Abstract
Smart homes can improve the quality of life and be implemented by Internet of Things (IoT) technologies. However, security is a very important issue in smart homes. For this reason, we propose a secrecy transmission protocol for primary user (PU) by selecting friendly jammer in cognitive IoT model. In particular, a secondary transmitter (ST) is selected to transmit secondary signals by the PU’s frequency spectrum, while another ST is chosen to transmit artificial noise to protect the transmission confidentiality of the PU against eavesdropping. Moreover, two selection schemes are presented to confirm the former and the latter ST, and the goal is to optimize the secondary transmission performance and the primary security performance, respectively. For the non-security model and the proposed protocol, we derive the closed-form expressions of the intercept probability and the outage probability for the PU. We also obtain the closed-form expression of outage probability for the secondary user. The numerical results show that the security performance of the PU is significantly enhanced in our protocol compared to the non-security model. In addition, the outage performance of the secondary users is also improved in high secondary transmit SNR region.
1. Introduction
The Internet of Things (IoT) is an emerging wireless application [1] and has many applications [2,3]. Many techniques for IoT have arisen in recent years such as adaptive monitoring techniques [4,5,6]. Moreover, IoT technologies can implement smart homes, which can improve the quality of life. However, the security and privacy problems are very important in smart homes [7] and have received significant interest [8,9,10,11,12]. Furthermore, combining cognitive radio technique and IoT, Cognitive Internet of Things (CIoT) is proposed, which is an enhanced IoT paradigm. However, the available bandwidth for IoT is very limited. Thus, the spectrum efficiency is a key issue for IoT design [13,14]. To improve the utilization efficiency of radio spectrum, Cognitive Radio (CR) [15] is a promising technology [16]. In Cognitive Radio Networks (CRN), unlicensed users opportunistically access to the licensed spectrum band [17]. Furthermore, unlicensed users cannot harm the performance of primary users. However, since the spectrum access is dynamic and the communication mode is broadcast communication in wireless communication, any unlicensed users and eavesdroppers can have access to the shared spectrum. Therefore, the eavesdroppers readily overhear any active transmissions over wireless networks. However, cognitive radio technology also introduces some new security threats, e.g., using the shared spectrum by selfish behavior, reporting false sensing information, etc. Therefore, ensuring security is a key issue in CIoT.
To ensure security, physical-layer security technology is an effective confidentially protection mechanism [18,19,20,21,22]. In Ref. [23], when the wiretap channel condition between a source node and an eavesdropper node is worse than the channel condition between the source node and the destination node, the source node can successfully communicate with the destination node in perfect secrecy. Ref. [22] emphasized that both the primary users (PUs) and secondary users (SUs) must be defended from eavesdropping in cognitive networks. Specifically, it is legitimate that the SUs are allowed to access the primary spectrum by cooperating with the PUs, where the SUs act as a relay or a friendly jammer to elevate the PU’s secrecy [24]. Some studies [25,26] reveal that resource allocation is an efficient approach to ensure the PU’s security requirement while achieving good transmission performance for the SUs who cooperate with the PUs. In addition, both the secure communications for PUs and SUs are considered in Ref. [25]. In contrast, Refs. [27,28,29] studied some transmission schemes to maximize secrecy rate or to minimize secrecy outage probability for the SUs in the underlay cognitive models, respectively. In addition, the user selection in cooperative transmission is also an efficient method to enhance the security performance for communication systems due to the multiuser gain. The security enhanced technologies of the SUs is investigated with the user selection in Refs. [21,30,31]. However, transmission protocols for improving the secrecy performance of the PUs are barely known. How to design the transmission protocol for protecting the PU’s security requirement remains a crucial issue in cognitive Internet of things model, where home terminal-to-terminal communication coexists with uplink or downlink of the femtocell station.
To improve the primary secrecy performance and secondary outage performance, we employ cooperative jammer and multi-user diversity technology in this paper. Namely, artificial noise is transmitted by selecting a secondary transmitter (ST), which can improve the outage performance of the primary system. Moreover, an ST has access to the primary spectrum if it can improve the outage performance of the secondary performance and satisfy the interference threshold. To encourage the secondary transmitter to act as a friendly jammer, the interference threshold for secondary system is relaxed by primary system in this paper. The main contributions are summarized as follows:
- We propose a ST cooperative transmission protocol by selecting jammer, which transmits an artificial noise to disturb the eavesdropper.
- We propose a selection scheme to determine the friendly jammer and secondary signal transmitter. The ST, which can provide the smallest intercept probability, is chosen as the friendly jammer to transmit artificial noise.
- We derive the closed-form expressions of the intercept probability and the outage probability for the primary system over Rayleigh fading channels, respectively. We also derive the outage probability of the secondary user over Rayleigh channels.
The remainder of the paper is organized as follows. The system model of cooperative jammer selection for primary systems is provided in Section 2. Section 3 analyzes the performances of transmission and security for our proposed protocol. Section 4 provides numerical simulations for the proposed protocol. Section 5 concludes this paper.
Notations: The channels coefficients over links , , , , , , and are denoted by , , , , , , and , respectively. denotes the minimum rate of transmission for primary systems. We also use to denote the minimum rate of transmission for secondary systems. The transmit power of ST and PT are denoted by and , respectively. The expectation of a variable X is denoted by . The probability of a variable X is denoted by .
2. The System Models and the Selection Schemes for STs
In this section, we propose a ST cooperative transmission protocol and a selection scheme to determine the friendly jammer and secondary transmitter. Figure 1b shows The system configuration of our protocols. The system model comprises a primary pair (PS-PD), an eavesdropper (E), a secondary receiver (SR) and K secondary transmitters , where , . In this transmission models, one secondary user is selected as a friendly jammer to interfere with eavesdropping at first, which is denoted by , . The other one has access to the licensed spectrum if the secondary transmission cannot cause an outage over link (PS→PD), which is denoted by , and . However, the transmitted information of primary users can be overheard by the eavesdropper. To prevent eavesdropping, transmits the artificial noise to interfere the eavesdropper. In the proposed model, PD and SR know the information of the artificial noise and the eavesdropper does not know the information. Therefore, PD and SR will not be affected by the artificial noise, which may disturb the eavesdropper. In the proposed protocol, on the one hand, , which provides the most optimal security performance, is selected as a cooperative jammer. On the other hand, if the best outage performance of the secondary system is achieved by selecting a secondary user , and the interference threshold of the primary system is satisfied for the secondary user , then has access to the licensed spectrum. Furthermore, we study two criterions, which are used to select the cooperative jammer and secondary information transmitter, respectively. In addition, we assume that , where . We also assume that noises are Additive White Gaussian Noise (AWGN) with zero mean and variance .
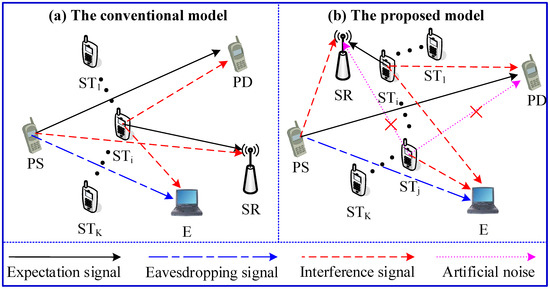
Figure 1.
The system models.
2.1. The System Model Based on the Security Enhancement Approach by Friendly Jammer Selection
To ensure the Quality of Service (QoS) of the primary system, the interference to primary users caused by secondary users must be less than a given threshold (i.e., the interference threshold is satisfied by secondary users). The secondary users have access to the licensed spectrum if they satisfy the above condition. A collection of the secondary transmitters is expressed as S, in which all STs can meet the interference threshold. The transmission process of the proposed protocol is illustrated as follows.
When , the primary signals are transmitted by PS, the artificial noise is transmitted by , but the secondary transmission is interrupted and SR does not work. PD can eliminate perfectly the artificial noise, which leads to a serious threat to the correct reception of the primary signals at E. Thus, the received signals at PD and E in this case are given by
and
where and represent the primary signal and the artificial noise, respectively. Furthermore, normalizing, and . and denote the noises at PS and E, respectively. Hence, the instantaneous capacities of the channel and the channel are given by
and
When , denoting and having , the primary signals, secondary signals and artificial noise are transmitted by PS, and , respectively, in the same spectrum band, where , and . In this case, mutual interferences are aroused between the primary and secondary users. The artificial noise is eliminated perfectly at PD and SR, but leads a serious threat to the correct reception of the primary signals at E. Thus, the received signals at PD, SR and E are given by
and
where is the secondary signal and denotes the noise at SR. Moreover, we assume that . Hence, the capacities of the channels , , and are given by
and
where and . The number of elements in set is denoted by . It is easy to know , and . Hence, if , then the physical-layer secrecy is obtained. If , the secrecy intercept event happens. Its definition refers to [32]. Hence, in wireless systems, the physical-layer security is measured by its probability. Two selection criteria of and are described in detail in the next subsection.
2.2. The Selection Schemes for and
In the multi-users underlay cognitive model, the primary security performance, and the primary and secondary transmission performances are the three most important indicators in system performance analysis. Moreover, the security performance of primary users can be improved effectively since a secondary user acts as a friendly jammer to interfere eavesdropping. By choosing a suitable user as the friendly jammer will further enhance the primary security performance. To optimize the primary physical-layer security performance, a secondary transmitter is selected to serve as a cooperative jammer, we use to denote the secondary transmitter, which can provide the most optimal security for the primary. Thus, the selection criteria of can be written as
where and are calculated by Equations (3) and (4), respectively. In addition, the secondary transmission performance is significantly improved by cooperative rewards that some primary spectrum is released or the value of interference threshold is relaxed for secondary transmission. However, different secondary transmitters have different transmission efficiencies. To maximize the secondary transmission performance, a secondary transmitter is denoted by that satisfies the interference threshold. Moreover, has access to the licensed spectrum if the optimal outage performance of the secondary system is obtained by . The selection criteria for can be written as
where is calculated by Equation (9). Therefore, we focus on the selection of the secondary, which can have access to the primary spectrum and can be the cooperative jammer.
2.3. The Conventional Non-Security Model
As shown in Figure 1a, the system model of the conventional non-security management protocol comprise of a primary pair (PS-PD), an eavesdropper (E), a secondary receiver (SR) and K secondary transmitters (). This conventional model is a typical cognitive underlay system, where STs can have access to the primary spectrum and need to satisfy the interference threshold settled by primary system. Compared with the conventional model, we can see that the received signals at PD and SR and the corresponding instantaneous capacities are identical. In contrast, the received signals at E and the corresponding instantaneous capacities are different. Thus, if , the received signals at E and the corresponding instantaneous capacities are given by
and
If the secondary signal is transmitted over primary spectrum (namely, ), the received signals at E and the corresponding instantaneous capacities are given by
and
3. Performance Analysis
3.1. The Primary Outage Probability for the Proposed Protocols
We use to denote an event, which represents an occurrence of outage of the channel . Hence, if or , the event occurs. Obviously, the secondary transmission may make the event happen when . Thus, we obtain
and
where is given by Equation (3). Since and are i.i.d. exponential distribution with parameters and , respectively, letting and , Equation (18) can be rewritten as
3.2. The Outage Probability of the Secondary System
We use to denote an event, which represents an occurrence of outage of the channel . If , then the event occurs. Therefore, we have
and
Furthermore, and are i.i.d. exponential distribution with parameters and , respectively. Let and , thus Equation (23) can be rewritten as
where . We can see that . Thus, the expression of the outage probability of the secondary system is obtained by substituting Equations (19), (21), (24) and into Equation (22).
3.3. The Intercept Probability of the Primary Transmission
The secrecy intercept event for the primary system is denoted by . Hence, the intercept probability of the primary transmission is equal to the probability of the event occurrence [33]. In addition, the secrecy intercept event occurs when or . Obviously, the event occurs only when . Therefore, we obtain
Moreover, , and are exponential variables with parameters , and , respectively. Let , and . Thus, when , the conditional intercept probability and can be derived as
and
Let , , , , and . Following Equations (A1) and (A9) in Appendix A, the probability density of random variables , and can be written as follows:
and
where , , , , . By using the equalities in Equations (28)–(30), Equations (26) and (27) can be rewritten, respectively, as follows:
and
where , , r is the Euler’s constant. Therefore, the intercept probability of the primary system in proposed protocol is obtained by substituting Equations (19), (21), (31) and (32) into Equation (25).
3.4. The Outage and Intercept Probability for the Conventional No-Security Protocol
Similar to the performance analysis for the proposed protocols, the primary and secondary outage probability and the primary intercept probability are calculated, respectively, as follows:
and
We can see that , . To encourage STs to aid the transmission of artificial noise, we set . Therefore, we also have
where , , and .
4. Numerical Results
The simulation results of the proposed protocols are provided in this section. The systems comprise a primary pair (PS-PD), an eavesdropper (E), a secondary receiver (SR) and K secondary transmitters (). Since the secondary user can serve as cooperative jammer, the primary user relaxes the interference threshold in return, which decreases the minimum achievable rate of primary user . Thus, we set Bit/s/Hz and Bit/s/Hz in the conventional model and the proposed model, respectively. If the parameters are not specified, the simulation parameters are settled as follow: Bit/s/Hz; dB is the average transmit SNR of the primary user. In addition, , , and .
The outage probabilities of the primary user versus in the conventional model and the proposed model are shown as Figure 2, where . The special parameter is the number of STs, which is fixed as . In Figure 2, the outage probability of primary system increases with increase of the secondary SNR. In the same protocol, the primary outage probability decreases with increase of the number of secondary users. This is because the diversity gain increases with increase of the number of secondary users. Furthermore, the outage probability of primary system in our proposed protocol is less than the conventional protocol, which is because that the secondary user is encouraged to serve as friendly jammer, which decreases the interference threshold.
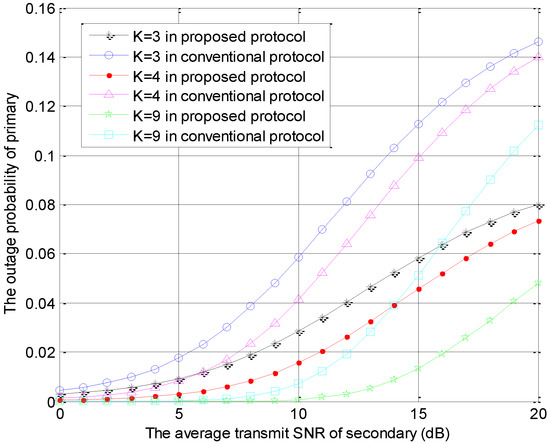
Figure 2.
The outage probabilities of primary users versus with different K values.
The outage probabilities of the secondary user versus are shown in Figure 3, which is generated by using the same parameters as those in Figure 2. In Figure 3, in the same protocol, the secondary outage performances are improved when the number of STs becomes larger. Moreover, the outage probabilities of secondary decrease firstly, and increase with the increase of the average SNR for secondary in the two protocols. Furthermore, the increasing trend is due to that the interference threshold is always not satisfied by secondary user when the SNR of the secondary user is too large. In the small secondary average SNR range, the outage performance of secondary users in the conventional model is better than the performance in the proposed protocol. This performance is mainly determined by the multi-user diversity gain. In this case, the proposed protocol has a lower multi-user diversity gain than the conventional model due to one secondary transmitter acting as the cooperative jammer. In contrast, the proposed protocol can provide a better secondary outage performance in the high secondary average SNR range because the primary user relaxes the interference threshold.
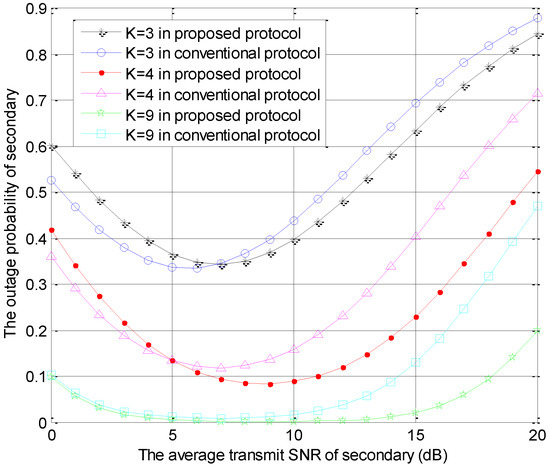
Figure 3.
The outage probability of secondary system versus in the two protocols with different K values.
Figure 4 is generated using the same parameters as those in Figure 2, which shows the intercept probabilities of the primary versus with different number of STs. In Figure 4, the primary security performance is improved significantly in the proposed protocol and is improved slightly in the conventional model as the number of STs becomes larger due to the multi-user diversity gain. Moreover, compared with the conventional protocol, our protocol can provide better primary security performance. The intercept probabilities of the primary system decrease with the increase of in the proposed protocol because the interference from ST to eavesdropper increases with the increase of . However, the intercept probabilities of the primary system decrease firstly and increase with the increase of in the conventional protocol. In the small value range of , the interference threshold is always satisfied, but the interference from ST to eavesdropper increases with the increase of , which causes the decreasing phenomenon. In the large value range of , the interference threshold is hard to satisfy. Thus, the access probability of the secondary transmission decreases and the interference from ST to eavesdropper is reduced with the increase of . This is the cause of the latter increasing phenomenon. These numerical results can also be found in Figure 5, Figure 6 and Figure 7.
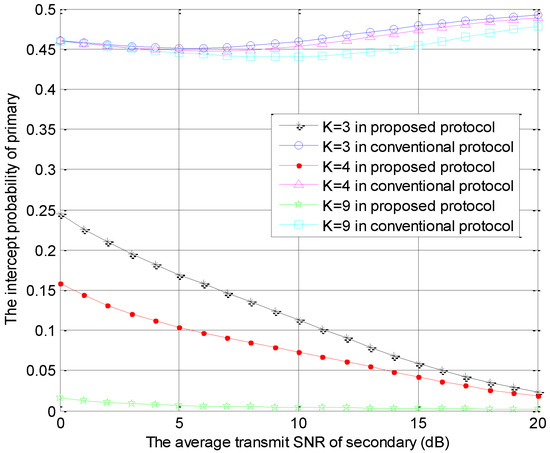
Figure 4.
The intercept probabilities of primary users versus with different K values.
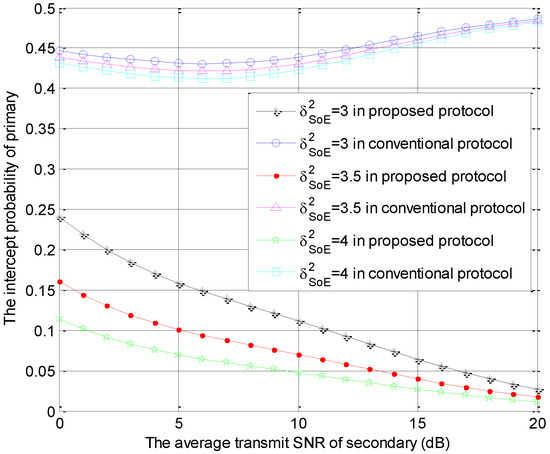
Figure 5.
The intercept probabilities of primary users versus with different values.
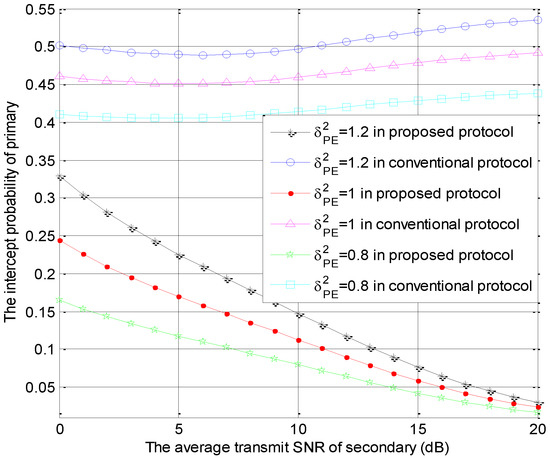
Figure 6.
The intercept probabilities of primary users versus with different values.
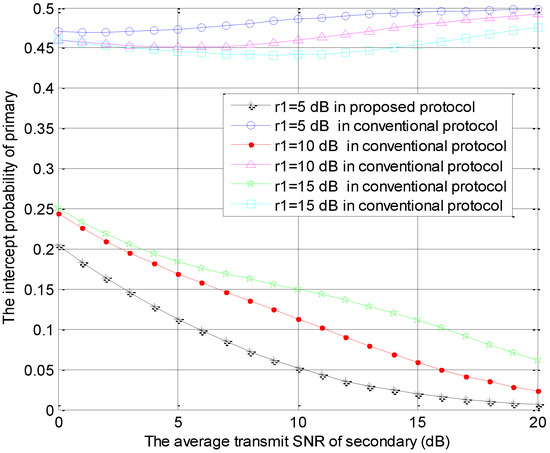
Figure 7.
The intercept probabilities of primary users versus with different values.
The intercept probabilities of primary users versus with different values of are shown in Figure 5. Namely, the special parameter is the channel coefficient , which equals 3, 3.5 or 4. As described in Figure 5, the primary security performance is improved significantly in the proposed protocol and is improved slightly in the conventional model as the value of becomes larger. Compared with the conventional protocol, our protocol can provide the better primary security performance because the larger value of represents the better channel conditions for links . In other words, the interference from to eavesdropper increases with the increase of . In addition, the interference to eavesdropper from is greater than that from . In proposed protocol, both and interfere with the eavesdropping. However, the interference to eavesdropper just comes from in the conventional model and the probability that i is equal to o is .
The intercept probabilities of primary users versus with different values of as shown in Figure 6. Namely, the special parameter is the channel coefficient , which equals to 1.2, 1 or 0.8. In Figure 6, a smaller value of can lead to a good primary security performance in the same protocol because a larger value of represents the better channel conditions for links . In other words, the instantaneous capacity of increases with the increase of . In the proposed protocol with the larger values of , the primary security performance is enhanced significantly in small value range of and is enhanced slightly in large value range of . Compared to the conventional protocol, the proposed protocol can provide the better primary security performance. These numerical results are consistent with those in Figure 4 and Figure 5.
The intercept probabilities of primary users versus with different values of are shown in Figure 7. Namely, the special parameter is the average SNR of the primary user, which is set as , 10 or 15 dB. In Figure 7, the primary security performance in the proposed protocol is improved as the value of becomes larger. On the contrary, the primary security performance in the conventional model is reduced as the value of becomes larger. The valid primary information received by eavesdropper and the interference to eavesdropper are the two main factors related to the security performance of primary system. The more valid primary information is received by the eavesdropper, the worse is primary security performance achieved, and the more interference to he eavesdropper, the greater is primary security performance achieved. In the proposed protocol, the smaller value of causes the less valid primary information received at eavesdropper, so the smaller intercept probability of the primary system is obtained. In the conventional model, the interference threshold is hard to satisfy with the smaller and the interference caused by to eavesdropper is very little, so the larger intercept probability of the primary system is obtained. All of the above numerical results are consistent with the theoretical results in Section 3.
5. Conclusions
In this paper, we have investigated the physical-layer security for a cognitive Internet of things model, which is composed of a primary pair (PS-PD), a secondary receiver (SR), K secondary transmitters and an eavesdropper. To protect the information of primary users against eavesdropping, we have proposed the ST cooperative jammer selection transmission protocol. In return, for the cooperation of , interference threshold for secondary user is relaxed by the primary system compared with the non-security management model. When this interference threshold is satisfied and the best outage performance of secondary users is obtained by selecting , then the secondary user has access to the licensed spectrum. Due to the cooperation of , the security performance of primary users are enhanced. Due to the cooperation of and the selection of , the outage performance of secondary users are enhanced in high secondary transmit SNR region. Furthermore, the intercept probability and outage probability of the primary system have been derived. The outage probability of the secondary system has also been obtained. For comparison purposes, the conventional non-security management was also investigated as a baseline. The numerical results have shown that our protocol has better primary secrecy performance than the non-security management model. In addition, the proposed protocol also has better secondary and primary transmission performance than the conventional model.
Author Contributions
Conceptualization, P.X., L.X., H.W., and I.Y. Formal analysis: P.X. and L.X. Funding acquisition: P.X. and I.Y. Investigation: P.X., L.X., J.T.S., and I.Y. Methodology: P.X., L.X., and I.Y. Performance evaluation: P.X., H.W., and J.T.S. Case study: H.W. and J.T.S. Supervision: P.X. and I.Y. Validation: P.X., L.X., H.W., J.T.S., and I.Y. Visualization: P.X. and L.X. Writing, original draft: P.X., L.X., H.W., J.T.S., and I.Y. Writing, review and editing: P.X., L.X., J.T.S., and I.Y.
Funding
This work was supported by the National Natural Science Foundation of China (NSFC) under Grants No. 61801171 and the Soonchunhyang University Research Fund.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Let , , and be exponentially variables with parameters , , , and , respectively. Let , , , , and . Since
we have
From Equation (34), we have
Therefore, we obtain
Similar to the derivation of the probability density of , the probability density of random variables can obtained by
In addition, since
we have
From Equation (A7), we have
Thus, we obtain
References
- Wu, Q.; Ding, G.; Xu, Y.; Feng, S.; Du, Z.; Wang, J.; Long, K. Cognitive Internet of Things: A New Paradigm Beyond Connection. IEEE Internet Things J. 2014, 1, 129–142. [Google Scholar] [CrossRef]
- Song, F.; Ai, Z.; Li, J.; Pau, G.; Collotta, M.; You, I.; Zhang, H. Smart collaborative caching for Information-centric IoT in fog computing. Sensors 2017, 17, 2512. [Google Scholar] [CrossRef] [PubMed]
- Ai, Z.; Liu, Y.; Song, F.; Zhang, H. A smart collaborative charging algorithm for mobile power distribution in 5G networks. IEEE Access 2018, 6, 28668–28679. [Google Scholar] [CrossRef]
- Trihinas, D.; Pallis, G.; Dikaiakos, M. Low-Cost Adaptive Monitoring Techniques for the Internet of Things. IEEE Trans. Serv. Comput. 2018, 99, 1. [Google Scholar] [CrossRef]
- Trihinas, D.; Pallis, G.; Dikaiakos, M. ADMin: Adaptive Monitoring Dissemination for the Internet of Things. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Tata, S.; Mohamed, M.; Megahed, A. An Optimization Approach for Adaptive Monitoring in IoT Environments. In Proceedings of the 2017 IEEE International Conference on Services Computing (SCC), Honolulu, HI, USA, 25–30 June 2017; pp. 378–385. [Google Scholar]
- Lee, Y.-T.; Hsiao, W.-H.; Lin, Y.-S.; Chou, S.-C.T. Privacy-Preserving Data Analytics in Cloud-Based Smart Home with Community Hierarchy. IEEE Trans. Consum. Electron. 2017, 63, 200–207. [Google Scholar] [CrossRef]
- Song, F.; Zhou, Y.; Wang, Y.; Zhao, T.; You, I.; Zhang, H. Smart Collaborative Distribution for Privacy Enhancement in Moving Target Defense. Inf. Sci. 2018. [Google Scholar] [CrossRef]
- Ai, Z.; Zhou, Y.; Song, F. A Smart Collaborative Routing Protocol for Reliable Data Diffusion in IoT. Sensors 2017, 18, 1926. [Google Scholar] [CrossRef]
- Uchida, N.; Takeuchi, S.; Ishida, T.; Shibata, Y. Mobile traffic accident prevention system based on chronological changes of wireless signals and sensors. J. Wirel. Netw. Ubiquitous Comput. Dependable Appl. 2017, 8, 57–66. [Google Scholar]
- Kotenko, I.; Saenko, I.; Branitskiy, A. Applying Big Data Processing and Machine Learning Methods for Mobile Internet of Things Security Monitoring. J. Internet Serv. Inf. Secur. 2017, 8, 54–63. [Google Scholar]
- Kotenko, I.; Saenko, I.; Kushnerevich, A. Parallel big data processing for security monitoring in Internet of Things networks. J. Wirel. Netw. Ubiquitous Comput. Dependable Appl. 2018, 8, 60–74. [Google Scholar]
- Afza, A.; Zaidi, S.A.R.; Shakir, M.Z.; Imran, M.A.; Ghogho, M. The Cognitive Internet of Things: A Unified Perspective. IEEE Mob. Netw. Appl. 2015, 20, 72–85. [Google Scholar] [CrossRef]
- Jackson, D.; Zang, W.; Gu, Q.; Yu, M. Robust detection of rogue signals in cooperative spectrum sensing. J. Internet Serv. Inf. Secur. 2015, 5, 4–23. [Google Scholar]
- Mitola, J. Cognitive Radio: An Integrated Agent Architecture for Software Defined Radio. Ph.D. Thesis, KTH Royal Institute of Technol, Stockholm, Sweden, December 2000. [Google Scholar]
- Haykin, S. Cognitive radio: Brain-empowered wireless communications. IEEE J. Sel. Areas Commun. 2005, 23, 201–220. [Google Scholar] [CrossRef]
- Goldsmith, A.; Jafar, S.; Maric, I.; Srinivasa, S. Breaking spectrum gridlock with cognitive radios: An information theoretic perspective. Proc. IEEE 2009, 97, 894–914. [Google Scholar] [CrossRef]
- Rajesh, K.S.; Danda, B.R. Advances on Security Threats and Countermeasures for Cognitive Radio Networks: A Survey. IEEE Commun. Surv. Tutor. 2015, 17, 1023–1043. [Google Scholar]
- Li, J.; Feng, Z.; Feng, Z.; Zhang, P. A Survey of Security Issues in Cognitive Radio Networks. IEEE J. Mag. China Commun. 2015, 12, 132–150. [Google Scholar] [CrossRef]
- Nguyen, V.D.; Hoang, T.M.; Shin, O.S. Secrecy capacity of the primary system in a cognitive radio network. IEEE Trans. Veh. Technol. 2015, 64, 3834–38435. [Google Scholar] [CrossRef]
- Yulong, Z.; Xianbin, W.; Weiming, S. Physical-Layer Security with Multiuser Scheduling in Cognitive Radio Networks. IEEE Trans. Commun. 2013, 61, 5103–5113. [Google Scholar]
- Zhihui, S.; Yi, Q.; Song, C. On physical layer security for cognitive radio networks. IEEE Netw. 2013, 27, 28–33. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Zhang, N.; Lu, N.; Cheng, N.; Mark, J.W.; Shen, X.S. Cooperative spectrum access towards secure information transfer for CRNs. IEEE J. Sel. Areas Commun. 2013, 31, 2453–2464. [Google Scholar] [CrossRef]
- Mokari, N.; Parsaeefard, S.; Saeedi, H.; Azmi, P. Cooperative secure resource allocation in cognitive radio networks with guaranteed secrecy rate for primary users. IEEE Trans. Wirel. Commun. 2014, 13, 1058–1073. [Google Scholar] [CrossRef]
- Xu, D.; Li, Q. Resource allocation for cognitive radio with primary user secrecy outage constraint. IEEE Syst. J. 2018, 12, 893–904. [Google Scholar] [CrossRef]
- Wang, C.; Wang, H.-M. On the secrecy throughput maximization for MISO cognitive radio network in slow fading channels. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1814–1827. [Google Scholar] [CrossRef]
- Nguyen, V.-D.; Duong, T.Q.; Dobre, O.A.; Shin, O.-S. Joint information and jamming beamforming for secrecy rate maximization in cognitive radio networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2609–2623. [Google Scholar] [CrossRef]
- Elkashlan, M.; Wang, L.; Duong, T.Q.; Karagiannidis, G.K.; Nallanathan, A. On the security of cognitive radio networks. IEEE Trans. Veh. Technol. 2015, 64, 3790–3795. [Google Scholar] [CrossRef]
- Yang, L.; Jiang, H.; Vorobyov, S.A.; Chen, J.; Zhang, H. Secure communications in underlay cognitive radio networks: User scheduling and performance analysis. IEEE Commun. Lett. 2016, 20, 1191–1194. [Google Scholar] [CrossRef]
- Zou, Y. Physical-layer security for spectrum sharing systems. IEEE Trans. Wirel. Commun. 2017, 16, 1319–1329. [Google Scholar] [CrossRef]
- Pei, Y.; Liang, Y.-C.; Teh, K.C.; Li, K. Secure communication in multiantenna cognitive radio networks with imperfect channel state information. IEEE Trans. Signal Process. 2011, 59, 1683–1693. [Google Scholar] [CrossRef]
- Wang, Z.; Xiao, M.; Skoglund, M.; Poor, H.V. Secure degrees of freedom of wireless networks using artificial noise alignment. IEEE Trans. Commun. 2015, 63, 2632–2646. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).