Abstract
Simultaneous ascending auctions find extensive applications in spectrum licensing and advertising space allocation. However, existing quantum sealed-bid auction protocols suffer from dual limitations: they cannot support multi-item simultaneous bidding scenarios, and their reliance on complex quantum resources along with requiring full quantum operational capabilities from bidders fails to accommodate practical constraints of quantum resource-limited users. To address these challenges, this paper proposes a multi-party semi-quantum simultaneous ascending auction protocol based on single-particle states. The protocol employs a trusted honest third party (HTP) responsible for quantum state generation, distribution, and security verification. Bidders determine their groups through quantum measurements and privately encode their bid vectors. Upon successful HTP authentication, each bidder obtains a unique identity code. During the bidding phase, HTP dynamically updates quantum sequences, allowing bidders to submit bids for multiple items by performing only simple unitary operations. HTP announces the highest bid for each item in real time and iteratively generates auction sequences until no new highest bid emerges, thereby achieving simultaneous ascending auctions for multiple items. It acts as a quantum-secured signaling layer, ensuring unconditional security for bid transmission and identity verification while maintaining classical auction logic. Quantum circuit simulations validate the protocol’s feasibility with current technology while satisfying critical security requirements, including anonymity, verifiability, non-repudiation, and privacy preservation. It provides a scalable semi-quantum auction solution for resource-constrained scenarios.
1. Introduction
Quantum cryptography, a key subfield of quantum information science, combines quantum-mechanical principles with classical cryptography. It has achieved major advances in protocol design and implementation, including Quantum Key Distribution (QKD) [1,2], Quantum Secure Direct Communication (QSDC) [3,4], and Quantum Secret Sharing (QSS) [5,6]. These technologies are increasingly deployed in practice, such as quantum voting systems [7] and quantum transaction platforms, offering new models for secure applications.
Auctions are fundamental mechanisms for resource allocation and trading [8,9,10]. By information transparency and bidding rules, they can be categorized into open-cry and sealed-bid formats [11]. English and Dutch auctions are open-cry, with real-time price discovery. Sealed-bid auctions require bidders to submit offers independently and confidentially, which better preserves strategy privacy and suits anonymity-sensitive scenarios.
However, conventional sealed-bid mechanisms rely on computational assumptions in classical cryptography (e.g., integer factorization and discrete logarithms). With rapid progress in quantum computing [12,13], Shor’s algorithm solves these problems in polynomial time [14] and Grover’s algorithm speeds up search [15], exposing sealed-bid systems to quantum attacks [16]. This motivates security protocols grounded in physical principles.
Unlike classical schemes that offer computational security, quantum cryptographic protocols provide information-theoretic security (or unconditional security). This ensures that encrypted data remains secure even against adversaries with unlimited computing power, guaranteeing forward secrecy. In the context of auctions, this prevents historical bid data from being decrypted retroactively once powerful quantum computers become available. It is important to clarify that our proposed protocol serves as a quantum-secured signaling layer. It utilizes quantum mechanics to secure the transmission of bids and verify identities, while the underlying auction allocation logic (comparing bids and determining winners) follows the classical simultaneous ascending auction mechanism.
Against this backdrop, research on quantum sealed-bid auction (QSA) protocols has grown rapidly. The goal is to design quantum-resilient mechanisms that ensure fairness, preserve privacy, and enhance security.
The conceptual framework of quantum auctions was introduced in 2008 [17]. In 2009, Naseri [18] proposed a GHZ-based QSA enabling secure multi-party bid transmission. That scheme resisted only external attacks and was vulnerable internally. Follow-up work refined designs and security analyses. Qin et al. [19] and Yang et al. [20] exposed attacks via double CNOT and pseudo-entangled states; their fixes did not consider a dishonest auction center. In 2010, Zhao et al. [21] added post-confirmation to mitigate collusion, later refined for partial collusion. In 2014, Liu et al. [22] integrated QKD for bid encryption and hash-based confirmation. In 2016, they proposed a single-particle QSBA [23], reducing quantum resources, but Zhang et al. [24] showed coordinated attacks remained. Recent advances include QFT- and d-dimensional-state protocols [25], an anonymous QSA via the Chinese Remainder Theorem [26], and an auctioneer-free scheme with Bell-state swapping [27]. Semi-quantum secure multi-party summation (SQSMS) [28,29,30,31,32,33] has also gained attention due to its compatibility with users of varying quantum capabilities.
Despite these advancements, existing QSA research faces two primary “shortages”: (1) Capability Shortage—most protocols require fully quantum-capable participants, which is impractical for general users. (2) Functional Shortage: Most studies focus on single-item sealed-bid auctions, failing to address the complexity of simultaneous ascending auctions for multiple items. To address this, we combine Milgrom’s simultaneous ascending auction theory [34] with a semi-quantum design and propose a quantum simultaneous ascending auction (QSAA) framework that supports users with diverse capabilities. Under capability constraints, semi-quantum bidders obtain unique identity codes from an honest, fully quantum third party (HTP) and submit bids using simple unitary operations. The protocol preserves anonymity, privacy, fairness, verifiability, and non-repudiation: only HTP learns bids; sealed bids are disclosed simultaneously; bidders cannot repudiate submitted bids and HTP cannot deny receipts.
The remainder of this paper is organized as follows: Section 2 introduces the fundamental concepts of simultaneous ascending auction mechanisms and semi-quantum protocols. Section 3 elaborates on a multi-party semi-quantum simultaneous ascending auction protocol in detail. Section 4 presents simulation analyses. Section 5 provides performance evaluations. Finally, Section 6 concludes the paper.
2. Preliminaries
Our protocol enables anonymous auctions for users with limited quantum capabilities. The semi-quantum simultaneous ascending auction (SQSAA) assigns each bidder a unique identity code. Bidders apply unitary operations to encode bid prices onto quantum sequences, implementing a simultaneous ascending-price auction. We first introduce the auction mechanism and the semi-quantum model used in this paper.
2.1. Simultaneous Ascending Auction Mechanism
The simultaneous ascending-price auction is a multi-item dynamic mechanism widely used in spectrum licensing and advertisement allocation. Its core characteristics include simultaneous bidding for multiple items, round-by-round price increments, and a public bidding process. In each round, bidders may raise bids on any items. After each round, each item’s price updates to the highest bid received. The process repeats until no further bids are submitted, and items are allocated to the highest bidders at their final prices.
2.2. Semi-Quantum Protocol Architecture and Trust Model
The semi-quantum architecture involves two types of users:
Quantum Users (HTP)—the honest third party (HTP) possesses full quantum capabilities (preparation, manipulation, and measurement). Assumption: In this semi-quantum model, the HTP is assumed to be a trusted authority. The HTP generates and measures states correctly and does not collude with bidders to reveal bids to others, although the HTP itself learns the bid values.
Semi-Quantum Users (Bidders): Participants with constrained quantum capabilities, typically limited to Z-basis or X-basis measurements (computational or Fourier bases), applying simple unitary operations, and reflecting received quantum states. This design reduces hardware complexity and cost.
2.3. Protocol Characteristics
The semi-quantum design offers two practical advantages [30]:
System compatibility—basic quantum operations can be implemented using low-cost optical components. When devices malfunction, systems can fall back to a semi-quantum mode, enhancing robustness and easing the transition from classical to quantum infrastructures.
Cost efficiency: Limiting some users’ quantum capabilities reduces dependence on expensive quantum resources and large-scale quantum memory processing, enabling economically viable deployment during the current transitional phase.
3. Multi-Party Semi-Quantum Simultaneous Ascending Auction Protocol
Assume an honest third party (HTP) with full quantum capability acts as the auction coordinator and never colludes with bidders. There are n semi-quantum participants who serve as bidders with restricted capabilities: computational-basis or Fourier-basis measurement, simple unitary operations, and reflection. Each bidder independently generates a private randomized identity vector satisfying These vectors serve as cryptographic identity anchors, dynamically integrated into quantum state manipulations through controlled unitary operations.
The protocol has four phases: initialization, identity encoding distribution, bidding, and result announcement. In initialization, HTP constructs differentiated quantum sequences for each bidder and collaborates with to validate channel security. In identity encoding distribution, each bidder generates a private identity vector, applies unitary operations to assigned particles, HTP constructs a verification matrix, and validates integrity against predefined rules. In bidding, each bidder applies unitary operations to encode bids and computes a commitment. In the result announcement, HTP determines the highest bid and bidder per item, and others verify using commitments. The schematic diagram of the protocol is shown in Figure 1.
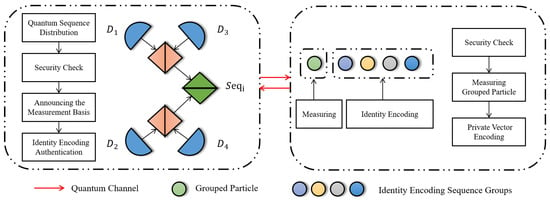
Figure 1.
Workflow of identity encoding distribution and verification at HTP. (Lateral diagrams correspond to Step 4 and 5).
3.1. Initialization Phase
Step 1: HTP and each authorized bidder pre-share an authenticated key sequence . * Note: These keys are distributed via a secure classical channel or a prior standard QKD session before the auction begins. If keys are compromised, the authentication fails; thus, key refreshment is recommended for subsequent sessions. * HTP randomly prepares rotation-basis particles and m decoy particles for each bidder. According to , HTP determines the embedding order of decoy and rotation particles in the quantum sequence, using (1) if = 0, a rotational particle is inserted into the sequence. (2) If = 1, a decoy particle is embedded instead. HTP then produces a quantum sequence of length . Repeating this for all bidders yields n sequences , which HTP sends over authenticated quantum channels.
Step 2: Upon receiving , bidder routes each particle according to : If , directly reflects the particle to HTP; if , retains the particle for Step 4.
Step 3: HTP measures the reflected particles using the preparation bases indicated by and computes the quantum bit error rate (QBER) by comparing outcomes with prepared states. If QBER exceeds a threshold , the protocol aborts; otherwise it proceeds. Threshold Selection: The threshold is not arbitrary; it is selected based on standard security proofs for BB84-type protocols. To tolerate environmental noise while securely detecting intercept-resend attacks (which theoretically induce error), is typically set strictly below the coherent attack bound (approx. 11%), for example, in the range of 5–8% in practical scenarios.
3.2. Identity Encoding Distribution Phase
Step 4: After eavesdropping detection, each discards decoy particles and keeps rotation particles. HTP designates the first rotation particle as the grouping particle and publishes its measurement basis on the bulletin board. HTP records initial states and counts bidders per group. Each measures the grouping particle according to determine its group: outcomes map to groups 1–4.
Step 5: Each generates a private n-dimensional vector , then applies unitary operations to assigned particles according to: (1) if = 0, it applies the Pauli-I operation () to the rotational particle. (2) If = 1, it performs the Pauli-Y operation () on the rotational particle.
Afterward, sends the updated sequence to HTP.
Step 6: Upon receiving from all bidders, HTP determines each bidder’s group from and the grouping particles, then measures each particle in the corresponding basis to form a mapping (Table 1). For both computational and Fourier bases, record if the outcome flips relative to the initial state; otherwise, set .

Table 1.
Initial states and mapping results.
After constructing the matrix from of the quantum sequences returned by bidders, HTP checks the Hamming weight of each valid column. Identity encoding distribution succeeds iff, for every valid column j,
and the number of bidders within each group matches HTP’s initial records. Liveness and Restart: If this condition is not met (e.g., column sum ) or if the number of bidders in a group mismatches the record (group collision), HTP broadcasts a “Restart” signal. The current round is discarded, and the Identity Encoding Phase repeats from Step 1. This ensures the protocol remains live and reaches a valid distribution state. Columns with no embedded identity encoding are excluded from verification.
3.3. Bidding Phase
Step 7: Completing these operations, each bidder obtains a unique identity code. Repeating Steps 1–3, HTP generates a new quantum sequence and new for each round r. In each sequence, the first particles encode identity (2 group particles followed by n identity particles). For item w with domain , the next particles encode the bid.
Step 8: Assuming HTP specifies that the initial bid range for the w-th auctioned item lies within . HTP broadcasts the valid bidding range and specifies the required bit-length for the bid vector. This ensures all bidders encode their bids using a consistent quantum sequence length. Each bidder converts their bid into a corresponding private bid binary sequence .
Each bidder first encodes their identity sequence. Based on the grouping of particles, the first two particles encode the group identifier, with the conventions 00, 01, 10, and 11 designating the first, second, third and fourth groups, respectively. For example, for group 2 (01), apply I to the first qubit and H to the second. The subsequent n particles encode the private identity code.
For all items, bits are encoded from most significant to least significant (left to right in the vector, applied right to left on qubits as specified in Step 9).
Step 9: The bidder applies the Hadamard, Pauli-Y and Pauli-I operations to the first two particles and encodes their identity vector. Subsequently, they encode their private bid binary sequence (where ) onto the specific bid particle sequence from right to left. If = 0, performs the operation; if = 1, applies the operation. Otherwise (if no bid is intended), the bidder performs no operations on any particles in the specific bid particle sequence. Then, returns the newly processed particle sequence to HTP, particle by particle. It is noteworthy that for multiple auction items, the initial-round bidding prices are encoded in the particle sequence following the first auctioned item. Correspondingly, the particle count of is augmented according to the same rule established for the first item.
Step 10: Concurrently, in each round, each bidder computes a binding, hiding commitment to their bid for each item using a collision-resistant hash function . Let be a per-round random nonce. Define where is the bidder’s decimal bid for item w in that round, and ∥ denotes concatenation. HTP records for each bidder and item per round. Any bid update must include a fresh commitment.
3.4. Result Announcement Phase
Step 11: After receiving the quantum sequences from all bidders, HTP first constructs a mapping result matrix according to the identity encoding distribution rules and verifies each bidder’s identity encoding sequence. Subsequently, HTP measures the first two particles using the following rules. When the Pauli-I operation is applied to a qubit, the HTP measures it in the same basis as its initial state. Conversely, when the Hadamard operation is applied, measurement occurs in the conjugate basis relative to the initial state.
Taking as an example, its identity code is Group 2, Number 3. The unitary operation for its group particles consists of applying the Pauli-I operation to the first particle and the Hadamard operation to the second particle. The HTP measures the first particle using the same measurement basis as its initial state. Regardless of the initial state, if the measurement outcome matches the initial state, the HTP calculates the mapping result of the first particle as 0. For the second particle, the HTP employs the measurement basis orthogonal to the initial state: if the initial state is or , the measurement outcome will be or ; conversely, if the initial state is or , the measurement outcome will be or . In this case, the HTP calculates the mapping result of the second particle as 1, as illustrated in the diagram. Please refer to Table 2 for detailed information.

Table 2.
Group mapping measurement and mapping results.
Then, HTP measures the specific bid particle sequence from right to left using the corresponding basis, recording each outcome : if the measurement result is opposite to the initial state, it is recorded as = 1; otherwise, = 0. Finally, HTP arranges all specific bid results , converts the bits to a decimal bid, selects the highest first-round bid, and publishes it on the bulletin board (or via a classical channel).
Step 12: After completing initial bidding for all auctioned items, bidders collectively negotiate the bid increment range for subsequent rounds.Specifically, suppose they determine the starting price for each new round as 10% of the previous round’s highest bid for that item, . Then, they repeat Steps 7–10 for the next round. Upon receiving quantum sequences, HTP executes Step 11.
If a bid does not exceed the current highest bid, HTP withholds updates. The auction concludes when no item receives a higher bid; HTP then publishes all final highest bids.
Step 13: Assume bidder is the highest bidder for item w. He discloses and , enabling others to recompute and check it matches the recorded commitment. If ’s commitment is validated by all bidders and HTP, he is confirmed as the highest bidder; otherwise, verification fails. If any bidder () claims their bid exceeds HTP’s published highest bid or , broadcasts a complaint and discloses for verification. Successful verification mandates HTP to update the item’s highest bid; failed verification maintains the current highest bid. HTP declares the winner for item w only when no valid complaints are substantiated (Figure 2).
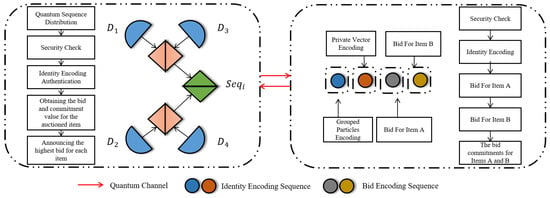
Figure 2.
Overall simultaneous ascending auction workflow with identity and bid encoding.
4. Simulation of the Proposed Protocol
The Qiskit simulation presented here aims to validate the correctness of the quantum physical layer—specifically the single-particle encoding, decoding, and noise robustness—rather than to simulate the classical arithmetic logic of the auctioneer.
We illustrate the protocol with Qiskit simulations in two phases: multi-party semi-quantum identity encoding distribution and multi-party semi-quantum simultaneous ascending auction. Consider an HTP coordinating three semi-quantum bidders . Bidders independently sample private vectors .
4.1. Multi-Party Semi-Quantum Identity Encoding Distribution
Assume at this stage, HTP allocates distinct key sequences to bidders respectively, where
Step 1: HTP randomly generates rotation particles and decoy particles from BB84 state . According to the rules specified in the aforementioned protocol, the quantum sequences , and are formed in Table 3. The quantum circuit diagram for is illustrated in Figure 3 according to the aforementioned conditions. In this simulation, we employ a decoy state ratio of approximately 50% (1:1 with rotation particles) to maximize statistical detection sensitivity for the case study.

Table 3.
Example construction of sequences based on keys and BB84 states.
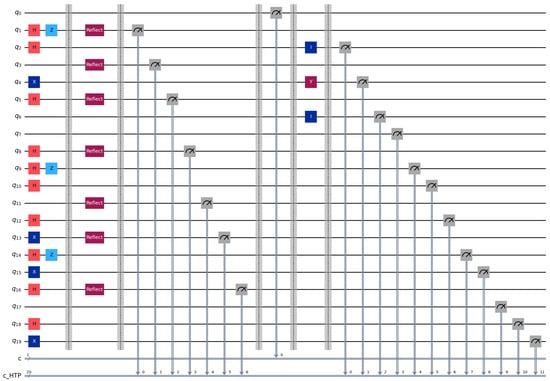
Figure 3.
Circuit for identity encoding distribution using BB84 single-qubit states.
Step 2: Each bidder routes particles according to . reflects decoy particles and retains rotation particles. HTP measures reflected particles in the corresponding bases and computes QBER. For example, in the particles at positions 2, 4, 6, 9, 12, 14, and 17 are reflected (Figure 4). If the error rate is below the threshold, the protocol proceeds (Figure 5).
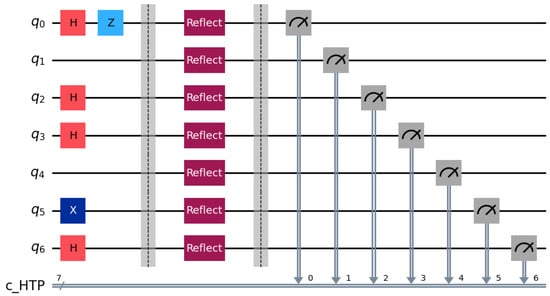
Figure 4.
Decoy particle reflection and QBER estimation circuit used for channel checking.
Figure 5.
Example of positions reflected by bidder for decoy checking according to .
Step 3: HTP publishes (or broadcasts via classical channel) the measurement basis for the first rotation particle on the bulletin board while recording the number of bidders in each group. Bidders measure the first particle in their respective rotation particle sequences , and using the announced basis. Taking as an example: when the first particle in its rotation sequence is ∣0⟩ (Figure 6) and the computational basis measurement yields 0, is assigned to Group 1. Similarly, and are assigned to Group 2 and Group 3, respectively. These grouping results are consistent with the HTP’s recorded data. Then, Bidder performs unitary operations on positions 2–4 of its rotation particle sequence: specifically applying the operation to the 3rd position and the operation to positions 2 and 4, while leaving other particles unchanged (Figure 7). Afterward, sends to HTP. Following the same rules, and execute their designated unitary operations and send their sequences and to HTP.
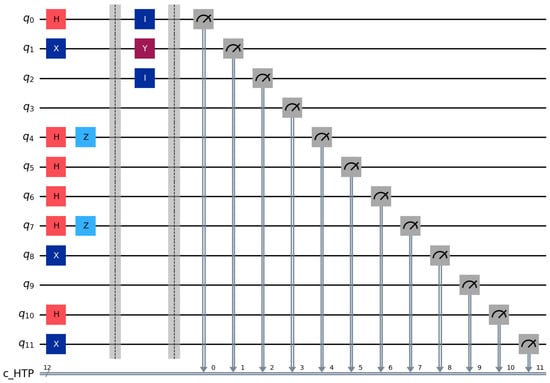
Figure 6.
Circuit example of rotation-basis particle operations for identity and bid encoding.
Figure 7.
Grouping via the first rotation particle and unitary operations per group.
Step 4: Upon receiving the modified quantum sequences , and from bidders , and , HTP performs sequential measurements on each qubit of the sequences using the measurement basis corresponding to each bidder’s group assignment. The mapping results are organized into a matrix M, where each row represents a bidder’s sequence and each column corresponds to a specific qubit position.
The per-column Hamming weights (column sums) are (0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0). For every valid column, the sum equals 1; therefore, bidders , and are assigned the identity designations Group 1 Member 2, Group 2 Member 3, and Group 3 Member 5, respectively, satisfying the predefined condition. Thus, the identity code distribution is successful without repetition (see Figure 8).
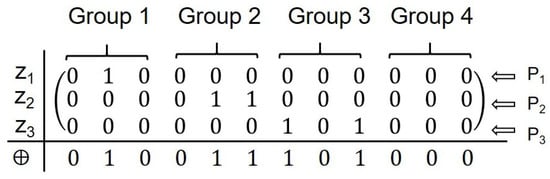
Figure 8.
Mapping results arranged into a matrix for identity verification.
4.2. Multi-Party Semi-Quantum Simultaneous Ascending Auction
In this stage, all bidders simultaneously place bids on both auction items, A and B (though the protocol permits optional single-item bidding). For demonstration clarity, we assume single-round auction completion. Suppose the initial price ranges for items A and B in the first-round auction are [0, 8] and [0, 10], respectively, with a bid increment benchmark of 10% per round. In the first round, bidders , and submit their initial bids for item A as (4, 7, 5) and for item B as (7, 7, 9). All bidders reveal their true maximum willingness-to-pay (i.e., their psychological reserve prices) in the first round, implying that no bidders will revise their bids in subsequent auction rounds.
Step 1: HTP initializes the protocol by assigning distinct key sequences to bidders respectively, where
Then, HTP randomly generates quantum sequences , and according to the rules of Step 1,where
Step 2: Following the aforementioned rules, we conduct channel security eavesdropping detection by referencing the case study from Simulation Experiment 4.1.
Step 3: According to the established rules, bidders , and perform group encoding operations on particles located at the first and second positions of the sequence, simultaneously executing identity encoding utilizing private vectors at positions 3 through 5.
As demonstrated in Simulation Experiment 4.1, the bidder was assigned the identity code “Group 1, Member 2” (with group encoding 00). Given ’s private vector (0, 1, 0), the identity encoding is implemented on qubits 1–5 through quantum operations: implements operations on the first and second particles within their respective rotational particle; the operation is applied to the 4th qubit and operations are maintained on qubits 3 and 5. Following the same rules, bidders and subsequently execute their respective unitary operations in accordance with their allocated group codes and private vectors.
Step 4:, and convert the decimal bid value of item A into corresponding binary sequences (0, 1, 0, 0), (0, 1, 1, 1) and (0, 1, 0, 1). Concurrently, specific bid particle encoding is implemented at positions 6–9 to comprehensively embed auction information.
Taking bidder as an example, implement unitary operations on the rotational particle. Specifically, the operation is applied at positions 7, 11, 12, and 13, while the operation is performed at positions 6, 8, 9, and 10. Then, sends to HTP. Following the same procedure, bidders and perform their corresponding quantum operations and return and to HTP.
Step 5: In accordance with the established rules, HTP constructs a identity verification matrix (0, 0, 0, 1, 0), which matches the identity encoding assigned in Simulation Experiment 4.1. Subsequently, HTP conducts the following operations: (1) Using the same measurement basis as the initial state, HTP measures qubits 6–13 of , obtaining a matrix (0, 1, 0, 0, 0, 1, 1, 1) (Figure 9). The auction prices for items A and B are derived from their respective quantum sequences. When converted to decimal notation, these sequences yield the values 4 for A and 7 for B. The same verification procedure is applied to and , revealing bids of (7, 7) and (5, 9) from and , respectively, for item A and B.
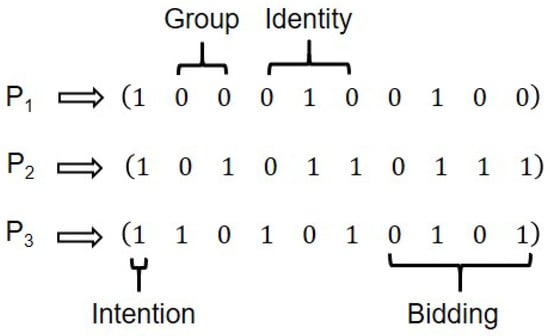
Figure 9.
Recovered bid bits per item and round at HTP and highest-bid update.
(2) HTP announces the highest bid for item A in the first auction round as 7 on the public bulletin board. Item B yields respective bids of 7, 7 and 9 from , and , with the highest bid of 9 being similarly published. (3) Bidders , and each generate hash commitments for their bids on items A and B according to Step 10. For example, for item A with bid 7, bidder samples a random nonce and computes which is recorded by HTP.
Step 6: According to the auction rules, the starting prices for items A and B in the second round are set to 7.7 and 9.9, respectively, calculated as . Subsequently, HTP and bidders , and repeat Steps 1–5 of the protocol. During Step 5, the bid matrices derived from the quantum sequences returned by the bidders to HTP are all (0, 0, 0, 0), indicating no new highest bids for either item. Next, the highest bidders for items A and B disclose their random numbers and commitment values to HTP and other bidders. Other bidders validate the commitment values, and HTP verifies both the commitment values and identity encodings.
If all verifications pass and no complaints are raised, HTP officially declares the highest bids for items A and B are 7 and 9, respectively. The winning bidders are Group 2 Member 3 for item A and Group 3 Member 5 for item B. The auction concludes upon this announcement.
5. Performance Analysis
We evaluate the proposed SQSAA protocol in terms of security, anonymity, verifiability, non-repudiation, and secrecy capacity.
5.1. External Attacks on Security
To obtain bidders’ secrets, an eavesdropper Eve may attempt intercept–resend, measure–resend, or Trojan-horse attacks.
5.1.1. Intercept-Resend Attack
In Step 1 or Step 7, Eve may intercept the quantum sequence or transmitted from HTP to , insert an equivalent number of single particles, and subsequently forward the altered quantum sequence to . Through this method, might encode the confidential information (identity codes or bidding information) onto these tampered particles. Eve then intercepts again the quantum sequence or sent from to HTP and obtains the identity codes or bidding information. It is noteworthy that the intercepted sequences or contain decoy particles, with the probability of Eve’s fake particles matching the decoy particles being . Without loss of generality, assuming the decoy particles prepared by HTP are in the ∣0⟩ state, the detection probabilities for Eve’s fake particles are presented in Table 4.

Table 4.
Measurement results and probabilities of fake particles.
Therefore, if the decoy particle is in the ∣+⟩ state and HTP measures in the Fourier basis, the probability of detecting Eve is
Similarly, we can compute that the non-detection probabilities for ∣−⟩, ∣0⟩, and ∣1⟩ are all .
In summary, the probability that HTP detects Eve’s attack is given by
where w represents the number of decoy particles (see Figure 10).
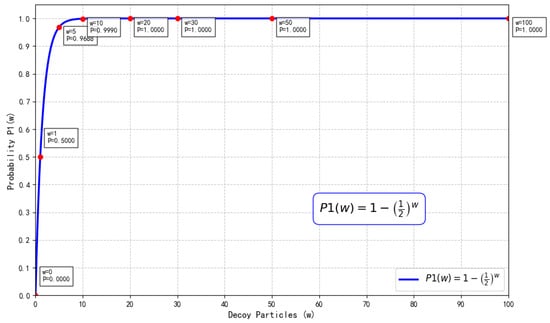
Figure 10.
Detection probability versus number of decoy particles w under intercept-resend.
Consequently, Eve’s intercept-resend attack introduces an error rate in the eavesdropping detection phase that exceeds the threshold. Particularly when the number of decoy particles is sufficiently large, the probability of detecting the attack approaches 1, thereby effectively countering this attack.
5.1.2. Measure-Resend Attack
In Step 1 or Step 7, Eve intercepts and measures the quantum sequences or transmitted from HTP to . Based on the measurement outcomes, she generates counterfeit quantum sequences or and transmits them to . Through this approach, may encode the secret information onto the tampered photons. Eve subsequently intercepts and measures the quantum sequences or sent from to HTP, thereby obtaining the secret information while simultaneously generating fake quantum sequences or to forward to HTP.
However, Eve possesses no prior knowledge regarding either the positions or preparation bases of the decoy particles. For each decoy particle, Eve has a statistical probability of 50% to select the correct measurement basis. If Eve chooses the correct measurement basis, she can successfully pass the eavesdropping detection. Conversely, if an incorrect basis is selected, Eve will be detected with a probability of statistically. Without loss of generality, assuming the decoy particles prepared by HTP are in the ∣+⟩ state, the detection probabilities for Eve’s modified particles are presented in Table 5.

Table 5.
Probabilities of Eve’s measurement choices and corresponding fake particles.
Similarly, we can compute that the detection probabilities for ∣−⟩, ∣0⟩, and ∣1⟩ are all . Therefore, if the decoy particle is in the ∣+⟩ state, the probability of detecting Eve is
In summary, the probability that HTP detects Eve’s attack is given by
where w represents the number of decoy particles (see Figure 11).
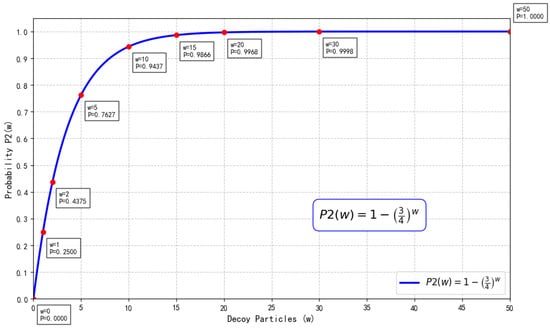
Figure 11.
Detection probability versus number of decoy particles w under measure-resend.
In practical implementations, the sequence length N is finite. Asymptotic security bounds do not strictly apply. Statistical fluctuations in the estimated error rate must be considered. Let be the number of decoy bits. The probability that an attacker’s induced error deviates from the expected value by a margin is bounded by Hoeffding’s inequality. To guarantee a security failure probability , the threshold must be adjusted (lowered) as the sequence length decreases, ensuring that any malicious intervention is statistically distinguishable from channel noise with high confidence.
5.1.3. Trojan Horse Attack
Since the proposed protocol employs symmetric channels, it is vulnerable to Trojan horse attacks. A potential attacker, Eve, could exploit such attacks to intercept the private information of . There are two primary types of Trojan horse attacks: delayed-photon attacks and invisible-photon attacks. To counter these attacks, each bidder needs to be equipped with both a wavelength quantum filter and a photon-number discriminator. The wavelength filter provides protection against invisible-photon attacks, while the photon-number splitter offers defense against delayed-photon attacks. These two devices have been demonstrated to exhibit strong resistance against Trojan horse attacks. Consequently, our protocol can effectively thwart Trojan horse attacks through the implementation of these devices.
5.2. Internal Attacks on Security
We focus on investigating an extreme case where dishonest users collaborate to attack the remaining single honest user. Without loss of generality, assume is the honest bidder while are dishonest bidders conspiring to attack , with the objective of obtaining ’s secret information.
In the SQSAA protocol, since each and HTP communicate through star-shaped symmetric channels, the dishonest bidders would attempt to intercept particles transmitted between HTP and to acquire secret information. In this scenario, the dishonest bidders will be detected as external attackers. According to the protocol specifications, each bidder shares a private key with HTP, and the private key determines the positions of both decoy particles and rotation particles. Since dishonest bidders possess neither the private key shared between HTP and nor the information about quantum states prepared by HTP, any attack strategy they employ will inevitably cause quantum state disturbance and transmission errors and ultimately lead to an error rate exceeding the predetermined threshold. That is to say, our protocol can resist attacks from dishonest users.
5.3. Secrecy Capacity Analysis
Generally speaking, any secure communication protocol can be analyzed using the wiretap channel model, wherein the SQSAA protocol the quantum channel serving as the main channel transmits secret information while Eve’s eavesdropping is modeled as the wiretap channel, whose specific model is illustrated in Figure 12.
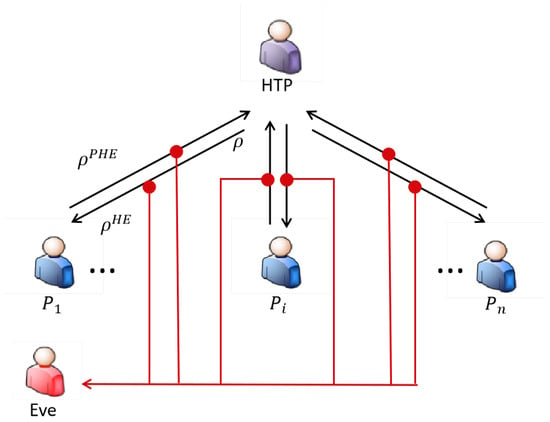
Figure 12.
Wiretap channel model for secrecy capacity analysis in SQSAA.
The secrecy capacity, serving as a fundamental metric for evaluating protocol security in quantum communications, represents the maximum secure information transmission rate between legitimate communicating parties (HTP and ) in the presence of eavesdropper Eve, which constitutes a critical parameter in SQSAA protocol analysis [35] and is expressed as according to Wyner’s wiretap channel theory.
where I(X:Y) characterizes the mutual information between random variables X and Y. Since the particles prepared by HTP have equal probabilities of being in states, the system exhibits a completely mixed state . Under collective attack scenarios, Eve may perform joint operations on both the transmitted qubits and the ancillary qubits she prepares.
where denotes the state of Eve’s prepared ancillary qubit, and U is a unitary operator acting on the joint space of the qubit and ancillary qubit. Eve transmits the qubit to bidder while retaining her ancillary qubit until forwards the qubit to HTP. Upon reception, applies the operator with probability p or the operator with probability (1 − p) based on secret information, evolving the qubit state to
where and . To obtain the secret information, Eve performs coherent measurements on an arbitrary number of qubits and ancillary qubits to distinguish between the quantum states and encoded by bidder , where based on the Holevo bound (whose distinguishing capability is bounded by the Holevo information quantity) we obtain
where S() denotes the von Neumann entropy. The von Neumann entropy of the original quantum state is . Therefore, the maximum mutual information between bidder and eavesdropper Eve is
where is the binary Shannon entropy of .
where and are the detection bit error rate (DBER) in the X-basis and the Z-basis, respectively. Taking into account channel losses, when denoting the maximum accessible qubit rate for Eve as , the maximum mutual information between bidder and Eve consequently becomes
Similarly, we denote the reception rate at HTP as and calculate the mutual information between the bidder and HTP.
Thus, the secrecy capacity becomes
where g represents the discrepancy rate between and , which depends on both channel loss and detector efficiency, reaching its maximum value at .
5.4. Anonymity Analysis
According to the protocol, HTP transmits the quantum sequence to each bidder respectively, where the first particle of sequence received by the j-th bidder serves as the grouping particle. Since this particle is randomly prepared by HTP from and the measurements of grouping particles among different bidders are mutually independent. Therefore, the mutual information between them can be quantitatively calculated as
where denotes any dishonest bidder. Any collusion attempt by dishonest bidders to obtain ’s identity encoding is bound to fail. Attackers can neither access other bidders’ measurement results nor determine honest bidders’ group affiliation through the first particle, thus failing to reconstruct complete identity encoding. Furthermore, the decoy states introduced by HTP in ensure that any external eavesdropping will be detected due to induced errors during eavesdropping detection. Consequently, except for the trusted HTP, no bidder can obtain others’ identity information, guaranteeing the protocol’s anonymity.
The protocol guarantees that bidders cannot ascertain the identities or bids of other participants. However, it is important to note the Trusted HTP Assumption: The HTP knows the mapping between identity codes and real identities. Thus, the protocol provides anonymity against peers and outsiders, but not against the HTP.
5.5. Verifiability and Non-Repudiation Analysis
In Step 10 of the protocol, each bidder computes and submits the hash value of their bid to HTP, establishing a binding commitment since the original bid cannot be deduced without the random nonce. The protocol’s security guarantees non-repudiation, as any bid modification would require finding a new nonce matching the original hash value—a computationally infeasible task even for quantum computers due to the collision-resistant hash function.
Distinction from Channel Disruption: It is crucial to distinguish between *channel disruption* and *repudiation*. High QBER (Step 3) indicates an active attack or denial-of-service, leading to a protocol abort. In contrast, Non-Repudiation (Step 13) prevents a legitimate bidder—who has successfully transmitted a valid bid without triggering high QBER—from later denying their submission.
The verification phase (Step 13) requires the highest bidder to reveal their nonce and hash value for public verification, where successful verification leads to HTP disclosing the winner’s identity number and bid amount, while failed verification triggers a complaint mechanism that either initiates a new auction round for validated complaints or maintains the current highest bid for rejected complaints. This commitment verification framework satisfies the protocol’s verifiability requirement while maintaining quantum-resistant security throughout the auction process.
6. Conclusions
We presented a multi-party semi-quantum simultaneous ascending auction protocol based on single-particle states. HTP generates, distributes, and verifies quantum states; bidders determine groups via measurements and encode private identity vectors, obtaining identity codes after HTP authentication. During bidding, HTP dynamically updates sequences, and bidders submit prices for multiple items using only simple unitary operations. HTP announces current highest bids in real time and iteratively regenerates sequences until no higher bids appear, thereby realizing simultaneous multi-item ascending auctions.
The protocol serves as a quantum-secured signaling layer, providing information-theoretic security for bid transmission and identity verification over a classical auction mechanism. The protocol offers several practical advantages over prior art. First, it accommodates heterogeneous participants by requiring only semi-quantum capabilities on the bidder side (Z/X measurements, reflections, and elementary single-qubit operations), and it relies solely on single-particle resources, substantially lowering implementation cost. Second, it scales naturally to multi-item settings: identity is encoded in the first particles, while each item uses particles for prices, enabling parallel, round-by-round price discovery. Third, the use of per-round hash commitments provides a simple, auditable path for public verification, supporting non-repudiation and complaint resolution without revealing secret randomness until the end.
From a deployment perspective, the protocol parameters are straightforward to tune. The decoy rate and QBER threshold control eavesdropping detectability and robustness; the per-item bit width balances price granularity and sequence length; and the basic operation set (I, H, , Z/X measurements) matches today’s photonic toolchains. Computational and storage complexity at bidders is minimal, and HTP’s classical processing (matrix checks and bit-to-decimal conversion) scales linearly in the number of bidders and items per round.
Finally, we must emphasize that theoretical validity does not automatically translate to immediate real-world applicability. Bridging the gap between our theoretical model and a fully operational real-world deployment remains a significant future challenge. This requires rigorous validation under realistic physical conditions, deep integration with existing technological infrastructures, and further study on practical device imperfections.
There remain limitations and opportunities for future work. The current model assumes a trusted HTP; relaxing this with distributed trust (e.g., threshold HTP, verifiable computation, or lightweight MPC among multiple centers) is an important direction. A finite-size and composable security analysis under realistic device imperfections and channel loss would strengthen the guarantees. On the systems side, building a prototype with time-bin or polarization-encoded photonics, integrating authenticated classical channels, and benchmarking end-to-end latency would support practical adoption. Finally, extending to richer auction formats (e.g., combinatorial or budget-constrained bidding), adaptive increment rules, and privacy-enhanced analytics while preserving semi-quantum feasibility are promising avenues.
Author Contributions
Methodology, X.W.; software, X.W.; formal analysis, X.W.; writing—original draft preparation, X.W.; validation, B.W. and Y.Y.; supervision, Y.H.; writing—review and editing, Y.Z. and Y.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China (Grant No. 62201252) and the Fundamental Research Funds for the Central Universities (NO. NS2025030). We also acknowledge the support from the Jiangsu Province Engineering Research Center of IntelliSense Technology and System.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zhang, W.; van Leent, T.; Redeker, K.; Garthoff, R.; Schwonnek, R.; Fertig, F.; Eppelt, S.; Rosenfeld, W.; Scarani, V.; Lim, C.C.W.; et al. A device-independent quantum key distribution system for distant users. Nature 2022, 607, 687–691. [Google Scholar] [CrossRef]
- Zahidy, M.; Ribezzo, D.; De Lazzari, C.; Vagniluca, I.; Biagi, N.; Müller, R.; Occhipinti, T.; Oxenløwe, L.K.; Galili, M.; Hayashi, T.; et al. Practical high-dimensional quantum key distribution protocol over deployed multicore fiber. Nat. Commun. 2024, 15, 1651. [Google Scholar] [CrossRef]
- Sheng, Y.B.; Zhou, L.; Long, G.L. One-step quantum secure direct communication. Sci. Bull. 2022, 67, 367–374. [Google Scholar] [CrossRef]
- Sun, X.F.; Fan, L.; Cao, C.; Yu, W.S. Measurement-device-independent quantum secure multiparty summation based on entanglement swapping. Laser Phys. Lett. 2023, 20, 125201. [Google Scholar] [CrossRef]
- Li, C.; Ye, C.; Tian, Y.; Chen, X.B.; Li, J. Cluster-state-based quantum secret sharing for users with different abilities. Quantum Inf. Process. 2021, 20, 385. [Google Scholar] [CrossRef]
- Ma, R.H.; Gao, F.; Cai, B.B.; Lin, S. Quantum Secret Reconstruction. Adv. Quantum Technol. 2024, 7, 2300273. [Google Scholar] [CrossRef]
- Wang, Q.; Yu, C.; Gao, F.; Qi, H.; Wen, Q. Self-tallying quantum anonymous voting. Phys. Rev. A 2016, 94, 022333. [Google Scholar] [CrossRef]
- Borjigin, W.; Ota, K.; Dong, M. In broker we trust: A double-auction approach for resource allocation in NFV markets. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1322–1333. [Google Scholar] [CrossRef]
- Bag, S.; Hao, F.; Shahandashti, S.F.; Ray, I.G. SEAL: Sealed-bid auction without auctioneers. IEEE Trans. Inf. Forensics Secur. 2019, 15, 2042–2052. [Google Scholar] [CrossRef]
- Borjigin, W.; Ota, K.; Dong, M. Multiple-Walrasian auction mechanism for tree valuation service in NFV market. IEEE Trans. Comput. Soc. Syst. 2022, 10, 61–71. [Google Scholar] [CrossRef]
- Ye, C.Q.; Li, J.; Chen, X.B.; Dong, M.; Ota, K. Measurement-based quantum sealed-bid auction. IEEE Trans. Circuits Syst. I Regul. Pap. 2023, 70, 5352–5365. [Google Scholar] [CrossRef]
- Dowling, J.P.; Milburn, G.J. Quantum technology: The second quantum revolution. Philos. Trans. R. Soc. Lond. Ser. A Math. Phys. Eng. Sci. 2003, 361, 1655–1674. [Google Scholar] [CrossRef] [PubMed]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Piotrowski, E.W.; Sładkowski, J. Quantum auctions: Facts and myths. Phys. A Stat. Mech. Its Appl. 2008, 387, 3949–3953. [Google Scholar] [CrossRef]
- Naseri, M. Secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 1939–1943. [Google Scholar] [CrossRef]
- Qin, S.J.; Gao, F.; Wen, Q.Y.; Meng, L.M.; Zhu, F.C. Cryptanalysis and improvement of a secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 4014–4016. [Google Scholar] [CrossRef]
- Yang, Y.G.; Naseri, M.; Wen, Q.Y. Improved secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 4167–4170. [Google Scholar] [CrossRef]
- Zhao, Z.; Naseri, M.; Zheng, Y. Secure quantum sealed-bid auction with post-confirmation. Opt. Commun. 2010, 283, 3194–3197. [Google Scholar] [CrossRef]
- Liu, W.J.; Wang, F.; Ji, S.; Qu, Z.G.; Wang, X.J. Attacks and improvement of quantum sealed-bid auction with EPR pairs. Commun. Theor. Phys. 2014, 61, 686. [Google Scholar] [CrossRef]
- Liu, W.J.; Wang, H.B.; Yuan, G.L.; Xu, Y.; Chen, Z.Y.; An, X.X.; Ji, F.G.; Gnitou, G.T. Multiparty quantum sealed-bid auction using single photons as message carrier. Quantum Inf. Process. 2016, 15, 869–879. [Google Scholar] [CrossRef]
- Zhang, R.; Shi, R.H.; Qin, J.Q.; Peng, Z.W. An economic and feasible Quantum Sealed-bid Auction protocol. Quantum Inf. Process. 2018, 17, 35. [Google Scholar] [CrossRef]
- Shi, R.H. Quantum sealed-bid auction without a trusted third party. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 4221–4231. [Google Scholar] [CrossRef]
- Shi, R.H. Anonymous quantum sealed-bid auction. IEEE Trans. Circuits Syst. II Express Briefs 2021, 69, 414–418. [Google Scholar] [CrossRef]
- Shi, R.H.; Li, Y.F. A feasible quantum sealed-bid auction scheme without an auctioneer. IEEE Trans. Quantum Eng. 2022, 3, 2100212. [Google Scholar] [CrossRef]
- Zhang, C.; Huang, Q.; Long, Y.; Sun, Z. Secure three-party semi-quantum summation using single photons. Int. J. Theor. Phys. 2021, 60, 3478–3487. [Google Scholar] [CrossRef]
- Yang, C.W.; Tsai, C.W.; Chen, C.A.; Lin, J. Robust Semi-Quantum Summation over a Collective-Dephasing Noise Channel. Mathematics 2023, 11, 1405. [Google Scholar] [CrossRef]
- Ye, C.Q.; Li, J.; Chen, X.B.; Dong, M.; Ota, K.; Khalique, A.; Durad, M.H. Semi-Quantum Secure Multiparty Summation and its Applications to Anonymous Auction and Ranking. Adv. Quantum Technol. 2024, 7, 2300347. [Google Scholar] [CrossRef]
- Tian, Y.; Zhang, N.; Ye, C.; Bian, G.; Li, J. Different secure semi-quantum summation models without measurement. EPJ Quantum Technol. 2024, 11, 35. [Google Scholar] [CrossRef]
- Ye, T.Y.; Xu, T.J.; Geng, M.J.; Chen, Y. Two-party secure semiquantum summation against the collective-dephasing noise. Quantum Inf. Process. 2022, 21, 118. [Google Scholar] [CrossRef]
- Hu, J.L.; Ye, T.Y. Three-party secure semiquantum summation without entanglement among quantum user and classical users. Int. J. Theor. Phys. 2022, 61, 170. [Google Scholar] [CrossRef]
- Milgrom, P. Putting auction theory to work: The simultaneous ascending auction. J. Political Econ. 2000, 108, 245–272. [Google Scholar] [CrossRef]
- Li, G.D.; Liu, J.C.; Wang, Q.L.; Sun, W.Q. Employing single photons for measurement-device-independent quantum secure direct communication with identity authentication. IEEE Commun. Lett. 2024, 28, 473–477. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.