Abstract
This study investigates combining the property of human vision system and a 2-phase data hiding strategy to improve the visual quality of data-embedded compressed images. The visual Internet of Things (IoT) is indispensable in smart cities, where different sources of visual data are collected for more efficient management. With the transmission through the public network, security issue becomes critical. Moreover, for the sake of increasing transmission efficiency, image compression is widely used. In order to respond to both needs, we present a novel data hiding scheme for image compression with Absolute Moment Block Truncation Coding (AMBTC). Embedding secure data in digital images has broad security uses, e.g., image authentication, prevention of forgery attacks, and intellectual property protection. The proposed method embeds data into an AMBTC block by two phases. In the intra-block embedding phase, a hidden function is proposed, where the five AMBTC parameters are extracted and manipulated to embed the secret data. In the inter-block embedding phase, the relevance of high mean and low mean values between adjacent blocks are exploited to embed additional secret data in a reversible way. Between these two embedding phases, a halftoning scheme called direct binary search is integrated to efficiently improve the image quality without changing the fixed parameters. The modulo operator is used for data extraction. The advantages of this study contain two aspects. First, data hiding is an essential area of research for increasing the IoT security. Second, hiding in compressed images instead of original images can improve the network transmission efficiency. The experimental results demonstrate the effectiveness and superiority of the proposed method.
1. Introduction
Rapid technological advances in network technology have made it possible to access large amounts of information on the Internet. However, the Internet environment is not secure enough for personal information to be stored safely. To ensure that personal information is not easily stolen or distributed maliciously, data hiding schemes are useful techniques for the Internet of Things (IoT) and visual IoT [1]. Due to the security problems of many image encryption schemes summarized in [2], data hiding is a critical area of research for increasing the security of the network information.
Nowadays, the data hiding technique has been investigated and published by many researchers. Data hiding is of two main kinds: reversible and irreversible. Reversible data hiding methods [3,4,5,6] emphasize that the original image can be recovered after data hiding. Thus, the images that require high detail information use reversible data hiding, such as mechanical drawing and medical imaging. However, to maintain the reversibility of the stego (i.e., the data-embedded) image, the amount of data that can be embedded will decrease or additional information would be required to recover from the stego image.
For irreversible data hiding [7,8], the least significant bit (LSB), exploiting modification directions (EMDs) and pixel value differencing (PVD) might be three of the most common techniques. The LSB method embeds binary secret data in the host image by replacing the LSB of the pixels to generate the stego image [9]. LSB is used because it can keep the minimal modification of the pixels while embedding data in the image. The EMD method embeds the digit data in n stego pixels, which at the most adjusts one of the stego pixels by increasing or decreasing its value by 1 (i.e., ±1) and leaving the rest unchanged [10]. The key advantage of EMD is that it decreases the number of pixels that need to be adjusted for data embedding; thus, it improves the quality of the stego image. The PVD method embeds the fixed size of data in the host image by adjusting the difference between the two pixels in pairs [11]. To reduce the modification between the two pixels in a pair that substantially decreases the quality of the stego image, the PVD method usually divides the pixel values into several sections of the same size. Although the irreversible data hiding technique cannot recover the stego image back to what it was, it usually does not need additional data for recovery and data extraction. In addition, the irreversible data hiding technique can achieve a higher hiding capacity. Therefore, in this paper, we propose the irreversible scheme. Figure 1 illustrates the application scenario (and the overall framework) of the proposed method.
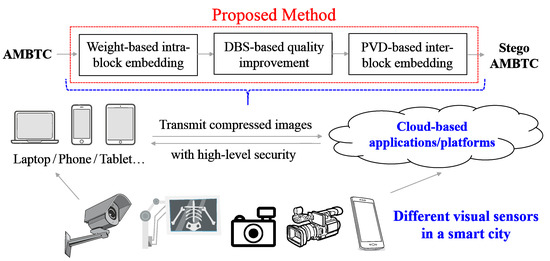
Figure 1.
Conceptual framework and the application scenario which illustrate the usage of the proposed method. In a smart city, the proposed method can perform data-hiding and compression jointly to increase the security level of visual sensing data.
Using the image data hiding techniques, we can embed secret data into an image to protect the owner’s intellectual property and prevent abuse or tampering. Image data hiding is typically based on some specific image compression format [12,13,14,15,16]. When the image is compressed, it requires less memory for storage and is more efficient for transmission via the Internet. Image compression formats can be divided into lossy image compression and lossless image compression. Although lossy compression cannot recover the original image, it significantly reduces the image size, i.e., the compression rate performance of lossy compression is better than that of lossless compression. In this study, we use a lossy image compression method called absolute moment block truncation coding (AMBTC), to effectively compress the image.
The advantage of the AMBTC compression technique is that it requires quite low computation power and can still achieve an acceptable image quality. Therefore, it is suitable for low-energy devices. Recently, several researchers have investigated the AMBTC-based data hiding methods. Ou and Sun [17] proposed a steganography method that classifies the AMBTC blocks into smooth or complex blocks. In [17], two embedding schemes are designed according to the block type, which helps the authors to exploit the different block properties more efficiently. Tang et al. [18] proposed an adaptive image steganography method that uses the interpolation technique to improve the hiding performance. Lin et al. [19] proposed an image authentication method that also divides the AMBTC blocks into smooth or complex blocks. In smooth blocks, the authentication code is embedded into the bitmap, whereas in complex blocks, the authentication code is embedded to adjust the quantization levels using a reference table. Huang et al. [20] proposed a hybrid secret hiding scheme for data hiding in AMBTC images, in which, similar to [17] and [19], two types of blocks are classified. Then, data embedding in the complex blocks exploits the difference between high and low mean values of a block; therefore, it achieves a higher embedding capacity than the previous methods. Al-Salhi and Lu [21] presented an image concealment scheme that uses PVD techniques. Furthermore, the human visual system and adaptive neural networks are integrated to improve the image quality. Hong et al. [22] proposed an AMBTC-based data hiding method that uses a suppress threshold mechanism and a perturbation technique to minimize the block distortion in the stego image.
However, image quality image is inevitably degraded or a few image details are lost after compression by AMBTC and the data hiding procedure. Thus, this study adopts a halftone image optimization technology called Direct Binary Search (DBS). DBS is widely used instead of the heuristic approach to optimize halftone images by using a human visual system to minimize the total squared perceived error between a continuous tone image and a halftone image [23,24]. In this study, we adopt the Swap operator from the DBS framework and use this operator to optimize the stego image that is compressed and contains the hidden data. Using the Swap operator not only makes the stego image visually closer to the original image without affecting the hiding data, but also upgrades the image quality.
2. Related Work (AMBTC Compression)
As mentioned, AMBTC is a lossy image compression method which requires quite low computation power [25]. Therefore, AMBTC is suitable for real-time embedded system applications and can obtain a satisfactory compressed image quality. In AMBTC, the input image is first divided into non-overlapped square blocks with the side length of n (i.e., the block size BS equals to n). To compress the image, the average value of all the pixel values in each block is calculated by:
where indicates the i-th pixel value of the block.
The average pixel value is then used as a threshold to generate a bit map by comparing with the pixel values in a block. For the case that is larger than the pixel value, the bit map value is set as 0 (later, it is replaced by the low mean value in the AMBTC compressed block) at the position; otherwise, it is set as 1 (replaced by the high mean value in the AMBTC compressed block). After comparison, the number of pixels whose pixel value is less than is referred as the number of low-mean bits (NL), and the number of pixels whose pixel value is larger than or equal to is referred as the number of high-mean bits (NH). For AMBTC compression, low mean and high mean are the two quantization levels calculated using the following:
and
Figure 2 shows an example of the AMBTC compression. Different from the original grayscale image block, in an AMBTC block, the pixel values are only two quantization levels (low mean and high mean), and thus it can save the memory for storage. In addition, the first absolute moment of each original image block is maintained.
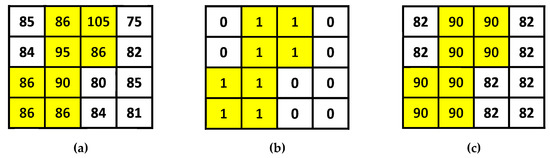
Figure 2.
Illustration of the Absolute Moment Block Truncation Coding (AMBTC) compression. (a) Original image block, where the average pixel value = 86 using (1). (b) The bit map used in AMBTC, where NH = 8 and NL = 8. (c) The AMBTC compressed block, where BS = 4, HM = 90, and LM = 82.
3. Proposed 2-Phase Intra- and Inter-Block Embedding Method
3.1. Intra-Block Embedding Phase
This study presents a 2-phase (intra-block and inter-block) data hiding strategy by manipulating AMBTC parameters. In the intra-block embedding phase, the hidden data are embedded into an AMBTC block by proper modification of the set containing five AMBTC parameters:
where HM, LM, NH, NL, and BS indicate, respectively, high mean, low mean, number of high-mean bits, number of low-mean bits, and AMBTC block size. The hidden function is defined as:
The secret bits to be embedded are converted to their decimal representation . For example, in the case of 5-bit secret data. The goal of intra-block embedding is to adjust the parameters in so that is equal to the result obtained from the modulo operation:
where n is the size of the secret bits embedded in a hidden function. Because the n-bit secret data are embedded by utilizing the modulo operation of with the divisor , the simplest case occurs when is equal to (no adjustment is required). Otherwise, the difference between and must be eliminated by determining the embedding difference such that . Two directions can be used to adjust the embedding difference:
where sgn is the signum function. However, too many combinations of the parameters can lead to the result of (6) for the given secret data. It is difficult to find the optimal parameters efficiently.
To address this problem, the concept of nominal parameters is proposed. As shown in Table 1, three parameters (NH, NL, and BS) in are referred to as the “nominal parameters”, which means that adjusting these three parameters in (6) does not change the actual information of an AMBTC block. Specifically, their actual value is maintained; however, when the hidden function value is calculated, the values of the three parameters are nominally changed, as the form of the trio code is changed. For example, when HM = 120, LM = 80, NH = 9, NL = 7, and BS = 4, the hidden function value is:
However, if the form of the trio code is changed to , the hidden function value becomes:

Table 1.
Rule of adjusting hidden function value by nominal parameters.
Note that for embedding 5-bit secret data, which has 32 combinations, according to Table 1, if the bottom trio code is transmitted, the change in the resulting hidden function value designed to be 16 (i.e., ), which is coincidentally half of 32. It will significantly reduce the search range and alleviate the effect of modifying to maintain image quality. Moreover, according to the rule listed in Table 1, two more directions can be used to adjust the embedding difference:
and
This work utilizes a two-step search approach to adjust the parameters HM and LM. In step 1, the final embedding difference is selected from if it has the minimum absolute value, such that:
In step 2, the parameters are adjusted according to , but the search constraints for the optimal HM (and LM) are set such that the variation of both must be less than a predefined threshold of six (an empirical value). Although using a larger threshold can expand the candidate pool of the eligible combinations, the quality of the stego image will degrade. By contrast, using a smaller threshold will limit the number of eligible combinations. For the combinations that pass the two-step search, the concept of mean square error (MSE) is used to determine the final parameters. The MSE value of a block can be expressed as follows:
where is the pixel value of the original image block, and is the pixel value of the stego block.
The following example describes the data hiding (and the data extraction) of intra-block embedding procedure. Assume that the original AMBTC parameters are , with , and the 5-bit secret data is . When (7) and (10) are applied, the four directions that can eliminate the difference between and are , and . In addition, according to (11), the final embedding difference is , in which the form of the trio code is . Six candidate pairs exist that increase the hidden function value by 5 and satisfy the search constraints:
- (Candidate 1) ;
- (Candidate 2) ;
- (Candidate 3) ;
- (Candidate 4) ;
- (Candidate 5) ; and
- (Candidate 6) ,
where the symbol “prime” indicates that the modification of parameters comes from the embedding of intra-block secret data. Finally, after the resulting MSE values of the six candidate pairs are compared, the candidate whose value corresponding with the minimum mean square error is selected.
Assume that the above fourth candidate pair is selected after comparing among the MSE values, and the stego AMBTC parameters become . In addition, the trio code is . At the receiving end, according to Table 1, the hidden function value is recalculated as 378. Then, the 5-bit secret code can be extracted by using (6) and applying the decimal-to-binary conversion.
3.2. Quality Improvement Phase
In this subsection, we want to improve the quality of the stego image which comes from the intra-block embedding phase. Because the hidden data are embedded by adjusting the AMBTC parameters to certain fixed values that satisfies (6), the challenging part is: How to improve the image quality of current stego image without changing the AMBTC parameters used in (6)? To address this problem, this work applies a modified DBS optimization framework which only uses the swap operator. Using the DBS method enables us to take the human vision system (HVS) into account in the quality Improvement phase. Figure 3 shows the concept of DBS swap operator, and Figure 4 shows the concept of DBS method.
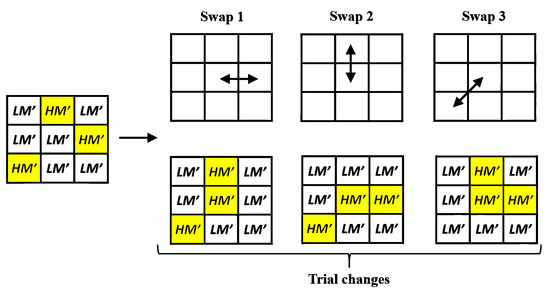
Figure 3.
Illustration of the Direct Binary Search (DBS) swap operator, which is used in the quality improvement phase.
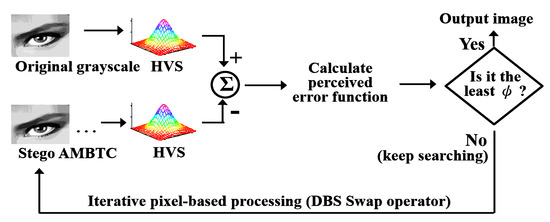
Figure 4.
Concept of the DBS optimization framework used in this study.
In this study, the perceived grayscale image (), the perceived stego AMBTC image () and the perceived error image () are defined, respectively, as
where indicates the HVS filter which simulates the property of human eye, and indicates the lattice basis of addressable dot. The error image indicates the error image between the original grayscale image and the stego image. The perceived error function is defined as
DBS [23] is a pixel-based processing method which changes the regional pattern centered at the current processing position iteratively. For the DBS swap operator, it swaps the current mean value with the mean value of its eight nearest neighbors and calculate the effects of all the trial changes. If an effect of trial change leads to the smallest error function, the corresponding trial swap is accepted. Furthermore, the DBS method introduces an autocorrelation function and a cross-correlation function to accelerate the computational efficiency. Because swapping the mean values between two adjacent pixel positions does not change the number of high-mean (low-mean) bits, the hidden function value is maintained, and the embedded data are preserved.
3.3. Reversible Inter-Block Embedding Phase
Inter-block embedding is performed on a pair of two adjacent blocks. First, all the AMBTC blocks are ordered and divided into two sets: even-order blocks and odd-order blocks :
For a pair of , the intra-block embedding of block is undertaken first. Subsequently, block is subject to the same intra-block embedding procedure; however, we add one more search constraint in the final step of determining , namely that both mean value differences between the two (and ) values must be even numbers:
where () and () represent the high (low) mean values from the even-order block and the odd-order block, respectively. Sometimes, no candidate parameter pairs of block are found because of the constraints used. In this case, we compulsorily change the values of using the method shown in Figure 5. Note that, for the example shown in Figure 5, the value of is increased by 1; however, the hidden function value is unchanged (i.e., the secret data of the intra-block embedding are not damaged) because the values of are modified accordingly.
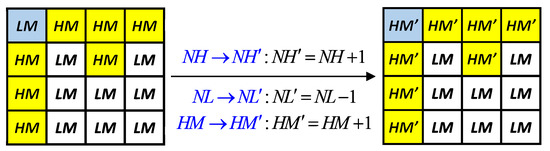
Figure 5.
Illustration of compulsorily modifying parameters to satisfy search constraints and maintain hidden function values simultaneously.
By setting the constraint of even parity in (18) in advance, two extra secret bits can be embedded between blocks according to the rules in Table 2, where the symbol “double prime” indicates that the modification of parameters comes from the embedding of inter-block secret data.

Table 2.
Rule of inter-block embedding.
In this work, we propose a reversible inter-block embedding scheme, meaning that, in the secret extraction phase, the change resulting from the interblock embedding procedure is reversible. Therefore, the quality of the stego image can be preserved to a certain extent. The following example describes the inter-block embedding and extraction procedures. Assume that the high (low) mean values of the block pair are and , and that the 2-bit secret code is . As per Table 2, the modified parameters of become , whereas in block , is maintained. At the receiving end, the differences between the mean values are first calculated as and . The 2-bit secret code can be extracted by utilizing the modulo operation
Furthermore, the original mean values can be retrieved using
4. Experimental Results and Discussions
For evaluation, the performance of the proposed method is compared with the recently published methods in [17] (2015), [20] (2017), and [22] (2017). Because medical images are essential sources of visual data in smart cities (for example, a smart home-based health care system which needs to transmit mass medical images for telemedicine), eight 400 × 400 test images are collected from the public database [25] (Figure 6).

Figure 6.
The eight test images. (a) Artifix. (b) Knee. (c) Macosessix. (d) Matrix. (e) Mecanix. (f) Obelix. (g) Panoramix. (h) Phenix.
Moreover, for the methods in [17,20,22], blocks are classified as smooth and complex blocks. Similarly, in our comparison, the concept in [17] is adopted to embed data into smooth blocks, and the proposed method is used to embed data into complex blocks. In addition to comparing the payload (i.e., data capacity in units of bits), this work adopts two image quality measures to fairly evaluate the performance of each method. The first quality measure is called HVS–based Peak Signal-to-Noise Ratio (HPSNR), which integrates the characteristics of HVS low-pass filter with the traditional Peak Signal-to-Noise Ratio (HPSNR). The HPSNR value can be expressed as follows;
where indicates the image size, indicates the HVS low-pass filter; and indicate the pixels values of the input grayscale image and the resulting stego AMBTC image, respectively.
The second quality measure is called Mean Structural Similarly Index Measure (MSSIM), which is an averaging result of multiple number of the traditional Structural Similarly Index Measure (SSIM). The MSSIM value can be expressed as:
where M is the number of SSIM local windows (set as 3 in this paper); and represent the image block within the j-th window, from the input grayscale image and the resulting stego AMBTC image, respectively. Table 3 shows the overall comparison of the four methods as the threshold value (for distinguishing smooth and complex blocks) is equal to 2. As shown in Table 3, because most AMBTC blocks are classified as complex blocks due to the small threshold, the quality of stego AMBTC image using the proposed method achieves very satisfactory results. As shown in Table 3, because most AMBTC blocks are classified as complex blocks due to the small threshold, the quality of stego AMBTC image using the proposed method achieves very satisfactory results. It demonstrates that the proposed quality improvement phase is effective.

Table 3.
Overall comparison of the four methods (when the threshold value is 2).
When a larger threshold value is applied, more blocks are classified smooth blocks. For the test image Matrix, embedding capacity for different methods is similar because the number of smooth blocks is considerably larger than that of complex blocks. However, the payload rows of Table 3 and Table 4 show that the proposed method completely outperforms the other three methods in terms of embedding capacity. The results validate that the proposed intra- and interblock embedding schemes could utilize the property of the complex blocks to embed data. The comparison of the image quality reveals that the proposed method has higher HPSNR/MSSIM values than the methods in [17,20,22], which are also higher than those for some original AMBTC images. Furthermore, for the comparison of computational performance, the average processing times required to produce a stego image are 5.47 ms (in [17]), 6.11 ms (in [20]), 5.85 ms (in [22]), and 6.93 ms (in the proposed method). All the data hiding methods are implemented in the Windows 7 operating system, with 2.7 GHz CPU and 4 GB RAM. Although adding the modified DBS into the proposed data hiding method increases the processing time, the improvement of the image quality is remarkable.

Table 4.
Overall comparison of the four methods (when the threshold value is 8).
Figure 7 presents a comparison of the variation of the usage of the thresholds of 2, 4, 8, 16, and 32 (using the test image Knee as an example). Because the pixel values in a smooth block are close to each other, the data capacity of a smooth block normally higher than that of a complex block. Thus, for all the methods, when the threshold is larger, more blocks are classified as smooth blocks, and larger average embedding capacity is yielded (Figure 6a). However, the quality of the stego image deteriorates accordingly (Figure 6b). The capacity of a pair of blocks in the proposed scheme is 12 bits, which is larger than the other three methods. Therefore, as the threshold increased from 32 to 2, capacity in the proposed scheme does not considerably decrease. The method in [20] exhibits maximum capacity when thresholds are 16 and 32 because in [20], the capacity of a complex block is given by , where indicates the threshold value. However, the image quality (HPSNR) of [20] abruptly decreases from to . In contrast, in the proposed method, the image quality is maintained to a certain extent.
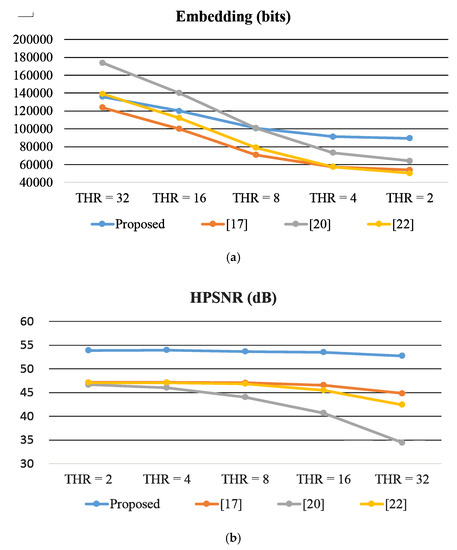
Figure 7.
Comparison of the variation of the usage of different thresholds. (a) Results of data capacity. (b) Results of Human Vision System-based Peak Signal-to-Noise Ratio (HPSNR) value.
Figure 8 shows the visual comparison of different methods. In Figure 8, the threshold is set as 8 for all methods. Compared with the other methods, the proposed method exhibits clearer results in the central parts, and the color is closer to the original grayscale image. The rib area (the right red box) in Figure 8f shows that the proposed method preserves the required details of the original image. For the methods in [17,20,22], the presence of block effects is observed, particularly in Figure 8c,d because the data embedding is based on each AMBTC block. By contrast, in the proposed method, quality improvement phase successfully alleviates these unnatural effects.

Figure 8.
Results of visual comparison using the test image Artifix. (a) Original grayscale. (b) Pure AMBTC without data embedding. (c) Result of [17]. (d) Result of [20]. (e) Result of [22]. (f) Result of the proposed method. From (c) to (f), the threshold value is set as 8.
Figure 9 and Figure 10 show the self-evaluation results. Similar to Figure 7, the plot of embedding capacity versus image quality is analyzed. When the threshold is higher than 32, the overall capacity abruptly increases, and a considerable amount of secret data are embedded, which deteriorates image quality. Therefore, in both figures, the image quality curves obviously drop in the right side. However, for these eight test images, with the increasing capacity (under a larger threshold), the reduction in image quality is observed from to . We find that the declination in the curve is not evident within this range. This phenomenon occurs particularly in the images with more flat regions, such as Matrix, Panoramix, and Phenix. Figure 11 shows the results of the proposed method using the test image Phenix (with different threshold values).
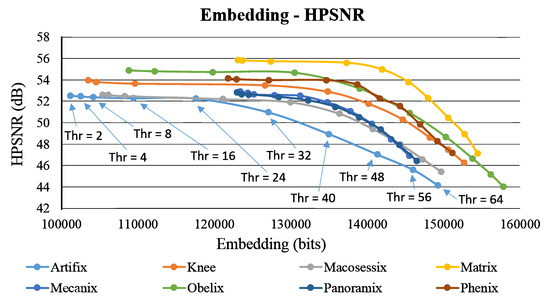
Figure 9.
Results of self-evaluation using different threshold values in terms of embedding capacity versus HPSNR.
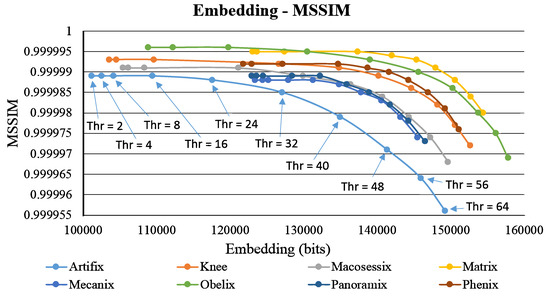
Figure 10.
Results of self-evaluation using different threshold values in terms of embedding capacity versus Mean Structural Similarly Index Measure (MSSIM).

Figure 11.
Results of the proposed method using the test image Phenix (with different threshold values). (a) Threshold = 2. (b) Threshold = 4. (c) Threshold = 8. (d) Threshold = 16. (e) Threshold = 24. (f) Threshold = 32. It can be seen in (e) and (f) that some artifacts occur in the hindbrain region.
Finally, we compare the difference of whether using the inter-block embedding scheme. Figure 12 shows that both stego images have the same capacity with an average capacity of 6 bits per block. Figure 12a presents the application of both intra- and inter-block embedding schemes simultaneously, whereas Figure 12b shows the application of only the intra-block embedding scheme. In Figure 12a, 5-bit secret data are embedded by forcing the hidden function value to be one of 32 possibilities, and the other secret bit is embedded through reversible inter-block embedding. Figure 12b shows the embedding of 6-bit secret data embedded into one block. Thus, the hidden function value in Figure 12b becomes one of 64 possibilities (according to the uncontrolled and random secret data), which severely changes AMBTC parameters and causes image degradation. Although the image quality improvement phase is applied in both figures, the result shown in Figure 12a apparently demonstrates a more pleasing visual quality.
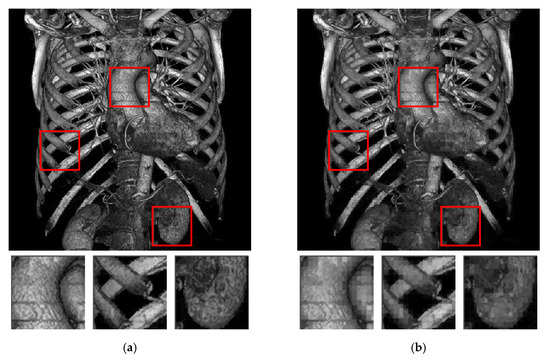
Figure 12.
The difference of whether using the inter-block embedding scheme. (a) Result of using both intra- and inter-block embedding schemes. (b) Result of using only the intra-block embedding scheme.
5. Conclusions
In the era of network and IoT, data hiding becomes a critical research topic for increasing the security of image data transmitted among IoTs. In the past, “seeing is believing” may have been a disputable claim. Today, however, tampering or counterfeiting digital images using current technologies presents no difficulty. It raises a challenge of IoT security and, might, even obstruct the progress of the popularization of IoT. To address this problem, this study presents a data hiding method using the intra- and inter-block embedding strategy. By embedding additional verification code or security-related data in image signal transmission, data hiding technique is an effective solution to the security problem. Embedding data while maintaining good image quality is difficult because the hidden data are random and uncontrollable. Therefore, this work integrates the modified DBS optimization framework into data hiding. As it can be seen in Table 3 and Table 4, the proposed method can embed averagely 121,792 (and 128,712) bits with the average HPSNR values 54.594 dB (and 53.989 dB), which validates the superiority of the proposed method. Compared with the state-of-the-art methods, the proposed method achieves better performance in terms of payload, HPSNR and MSSIM. In our next step, an extended framework about color image steganography is considered.
Author Contributions
Y.H.L. and Y.Y.C. carried out the studies and drafted the manuscript. C.-H.H. participated in its design and helped to draft the manuscript. B.Y.C. conducted the experiments and performed the statistical analysis. All authors read and approved the final manuscript.
Funding
This work was partially supported by the Ministry of Science and Technology, TAIWAN, under Grant No. MOST 107-2221-E-027 -123 - and Ministry of Education, TAIWAN, under the Higher Education Sprout Project (Grant No. 1300-107P735).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liao, X.; Yu, Y.; Li, Z.; Qin, Z. A new payload partition strategy in color image steganography. IEEE Trans. Circuits Syst. Video Technol. 2019. early access. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lu, J.; Hao, F. Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimed. 2018, 25, 46–56. [Google Scholar] [CrossRef]
- Qin, C.; Zhang, X. Effective reversible data hiding in encrypted image with privacy protection for image content. J. Vis. Commun. Image Represent. 2015, 31, 154–164. [Google Scholar] [CrossRef]
- Xiong, L.; Xu, Z.; Shi, Y. An integer wavelet transform based scheme for reversible data hiding in encrypted images. Multidimens. Syst. Signal Process. 2018, 29, 1191–1202. [Google Scholar] [CrossRef]
- Huang, F.; Qu, X.; Kim, H.; Huang, J. Reversible data hiding in JPEG images. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 1610–1621. [Google Scholar] [CrossRef]
- Qian, Z.; Zhang, X. Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 636–646. [Google Scholar] [CrossRef]
- Li, W.; Lin, C.; Pan, J. Novel image authentication scheme with fine image quality for BTC-based compressed images. Multimed. Tools Appl. 2016, 75, 4771–4793. [Google Scholar] [CrossRef]
- Saha, S.; Ghosal, S.; Chakraborty, A.; Dhargupta, S.; Sarkar, R.; Mandal, J. Improved exploiting modification direction-based steganography using dynamic weightage array. Electron. Lett. 2018, 54, 498–500. [Google Scholar] [CrossRef]
- Sharma, D.; Saxena, R.; Singh, N. Dual domain robust watermarking scheme using random DFRFT and least significant bit technique. Multimed. Tools Appl. 2017, 76, 3921–3942. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Sun, Q. Enhance embedding capacity of generalized exploiting modification directions in data hiding. IEEE Access 2017, 6, 5374–5378. [Google Scholar] [CrossRef]
- Shukla, A.; Singh, A.; Singh, B.; Kumar, A. A secure and high-capacity data-hiding method using compression, encryption and optimized pixel value differencing. IEEE Access 2018, 6, 51130–51139. [Google Scholar] [CrossRef]
- Qian, Z.; Zhou, H.; Zhang, X.; Zhang, W. Separable reversible data hiding in encrypted JPEG bitstreams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 1055–1067. [Google Scholar] [CrossRef]
- Qin, C.; Ji, P.; Chang, C.; Dong, J.; Sun, X. Non-uniform watermark sharing based on optimal iterative BTC for image tampering recovery. IEEE Multimed. 2018, 25, 36–48. [Google Scholar] [CrossRef]
- Rahmani, P.; Dastghaibyfard, G. Two reversible data hiding schemes for VQ-compressed images based on index coding. IET Image Process. 2018, 12, 1195–1203. [Google Scholar] [CrossRef]
- He, J.; Huang, S.; Tang, S.; Huang, J. JPEG image encryption with improved format compatibility and file size preservation. IEEE Trans. Multimed. 2018, 20, 2645–2658. [Google Scholar] [CrossRef]
- Li, X.; Meng, X.; Yang, X.; Yin, Y.; Wang, Y.; Peng, X.; He, W.; Dong, G.; Chen, H. Multiple-image encryption based on compressive ghost imaging and coordinate sampling. IEEE Photonics J. 2016, 8, 3900511. [Google Scholar] [CrossRef]
- Ou, D.; Sun, W. High payload image steganography with minimum distortion based on absolute moment block truncation coding. Multimed. Tools Appl. 2015, 74, 9117–9139. [Google Scholar] [CrossRef]
- Tang, M.; Zeng, S.; Chen, X.; Du, Y. An adaptive image steganography using AMBTC compression and interpolation technique. Optik 2016, 127, 471–477. [Google Scholar] [CrossRef]
- Lin, C.; Huang, Y.; Tai, W. A novel hybrid image authentication scheme based on absolute moment block truncation coding. Multimed. Tools Appl. 2017, 76, 463–488. [Google Scholar] [CrossRef]
- Huang, Y.; Chang, C.; Chen, Y. Hybrid secret hiding schemes based on absolute moment block truncation coding. Multimed. Tools Appl. 2017, 76, 6159–6174. [Google Scholar] [CrossRef]
- Al-Salhi, Y.; Lu, S. New steganography scheme to conceal a large amount of secret messages using an improved-AMBTC algorithm based on hybrid adaptive neural networks. In Proceedings of the IEEE 3rd Conference on Big Data Security on Cloud, Beijing, China, 26–28 May 2017; pp. 112–121. [Google Scholar]
- Hong, W.; Chen, T.; Yin, Z.; Luo, B.; Ma, Y. Data hiding in AMBTC images using quantization level modification and perturbation technique. Multimed. Tools Appl. 2017, 76, 3761–3782. [Google Scholar] [CrossRef]
- Liao, J. Theoretical bounds of direct binary search halftoning. IEEE Trans. Image Process. 2015, 24, 3478–3487. [Google Scholar] [CrossRef] [PubMed]
- Thomas, S.; Gharge, S. Halftone visual cryptography for grayscale images using error diffusion and direct binary search. In Proceedings of the 2nd International Conference on Trends in Electronics and Informatics (ICOEI 2018), Beijing, China, 11–12 May 2018; pp. 1091–1096. [Google Scholar]
- Osirix Database. Knowledge Base. Available online: https://www.osirix-viewer.com/support/knowledge-base/ (accessed on 10 March 2019).
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).