Abstract
The Loop-Back Quantum Key Distribution (LB-QKD) protocol establishes a bidirectional architecture in which a single photon travels forth and back through the same optical channel. Unlike conventional one-way schemes such as BB84, Alice performs both state preparation and measurement, while Bob acts as a passive polarization modulator and reflector. This design eliminates detectors at Bob’s side, minimizes synchronization requirements, and enables compact, low-power implementations suitable for quantum-mobile and IoT platforms. An extended three-basis configuration is introduced, preserving the simplicity of the two-basis scheme while improving noise tolerance through enhanced orthogonality-based filtering. Analytical modeling shows that the effective protocol error decreases from to , achieving a 33% improvement in noise resilience. Despite its slightly lower sifting efficiency (), the total information gain reaches bits per pulse, maintaining post-sifting throughput comparable to BB84. The protocol doubles the tolerable QBER of conventional QKD, sustaining secure operation up to for two bases and approximately for three bases. Its passive, self-verifying architecture enhances resistance to man-in-the-middle, photon-number-splitting, and side-channel attacks, providing a scalable and energy-efficient framework for secure key distribution and authentication in next-generation mobile and distributed quantum networks.
1. Introduction
In the 1970s, Stephen Wiesner proposed a visionary scheme for unforgeable quantum money, based on the fundamental principles of quantum mechanics, particularly the no-cloning theorem [1]. In his proposal, Alice (the bank) encodes quantum states, such as polarizations in orthogonal bases (X, Z), into a quantum banknote. Bob, the user, presents this banknote, and Alice authenticates its validity by measuring the states in the correct bases, previously stored, thereby detecting any tampering due to the impossibility of cloning unknown quantum states. Although theoretically sound, this concept faced significant technological limitations, as it required quantum memories to preserve the original states—a challenge that was unattainable at the time and remains so today [2].
The Loop-Back QKD (LB-QKD) protocol realizes this vision by transferring Wiesner’s quantum authentication scheme to an experimentally feasible context [3]. Instead of quantum memories, the polarization bases () are encoded at the receiver (Bob) using an electro-optic modulator (EOM) and a retroreflector. Alice sends attenuated laser pulses with an average photon number (typically ), which Bob reflects after applying a selected basis. Upon reception of the reflected pulse, Alice measures it in the same preparation basis and compares the outcome with the state initially sent. An orthogonal outcome implies that Bob used the conjugate basis, so Alice can infer his basis choice and assign a classical bit value (e.g., , ), in direct analogy with Wiesner’s banknote verification scheme illustrated in Figure 1. In this way, each successful round simultaneously authenticates the remote device and contributes one symbol to the raw key. This design removes the need for quantum storage while preserving the essence of the quantum banknote in modern applications. An alternative scenario with static polarizers arranged in a matrix and scanned by Alice further reinforces the analogy with Wiesner’s scheme: each polarizer corresponds to a banknote element, encoded in a fixed basis, whose validity is verified by measurement. The no-cloning principle guarantees security against adversaries. In the dynamic version of LB-QKD, the randomness in basis selection increases flexibility and enables real-time key generation.
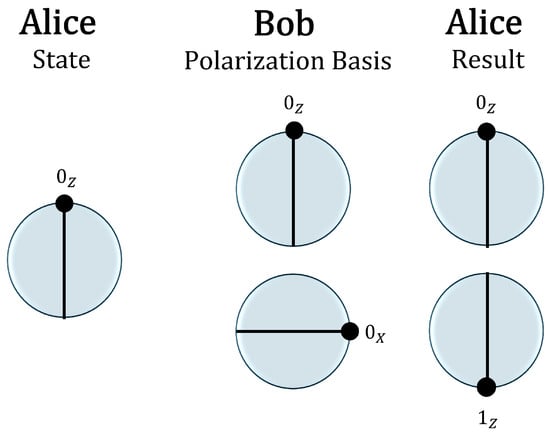
Figure 1.
Steps of the protocol: (1) Alice prepares and sends the state to Bob using the Z basis. (2) Bob randomly selects a basis with equal probability. If he chooses the Z basis, the state remains unchanged and is returned to Alice, who measures in the same basis and obtains . This outcome is ambiguous. (3) If Bob chooses the X basis, the state collapses to or with equal probability. As illustrated, if the state is sent back, Alice measures in the Z basis and obtains either or with equal probability. In the latter case, she can infer that Bob used the X basis. In this scheme, information is encoded in the basis: , .
The BB84 protocol, subsequently developed by Bennett and Brassard, marked a turning point in quantum cryptography by introducing a key distribution method based on the transmission of photons polarized in mutually incompatible bases [4]. Although its security relies on physical principles and has proven robust against both classical and quantum attacks, the protocol requires active components at both ends, precise synchronization, and a complex optical infrastructure. These requirements increase implementation costs and limit integration into portable devices. Traditional one-way DV-QKD protocols such as BB84 require single-photon detection and actively stabilized optics at the receiver, and often also dedicated quantum hardware at the transmitter side. After several decades of development, highly integrated and even commercial implementations of BB84-based QKD are now available, providing turnkey systems for metropolitan and backbone networks [5,6]. However, these architectures typically retain a symmetric allocation of quantum hardware, with single-photon detectors and actively stabilized optics at the receiver and, in many cases, specialized transmitters. In contrast, the Loop-Back architecture concentrates all single-photon detectors and basis-dependent post-processing at a single node (Alice), while the remote station (Bob) can be implemented as a nearly passive device equipped only with a low-power electro-optic modulator and a retroreflector. This asymmetry enables lower-cost and simpler remote terminals and reduces the side-channel exposure at the network edge, which is particularly attractive in scenarios with many distributed users or constrained devices (see Figure 2).
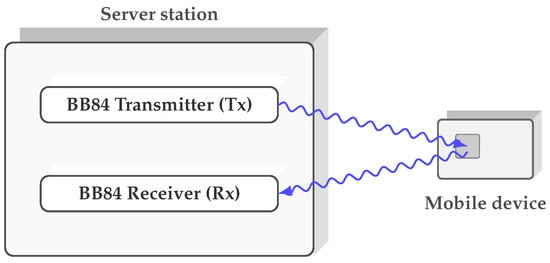
Figure 2.
Conceptual diagram of the loop-back architecture. The BB84 transmitter (Tx) and receiver (Rx) are integrated into a single server station. A mobile device, modeled as a compact token, participates in a quantum loop-back process: a quantum pulse emitted by the Tx is directed towards the device, interacts at the mobile interface, and is then returned to the Rx, enabling the system either to establish a key with the server or to provide an authentication code.
Subsequent extensions, such as B92 [7,8], 6-State [9,10], MDI-QKD [11,12], and TF-QKD [13,14], have aimed to improve efficiency and security, albeit with greater technological demands that hinder widespread deployment.
The driving force behind these advances stems from the development of quantum computing, a disruptive technology capable of solving problems intractable for classical computation. However, the same algorithms that promise to accelerate scientific calculations and process optimization also pose a direct threat to currently used public-key cryptography. Shor’s algorithm, for instance, compromises integer factorization and discrete logarithm computations, which are the foundations of RSA and ECC systems [15,16]. This scenario has motivated the search for solutions offering security grounded in physical principles, such as quantum key distribution (QKD), whose intrinsic nature ensures the detection of any eavesdropping attempts [5,6].
At the international level, significant milestones have been achieved, such as the Beijing–Shanghai quantum network and the Micius satellite mission, which have demonstrated the technical feasibility of large-scale quantum links. Nonetheless, fiber-optic attenuation and the high costs of space-based links remain significant limitations [17,18,19]. In parallel, mobile and portable QKD schemes have been explored, including prototypes developed by Nokia and the University of Oxford, the reference-frame-independent QKD (rfi-QKD) modality, and experimental demonstrations on moving platforms such as drones [20,21,22,23]. These efforts aim to integrate quantum security into everyday applications, although current solutions still face practical constraints.
In this context, the Loop-Back QKD protocol emerges as a particularly attractive alternative. Unlike Wiesner’s quantum banknote, which is unfeasible in its original implementation, and BB84, which requires active infrastructure at both nodes, LB-QKD employs a passive remote device with a low-power electro-optic modulator. The higher technological complexity resides with Alice, who handles transmission, detection, and analysis, while Bob only dynamically selects polarization bases. This design eliminates the need for detectors at Bob’s side, significantly reduces infrastructure requirements, and facilitates device miniaturization. Its analogy to a barcode scanner, where Alice “reads” a passive pattern modulated by Bob, highlights the simplicity and scalability of the approach, positioning it as a viable solution for cybersecurity applications in mobile payments, authentication, and access control in Internet of Things environments.
The remainder of this article is organized as follows. Section 2 describes the Loop-Back QKD protocol and establishes its conceptual and operational equivalence to the standard BB84 scheme. Section 3 introduces the three-basis extension of the Loop-Back protocol, highlighting its structural simplicity and enhanced error tolerance. Section 4 presents a detailed analysis of channel-induced errors and the intrinsic error-compensation mechanisms arising from the round-trip configuration. In Section 5, we derive the analytical bounds for the effective QBER and determine the corresponding security thresholds for both the two- and three-basis configurations. Section 6 discusses the protocol’s robustness against common quantum attacks, including man-in-the-middle, photon-number-splitting, and side-channel exploits. Finally, Section 8 summarizes the main contributions and outlines potential directions for further research and experimental validation.
2. The Loop-Back QKD Protocol
The Loop-Back Quantum Key Distribution (LB-QKD) protocol establishes a bidirectional quantum communication scheme in which a single optical pulse travels forth and back through the same channel. Unlike one-way protocols such as BB84, the loop-back architecture allows Alice to both prepare and measure the quantum state, while Bob performs only a controlled polarization operation. This configuration inherently verifies the coherence of the optical path and enhances resistance to man-in-the-middle (MitM) attacks, as the quantum channel itself must remain consistent over both directions.
2.1. Operational Steps
- Parameter Agreement. Alice and Bob agree on two mutually unbiased polarization bases, and , which are associated with logical bits 0 and 1, respectively. They also synchronize timing, detector thresholds, and any classical authentication mechanisms.
- State Preparation (Alice). For each transmission round, Alice randomly selects a preparation basis and prepares a quantum state uniformly chosen from . The state is then launched into the quantum channel toward Bob.
- Random Polarization (Bob). Upon reception, Bob chooses at random his polarization basis . He applies the corresponding polarization operation to the incoming state and immediately reflects it back to Alice through the same optical path. Bob performs no quantum measurement; his role is purely passive and reflective.
- Return and Measurement (Alice). The pulse travels back through the same optical fiber. Alice measures the returned photon in her original preparation basis , obtaining one of the two possible outcomes within that basis.
- Inference Rule. If the measurement result is orthogonal to the prepared state, Alice infers that Bob’s basis was opposite to hers (). Conversely, if the measurement coincides with the original state, she concludes that . Only the former case (orthogonal outcome) is kept for key generation.
- Public Announcement and Sifting. Alice publicly announces only the indices of successful rounds (those with orthogonal outcomes). Bob retains the corresponding rounds in which he used the opposite basis. Both parties now share an implicit bit value determined by Bob’s chosen basis:
- Raw Key Formation. After multiple repetitions of the above procedure, the subset of successful rounds forms the raw key sequence shared between Alice and Bob. Subsequent stages such as error correction, parameter estimation, and privacy amplification are applied later to obtain the final secret key.
The defining feature of LB-QKD is that only Alice performs quantum detection, while Bob’s station acts as a controllable polarization mirror. The correlation between Alice’s measurement outcome and Bob’s random polarization basis allows both parties to share key bits without ever revealing their bases through the public channel. This intrinsic symmetry provides a built-in check of channel integrity and forms the conceptual foundation for advanced loop-back schemes and MitM-resilient network architectures.
2.2. BB84-Equivalent Loop-Back
The BB84 protocol constitutes the foundational standard for Quantum Key Distribution (QKD). In its standard version, Alice transmits photons polarized in one of two possible bases, , while Bob measures in a randomly selected basis. Security arises from the fact that an external observer cannot simultaneously know both bases without introducing detectable errors.
In the BB84-equivalent Loop-Back QKD protocol, Alice’s station integrates both the transmitter (Tx) and receiver (Rx)—the latter associated with a fixed Bob—and is equipped with a half-wave plate (HWP) (see Figure 3). The mobile Bob, in contrast, only possesses a random polarizer and a dielectric mirror. The pulse is reflected, undergoes a transformation induced by the HWP, which effectively returns the orthogonal quantum state, and is subsequently measured by Alice (fixed Bob) in her original preparation basis with a 50% probability.
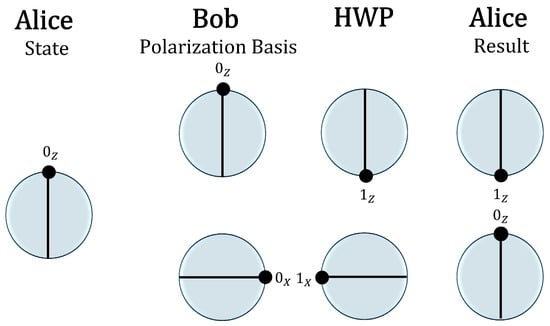
Figure 3.
Protocol steps: (1) Alice prepares the state and sends it to Bob using the Z basis. (2) Bob randomly selects a measurement basis with equal probability. (3) At Alice’s station (fixed Bob), a half-wave plate (HWP) transforms the incoming pulse into the orthogonal quantum state. A successful event occurs when the fixed Bob chooses the same basis as Alice (as in standard BB84) and produces the same measurement outcome, as Alice has access to the results. This constitutes the Loop-Back equivalent of the protocol.
- BB84 standard: Success occurs when Alice and Bob choose the same basis. The probability of success is , and after the sifting process, the key is obtained.
- Equivalent Loop-Back: Success occurs when Alice and Bob choose the same basis and, additionally, the measured state matches the state sent by Alice. It is important to note that both the transmitter (Tx) and receiver (Rx) are located at Alice’s station. In this scenario, Alice can infer the basis selected by Bob (mobile). The effective probability of success is , which is equivalent to the expected yield after discarding events in which the state does not match. Therefore, the adjustment system in the BB84-equivalent Loop-Back QKD requires minimal modifications compared to the standard BB84 system.
It should be noted that the component described as a dielectric mirror in Bob’s configuration specifically refers to a retroreflector (e.g., a corner-cube). This device reflects quantum pulses back along the direction of incidence regardless of Bob’s angular orientation, which is critical for mobile applications where the receiver device (e.g., tag, smartphone, or IoT device) may change position or orientation during transmission.
A key advantage of the Loop-Back QKD scheme is that Bob’s hardware operates in an almost passive manner, as it does not require an active pulse detection system. This also provides another significant benefit: Alice and Bob do not need complex synchronization, since Alice’s objective is to identify the basis used by Bob at the detection instants.
3. The Three-Basis Loop-Back QKD Protocol
The Three-Basis Loop-Back Quantum Key Distribution (LB-QKD) protocol extends the bidirectional configuration of the original two-basis scheme by operating over three mutually orthogonal polarization bases, , , and . The system preserves the core principle of the Loop-Back architecture: Alice performs both state preparation and measurement, while Bob only applies a polarization transformation and reflects the photon without detection. This configuration maintains bidirectional coherence and provides enhanced error filtering due to the triaxial encoding.
Operational Steps
- Parameter Agreement. Alice and Bob agree on the three mutually unbiased polarization bases , each associated with a distinct logical label:They synchronize timing, detector thresholds, and classical authentication parameters as in the two-basis configuration.
- State Preparation (Alice). In each transmission round, Alice randomly selects a preparation basis and prepares a quantum state uniformly chosen from the corresponding basis . The photon is then sent through the quantum channel to Bob.
- Random Polarization (Bob). Upon reception, Bob randomly selects his polarization basis with uniform probability . He applies the corresponding polarization transformation to the incoming state and immediately reflects it back toward Alice through the same optical path. Bob performs no quantum measurement; his role remains purely passive.
- Return and Measurement (Alice). The photon travels back through the same optical fiber. Alice measures it in her original basis , obtaining one of the two possible outcomes in that basis.
- Inference Rule. If the measurement result is orthogonal to the state she initially sent, Alice infers that Bob’s basis was different from hers (). In this case, Bob’s chosen basis must belong to the plane orthogonal to her own preparation basis.
- Public Announcement and Sifting. To enable basis identification without revealing it directly, Bob publicly announces a pair of bases selected from , ensuring that his actual basis is one of the two in the announced pair. Among these three possible pairs, exactly one does not include Alice’s basis and is therefore ambiguous. If the announced pair excludes , the round is discarded. If the announced pair includes and Alice’s measurement result was orthogonal, the round is retained for key generation, as Alice can unambiguously determine Bob’s basis.
- Raw Key Formation. The retained rounds form the raw key, with bit values assigned according to Bob’s basis using the mappingSubsequent stages of error correction and privacy amplification are applied to distill the final secret key.
In ideal conditions, the probability that Bob selects a basis different from Alice’s is , the probability that the announced pair includes Alice’s basis is , and the probability of obtaining an orthogonal outcome in Alice’s measurement is . The resulting sifting efficiency is therefore
Given that three bases convey bits of information, the theoretical information gain is
This scheme maintains a comparable efficiency to the two-basis version while achieving a slightly higher information gain of approximately bits per pulse.
4. Channel Error Analysis
We now extend the analysis of the quantum bit error rate (QBER) to compare the two- and three-basis versions of the Loop-Back QKD protocol. Let e denote the error probability introduced by the quantum channel during one-way propagation. The Loop-Back architecture allows partial compensation of these errors through Bob’s active polarization regeneration and Alice’s orthogonality-based filtering.
4.1. Two-Basis Configuration
Consider first the bidimensional configuration operating over the bases . When Alice and Bob select the same basis, the polarization transformation applied by Bob acts as an active regenerator, partially compensating for the forward-path distortion. Under this condition, the effective error seen by Alice is approximately equal to the channel error,
When the bases differ (), Alice measures the returned photon in her preparation basis. The projection and orthogonality acceptance criterion remove most of the depolarization effects, leading to
Since each basis is chosen with equal probability, the overall average error over the accepted rounds is
This error reduction by a factor of two relative to the raw channel error explains the improved tolerance and longer operational distance compared to BB84, while preserving a comparable key rate.
4.2. Three-Basis Configuration
In the triaxial configuration using , the probabilities of coinciding and differing bases change: the chance of selecting the same basis becomes , while differing bases occur with probability . As before, only the same-basis cases accumulate the full channel error, while the mismatched rounds are largely immune to depolarization due to the filtering mechanism:
Therefore, the average protocol error for the three-basis system becomes
The expected QBER of the accepted qubits is thus further reduced by a factor of , yielding an effective improvement in noise resilience compared to the two-basis scheme. This property implies that the secret key rate remains positive under higher physical QBER or longer transmission distances.
4.3. Comparative Discussion
While the sifting efficiency of the three-basis scheme is slightly lower () than that of the two-basis configuration (), the overall information gain remains comparable:
Hence, the advantage of the three-basis protocol lies not in the information throughput but in its intrinsic robustness to channel errors. The effective error ratio,
quantifies a relative improvement in error suppression over the two-basis case.
5. Error Thresholds
The asymptotic secret-key rate R for the Loop-Back QKD protocol is evaluated using the Devetak–Winter bound under the assumption of collective symmetric attacks. In this idealized framework, R depends on the mutual information shared between Alice and Bob and on the Holevo bound representing Eve’s accessible information. Here, collective symmetric attacks refer to the standard scenario in which Eve applies the same interaction to each signal, stores her quantum ancillae in a long-term quantum memory and performs a joint measurement at the end of the protocol. The Devetak–Winter bound then provides a lower bound on the asymptotic secret-key rate under this restricted but widely used attack model. A rigorous extension of our analysis to the most general coherent attacks in two-way architectures such as Loop-Back QKD, where Eve may correlate arbitrarily many rounds at the level of the global quantum state, is beyond the scope of this work and remains an open problem. Therefore, the error thresholds derived in Section 5 should be interpreted as asymptotic benchmarks under symmetric collective attacks, rather than as full-security bounds against all possible coherent strategies.
For symmetric channels, these quantities can be expressed as
where n denotes the number of polarization bases defining the protocol (two or three), and is the conditional Shannon entropy of Bob’s basis given Alice’s preparation. In the Loop-Back setting, this symmetry arises from two ingredients. First, Alice and Bob choose each of the n mutually unbiased bases with equal probability, so that all logical symbols are used in a perfectly balanced way. Second, the physical channel is modeled as an isotropic depolarizing map acting on the polarization qubit, which affects all basis states in the same way. As a consequence, the effective classical channel from Alice’s basis label A to Bob’s reconstructed label B is a discrete symmetric channel: for any input symbol a, the correct output occurs with probability , while the error symbols occur with equal probability .
The resulting asymptotic key rate is
with being the sifting efficiency.
5.1. Two-Basis Configuration
For the standard Loop-Back QKD protocol with two bases (, ), the quantum bit error rate (QBER) in the accepted key is denoted by , where e is the one-way physical channel error. In what follows, we model this physical error as arising from an isotropic depolarizing channel acting on the polarization qubit. In this picture, e plays the role of the depolarizing probability per one-way use of the link, effectively capturing the aggregate effect of random polarization rotations and decoherence in the optical channel. In this case, reduces to the binary entropy function:
Setting in Equation (1) gives the critical condition
Solving numerically yields . Using , the maximum tolerable physical error is
Hence, the two-basis Loop-Back protocol doubles the tolerable physical QBER compared to the standard BB84 threshold (), as a result of bidirectional propagation and orthogonality-based filtering.
5.2. Three-Basis Configuration
For the extended Loop-Back QKD protocol employing three orthogonal polarization bases (, ), the effective QBER is reduced to following the Devetak–Winter bound for symmetric collective attacks [24]. Here, Bob’s outcomes form a ternary symmetric channel, conceptually related to the three-basis (six-state) model introduced by Bruß [9] with correct transmission probability and two equiprobable error outcomes each of probability . This structure follows directly from the combination of uniform basis selection over and isotropic depolarization: conditioned on Alice’s basis label A, Bob obtains the same label with probability , while each of the two remaining labels occurs with probability , defining a standard ternary symmetric channel. The conditional entropy becomes
Substituting this into Equation (1) and setting gives the threshold condition
which corresponds to . Solving numerically yields , and therefore
This represents an idealized upper bound under perfect ternary symmetry: in this regime, the effective error in the accepted key () remains below the Shannon limit where the mutual information vanishes.
The binary and ternary derivations provide complementary perspectives on the Loop-Back protocol’s error tolerance. The two-basis formulation, employing binary entropy , yields the effective threshold and the corresponding physical limit , which is twice that of BB84. The three-basis model, based on ternary entropy , yields the higher bound , emphasizing the robustness of triaxial encoding under isotropic depolarization.
The use of an isotropic depolarizing channel as an effective description of polarization noise is standard in QKD performance and security studies, where the various physical imperfections of the optical link are lumped into a single depolarizing parameter that reproduces the observed QBER and bounds the impact of eavesdropping strategies [25,26]. For polarization-encoded implementations, random birefringence fluctuations, misalignment and environmental perturbations tend to scramble the state of polarization over time; the time-averaged action of these effects is well captured by an isotropic depolarizing map that shrinks the Bloch vector toward the maximally mixed state [27,28]. Within this framework, the parameter e quantifies the depolarizing probability per one-way channel use, while additional implementation-dependent imperfections (such as detector dark counts or timing jitter) can be treated as extra contributions to the QBER that affect Loop-Back and one-way protocols in a comparable way, without altering the relative robustness indicated by and .
In practice, real optical channels are neither perfectly symmetric nor memoryless, so the effective threshold will lie between these two limits. Nevertheless, the ternary extension highlights the key advantage of Loop-Back QKD: by expanding the Hilbert space dimensionality and employing bidirectional verification, the protocol distributes channel noise over more degrees of freedom, effectively increasing the tolerable physical error while preserving secure key generation.
The combined effect of this reduction is a slower decay of the secret key rate as the QBER increases, as shown in Figure 4. The three-basis scheme maintains positive key generation at higher channel noise levels and extends the secure communication distance without requiring additional optical components. This behavior stems from the expansion of the polarization space, which increases the proportion of rounds that benefit from orthogonality-based filtering.
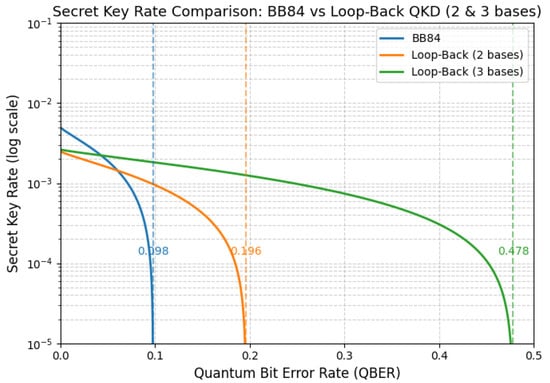
Figure 4.
Comparison of the effective quantum bit error rate (QBER) and the corresponding secret key rate for the two- and three-basis Loop-Back QKD configurations. The three-basis scheme exhibits a reduced effective protocol error () and maintains a positive secret key rate under higher-channel-noise conditions.
6. Security Analysis
The Loop-Back QKD protocol belongs to the class of bidirectional quantum communication schemes, where the same photon traverses the channel twice—first from Alice to Bob and then back to Alice. This topology establishes a natural connection with earlier deterministic communication protocols, notably the LM05 scheme proposed by Lucamarini and Mancini in 2005 [29]. While both architectures exploit the round-trip propagation of a single photon, their objectives, encoding strategies, and physical security assumptions differ fundamentally.
6.1. Operational and Conceptual Paradigm
In the LM05 protocol, the photon acts as a deterministic carrier of information. Alice prepares a qubit in one of two nonorthogonal bases (Z or X) and transmits it to Bob, who encodes his bit by applying one of two unitary operations,
The unitary performs a rotation on the Bloch sphere, mapping each logical state to its orthogonal complement in both bases. After applying the transformation, Bob returns the photon to Alice, who measures it in the same basis used for preparation. This configuration achieves deterministic communication: in the absence of noise, Alice can infer Bob’s bit value with certainty, without discarding events or performing basis reconciliation.
Loop-Back QKD, in contrast, remains strictly probabilistic. Bob does not encode any information; instead, he randomly polarizes the incoming photon in one of the allowed bases and reflects it. All bit generation and basis inference occur at Alice’s side, using only the subset of orthogonal measurement outcomes. This design choice preserves the randomness necessary for secure key distribution and shifts the focus from deterministic information transfer to entropy extraction and continuous channel verification.
6.2. Security Implications
The structural divergence between LM05 and Loop-Back QKD yields distinct security profiles. In LM05, Bob’s active unitary modulation requires electro-optic devices synchronized to Alice’s emission, introducing an optical activity that becomes a potential source of side-channel leakage. Residual back-reflections or phase fluctuations may carry information about the applied operation, enabling Trojan-Horse Attacks (THA) [30], in which an eavesdropper injects probe light to infer Bob’s modulator state. Although countermeasures such as optical isolators, power monitors, and authentication layers can mitigate these attacks, they increase the system’s hardware complexity and synchronization requirements.
Loop-Back QKD eliminates the need for active modulation altogether. Bob performs no unitary encoding, measurement, or detection. His setup consists of a passive polarization modulator operating under a random control signal and a retroreflector that ensures spatial mode reversibility. No data is stored or processed in Bob’s node, making the system inherently immune to Trojan-Horse probing: an injected photon cannot interact with any basis-dependent optical component capable of encoding useful information. Furthermore, the absence of emissions or switching transients suppresses classical side-channel leakage, including electromagnetic or thermal signatures. The protocol thus achieves higher security not through added hardware, but through architectural minimalism—a reduction in attack surface by design.
6.3. Intrinsic Security Properties of the Loop-Back Protocol
Beyond its structural resilience, Loop-Back QKD integrates continuous channel verification within its operation. Every photon traverses the quantum link twice, and deviations in the expected statistics of orthogonal detections immediately reveal channel perturbations or interception. This built-in monitoring replaces the control mode used in LM05, where Bob alternates between coding and reflection to estimate the QBER. Loop-Back achieves the same verification intrinsically, without mode switching or classical disclosure.
- Resistance to Man-in-the-Middle (MiTM) Attacks
As previously discussed in [3], the round-trip propagation in Loop-Back QKD allows Alice to verify channel integrity by monitoring unmodified reflections. Any deviation from the expected error rate serves as a direct indicator of eavesdropping. Moreover, an adversary cannot conceal the temporal delay introduced by an intermediate relay. Even minimal tampering produces a cumulative delay of over the ABA path. Precise round-trip timing analysis thus enables physical-layer detection of MitM attempts without requiring additional quantum resources.
- Resistance to Photon Number Splitting (PNS) Attacks
Photon-number-splitting attacks exploit multi-photon emissions to gain partial information about the key. In Loop-Back QKD, Bob’s passive configuration—using a polarization modulator and retroreflector without detectors—prevents any measurement leakage from Bob’s side. Since the polarization bases are never disclosed over the classical channel and are inferred solely by Alice through successful detection events (), Eve cannot correlate her intercepted photons with Bob’s actual basis choices.
- Protection Against Side-Channel Attacks
Side-channel vulnerabilities, such as power consumption analysis or electromagnetic emissions, are inherently suppressed by the passive nature of Bob’s module. In most DV-QKD implementations, the most technologically demanding and attack-prone components are the single-photon detectors at the receiver side, whose efficiency, dark-count rate and afterpulsing behavior directly limit the achievable key rate and enable powerful detector side-channel attacks [5,31]. By design, the Loop-Back architecture removes all detection hardware from the remote node and concentrates it at Alice’s station, so that Bob does not include single-photon detectors, time-tagging electronics or local key-dependent processing. Compared with other two-way QKD schemes where the remote node plays a nominally passive role (such as LM05- and Ping-Pong-like protocols, or plug-and-play architectures that still rely on local detectors, entangled sources or active encoders at the remote site) [29,32,33], the Loop-Back configuration keeps all basis-dependent detection and post-processing at Alice. The remote device only performs basis selection via a low-power electro-optic modulator and a retroreflector, and never stores or measures key-dependent information, which provides a concrete security advantage by further reducing the available attack surface at Bob’s side. The electro-optic modulator operates at constant low power, producing no deterministic timing pattern related to the chosen basis. Furthermore, the non-disclosure of bases in classical communication eliminates the possibility of statistical correlation with external measurements, thereby minimizing leakage channels such as EOM switching times or synchronization artifacts.
- Limitations and Practical Considerations
Despite the above advantages, the Loop-Back architecture also presents some intrinsic limitations. The most relevant one is its sifting efficiency: in the current two- and three-basis configurations, only about and of the detected rounds, respectively, contribute to the raw key, in contrast with the basis-matching efficiency of standard BB84. From a purely rate-oriented perspective, this represents a disadvantage with respect to optimized one-way DV-QKD schemes when operated at comparable clock frequencies. However, in short-range applications such as device authentication, access-control or payment terminals, the required amount of secret key per session is modest and the logical authentication string can be embedded into a redundant, shuffled encoding, so that only a subset of the physical positions must be successfully received to reconstruct the underlying code. In this way, the reduced sifting efficiency is addressed at the protocol level using simple classical redundancy, without demanding more aggressive quantum hardware.
Interestingly, the main quantitative advantage of Loop-Back lies in its robustness against isotropic depolarizing noise, which is typically associated with long-distance or highly perturbed optical channels. This feature can nevertheless be exploited in short-range but non-ideal environments, for instance when the remote device is partially occluded or embedded in a non-transparent medium (e.g., inside bags, cases or enclosures) that introduces strong polarization scrambling. In such settings, the enhanced depolarization tolerance becomes a relevant asset compared with one-way protocols using the same hardware resources.
Finally, the security analysis presented in this work is carried out under an idealized symmetric depolarizing-channel model and in the asymptotic regime. Extending the treatment to include finite-size effects, realistic device imperfections and more general attack models is an important direction for future work. Moreover, as in any bidirectional QKD protocol, the Loop-Back configuration requires standard countermeasures against bright-light and Trojan-horse attacks on the remote module, even though the absence of single-photon detectors at Bob already reduces his side-channel exposure.
A concise overview of the error models and attack scenarios considered in this work, together with their implications for the Loop-Back architecture, is presented in Table 1.

Table 1.
Summary of the main error models and security considerations addressed for the Loop-Back QKD protocol.
7. Advances and Perspectives
The Loop-Back QKD architecture represents a structural evolution of bidirectional quantum communication protocols such as LM05, achieving passive operation, intrinsic channel verification, and continuous intrusion detection. Building upon this foundation, the introduction of a three-basis configuration extends the theoretical robustness of the system, improving its tolerance to depolarization and its statistical stability without increasing experimental complexity.
The transition from LM05 to Loop-Back QKD replaces active modulation with passive reflection, transforming Bob from an information-encoding node into a purely optical regenerator. This structural simplification removes side-channel vulnerabilities while preserving the compensating effect of bidirectional propagation. The next logical step—the extension from two to three polarization bases—constitutes a dimensional expansion of the encoding space. While the average sifting efficiency slightly decreases to , the protocol benefits from a lower effective error rate and greater noise resilience.
In the two-basis configuration, half of the transmitted rounds correspond to matching bases, which fully experience the channel error e, while the remaining half benefit from the orthogonality-based filtering that effectively cancels depolarization. In the three-basis system, the probability of matching bases is reduced to , and two-thirds of the rounds exploit the filtering effect. As a result, the effective error rate for the accepted key bits becomes
compared to for the two-basis case. This reduction by one third translates into improved noise tolerance and a more gradual degradation of the secret key rate as the channel QBER increases.
Beyond error suppression, the use of three mutually orthogonal bases introduces statistical symmetry into the operation of the protocol. In the two-basis version, the basis pairings alternate between X and Z, producing an inherent anisotropy in the sampling of polarization states. The triaxial configuration uniformly distributes state preparation and reflection across the Bloch sphere, reducing systematic bias and improving the homogeneity of the raw key distribution. This property strengthens the resistance to adaptive attacks and polarization drift, particularly over long-distance fiber links where birefringence fluctuates dynamically.
Moreover, the three-basis framework generalizes the principle of orthogonality-based inference: since each measurement plane shares overlap with the other two, every mismatched event contributes indirectly to the estimation of channel stability. This continuous sampling of orthogonal subspaces enhances real-time monitoring and allows the system to distinguish depolarization effects from deliberate eavesdropping with higher statistical confidence.
The implementation of the three-basis Loop-Back protocol does not require additional optical components beyond those used in the two-basis version. The same electro-optic modulator (EOM) and retroreflector can be operated under three discrete voltage settings corresponding to the bases X, Y, and Z. Synchronization and timing constraints remain identical, as all modulation events are passive and randomized. Consequently, the scalability of the system is achieved entirely in software—through an expanded control sequence—without modification of the optical hardware.
From a practical perspective, the three-basis Loop-Back configuration combines the advantages of passive bidirectional QKD with an expanded polarization space that provides improved noise resilience and enhanced statistical uniformity. Although the raw information gain remains comparable to the two-basis version ( bits/pulse), the reduction in effective channel error () directly translates into an extended secure communication range and increased stability under fluctuating channel conditions.
In the context of short-range deployments, an interesting direction for future work is the integration of Loop-Back QKD with tailored classical coding for authentication. Instead of requiring every quantum round to contribute directly to a raw key, the logical authentication string could be embedded into a redundant, shuffled pattern spread over multiple Loop-Back exchanges, so that only a subset of the detected positions needs to be successfully received to reconstruct the underlying code. This approach shifts part of the burden from quantum hardware to classical post-processing, leveraging simple repetition- or erasure-like coding combined with random interleaving. A full information-theoretic and implementation-level study of such redundancy schemes, including optimal overhead, robustness against noise and joint security with the quantum layer, is left for future work.
8. Conclusions
The Loop-Back QKD protocol provides a versatile framework for secure key distribution and authentication across scalable and mobile quantum networks, balancing efficiency, security, and implementation simplicity. Its quasi-passive Bob architecture—requiring minimal hardware and no detection modules—makes it particularly suitable for low-power or space-constrained environments such as portable quantum devices, edge nodes, and IoT infrastructures. By concentrating all active functionality at Alice’s station, the system supports compact, energy-efficient deployments with reduced synchronization and calibration overhead.
A principal theoretical advantage of the scheme lies in its intrinsic error-suppression mechanism: the combination of active polarization regeneration and orthogonality-based filtering reduces the effective channel error to in the two-basis version and in the three-basis configuration. This improvement effectively doubles the tolerable QBER threshold relative to BB84 (up to ), enabling reliable operation in noisy or lossy optical channels. Because the protocol remains conceptually equivalent to BB84 up to the sifting phase, it inherits its well-established theoretical security while simplifying experimental implementation.
Security is reinforced through multiple layers of physical and statistical defense. Continuous round-trip monitoring enables real-time detection of man-in-the-middle (MiTM) attempts via delay-invariance analysis, while the passive nature of Bob’s module inherently mitigates photon-number-splitting (PNS) and side-channel attacks.
Overall, the Loop-Back QKD protocol constitutes a practical and theoretically grounded alternative to classical authentication and key-exchange methods, such as QR-based or NFC-based secure identification. Its lightweight optical architecture, coarse synchronization tolerance, and resilience to depolarization make it an appealing candidate for integration into emerging quantum-mobile ecosystems. While current results are primarily theoretical, ongoing experimental validation aims to confirm the feasibility, scalability, and robustness of this protocol in real-world mobile and distributed quantum communication scenarios.
Author Contributions
Conceptualization, L.A.L.-P.; Methodology, L.A.L.-P.; Validation, P.M.-C.; Formal analysis, L.A.L.-P.; Writing–original draft, L.A.L.-P.; Writing—review & editing, P.M.-C.; Visualization, L.A.L.-P.; Project administration, P.M.-C.; Funding acquisition, P.M.-C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Universidad Técnica Federico Santa María under project PI_LII_24_15, and by the Agencia Nacional de Investigación y Desarrollo (ANID), Chile, through ANID/FONDECYT grant No. 11251432. The APC was funded by Universidad Técnica Federico Santa María through ANID support.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Wiesner, S. Conjugate coding. ACM Sigact News 1983, 15, 78–88. [Google Scholar] [CrossRef]
- Horodecki, K.; Stankiewicz, M. Semi-device-independent quantum money. New J. Phys. 2020, 22, 023007. [Google Scholar] [CrossRef]
- Lizama-Perez, L.A.; López-Romero, J. Loop-Back Quantum Key Distribution (QKD) for Secure and Scalable Multi-Node Quantum Networks. Symmetry 2025, 17, 521. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. ‘Quantum cryptography: Public key distribution and coin tossing’. In Proceedings of the IEEE International Conference on Computers, Systems & Signal Processing, Bangalore, India, 10–12 December 1984; pp. 175–179. [Google Scholar]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Diamanti, E.; Lo, H.K.; Qi, B.; Yuan, Z. Practical challenges in quantum key distribution. Npj Quantum Inf. 2016, 2, 1–12. [Google Scholar] [CrossRef]
- Bennett, C.H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 1992, 68, 3121. [Google Scholar] [CrossRef] [PubMed]
- Anghel, C.; Istrate, A.; Vlase, M. A comparison of several implementations of b92 quantum key distribution protocol. In Proceedings of the 2022 26th International Conference on System Theory, Control and Computing (ICSTCC), Sinaia, Romania, 19–21 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 374–379. [Google Scholar]
- Bruß, D. Optimal eavesdropping in quantum cryptography with six states. Phys. Rev. Lett. 1998, 81, 3018. [Google Scholar] [CrossRef]
- Gottesman, D.; Lo, H.K. Proof of security of quantum key distribution with two-way classical communications. IEEE Trans. Inf. Theory 2003, 49, 457–475. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Tamaki, K.; Lo, H.K.; Fung, C.H.F.; Qi, B. Phase encoding schemes for measurement-device-independent quantum key distribution with basis-dependent flaw. Phys. Rev. A—Atomic Mol. Opt. Phys. 2012, 85, 042307. [Google Scholar] [CrossRef]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, W.J.; Jiang, C.; Chen, J.P.; Zhang, C.; Pan, W.X.; Ma, D.; Dong, H.; Xiong, J.M.; Zhang, C.J.; et al. Experimental twin-field quantum key distribution over 1000 km fiber distance. Phys. Rev. Lett. 2023, 130, 210801. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Bernstein, D.J. Post-quantum cryptography. In Encyclopedia of Cryptography, Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2025; pp. 1846–1847. [Google Scholar]
- Yin, J.; Cao, Y.; Li, Y.H.; Liao, S.K.; Zhang, L.; Ren, J.G.; Cai, W.Q.; Liu, W.Y.; Li, B.; Dai, H.; et al. Satellite-based entanglement distribution over 1200 kilometers. Science 2017, 356, 1140–1144. [Google Scholar] [CrossRef] [PubMed]
- Ren, J.G.; Xu, P.; Yong, H.L.; Zhang, L.; Liao, S.K.; Yin, J.; Liu, W.Y.; Cai, W.Q.; Yang, M.; Li, L.; et al. Ground-to-satellite quantum teleportation. Nature 2017, 549, 70–73. [Google Scholar] [CrossRef]
- Liao, S.K.; Cai, W.Q.; Handsteiner, J.; Liu, B.; Yin, J.; Zhang, L.; Rauch, D.; Fink, M.; Ren, J.G.; Liu, W.Y.; et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett. 2018, 120, 030501. [Google Scholar] [CrossRef]
- Zavitsanos, D.; Ntanos, A.; Stathopoulos, T.; Raptakis, A.; Setaki, F.; Lyberopoulos, G.; Kouloumentas, C.; Giannoulis, G.; Avramopoulos, H. Feasibility analysis of QKD integration in real-world FTTH access networks. J. Light. Technol. 2023, 42, 4–11. [Google Scholar] [CrossRef]
- Wabnig, J.; Bitauld, D.; Li, H.; Laing, A.; O’brien, J.; Niskanen, A. Demonstration of free-space reference frame independent quantum key distribution. New J. Phys. 2013, 15, 073001. [Google Scholar] [CrossRef]
- Tian, X.H.; Yang, R.; Liu, H.Y.; Fan, P.; Zhang, J.N.; Gu, C.; Chen, M.; Hu, M.; Lu, F.Y.; Zhu, C.; et al. Experimental demonstration of drone-based quantum key distribution. Phys. Rev. Lett. 2024, 133, 200801. [Google Scholar] [CrossRef] [PubMed]
- Bourgoin, J.P.; Higgins, B.L.; Gigov, N.; Holloway, C.; Pugh, C.J.; Kaiser, S.; Cranmer, M.; Jennewein, T. Free-space quantum key distribution to a moving receiver. Opt. Express 2015, 23, 33437–33447. [Google Scholar] [CrossRef] [PubMed]
- Devetak, I.; Winter, A. Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A Math. Phys. Eng. Sci. 2005, 461, 207–235. [Google Scholar] [CrossRef]
- Qiao, H.; Chen, X.Y. Simulation of BB84 Quantum Key Distribution in depolarizing channel. In Proceedings of the 14th Youth Conference on Communication, Dalian, China, 24–26 July 2009; pp. 123–129. [Google Scholar]
- Slimen, I.B.; Trabelsi, O.; Rezig, H.; Bouallègue, R.; Bouallègue, A. Stop conditions of BB84 protocol via a depolarizing channel (quantum cryptography). J. Comput. Sci. 2007, 3, 424–429. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Ding, Y.Y.; Chen, H.; Wang, S.; He, D.Y.; Yin, Z.Q.; Chen, W.; Zhou, Z.; Guo, G.C.; Han, Z.F. Polarization variations in installed fibers and their influence on quantum key distribution systems. Opt. Express 2017, 25, 27923–27936. [Google Scholar] [CrossRef] [PubMed]
- Lucamarini, M.; Mancini, S. Secure deterministic communication without entanglement. Phys. Rev. Lett. 2005, 94, 140501. [Google Scholar] [CrossRef] [PubMed]
- Pavičić, M. How secure are two-way ping-pong and LM05 QKD protocols under a man-in-the-middle attack? Entropy 2021, 23, 163. [Google Scholar] [CrossRef]
- Lydersen, L.; Wiechers, C.; Wittmann, C.; Elser, D.; Skaar, J.; Makarov, V. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 2010, 4, 686–689. [Google Scholar] [CrossRef]
- Boström, K.; Felbinger, T. Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 2002, 89, 187902. [Google Scholar] [CrossRef]
- Muller, A.; Herzog, T.; Huttner, B.; Tittel, W.; Zbinden, H.; Gisin, N. “Plug and play” systems for quantum cryptography. Appl. Phys. Lett. 1997, 70, 793–795. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).