Abstract
Relay channels capture the essence of several important communication scenarios such as sensor network and satellite communication. In this paper, first, we propose an efficient coding scheme for an additive white Gaussian noise (AWGN) relay channel in the presence of AWGN feedback, which generalizes the conventional scheme for the AWGN relay channel with noiseless feedback by introducing a lattice-based strategy to eliminate the impact of the feedback channel noise on the performance of the original scheme. Next, we further extend the proposed scheme to the multi-input single-output (MISO) fading relay channel (FRC) with noisy feedback. The key to this extension is to use a pre-coding strategy to transform the MISO channel into a single-input single-output (SISO) channel and applying a two-dimensional lattice coding strategy to deal with the feedback fading channel noise. Finally, we analyze the security performance of our proposed scheme in several cases, and the results of this paper are further illustrated by numerical examples.
1. Introduction
The relay channel (RC), which captures the essence of satellite communication [1,2,3], receives much attention in the literature. To explore the fundamental limit of the transmission over the RC, in recent years, the studies [4,5,6,7,8,9,10], respectively, have extended the decode-and-forward (DF) strategy [11], the compress-and-forward (CF) strategy [11], and the amplify-and-forward (AF) strategy [12] for the single relay case to the RC. These extensions have provided corresponding lower bounds on the capacity of the RC according to these relay strategies.
Nowadays, ultra-reliable and low-latency communication (URLLC) [13] serves as one of the key technologies in fifth-generation (5G) wireless communications since it supports many critical services in 5G that require a high level of reliability and low latency. Recently, the study of URLLC in the RC has received much attention, which mainly focuses on performance analysis [14,15,16] and emerging wireless access techniques [17,18,19], evaluating key metrics such as transmission rates, latency, and reliability to improve RC performance. However, there is a notable lack of attention to the design of efficient, low-complexity coding schemes for RC. This gap highlights the need for further exploration into coding strategies that can reduce computational demands while maintaining or improving system performance.
Though channel feedback does not increase the memoryless channel capacity [20], it helps to construct an efficient coding scheme, such as the well-known Schalkwijk–Kailath (SK) scheme [21]. It has been shown that the SK scheme achieves a desired decoding error probability with extremely short coding blocklength [22], which indicates that it may be a good code for URLLC scenarios. Recently, ref. [23] extended the classical SK scheme [21] to the Gaussian relay channel (GRC) with noiseless feedback. In [23], the AF relay strategy and the classical SK coding scheme are combined, and to eliminate the impact of the relay noise on the performance of the original coding scheme, an auxiliary signal is generated, and the difference between the receiver’s received signal and this auxiliary signal is used for the receiver’s decoding. However, note that this SK-type scheme is based on noiseless feedback, which is unrealistic in practical communication scenarios. Then, it is natural to ask: can we extend the SK-type scheme in [23] to the noisy feedback case?
On the other hand, due to the broadcast nature of wireless communication, in recent years, physical layer security (PLS), which started from [24], has been proven to be a useful tool to deal with the eavesdropping problem in wireless communication. In [25], it has already been shown that the classical SK [21] scheme achieves perfect weak secrecy by itself, where the perfect weak secrecy is known as one standard for the PLS. This self-secure property has been extensively studied in the literature; see [26,27,28]. However, we should note that this property holds for the noiseless feedback case, and whether it also holds for the noisy feedback case remains unknown.
To answer the aforementioned questions, in this paper, we aim to extend the SK-type scheme to the GRC with noiseless feedback [23] to the wireless scenario and explore its security performance when an external eavesdropper is considered. First, we propose such an extended scheme for the additive white Gaussian noise (AWGN) RC in the presence of AWGN feedback, where the modulo-lattice function is introduced to mitigate the influence of noise within the feedback channel on the efficacy of the SK scheme.
Furthermore, the utilization of multiple-input, single-output (MISO) technology in satellite relay communications offers significant advantages in enhancing the performance and reliability of the communication system [2,3]. The above scenario can be modeled as using multiple transmitting antennas at the satellite and a single receiving antenna at the ground station and relay station. Then, another question is whether we can extend the scheme for the AWGN RC with AWGN feedback to the MISO fading relay channel (FRC) with noisy feedback. To this end, we further extend the proposed scheme to the MISO fading relay channel (FRC) with noisy feedback. In this extension scheme, to deal with the complex signals in the fading channel, we introduce the two-dimensional complex plane mapping method. Furthermore, the pre-coding strategy is used to transform the feedforward MISO channel into a complex-valued SISO channel, and the beamforming strategy is employed to convert the feedback single-input, multi-output (SIMO) channel into a complex-valued SISO channel. Then, following the scheme for the AWGN RC with AWGN feedback, the scheme for the MISO FRC with noisy feedback is obtained. Finally, we show that our extended scheme may achieve the PLS requirement for some cases.
The remainder of this paper is organized as follows. A formal definition of the RC with noisy feedback is introduced in Section 2. The proposed SK-type scheme for the AWGN RC with AWGN feedback is shown in Section 3. The extended SK-type scheme for the MISO fading RC with noisy feedback and its secrecy analysis are shown in Section 4. Numerical results are given in Section 5. Section 6 summarizes all results in this paper and discusses future works.
2. Model Formulation
The notations: and represent the real and complex space, respectively. The superscript denotes the conjugate transpose. represents the absolute value if applied to a complex number or the cardinality if applied to a set. And represents the -norm of a vector. denotes uniform distribution in . and , respectively, denote the Gaussian distribution and circularly symmetric complex Gaussian distribution with mean 0 and covariance .. and represent statistical expectation and variance for random variables, respectively. The Gaussian Q-function is defined by , and is its inverse function. The log function takes base 2 in this paper.
2.1. The Gaussian Relay Channel with Noisy Feedback
In this subsection, the communication scenario is depicted in Figure 1a, which consists of a Source, a Relay, and a Destination. Source wishes to transmit the message to Destination with the help of Relay, and the message received by Destination can be sent to Source through an AWGN feedback channel. The channel gains of the Source–Relay channel, the Relay–Destination channel, the Source–Destination channel and the Destination–Source channel are denoted by , respectively.
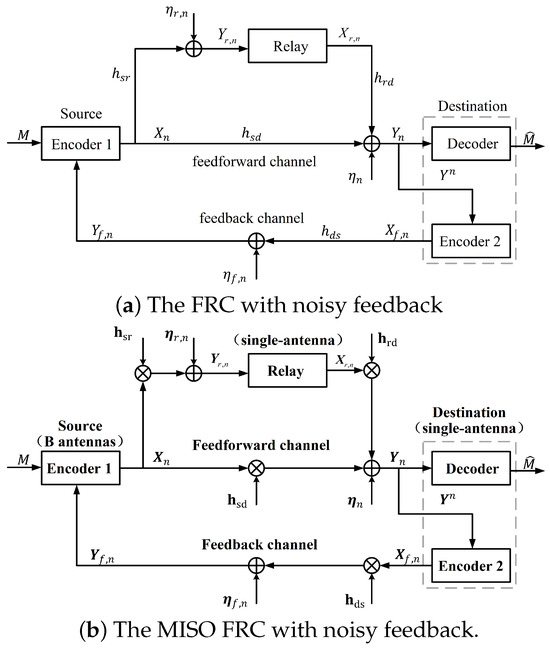
Figure 1.
The information-theoretic schematic diagram.
So the channel inputs-outputs relationships are given by
where (resp. ) and (resp. ) are the feedforward inputs (resp. outputs), and and are the feedback channel input and output, respectively. The channel noises of are independent and identically distributed (i.i.d.) as , , , respectively.
Definition 1.
For the GRC with noisy feedback in Figure 1a, a ()-code with the average power constraints consist of:
- A uniformly distributed message M, which takes values over the set .
- Encoder 1 with output , where is an encoding function of Source at the time index , satisfying the average power constraint .
- Relay with output , where is an encoding function of Relay at time index , satisfying the average power constraint .
- Encoder 2 with output , where is an encoding function of Destination at time index , satisfying the average feedback power constraint .
- Decoder has output , where ψ is the decoding function of Destination. The average decoding error probability is defined as
Definition 2.
The rate R is said to be -achievable if for given coding block length N and decoding error probability ϵ, there exists a
-code described in Definition 1 such that
The-capacity [29] of the GRC with noisy feedback is defined as the supremum over all achievable rates in Definition 2, denoted as .
Definition 3.
The modulo-d function [30,31] (also named the one-dimensional modulo-lattice function) is defined as
where is the step size of the one-dimensional modulo-lattice and represents the largest integer that is smaller than x. Proposition 1 provides the properties of the modulo-d function [30,31].
Proposition 1
([30,31]).
- (1)
- .
- (2)
- .
- (3)
- if ,otherwise, a random error termed is added to the right-hand side of (5) for , which means that a modulo aliasing error has occurred.
- (4)
- Let , for any and .
- (5)
- For any random variable Y that is statistically independent of ν, is statistically independent of Y.
2.2. The MISO Fading Relay Channel with Noisy Feedback
The MISO FRC with noisy feedback studied in this subsection is also depicted in Figure 1b, which consists of a Source equipped with antennas, a Relay, and a Destination with a single-antenna, respectively. The channel gains of the Source-=Relay channel, the Relay-=Destination channel, the Source=-Destination channel and the Destination-=Source channel are denoted by , respectively. In this work, the channels of these four links are independent and experience quasi-static fading; i.e., the channel state of each link is constant during one block and varies independently for the next.
So the channel input–output relationships are given by
where (resp. ) and (resp. ) are the feedforward inputs (resp. outputs), and and are the feedback channel input and output, respectively. The channel noises of and are i.i.d. as , , respectively, and the elements of are i.i.d. as .
Definition 4.
For the MISO FRC with noisy feedback in Figure 1b, a -code with the average power constraints consists of
- A uniformly distributed message M, which takes values over the set .
- Encoder 1 with output , where is an encoding function of Source at the time index , satisfying the average power constraint .
- Relay with output , where is an encoding function of Relay at time index , satisfying the average power constraint .
- Encoder 2 with output , where is an encoding function of Destination at time index , satisfying the average feedback power constraint .
- Decoder has output , where ψ is the decoding function of Destination. The average decoding error probability is also defined as (2).
Definition 5.
The rate R is said to be -achievable if for given coding blocklength N and decoding error probability ϵ, there exists a -code described in Definition 4 such that (3). The -capacity [29] of the FRC with noisy feedback is defined as the supremum over all achievable rates in Definition 4, denoted as .
Definition 6.
The two-dimensional modulo-lattice function [31] (modulo-Λ function) is defined as
where is a complex plane with , , j is the imaginary unit, is a complex-valued number, and is the nearest neighbor quantization of with respect to Λ.
Proposition 2
([31]).
- (1)
- The distributive law .
- (2)
- If , ; otherwise, a modulo-aliasing error has occurred.
- (3)
- Let the dither signal be uniform over Λ; then, is uniform over Λ, and .
- (4)
- For any random variable that is statistically independent of the dither signal , is statistically independent of .
3. An SK-Type Feedback Scheme for the Gaussian Relay Channel with Noisy Feedback
In this section, an SK-type feedback scheme for the Gaussian relay channel with noisy feedback is proposed. The key to this scheme involves the introduction of the modulo-lattice function to mitigate the impact of feedback channel noise on the performance of the SK-type scheme. Additionally, an auxiliary signal is generated at the receiver, which is the receiver’s estimation of the output of the AF strategy-based relay node, and using a difference between the received signal and this auxiliary signal to do the receiver’s MMSE about the transmitted message. The main result and details about this scheme are given below.
3.1. Main Result
Theorem 1.
For given coding blocklength N and decoding error probability ϵ, the lower bound on the
-capacity of the GRC with noisy feedback is given by
where
and the correlation coefficient is given by the unique solution in [0, 1] of the following equation:
Remark 1.
When the blocklength N is sufficiently large, the achievable rate approaches , which is given in (9).
Remark 2.
The upper bound of the GRC with noisy feedback is given in [23], where
is the unique solution in of the following equation
3.2. Our Achievable Scheme
3.2.1. Message Mapping Method
For a given coding blocklength N and decoding error probability , let , where M is the transmitted message uniformly distributed over the set . Divide the interval into equally spaced sub-intervals, and the center of each sub-interval is mapped one-to-one to a message value in . Let be the center of each sub-interval with respect to the message M. Since M is equi-probably distributed over the set , is approximately uniformly distributed over the interval (i.e., ) and has a variance of approximately , i.e., .
3.2.2. Dither Signal for the Feedback Channel Power Constaint
In the proposed scheme, we introduce a dither signal to ensure the transmitted codewords satisfy the feedback channel’s power constraint at time n. Here is perfectly known by Source, and it is i.i.d. generated and uniformly distributed over . In addition, is chosen to avoid modulo-aliasing errors occurring in Source.
3.2.3. Coding Procedure
At time instant 1, Source transmits
where , which satisfies the average power constraint of Source.
Meanwhile, Relay remains quiet, and Destination obtains the first output signal
then computes the first estimation of by
where is the first estimation error, denoted by
and its variance is
Then, Destination encodes
and sends back to Source. Here from Property (1) of Proposition 1 and , the power constraint of satisfies .
Then Source receives the feedback signal
At time 2, by using the feedback signals (see (28)), Source firstly computes the noisy versions of the Destination’s estimation errors, i.e.,
where follows from (28), follows from Property (1) of Proposition 1 and the fact that . In accordance with (4), we know that if , (29) can be rewritten by
otherwise, it implies that a modulo-aliasing error does occur in Source. Hence understanding how to choose the modulation coefficient is crucial to avoid the modulo-aliasing error.
After decoding , Source sends
where , and , which satisfies the average power constraint of Source.
At this time instant, Relay also keeps quiet. And once it receives
Destination carries out the MMSE of based on and updates the estimation of by computing
where the second estimation error is denoted as
and the variance of the estimation error is denoted as
Iteration:
At time instant , Destination sends
back to Source.
At time , once it receives the feedback signals
Source computes the noisy version of the Destination’s estimation errors, i.e.,
where follows from (37), Property (1) of Proposition 1 and the fact that . follows from , which means that modulo-aliasing error does not occur in Source.
After decoding , Source transmits
where , and , which satisfies the average power constraint of Source.
At time instant , Relay does not remain quiet and transmits the received messages from Source to Destination through an AF strategy, that is, it transmits a scaled version of its observation in the previous step, i.e.,
where the scaling factor is chosen as
and , which satisfies the average power constraint of Relay.
So, Destination obtains the n-th channel output signal
Upon receiving , Destination first computes the auxiliary signal, that is,
and this auxiliary signal will be used to form the innovation based on the fact that ,
and it carries out the MMSE of based on , then updates the estimation of by computing
where the estimation error of is denoted as
and the variance of the estimation error is denoted as
At time instant N, Destination computes the final estimation
According to the mapping method in Section 3.2.1, if the final estimation error is given by
the final estimation is closest to the transmitted point , and thus Destination successfully decodes the transmitted message M.
For better understanding, the schematic diagram of the above proposed scheme is shown in Figure 2.
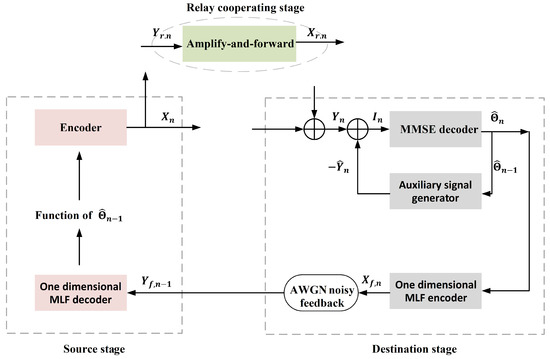
Figure 2.
The schematic diagram of the proposed SK-Type finite blocklength (FBL) scheme for the GRC with noisy feedback.
Proof.
The detailed proof is given in Appendix A. □
4. An SK-Type Scheme for the MISO Fading Relay Channel with Noisy Feedback and Its Security Analysis
In this section, an SK-type scheme for the MISO fading relay channel with noisy feedback is proposed. In this extension scheme, to deal with complex signals in the fading channel, we introduce the two-dimensional complex plane mapping method. Furthermoreavesdropper does not know t, a pre-coding strategy is used to transform the feedforward MISO channel into a complex-valued SISO channel, while a beamforming strategy is used to transform the feedback SIMO channel into a complex-valued SISO channel. Consequently, by following the scheme for the AWGN RC with AWGN feedback, we obtain the scheme for the MISO FRC with noisy feedback. The main result and security analysis of this extension scheme are given below.
4.1. Main Result
Theorem 2.
For given coding blocklength N and decoding error probability ϵ, the lower bound on the -capacity
of the FRC with noisy feedback is given by
where
and the correlation coefficient is given by the unique solution in [0, 1] of the following equation
Remark 3.
When the blocklength N is sufficiently large, the achievable rate approaches , which is given in (51).
Remark 4.
For the MISO FRC without feedback, the AF lower bound is given by [32], i.e.,
Proof.
The detailed proof is given in Appendix B. □
4.2. Security Analysis of the Proposed Extended Scheme
The communication scenario is similar to Figure 1b, except that the existence of Eavesdropper equipped with antennas. The information-theoretic schematic diagram is depicted in Figure 3. We assume that Eavesdropper can simultaneously eavesdrop on the signals of both the forward and feedback channels. Here, the channel gains of the Source–Eavesdropper channel, the Relay–Eavesdropper channel and the Destination–Eavesdropper channel are, respectively, denoted by . We assume that these three links are independent of each other and experience quasi-static fading.
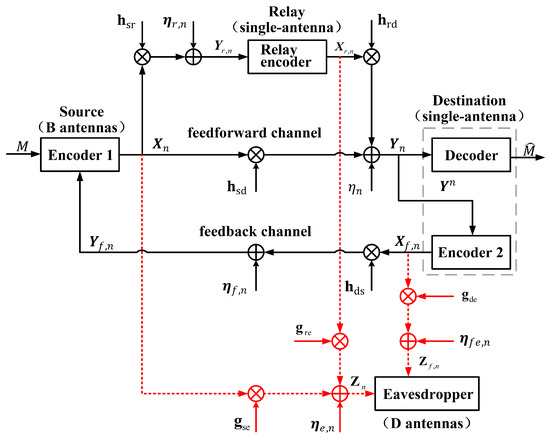
Figure 3.
The MISO FRC with noisy feedback and a multi-antenna external eavesdropper.
So, the signals received by Eavesdropper are given by
where , represent the input of Source, Relay and Destination, respectively. are the channel noise, which are i.i.d. across the time index n.
Definition 7.
Following the secrecy criteria defined in [33], a normalized eavesdropper’s equivocation (also called the secrecy level) is adopted in this paper and is given by
where , , , . Here, note that corresponds to perfect secrecy, indicating that Eavesdropper cannot obtain any useful information, which was first introduced in [34], and corresponds to no secrecy constraint.
Furthermore, in terms of whether Eavesdropper is powerful enough to acquire the complex dither signal sequence shared between legal parties in our scheme, we define the following two cases.
- Case I: Eavesdropper does not know the complex dither signal sequence , and the secrecy level is defined by
- Case II: Eavesdropper knows the complex dither signal sequence , and the secrecy level is defined by
Theorem 3.
For given coding blocklength N and decoding error probability ϵ, the secrecy levels and of the proposed scheme are, respectively, lower-bounded by
where
Note that and , respectively, represent the information leaked in Source at time 1 and in the feedback channel from time 1 to .
Proof.
The detailed proof is given in Appendix C. □
5. Numerical Results
The aim of these numerical results is to evaluate the performance of our proposed schemes versus different parameters. Here, note that the simulation results for the fading scenario are based on an average of 1000 independent channel realizations.
Figure 4 shows the performance analysis of the SK-Type scheme for the GRC with noisy feedback. Here, the achievable rate of this proposed scheme is given in (8). In Figure 4a, we show the relationship between the achievable rate , the coding blocklength N and the decoding error probability . From Figure 4a, we see that when the coding blocklength N and the decoding error probability increase, the achievable rate also increases. Figure 4b depicts the relationship between the achievable rate and its asymptotic value . Figure 4b shows that as blocklength N increases, there exists an asymptotic value for the achievable rate . And as blocklength N and the power of the feedback channel increase, it will approach its asymptotic value more closely. This simulation result is the same as the theoretical result in Remark 1. Figure 4c illustrates the relationship between the relative rate and the relative power , where the relative rate and the relative power are, respectively, defined as
where is given in (8) and is given in (19). From Figure 4c, it shows that when the power of the Destination–Source feedback channel is sufficiently large, the achievable rate of the noisy feedback scheme in Theorem 1 approaches the rate of the noiseless feedback scheme in [23].
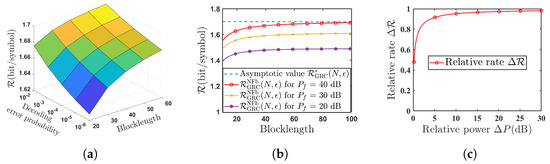
Figure 4.
Performance analysis of the proposed scheme for the GRC with noisy feedback (). (a) Achievable rate versus blocklength N and various decoding error probability (); (b) relationship between the achievable rate and its asymptotic value (); (c) relationship between the relative rate and the relative power ().
Figure 5 shows the performance analysis of the SK-Type scheme for the MISO FRC with noisy feedback. Here, the achievable rate of this proposed scheme is given in (50). The conclusions drawn in Figure 4a,b are consistent with the results in the Gaussian case; i.e, when the coding blocklength N and the decoding error probability increase, the achievable rate also increases. And as blocklength N increases, there exists an asymptotic value for the achievable rate . Figure 5c illustrates the influence of the number of the Source’s antennas B on the achievable rate in the proposed SK-Type coding scheme. From Figure 5c, we conclude that as the number of the Source’s antennas B increases, the achievable rate also increases, which indicates that the number of the Source’s antennas B can bring a gain to the achievable rate of our proposed SK-Type coding scheme. Figure 5d compares the achievable rates of the SK-Type coding scheme for the MISO FRC with noisy feedback and the scheme without feedback [32], where both Relays use the AF strategy. Figure 5d shows that our proposed scheme can significantly enhance the achievable rate even in the presence of noise in the feedback channel.
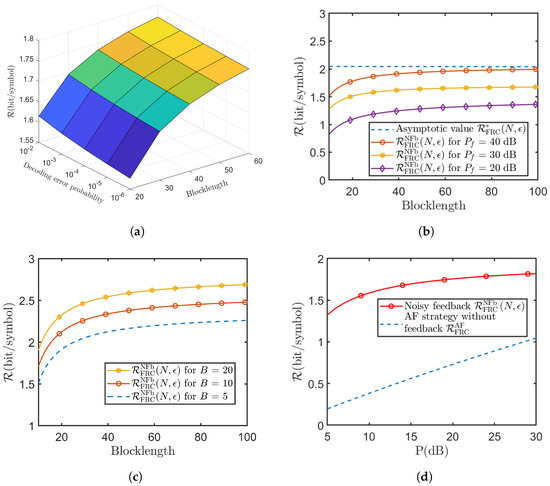
Figure 5.
Performance analysis of the proposed scheme for the MISO FRC with noisy feedback (). (a) Relationship among the achievable rate , blocklength N and decoding error probability (); (b) telationship between the achievable rate and its asymptotic value (); (c) the influence of the number of Source’s antennas B on the achievable rate (); (d) comparison of achievable rate for MISO FRC with noisy and without feedback ().
Figure 6 shows the relationship between secrecy level , blocklength N and decoding error probability of the proposed SK-Type FBL coding scheme for the MISO FRC with noisy feedback and in the presence of Eavesdropper. From Figure 6a,b, we see that both the secrecy level in Case I and Case II increase with the increase of the blocklength N and decoding error probability . To be specific, when the blocklength and decoding error probability , the secrecy level in case I has already exceeded 0.99 (secrecy level equal to 1 corresponds to perfect secrecy). However, under the same parameters, the secrecy level in case II only approaches 0.7. This result indicates that the maximum secrecy level achieved in case I (Eavesdropper does not know the complex dither signal sequence ) is superior to that of case II (Eavesdropper knows complex dither signal sequence ), which is consistent with the theoretical analysis.
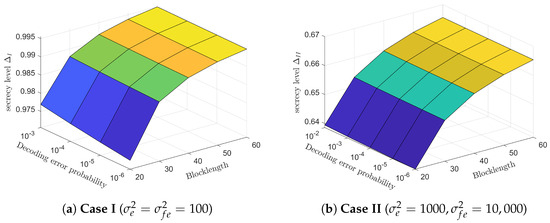
Figure 6.
The relationship among the secrecy levels , blocklength N, and decoding error probability of the proposed scheme for the MISO FRC with noisy feedback and a multi-antenna external Eavesdropper ().
Figure 7 shows the relationship between the secrecy level and blocklength N under various powers of the proposed SK-Type FBL coding scheme. Figure 7a compares the secrecy level in Case I under different powers of Source encoder P. It is easy to see that secrecy level in Case I approaches perfect secrecy when the blocklength N is about 100, and a larger P causes secrecy performance degradation on small N. Figure 7b, plots secrecy level in Case II under several powers of the feedback channel . From this figure, we can see that the secrecy level in Case II of the proposed scheme cannot achieve perfect secrecy in general cases. Actually, only when the channel quality of Destination-Eavesdropper is much poorer (i.e., ), the secrecy level in Case II may approach 1 as the blocklength N tends to infinity.
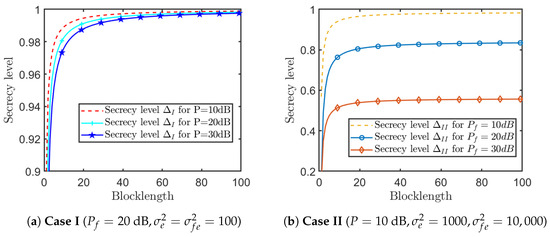
Figure 7.
Relationship between the secrecy levels and blocklength N under various power ().
6. Conclusions and Future Work
In this paper, we first proposed an SK-Type FBL coding scheme for the GRC with noisy feedback by introducing the lattice-based strategy to reduce the impact of the feedback channel noise. Numerical results show that when the power of the feedback channel is sufficiently large, the achievable rate almost approaches the rate of the GRC with noiseless feedback, and the required blocklength to achieve a desired decoding error probability is significantly short. Then, based on this scheme, we extended it to the MISO FRC with noisy feedback. The essence of this proposed scheme is to further extend the original real number scheme to the complex number. Simulation results show that even if there is noise in the feedback channel, this proposed scheme can still significantly improve the achievable rate of the MISO FRC without feedback. Finally, for the above MISO FRC with the noisy feedback model, we further consider multi-antenna Eavesdropper and derive a lower bound of the secrecy level in different cases by calculating the equivocation rate when Eavesdropper knows the complex dither signal sequence or not. We show that though perfect secrecy cannot be achieved in the noisy feedback model, it almost approaches perfect secrecy for some special cases. One possible future work is to extend this scheme to the fading MIMO case.
Author Contributions
Formal analysis, H.Y.; writing—original draft, R.H.; writing—review and editing, H.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author due to (specify the reason for the restriction).
Acknowledgments
Authors would like to thank anonymous reviewers for careful reading of the manuscript and providing constructive comments and suggestions, which have helped them to improve the quality of the paper.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A. Coefficient’s Derivation and Error Probability Analysis of Theorem 1
Let be the estimate of the transmitted message M, the decoder declares an error if . To determine the parameters, we need to analyze the error event in . And the error events of the SK-Type FBL approach for the GRC with noisy feedback are described in Section 3.2.3, consisting of
- (1)
- A modulo-aliasing error occurs in Source at time instant . The event is defined as
- (2)
- A decoding error occurs in Destination at time instant N. The event is defined as
Hence, by applying the union bound, we can derive
where denotes the complement of the set C, , . represents the error probability that a modulo-aliasing occurs in Source at time instant n when there is no error occurring in all previous times, and represents the error probability of the final decoding without any modulo-aliasing error occurring in Source before time instance N.
For a given decoding error probability , let
For the event , since no modulo-aliasing error occurs before time instant n, from (A1) and the fact that is Gaussian-distributed, we conclude that . From (A1), (A4) and , we have
To simplify the calculation, we introduce a looseness parameter , which is denoted by
According to (38), we obtain
where follows from the fact that is dependent on , follows from (A7), and follows from .
To derive the achievable rate of this SK-type scheme, we focus on the final estimation error. At time instant 1, the estimation error and its variance are given in (25) and (26). So we consider the second moment and the following moments.
At time instant 2, we first need to calculate the MMSE estimation coefficient of Destination based on , that is,
and the estimation error is given in (34). So, the variance of is
where is given in (26).
At time instant , similar to the second moment, we also calculate the MMSE estimation coefficient of Destination based on instead of ; that is,
where .
The estimation error at time instant is given in (46), so the variance of is
where is the correlation coefficient between and , denoted by
and
It is worth noting that the initial value of is given by
From (A13) and (A14), it is apparent that . By applying Cesáro’s Mean Theorem in [20] to the , it follows that this sequence will converge to a unique fixed point in . Hence, we obtain the following equation
where
Let be defined as the unique solution within of (A16). Then, according to (A12), the variance of the final estimation error is as follows
where
Substituting (A18) and (A19) into (A20), we obtain
where and are, respectively, given in (9) and (10). It should be noted that represents the maximum achievable rate when blocklength N is sufficiently large. And represents the achievable rate loss caused by given blocklength N and decoding error probability .
Appendix B. Proof of Theorem 2
Appendix B.1. Channel Transformation Strategy
Pre-coding strategy for the feedforward MISO channels: At time instant , the output signal received by Destination is given in (6). Let
where , and
which indicates that the power constraint of and are exactly the same as that of , respectively. Therefore, by substituting (A22) into (6), the signal received by Destination can be further expressed as
Specifically, the link from Source to Relay is also a MISO channel, and the messages sent by Source and Relay are related. So, at time instant , the signal received by Relay can be further expressed as
where , and
. It indicates that the complex-valued feedforward MISO FRC can be transformed into a complex-valued single-input single-output (SISO) FRC case.
Beamforming strategy for the feedback SIMO channel: At time , the signal received by Source (see (6)) can be proceeded as
where . This indicates that the complex-valued feedback SIMO channel can be transformed into complex-valued SISO channels.
Appendix B.2. Message Mapping Method
In the proposed SK-Type FBL scheme for the MISO FRC with noisy feedback, we extend the one-dimensional real number axis mapping in the GRC with noisy feedback to the two-dimensional complex plane mapping. To be specific, for given coding blocklength N and decoding error probability , let , where M is the transmitted message uniformly distributed over the set . We divide a complex plane region into equally spaced sub-complex plane regions with both the length and width of each sub-complex plane region being . The message M is one-to-one mapped to the center point of each sub-complex plane region, denoted as , where and , respectively, represent the real and imaginary parts of the complex element , j is the imaginary unit. Since M is equi-probably distributed over the set , and are both approximately uniformly distributed over the interval (i.e., ), and their variances approximately equal , i.e., , so
Appendix B.3. Dither Signal for the Feedback Channel Power Constaint
In this proposed scheme, we further extend the dither signal in the real number (see in Section 3.2.2) to the complex dither signal to ensure the codewords encoded by Destination satisfy the power constraints at time n. It is also perfectly known by Source and Destination, and it is i.i.d. generated and uniformly distributed over , where with . Due to the average power constraint of on the feedback channel encoder, the value of d is . In addition, is the real-valued number and is chosen to avoid modulo-aliasing errors occurring in Source.
Appendix B.4. Coding Procedure
The specific coding process is similar to what was described in Section 3.2.3. For the similar parts, we omit them directly, focusing here on elaborating the distinctions from Section 3.2.3.
After channel transformation, at time 1,
- Source sends , the relay keeps quiet and Destination receives .
- Once it receives , Destination first computes the estimation of by . The first estimation error is denoted by , and the variance of is .
- Then, Destination uses the two-dimensional modulo- function to encode as and transmits it back to Source via a noisy feedback channel.
At time 2,
- Once receiving , Source also uses the two-dimensional modulo- function to decode this message and computes the noisy versions of Destination’s estimation error, i.e., . If the modulo-aliasing error does not occur, using Property (2) of Proposition 2, Source can obtain .
- The Source sends to Destination, where . At this time instant, Relay also keeps quiet, so Destination receives the output signal .
- Next, Destination evaluates MMSE of based on and updates the estimation of by computing . The second estimation error is denoted by , and the variance of is . Then, Destination encodes and transmits it back to Source via a noisy feedback channel.
At time ,
- Once it receives , Source computes the noisy versions of Destination’s estimation error, i.e., . If the modulo-aliasing error does not occur, using Property (2) of Proposition 2, Source can get .
- The Source sends to both the Relay and Destination, where . Furthermore, Relay does not keep quiet and utilizes the AF strategy to transmit a scaled version of ; that is, , and the value of the Relay’s AF coefficient is .
- Next, the n-th channel output signal of Destination received is . Destination first calculates the auxiliary signal about the received message , then forms the innovation based on the fact that . is denoted by .
- Then Destination evaluates MMSE of based on and updates the estimation of by computing . The estimation error at time instant is denoted by , and the variance of is .
Finally, at time instant N, Destination computes the final estimation . According to the mapping method in Appendix B.2, if the final estimation error satisfies both of the following conditions
the final estimation is closest to the , and thus Destination successfully decodes the message M.
For a better understanding, the schematic diagram of the scheme proposed above is shown in Figure A1.
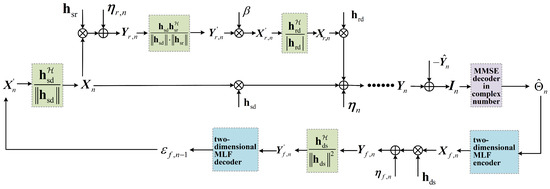
Figure A1.
The schematic diagram of the proposed SK-type FBL scheme for the MISO GRC with noisy feedback.
The coefficient’s derivation and the analysis of error probability for Theorem 2 are fundamentally consistent. We omit the similar parts directly and focus on elaborating the differences between them. See details below.
Appendix B.5. Coefficient’s Derivation and Error Probability Analysis
The error events of the SK-type FBL coding scheme for the MISO FRC with noisy feedback described in Appendix B.4 consist of
- (1)
- A modulo-aliasing error occurs in Source at time instant . The event is defined aswhere and are both complex numbers, so (A30) can be further expressed aswhere and the subscripts R and I represent the real and imaginary parts of the original complex elements, respectively.
- (2)
- A decoding error occurs in Destination at time instant N. The event is defined as
Hence, the error probability is bounded by (A3). And for a given decoding error probability , from (A30)–(A32), let
Since no modulo-aliasing error occurs at time instant , from (A30) and (A31) and the fact that is a circularly symmetric Gaussian distribution, we conclude that , . So we have
where .
Similar to the GRC scenario, we also introduce a looseness parameter L, which is denoted by
Then, we determine the appropriate selection of coefficient ,
where is the real-value number.
According to , we obtain
where follows from .
The computation process of estimation errors at each time instant is analogous to that described in Appendix A. Here, we will omit the detailed procedures and provide the results directly.
At time instant 1, and .
At time instant 2, , where
and
At time instant , , where
where .
So, at time instant N, the variance of the final estimation error is as follows
where
is given in (A39). is defined as the unique solution within of the following equation,
and
Appendix C. Proof of Theorem 3
For the MISO FRC case, at time n, according to (A22) and (62), the signals received by Eavesdropper can be rewritten as
The proof of Theorem 3 consists of the following two parts (I)–(II).
- (I)
- To analyze the secrecy level , can be bounded by
where
- (a)
- follows from the fact that is a deterministic function of M, , and conditioning reduces entropy;
- (b)
- follows from (A47);
- (c)
- follows from , and are deterministic functions of . Additionally, is only dependent on the complex dither signal sequence (see Property (2) of Proposition 2), and is independent of ;
- (d)
- follows from the fact that is independent of ;
- (e)
- follows fromwhere follows from and represents a identity matrix.
- (II)
- To analyze secrecy level , can be bounded bywhere
- (a)
- follows from the fact that is a deterministic function of M, , and conditioning reduces entropy;
- (b)
- follows from (A47);
- (c)
- follows from , and are deterministic functions of ;
- (d)
- follows from the fact that , is independent of , for , and are both deterministic functions of ;
- (e)
- follows fromwhere is similar to (A49).
According to (I)–(II), the proof of Theorem 3 is completed.
References
- De Sanctis, M.; Cianca, E.; Araniti, G.; Bisio, I.; Prasad, R. Satellite communications supporting internet of remote things. IEEE Internet Things J. 2016, 3, 113–123. [Google Scholar] [CrossRef]
- An, K.; Lin, M.; Liang, T.; Wang, J.B.; Wang, J.; Huang, Y.; Swindlehurst, A.L. Performance analysis of multi-Antenna hybrid satellite-terrestrial relay networks in the presence of interference. IEEE Trans. Commun. 2015, 63, 4390–4404. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, D.H.; Van Chien, T.; Phan, V.D.; Voznak, M.; Chatzinotas, S. Security and reliability analysis of satellite-terrestrial multirelay networks with imperfect CSI. IEEE Syst. J. 2023, 17, 2824–2835. [Google Scholar] [CrossRef]
- Gupta, P.; Kumar, P.R. Towards an information theory of large networks: An achievable rate region. IEEE Trans. Inf. Theory 2003, 49, 1877–1894. [Google Scholar] [CrossRef]
- Xie, L.-L.; Kumar, P.R. A network information theory for wireless communication: Scaling laws and optimal operation. IEEE Trans. Inf. Theory 2004, 50, 748–767. [Google Scholar] [CrossRef]
- Xie, L.-L.; Kumar, P.R. An achievable rate for the multiple-level relay channel. IEEE Trans. Inf. Theory 2005, 51, 1348–1358. [Google Scholar] [CrossRef]
- Kramer, G.; Gastpar, M.; Gupta, P. Cooperative strategies and capacity theorems for relay networks. IEEE Trans. Inf. Theory 2005, 51, 3037–3063. [Google Scholar] [CrossRef]
- Gastpar, M. The Wyner-Ziv problem with multiple sources. IEEE Trans. Inf. Theory 2004, 50, 2762–2768. [Google Scholar] [CrossRef]
- Maric, I.; Goldsmith, A.; Medard, M. Multihop analog network coding via amplify-and-forward: The high SNR regime. IEEE Trans. Inf. Theory 2012, 58, 793–803. [Google Scholar] [CrossRef]
- Simmons, D.E.; Coon, J.P.; Warsi, N. Capacity and power scaling laws for finite antenna MIMO amplify-and-forward relay networks. IEEE Trans. Inf. Theory 2016, 62, 1993–2008. [Google Scholar] [CrossRef]
- Cover, T.M.; El Gamal, A. Capacity theorems for the relay channel. IEEE Trans. Inf. Theory 1979, 25, 572–584. [Google Scholar] [CrossRef]
- Schein, B.; Gallager, R. The Gaussian parallel relay network. In Proceedings of the 2000 IEEE International Symposium on Information Theory, Sorrento, Italy, 25–30 June 2000; p. 22. [Google Scholar]
- Durisi, G.; Koch, T.; Popovski, P. Toward massive, ultra-reliable, and low-latency wireless communication with short packets. Proc. IEEE 2016, 104, 1711–1726. [Google Scholar] [CrossRef]
- Ren, H.; Pan, C.; Deng, Y.; Elkashlan, M.; Nallanathan, A. Joint power and blocklength optimization for URLLC in a factory automation scenario. IEEE Trans. Wirel. Commun. 2020, 19, 1786–1801. [Google Scholar] [CrossRef]
- Yuan, L.; Yang, N.; Fang, F.; Ding, Z. Performance analysis of UAV-assisted short-packet cooperative communications. IEEE Trans. Veh. Technol. 2022, 71, 4471–4476. [Google Scholar] [CrossRef]
- Hu, Y.; Zhu, Y.; Gursoy, M.C.; Schmeink, A. SWIPT-enabled relaying in IoT networks operating with finite blocklength codes. IEEE J. Sel. Areas Commun. 2019, 37, 74–88. [Google Scholar] [CrossRef]
- Jee, A.; Agrawal, K.; Prakriya, S. A coordinated direct AF/DF relay-aided NOMA framework for low outage. IEEE Trans. Commun. 2022, 70, 1559–1579. [Google Scholar] [CrossRef]
- Jee, A.; Prakriya, S. Performance of energy and spectrally efficient AF relay-aided incremental CDRT NOMA-based IoT network with imperfect SIC for smart cities. IEEE Internet Things J. 2023, 10, 18766–18781. [Google Scholar] [CrossRef]
- Agrawal, K.; Jee, A.; Prakriya, S. Performance of SWIPT in cooperative networks with direct link and nonlinear energy harvesting at the battery-assisted relay. IEEE Trans. Green Commun. Netw. 2022, 6, 1198–1215. [Google Scholar] [CrossRef]
- Gamal, A.E.; Kim, Y.-H. Network Information Theory; Cambridge University Press: New York, NY, USA, 2012. [Google Scholar]
- Schalkwijk, J.; Kailath, T. A coding scheme for additive noise channels with feedback–I: No bandwidth constraint. IEEE Trans. Inf. Theory 1966, 12, 172–182. [Google Scholar] [CrossRef]
- Truong, L.V.; Fong, S.L.; Tan, V.Y.F. On Gaussian channels with feedback under expected power constraints and with non-vanishing error probabilities. IEEE Trans. Inf. Theory 2017, 63, 1746–1765. [Google Scholar] [CrossRef]
- Bross, S.I.; Wigger, M.A. On the Relay Channel With Receiver–Transmitter Feedback. IEEE Trans. Inf. Theory 2009, 55, 275–291. [Google Scholar] [CrossRef]
- Wyner, A.D. The Wire-Tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Gunduz, D.; Brown, D.R.; Poor, H.V. Secret communication with feedback. In Proceedings of the International Symposium on Information Theory and Its Applications (ISITA), Auckland, New Zealand, 7–10 December 2008; pp. 1–6. [Google Scholar]
- Dai, B.; Li, C.; Liang, Y.; Ma, Z.; Shamai Shitz, S. Impact of action-dependent state and channel feedback on Gaussian wiretap channels. IEEE Trans. Inf. Theory 2020, 66, 3435–3455. [Google Scholar] [CrossRef]
- Li, C.; Liang, Y.; Poor, H.V.; Shamai, S. A coding scheme for colored Gaussian wiretap channels with feedback. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Vail, CO, USA, 17–22 June 2018; pp. 131–135. [Google Scholar]
- Dai, B.; Li, C.; Liang, Y.; Ma, Z.; Shamai Shitz, S. Self-secure capacity-achieving feedback schemes of Gaussian multiple-access wiretap channels with degraded message sets. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1583–1596. [Google Scholar] [CrossRef]
- Xia, D.; Yang, C.; Dai, B. Two-Way Full-Duplex Gaussian Channels With or Without Eavesdropper: Revisit. IEEE Trans. Commun. 2022, 70, 5434–5450. [Google Scholar] [CrossRef]
- Ben-Yishai, A.; Shayevitz, O. Interactive schemes for the AWGN channel with noisy feedback. IEEE Trans. Inf. Theory 2017, 63, 2409–2427. [Google Scholar] [CrossRef]
- Zamir, R. Lattice Coding for Signals and Networks; Cambridge University Press: Cambridge, UK, 2014. [Google Scholar]
- Laneman, J.N.; Tse, D.N.C.; Wornell, G.W. Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Trans. Inf. Theory 2004, 50, 3062–3080. [Google Scholar] [CrossRef]
- Tekin, E.; Yener, A. The Gaussian Multiple Access Wire-Tap Channel. IEEE Trans. Inf. Theory 2008, 54, 5747–5755. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).