA result of He and Zeadally’s protocol.
4.3.7. Ellouze et al.’s Protocol
This protocol [29] is a mutual authentication protocol for cardiac IMDs that integrates a powerless device called wireless identification and sensing platform (WISP) with IMDs to conserve the battery lifetime of IMDs by drawing energy from an RFID reader. The authentication scheme operates in regular and emergency modes between the WISP and the RFID reader. The final goal is to create mutual authentication between the programmer and the IMD. Figure 16 shows both modes of the protocol. The authors of this protocol performed AVISPA-based security verification and claimed that the protocol is secure. Hence, only BAN logic-based analysis is performed here.
- BAN logic-based formal security analysis.
- Regular mode.
● Idealization (I1) (I2) (I3) ● Assumption (A1) (A2) (A3) (A4) ● Hypotheses (H1) (H2) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) ● Derivations (D1) (D2) (D3) (D4) (D5) (D6) (I2) (D7) (D8) (D9) (D10) (D11) (D12) (D13) By (D12), (A2), FR, NV - Emergency Mode
● Idealization (I1) (I2) (I3) 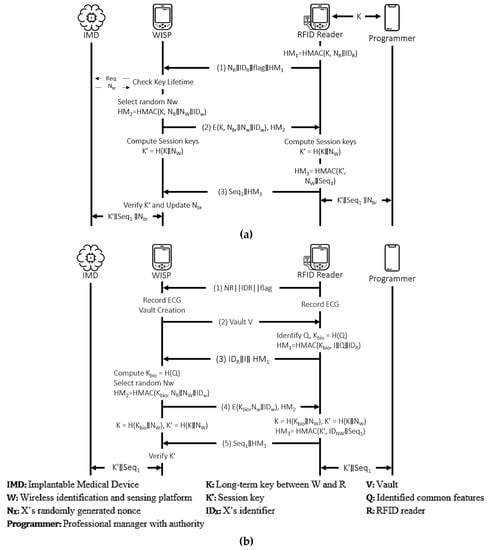 Figure 16. Ellouze et al.’s protocol. (a) Regular Mode. (b) Emergency Mode.
Figure 16. Ellouze et al.’s protocol. (a) Regular Mode. (b) Emergency Mode.● Assumption (A1) (A2) (A3) (A4) ● Hypotheses (H1) (H2) ● Goals (G1) (G2) (G3) (G4) (G5) (G6) (G7) ● Derivations (D1) (D2) . (D3) . (D4) (D5) (D6) (I2) (D7) (D8) (D9) (D10) (D11) (I3) (D12) (D13)
5. Discussion
The authentication protocols described and analyzed in the previous section have shown the importance of formally analyzing security protocols for usage reliability.
Khan et al.’s protocol is safe as per the output of both BAN logic and AVISPA in satisfying the goals. The hub node can be sure about the validity of the temporary identification (G1 and G2) and the auxiliary authentication parameter (G3 and G4). Furthermore, the sensor node trusts the newly generated session key (G6 and G7).
The proxy-assisted access control scheme proposed by Wu et al. is the second safe protocol for the authentication goals set. The main objective of the protocol is to device a shared symmetric key Kt that the programmer and the IMD will use to secure the information exchanged. Accordingly, (G2) to (G5), (G8), and (G9) show that this objective is satisfied. Furthermore, other less essential facts that involve the IDs of the participating agents are authentic.
Chi et al.’s access control scheme with forensic capability is designed to safeguard IMDs from unauthorized access. The protocol is secure as per the results of BAN logic and AVISPA on authenticity and secrecy properties. The goals in the BAN logic analysis investigated the authentication between the IMD, smartphone, and the programmer through the keys Kd, Kr, Kp, and Ki.
The user authentication scheme in WBAN, as proposed by Parvez et al., is found to be unsafe, by both AVISPA and BAN logic, on the authentication of the shared key Kssk. The shared key that will be used by the medical expert and the IMD is computed from the nonce, SNj, and Mid. In terms of BAN logic, this means the IMD has to believe these values to believe the computed session key. Consequently, the derivations (D11) to (D13) alone cannot enable the IMD to derive its belief to the shared key- which calls for two new hypotheses about the control of the nonce and Mid by the mobile device that acts as a proxy between the IMD and the external devices. Such hypotheses may not be accurate given that ME and GW generated these values, respectively. However, since the message passed from the MD to the IMD is fresh and protected by the key that both parties trust, we may still be convinced that the IMD can derive the session key. The final goal, (G5), can be derived after a new message arrives from the ME to IMD using the session key Kssk.
Iqbal et al.’s authentication and key agreement scheme are proposed for node authentication in the body sensor environment. The protocol has some serious issues, typically concerning reply attacks. Specifically, the security goals (G4) and (G5) related to the mutual authentication between the medical server and the IMD cannot be satisfied as-is. The medical server cannot be sure about the freshness of the shared session key forwarded by the base station, making the message vulnerable to replay attack. Consequently, the hypotheses (H1) and (H2) need to be added to maintain authentication. More importantly, it is possible to improve the protocol by including a nonce along with the session key SK when BS sends the message to the MS.
He and Zeadally’s scheme aims to improve the security of ambient assisted living. It mainly focuses on the mutual authentication between the Controller and the User via the AAL server. With this regard, the goals (G3), (G5), (G8), and (G10) refer to the secure information exchange, while (G6) and (G11) specify the secure session key exchange between the User and the Controller. The remaining goals are related to the exchange of symmetric keys among all the participants of the authentication scheme. The result of both the BAN logic and AVISPA illustrate that it is not possible to conclusively state the protocol as safe to use. That is, the derivations show that for the AAL server to believe that TKA-U is a key that is only known by itself and the User (G1), it must first believe that PU is the public key of the User that is encrypting the messages by the key TKA-U (G2). This, in turn, needs the AAL server to believe that this User has jurisdiction over the public key PU, meaning that the AAL server has to trust this User concerning PU (H1). Consequently, we cannot prove the goals (G1) and (G2) without the hypothesis we added.
Ellouze et al.’s scheme is a specific authentication protocol proposed for cardiac IMDs with powerless authentication mechanisms. The protocol operates in both emergency and regular modes to authenticate the programmer to the IMD and vice versa. The authors of this protocol have performed AVISPA based formal security analysis and reported that the protocol is safe. However, when the protocol is analyzed using BAN logic, a contrary result is found. The result from the analysis of the BAN logic in the emergency mode of the protocol shows the requirement of two additional hypotheses to satisfy the authentication between the WISP and the RFID Reader. Specifically, the WISP cannot conclusively believe the KBio. This key will be used to derive the session key K’ latter if the reader believes it without guaranteeing the freshness of NR. Furthermore, the security goal that conditions the guarantee for the WISP that the RFID Reader believes the session key K’ (G7) can only be satisfied if the freshness of NW is guaranteed. Concerning the regular mode, the same issue exists as shown in the hypotheses (H1) and (H2) for the derivation of (D3), (D4), and (D10).
6. Comparative Analysis
6.1. Comparison by Security Strength
Here, we compare the authentication schemes that are formally analyzed in Section 3. The comparisons are based on security properties, key features that IMD authentication protocols need to possess, computational overhead, and latency. Accordingly, each of the authentication protocols is checked against different security requirements (integrity (INT), confidentiality (CNF), authentication (AUT), session key agreement (SKA), perfect forward secrecy (PFS), and replay attack protection (RAP)) as shown in Table 3.

Table 3.
Comparison by security strength.
6.2. Comparison by Functionality
Various vital functionalities are expected to be satisfied by authentication protocols, in particular features like emergency authentication (EMA), key update mechanisms (KUM), adaptability (ADP), application (APP), and anonymity (ANO) is used to compare the protocols. The comparison result of the authentication schemes concerning these functionalities is shown in Table 4.

Table 4.
Comparison by functionality.
6.3. Comparison by Computational and Communicational Overhead
The computational and communication overheads, in terms of time, to perform the cryptographic operations (such as the number of signatures, symmetric, and asymmetric key encryption and decryption, hash functions, and XOR operations) [46,47,48], and size of the messages communicated [46,49], respectively, are shown in Table 5, Table 6, Table 7 and Table 8. The comparison of protocols concerning computational and communication overheads is depicted in Figure 17.

Table 5.
Approximate computational time in millisecond.

Table 6.
Approximate message length in Bits.

Table 7.
Computational overheads of the authentication protocols.

Table 8.
Communication overheads of the authentication protocols.
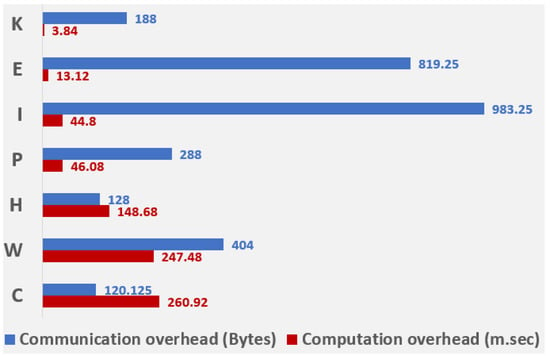
Figure 17.
Computational and communication overheads of the authentication protocols.
6.4. Overall Comparison of the Authentication Protocols
The comparison metrics—security strength, functionality, and efficiency—can be collectively used to understand better these schemes regarding security, competence, and capability. Such comparison can be best described in a triangular graph, as shown in Figure 18.
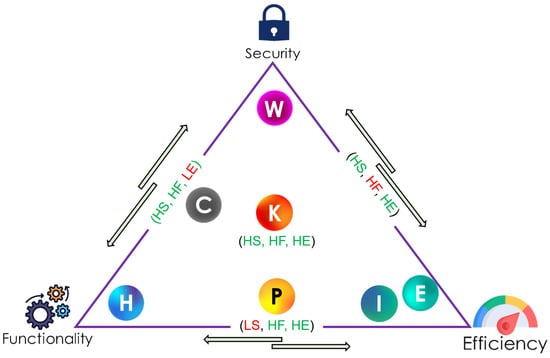
Figure 18.
Overall comparison of the authentication protocols using triangular graph.
Figure 18 shows that Khan et al.’s scheme is located at the center since the protocol satisfies all the three metrics compared to the other protocols. On the other hand, while Iqbal et al. and Ellouze et al.’s schemes are only good at efficiency, Wu et al.’s and He and Zeadally’s protocols fulfill only security and functionality, respectively. Concerning Chi et al.’s scheme, only functionality and security is satisfied while efficiency is not met. On the other hand, the Parvez et al.’s, satisfy functionality and efficiency while falling short in meeting security.
7. Conclusions
In this research, we studied various IMD-related security and privacy requirements, such as confidentiality, integrity, availability, mutual authentication, non-traceability, user anonymity, session-key agreement, forward and backward secrecy, known attack resistance, device-existence privacy, device-type privacy, specific-device ID privacy, measurement and log privacy, and bearer privacy. Furthermore, we examined some of the well-known threats of IMDs: learning the existence of IMD, eavesdropping on the wireless channel that links the IMDs to the external devices, replay attacks by forwarding exchanged messages at a later time, changing critical settings of the implants by producing new commands, and exhausting the battery life of IMDs to execute denial of service attacks. After studying various IMD-related security and privacy concepts, we have used a formal approach to test the strength of seven contemporary authentication schemes designed to thwart attacks surrounding IMD-enabled systems. Consequently, we formally analyzed these authentication schemes using AVISPA and BAN logic, and compared them against their security strength, computational and communication overheads, and other features. The result analysis indicates that Khan et al. is the lightest and fastest while preserving privacy and satisfying the security properties shown in Table 3. The protocol uses only a cryptographic hash function and a bitwise XOR function, which made its computational and communication overheads lighter. Furthermore, the protocol is adaptable with minimal effort for the already implanted devices and no trouble for the yet-to-be implanted devices. Another important lesson taken from the analysis of the protocols is the necessity of formal security verification before IMD protocols are released for public use. In addition, IMD authentication schemes need to satisfy essential functionalities such as portability and emergency authentication while remaining lightweight. Accordingly, there is an interest to design a new security protocol for IMD-enabled insulin pumps in the future, which will serve as an artificial pancreas for patients in need. While designing such protocols, the authors would like to apply the essential lessons learned during this study. The newly designed protocol should be formally analyzed while satisfying the emergency authentication, adaptability, key update mechanisms, and anonymity requirements. The authors would also put forth an effort to balance these requirements with efficient communication and computational overhead and good attack resistance.
Author Contributions
Conceptualization, D.G.D., I.Y. and J.K.; methodology, D.G.D. and I.Y.; validation, D.G.D. and J.K.; formal analysis, D.G.D. and J.K.; investigation, D.G.D. and Y.E.G.; data curation, D.G.D. and J.K.; writing—original draft preparation, D.G.D., Y.E.G. and J.K.; writing—review and editing, I.Y. and J.K.; visualization, D.G.D.; supervision, I.Y.; project administration, I.Y.; funding acquisition, I.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2020R1I1A2073603) as well as the Soonchunhyang University Research Fund.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Coherent Market Insights. U.S. Implantable Medical Devices Market Analysis. 2020. Available online: https://www.coherentmarketinsights.com/market-insight/us-implantable-medical-devices-market-3853 (accessed on 20 November 2021).
- IMARC Implantable Medical Devices Market: Global Industry Trends, Share, Size, Growth, Opportunity and Forecast 2020–2025. 2020. Available online: https://www.imarcgroup.com/implantable-medical-devices-market (accessed on 20 November 2021).
- Maddock, N.A.; James, N.L.; McKenzie, D.R.; Patrick, J.F. Technological advances for polymers in active implantable medical devices. In The Design and Manufacture of Medical Devices; Elsevier: Amsterdam, The Netherlands, 2012; pp. 239–272. [Google Scholar]
- Kitana, A.; Traore, I.; Woungang, I. Towards an Epidemic SMS-based Cellular Botnet. J. Internet Serv. Inf. Secur. 2020, 10, 38–58. [Google Scholar]
- Shichkina, Y.A.; Kataeva, G.V.; Irishina, Y.A.; Stanevich, E.S. The use of mobile phones to monitor the status of patients with Parkinson’s disease. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 55–73. [Google Scholar]
- Camara, C.; Peris-Lopez, P.; Tapiador, J.E. Security and privacy issues in implantable medical devices: A comprehensive survey. J. Biomed. Inform. 2015, 55, 272–289. [Google Scholar] [CrossRef] [Green Version]
- Liu, N.; Yu, M.; Zang, W.; Sandhu, R.S. Cost and Effectiveness of TrustZone Defense and Side-Channel Attack on ARM Platform. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 1–15. [Google Scholar]
- Kasturi, G.S.; Jain, A.; Singh, J. Detection and Classification of Radio Frequency Jamming Attacks using Machine learning. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 49–62. [Google Scholar]
- Wong, S.K.; Yiu, S.-M. Location spoofing attack detection with pre-installed sensors in mobile devices. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 16–30. [Google Scholar]
- Alizadeh, M.; Andersson, K.; Schelen, O. A Survey of Secure Internet of Things in Relation to Blockchain. J. Internet Serv. Inf. Secur. 2020, 10, 47–75. [Google Scholar]
- Wong, S.K.; Yiu, S.-M. Identification of device motion status via Bluetooth discovery. J. Internet Serv. Inf. Secur. 2020, 10, 59–69. [Google Scholar]
- Rushanan, M.; Rubin, A.D.; Kune, D.F.; Swanson, C.M. Sok: Security and privacy in implantable medical devices and body area networks. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 524–539. [Google Scholar]
- Siddiqi, M.A.; Doerr, C.; Strydis, C. Imdfence: Architecting a secure protocol for implantable medical devices. IEEE Access 2020, 8, 147948–147964. [Google Scholar] [CrossRef]
- Belkhouja, T.; Sorour, S.; Hefeida, M.S. Role-Based Hierarchical Medical Data Encryption for Implantable Medical Devices. In Proceeding of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Tutari, V.H.; Das, B.; Chowdhury, D.R. A Continuous Role-Based Authentication Scheme and Data Transmission Protocol for Implantable Medical Devices. In Proceedings of the 2019 Second International Conference on Advanced Computational and Communication Paradigms (ICACCP), Gangtok, India, 25–28 February 2019; pp. 1–6. [Google Scholar]
- Camara, C.; Peris-Lopez, P.; De Fuentes, J.M.; Marchal, S. Access control for implantable medical devices. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1126–1138. [Google Scholar] [CrossRef]
- Zhang, Z.; Xu, X.; Han, S.; Liang, Y.; Liu, C. Wearable Proxy Device-Assisted Authentication Request Filtering for Implantable Medical Devices. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Astillo, P.V.; Choudhary, G.; Duguma, D.G.; Kim, J.; You, I. TrMAps: Trust Management in Specification-based Misbehavior Detection System for IMD-Enabled Artificial Pancreas System. IEEE J. Biomed. Health Inform. 2021, 25, 3763–3775. [Google Scholar] [CrossRef]
- Astillo, P.V.; Duguma, D.G.; Park, H.; Kim, J.; Kim, B.; You, I. Federated intelligence of anomaly detection agent in IoTMD-enabled Diabetes Management Control System. Futur. Gener. Comput. Syst. 2021, 128, 395–405. [Google Scholar] [CrossRef]
- Abhishta, A.; van Heeswijk, W.; Junger, M.; Nieuwenhuis, L.J.M.; Joosten, R. Why would we get attacked? An analysis of attacker’s aims behind DDoS attacks. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 3–22. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. A. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.-C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Khan, H.; Dowling, B.; Martin, K.M. Highly efficient privacy-preserving key agreement for wireless body area Networks. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy in Computing and Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1064–1069. [Google Scholar]
- Wu, L.; Chi, H.; Du, X. A Secure Proxy-based Access Control Scheme for Implantable Medical Devices. arXiv 2018, arXiv1803.07751. [Google Scholar]
- Chi, H.; Wu, L.; Du, X.; Zeng, Q.; Ratazzi, P. e-SAFE: Secure, efficient and forensics-enabled access to implantable medical devices. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Parvez, K.; Zohra, F.T.; Jahan, M. A secure and lightweight user authentication mechanism for wireless body area network. In Proceedings of the 6th International Conference on Networking, Systems and Security, Dhaka, Bangladesh, 17–19 December 2019; pp. 139–143. [Google Scholar]
- Iqbal, J.; Umar, A.I.; ul Amin, N.; Din, N. Efficient Key Agreement and Nodes Authentication Scheme for Body Sensor Networks. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 180–187. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S. Authentication protocol for an ambient assisted living system. IEEE Commun. Mag. 2015, 53, 71–77. [Google Scholar]
- Ellouze, N.; Allouche, M.; Ben Ahmed, H.; Rekhis, S.; Boudriga, N. Securing implantable cardiac medical devices: Use of radio frequency energy harvesting. In Proceedings of the 3rd International Workshop on Trustworthy Embedded Devices, Berlin, Germany, 4 November 2013; pp. 35–42. [Google Scholar]
- Fu, C.; Du, X.; Wu, L.; Zeng, Q.; Mohamed, A.; Guizani, M. Poks based secure and energy-efficient access control for implantable medical devices. In International Conference on Security and Privacy in Communication Systems; Springer: Cham, Switzerland, 2019; pp. 105–125. [Google Scholar]
- Antonescu, B.; Basagni, S. Wireless body area networks: Challenges, trends and emerging technologies. In Proceedings of the 8th International Conference on Body Area Networks, Boston, MA, USA, 30 September–2 October 2013; pp. 1–7. [Google Scholar]
- Ellouze, N.; Allouche, M.; Ahmed, H.B.; Rekhis, S.; Boudriga, N. Security of implantable medical devices: Limits, requirements, and proposals. Secur. Commun. Netw. 2014, 7, 2475–2491. [Google Scholar] [CrossRef]
- Amar, A.B.; Kouki, A.B.; Cao, H. Power approaches for implantable medical devices. Sensors 2015, 15, 28889–28914. [Google Scholar] [CrossRef]
- Islam, M.N.; Yuce, M.R. Review of medical implant communication system (MICS) band and network. ICT Express 2016, 2, 188–194. [Google Scholar] [CrossRef] [Green Version]
- Strydis, C.; Seepers, R.M.; Peris-Lopez, P.; Siskos, D.; Sourdis, I. A system architecture, processor, and communication protocol for secure implants. ACM Trans. Archit. Code Optim. 2013, 10, 57. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.-H. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- Halperin, D.; Heydt-Benjamin, T.S.; Ransford, B.; Clark, S.S.; Defend, B.; Morgan, W.; Fu, K.; Kohno, T.; Maisel, W.H. Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses. In Proceedings of the 2008 IEEE Symposium on Security and Privacy (SP 2008), Oakland, CA, USA, 18–22 May 2008; pp. 129–142. [Google Scholar]
- Burleson, W.; Clark, S.S.; Ransford, B.; Fu, K. Design challenges for secure implantable medical devices. In Proceedings of the DAC Design Automation Conference 2012, San Francisco, CA, USA, 3–7 June 2012; pp. 12–17. [Google Scholar]
- Zheng, G.; Shankaran, R.; Orgun, M.A.; Qiao, L.; Saleem, K. Ideas and challenges for securing wireless implantable medical devices: A review. IEEE Sens. J. 2016, 17, 562–576. [Google Scholar] [CrossRef]
- Gollakota, S.; Hassanieh, H.; Ransford, B.; Katabi, D.; Fu, K. They can hear your heartbeats: Non-invasive security for implantable medical devices. In Proceedings of the ACM SIGCOMM 2011 Conference, Toronto, ON, Canada, 15–19 August 2011; pp. 2–13. [Google Scholar]
- Duguma, D.G.; Kim, J.; Kim, B.; You, I. A Formal Security Verification on He and Zeadally’s Authentication Protocol for IMD-Enabled Ambient Assisted Living System. In Proceedings of the 2020 ACM International Conference on Intelligent Computing and its Emerging Applications, GangWon, Korea, 12–15 December 2020; pp. 1–6. [Google Scholar]
- Kim, J.; Lee, S.; Duguma, D.G.; Kim, B.; You, I. Comments on” Securing implantable cardiac medical devices” Use of radio frequency energy harvesting. In Proceedings of the 2020 ACM International Conference on Intelligent Computing and its Emerging Applications, GangWon, Korea, 12–15 December 2020; pp. 1–5. [Google Scholar]
- Boyd, C.; Mao, W. On a Limitation of BAN Logic. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993; pp. 240–247. [Google Scholar]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project AVISPA. In Proceedings of the APPSEM 2005 Workshop, Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- Al-Turjman, F.; Alturjman, S. Context-sensitive access in industrial internet of things (IIoT) healthcare applications. IEEE Trans. Ind. Inform. 2018, 14, 2736–2744. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Khan, M.K. Authentication protocols for implantable medical devices: Taxonomy, analysis and future directions. IEEE Consum. Electron. Mag. 2017, 7, 57–65. [Google Scholar] [CrossRef]
- Saho, N.J.G.; Ezin, E.C. Comparative Study on the Performance of Elliptic Curve Cryptography Algorithms with Cryptography through RSA Algorithm. In Proceedings of the CARI 2020-Colloque Africain sur la Recherche en Informatique et en Mathématiques Apliquées, Thiès, Senegal, 22 September–2 October 2020. [Google Scholar]
- Fog, A. Instruction tables: Lists of Instruction latencies, Throughputs and Micro-Operation Breakdowns for Intel, AMD and VIA CPUs. Available online: https://www.agner.org/optimize/instruction_tables (accessed on 20 November 2021).
- FM4DD. X509 Certificate Examples for Testing and Verification. Available online: http://fm4dd.com/openssl/certexamples.htm (accessed on 20 November 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).